Message generation and authentication methods and equipment in Internet-of-vehicles system
A technology of Internet of Vehicles and vehicle equipment, applied in the field of communication, can solve problems such as lack of clear technical solutions and inability to obtain private information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
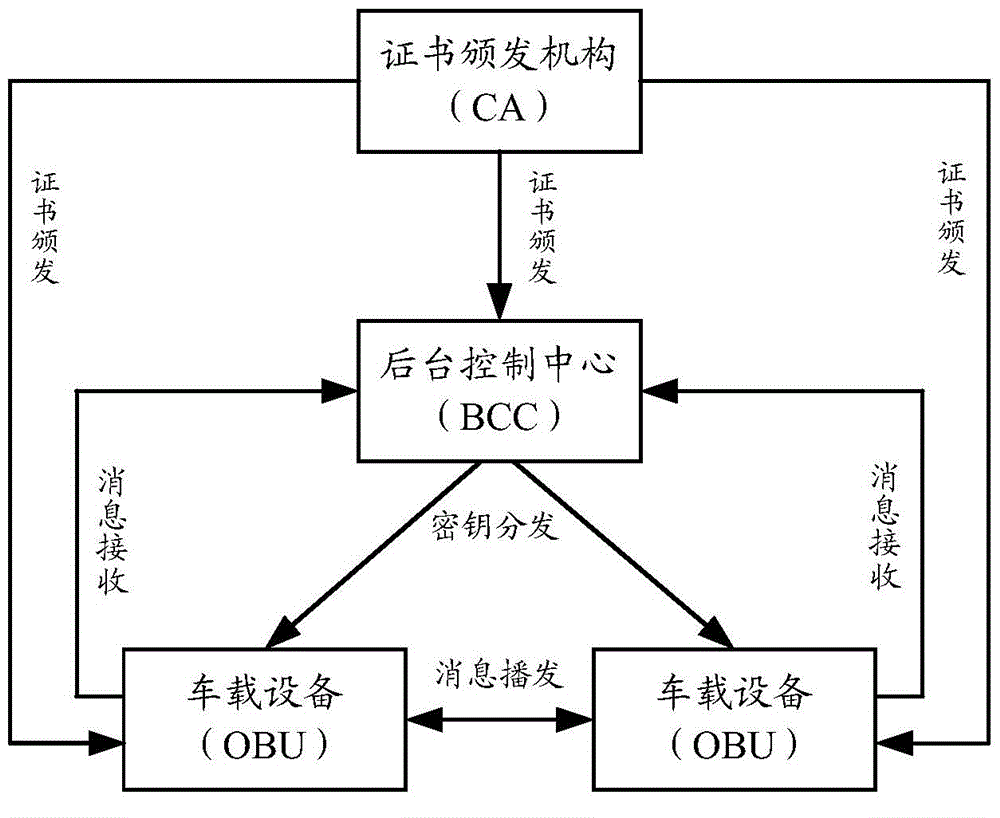
[0195] Embodiment 1. This embodiment is mainly used to describe the issuance process of the encrypted public key certificate of BCC, as follows:
[0196]1. BCC generates a key pair for asymmetric encryption and decryption: [BCC-Public-Key, BCC-Private-Key], where BCC-Public-Key is the public key used for encryption, and BCC-Private-Key is the The private key used for decryption; BCC generates a key pair [BCC-Public-Key-S, BCC-Private-Key-S] for applying for a certificate, where BCC-Public-Key-S is the public key used to verify the digital signature key, BCC-Private-Key-S is the private key used for digital signature.
[0197] 2. BCC keeps the privacy of its private key BCC-Private-Key and BCC-Private-Key-S, and uses BCC-Public-Key and BCC-Public-Key-S to apply for an encrypted public key certificate from CA, that is, The encryption public key certificate contains the encryption public key used for data encryption.
[0198] 3. CA issues to BCC an encrypted public key certific...
Embodiment 2
[0200] Embodiment 2. This embodiment is mainly used to describe the publishing process of the encrypted public key of BCC, as follows:
[0201] 1. BCC generates a key pair [BCC-Public-Key-S, BCC-Private-Key-S] for applying for a signed public key certificate, where BCC-Public-Key-S is the public key used to verify the digital signature , BCC-Private-Key-S is the private key used for digital signature.
[0202] 2. BCC keeps the privacy of its private key BCC-Private-Key-S, and uses BCC-Public-Key-S to apply for a signed public key certificate from CA.
[0203] 3. CA issues a signed public key certificate to BCC: BCC-SCert.
[0204] 4. BCC uses the signature message to correctly write the encrypted public key BCC-Public-Key into the OBU, and endows the encrypted public key with an identifier BCC-EPK that uniquely identifies the encrypted public key. BCC may write multiple different encryption public keys into OBU, and stipulate how to use these encryption public keys.
Embodiment 3
[0205] Embodiment 3. This embodiment is mainly used to describe the issuance process of the signature public key certificate of the OBU, as follows:
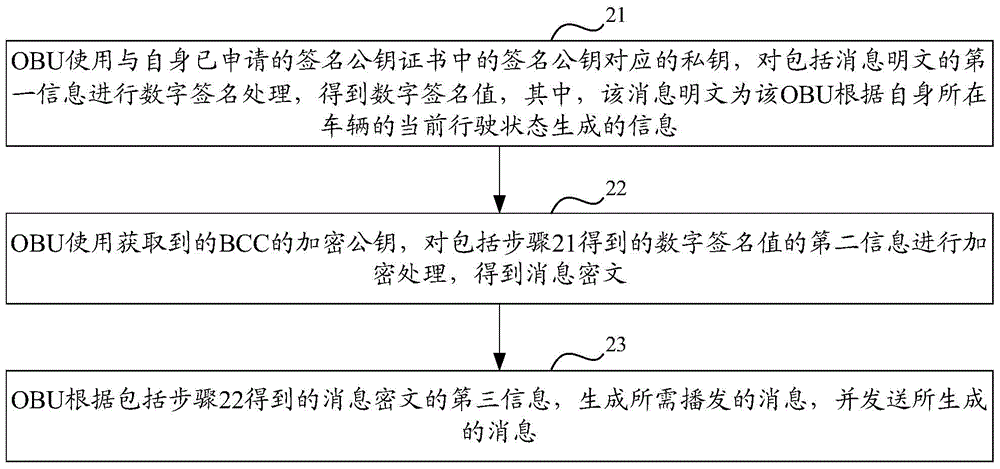
[0206] 1. OBU-X generates a key pair for digital signature: [OBUX-Public-Key, OBUX-Private-Key], where OBUX-Public-Key is the public key used to verify the digital signature, and OBUX-Private-Key is the private key used for digital signatures.
[0207] 2. OBU-X keeps the privacy of its private key OBUX-Private-Key, and uses OBUX-Public-Key to apply for a signed public key certificate from CA.
[0208] 3. CA issues a signed public key certificate to OBU-X: OBUX-SCert.
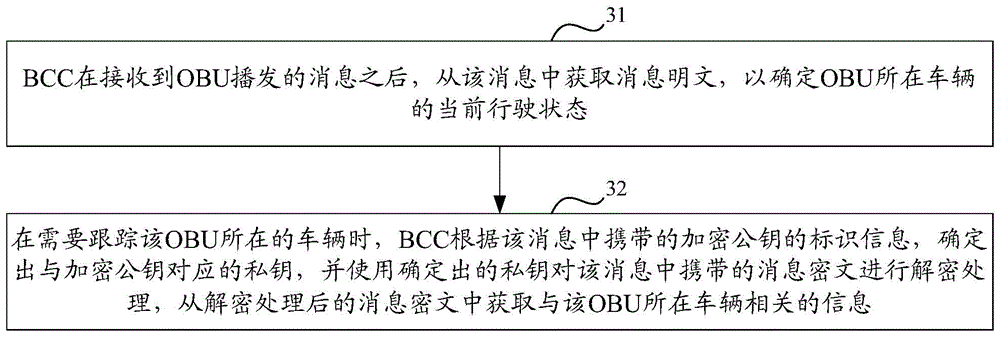
[0209] 4. BCC saves OBUX-SCert, so OBU-X does not need to carry the signature public key certificate used to verify the digital signature in its broadcast message, but only provides the identification of the signature public key certificate.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com