System and method for supplying information security operation service to medium-sized and small enterprises
A technology for information security, small and medium-sized enterprises, applied in the field of network management, business management, and information security, it can solve the problems of lack of equipment linkage, no OMC, and inability to obtain knowledge, and achieve the effect of reducing information security operation and maintenance costs and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] Below is further detailed description of the present invention according to accompanying drawing and example:
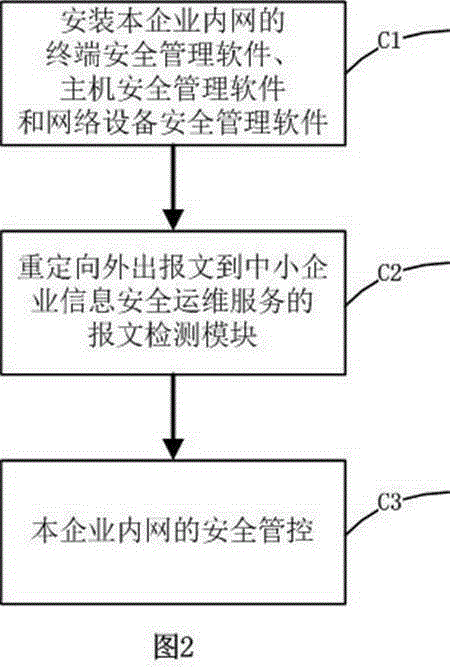
[0054] Such as figure 1 As shown, it is a functional diagram of the network information security operation and maintenance service system of the small and medium-sized enterprise information system of the present invention. It includes a security operation and maintenance data acquisition module, a security operation and maintenance service module, a security policy module and a security operation and maintenance support module.
[0055] The security operation and maintenance data collection module includes the message detection module , terminal security management module , host security management module and network device management module .
[0056] The security operation and maintenance service module includes the asset security management module and business security management module .
[0057] Among them, the terminal security management ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com