Facial feature cryptographic key generation-based internet identity authentication method
A face feature and identity authentication technology, applied in user identity/authority verification, equipment, character and pattern recognition, etc., can solve the problems of large intra-variance of biometric features, increased false rejection rate, and large key gap, etc., to achieve The effect of protecting privacy and security and convenient application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
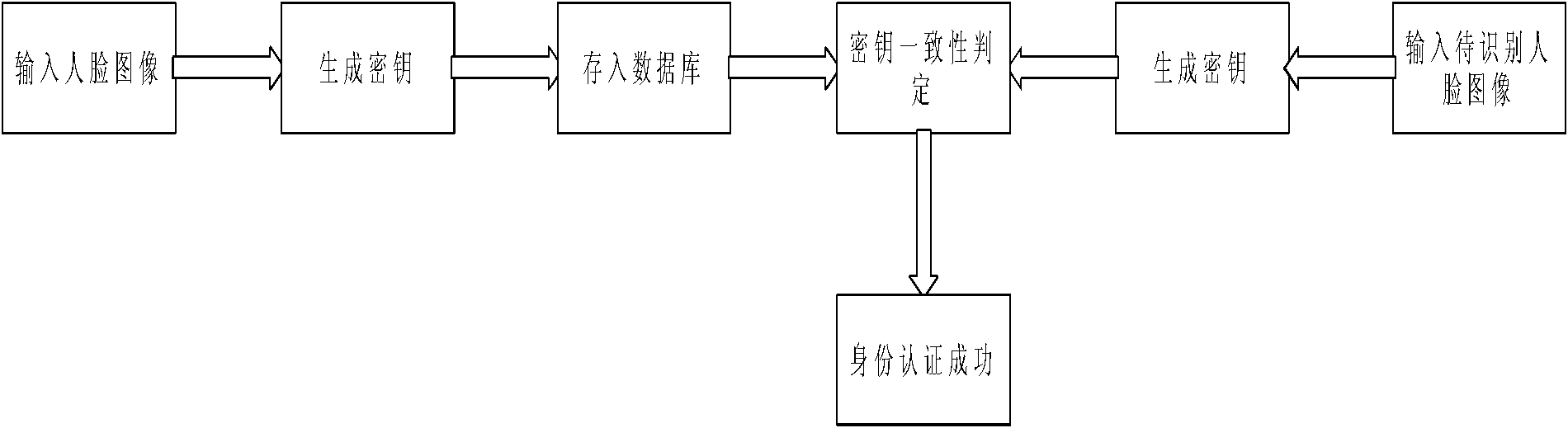
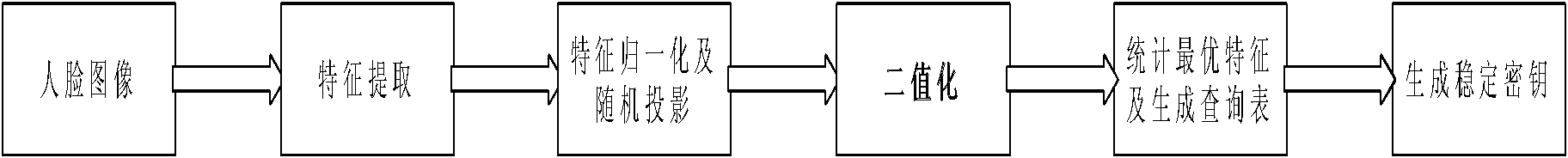
[0042] The overall process of the technical solution is shown in the attached figure 1 As shown, this example is to perform feature extraction, key generation, error correction coding, etc. on the input original face image, and use the generated key to authenticate the identity, so as to protect the security of user information. The input original image size is a BMP bitmap of 64*64 pixels, the 128-dimensional PCA feature of the input image is extracted, and the face feature is thresholded to become a binary string. The method of statistical optimal features is used to find out the distinguishable features of the input face, and all the distinguishable features are cascaded to generate the key required by the identity registration system. In the identity authentication stage, first input the face image to be recognized, perform feature extraction, thresholding, and count the optimal features to generate the key of the face to be recognized. Use the error correction code infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com