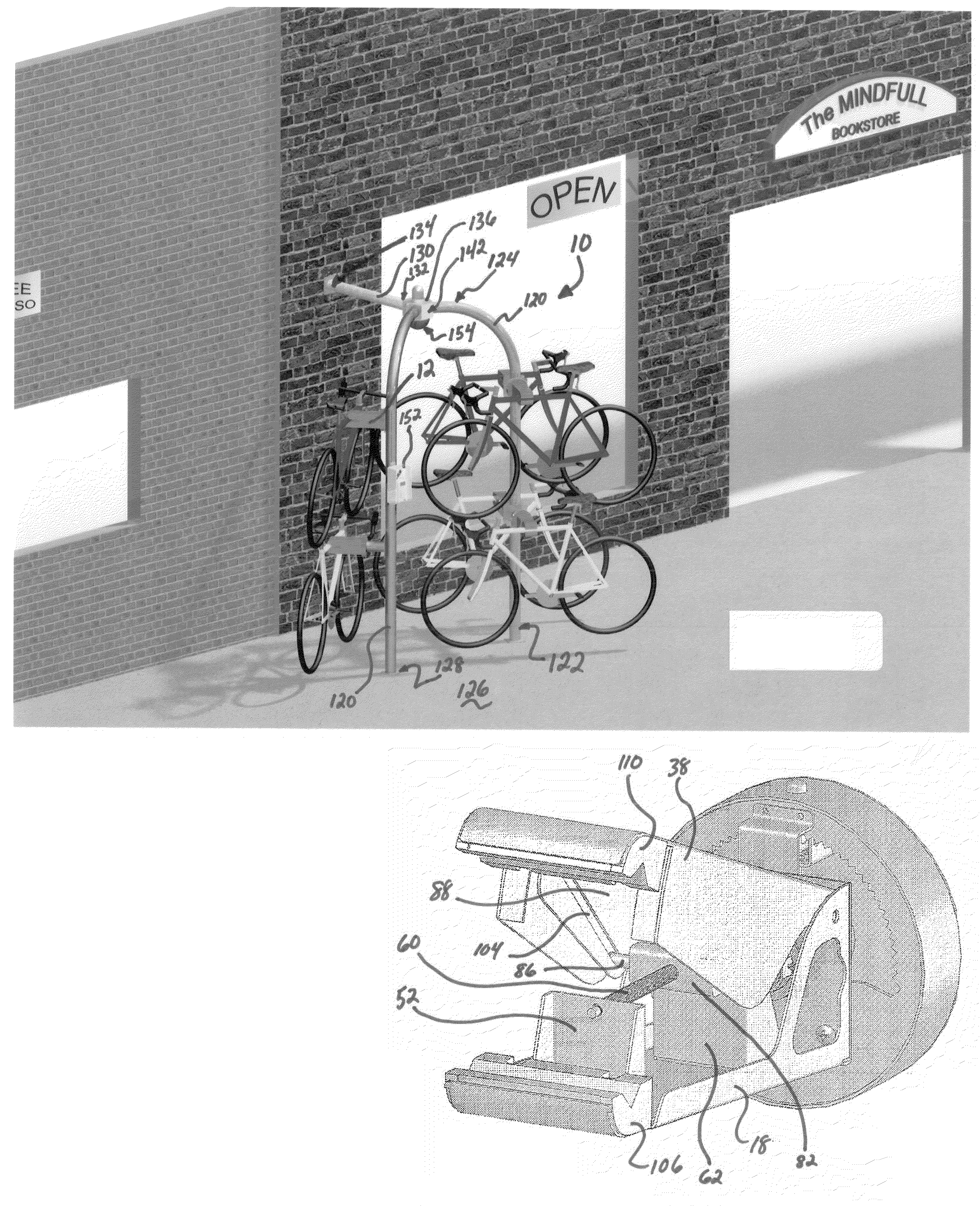Patents
Literature
146results about How to "Protection from theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Protecting Information Using Policies and Encryption
ActiveUS20130097421A1Ensure confidentialityAvoid data lossDigital data protectionSecuring communicationDocumentation procedureConfidentiality
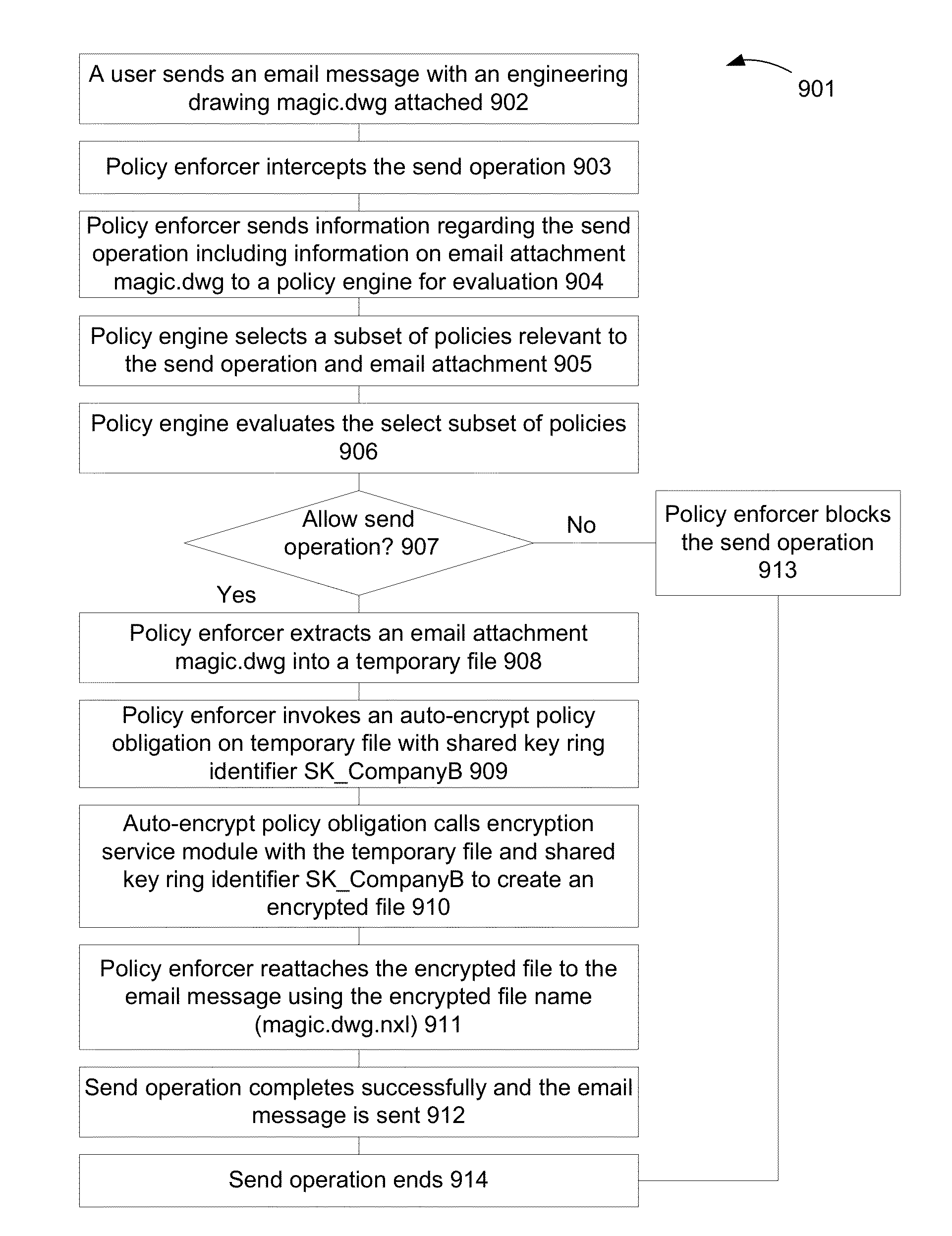
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS
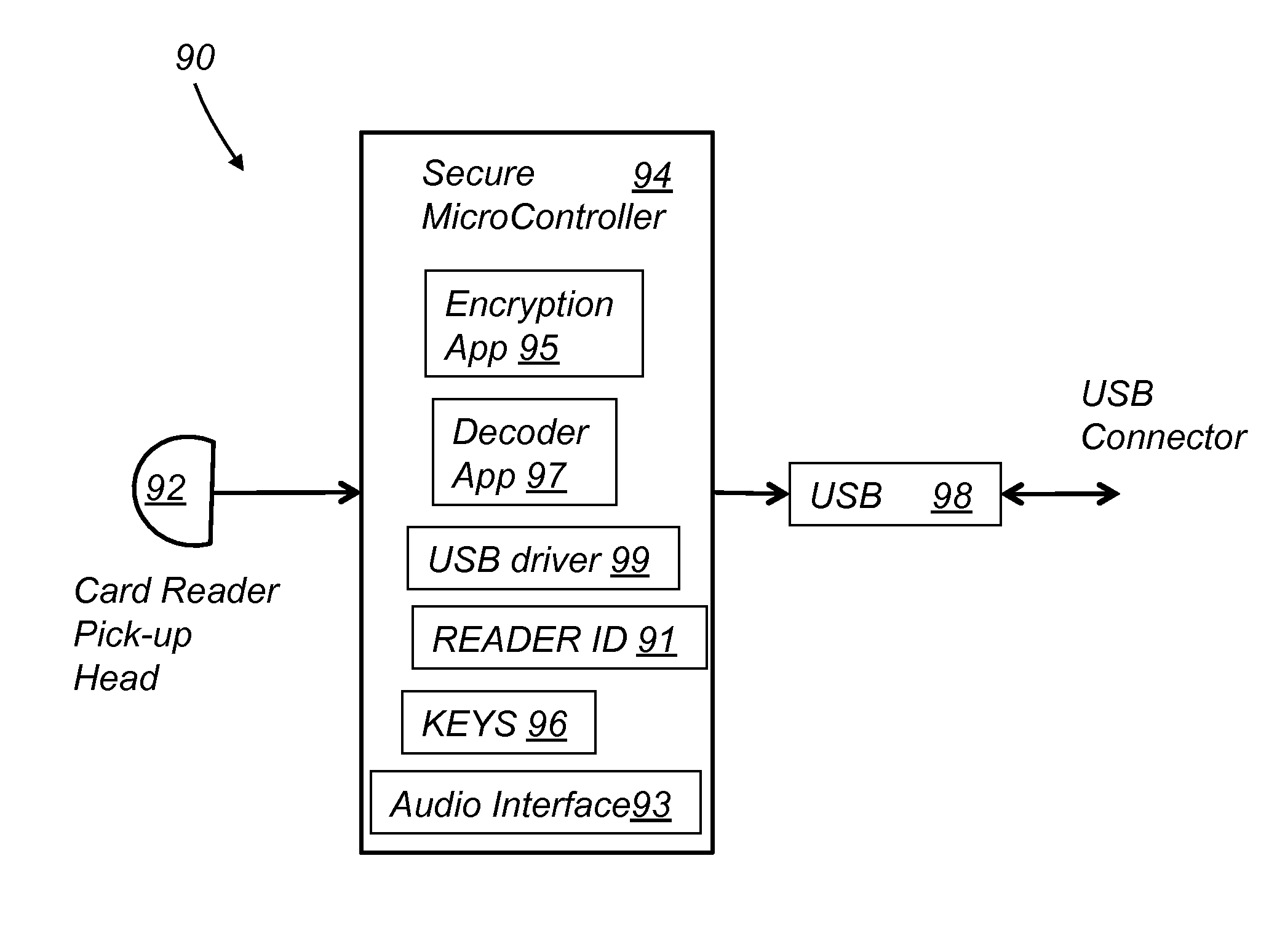
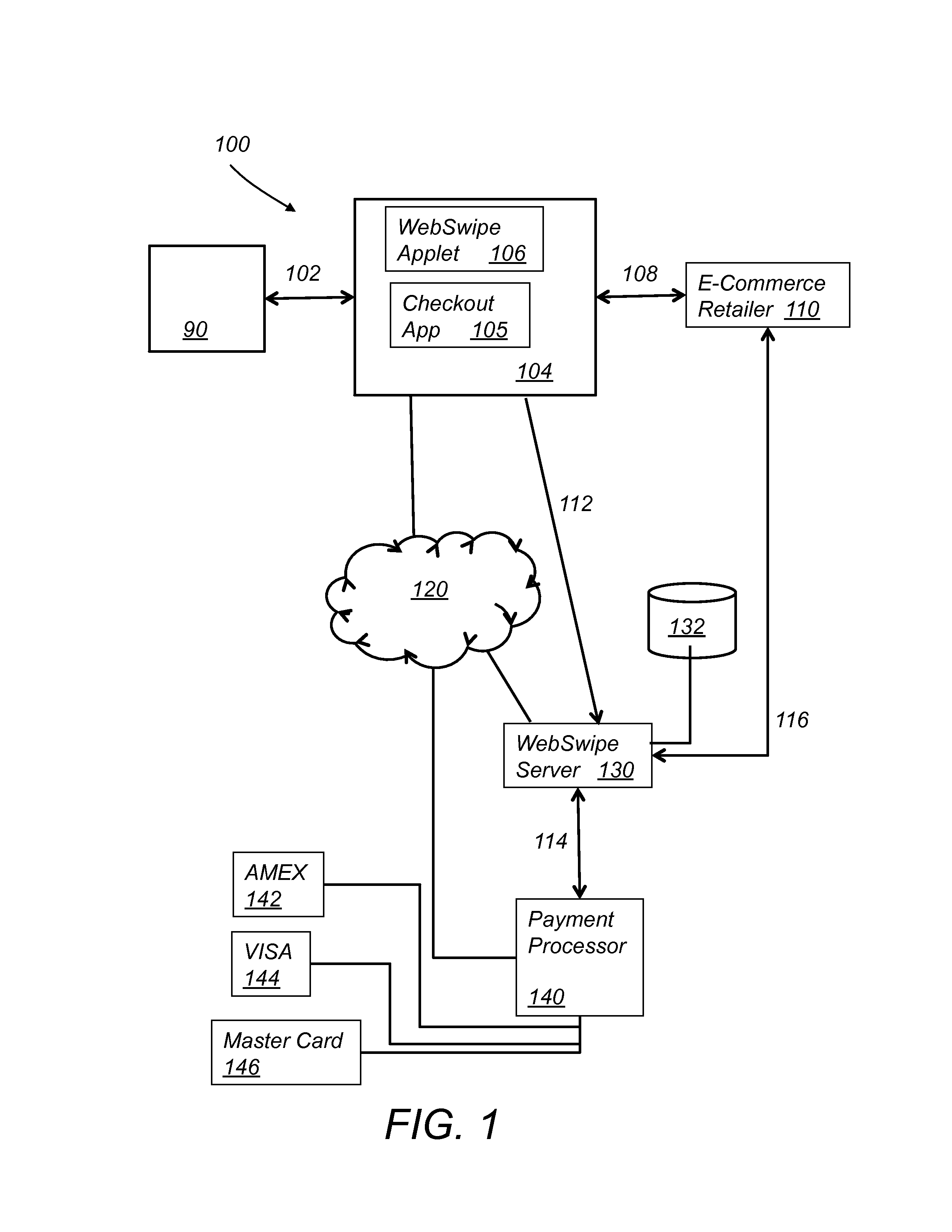
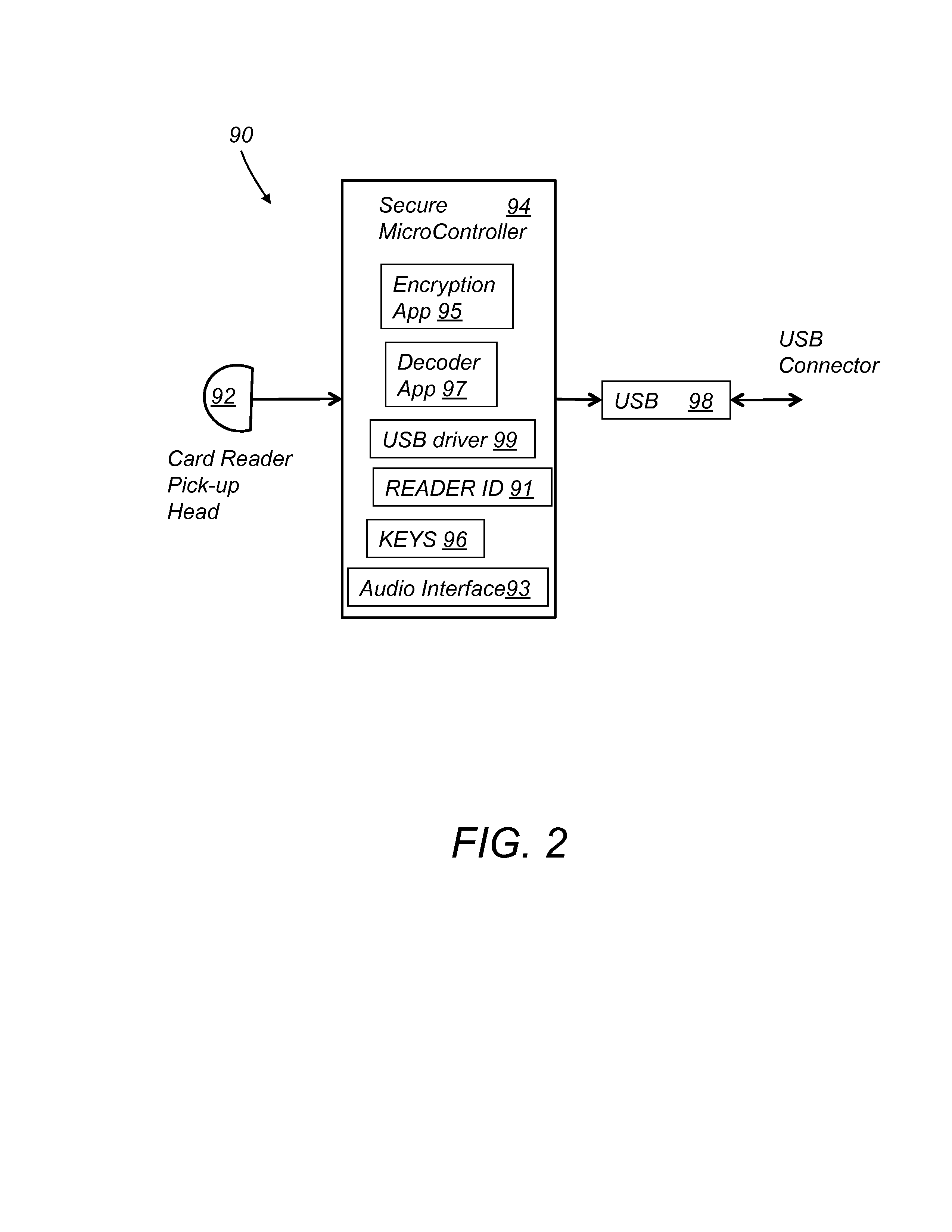
System and method for an authenticating and encrypting card reader
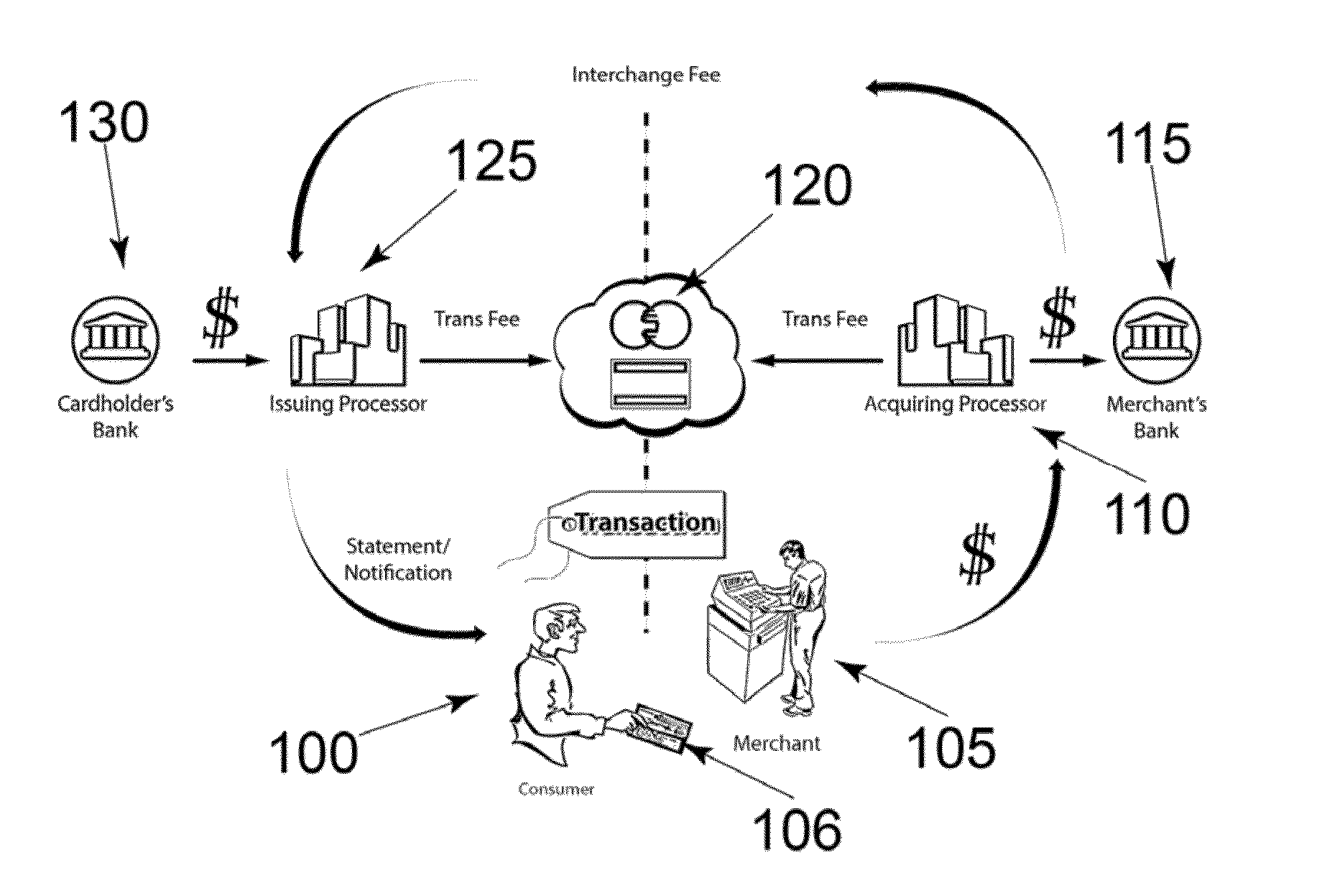
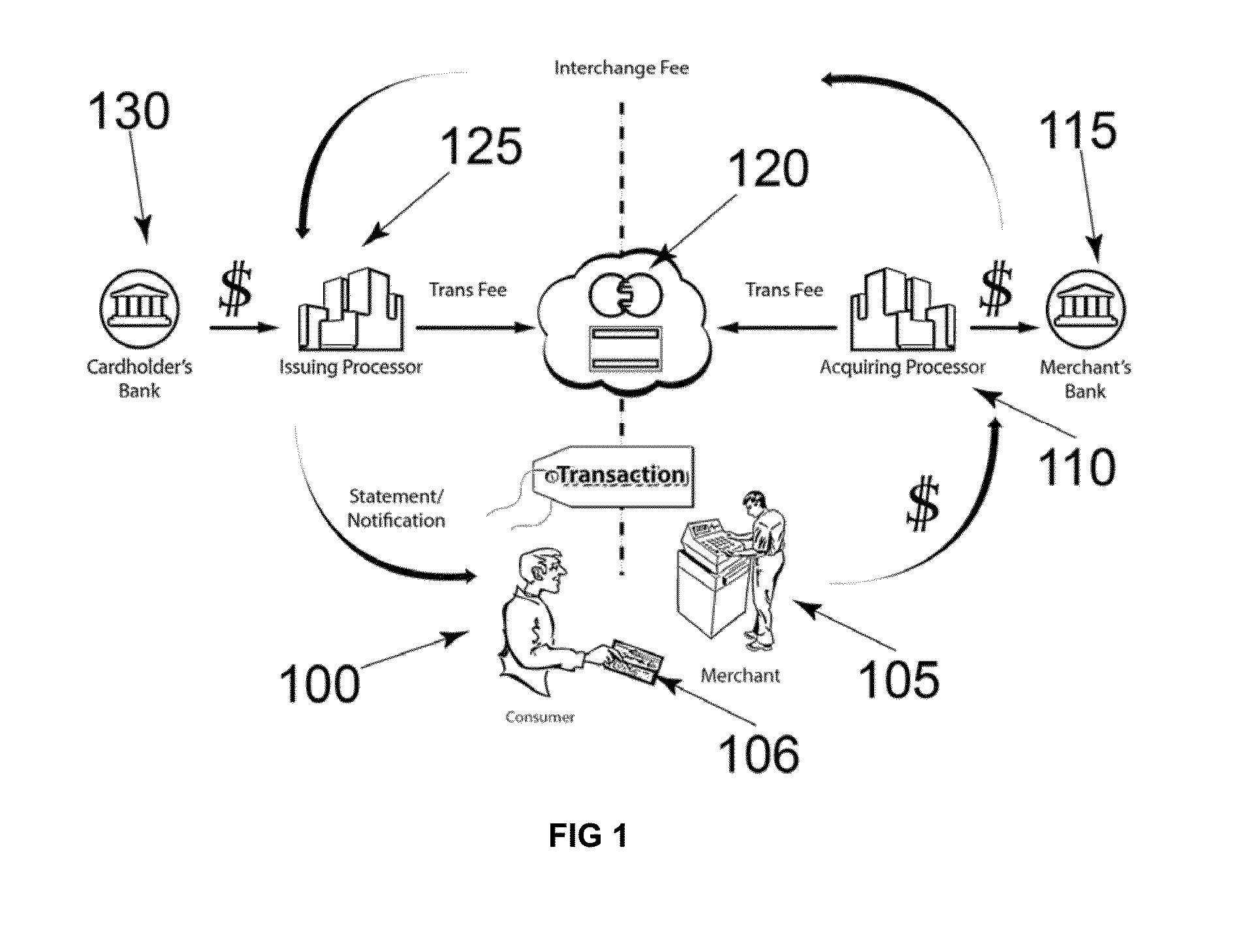
InactiveUS20130179351A1Easy checkoutLow InterchangeAcutation objectsPoint-of-sale network systemsMicrocontrollerPayment transaction
A system for encrypting and authenticating a payment transaction includes a card reader, a computing device, a card swipe application and a checkout application. The card reader includes a reader head, a secure microcontroller, and an interface. The reader head reads payment card data from a payment card. The secure microcontroller stores a unique reader identification (reader ID), and at least a first encryption key, and includes a payment card decoder application and an encryption application. The encryption application encrypts the payment card data and produces encrypted payment card data. The encryption application further encrypts the transaction data with the first encryption key and produces encrypted transaction data. The checkout application receives the encrypted payment card data and the encrypted transaction data and forwards them to a payment server for processing of the payment transaction.
Owner:WALLNER GEORGE
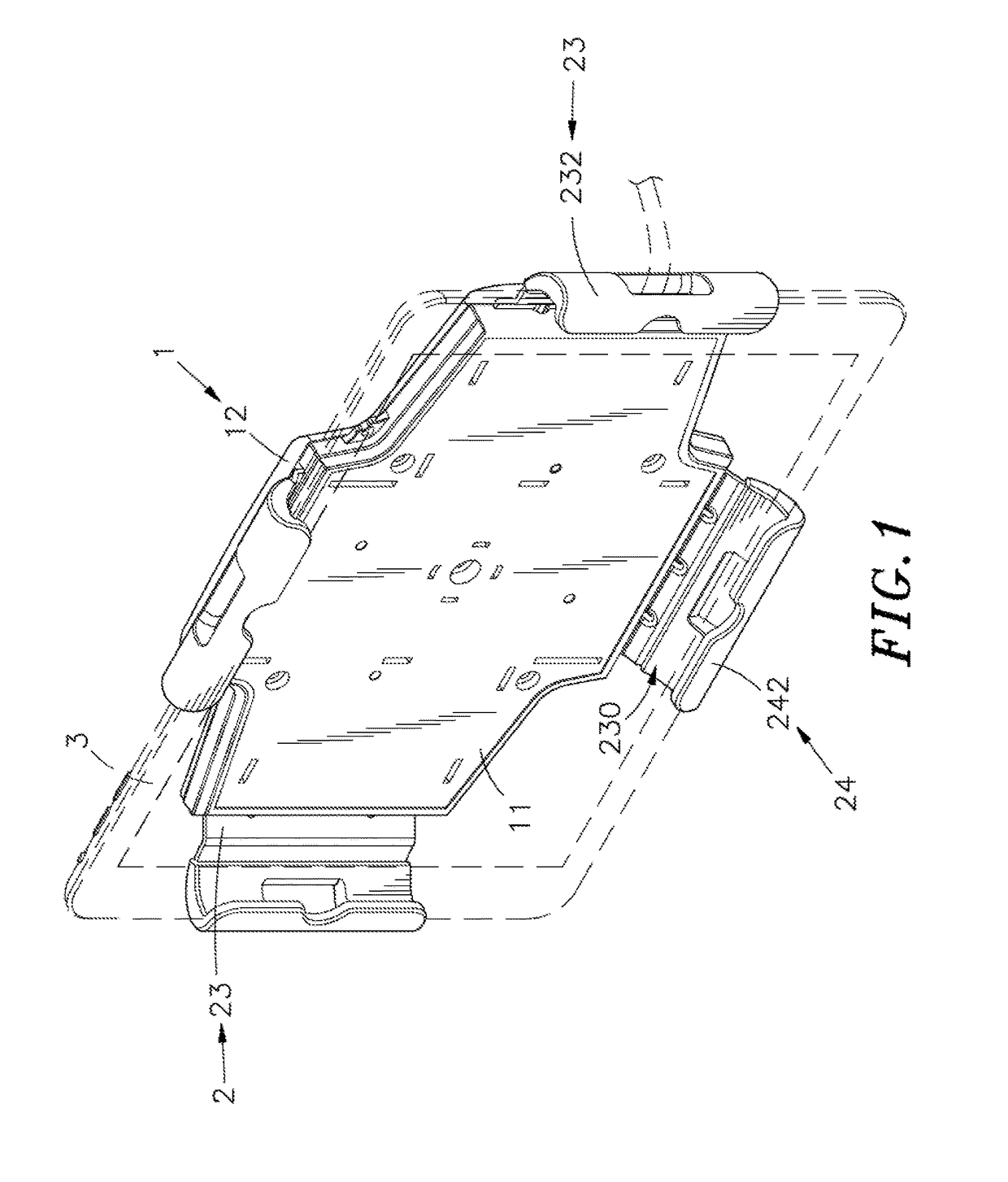
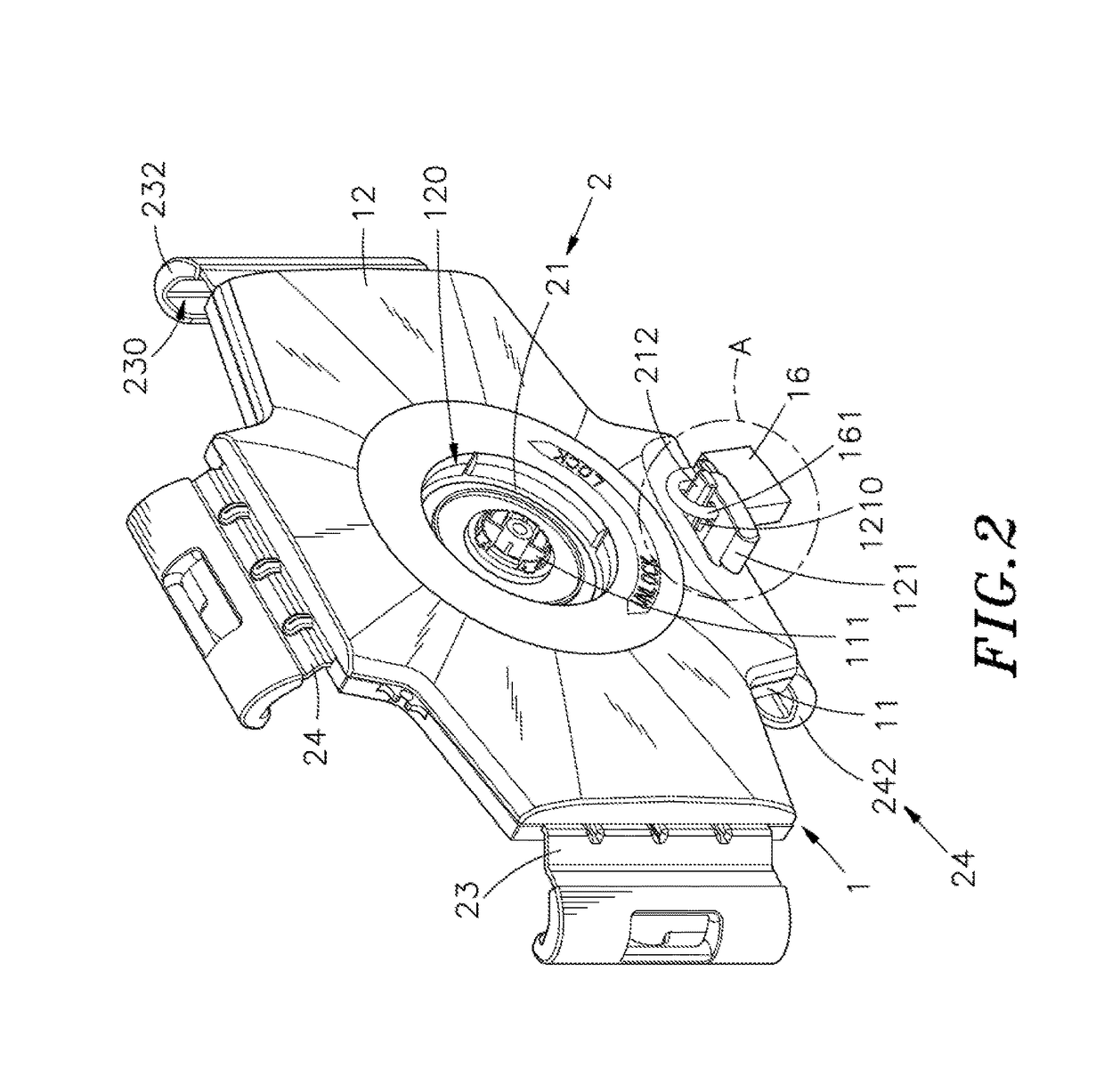
Electronic key for merchandise security device
InactiveUS20120047972A1Protection from theftElectric signal transmission systemsDigital data processing detailsElectricityElectric power transmission
An electronic key including an internal power source is provided for transferring electrical power to a merchandise security device to operate a mechanical lock mechanism. In one embodiment, the key transfers power to the device via electrical contacts disposed on a transfer probe of the electronic key and corresponding electrical contacts disposed within a transfer port of the device when the transfer probe engages the transfer port. In another embodiment, the key transfers power to the device via inductive transfer as a result of passing an electrical current through an inductive coil disposed within the transfer probe to generate a magnetic field in the vicinity of a corresponding inductive coil disposed within the transfer port and thereby induce an electric current in the inductive coil of the device. In other embodiments, the electronic key is programmed with a security code and the key initially programs the merchandise security device with the security code and subsequently determines whether the security code of the key matches the security code of the device to permit the key to transfer power to the device.
Owner:INVUE SECURITY PROD INC
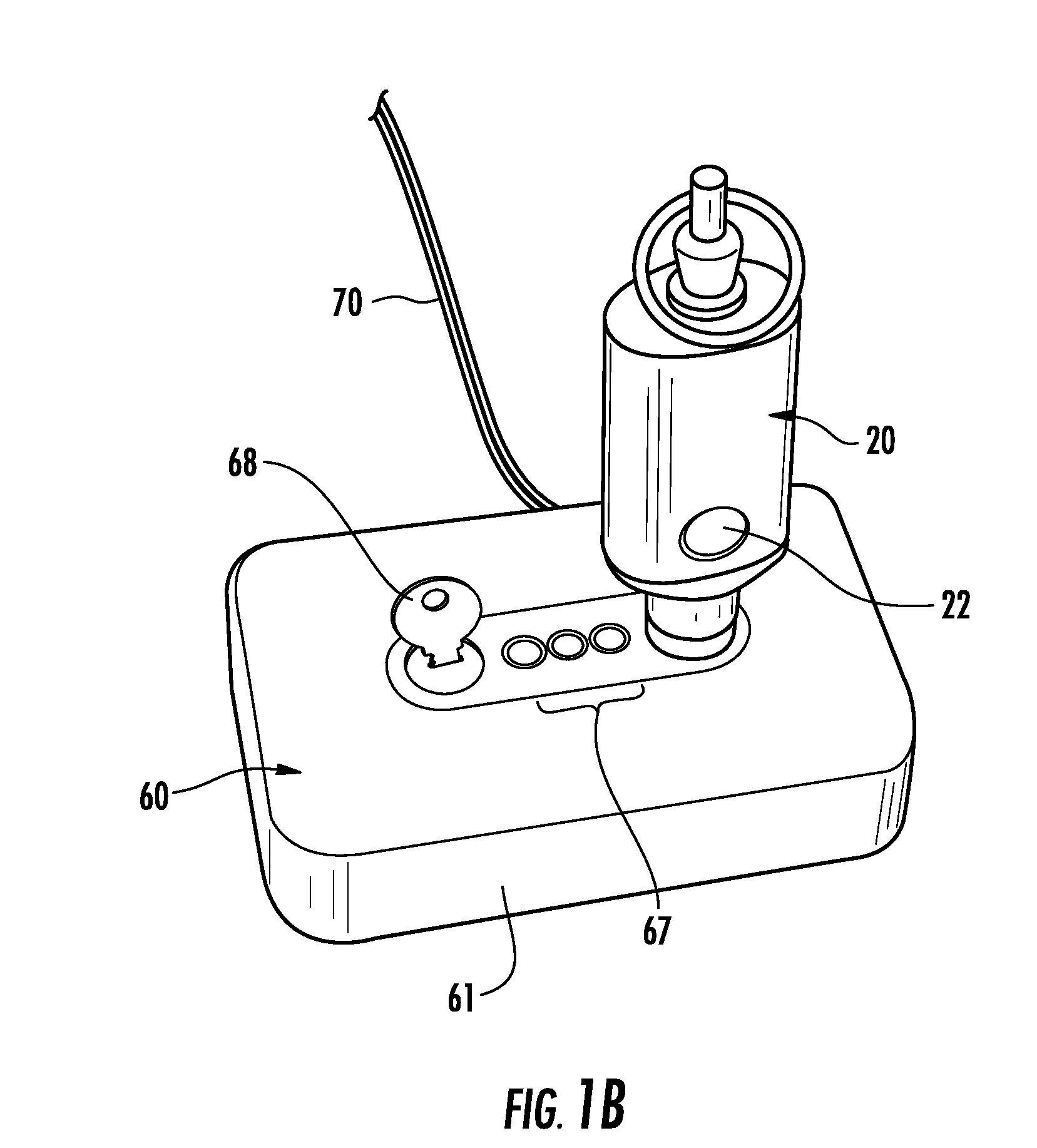
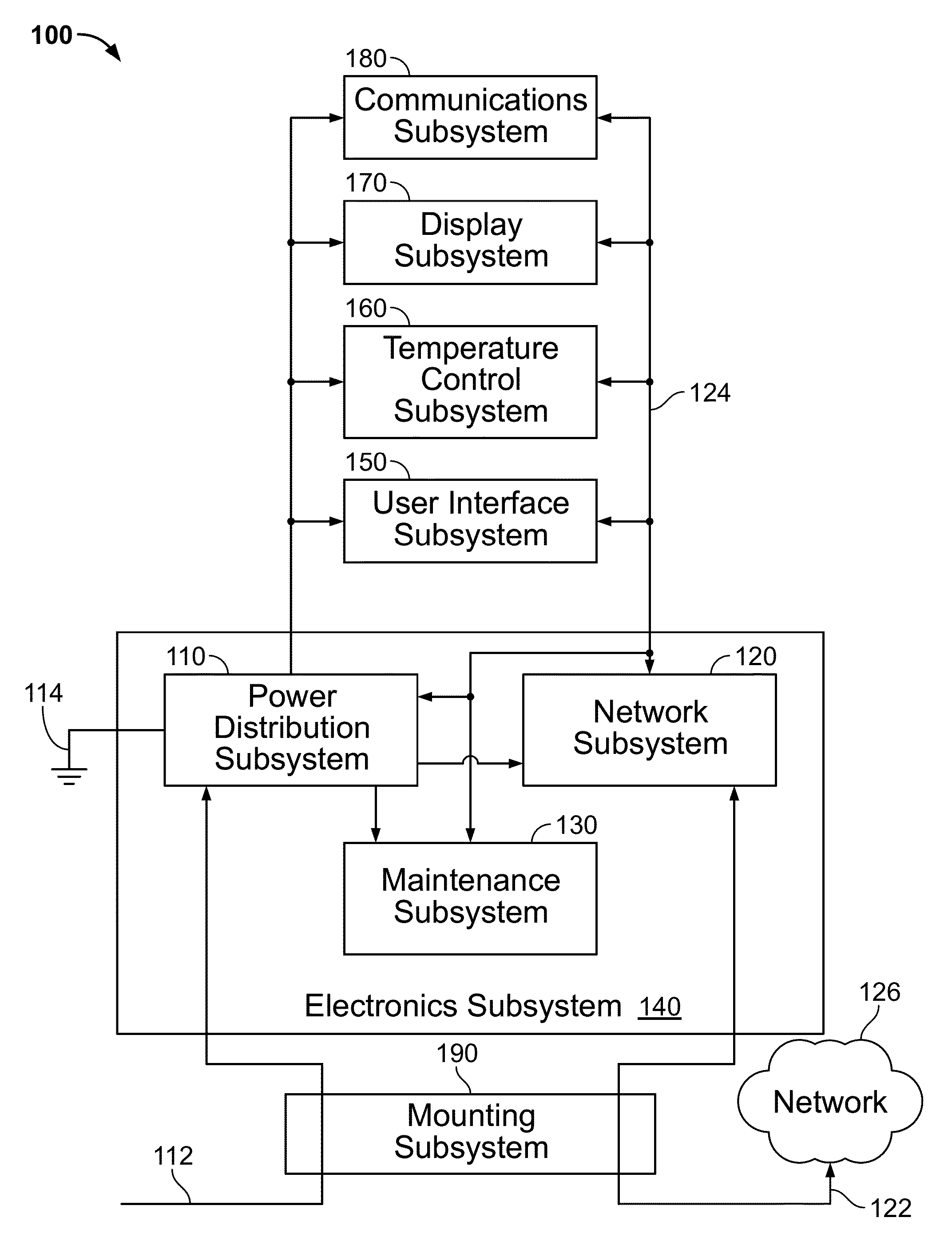
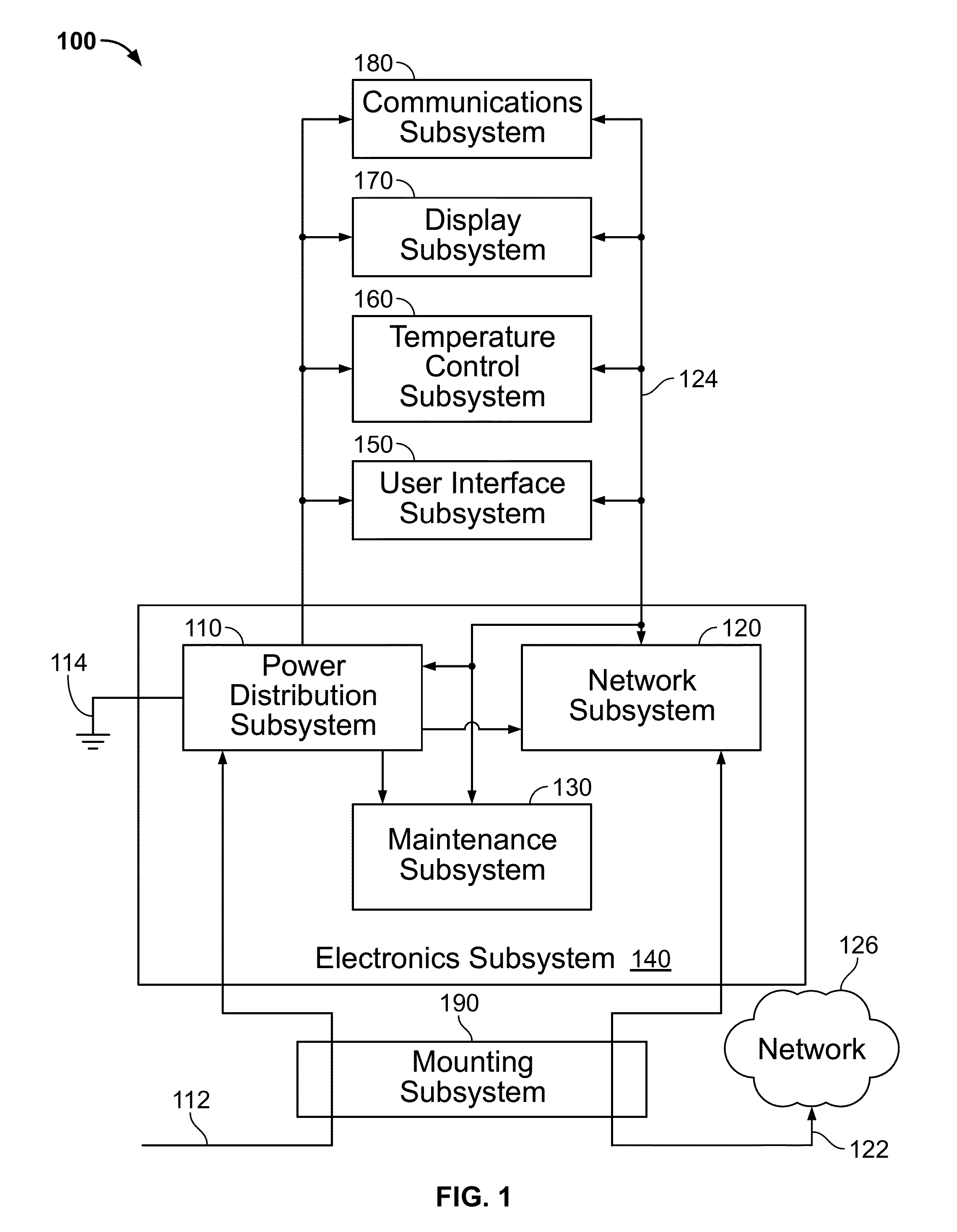
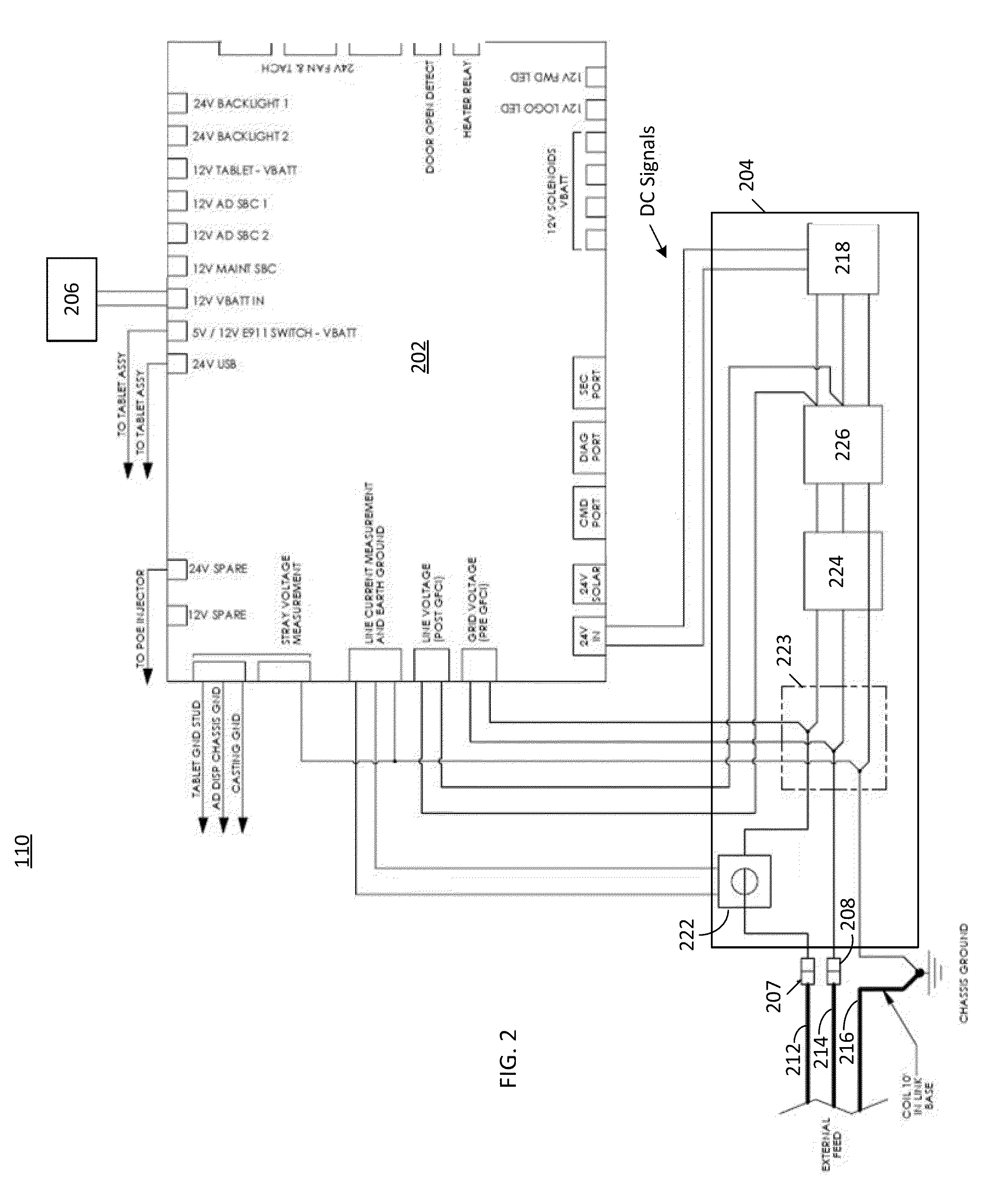
Techniques and apparatus for controlling access to components of a personal communication structure (PCS)
ActiveUS9451060B1Easy accessExpand accessSpecial buildingRestaurantsStructure of Management InformationEngineering
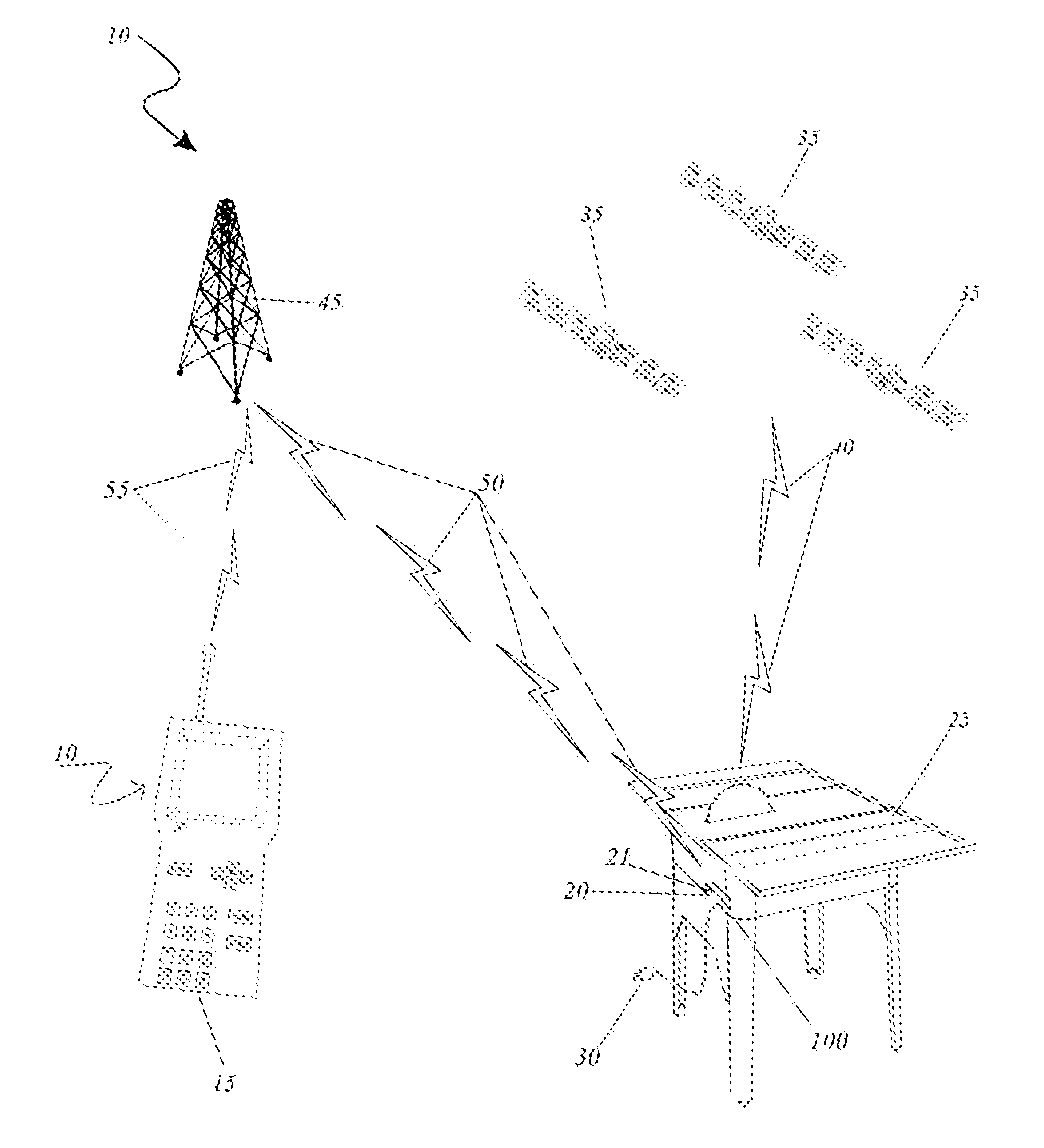
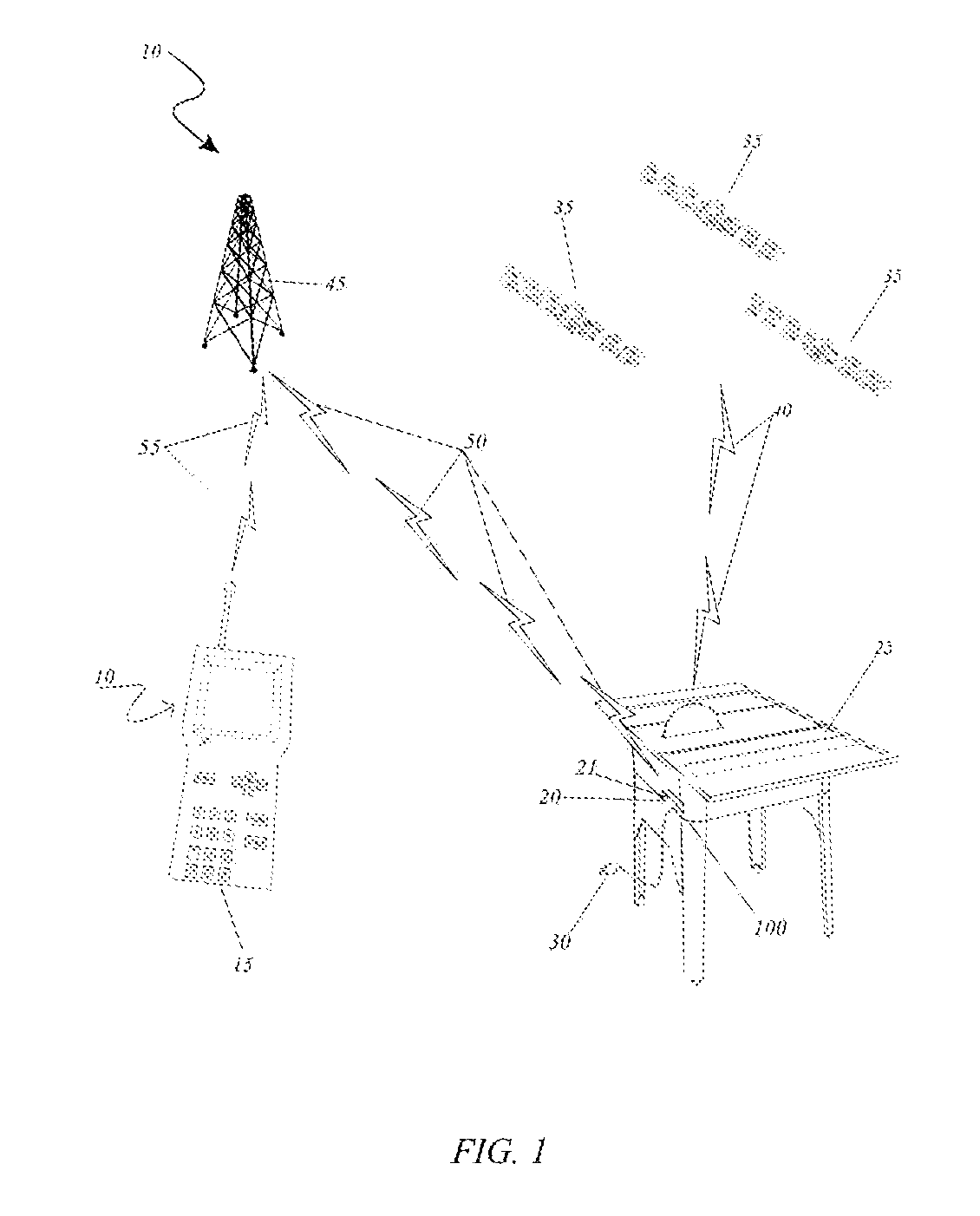
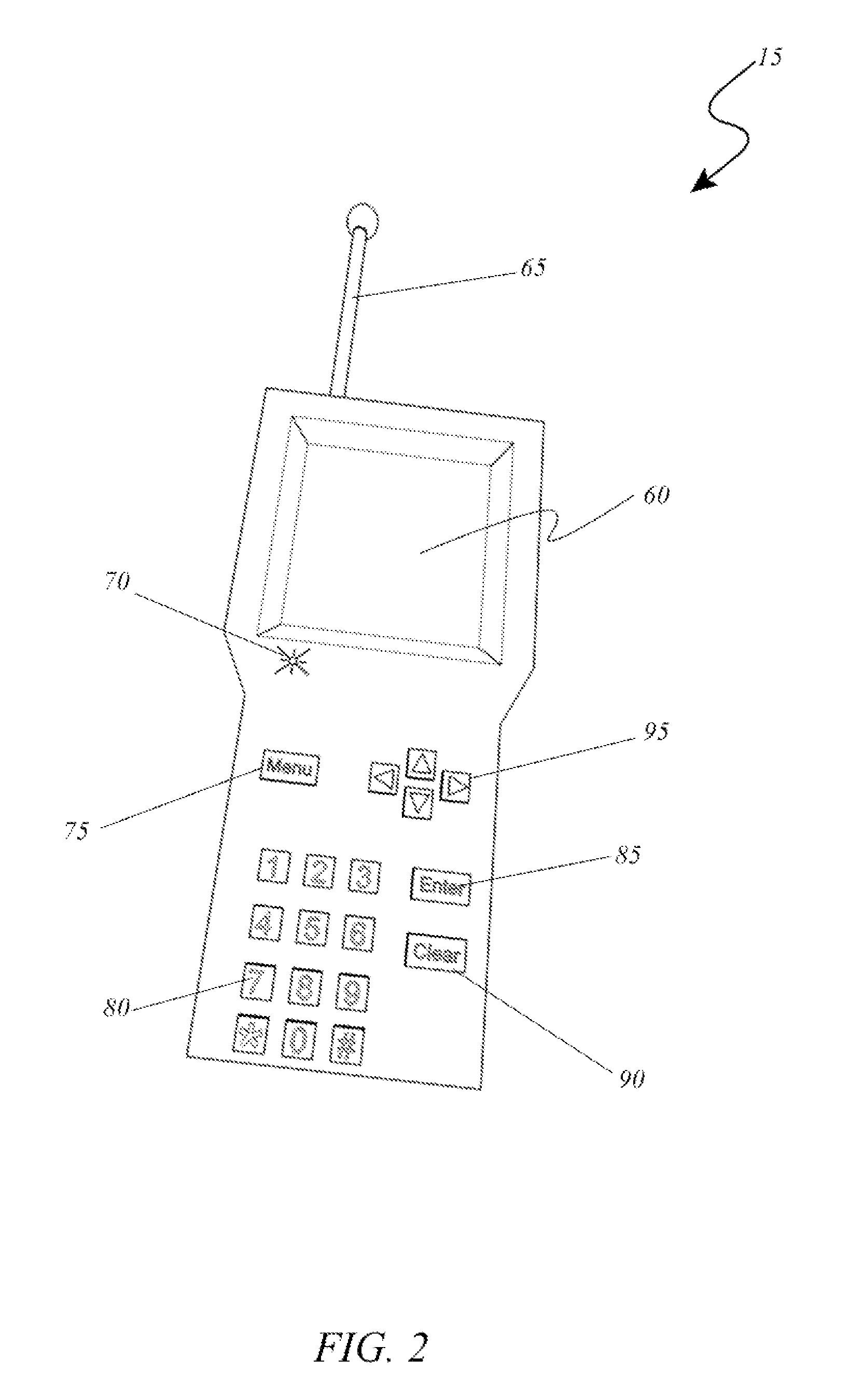
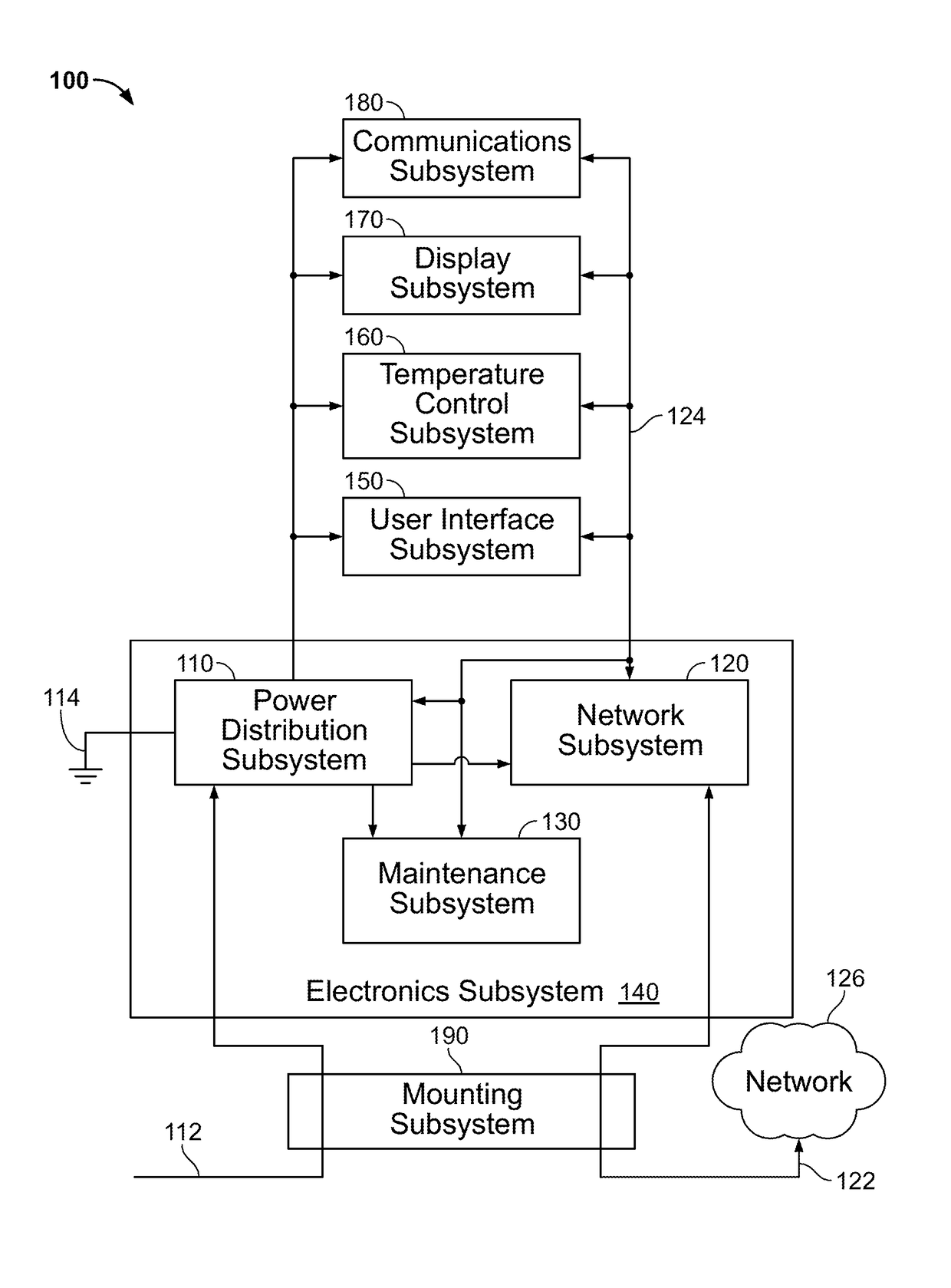
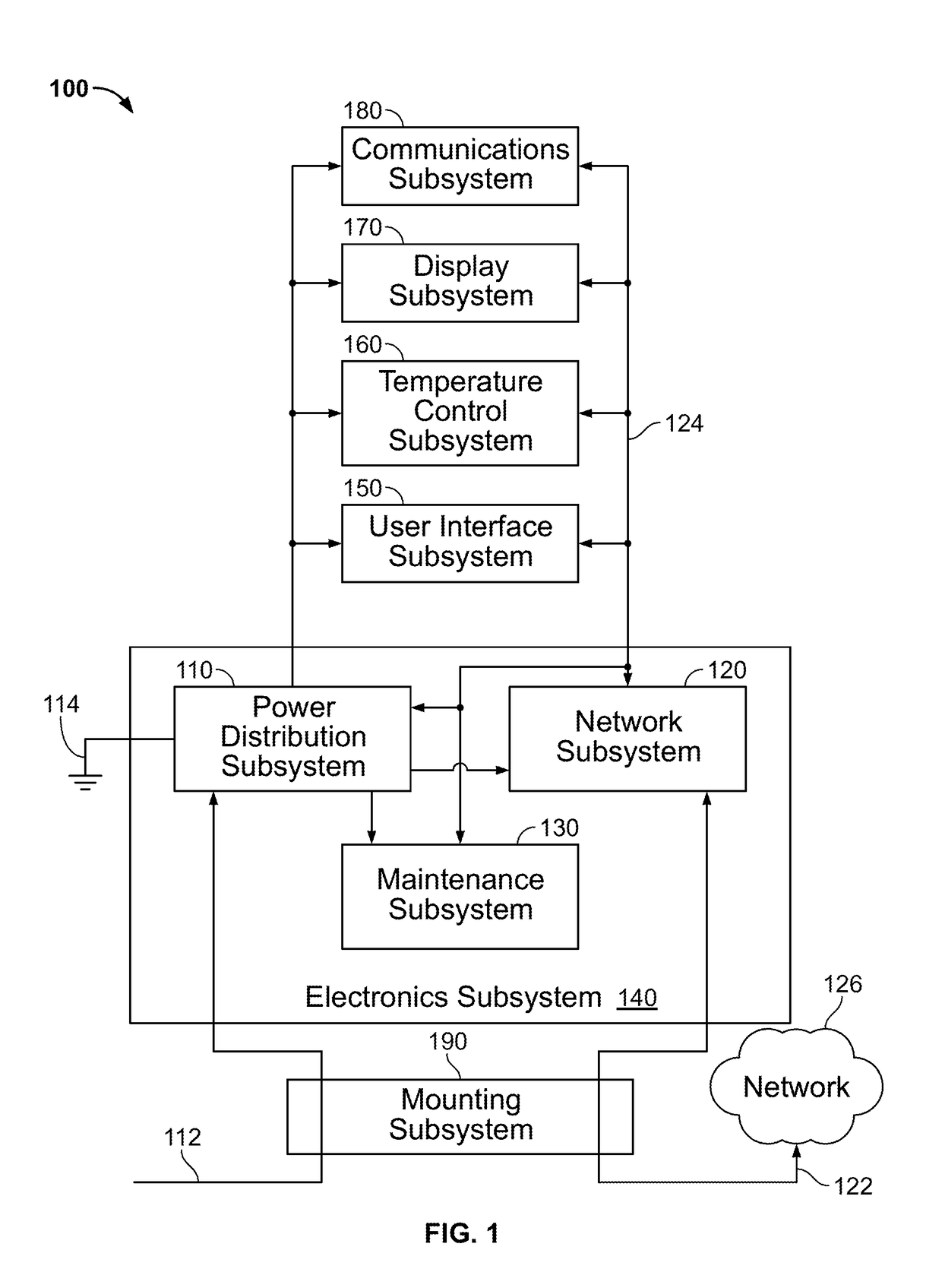
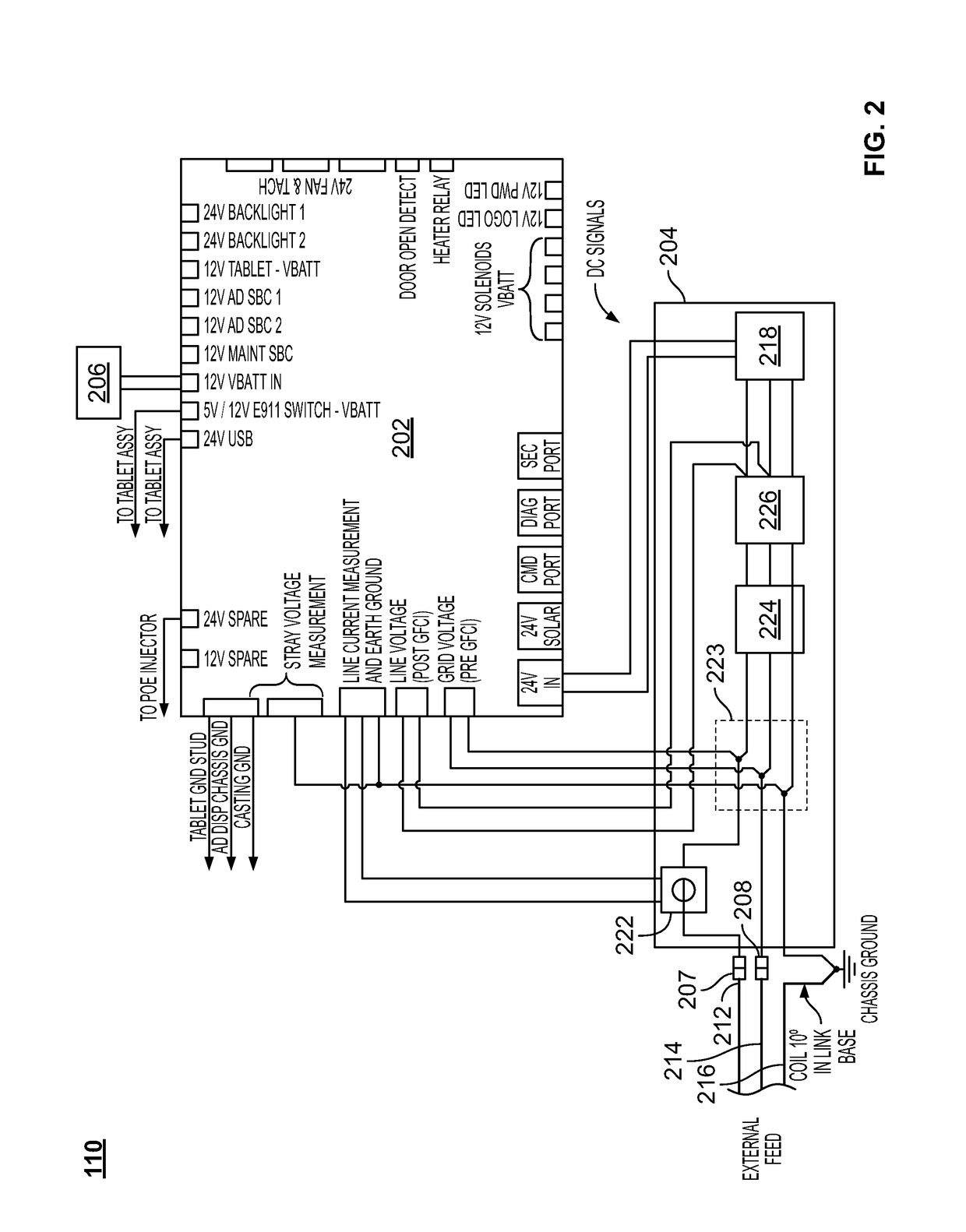
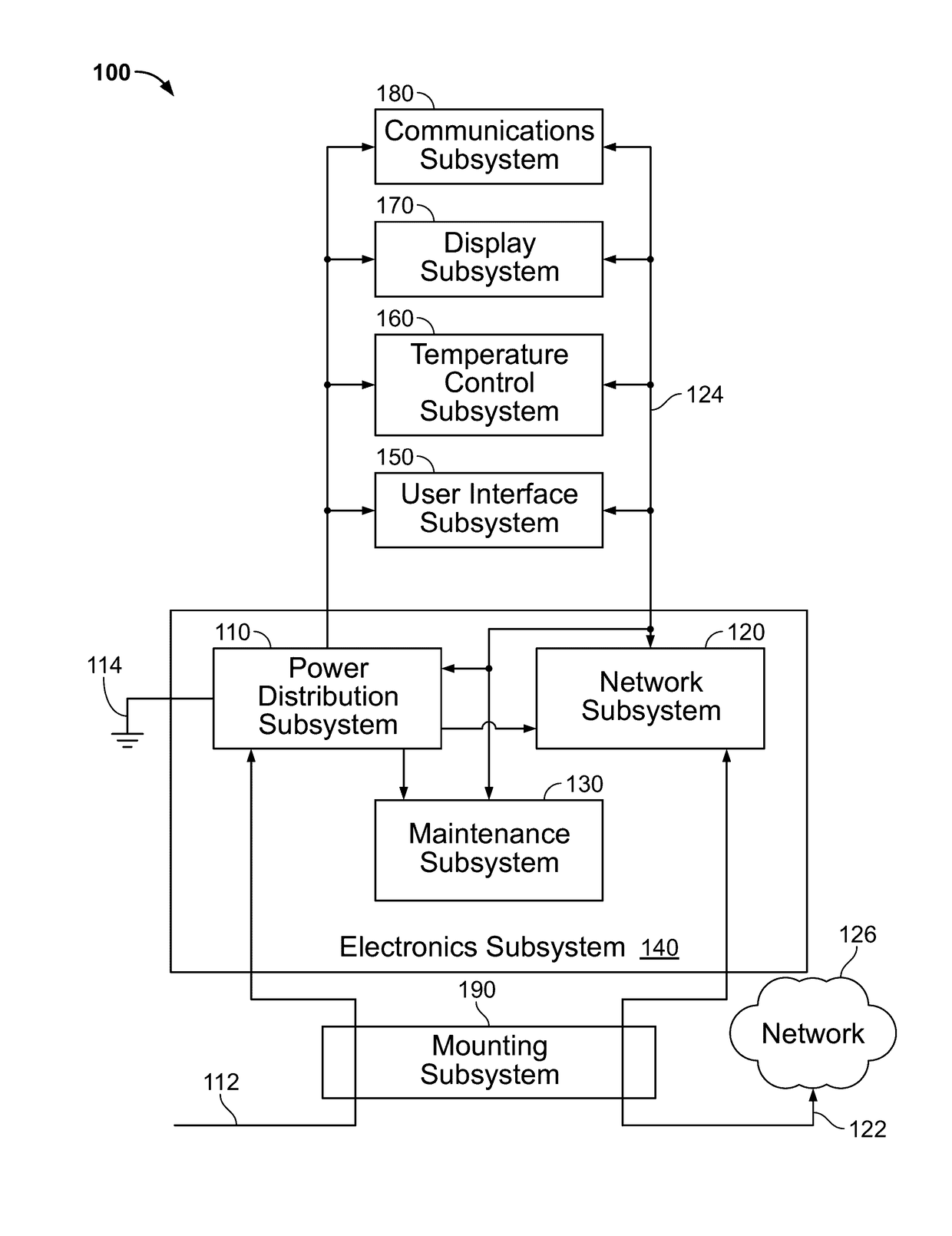
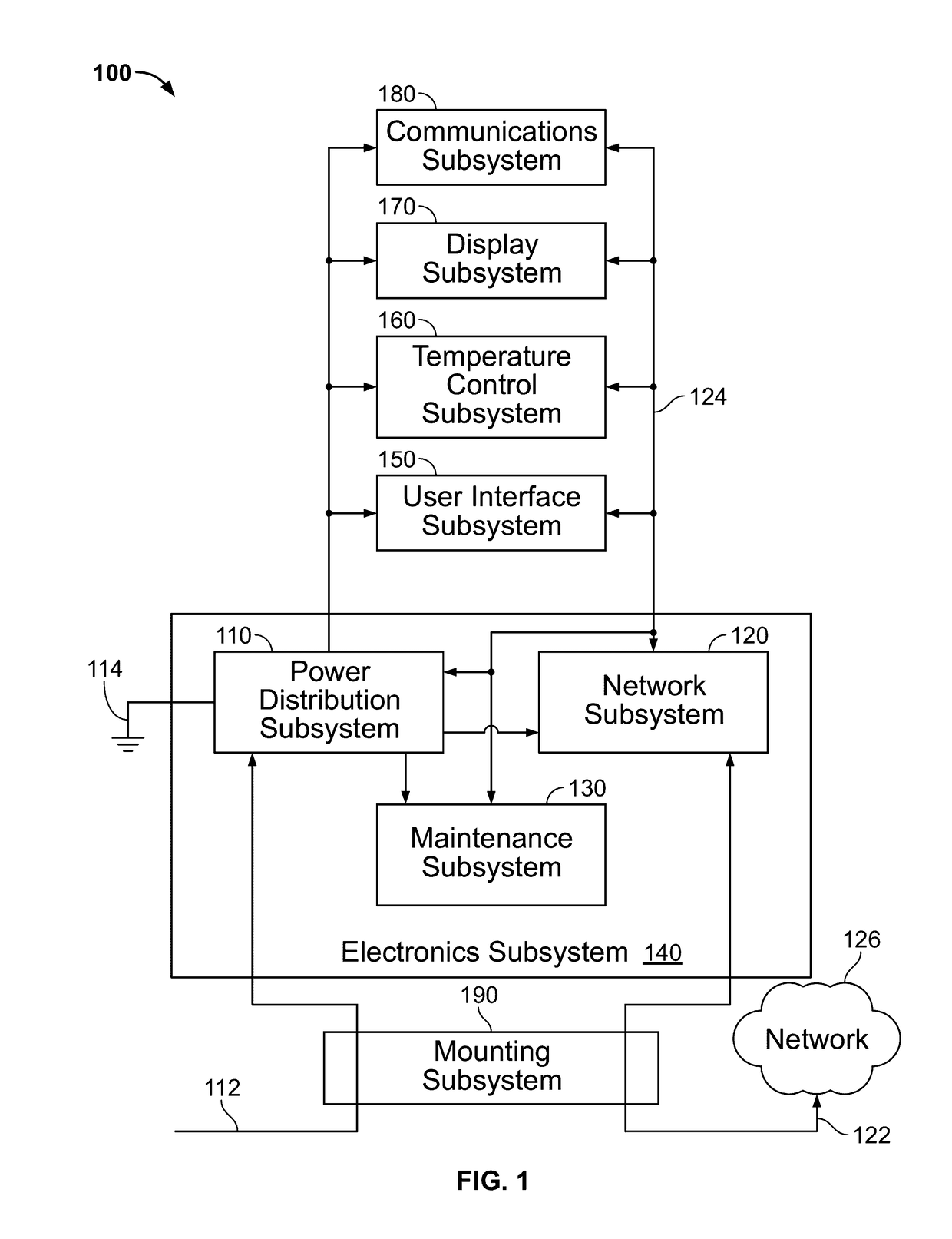
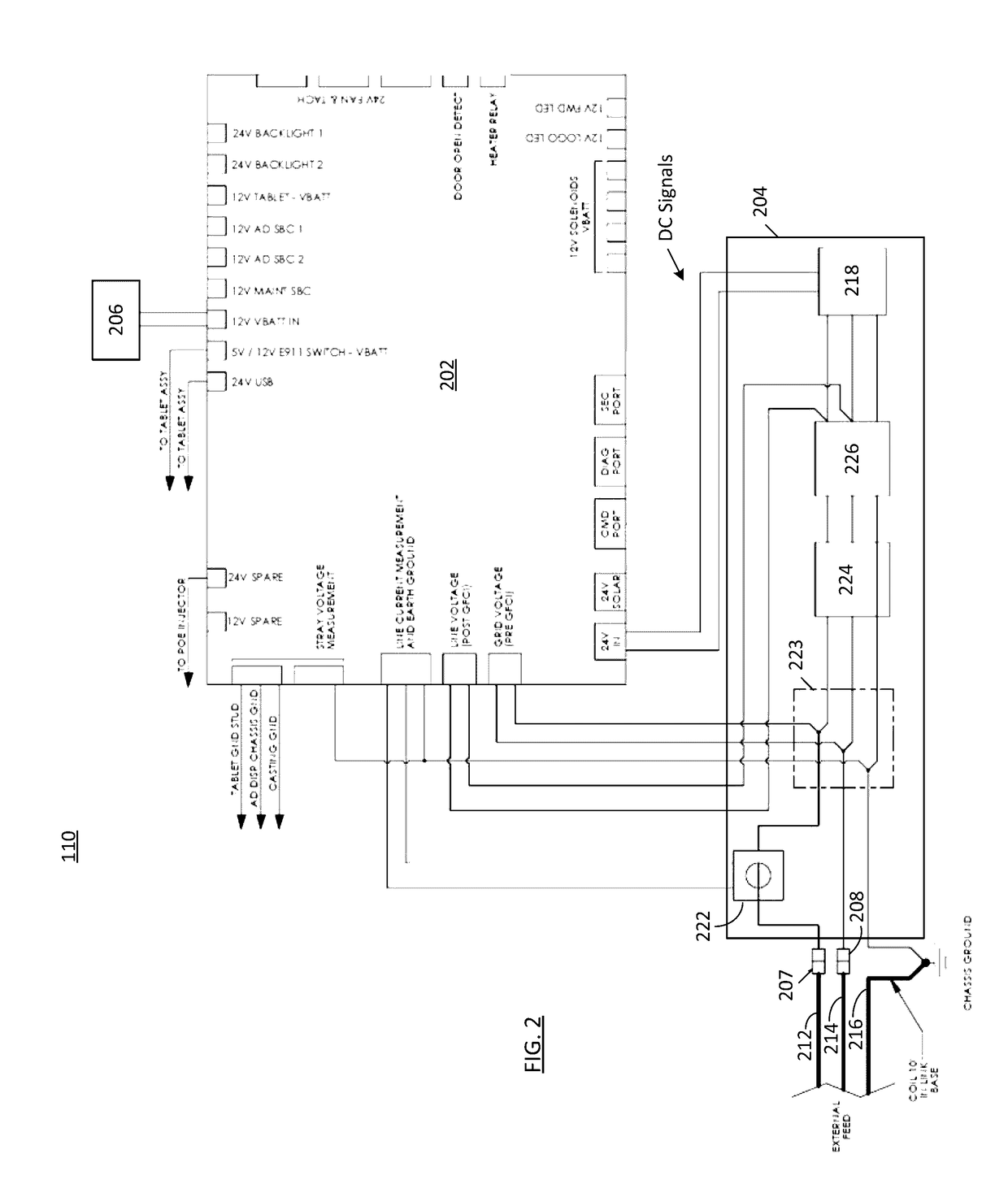
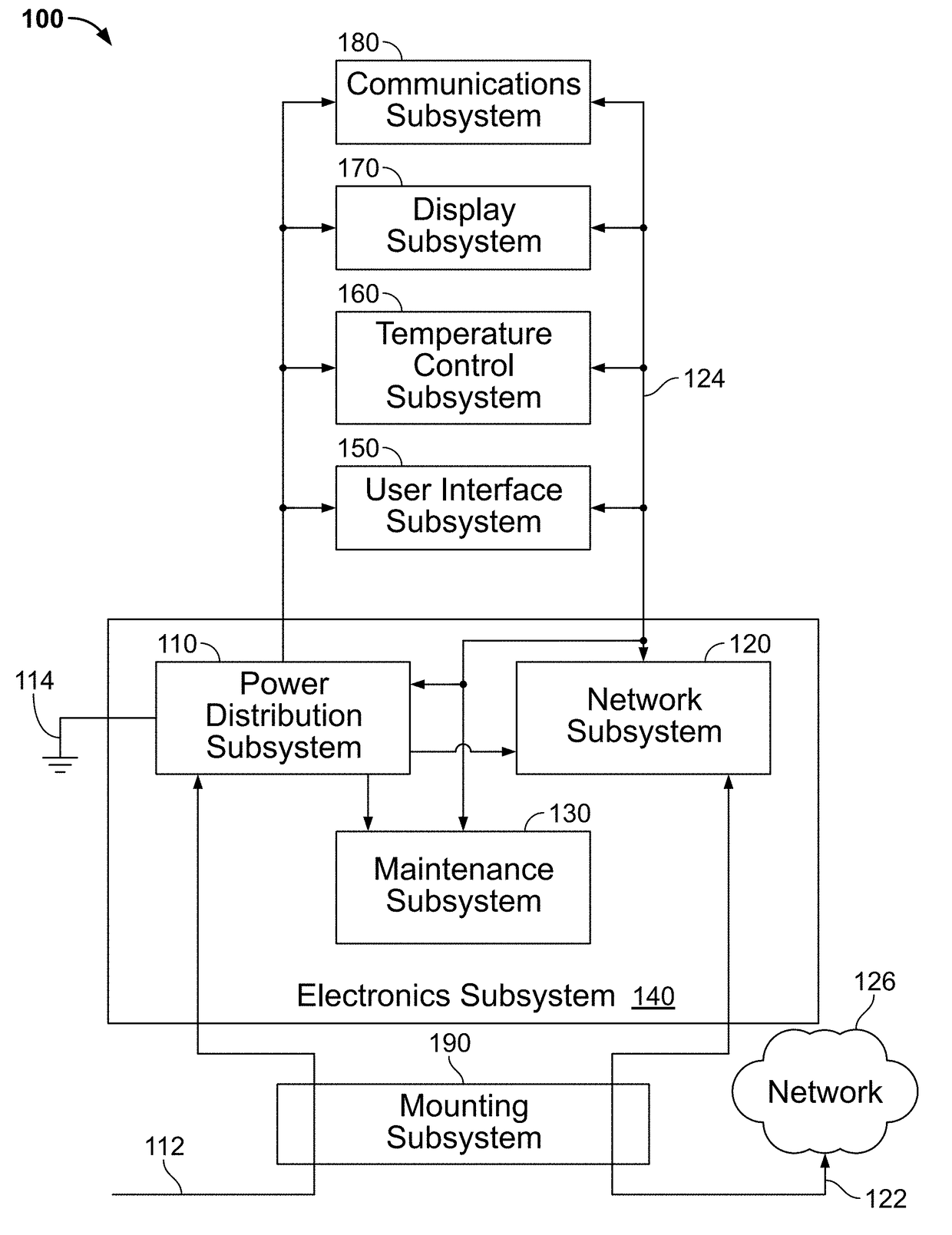
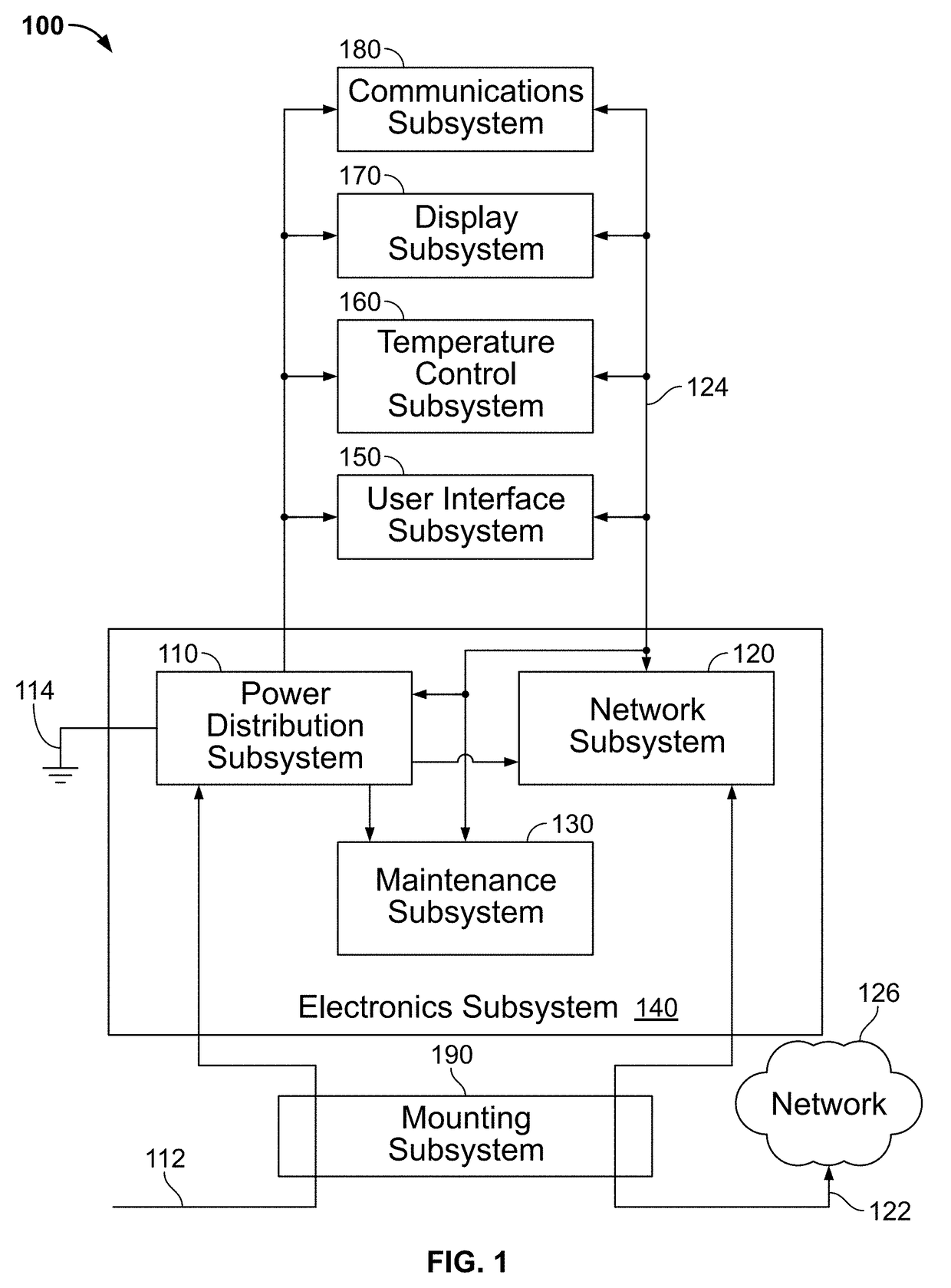
Techniques and apparatus for controlling access to a personal communication structure (PCS) are described. The PCS may include independently accessible compartments at least partially enclosing respective subsystems of the PCS. The independently accessible compartments include an electronics compartment, a communications compartment, and a display compartment. The electronics, communications, and display compartments at least partially enclose a power distribution subsystem, a communications subsystem, and a display subsystem, respectively. The PCS also includes an access controller operable to provide access independently to respective interiors of at least a subset of the compartments to authorized users.
Owner:CITYBRIDGE LLC
Electrical lock-out and locating apparatus with GPS technology
InactiveUS8044796B1Protection from theftAccurate and quick and effectivePosition fixationIndividual entry/exit registersEngineeringGlobal positioning system receiver
A system and method by which construction tools, electronics, and other electrically powered devices are protected from theft and unauthorized use is disclosed. A tool or electronic device is equipped with an electronic receiver that receives an authorization code from a remote transmitter. Should the item be stolen, the rightful owner can disable it remotely, rendering it worthless. Additionally, the system provides for a Global Positioning System Receiver (GPS) that allows the invention to determine its physical location to within a few feet anywhere on the face of the earth, and transmit its location to the original owner such that it may be recovered. The use of the present invention allows for increased security of portable tools and electronics in a manner that is quick, easy and effective.
Owner:CARR SR SYD K
Techniques and apparatus for controlling access to components of a personal communication structure (PCS)
ActiveUS20170111486A1Easy accessExpand accessSpecial buildingRestaurantsElectronic systemsEngineering
Techniques and apparatus for controlling access to a personal communication structure (PCS) are described. The PCS may include independently accessible compartments at least partially enclosing respective subsystems of the PCS. The independently accessible compartments include an electronics compartment, a communications compartment, and a display compartment. The electronics, communications, and display compartments at least partially enclose a power distribution subsystem, a communications subsystem, and a display subsystem, respectively. The PCS also includes an access controller operable to provide access independently to respective interiors of at least a subset of the compartments to authorized users.
Owner:CITYBRIDGE LLC
Protecting information using policies and encryption
ActiveUS8843734B2Ensure confidentialityAvoid data lossUnauthorized memory use protectionHardware monitoringConfidentialityDocumentation
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS INC
Method for optically decoding a debit or credit card
InactiveUS20130202185A1Eliminate logistical needReduce confusionAcutation objectsCharacter and pattern recognitionCredit cardComputer hardware
A method for collecting and transmitting information desired for a commercial transaction from a debit or credit card uses a processor configured with optical character recognition (OCR) capability. At least one optical image of the debit or credit card is collected by the processor. The edges of the card are algorithmically defined from the collected image. Predefined offsets are applied to the algorithmically defined edges of the debit or credit card to algorithmically locate an area in the collected image having the desired transactional data. The transactional data within the located area is encoded and transmitted for further processing of the commercial transaction.
Owner:SCI GAMES INT
Techniques and apparatus for controlling access to components of a personal communication structure (PCS)
InactiveUS20170111521A1Enhance public accessImprove network coverageDigital data processing detailsNetwork topologiesElectronic systemsEngineering
Techniques and apparatus for controlling access to a personal communication structure (PCS) are described. The PCS may include independently accessible compartments at least partially enclosing respective subsystems of the PCS. The independently accessible compartments may include an electronics compartment, a communications compartment, and a display compartment. The electronics compartment may be disposed along a lower portion of the PCS, and may at least partially enclose a power distribution subsystem. The communications compartment may be located proximate a top of the PCS, and may at least partially enclose a communications subsystem. The display compartment may be disposed along an upper portion of the PCS, and may at least partially enclose a display subsystem. Access to the interior of a compartment may be provided to authorized users without providing access to interiors of other independently accessible compartments.
Owner:CIVIQ SMARTSCAPES LLC
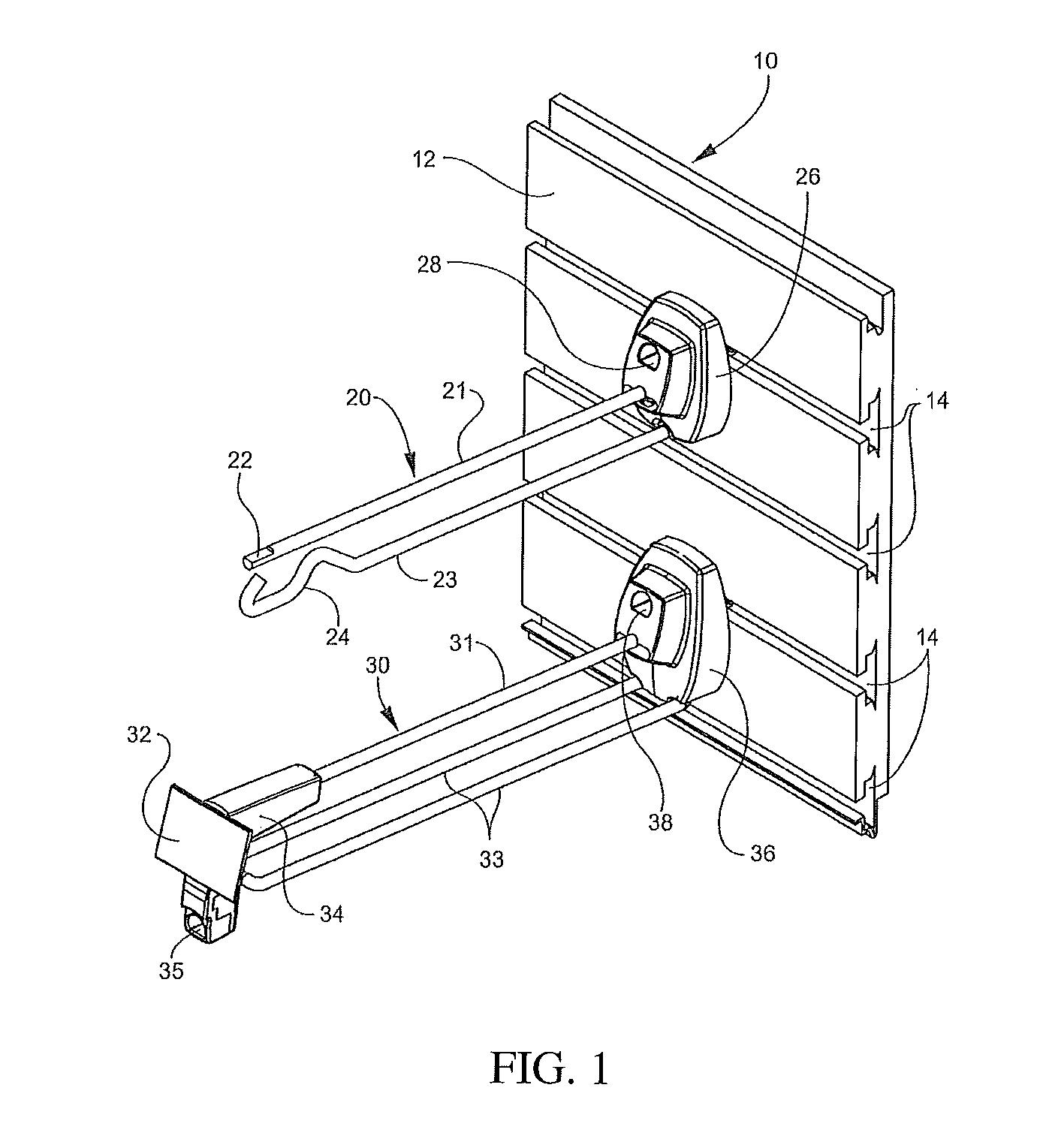
Merchandise display hook with alarm
Display hooks for displaying items of merchandise are provided. For example, the display hook includes at least one rod for supporting a plurality of items of merchandise and an end assembly coupled to the at least one rod. The end assembly includes an alarm mechanism configured to generate at least one alarming signal. The end assembly is configured to detect removal of each item of merchandise, wherein the alarm mechanism does not generate an alarming signal when at least a first item of merchandise is removed from the rod, and wherein the alarm mechanism is further configured to generate an alarming signal when a second item of merchandise has been removed from the rod within a predetermined period of time from the first item of merchandise being removed.
Owner:INVUE SECURITY PROD INC
Information entry system
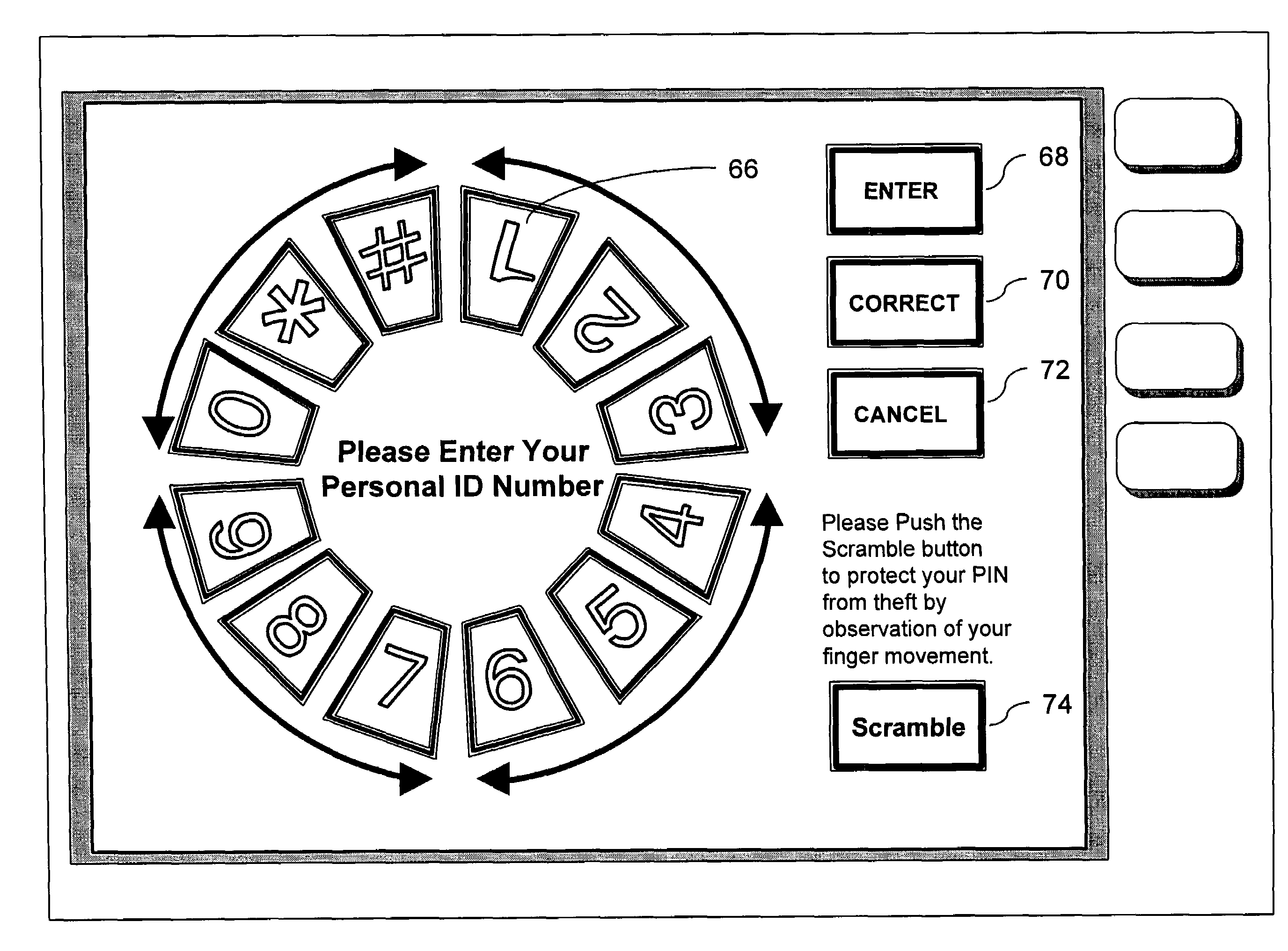
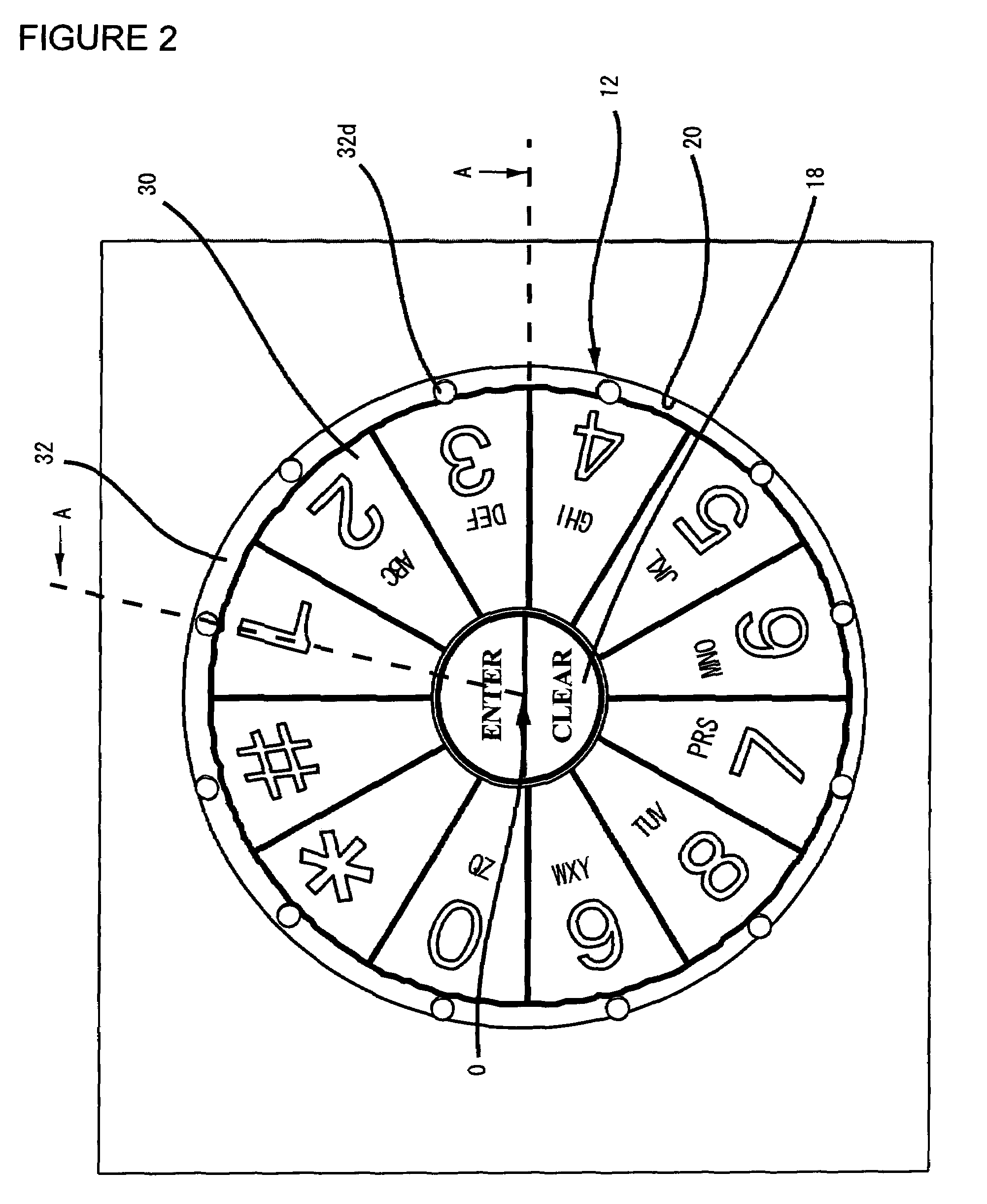
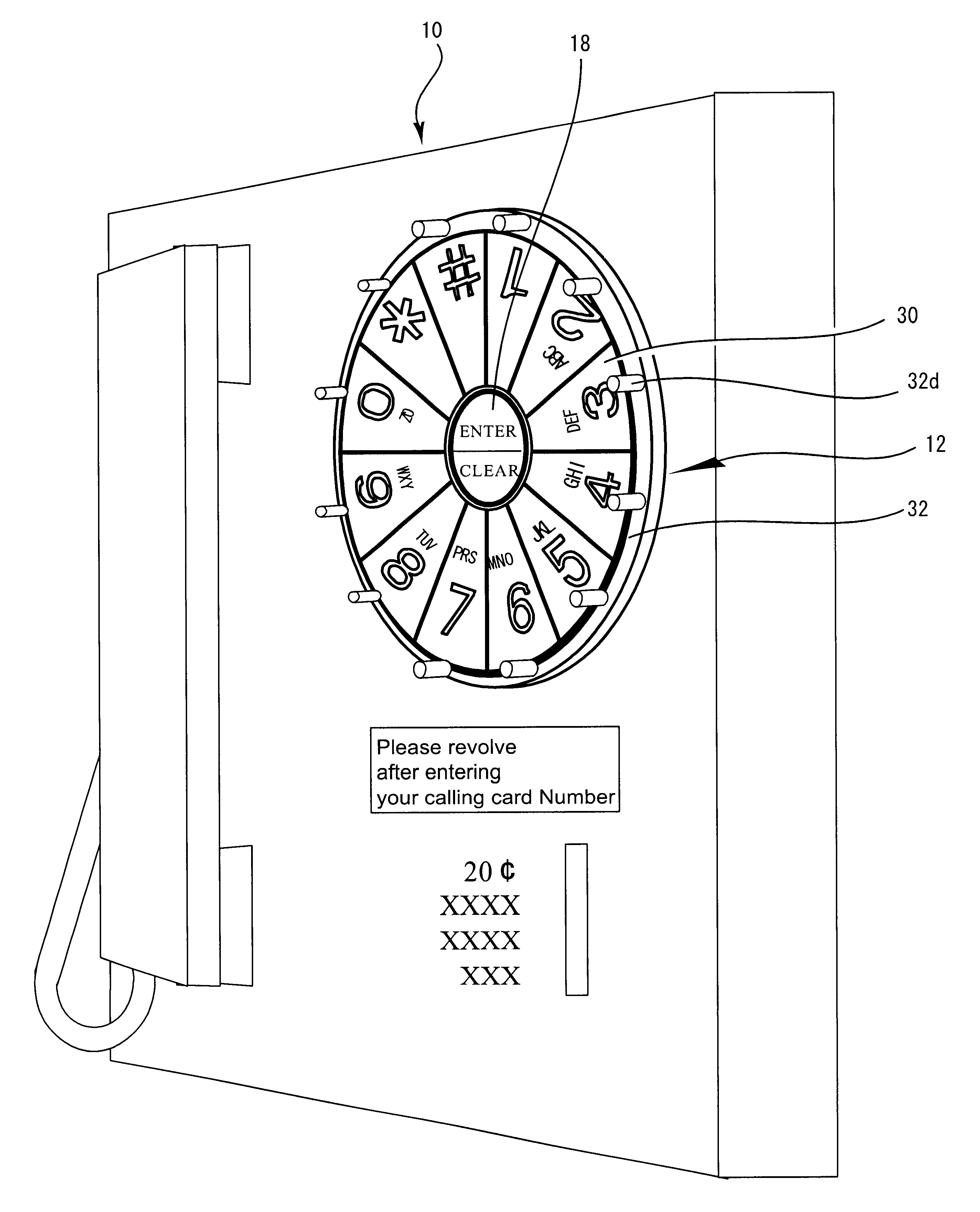
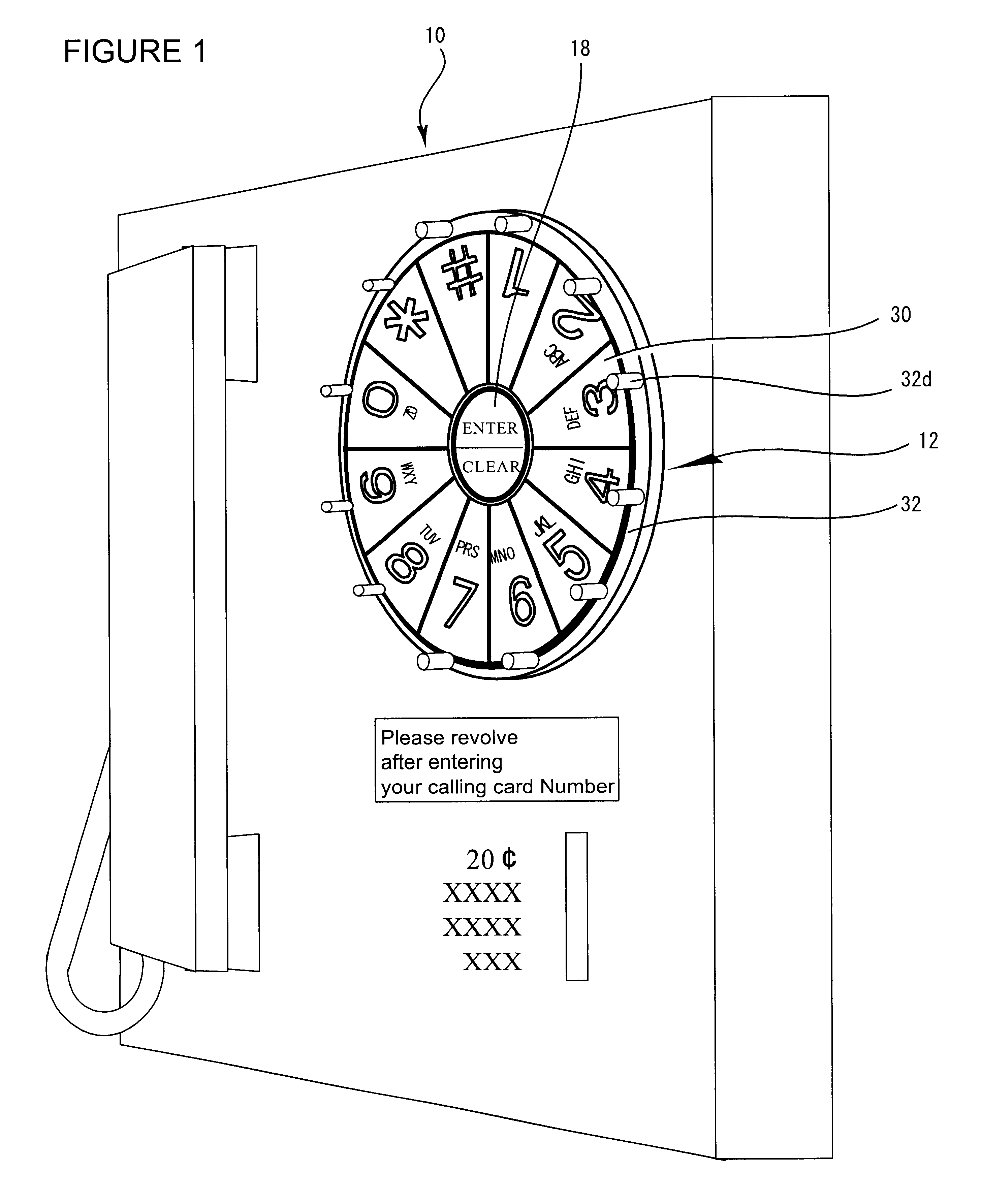
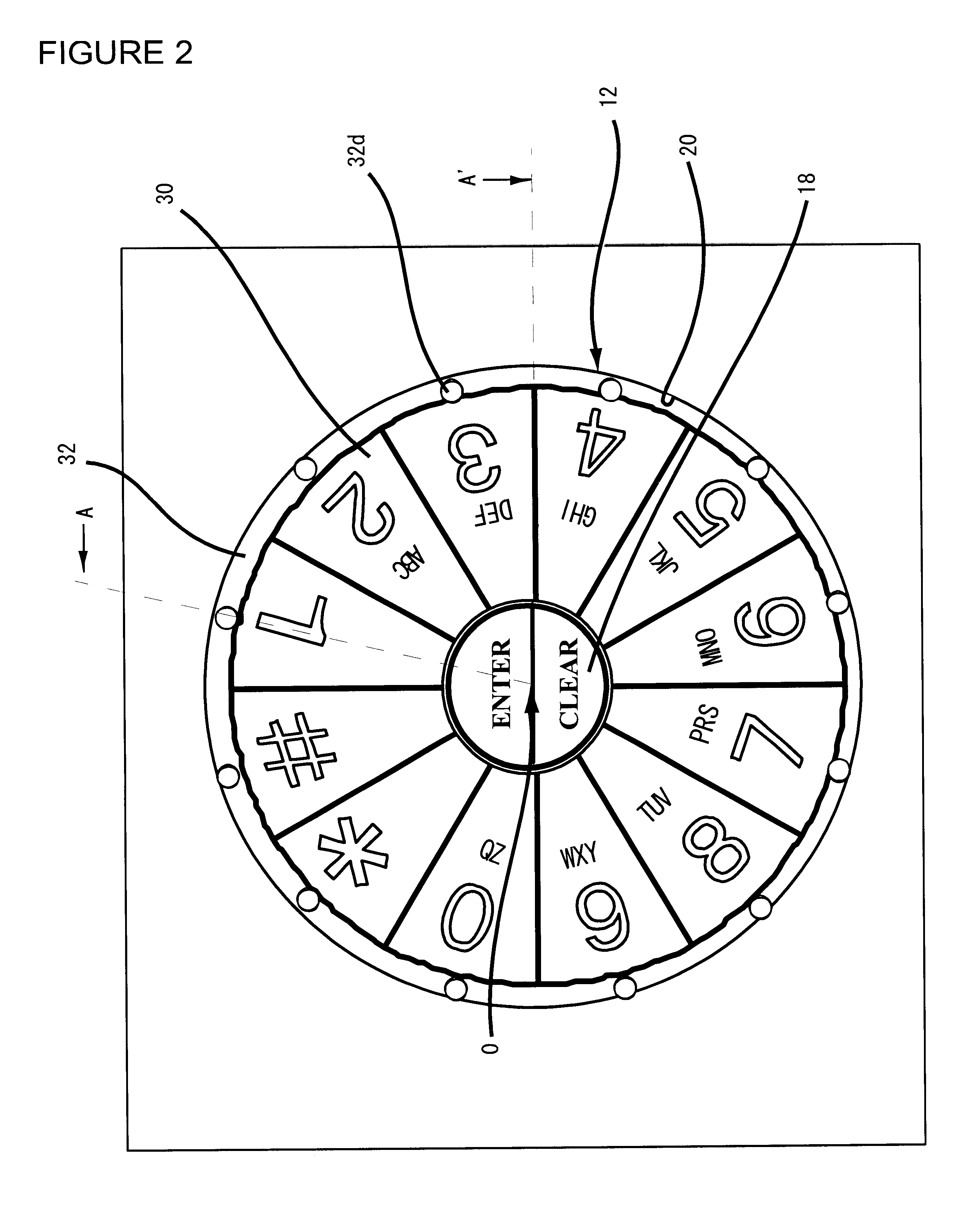
InactiveUS7333602B2Easy to pushProtection from theftComplete banking machinesInput/output for user-computer interactionFinger movementNumber generator
The present invention is an information entry system comprising a touch panel monitor screen, wherein the touch panel monitor screen displays keys for information entry, which are arranged circularly in order and the keys are rotationally shifted by a random number of key units around the center of the circular arrangement without changing the order when a user touches a predetermined option key before or after the information entry. This system also has a central processing unit and a program storage unit including an Information entry Screen Generator, a Random Number Generator, a Key Moving Unit, and a PIN Information output unit. This information entry device prevents a PIN or any other information entry from being stolen by someone who glances at the finger movement, since the entire series of the entry keys are rotated before or after the PIN entry.
Owner:HABU TOMOHIRO
Logistics Methods for Portable, Mobile Processing of Lottery and Contest Tickets
ActiveUS20130204777A1Eliminate logistical needReduce clutterAcutation objectsFinanceBarcodeLogistics management
A method for portable lottery ticket sales and redemptions by mobile vendors is provided wherein the vendor have an existing credit or debit card processing interchange. The vendor is provided with a portable local processor having a memory, and with a local printer connected to the local processor. The local processor is in wireless communication with a network. A bank identification number (BIN) is assigned to lottery tickets sold or redeemed by the vendor that is unique to lottery tickets in the vendor's existing credit or debit card processing interchange. The unique lottery BIN is also associated with a lottery data blob provided on the lottery ticket. The BIN and lottery data blob are entered into the vendor's existing credit or debit card barcode protocol to initiate transfer of the lottery data to a lottery central site via the interchange, wherein a processor within the interchange recognizes the unique lottery BIN and initiates special routing to and further processing of the lottery data at the lottery central site outside of the interchange's debit or credit card data transfer and processing procedures.
Owner:SCI GAMES LLC
Display of video and other content in retail stores
InactiveUS20100012600A1Protection from theftLess expensiveChestsDressing tablesEngineeringElectronic component
A shelf for use in a conventional retail display gondola or perimeter wall shelving includes an upper support surface for merchandise and an enclosure below that surface in which electronic components including a thin client computer or a media player are housed. A video display monitor has a screen visible through an opening in a front face of the shelf. The enclosure is usually secured to deny access to the electronic component, but can be opened to provide access to the electronic components housed therein.
Owner:MADIX
Adjustable tablet device holder
ActiveUS9797543B2Protection from theftLocks for portable objectsStands/trestlesEngineeringMechanical engineering
Owner:CHEN-SOURCE INC
Pre-alarm for abnormal merchandise handling
InactiveUS20130257616A1Protection from theftBurglar alarm by hand-portable articles removalBurglar alarm by disturbance/breaking stretched cords/wiresSecurity systemAlarm signal
Security systems and methods configured for use with an item of merchandise for retail display are provided. In one example, a security system includes at least one sensor operably coupled to the item of merchandise and at least one alarm module operably coupled to, and configured to communicate with, the at least one sensor. The alarm module is configured to generate a first alarm signal in response to the item of merchandise being handled in an abnormal manner, and the alarm module is further configured to generate a second alarm signal in response to the item of merchandise continuing to be handled in an abnormal manner. In general, the second alarm signal is different than the first alarm signal.
Owner:INVUE SECURITY PROD INC
Mounting device for mobile information terminal, and mobile information terminal
ActiveUS20070142097A1Avoid accidental ejectionReduce processing stepsBatteries circuit arrangementsSubstation equipmentElectrical connectionEngineering
A mounting device includes a case that has an insertion inlet for a mobile information terminal, a connector that establishes electrical connection to the mobile information terminal inserted in the insertion inlet, and an ejection mechanism that ejects the mobile information terminal after completion of processing through the connector. After the completion of the processing, by an action of the ejection mechanism, the mobile information terminal is popped up from the mounting device, and a user is understandably notified of the completion of the processing.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Systems and techniques for vandalism detection in a personal communication structure (PCS)
ActiveUS20170175411A1Enhance public accessImprove network coverageComplete banking machinesBurglar alarm with fastening tamperingCommunications systemEngineering
Systems and techniques for vandalism detection in a personal communication structure (PCS) are described. The PCS may include one or more vandalism detection systems which may be located in different system compartments of the PCS. Each vandalism detection system may include (or being communicatively coupled to) an accelerometer and may be able to differentiate forces associated with acts of vandalism from other forces. The vandalism detection systems may transmit alerts with accompanying data to a remote entity. The data allows for an appropriate response to the alert. The alert may be transmitted to a remote security center over a wired or wireless communications system. The controller may transmit the alert again or to other locations if an acknowledgement is not received.
Owner:CITYBRIDGE LLC
Display of video and other content in retail stores
InactiveUS8231017B2Protection from theftLess expensiveChestsDressing tablesEngineeringElectronic component
A shelf for use in a conventional retail display gondola or perimeter wall shelving includes an upper support surface for merchandise and an enclosure below that surface in which electronic components including a thin client computer or a media player are housed. A video display monitor has a screen visible through an opening in a front face of the shelf. The enclosure is usually secured to deny access to the electronic component, but can be opened to provide access to the electronic components housed therein.
Owner:MADIX
Solar collector support system for efficient storage, transport, and deployment of an expandable array of rotatable solar collectors
InactiveUS20110023864A1Larger power generation capabilitiesEasy to deployPhotovoltaic supportsSolar heating energySupporting systemSolar energy harvesting
Compact solar collector arrays with multiple axis adjustability for use with mobile structures, such as trailers, RVs, etc., and temporary support structures and associated methods of use are disclosed that provide significant power generation capacity per roof area, easy deployment, optimum orientation regardless of underlying vehicle or structure orientation, and protection for solar collector arrays during transport. Some embodiments include a plurality of solar collector mounts coupled to a support surface, the plurality of solar collector mounts being capable of changing relative spatial arrangement of each solar collector with respect to at least a neighboring solar collector.
Owner:ANDRETICH MICAH F
Identification Processing Apparatus and Mobile Device Using the Same
ActiveUS20120001725A1Protection from theftElectric signal transmission systemsDigital data processing detailsStorage cellPassword
An identification processing apparatus is provided for performing an identification procedure according to a smart card, including a storage unit for storing a first password; and an authentication unit for determining whether to perform the identification procedure according to a second password and the first password.
Owner:XUESHAN TECH INC
Device and method for the automatic handover of goods
InactiveUS20040133304A1Flexible adaptationEasy usabilityDigital data processing detailsApparatus for meter-controlled dispensingComputer networkControl cell
The invention pertains to an apparatus for receiving ordered products and / or making products available for pickup, particularly in the absence of the user. The apparatus has a lockable container of the products with at least an input device and a controller with a memory element. The method employs this reception / provision apparatus. In order to create a method for receiving ordered products and / or making products available for pickup that requires easy handling and slight construction measures at the residence or place of business of the user, it is proposed in regard to the apparatus that a control unit (18) comprising at least input device (6), controller (7) and memory element (8) can be positioned with container (2) in front of the user's residence or place of business for an expected delivery / pickup. With regard to the method, it is proposed that, after a completed ordering process, the obtained order information (9) be input by the user into memory element (8) of reception / provision apparatus (1) to put reception / provision apparatus (1) in a state of readiness and that transportable reception / provision apparatus (1) be positioned in front of the user's residence or place of business for the expected delivery or pickup of product (11).
Owner:SESAM
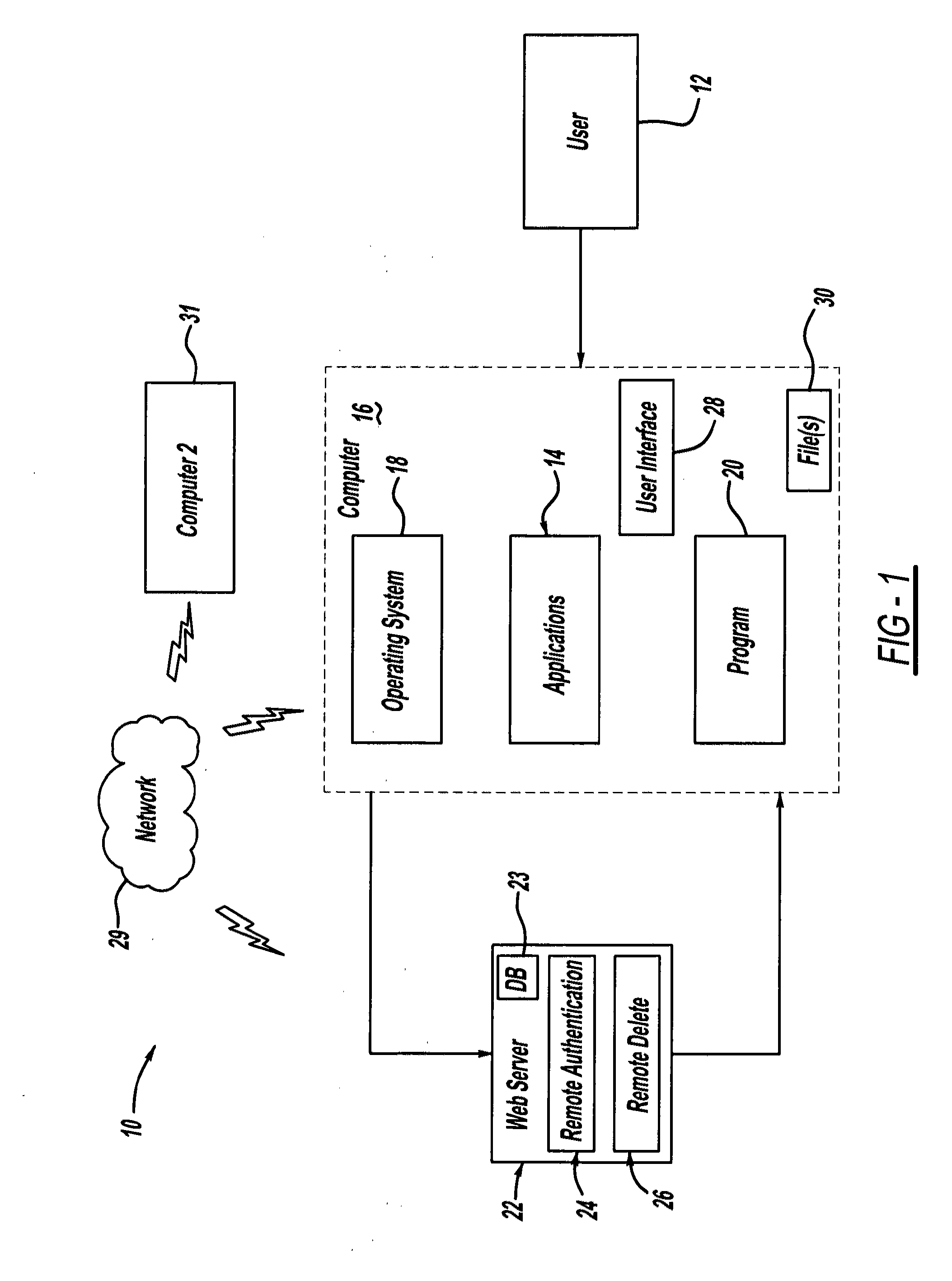
Document encryption and decryption
InactiveUS20120036358A1Easy to readEasy to viewVolume/mass flow measurementUser identity/authority verificationWeb serviceDocumentation
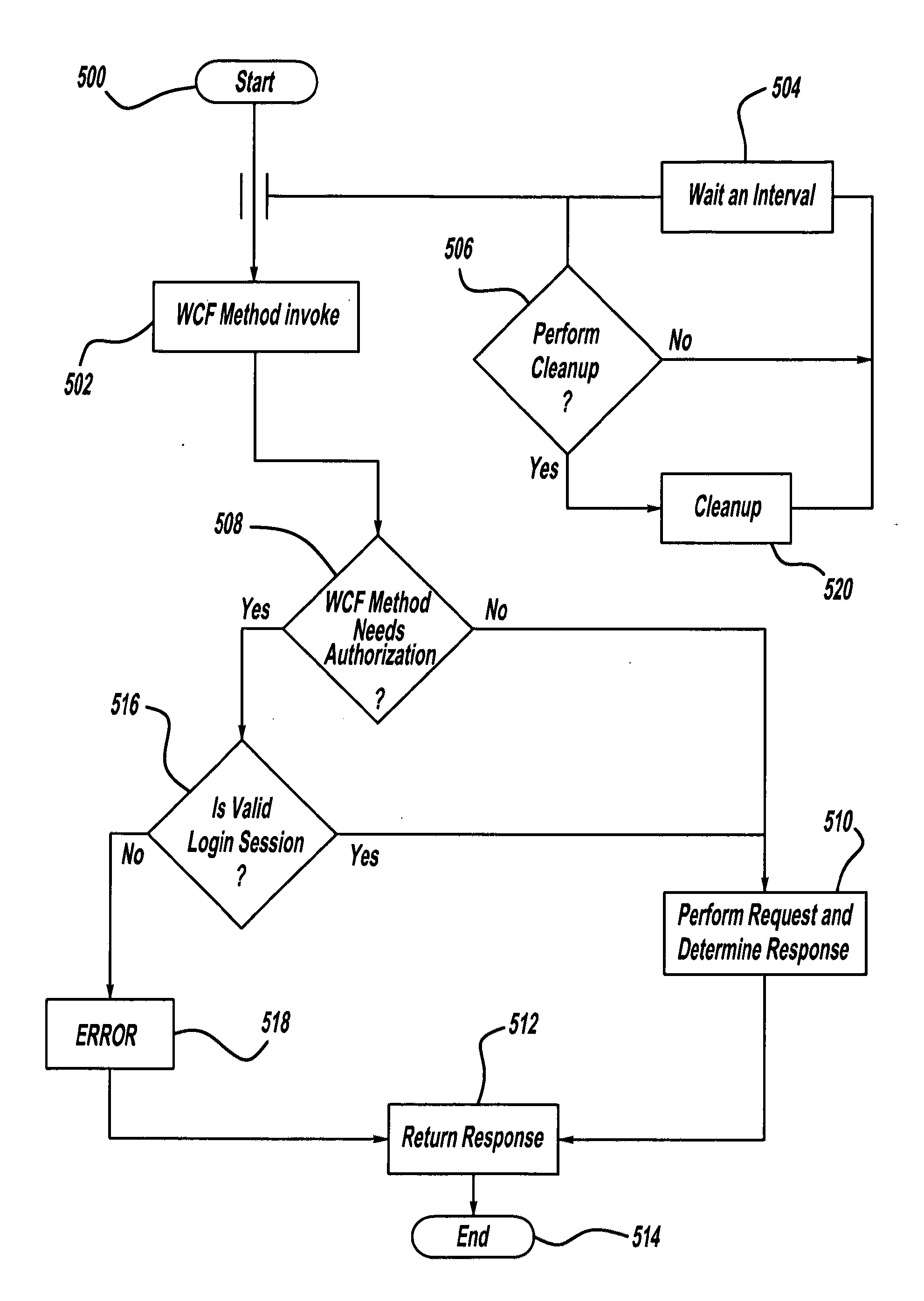
A document encryption and decryption system for selectively encrypting and decrypting files and any other items and method for same to protect or secure its contents by helping to prevent unauthorized individuals from viewing data in human-perceivable or readable form. The encryption system includes remote authentication to verify a user's credentials stored on a remote database hosted by a web server. The encryption system further includes remote delete to automatically delete encrypted items stored on the user's computer, handheld or portable device, smartphone, and any other computing device of any kind when it logs onto a network if the user's computer or computing device is reported lost, stolen, or otherwise compromised. Decryption keys allow selective decryption of encrypted items that are on the computer or computing device of any kind. A Windows Communication Foundation service helps with authenticating the users with the encryption key and login process stored and processed by the web server.
Owner:SECURENCRYPT
Mechanism for locking and fault detection in the electrical vehicle supply equipment cord
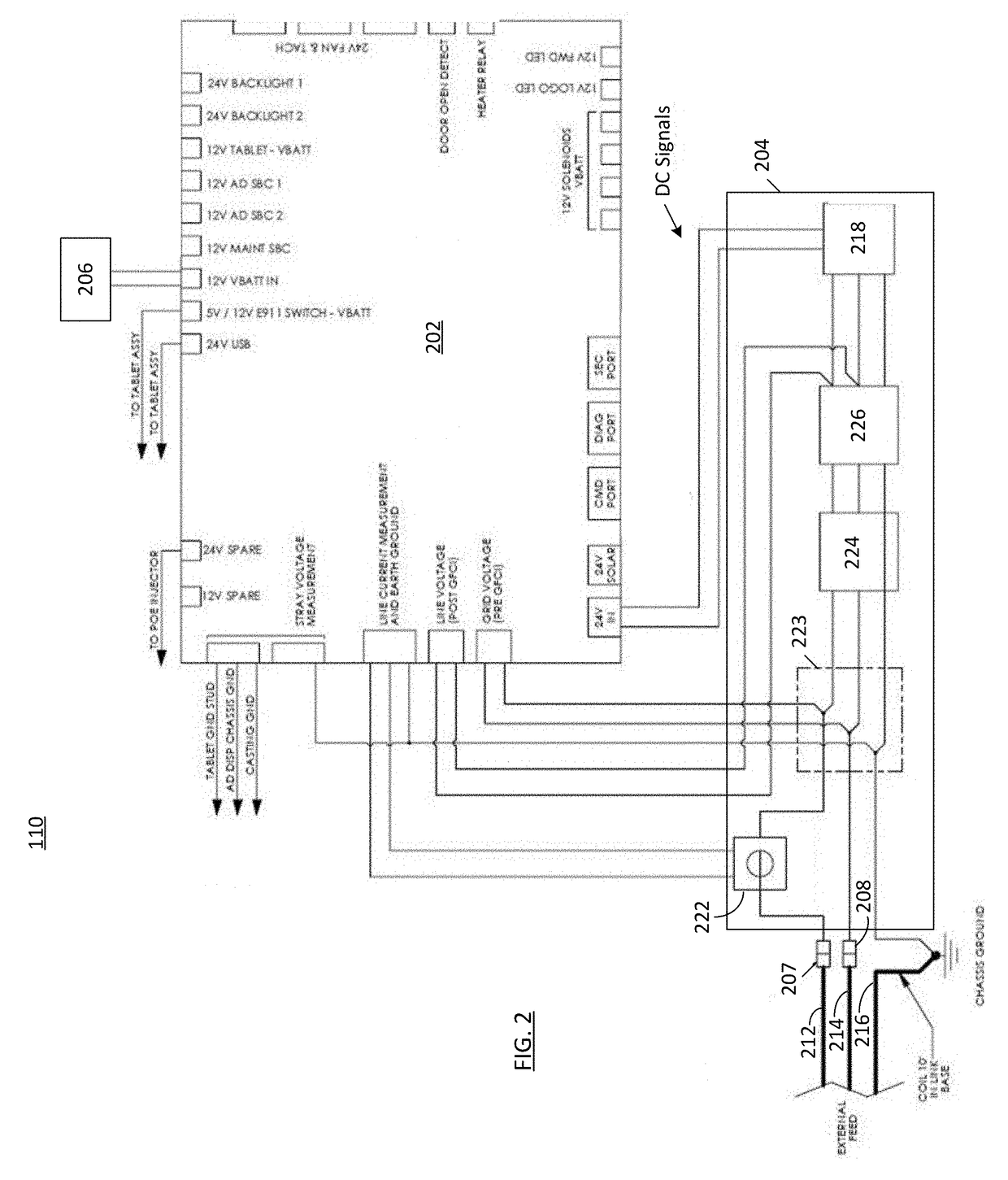
ActiveUS20150048791A1Protection from theftBatteries circuit arrangementsCharging stationsLocking mechanismEngineering
An electric vehicle charging assembly includes a cord reel, a cord reel locking mechanism, and a master control unit for selectively unlocking the cord reel in response to an authorization signal. The electric vehicle charging assembly monitors the rotational position of the cord reel to prevent unauthorized use, and to record or relay information related to the improper use or malfunction of the electric vehicle charging assembly.
Owner:KONNECTRONIX INC
Autonomous, multipurpose floating platform for environmental and oceanographic monitoring
InactiveUS20080223278A1Improve stabilityLow displacement of volumeWaterborne vesselsBuoysGravity centerEngineering
Highly stable floating platform for measuring surface and subsurface environmental variables. It consists of a main toroidal body, inside of which equipments are installed, mainly on its base, to maintain low and nearby the centers of gravity and of buoyancy, allowing the in situ inspection, maintenance and installation of equipments. One winch in its interior allows the translation of equipment and / or to take water samples, from surface to a user-defined depth, using a cable deployed through the center of the platform, for providing power and communication with the surface to said equipment.
Owner:UNIV CATOLICA DE LA SANTISIMA CONCEPCION
Logistics Methods for Processing Lottery and Contest Tickets with Generic Hardware
ActiveUS20160019749A1Reduce clutterSimplify interfaceApparatus for meter-controlled dispensingBuying/selling/leasing transactionsDebit cardLogistics management
A lottery data transfer method for processing lottery ticket data piggybacks on a merchant's existing transaction card interchange system, such as a debit or credit card interchange system. A routing code is assigned to lottery tickets that is unique in the merchant's transaction card exchange, the routing code associated with a lottery data blob also provided on the lottery ticket. The routing code and data blob are entered into the merchant's existing transaction card activation protocol to initiate transfer of the lottery data to a central lottery site via the interchange. At an issuing processor within the exchange, the routing code is recognized and initiates special routing to and further processing of the lottery data blob at the lottery central site.
Owner:SCI GAMES LLC
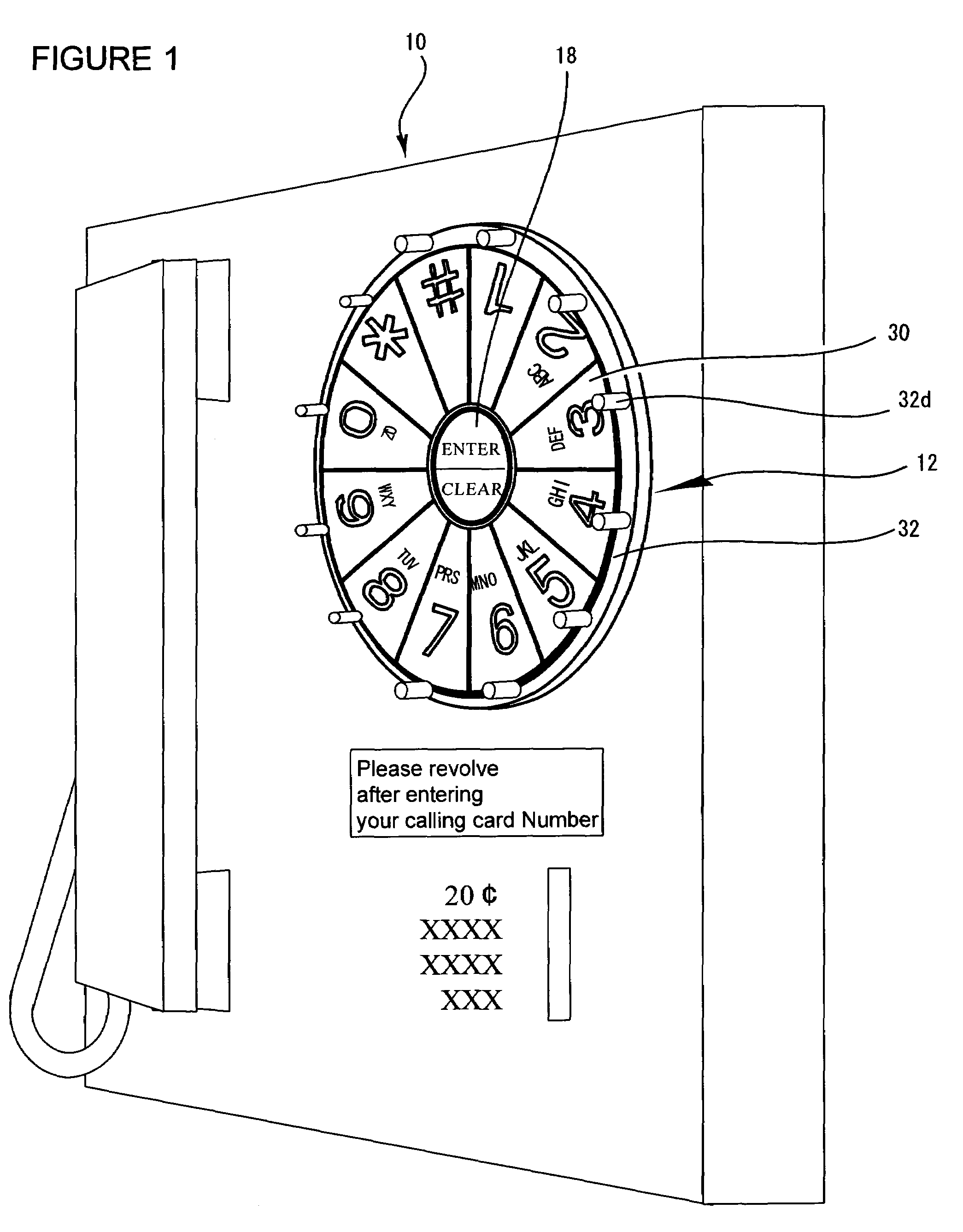
Information entry device
InactiveUS6925169B2Easy to touchEasy to pushInput/output for user-computer interactionInterconnection arrangementsDiscriminatorEngineering
The objective of this invention is to protect the information entry such as a PIN from theft by observation of the finger movement based on the conventional fixed arrangement of entry keys.The present invention is an information entry device including: keys for information entry; a circular support base on which the keys are mounted concentrically and arranged circularly in order, the support base being rotatable around the center of the circular arrangement for enabling a user to rotate the entire series of the mounted keys without changing their order around the center of the circular arrangement before or after the information entry; and an information discriminator for identifying the respective information of selected keys.This information entry device prevents a PIN or any other information entry from being stolen by someone who glances at the finger movement, since the entire series of the entry keys are rotated before or after the PIN entry. The information entry device of the present invention can be adapted for an ATM or POS terminal as well as for a touch panel screen monitor.
Owner:HABU TOMOHIRO
Logistics Methods for Processing Lottery and Contest Tickets with Generic Hardware
ActiveUS20130260856A1Reduce clutterSimplify interfacePayment architectureApparatus for meter-controlled dispensingBarcodeLogistics management
A lottery data transfer method for processing lottery ticket data piggybacks on a merchant's existing debit or credit card interchange system. A BIN is assigned to lottery tickets that is unique in the merchant's credit or debit card interchange, the BIN associated with a lottery data blob also provided on the lottery ticket. The lottery BIN and data blob are into the merchant's existing credit or debit card activation barcode protocol to initiate transfer of the lottery data to a central lottery site via the interchange. At a processor within the interchange, the unique lottery BIN is flagged to initiate special routing to and further processing of the lottery data blob at the lottery central site, wherein the lottery data blob is processed outside of the interchange's debit or credit card data transfer and processing procedures.
Owner:SCI GAMES LLC
Link-stealing-prevention method and system for media files and server
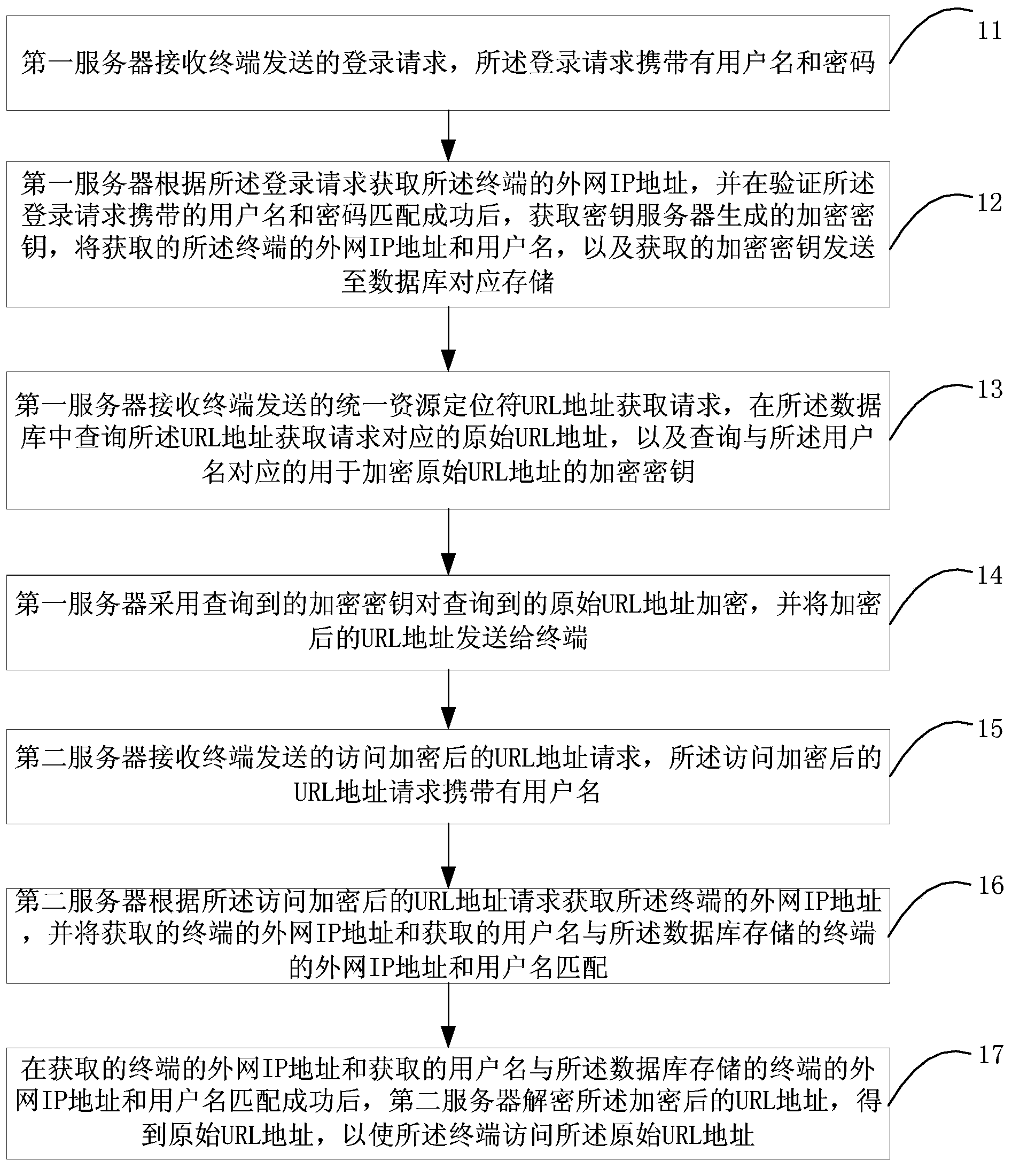
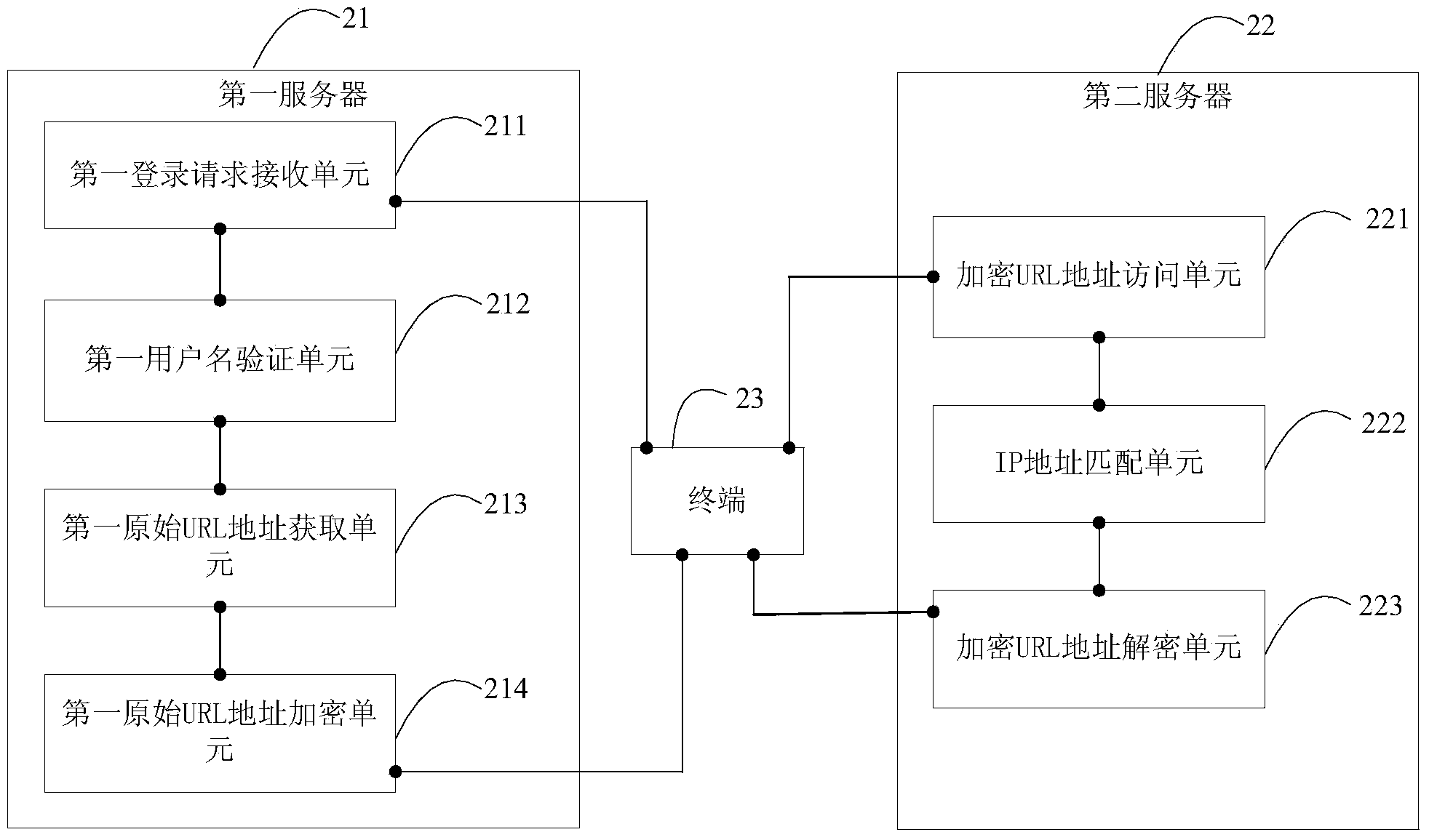
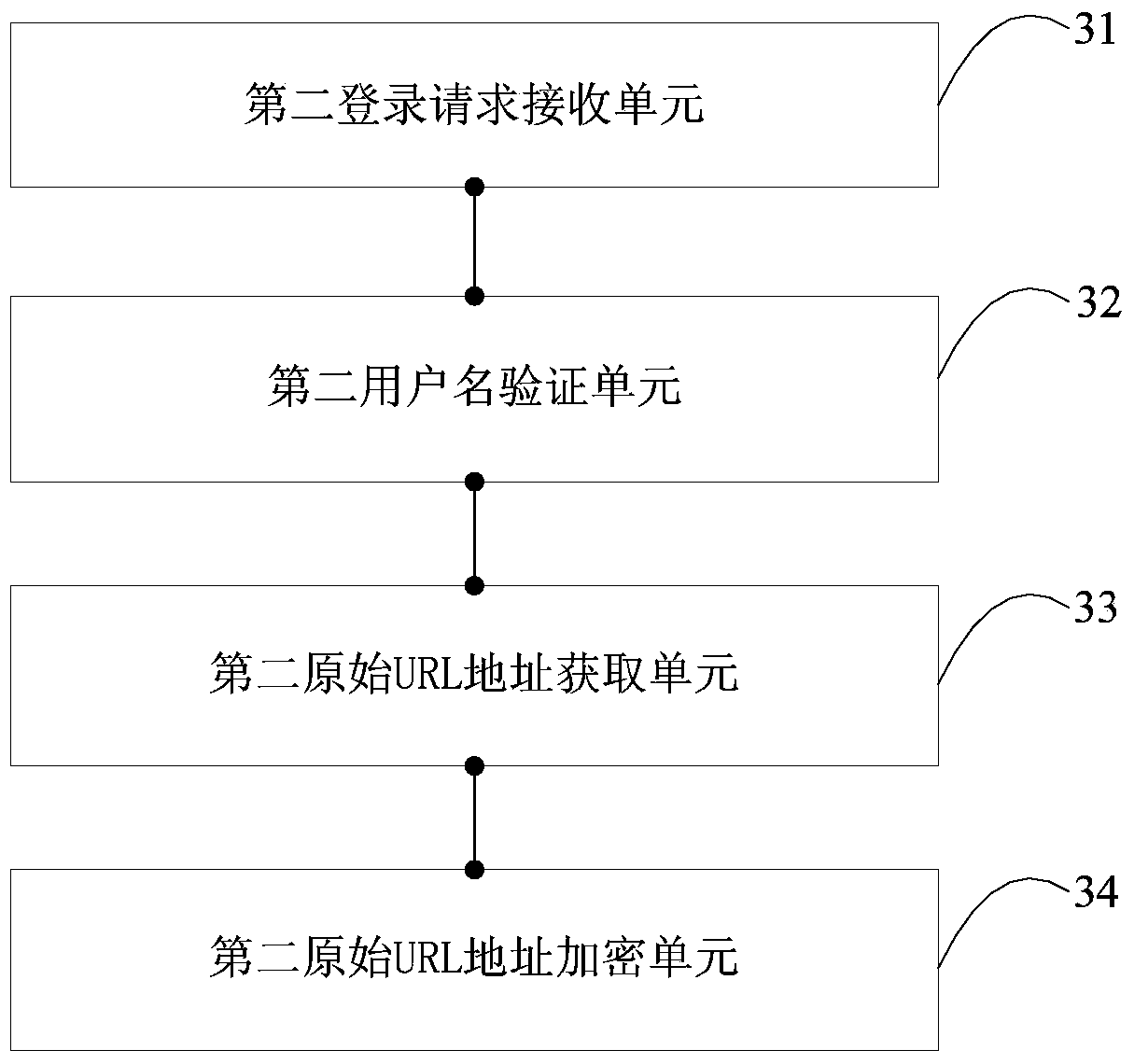
ActiveCN104009989AImprove confidentialityProtection from theftTransmissionIp addressUniform resource locator
The invention is suitable for the field of communications, and provides a link-stealing-prevention method and system for media files and a server. The method comprises the steps that a first server receives a log-in request; an outer network IP address and an encryption key of a terminal are obtained and the outer network IP address, a user name and the encryption key of the terminal are sent to a database to be stored; a URL address obtaining request is received, an original URL address corresponding to the URL address obtaining request is inquired and the encryption key corresponding to the user name is inquired; the original URL address is encrypted and the encrypted URL address is sent to the terminal; a second server receives an encrypted URL address access request; an outer network IP address of the terminal is obtained and the outer network IP address and the user name of the terminal are matched with the outer network IP address and the user name, stored in the database, of the terminal; after matching successes, the second server decrypts the encrypted URL address and the original URL address is obtained so that the terminal can have access to the original URL address. The link-stealing-prevention method and system can improve URL security.
Owner:TCL CORPORATION
Lock apparatus and method of use
InactiveUS20100089108A1Easily securedProtection from theftBicycle locksAnti-theft cycle devicesBiomedical engineering
Owner:SECURE STORAGE TECH
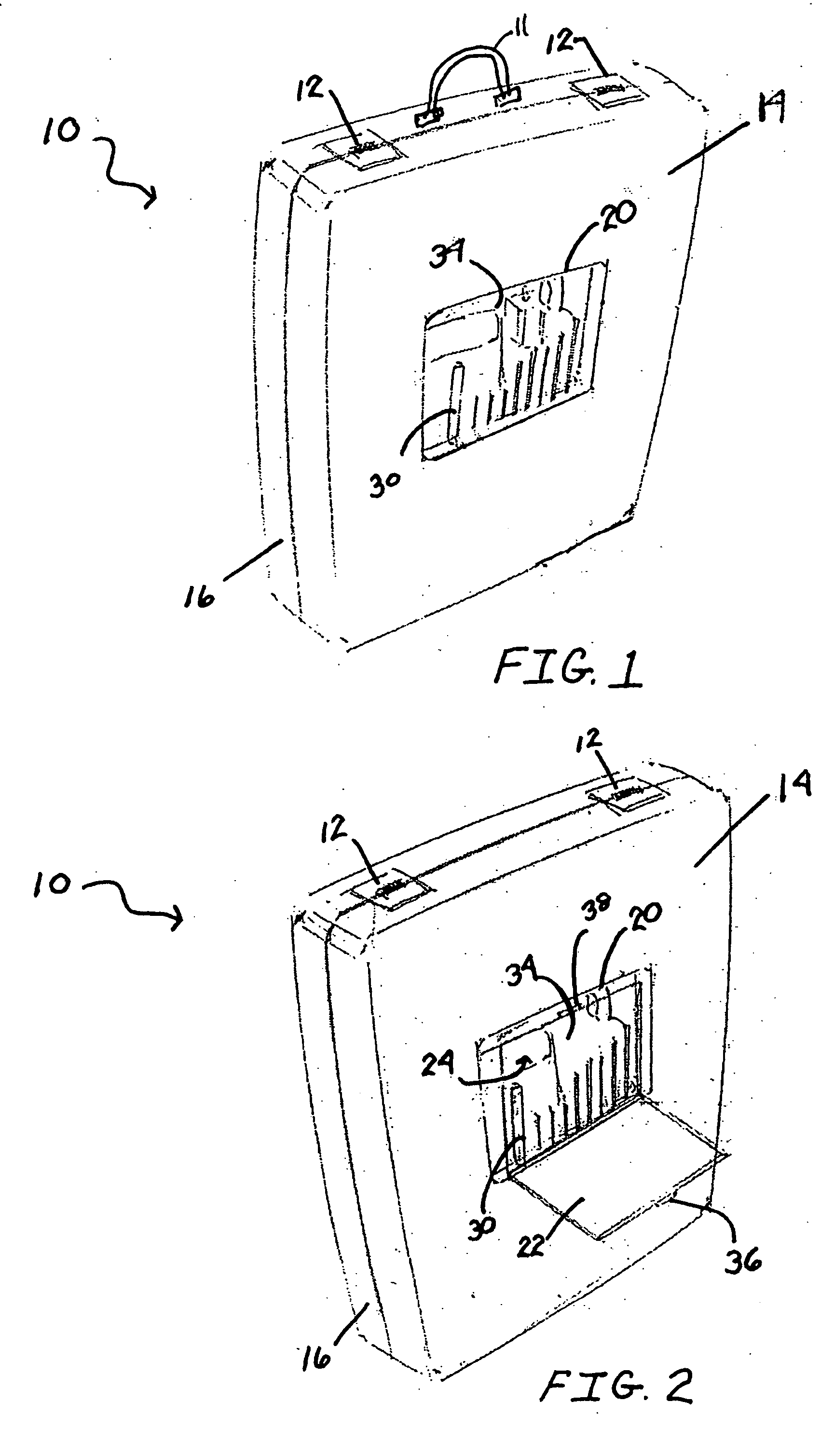
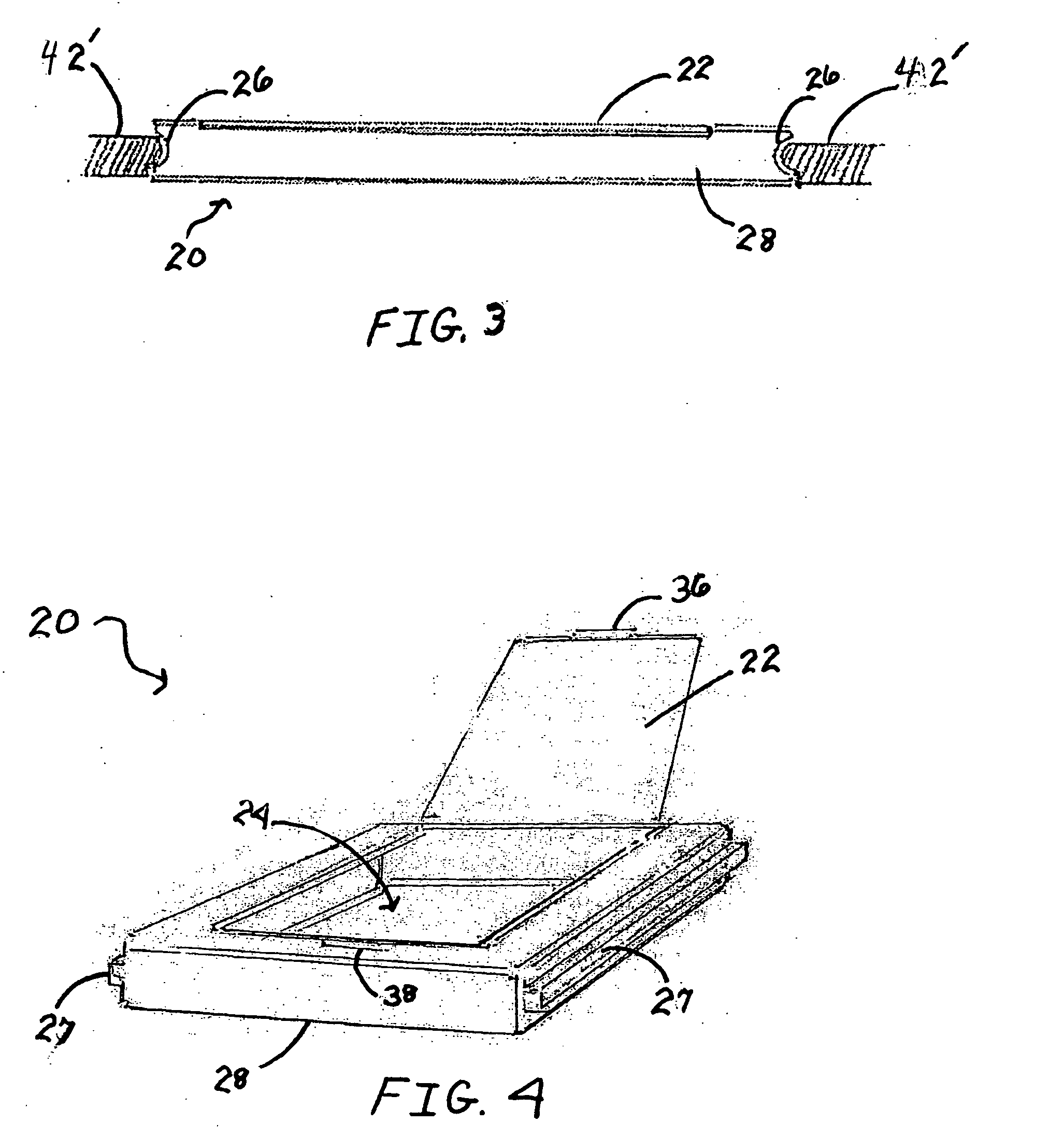
Case with removable accessory holder
A container, such as a toolbox, is disclosed with a reversible accessory holder. When the accessory holder is inserted into the container in a first position, the theft of the contents of the holder is prevented because the contents cannot be accessed from the exterior of the container nor can the holder be removed. When the accessory holder is inserted into the container in a second position, its contents can be conveniently accessed from the outside of the container by opening the accessory holder door without opening the entire container. A method of deterring the theft of items displayed in a container, while allowing access to those items from the outside of the container after purchase is also disclosed. The method includes inserting a reversible, transparent accessory holder into an aperture within a container, with the door of the holder facing the interior of the container, and then reversing the orientation of the holder to allow external access after purchase.
Owner:ONE WORLD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com