Link-stealing-prevention method and system for media files and server
A technology of media files and servers, applied in the field of communication, can solve problems such as exposure and difficult hotlinking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
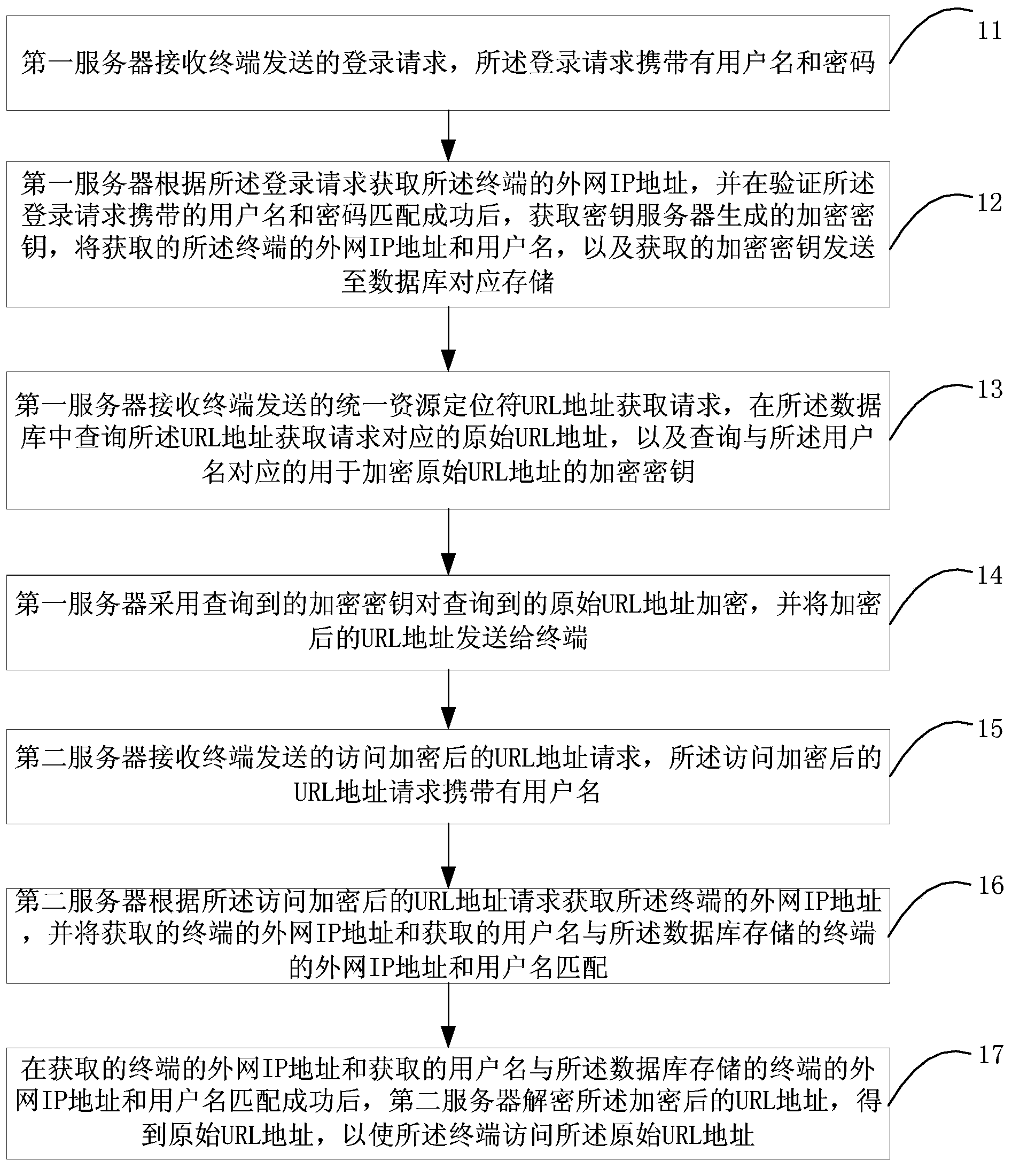
[0033] figure 1 Shows a flowchart of a method for preventing theft of media files provided by the first embodiment of the present invention. In this embodiment, the “first” in the “first server” and the “second” in the “second server” "Is only used to distinguish between different servers, and has no actual meaning such as sequence, etc. The details are as follows:
[0034] Step 11: The first server receives a login request sent by the terminal, where the login request carries a user name and a password.
[0035] In this step, the first server receives the http login request sent by the terminal. The http login request carries the user name and the password corresponding to the user name. Of course, the http login request may also carry information such as the identification code of the terminal.
[0036] Step 12: The first server obtains the external network IP address of the terminal according to the login request, and after verifying that the user name and password carried in the ...
Embodiment 2
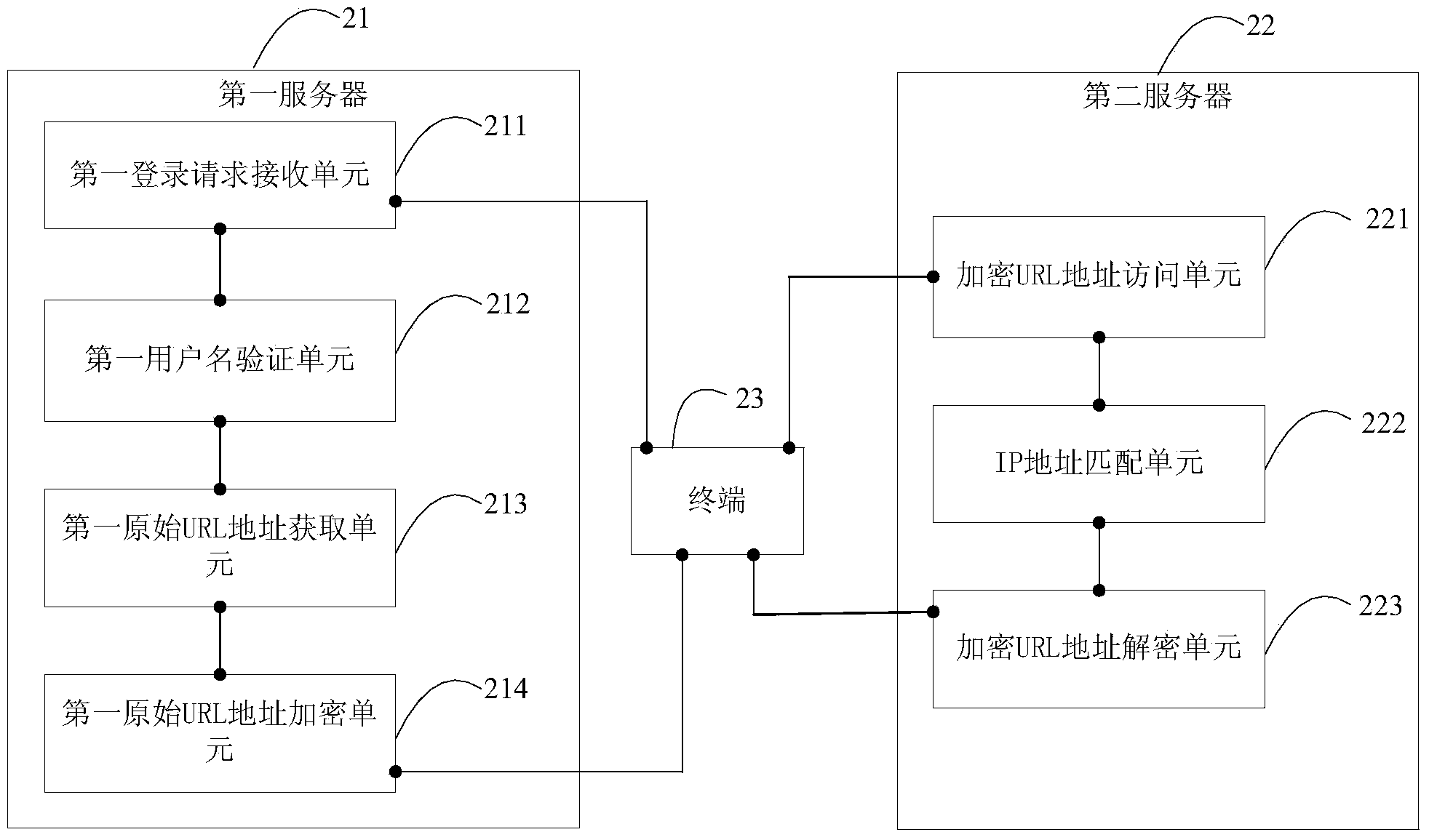
[0066] figure 2 It shows a structural diagram of an anti-theft chaining system for media files provided by the second embodiment of the present invention. For ease of description, only the parts related to the embodiment of the present invention are shown.
[0067] The anti-theft chaining system for media files includes: a first server 21, a second server 22, and a terminal 23. The first server 21 includes a first login request receiving unit 211, a first username verification unit 212, a first original URL address obtaining unit 213, and a first original URL address encryption unit 214. The second server 22 includes an encrypted URL address access unit 221. An IP address matching unit 222 and an encrypted URL address decrypting unit 223.
[0068] among them:
[0069] The first login request receiving unit 211 is configured to receive a login request sent by the terminal, where the login request carries a user name and password.
[0070] The login request refers to an http login re...
Embodiment 3
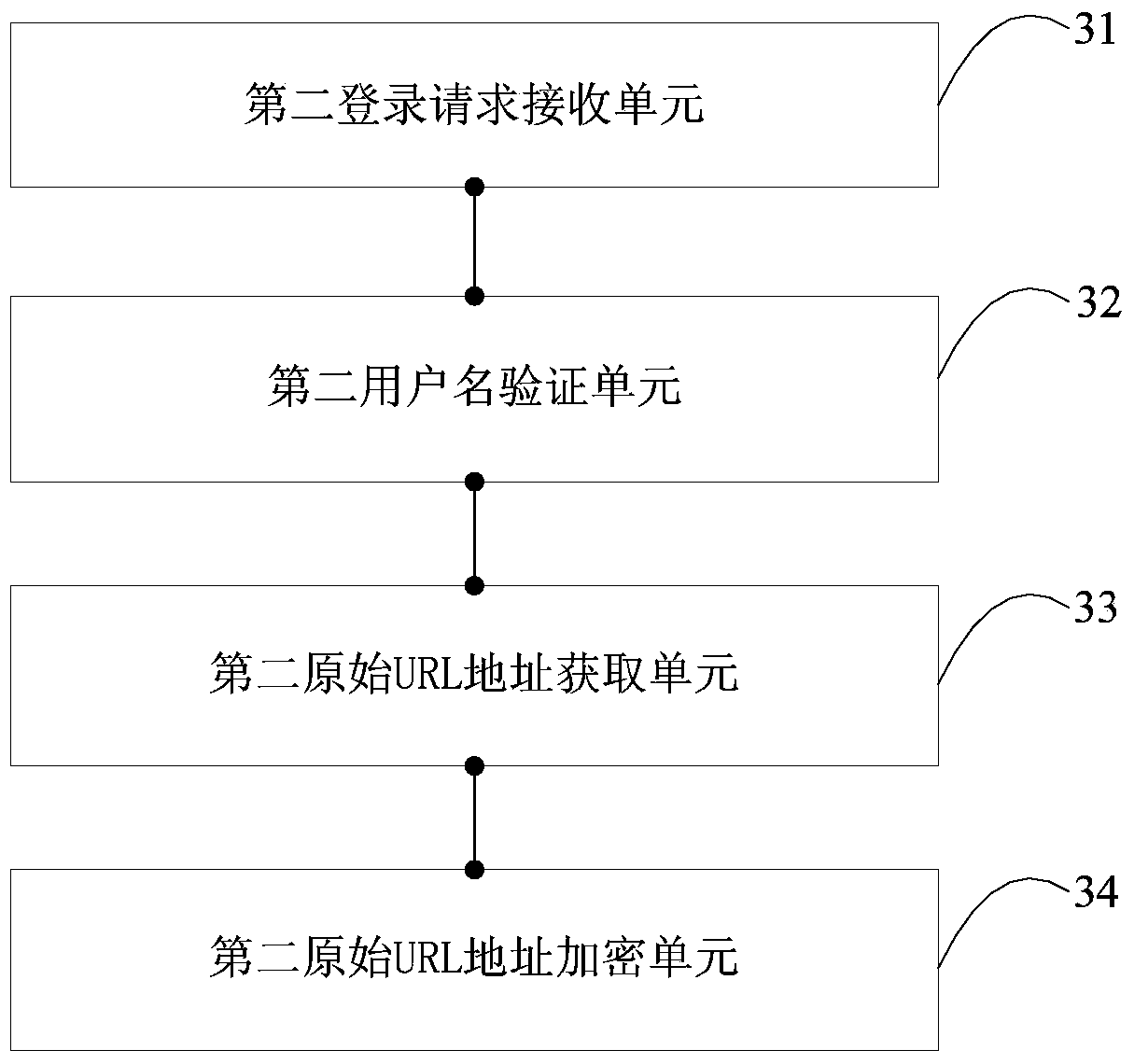
[0096] image 3 It shows a structural diagram of a server provided by the third embodiment of the present invention. For ease of description, only the parts related to the embodiment of the present invention are shown.
[0097] The server includes: a second login request receiving unit 31, a second user name verification unit 32, a second original URL address obtaining unit 33, and a second original URL address encryption unit 34. among them:
[0098] The second login request receiving unit 31 is configured to receive a login request sent by the terminal, where the login request carries a user name and password.
[0099] The login request refers to an http login request sent by the terminal, and the http login request may also carry information such as the identification code of the terminal.
[0100] The second user name verification unit 32 is configured to obtain the external network IP address of the terminal according to the login request, and obtain the encryption key generated ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com