Secure file processing method, equipment and system
A security processing and file technology, applied in the field of Internet application technology and communication, can solve the problems of frequent upgrades, complex encryption technology, frequent upgrades of virus signature databases, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions of the present invention will be described in further detail below with reference to the accompanying drawings and embodiments.
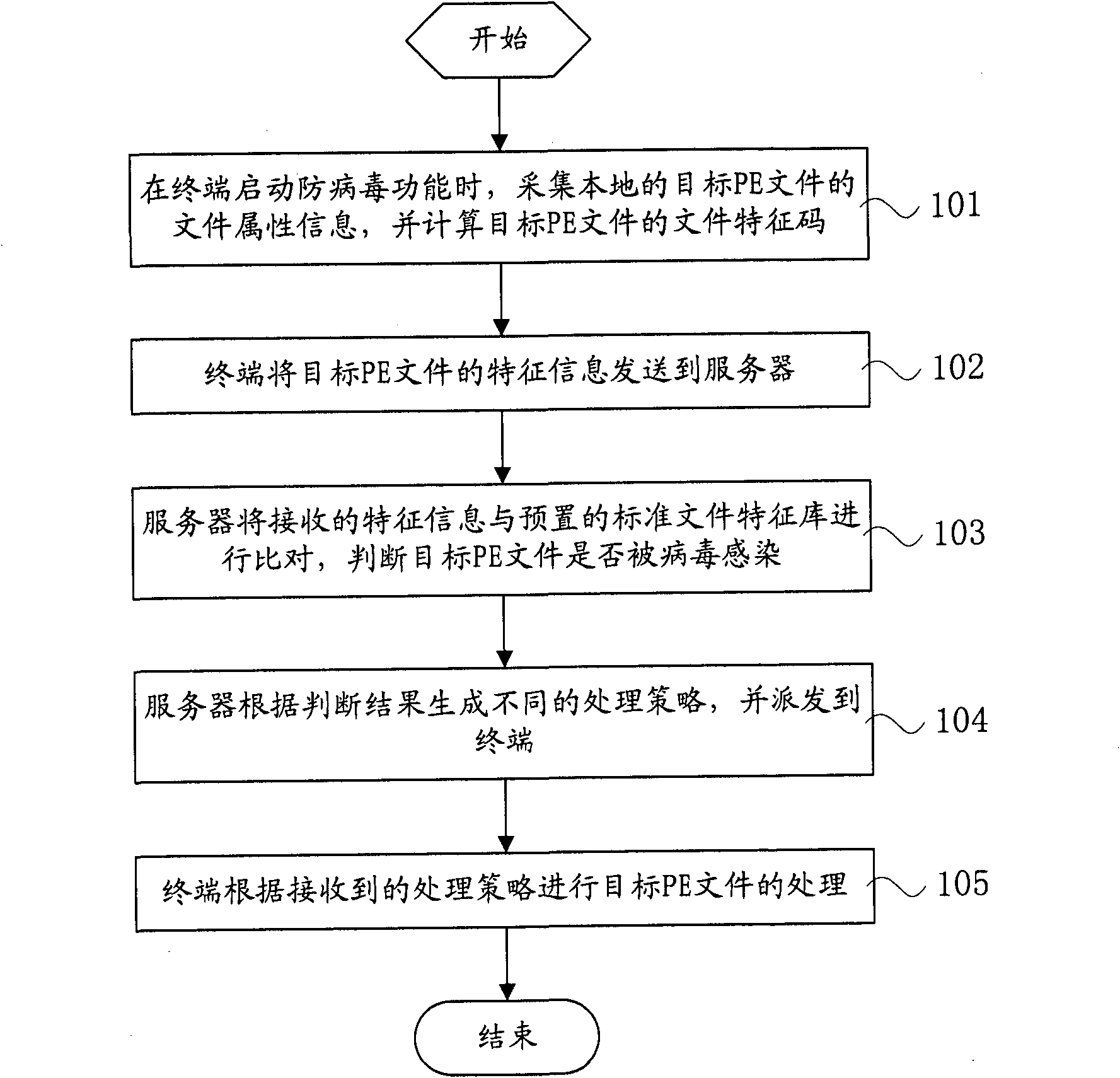
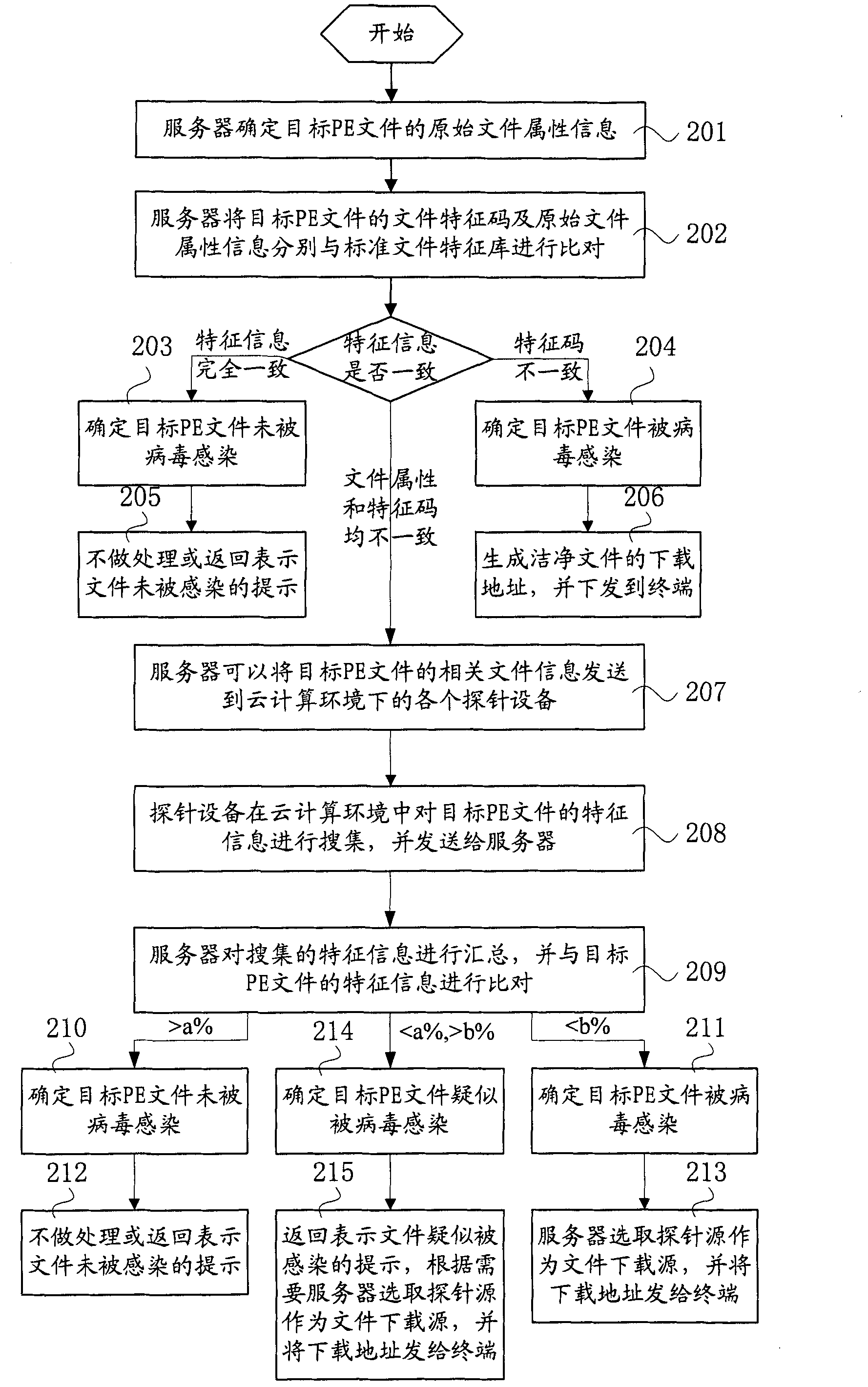
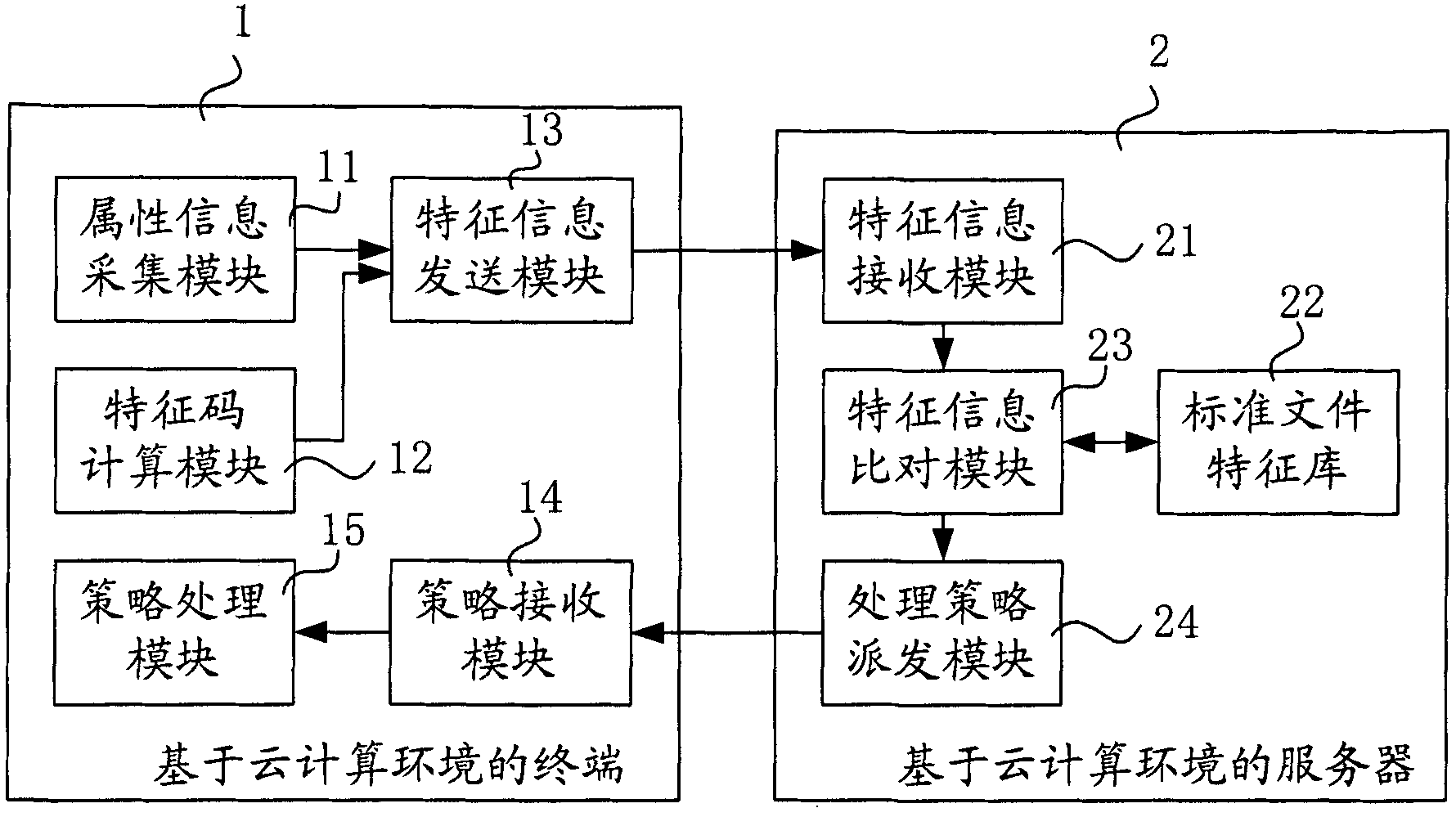
[0039] File type virus among the present invention refers to the PE file (portable executable file, portable executable file, comprises system executable or by link executable file, as COM, EXE, SYS and DLL file) on the infectable disk Virus. Such files usually have relatively fixed file attributes, and are also the main type of files infected by parasitic file viruses. File-type virus infection is mainly by modifying the code of a specific part of the file (such as the value of the words 02, 04, 0E, 10H, 14H, and 16H in the EXE file header) and inserting the virus code into the file body to make the program file run The virus code is able to reside in memory prior to the execution of program files.
[0040] The main way of file-type virus infection in the Internet age is the resource sharing between user terminals o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com