Network login system and method with face authentication
A network login and network system technology, applied in user identity/authority verification, instrument, character and pattern recognition, etc., can solve the problems of password theft, poor security performance, inability to accurately confirm the real identity of network users, etc. The effect of embezzlement and security improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
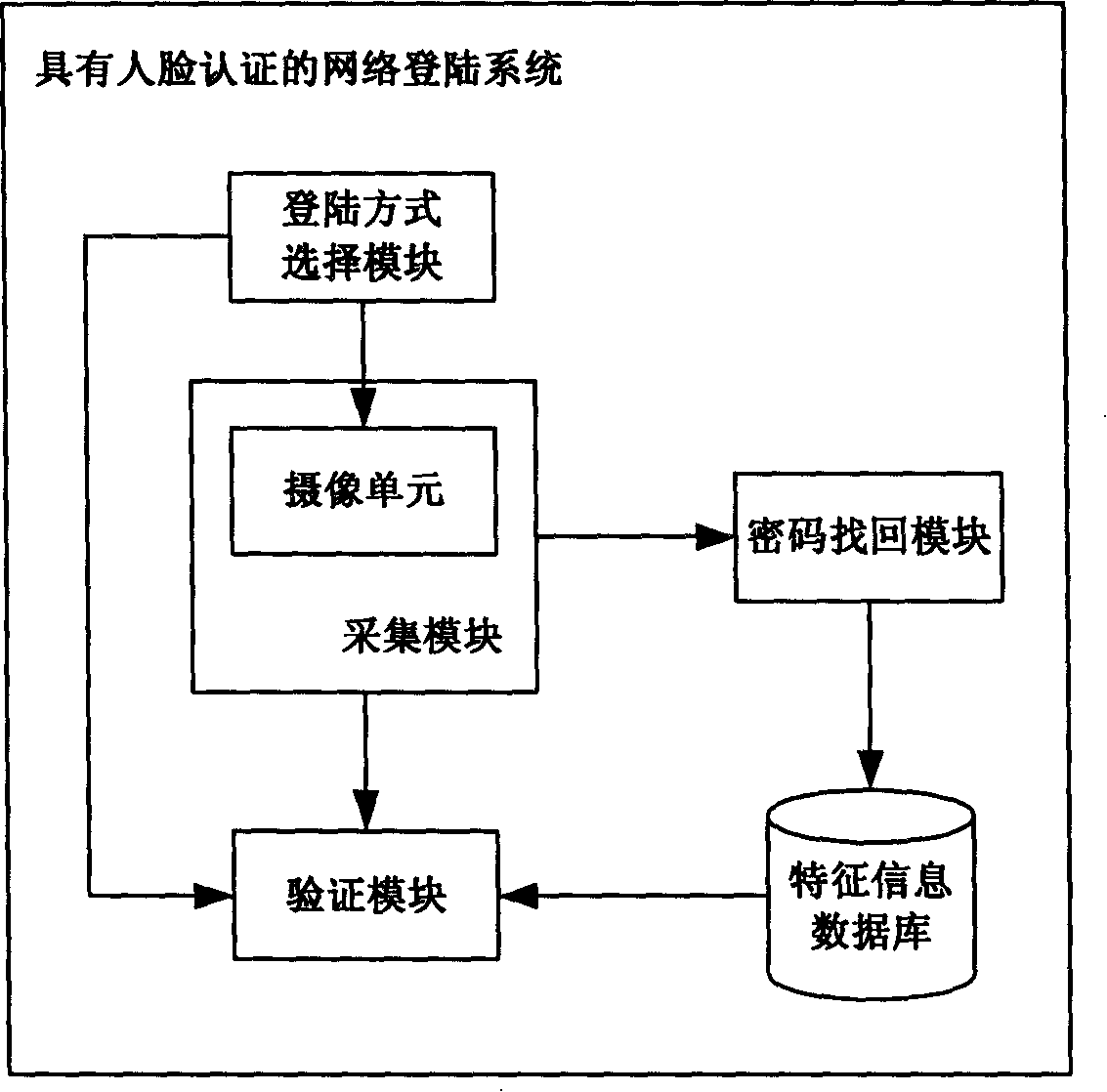
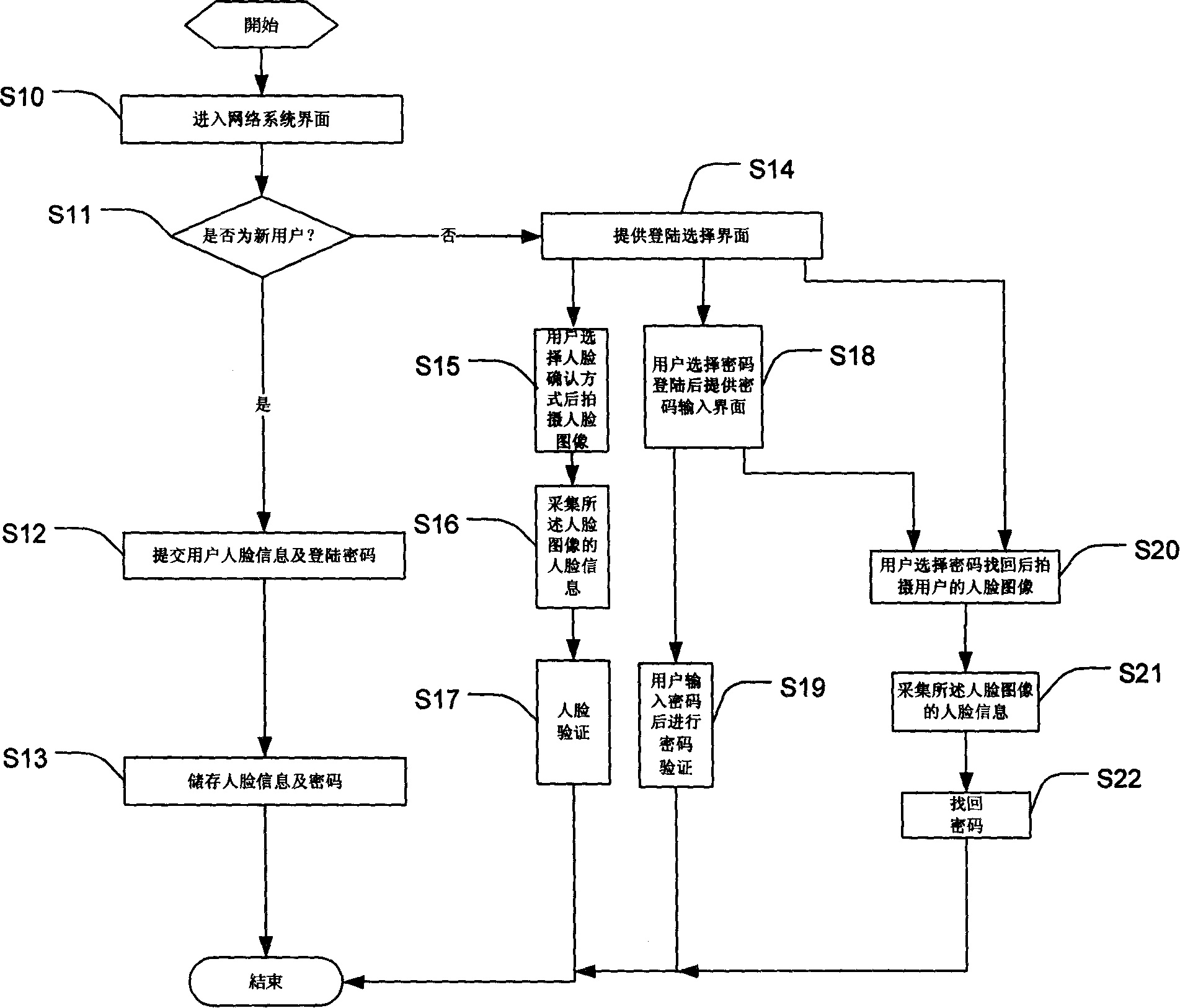
[0014] see figure 1 , the network login system with face authentication of the present invention at least includes: a feature information database, a login mode selection module, a collection module, a verification module and a password retrieval module.
[0015] The characteristic information database is used to store the characteristic information including face information submitted by the user when registering in the network system. For example, when the user registers in the QQ chat system or the MSN system, his own photo is extracted through the facial feature extraction algorithm. extract its face information, and store the face information and the set login password in the feature information database, wherein the feature information database can be set on the user's local machine for the user to manage, In order to avoid the management of many user identity information by network system administrators, it can also improve the security of network user identities. In ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com