Method for obtaining digital siguature and realizing data safety
A digital signature and data security technology, which is applied in the direction of electronic digital data processing, security devices, digital transmission systems, etc., can solve problems such as long calculation time, key leakage, and loss of both parties in the transaction, so as to reduce CA authentication links and avoid Private key management, the effect of reducing the implementation process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
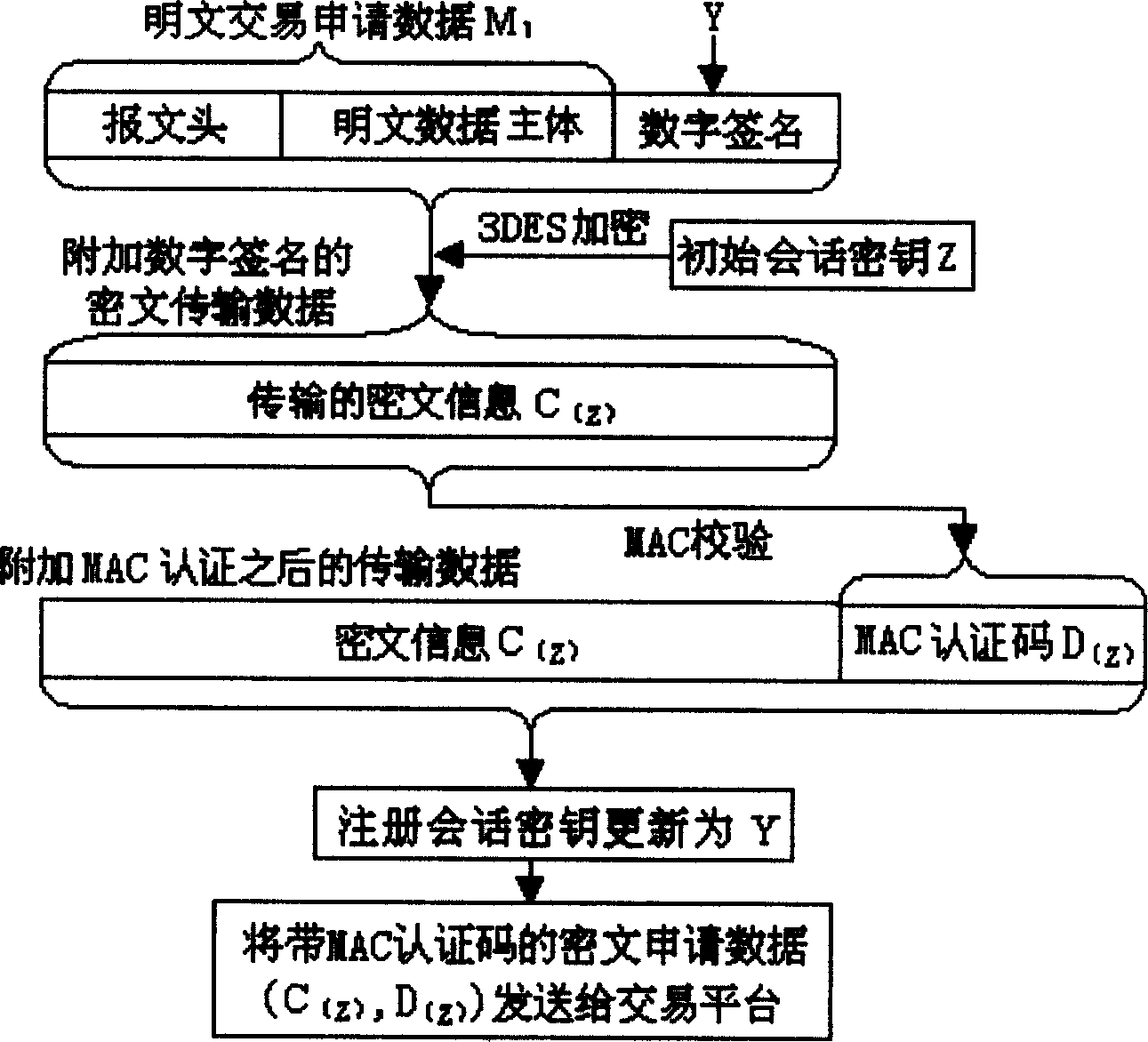
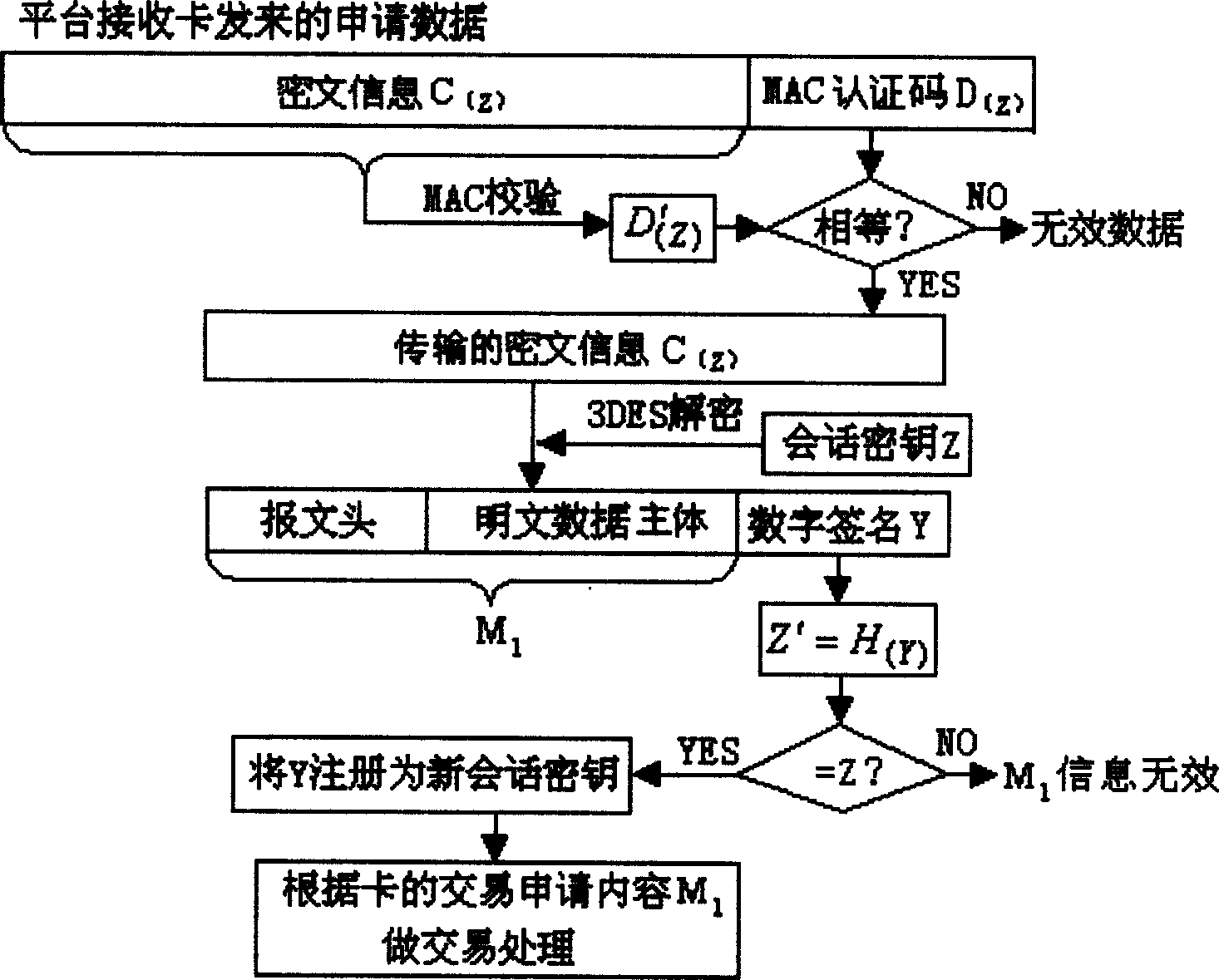
[0044] An embodiment of the application of the present invention in the mobile transaction process is described below with reference to the accompanying drawings.
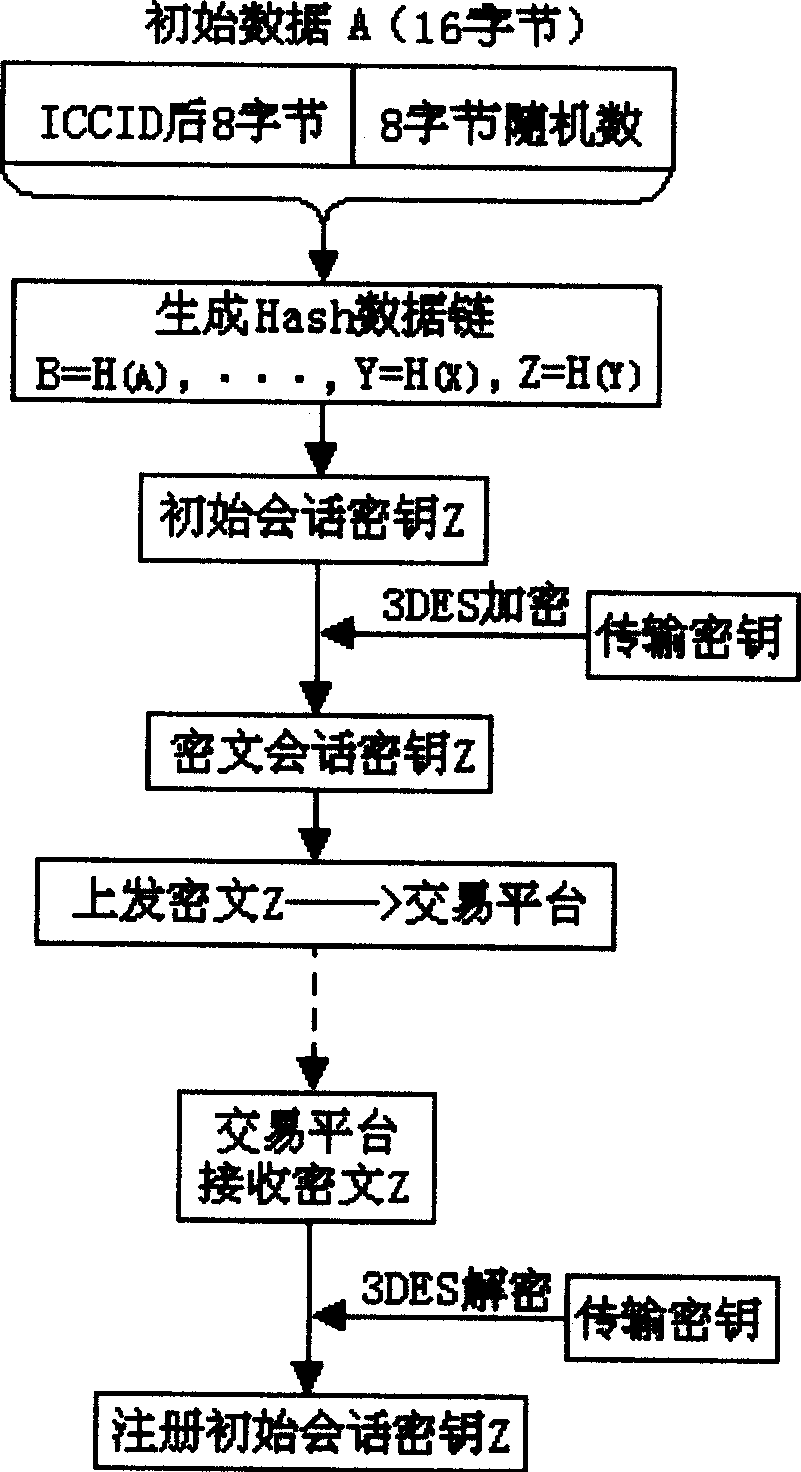
[0045] The following comparison figure 1 Explain the principle of registering the initial session key in the method for realizing data security.
[0046] In the initial stage of information interaction with the trading platform, the SIM card or UIM card must first register the initial session key. The session key is the common encryption and decryption key adopted by both parties of data exchange.
[0047] ①The card end generates the initial data A of the Hash data chain
[0048] The initial data A of the Hash data chain is composed of 16 bytes, including the last 8 bytes of ICCID (Integrated Circuit Card Identifier, that is, the integrated circuit card user identification number) and 8 bytes of random numbers. The ICCID of each card guarantees The digital signatures and session keys generated by all SIM cards o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com