Terminal verification method and device
A verification method and verification device technology, applied in the field of communication, can solve the problems of no binding mechanism and lack of binding mechanism between software and hardware, and achieve the effect of being difficult to be cracked and the encryption method is effective.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
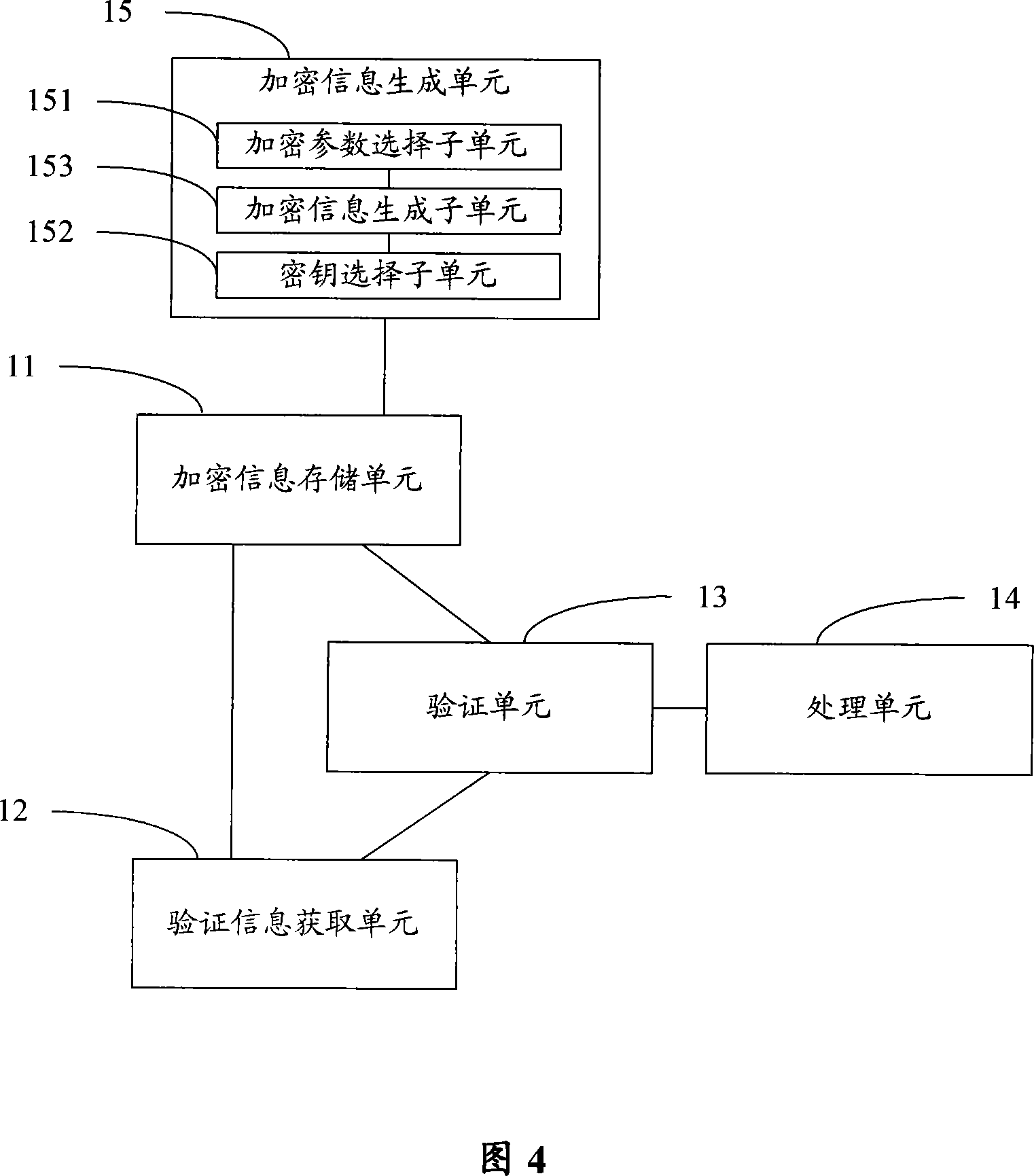
Image
Examples
Embodiment Construction
[0023] The specific implementation manners of the present invention will be further described below in conjunction with the drawings and embodiments.
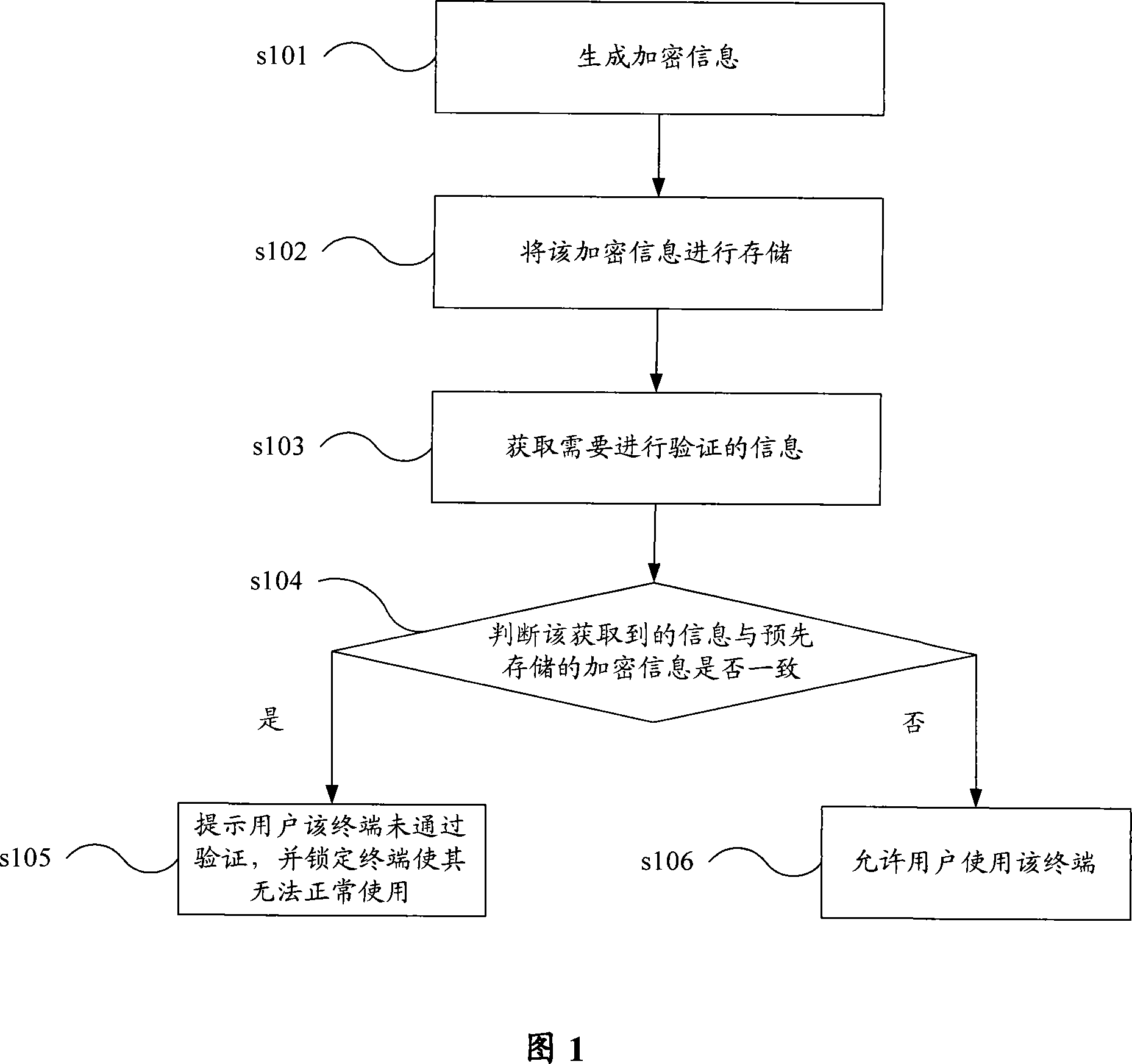
[0024] In Embodiment 1 of the present invention, a terminal verification method is shown in Figure 1, including the following steps:
[0025] Step s101, generating encrypted information.
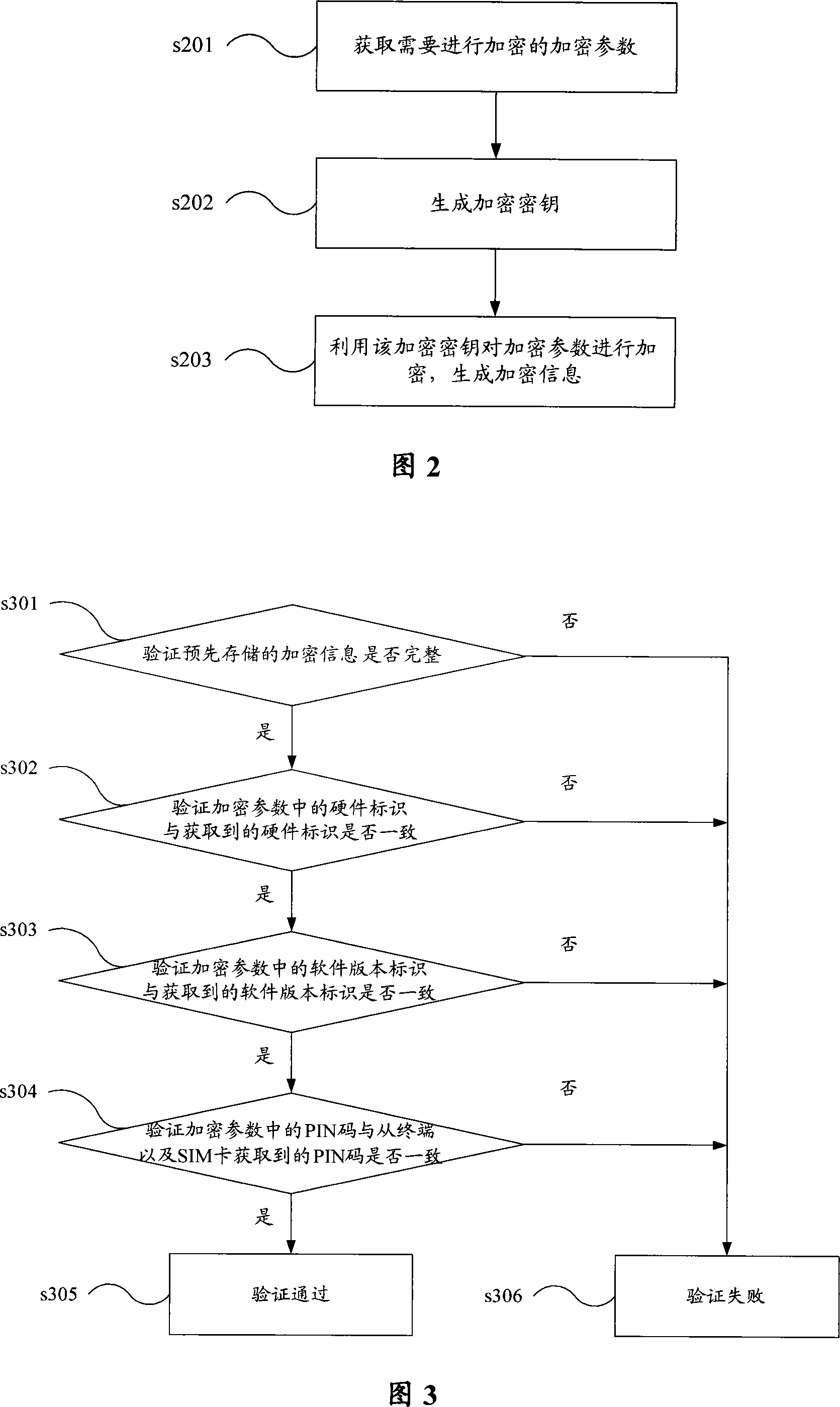
[0026] Taking mobile terminal equipment as an example, the encrypted information may include one or more of parameters such as hardware identification, terminal software version identification, PIN code, SIM card IMSI code (International Mobile Subscriber Identifier, International Mobile Subscriber Identifier), etc. Encrypted information obtained after encryption.
[0027] Step s102, storing the encrypted information.
[0028] The storage location of the encrypted information in the terminal can be selected according to needs, so that it is difficult for crackers to find the encrypted information.
[0029] Step s103, acquiring information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com