Digital encryption algorithm
An encryption algorithm and digital technology, applied in encryption devices with shift registers/memory, key distribution, can solve the problem of time-consuming decryption of asymmetric algorithms, and achieve the effect of low cost and data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
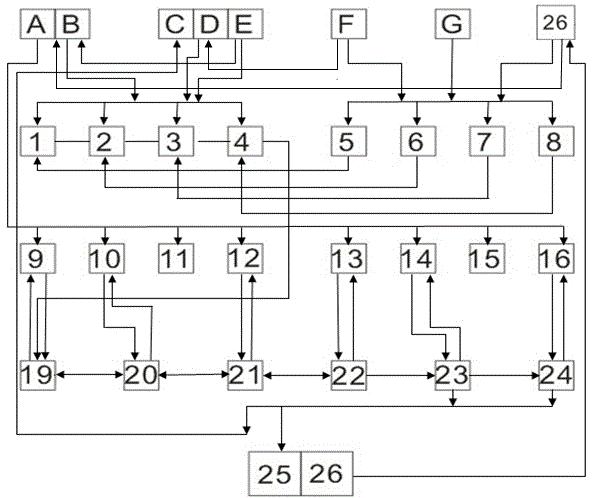
[0010] Specific implementation methods: The implementation methods discussed in this specification introduce the general process of implementing this patent, but implementing this patent does not necessarily need to completely follow the process described here, it is only a special case of implementing this patent.
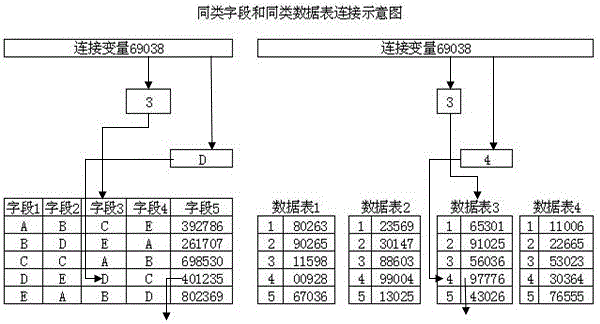
[0011] Explanation of terms: source data, strictly speaking, connection variables, passwords entered by users, etc. are also source data, but the source data in this manual is defined in a narrow sense, which only refers to encrypted data, such as 6 groups of connection variables through magnetic stripe cards The imported 6 sets of data, these 6 sets of data are the source data, and the others are not source data. For encryption needs, the source data has more characters, too few characters, and the encryption strength is not enough.
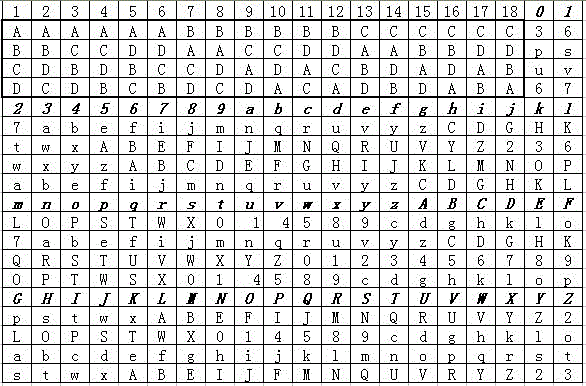
[0012] Data and characters, strings, in computer and telecommunications technology, a character is the basic information of a unit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com