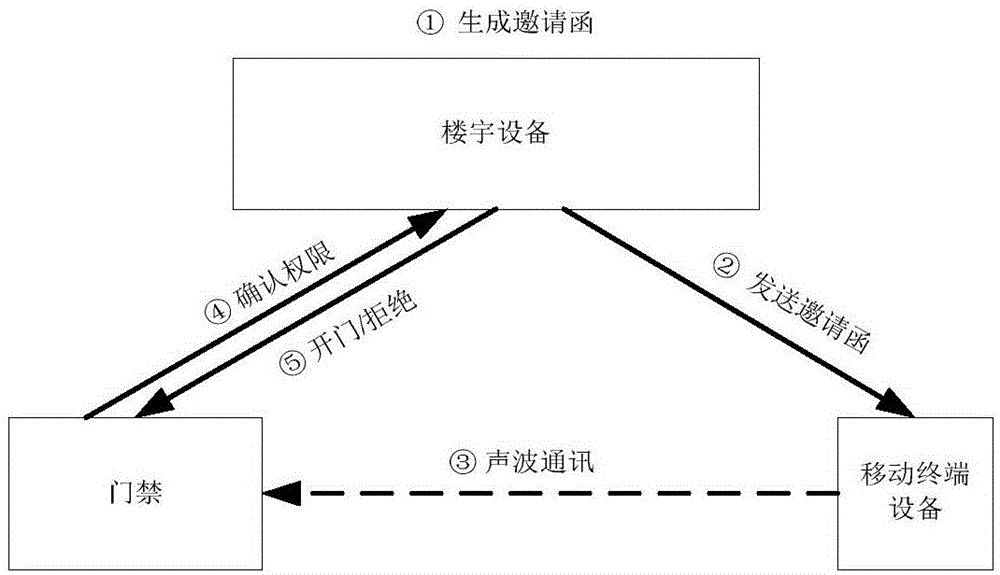
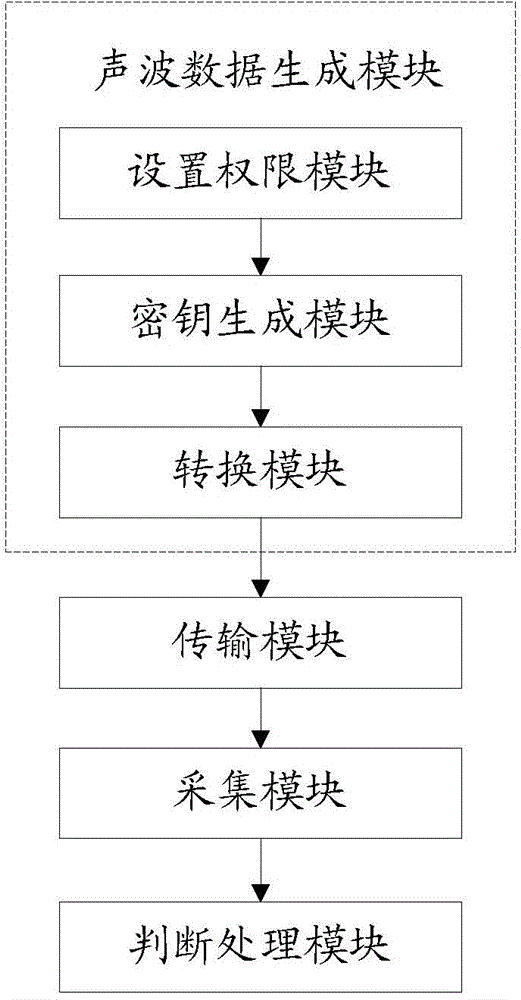
Long-distance door access control method and long-distance door access control system utilizing acoustic wave communication
An access control and sound wave technology, which is applied to user identity/authority verification and key distribution, can solve problems such as increased costs, and achieve the effects of improved security, low cost, and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0062] Example 1: The owner asks the cleaning staff to come to the house every Sunday this month to do sanitation: the access time authority is limited to Sundays, limited to 4 times, and expired;
[0063] According to the temporary access permission required by the cleaning staff (limited to 4 times on Sundays), a key is generated, and then converted into sound wave data through encoding;
[0064] The owner determines the temporary access permission information required by the cleaning staff. The permission information is on Sundays, limited to 4 times, and becomes invalid when it expires;
[0065] Then the server generates a unique random key and the permission according to the permission information of the temporary access, and saves it locally;
[0066] The server performs sound wave encoding on the key and converts it into sound wave data.
[0067] Send the sound wave data to the mobile phone of the cleaning staff;
[0068] The cleaning staff arrives at the gate and pla...
Embodiment 2
[0071] Embodiment 2: The entrance of the school dormitory is controlled from 6:00 to 22:00, and at other times, random entry and exit are not allowed;
[0072] According to the student's temporary access permission (dormitory access control 6:00~22:00), generate a key, and then convert it into sound wave data through encoding;
[0073] The building manager determines the temporary access permission information required by the students. The permission information is: dormitory access control from 6:00 to 22:00;
[0074] According to the permission information of the temporary access, the ladder machine generates a unique random key and the permission, and saves it locally;
[0075] The ladder machine performs sound wave encoding on the key and converts it into sound wave data.
[0076] Send the sound wave data to the student's tablet or mobile phone;
[0077] Students arrive at the access control at the door of the dormitory, and play the sound wave data through the player of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com