Patents
Literature
113results about How to "Difficult to access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
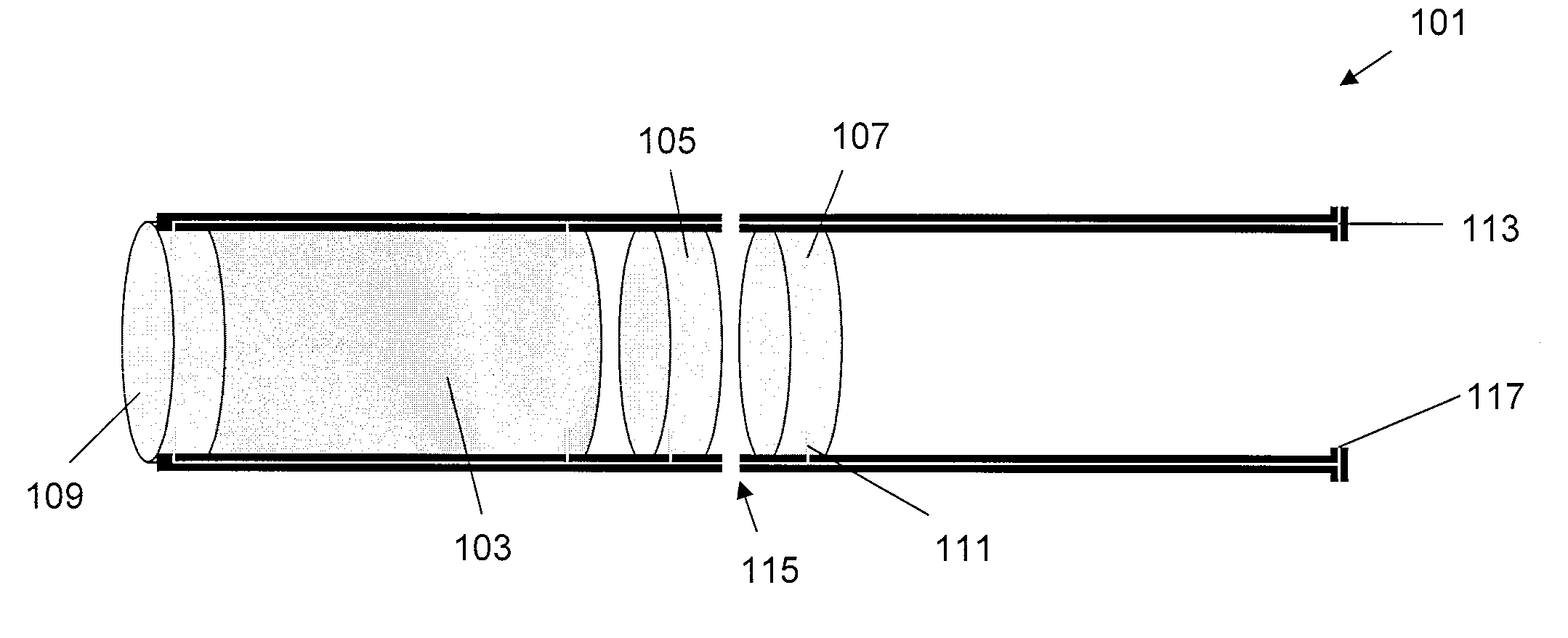
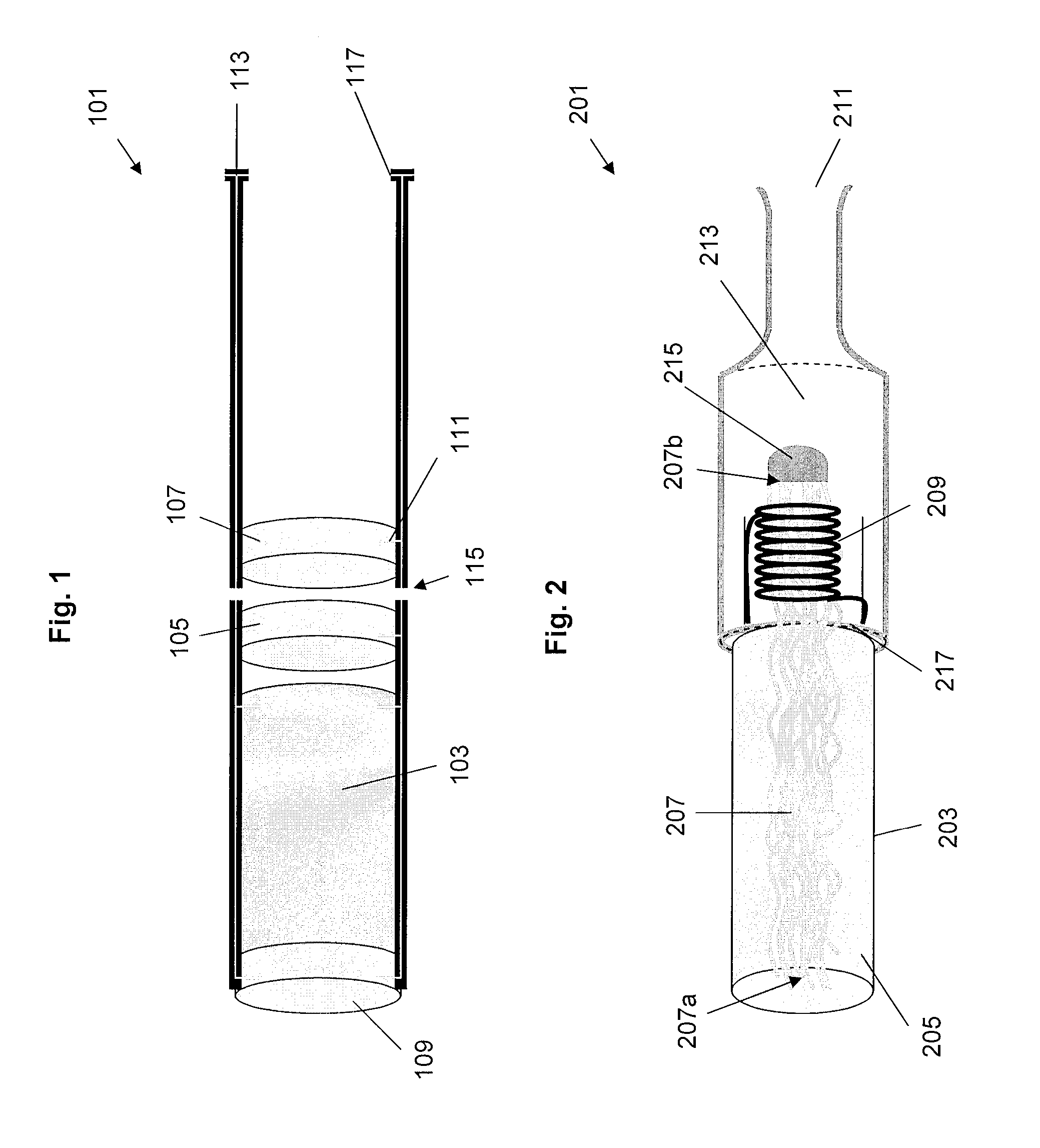
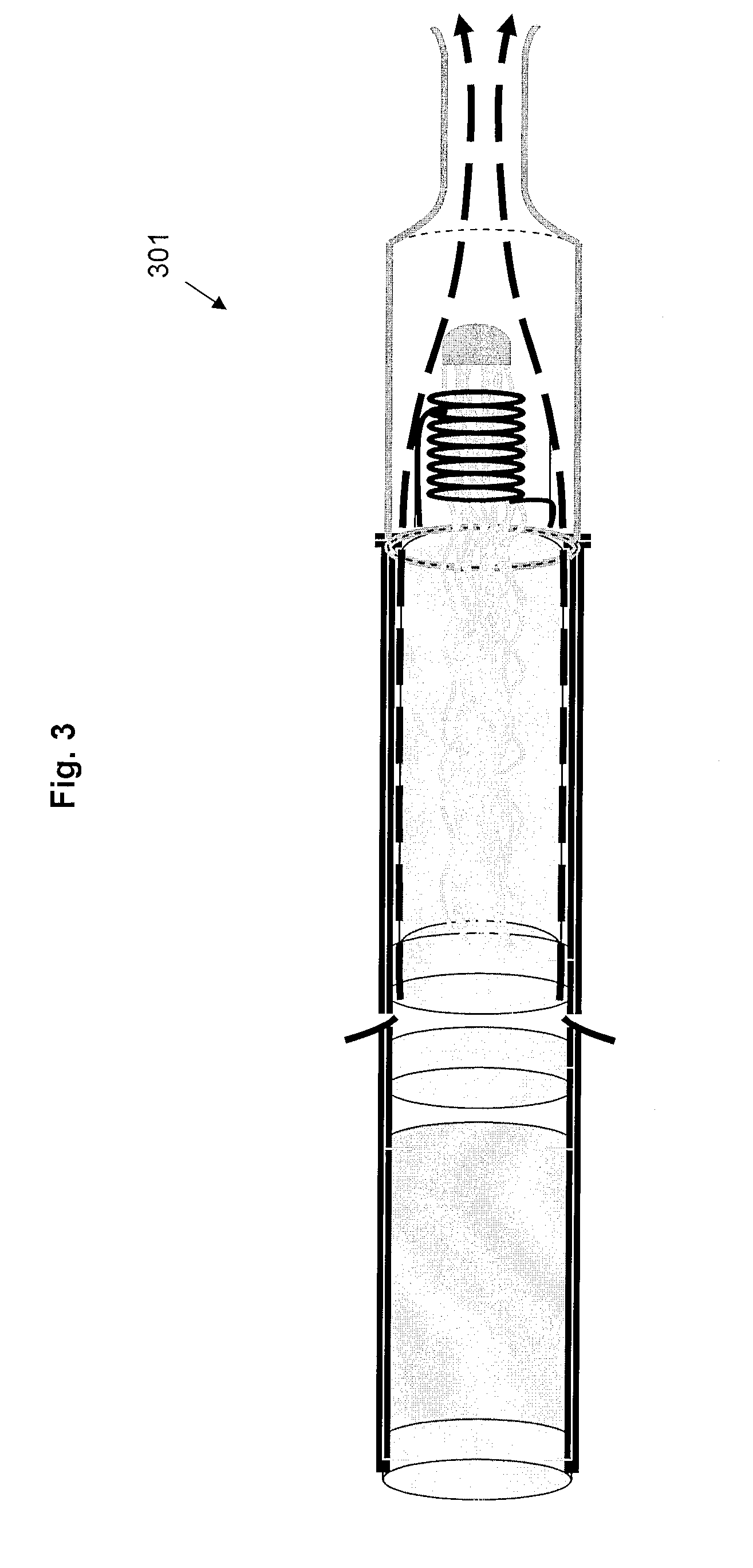
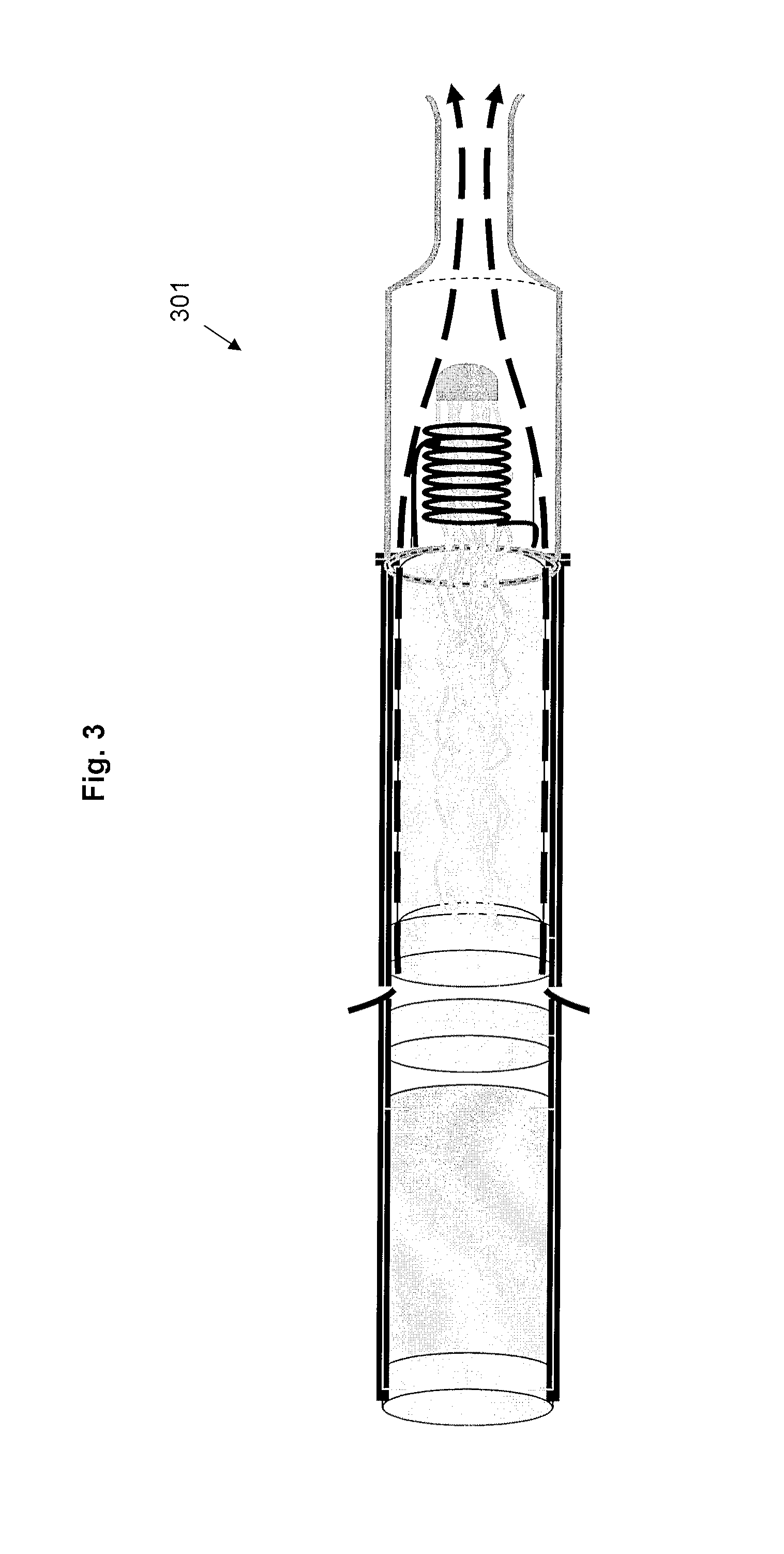
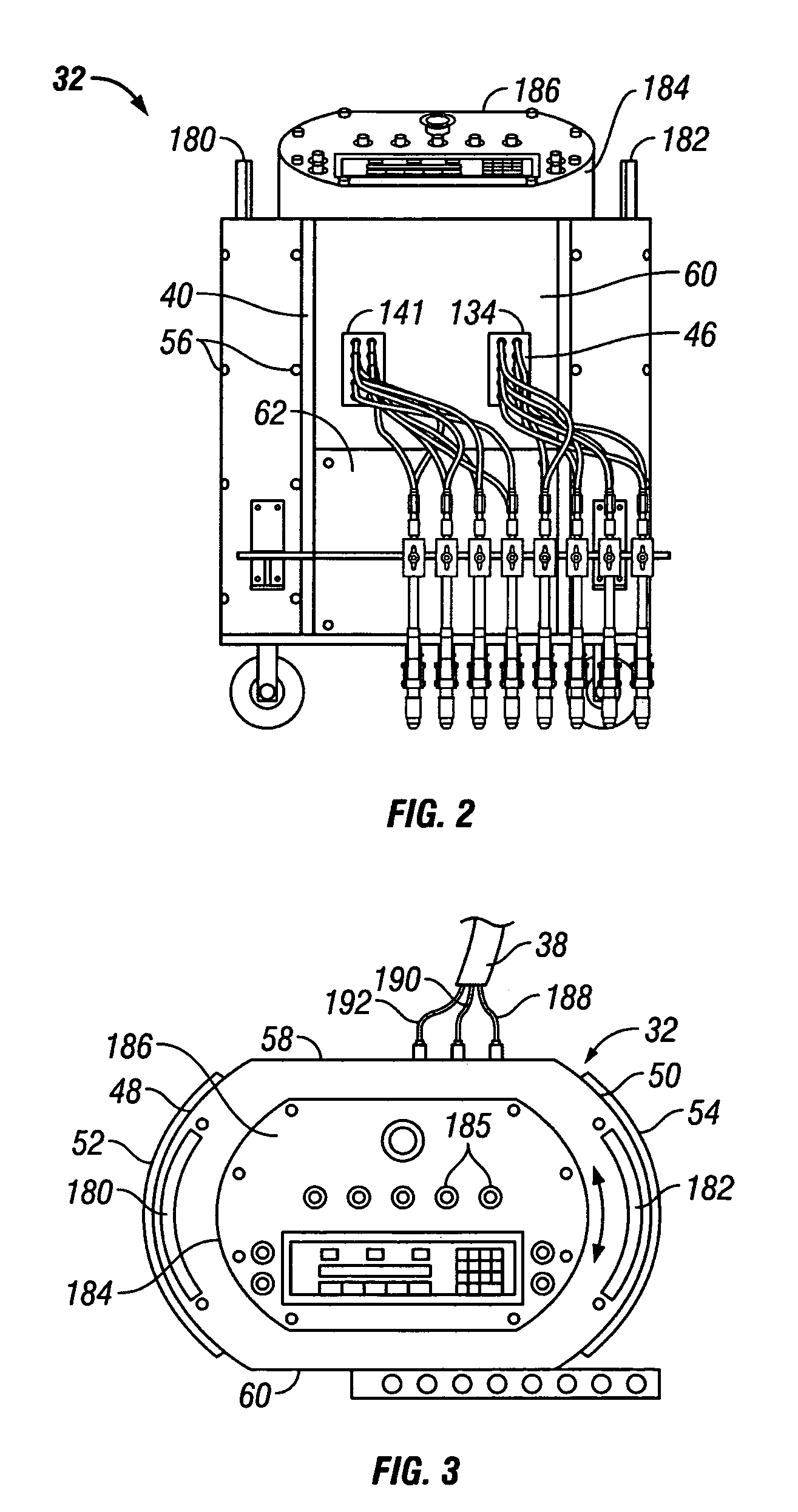
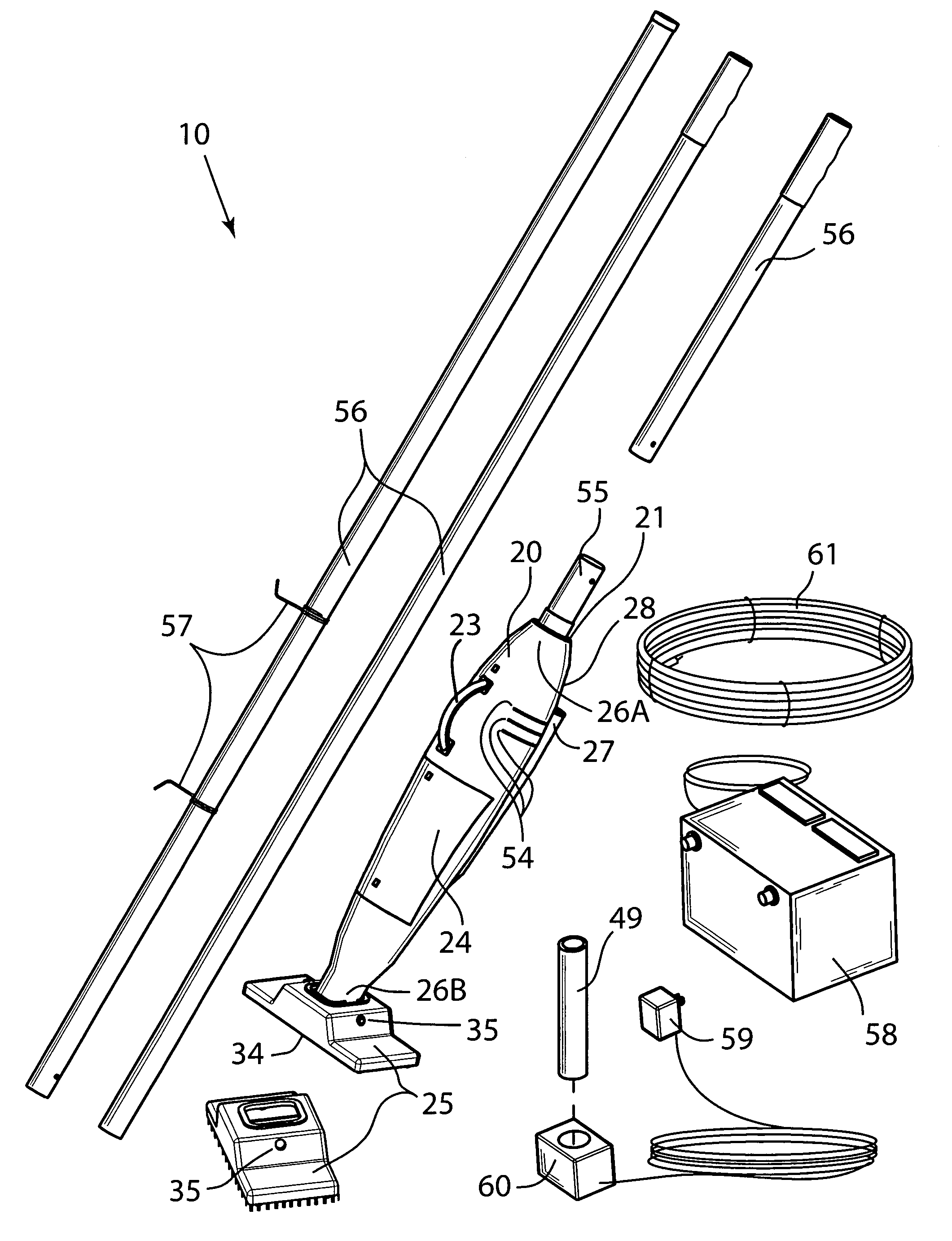
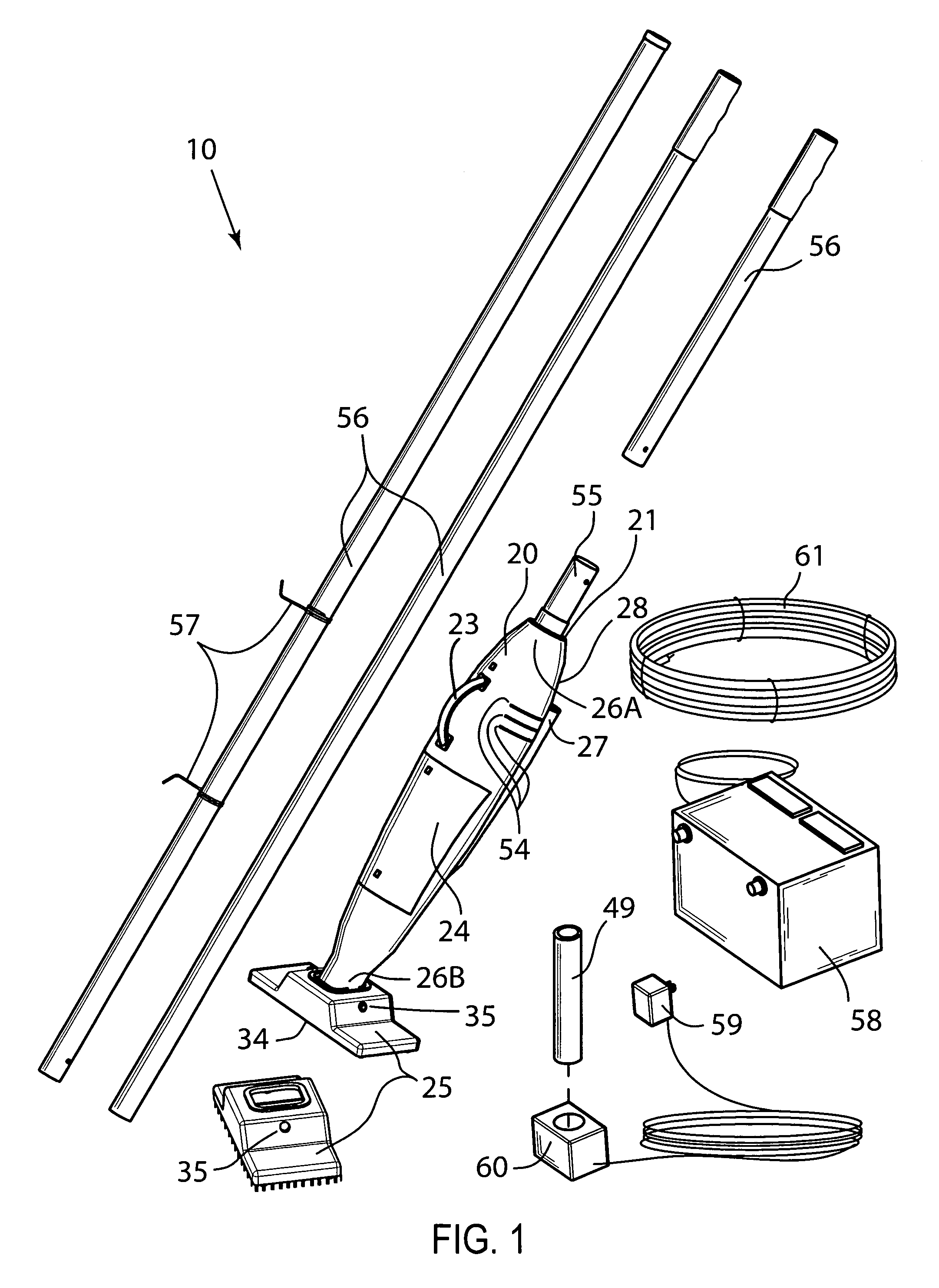
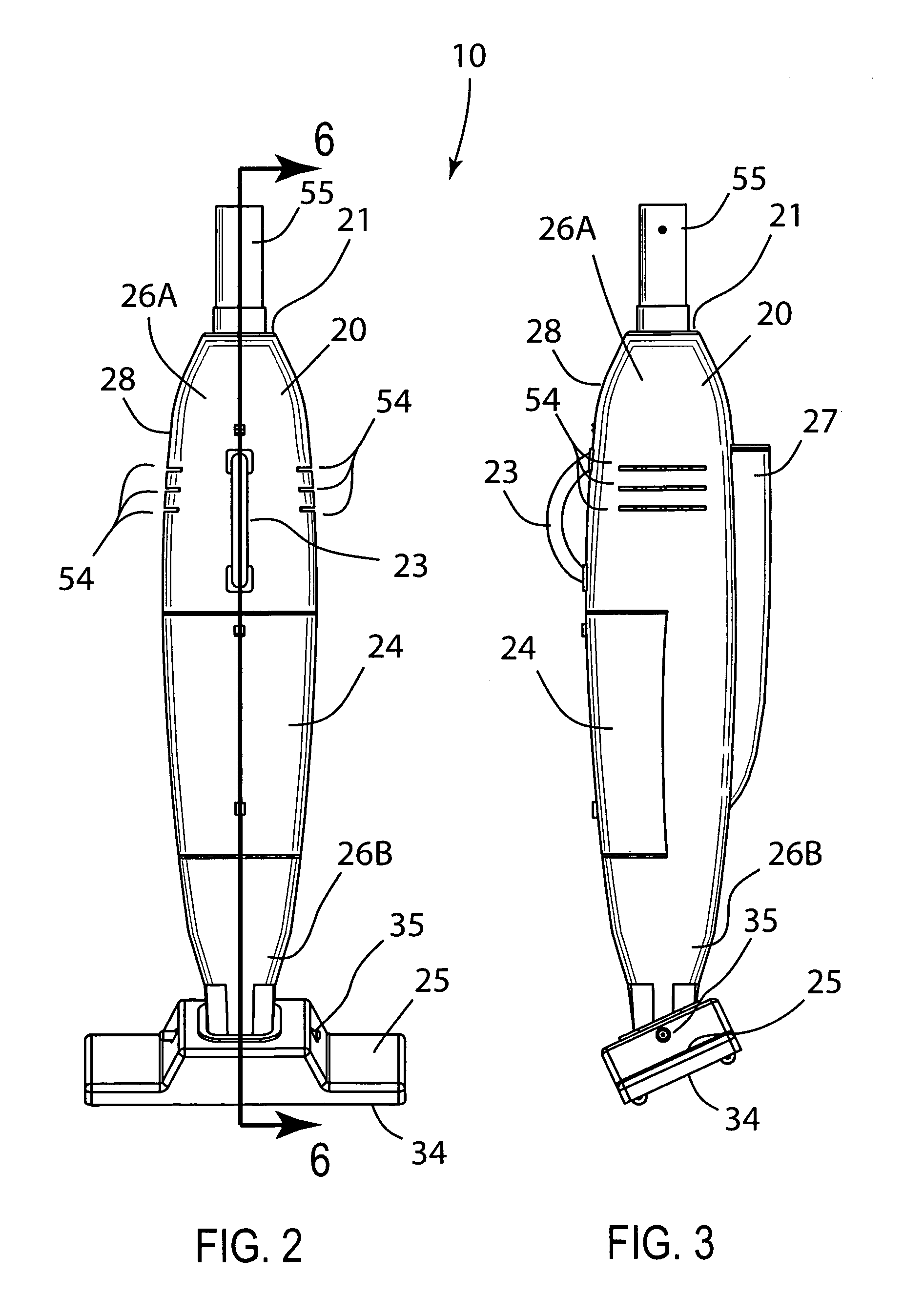
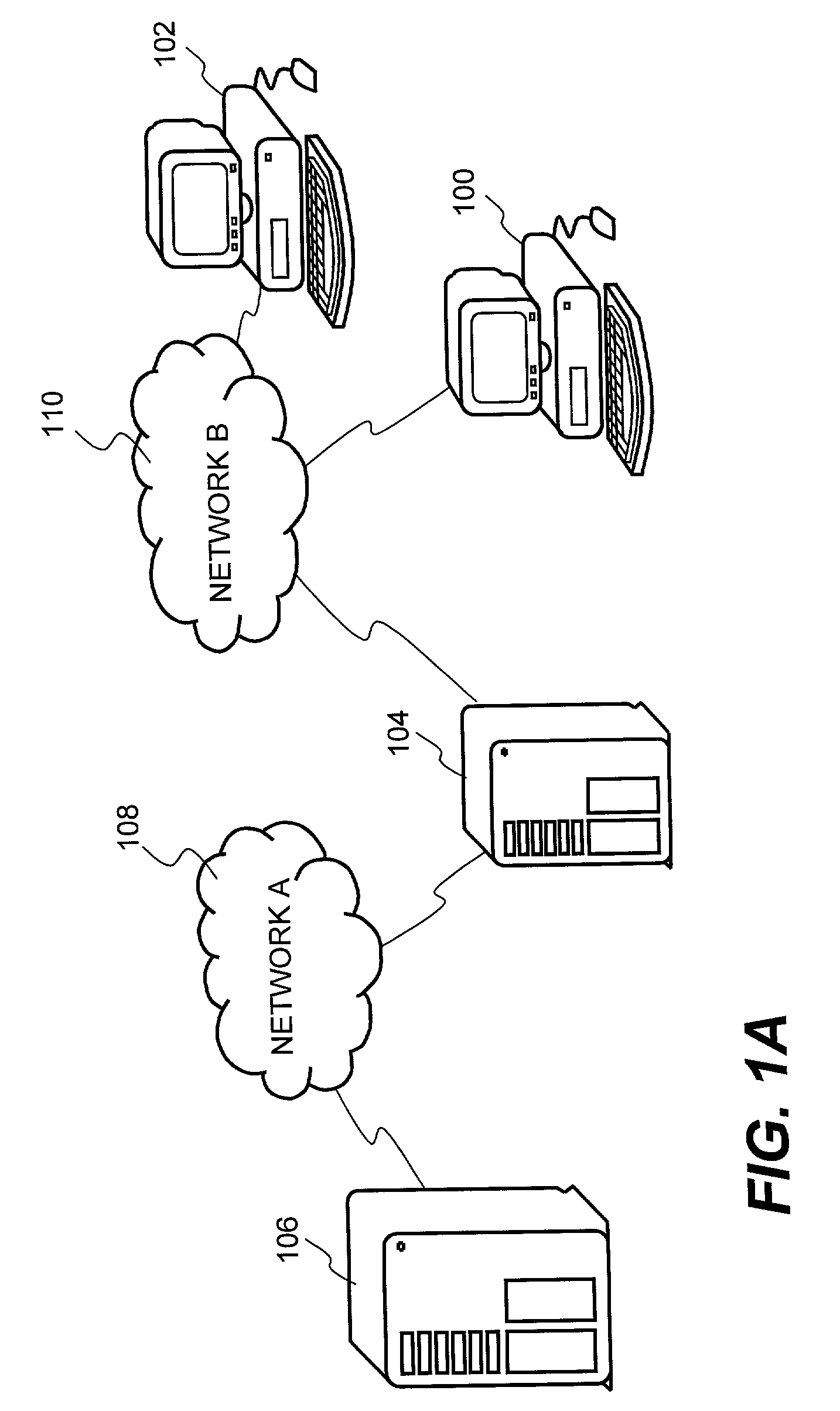
Electrically heated smoking system having a liquid storage portion
ActiveUS20090272379A1Prevent degradationSimple structureOhmic-resistance heating circuitsCoil arrangementsElectricityElectrical connection
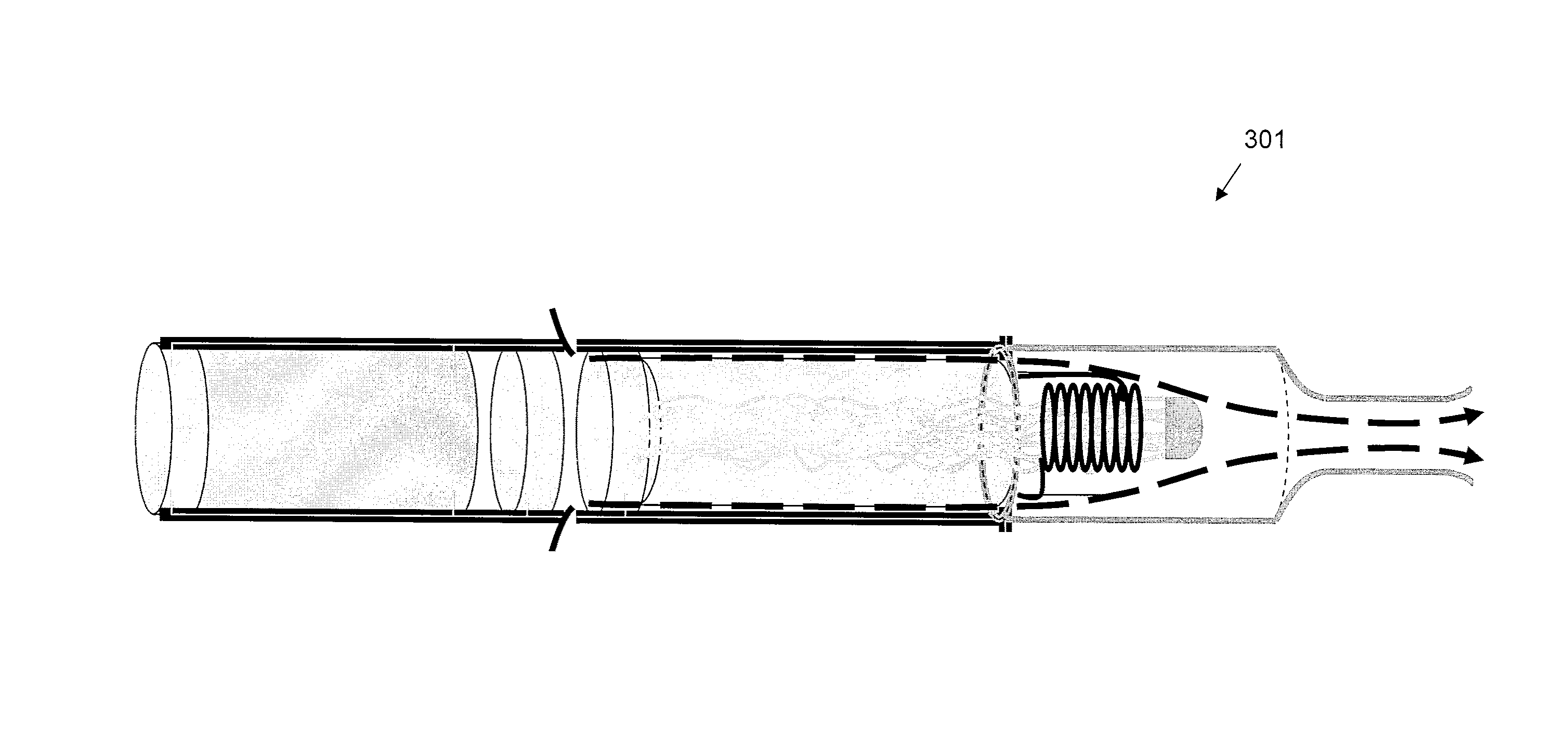
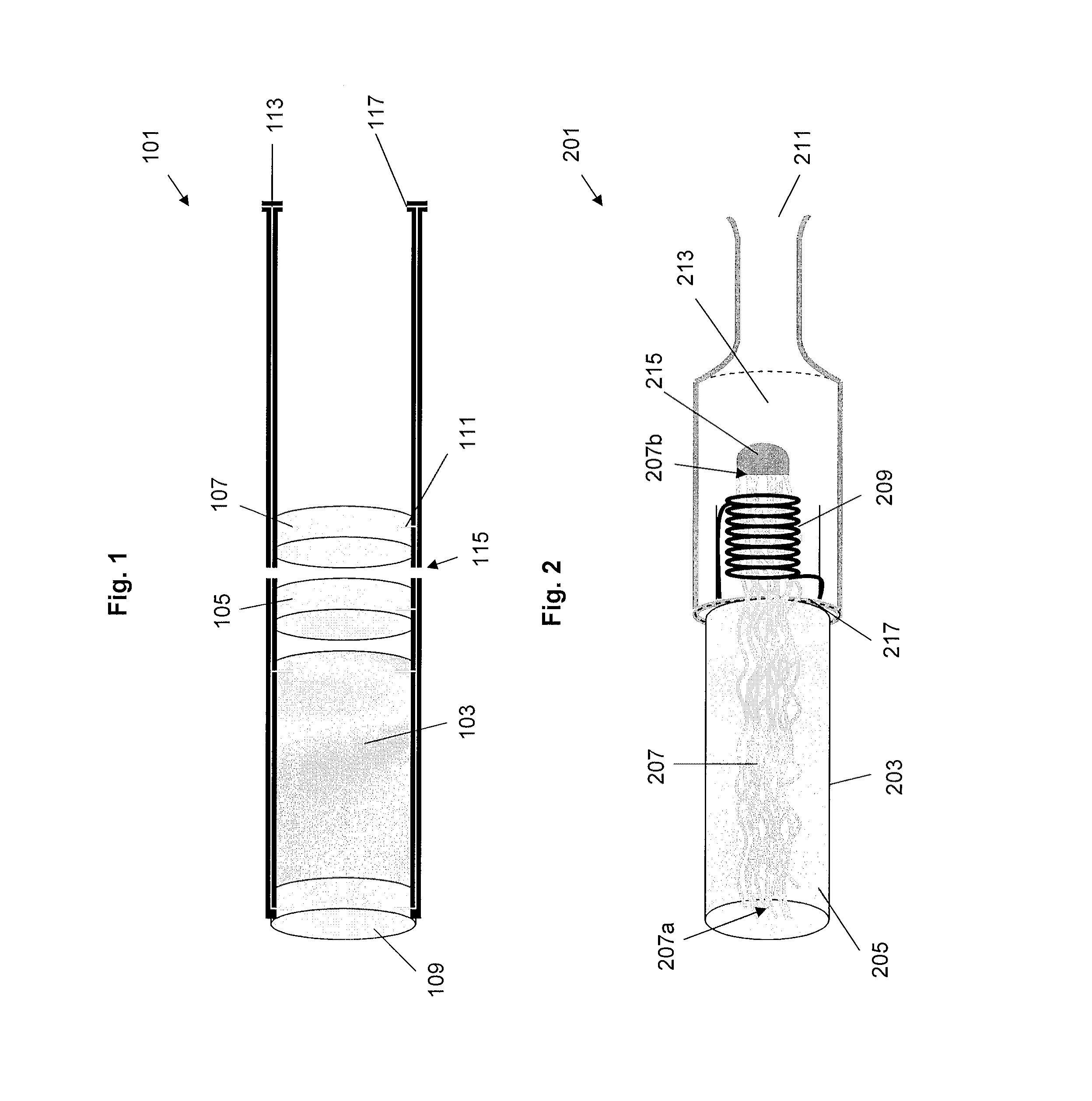
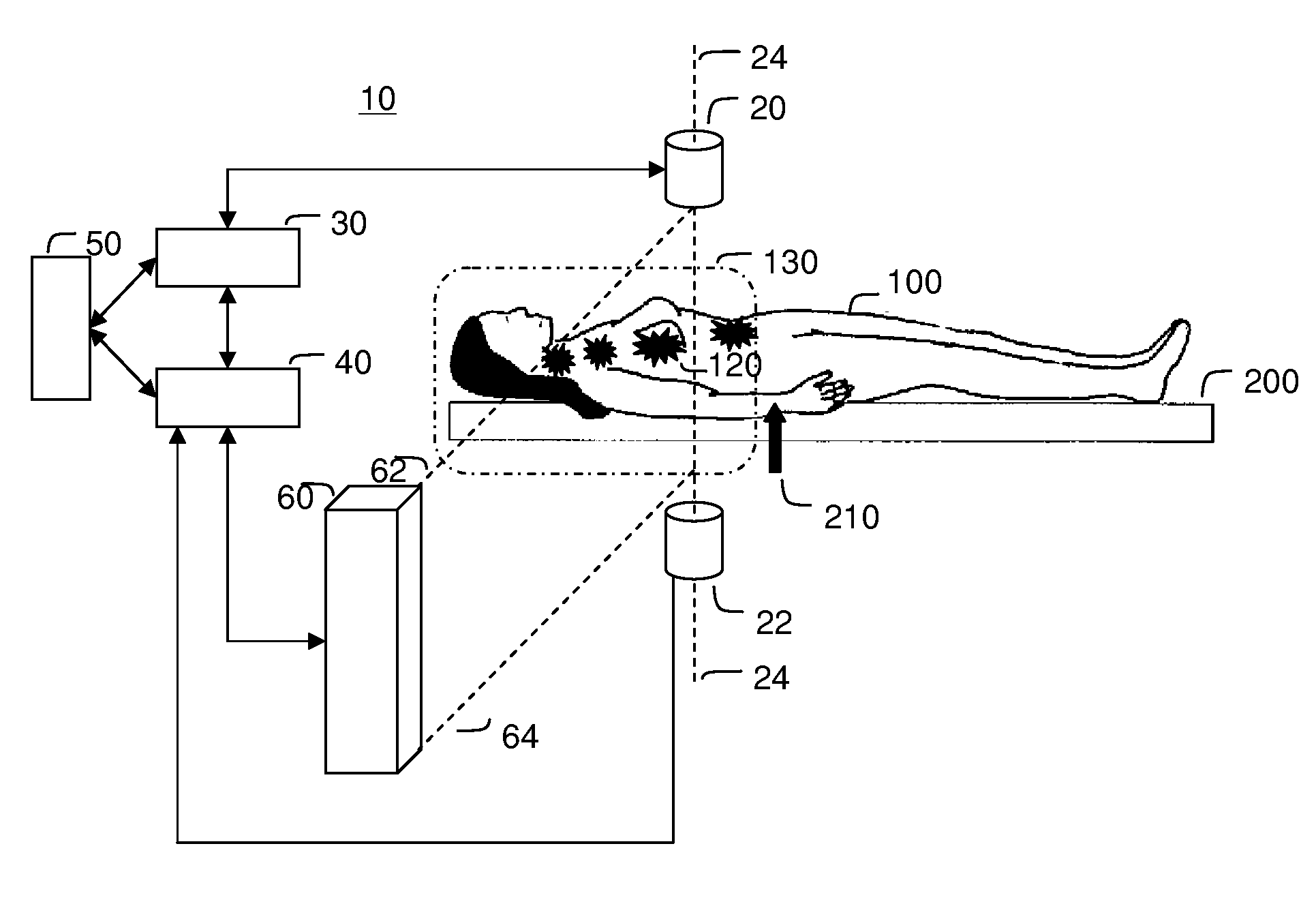
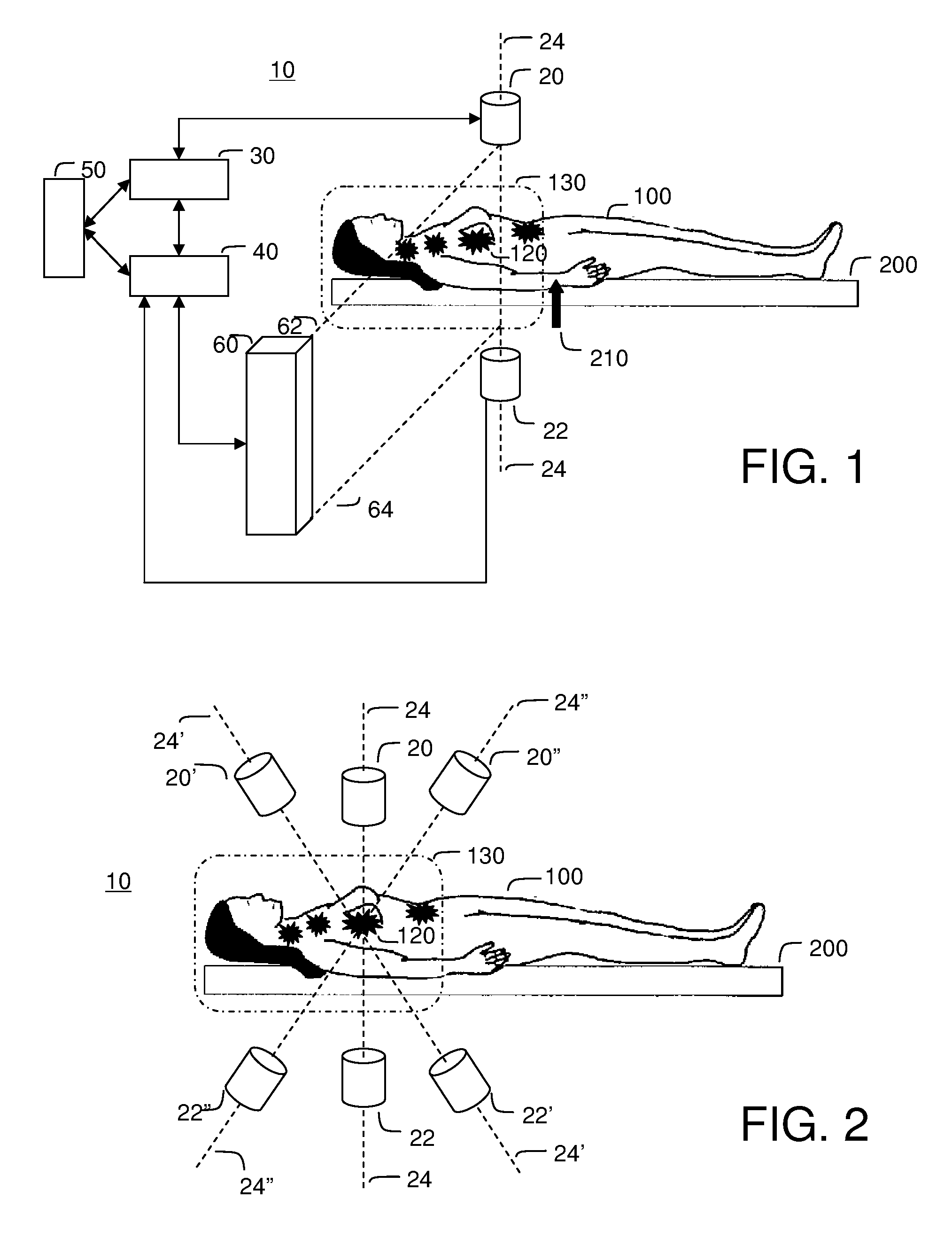
An electrically heated smoking system includes a shell and a replaceable mouthpiece. The shell includes an electric power supply and electric circuitry. The mouthpiece includes a liquid storage portion and a capillary wick having a first end and a second end. The first end of the wick extends into the liquid storage portion for contact with liquid therein. The mouthpiece also includes a heating element for heating the second end of the capillary wick, an air outlet, and an aerosol forming chamber between the second end of the capillary wick and the air outlet. When the shell and mouthpiece are engaged or connected, the heating element is in electrical connection with the power supply via the circuitry, and a flowpath for air is defined from at least one air inlet to the air outlet via the aerosol forming chamber. In use, liquid is transferred from the liquid storage portion towards the heating element by capillary action in the wick. Liquid at the second end of the capillary wick is vaporized by the heating element. The supersaturated vapor created, is mixed and carried in the air flow from the at least one air inlet to the aerosol forming chamber. In the aerosol forming chamber, the vapor condenses to form an aerosol, which is carried towards the air outlet.
Owner:PHILIP MORRIS USA INC
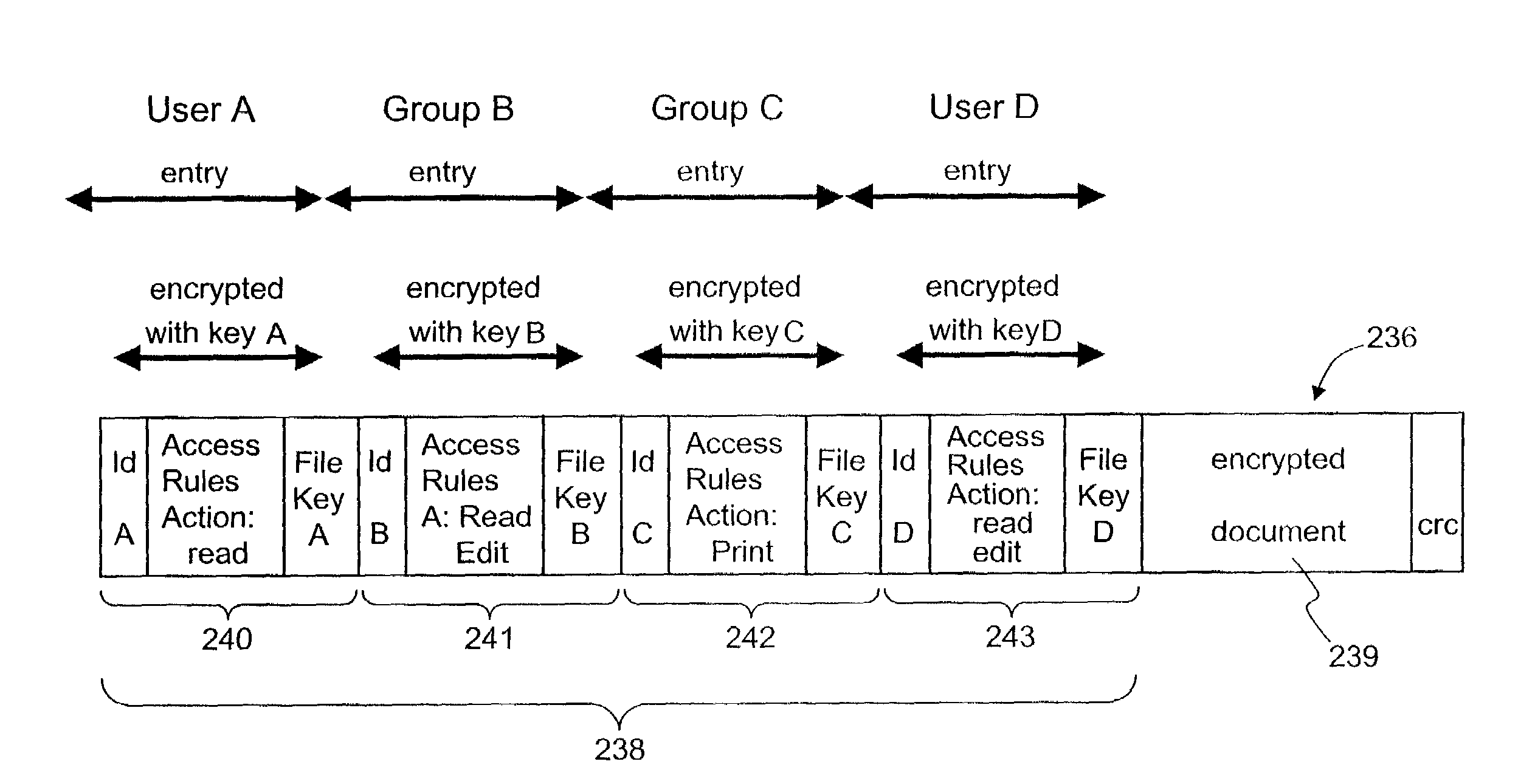
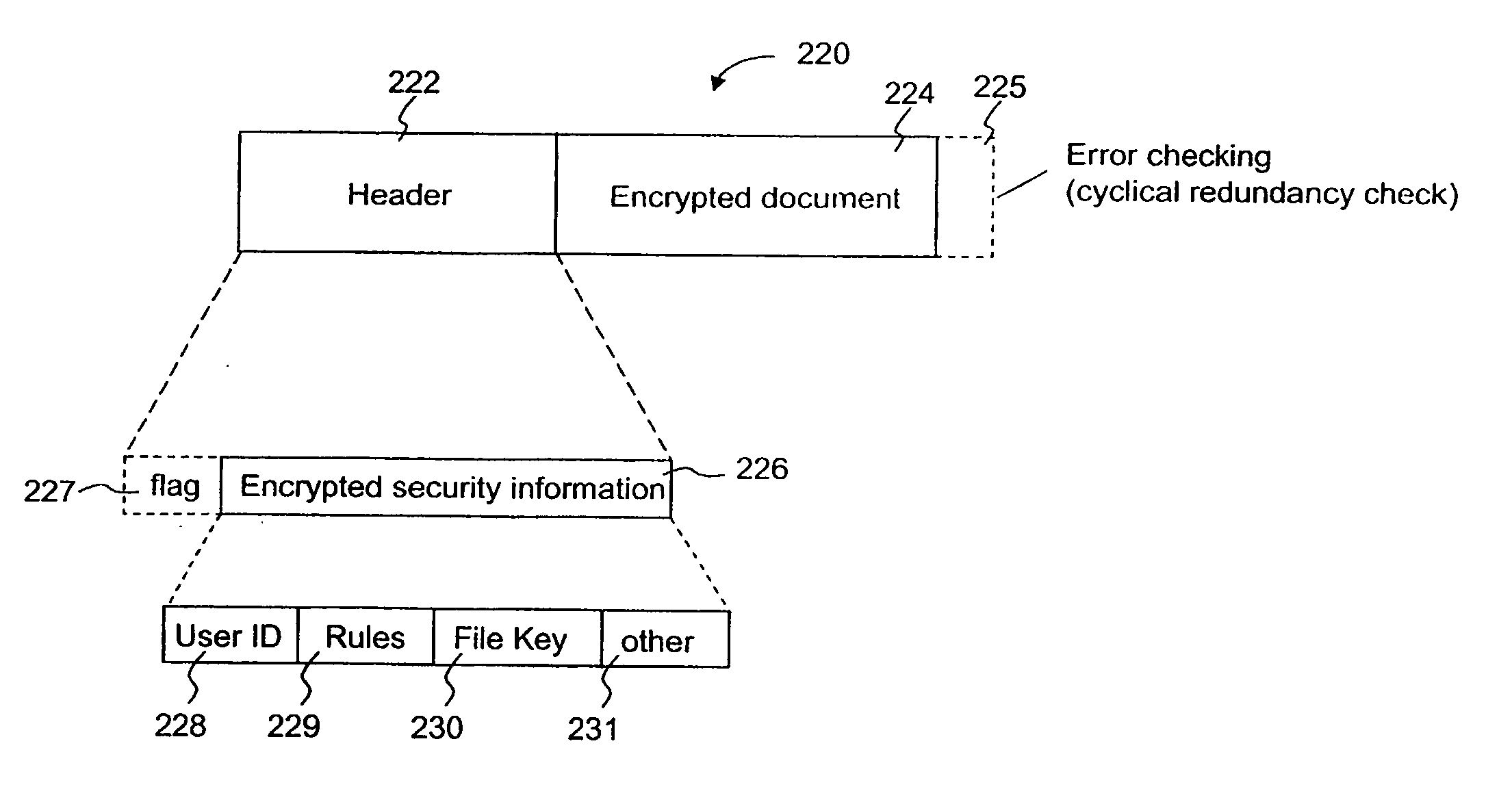
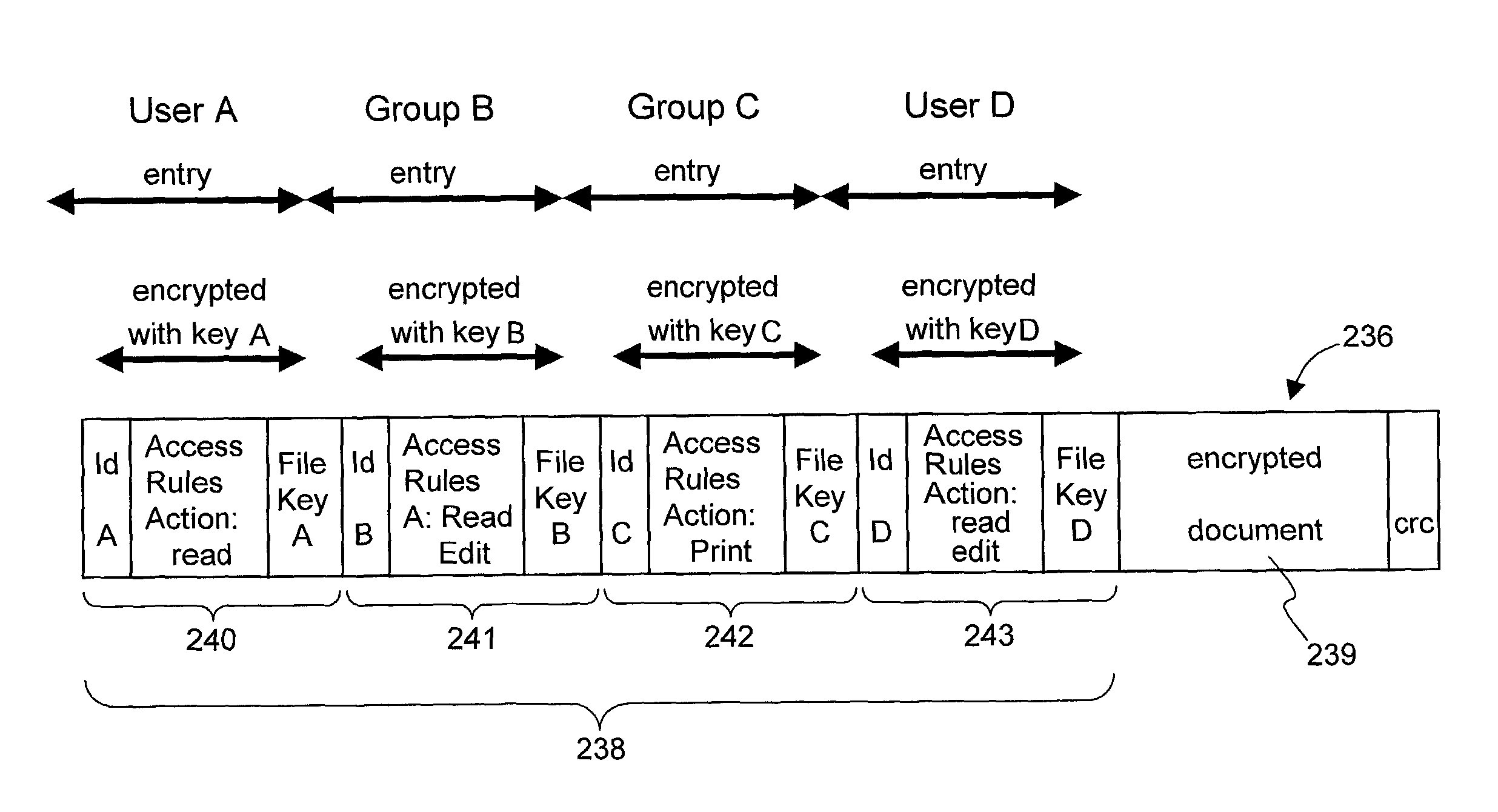
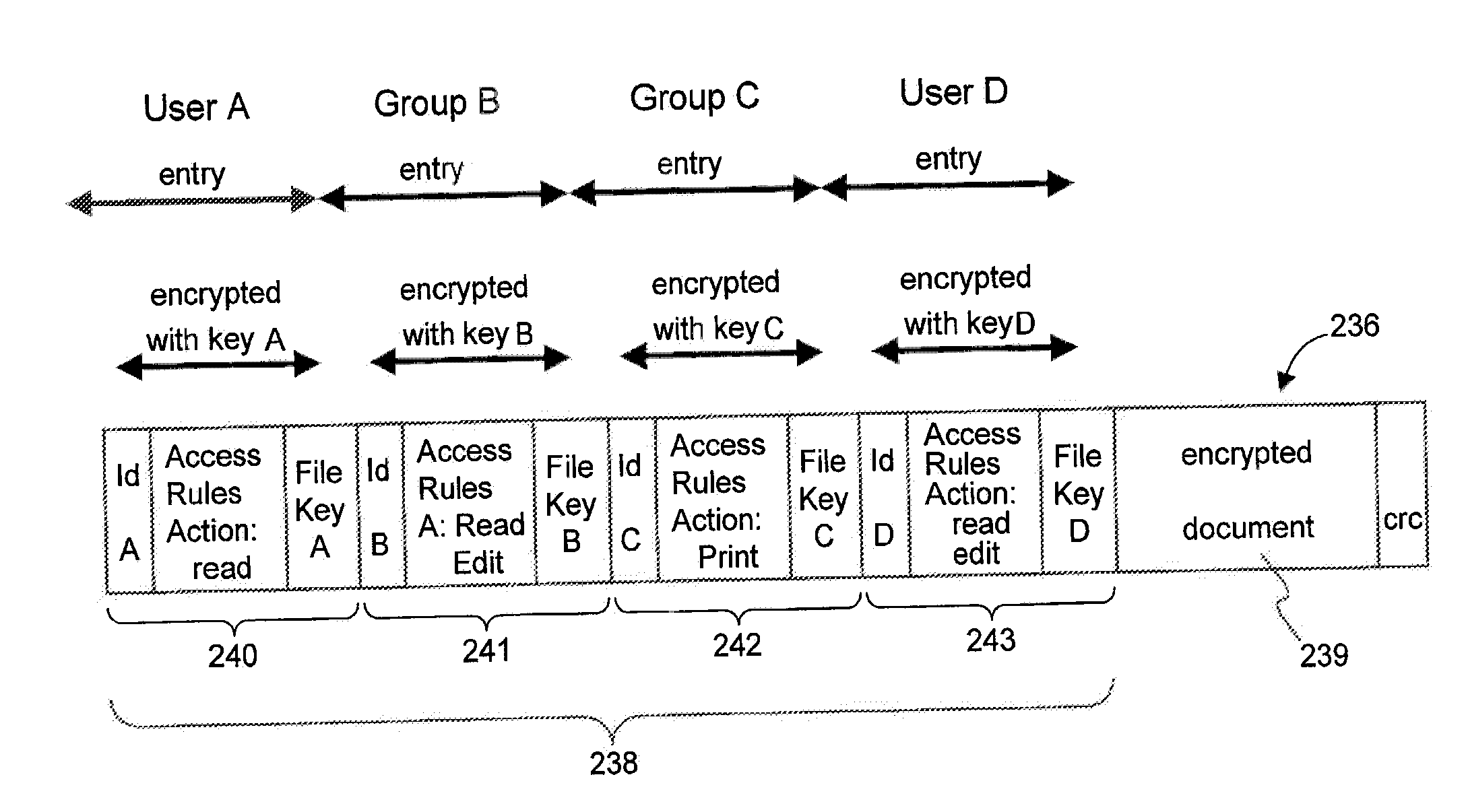
Secured data format for access control
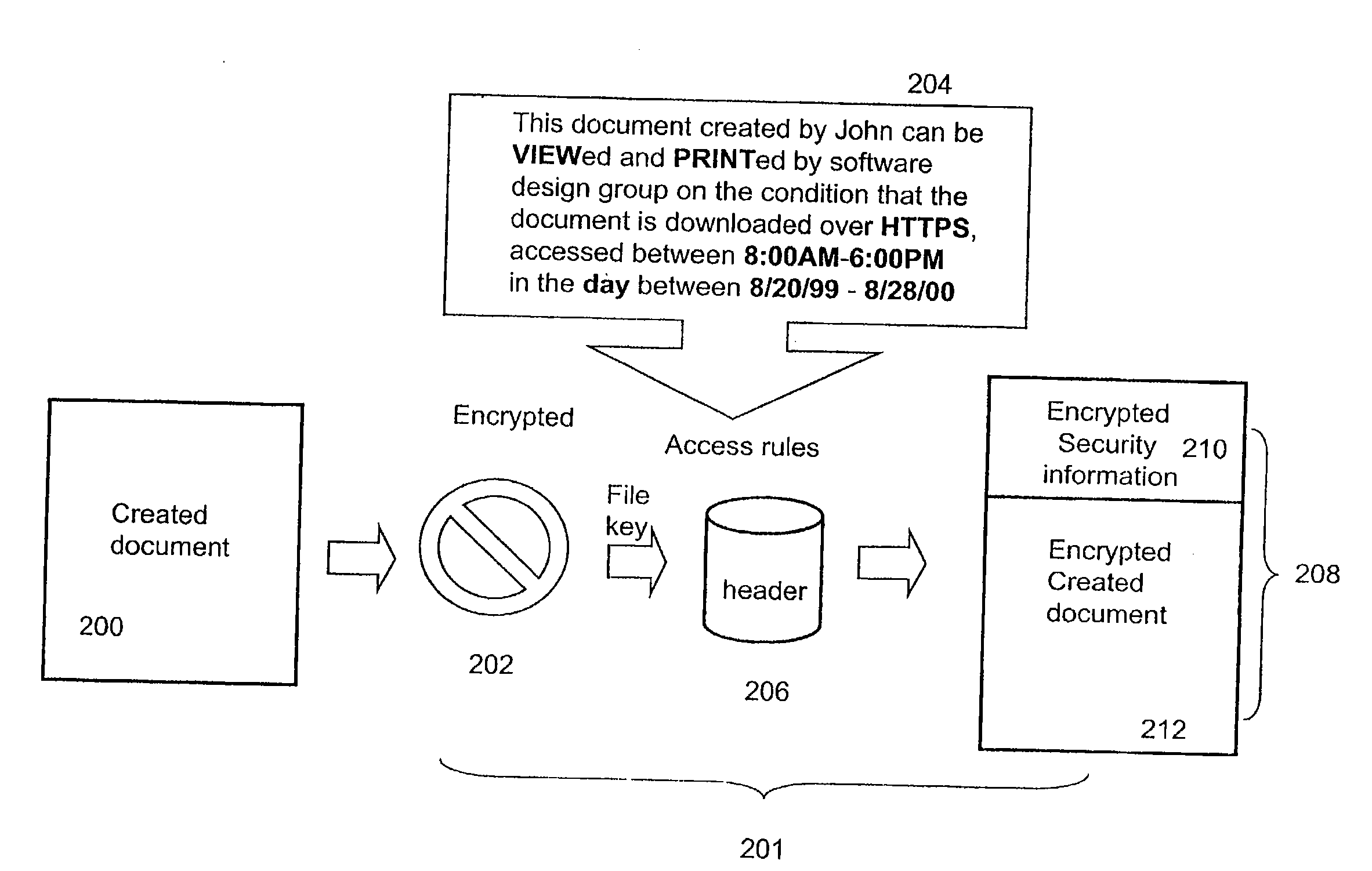
ActiveUS7380120B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationMedia access controlDocumentation
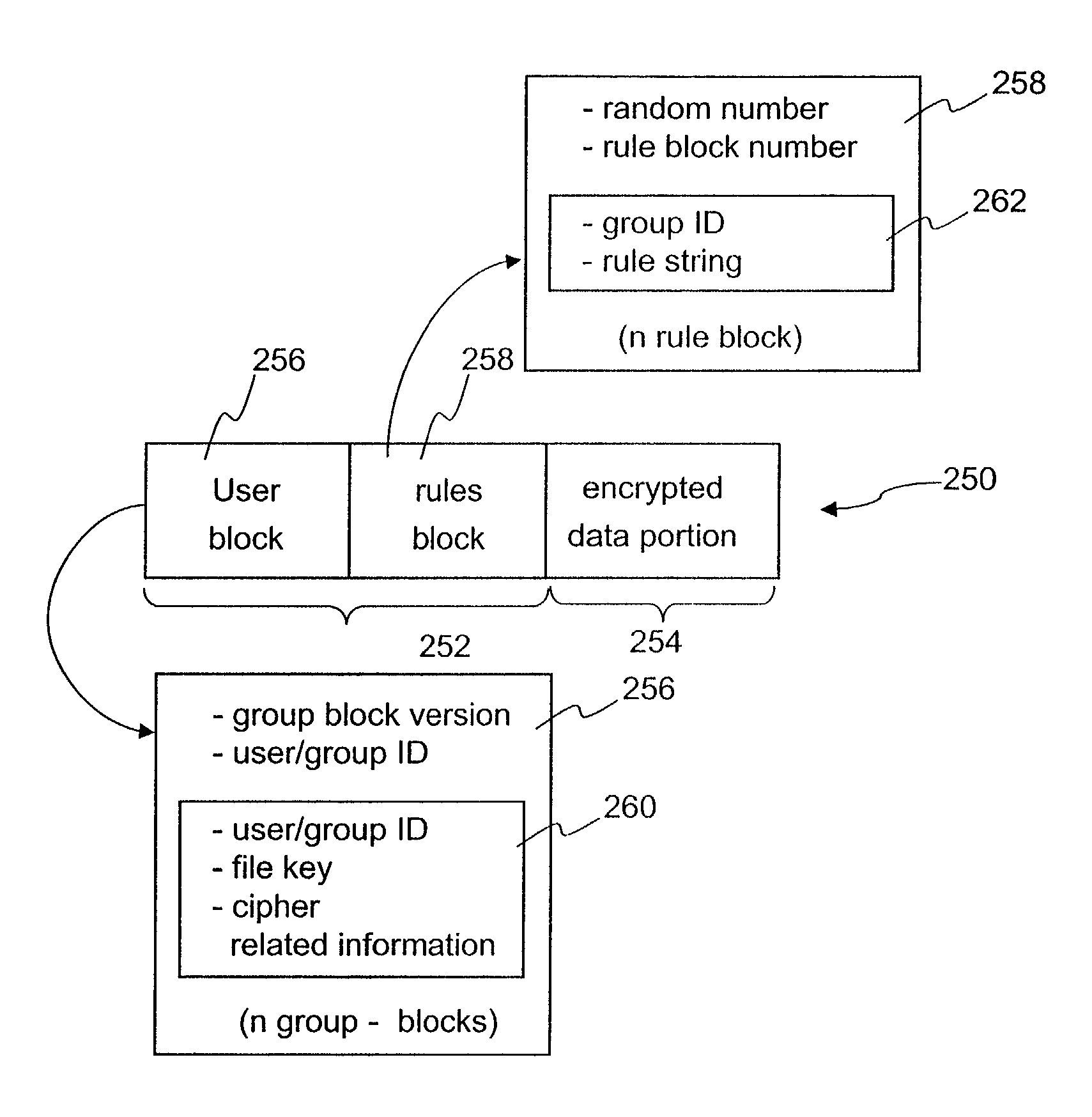
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
Electrically heated smoking system having a liquid storage portion
ActiveUS8794231B2Avoid wastingReduce riskOhmic-resistance heating circuitsCigar manufactureElectricityElectrical connection
An electrically heated smoking system includes a shell and a replaceable mouthpiece. The shell includes an electric power supply and electric circuitry. The mouthpiece includes a liquid storage portion and a capillary wick having a first end and a second end. The first end of the wick extends into the liquid storage portion for contact with liquid therein. The mouthpiece also includes a heating element for heating the second end of the capillary wick, an air outlet, and an aerosol forming chamber between the second end of the capillary wick and the air outlet. When the shell and mouthpiece are engaged or connected, the heating element is in electrical connection with the power supply via the circuitry, and a flowpath for air is defined from at least one air inlet to the air outlet via the aerosol forming chamber. In use, liquid is transferred from the liquid storage portion towards the heating element by capillary action in the wick. Liquid at the second end of the capillary wick is vaporized by the heating element. The supersaturated vapor created, is mixed and carried in the air flow from the at least one air inlet to the aerosol forming chamber. In the aerosol forming chamber, the vapor condenses to form an aerosol, which is carried towards the air outlet.
Owner:PHILIP MORRIS USA INC
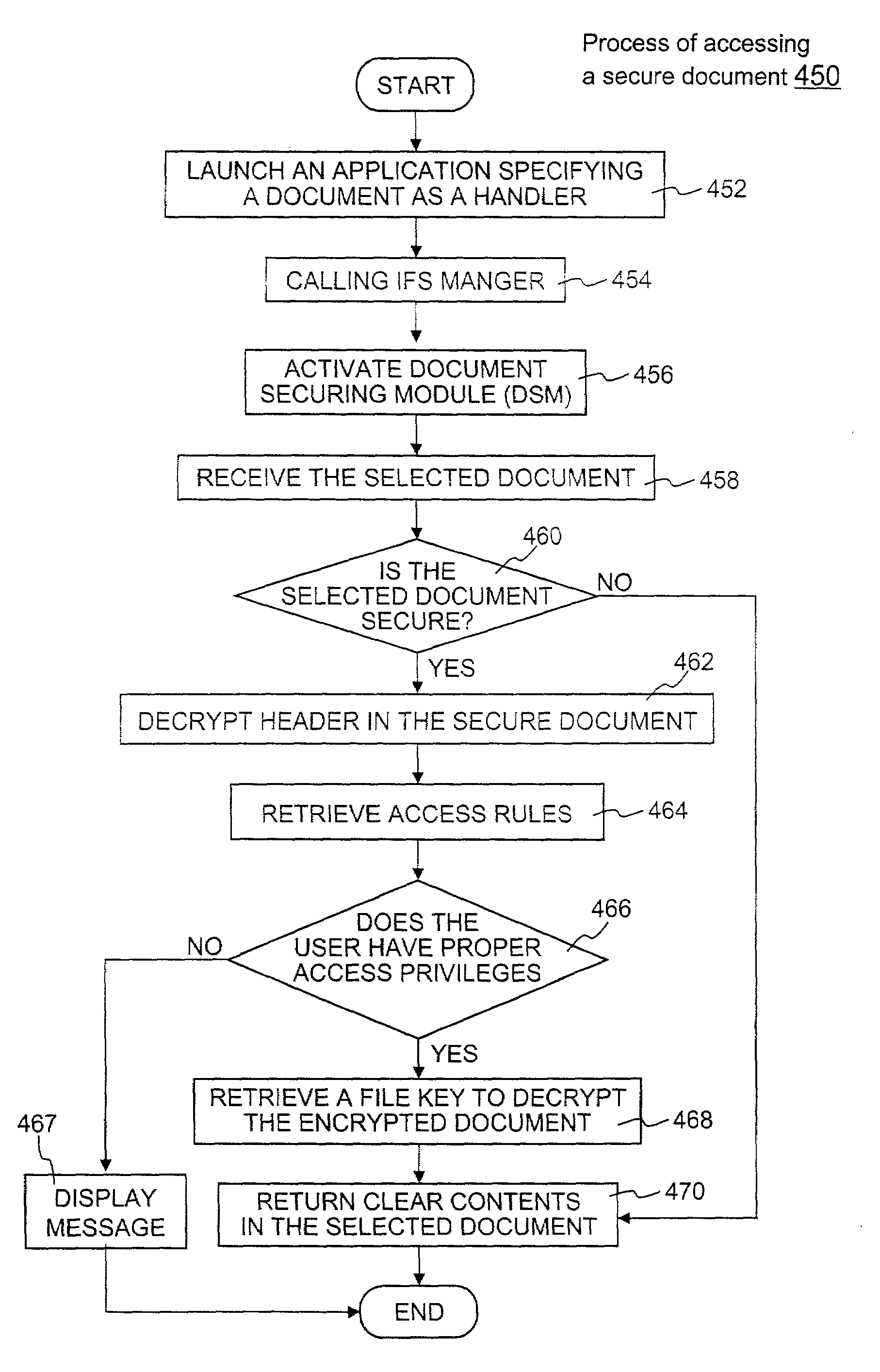
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
Methods and systems for providing access control to secured data
ActiveUS20090100268A1Ensures dependabilityEnsure reliabilityDigital data processing detailsUser identity/authority verificationEngineeringEncryption decryption
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
Method and architecture for providing pervasive security to digital assets
ActiveUS7260555B2Facilitate access control managementGood synchronizationKey distribution for secure communicationDigital data processing detailsDocumentationSoftware agent
Techniques for providing pervasive security to digital assets are disclosed. According to one aspect of the techniques, a server is configured to provide access control (AC) management for a user (e.g., a single user, a group of users, software agents or devices) with a need to access secured data. Within the server module, various access rules for the secured data and / or access privileges for the user can be created, updated and managed so that the user with the proper access privileges can access the secured documents if granted by the corresponding access rules in the secured data.
Owner:INTELLECTUAL VENTURES I LLC
Methods and systems for providing access control to electronic data
InactiveUS20080034205A1Ensures dependability and reliability and scalabilityEfficient executionKey distribution for secure communicationDigital data processing detailsDocumentationSoftware agent
Techniques for providing pervasive security to digital assets are disclosed. According to one aspect of the techniques, a server is configured to provide access control (AC) management for a user (e.g., a single user, a group of users, software agents or devices) with a need to access secured data. Within the server module, various access rules for the secured data and / or access privileges for the user can be created, updated, and managed so that the user with the proper access privileges can access the secured documents if granted by the corresponding access rules in the secured data.
Owner:INTELLECTUAL VENTURES I LLC
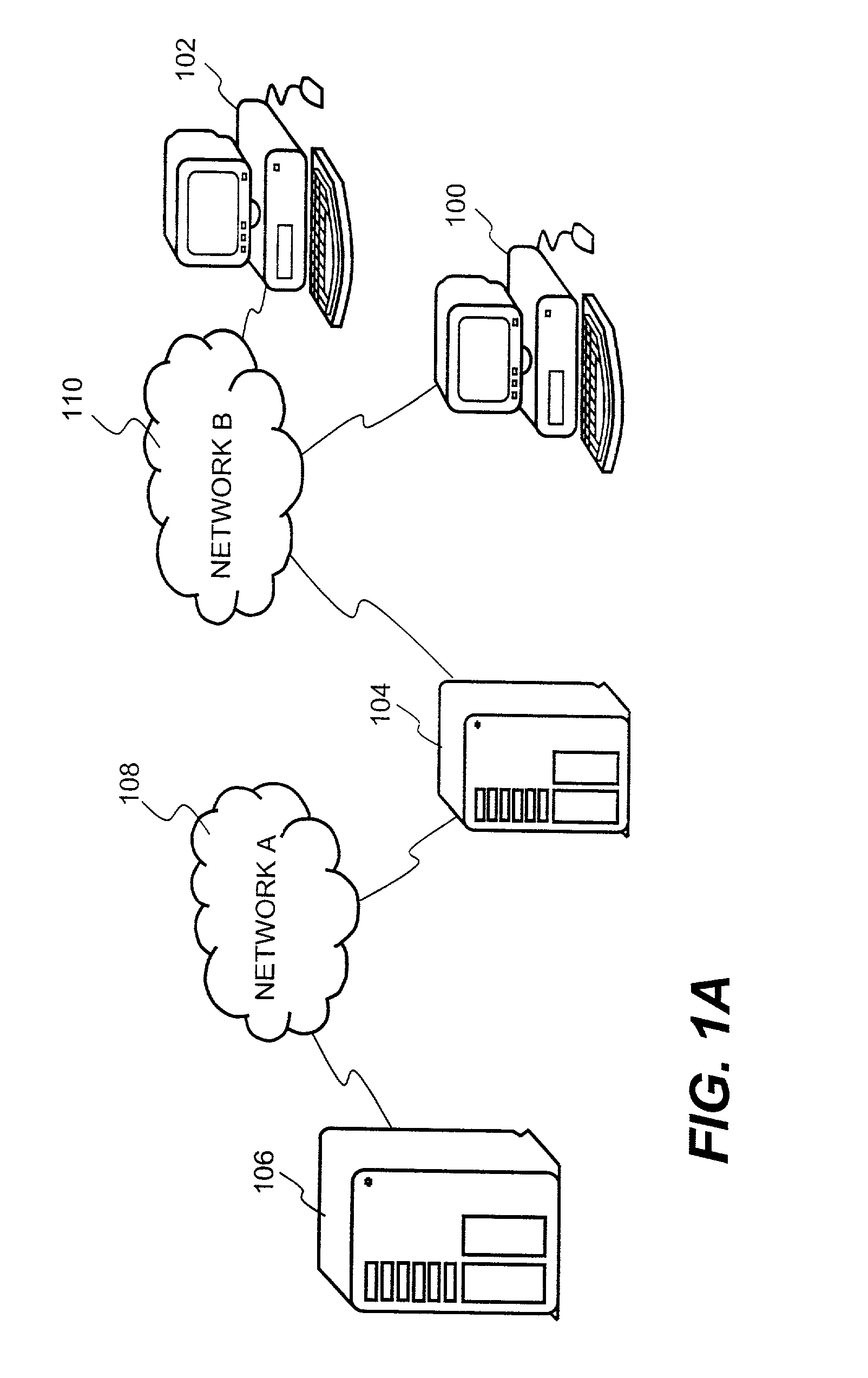
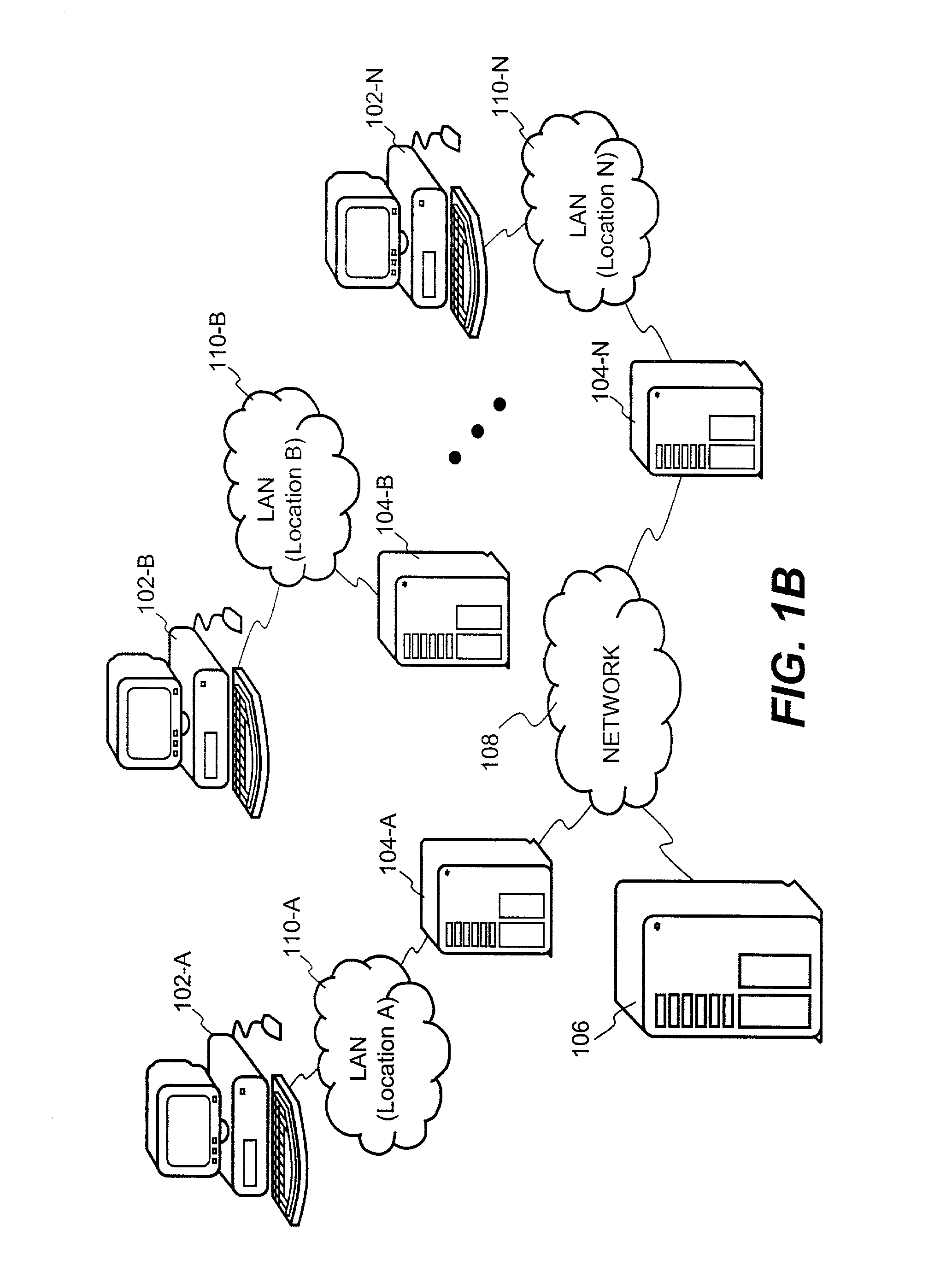
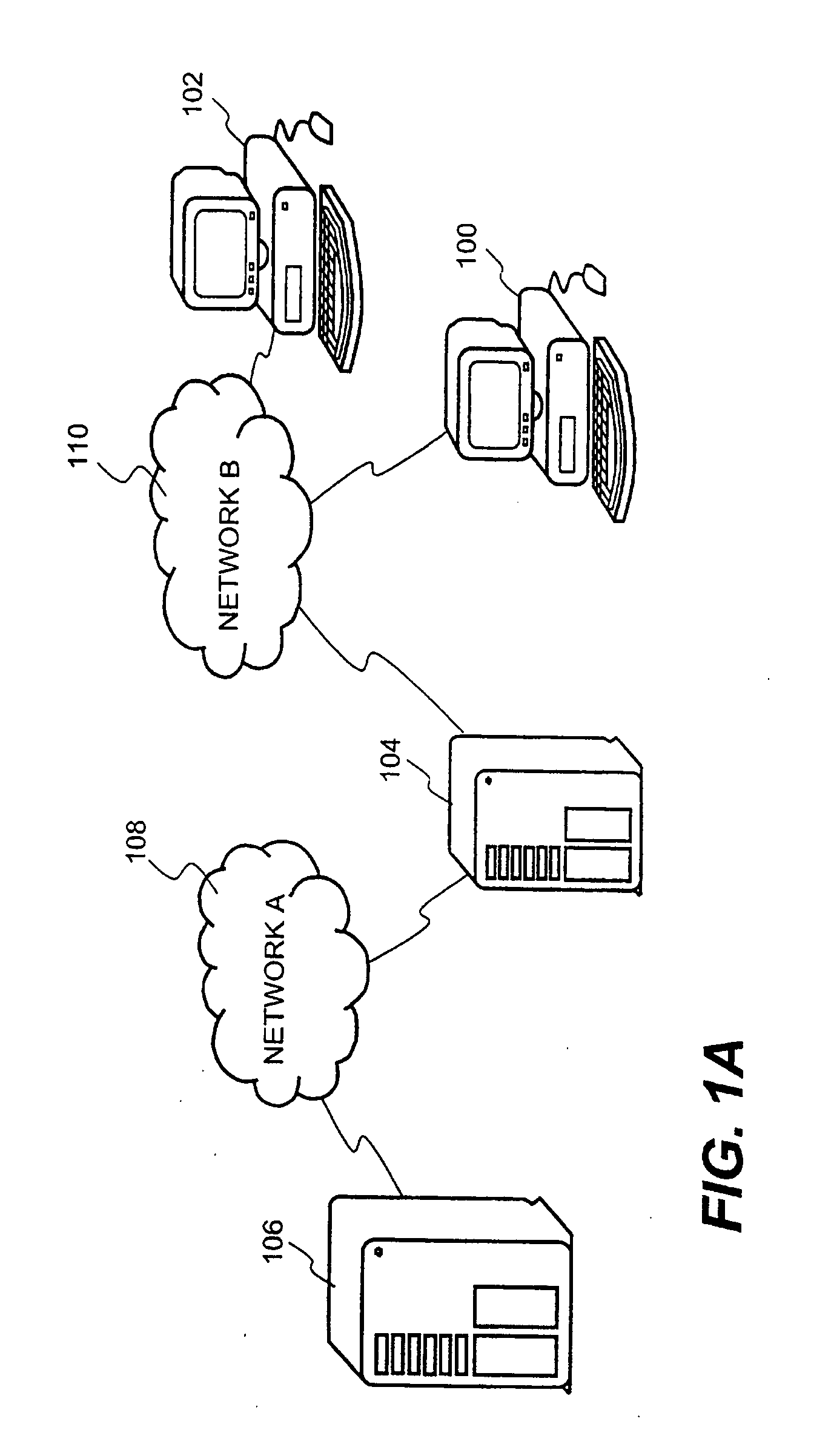
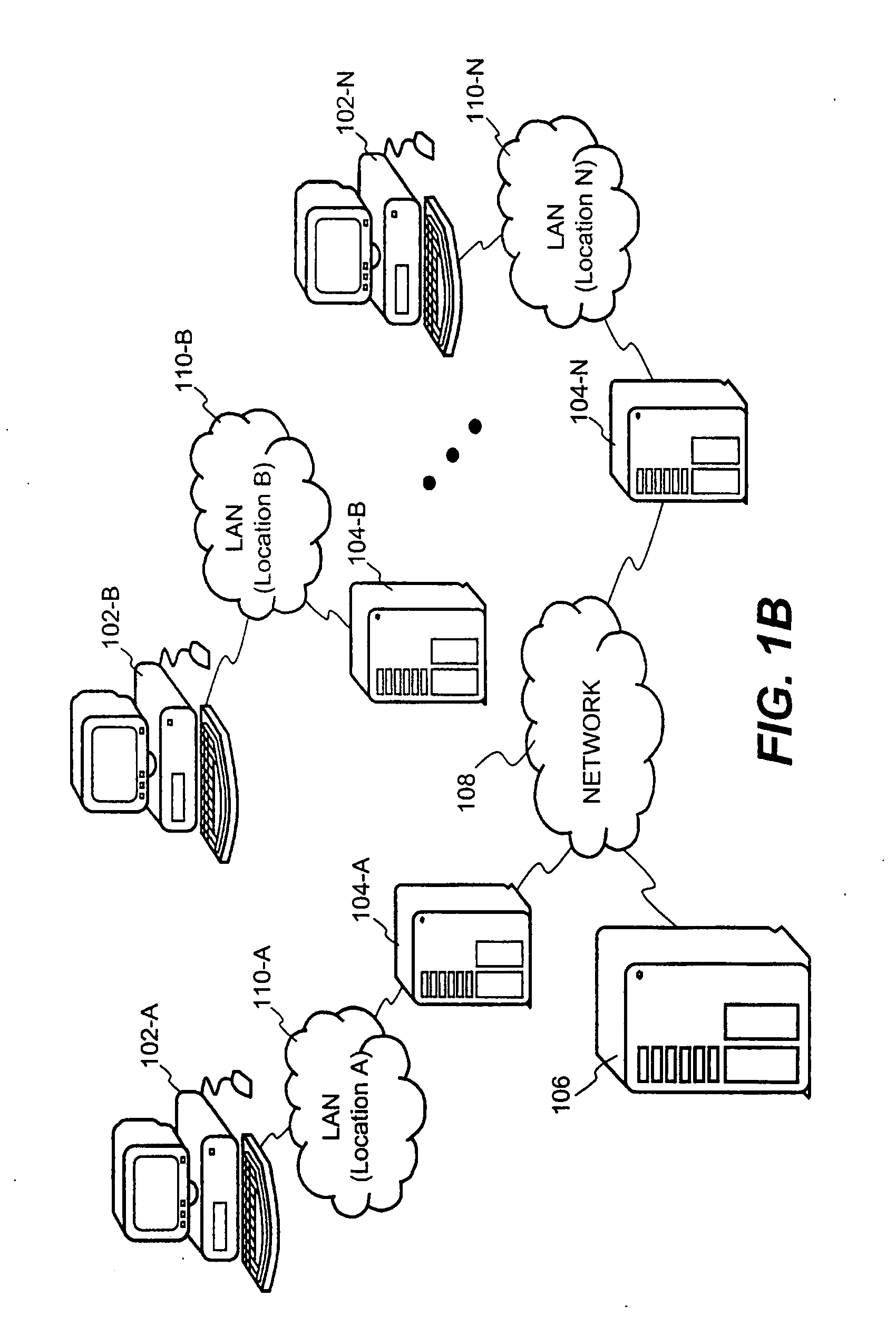
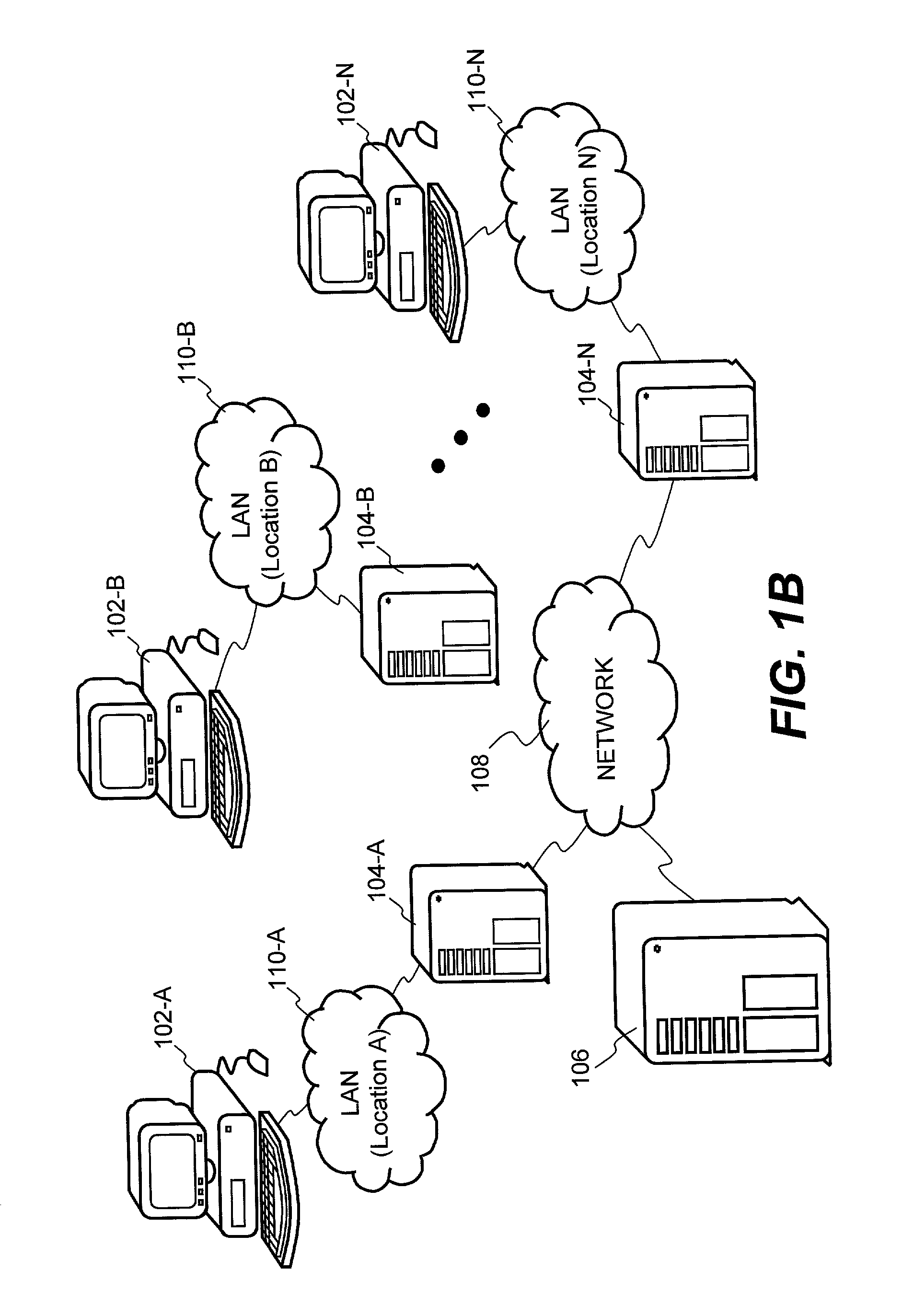
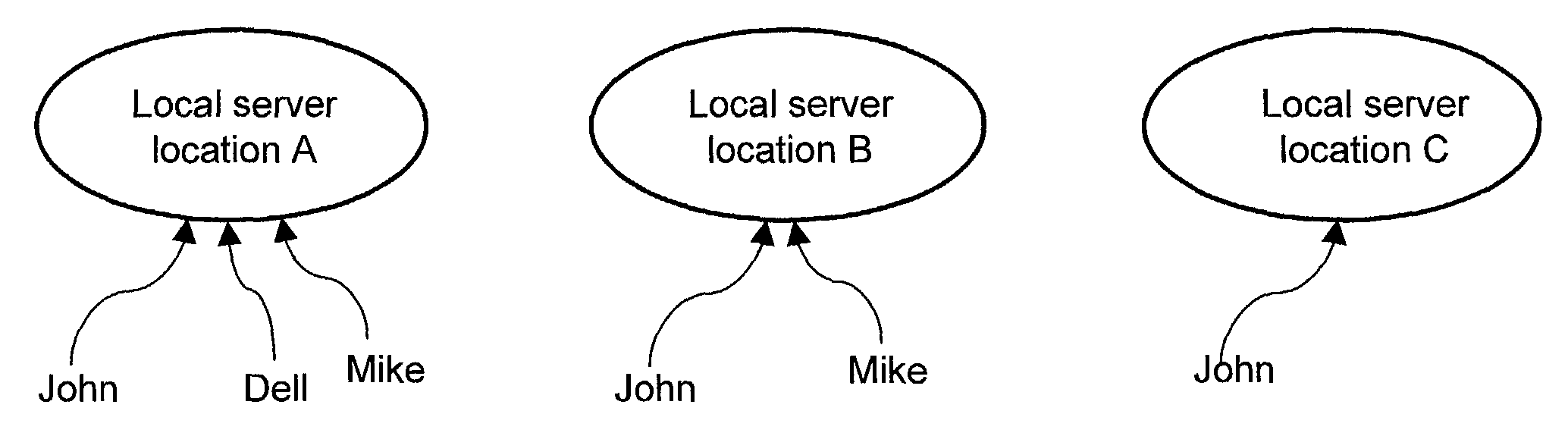
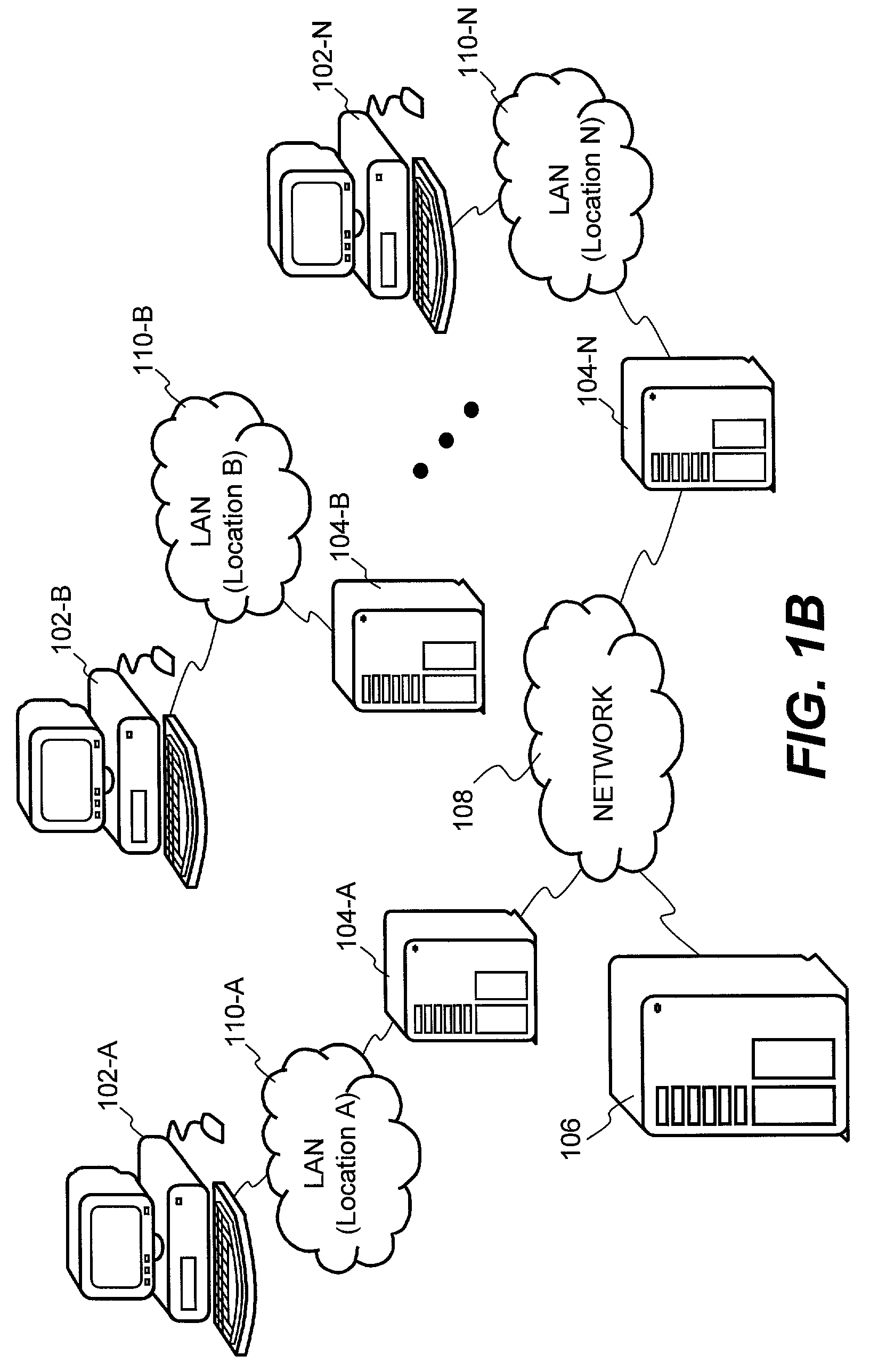
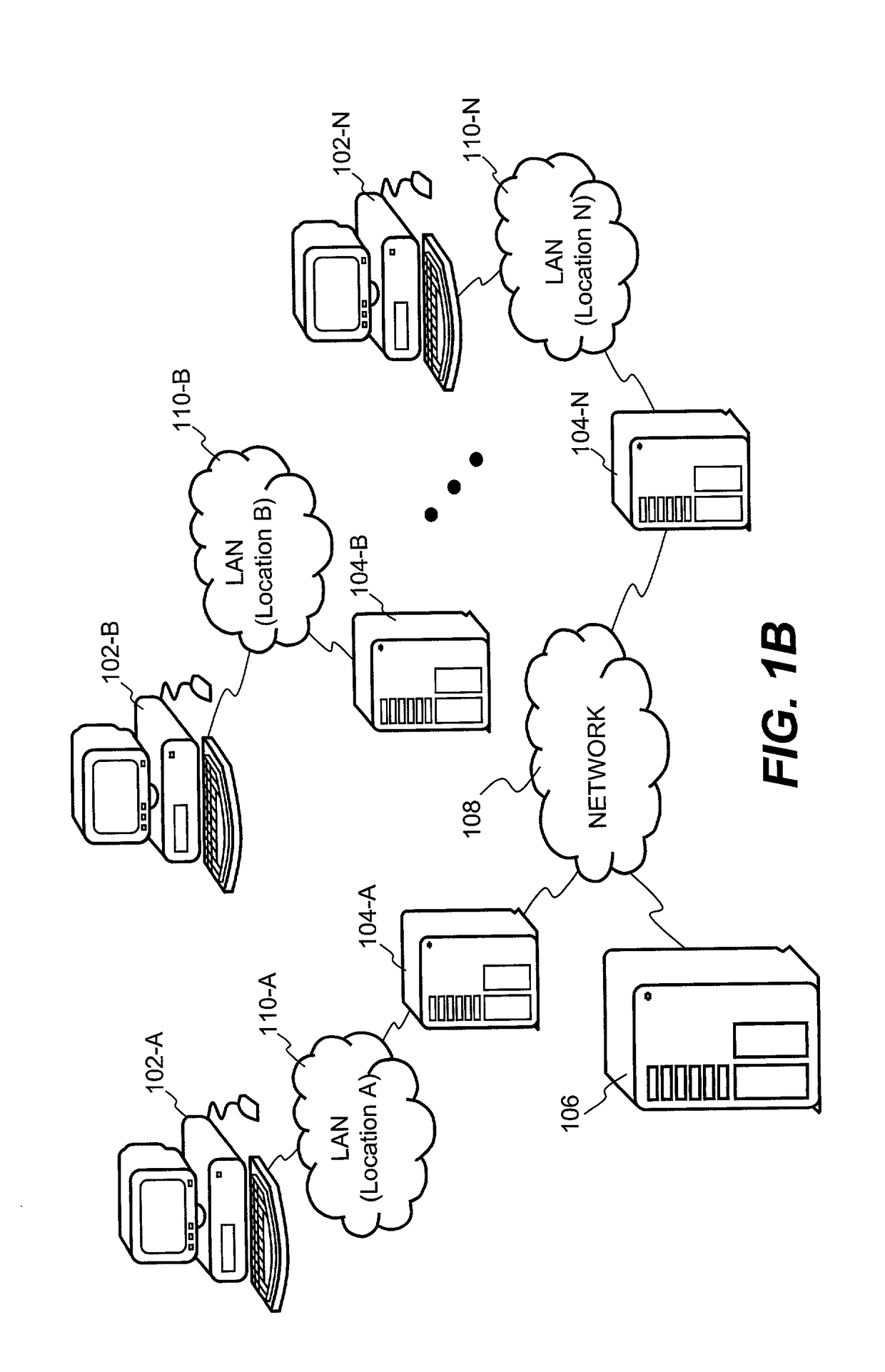
System and method for providing multi-location access management to secured items
ActiveUS8065713B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationAccess managementWorld Wide Web
A system and method for providing access management to secured items through use of a plurality of server machines associated with different locations are disclosed. According to one embodiment, a local server can be dynamically reconfigured depending on a user's current location. Typically, a local server services only those users that are local to the local server. When a user moves from one location to another location, upon detecting a new location of the user who has moved from a previous location, the local server for the new location can be reconfigured to add support for the user, while at the same time, the local server for the previous location is reconfigured to remove support for the user. As a result, security is enhanced while the access management can be efficiently carried out to ensure that only one access from the user is permitted at any time across an entire organization, regardless of how many locations the organization has or what access privileges the user may be granted.
Owner:INTELLECTUAL VENTURES I LLC
Imaging system
InactiveUS20170205618A1Enhance imageImprove performanceMechanical apparatusPlanar/plate-like light guidesLight waveLight source
An imaging system suitable to provide an image of a surface portion of an object is disclosed. The system includes a light source arranged to provide a light beam, at least a first optical waveguide having a first face and having a second face opposite to the first face, the first face having an incoupling surface. The optical waveguide includes an outcoupling surface, a first diffraction grating arranged on the optical waveguide, and an imaging subsystem arranged to the outcoupling surface. The first diffraction grating is arranged to outcouple at least a fraction of the light beam.
Owner:CSEM CENT SUISSE DELECTRONIQUE & DE MICROTECHNIQUE SA RECH & DEV
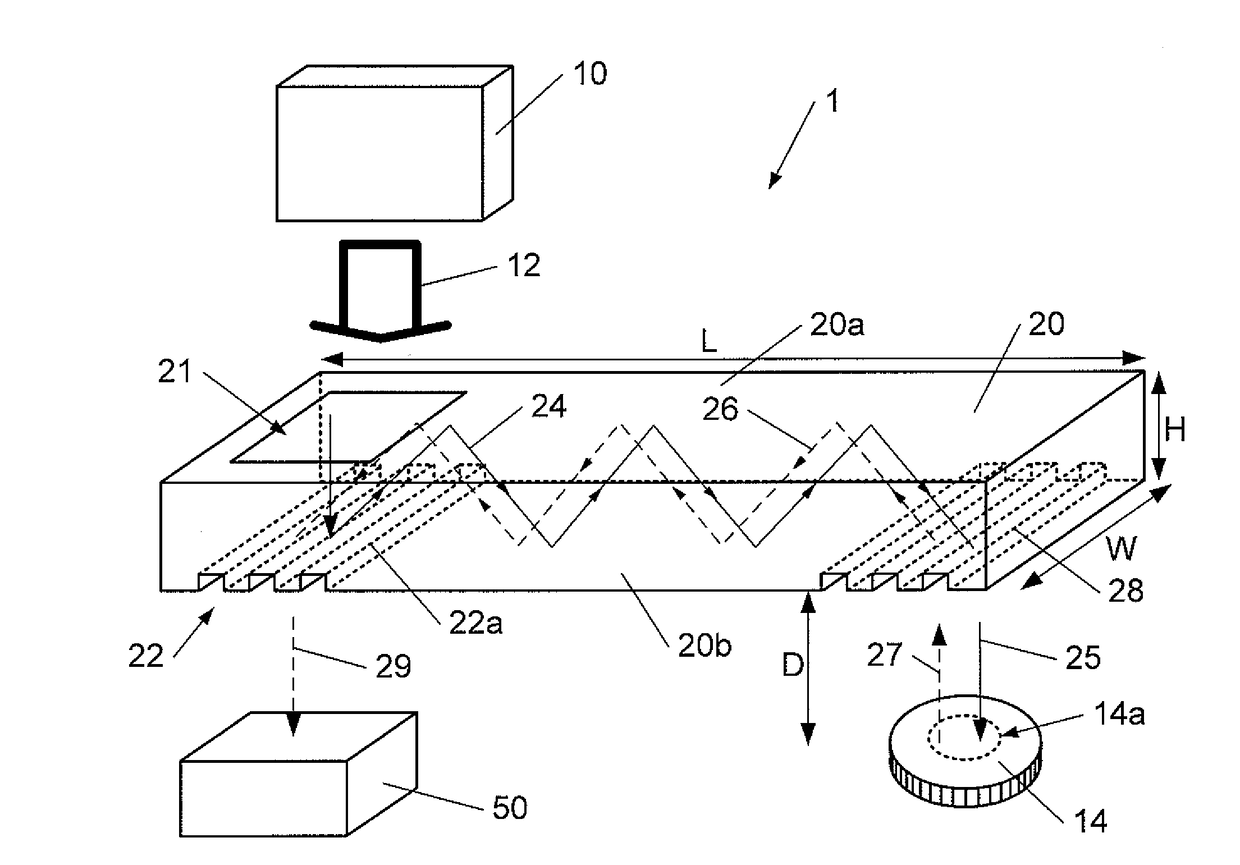
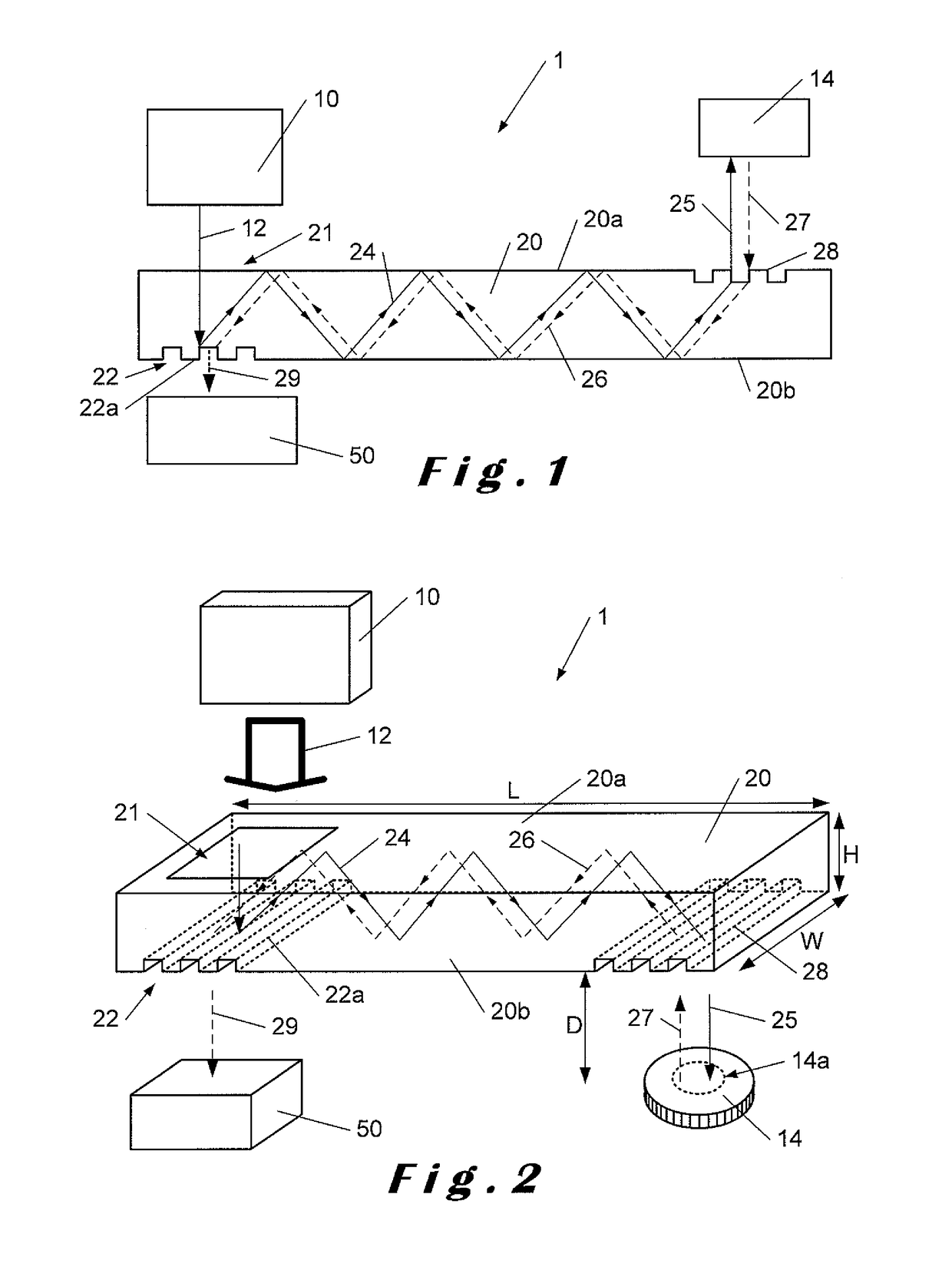
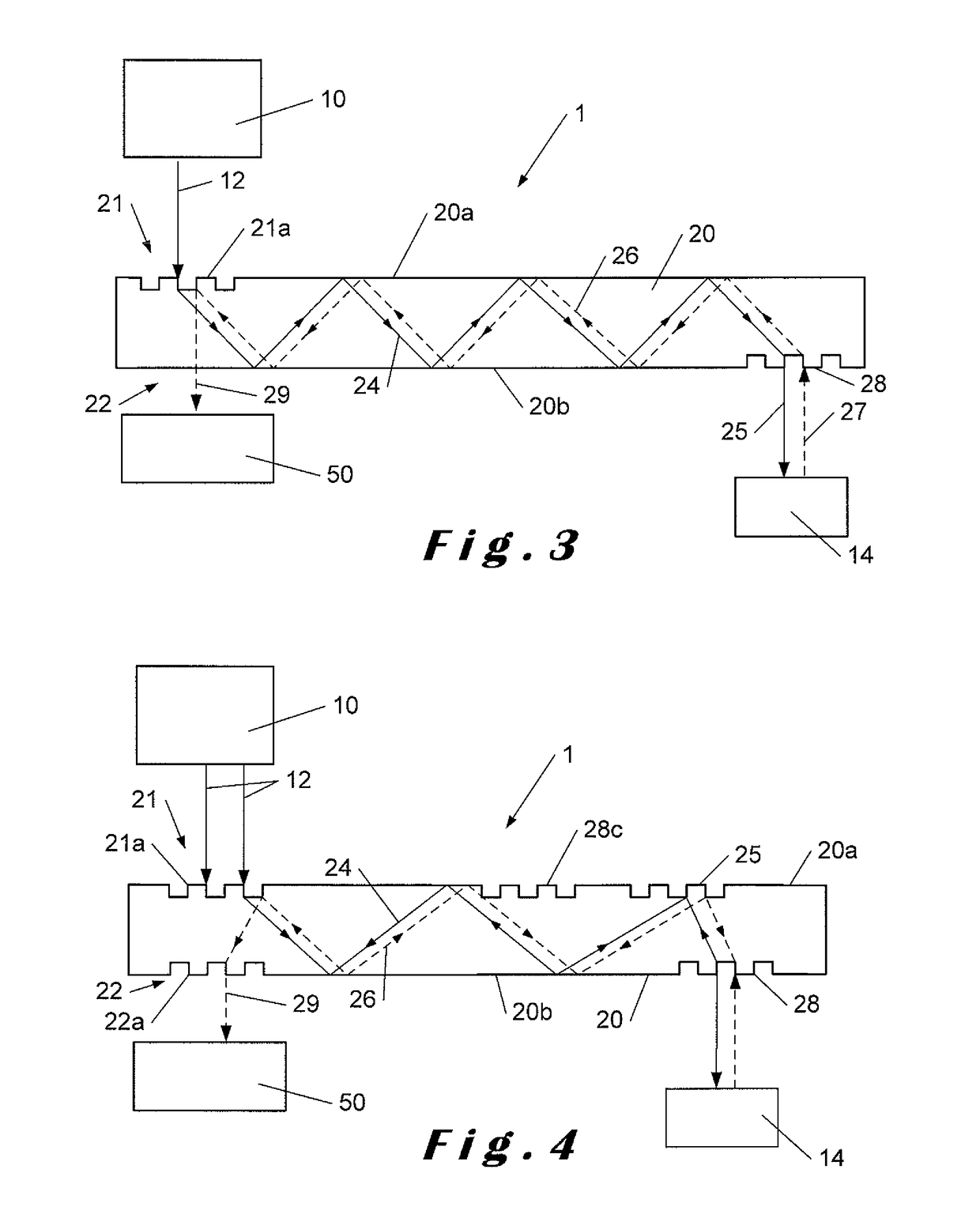
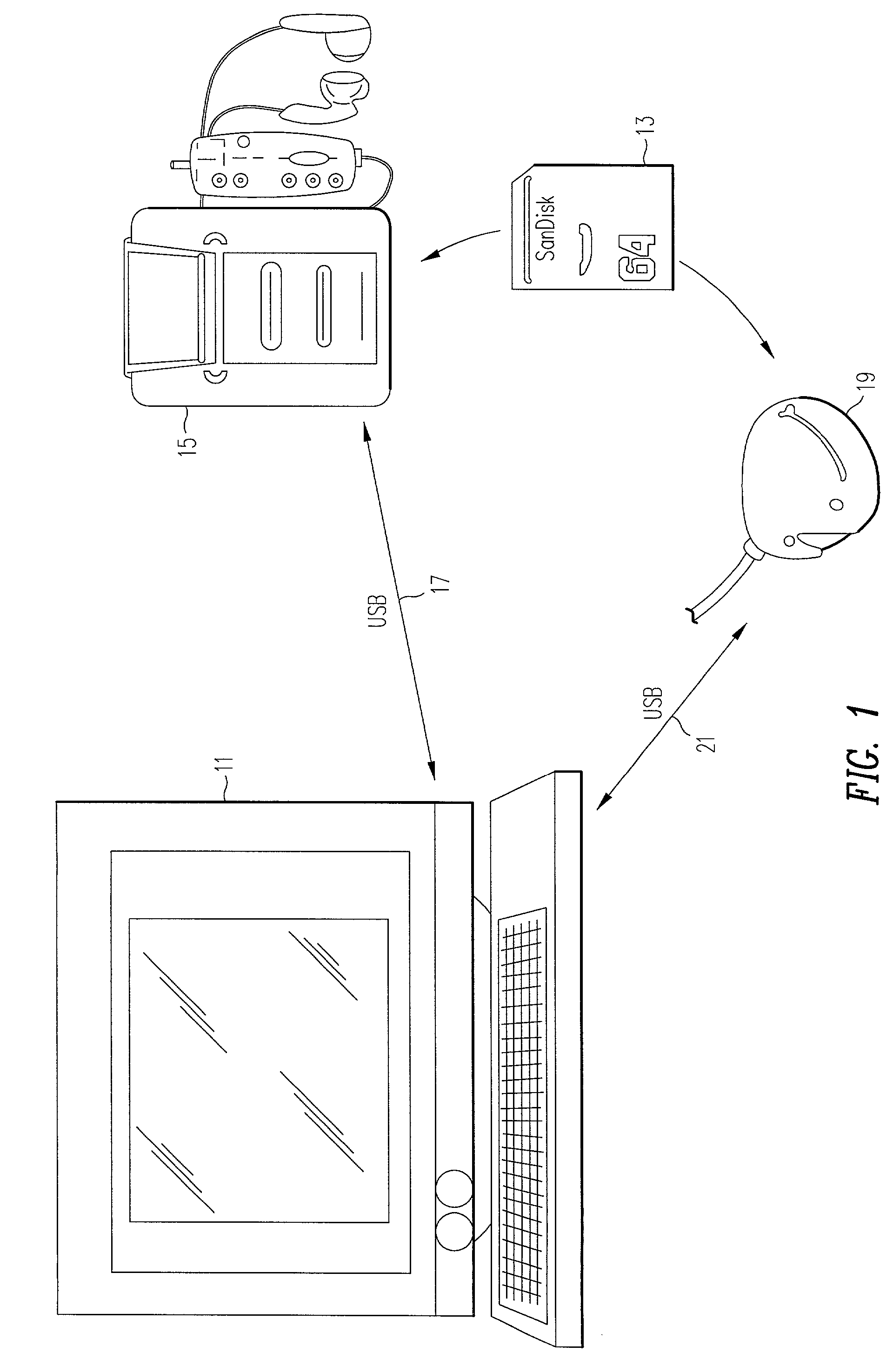
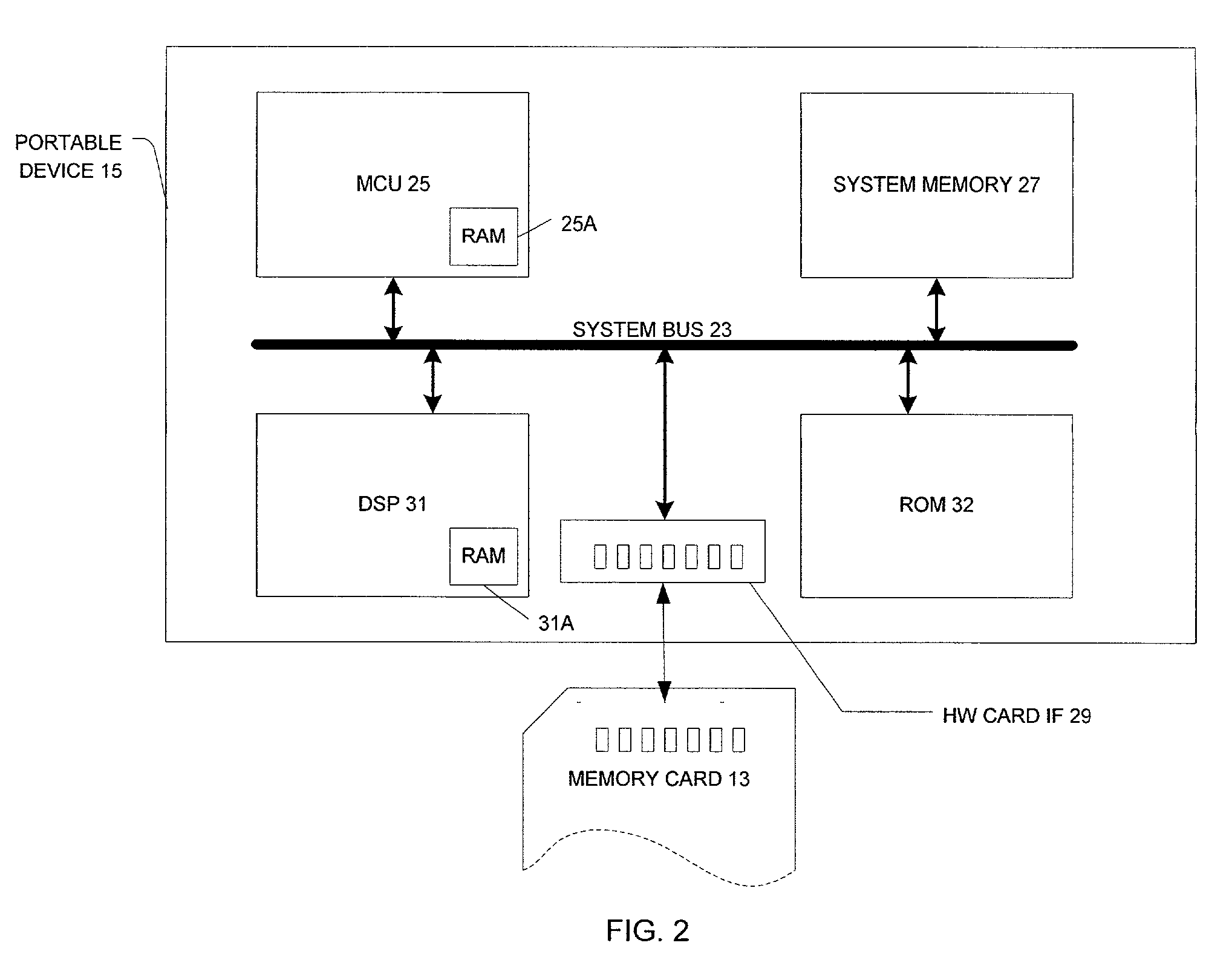
System, method, and device for playing back recorded audio, video or other content from non-volatile memory cards, compact disks or other media
InactiveUS7227952B2Minimize exposureDifficult to accessTelevision system detailsKey distribution for secure communicationSoftware systemSecurity software
A secure software system for a portable device or computer that provides a simple interface to the device or computer and that retrieves and dynamically decrypts keys and content from a secure media while minimizing exposure of the keys and eliminating the need for manufacturers of the device or computer to create a their own system to manage these complex processes.
Owner:SANDISK TECH LLC
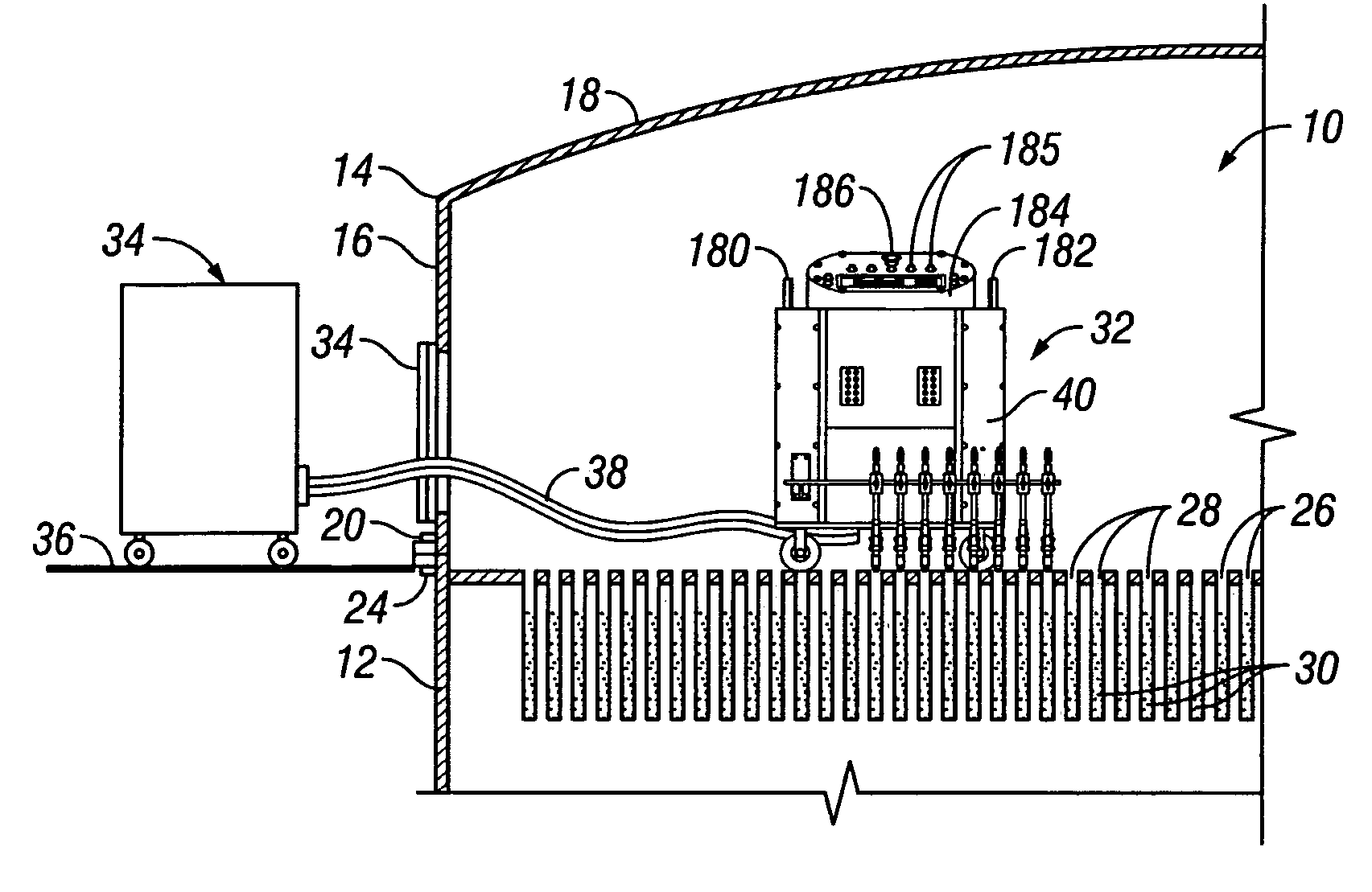
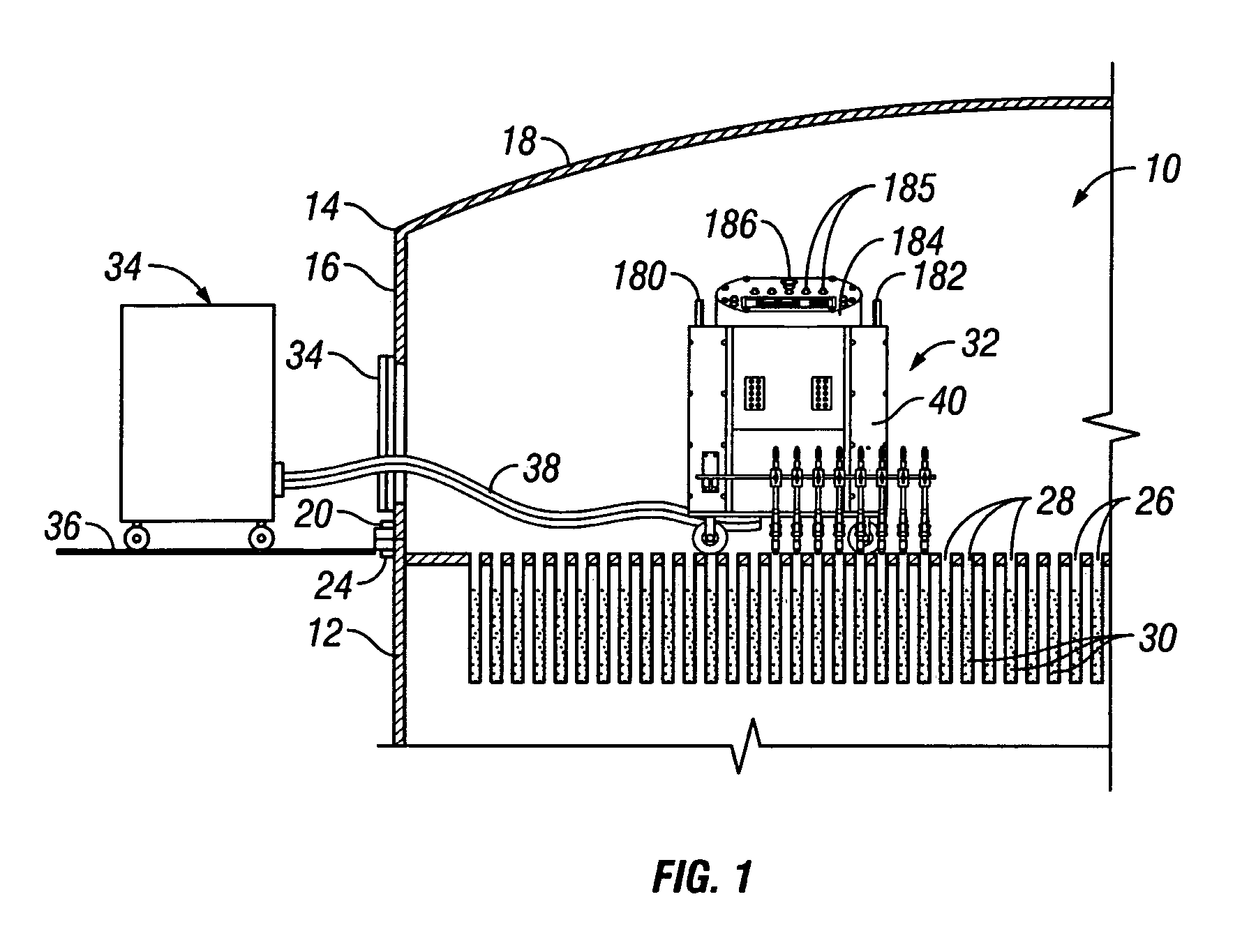
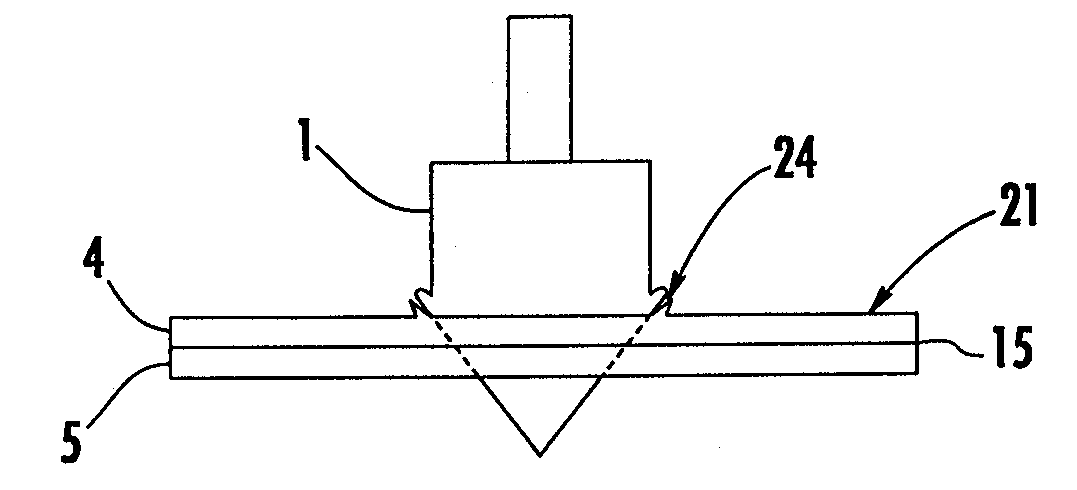
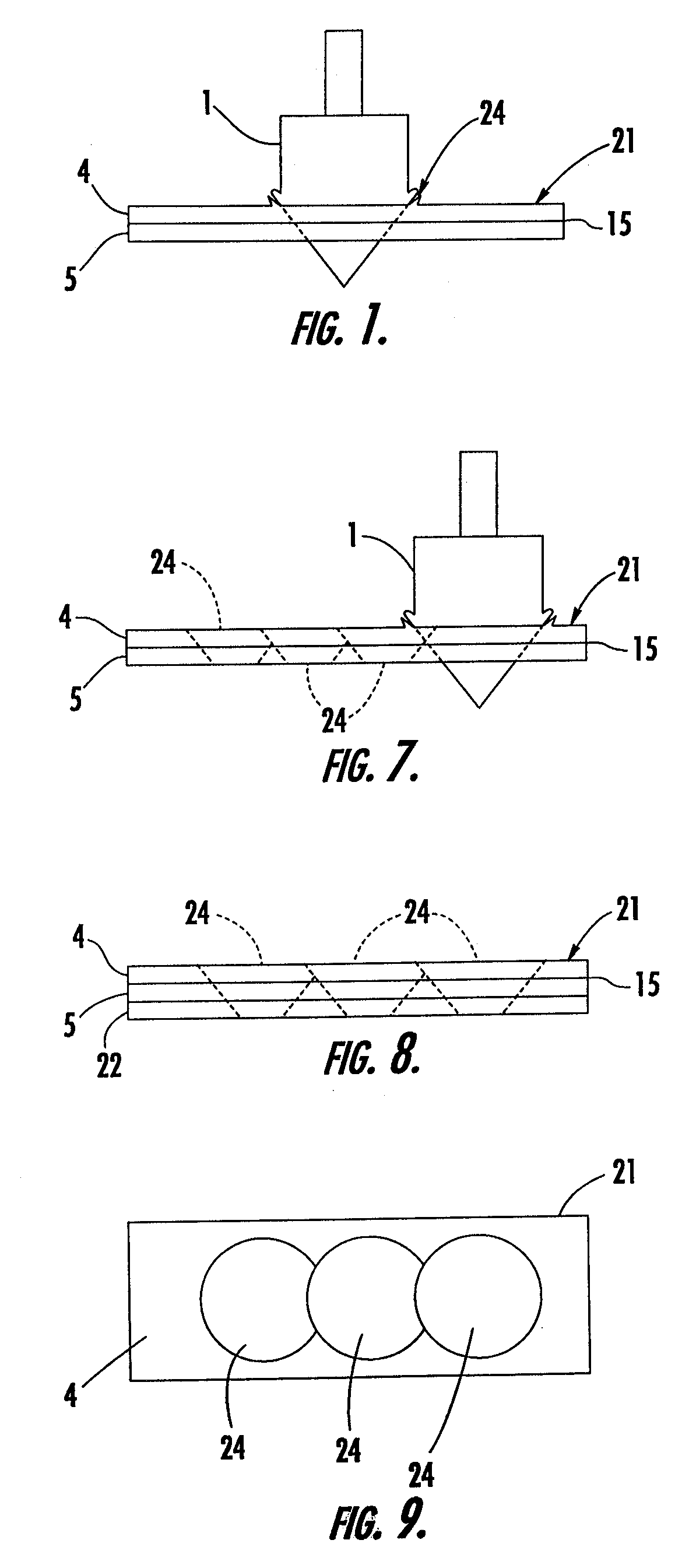
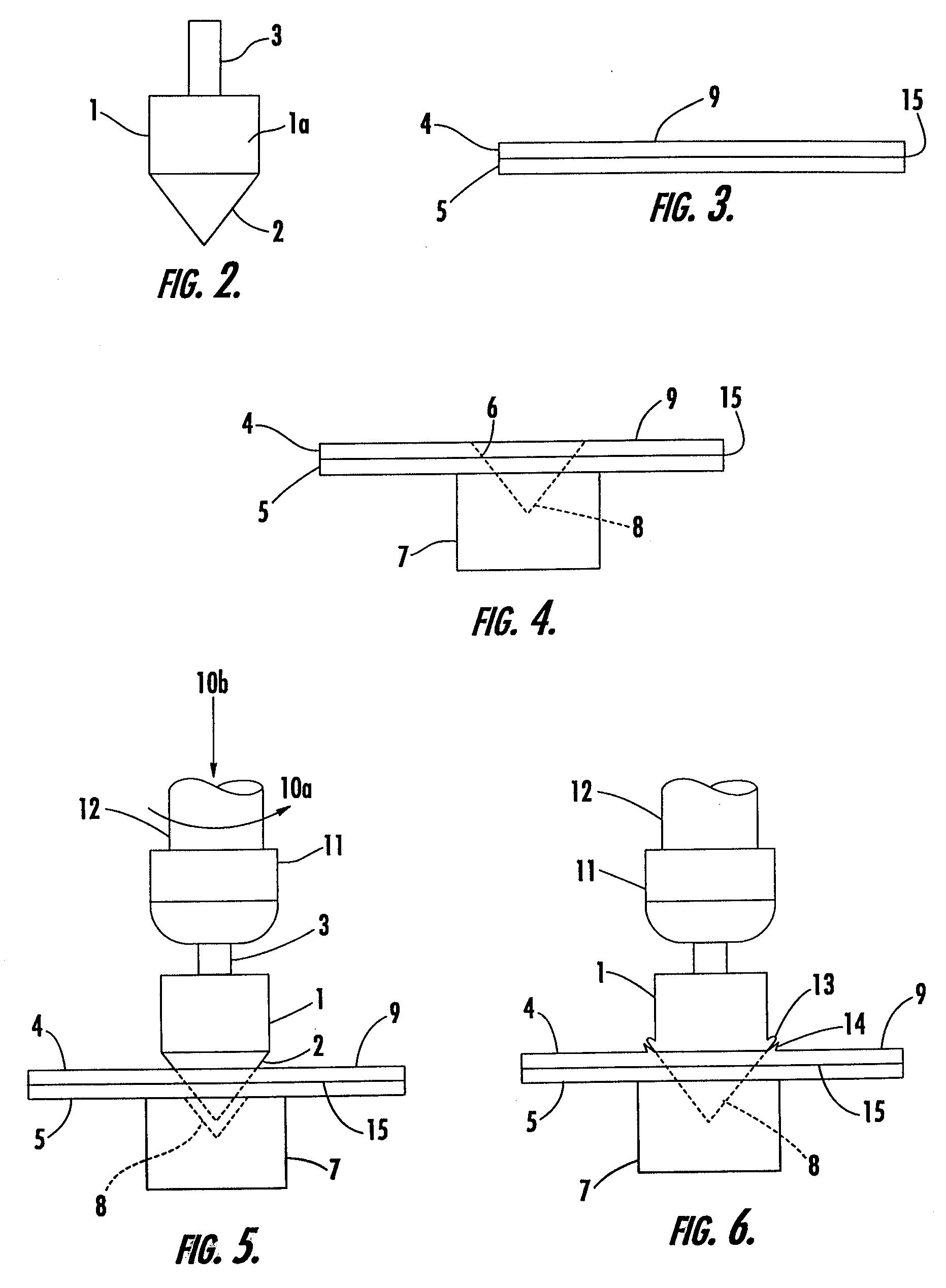
Method and apparatus for differential pressure testing of catalytic reactor tubes
ActiveUS6981422B1Efficient testingMinimizes servicing timeProcess control/regulationMaterial strength using tensile/compressive forcesDifferential pressureEngineering
A multi-tube differential pressure (Delta P) testing system for testing catalyst filled tubes of tube and shell type catalytic reactors has at least one mobile test unit for movement on the upper tube sheet of a catalytic reactor. An array of test probes is mounted to the mobile test unit and is selectively positionable in sealed gas pressure communicating engagement within the upper ends of selected reactor tubes. A pressure testing gas delivery system is interconnected with the test probes and selectively communicates pressurized gas to the testing tubes at a blow-down pressure or selected test pressure determined by restricted orifices. A differential pressure measurement system measures the back-pressure resulting from application of test pressure to individual reactor tubes and having a computer receiving electronic back-pressure measurement data and producing an electronic and / or visual record correlated with a reactor tube numerical sequence and identifying the resulting back-pressure of each reactor tube of the multi-tube test. The testing system is capable of selectively electronically counting in normal sequence and in inverted sequence to accommodate test unit orientation and incorporates a separate manually positioned testing wand to accommodate tube positions of the reactor that cannot be readily accessed by one or more of the array of test probes.
Owner:WINDLASS METALWORKS
Joining of structural members by friction plug welding
InactiveUS20030201306A1Cost effectiveEfficiently joinedWelding/cutting auxillary devicesAuxillary welding devicesFriction weldingEngineering
Abstract of the Disclosure The method of manufacturing a structural assembly includes positioning a first structural member at least partially adjacent a second structural member to define an interface therebetween and inserting a rotating plug into the first and second structural members at the interface to thereby join the first structural member to the second structural member. The resulting friction plug weld provides a relatively strong joint between the structural members, requires less forming and machining time, and is compatible with single-sided tooling. Additionally, the friction plug weld is compatible with other joining methods, such as friction stir welding.
Owner:THE BOEING CO
Methods And Systems For Using Therapeutic, Diagnostic or Prophylactic Magnetic Agents
ActiveUS20090287036A1Good curative effectPoor therapy deliveryAdditive manufacturing apparatusElectrotherapyDisease areaMedicine
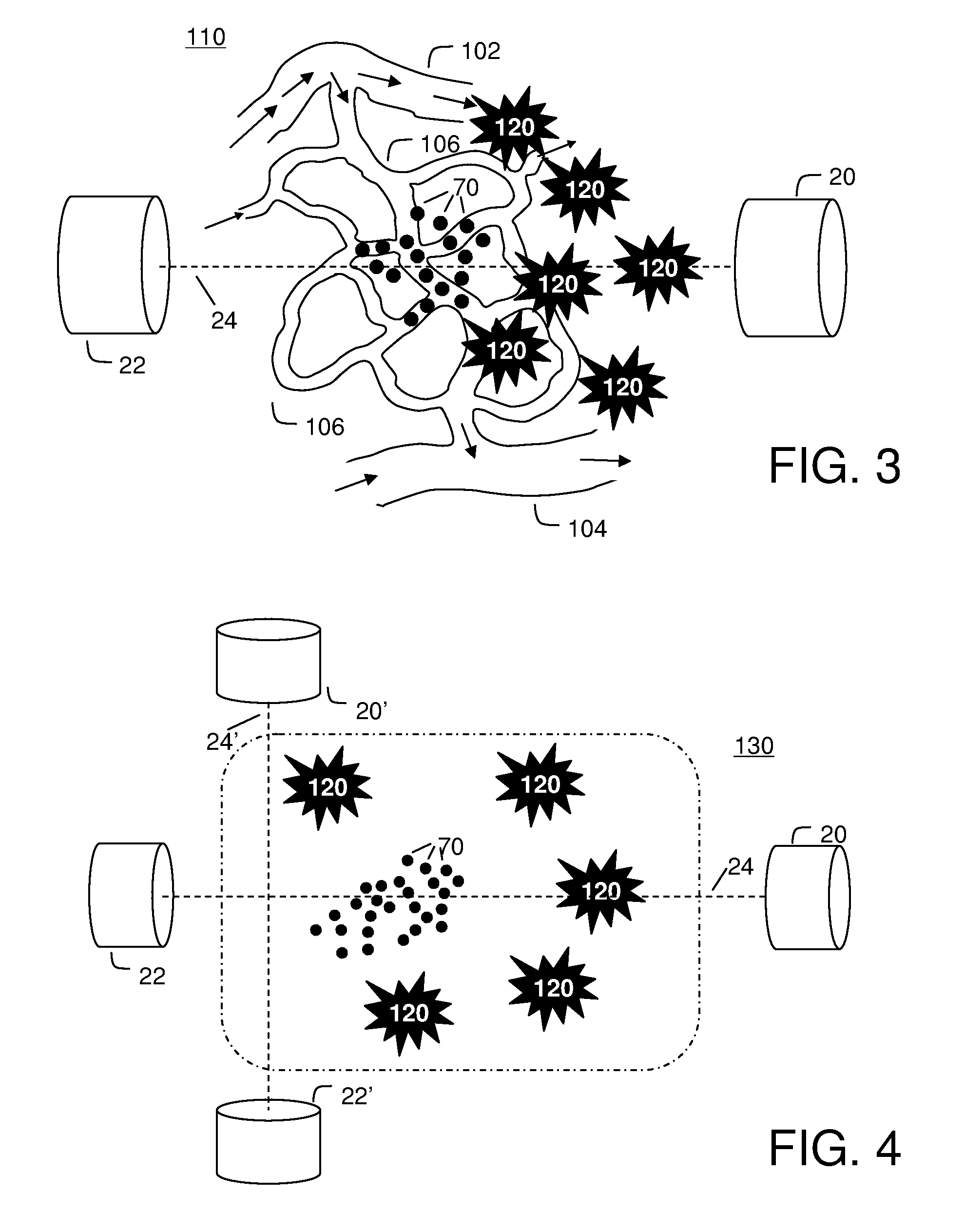
Systems and methods are disclosed for directing magnetizable particles comprising therapeutic agents to a target volume, or for guiding magnetizable particles comprising therapeutic agents from a first target volume to a second target volume, at a distance using a magnetic field, to enable the treatment of diseased areas including areas deep inside a patient's body. The methods may be used to diagnose or treat diseased areas within a patient, for example tumors of the lungs, intestines, and liver, and is also useful in enhancing the permeability of solid tumors to chemotherapeutic agents.
Owner:UNITED STATES OF AMERICA +1
Medical implants and methods for regulating the tissue response to vascular closure devices
InactiveUS20050004158A1High incidenceReducing host responseBiocideSurgeryVascular closure deviceFibrosis
Devices and methods for reducing, eliminating, preventing, suppressing, or treating tissue responses to hemostatic devices e.g., biological sealants or vascular procedures are disclosed. The invention employs a combination of resorbable, biocompatible matrix materials and a variety of therapeutic agents, such as antiproliferatives or antibiotics, applied to a vascular puncture or incision to achieve hemostasis following diagnostic or interventional vascular catheterizations and to treat neointimal hyperplasia and stenosis. A matrix of a material such as collagen provides a reservoir of a therapeutic agent such as rapamycin (sirolimus) and its derivatives and analogs for delivery at a tissue site at risk for vasculoproliferation, infection, inflammation, fibrosis or other tissue responses.
Owner:VASCULAR THERAPIES LLC (US)
Managing secured files in designated locations
ActiveUS7729995B1Ensures dependability and reliability and scalabilityEfficient executionKey distribution for secure communicationUser identity/authority verificationComputer scienceDatabase
Techniques for managing files in a designated location are disclosed. An example of the designated location is a folder, a directory, a repository, a device, or a storage place. A set of access rules is applied to a designated location such that all files in the designated location shall have substantially similar security. As a result, secured files can be easily created and managed with respect to the designated location and users with access privilege to the designated location can access most of the files, in not all, in the designated location.
Owner:INTELLECTUAL VENTURES I LLC
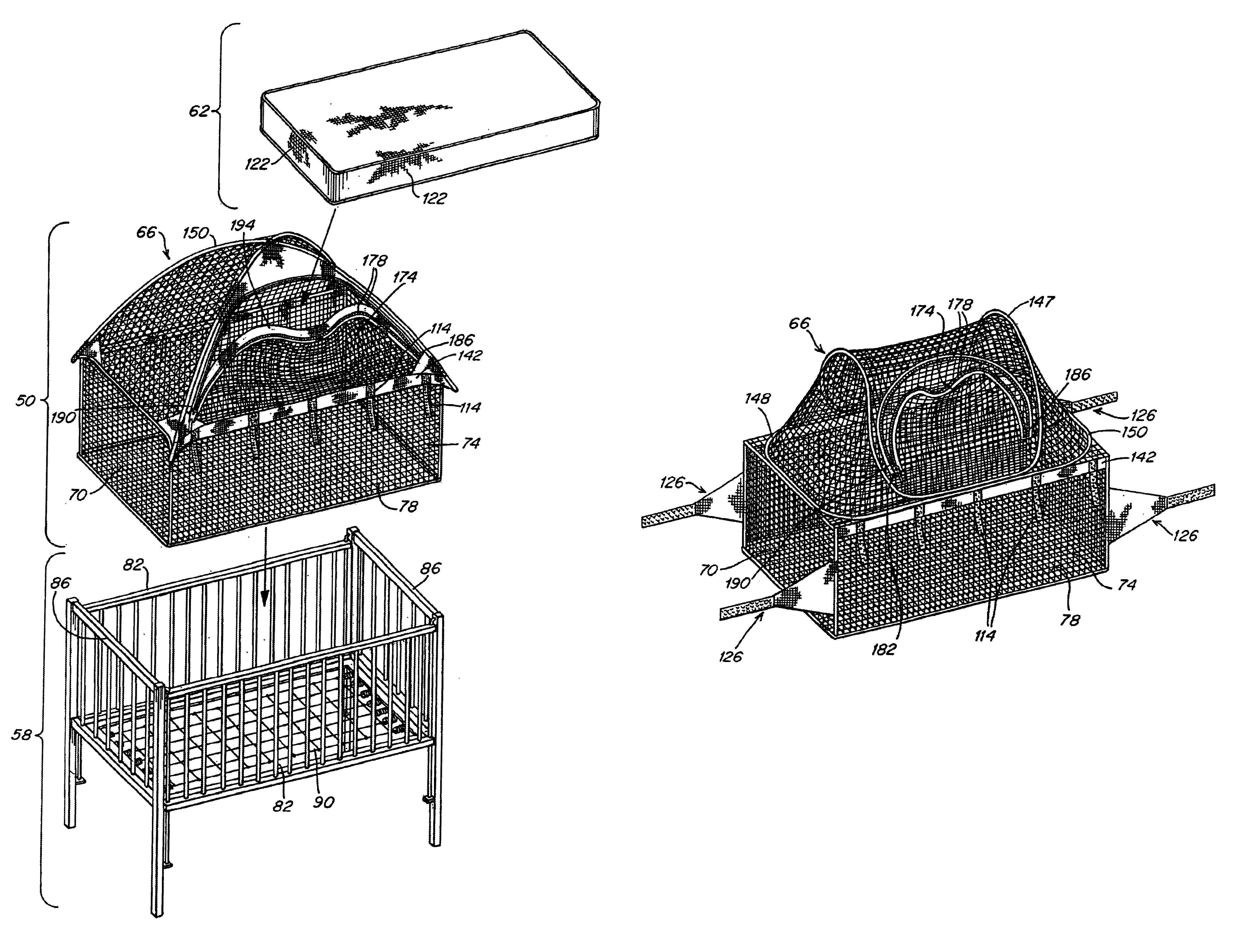
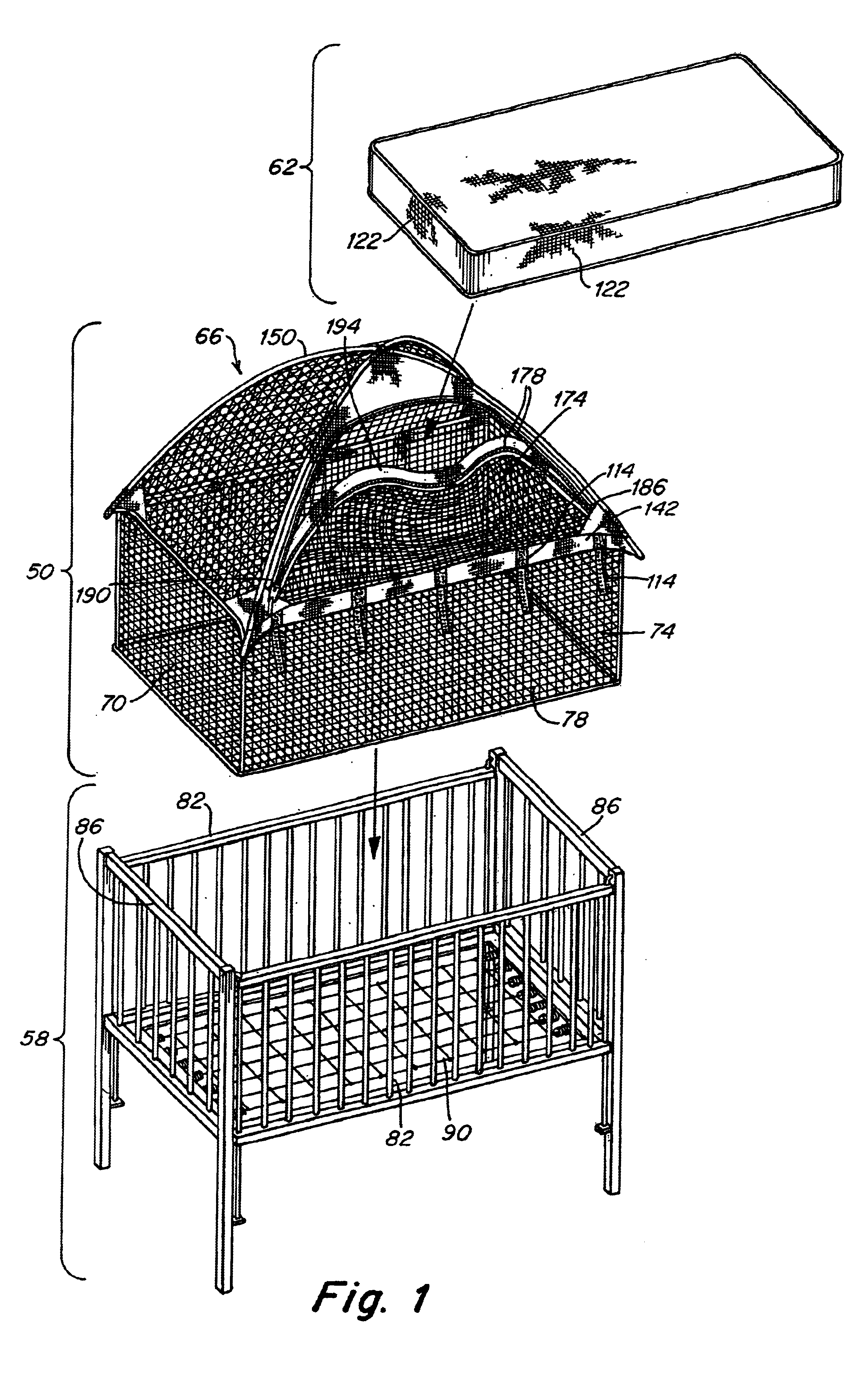
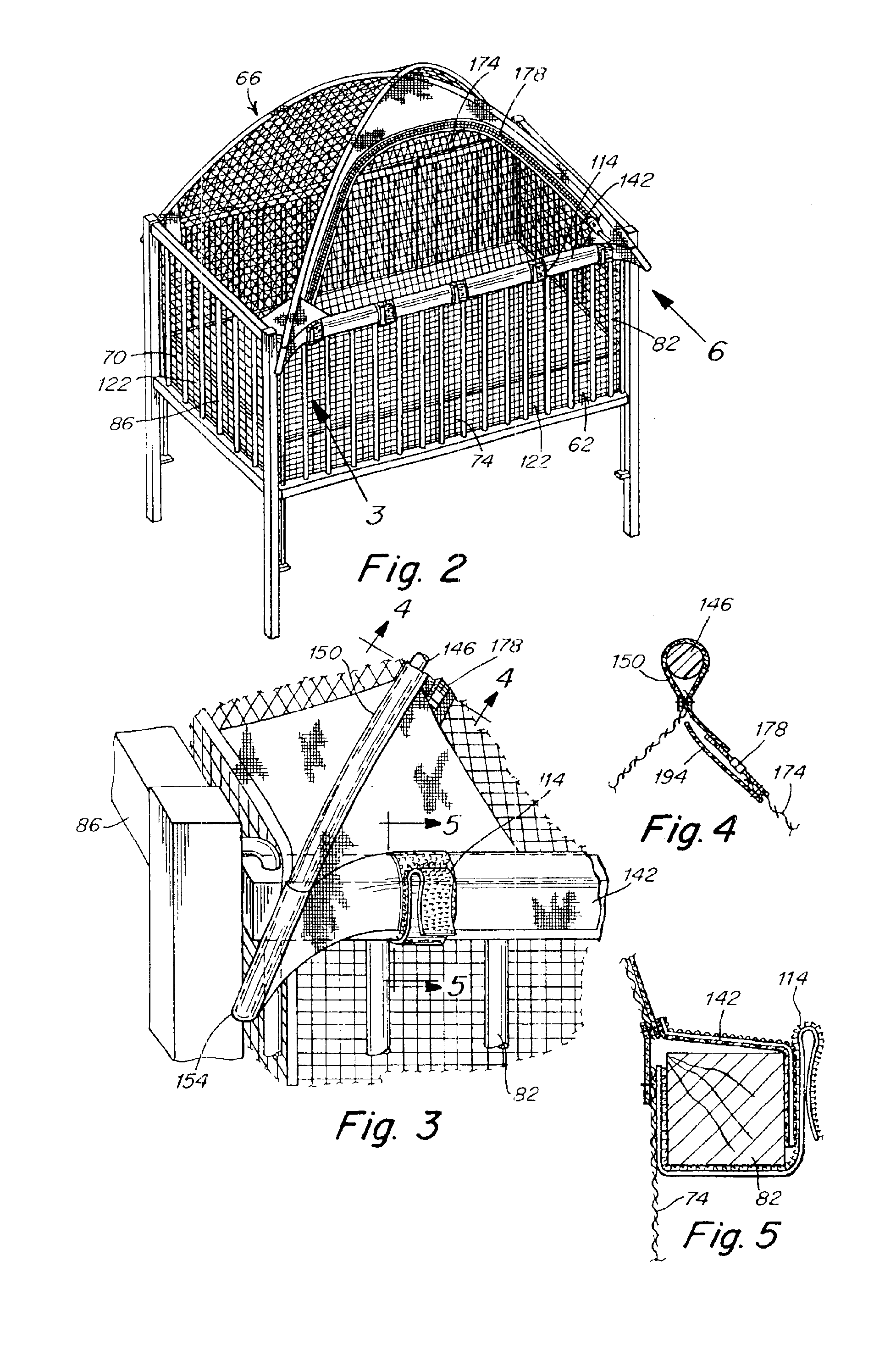
Crib and playpen protective enclosure
An enclosure for a crib or playpen includes a dome-shaped top and a box-shaped bottom structure completely enclosing the interior of a crib or playpen. The enclosure includes a flap in the dome-shaped top to allowing a parent or guardian to easily place a child in or remove a child from the crib or playpen. The enclosure also has features which prevent a child from opening the flap.
Owner:LAMANTIA MARK
Portable submersible cleaning device
InactiveUS7520015B1Efficient extractionEfficient removalWater/sewage treatmentGymnasiumEngineeringWaterline
A portable submersible cleaning device includes a housing that has axillary opposed top and bottom apertures. The housing has a frusto-conical shape, and includes a handle and an access door removably attached thereto. A cleaning head is pivotally and removably attached to a distal end of the housing, and an exterior receptacle is abutted to an outer surface thereof. A mechanism inhales a predetermined volume of debris-saturated water upwardly through the cleaning head and along a unidirectional passageway such that debris is extracted from the debris-saturated water while clean water is expelled outwardly from the housing and reintroduced into the aqueous environment. The exterior receptacle is isolated from the aqueous environment such that power is transmitted to the inhaling mechanism while the housing is submerged beneath a water line of the aqueous environment.
Owner:AJELLO MIKE
System and method for providing distributed access control to secured documents
ActiveUS7783765B2Ensures dependability and reliability and scalabilityEfficient executionDigital data processing detailsAnalogue secracy/subscription systemsAccess control matrixControl system
A system and method for providing distributed access control are disclosed. A number of local servers are employed to operate largely on behalf of a central server responsible for centralized access control management. Such a distributed fashion ensures the dependability, reliability and scalability of the access control management undertaking by the central server. According to one embodiment, a distributed access control system that restricts access to secured items can include at least a central server having a server module that provides overall access control, and a plurality of local servers. Each of the local servers can include a local module that provides local access control. The access control, performed by the central server or the local servers, operates to permit or deny access requests to the secured items by requestors.
Owner:INTELLECTUAL VENTURES I LLC
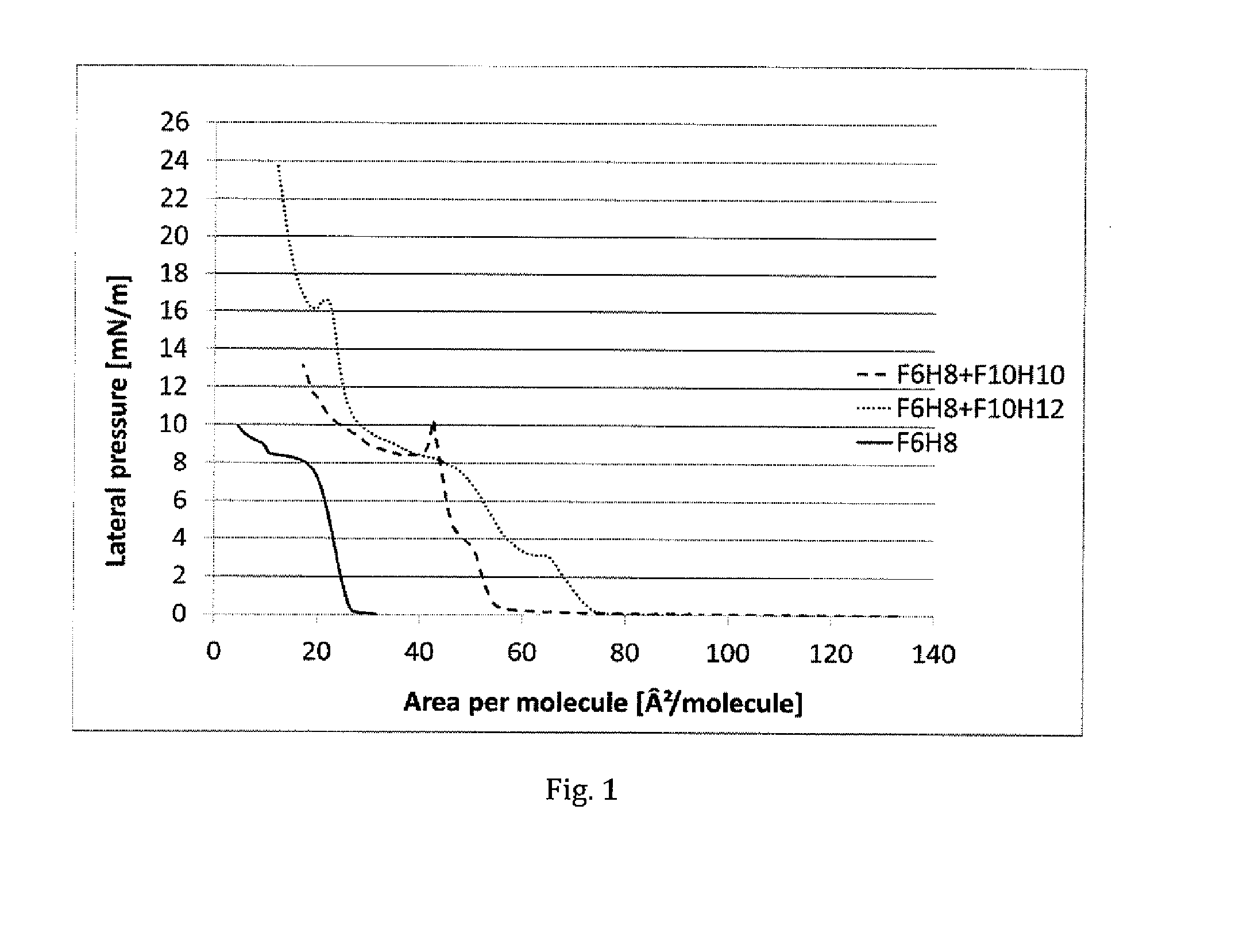
Compositions comprising mixtures of semifluorinated alkanes
ActiveUS20150224064A1Effective timeTune viscosityBiocideHalogenated hydrocarbon active ingredientsAlkaneKERATOCONJUNCTIVITIS SICCA
The invention provides novel compositions comprising at least two or more semifluorinated alkanes. The compositions can be used as medicines that are topically administered to an eye or ophthalmic tissue, such as for use in the treatment of keratoconjunctivitis sicca (dry eye) and / or meibomian gland dysfunction and symptoms associated therewith. The invention further provides kits comprising such compositions.
Owner:NOVALIQ GMBH
System and Method for Providing Multi-Location Access Management to Secured Items
InactiveUS20120137130A1Ensures dependability and reliability and scalabilityEfficient executionComputer security arrangementsTransmissionAccess managementDatabase
A system and method for providing access management to secured items through use of a plurality of server machines associated with different locations are disclosed. According to one embodiment, a local server can be dynamically reconfigured depending on a user's current location. Upon detecting that a user has moved to a new location, the local server for the new location can be reconfigured to add support for the user, while simultaneously, the local server for the previous location is reconfigured to remove support for the user. As a result, security is enhanced while the access management can be efficiently carried out to ensure that only one access from the user is permitted at any time across an entire organization, regardless of how many locations the organization has or what access privileges the user may be granted.
Owner:INTELLECTUAL VENTURES I LLC
Methods and systems for using therapeutic, diagnostic or prophylactic magnetic agents
ActiveUS8579787B2Poor treatment effectPoor supplyElectrotherapyAdditive manufacturing apparatusDisease areaMedicine
Owner:UNITED STATES OF AMERICA +1
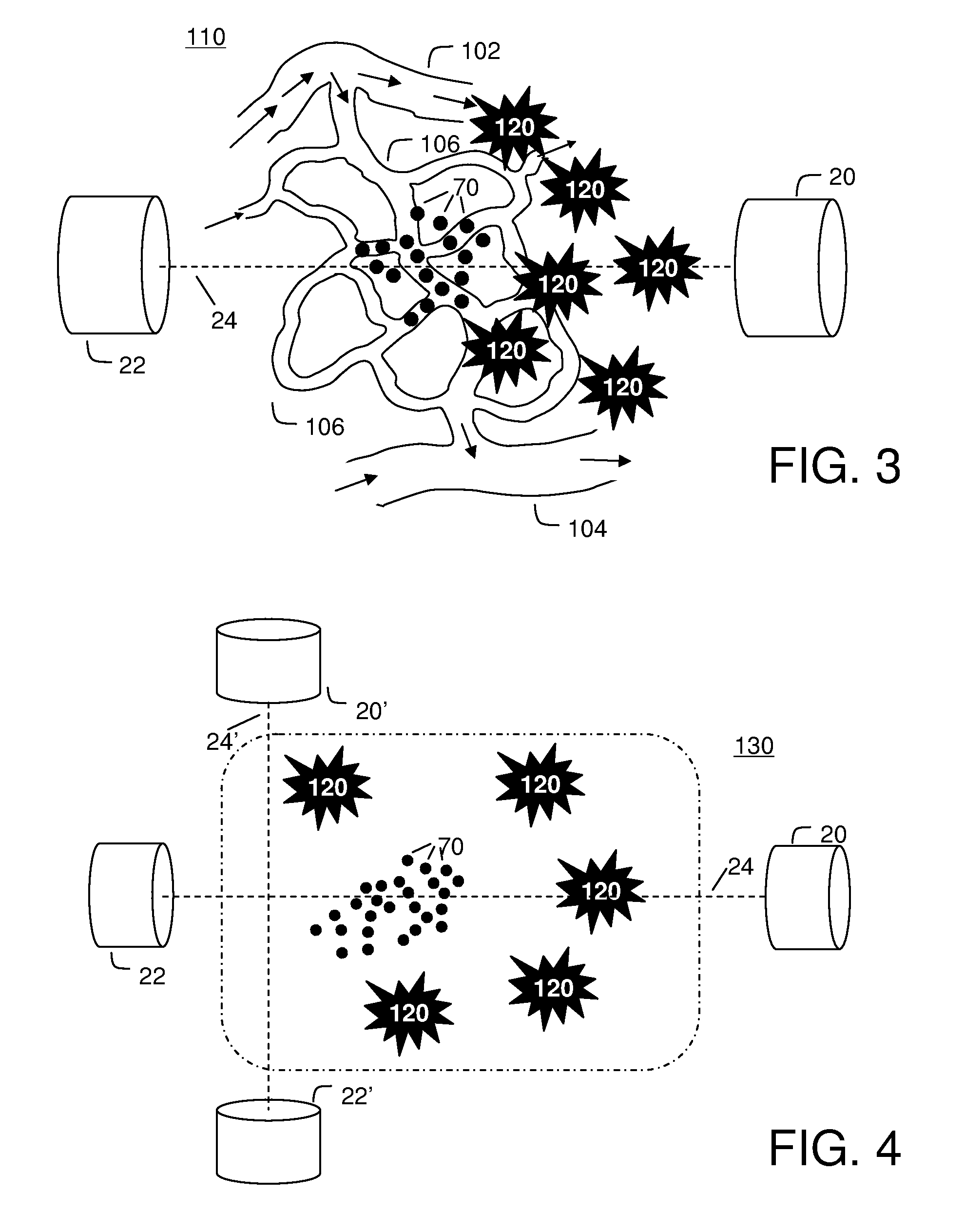
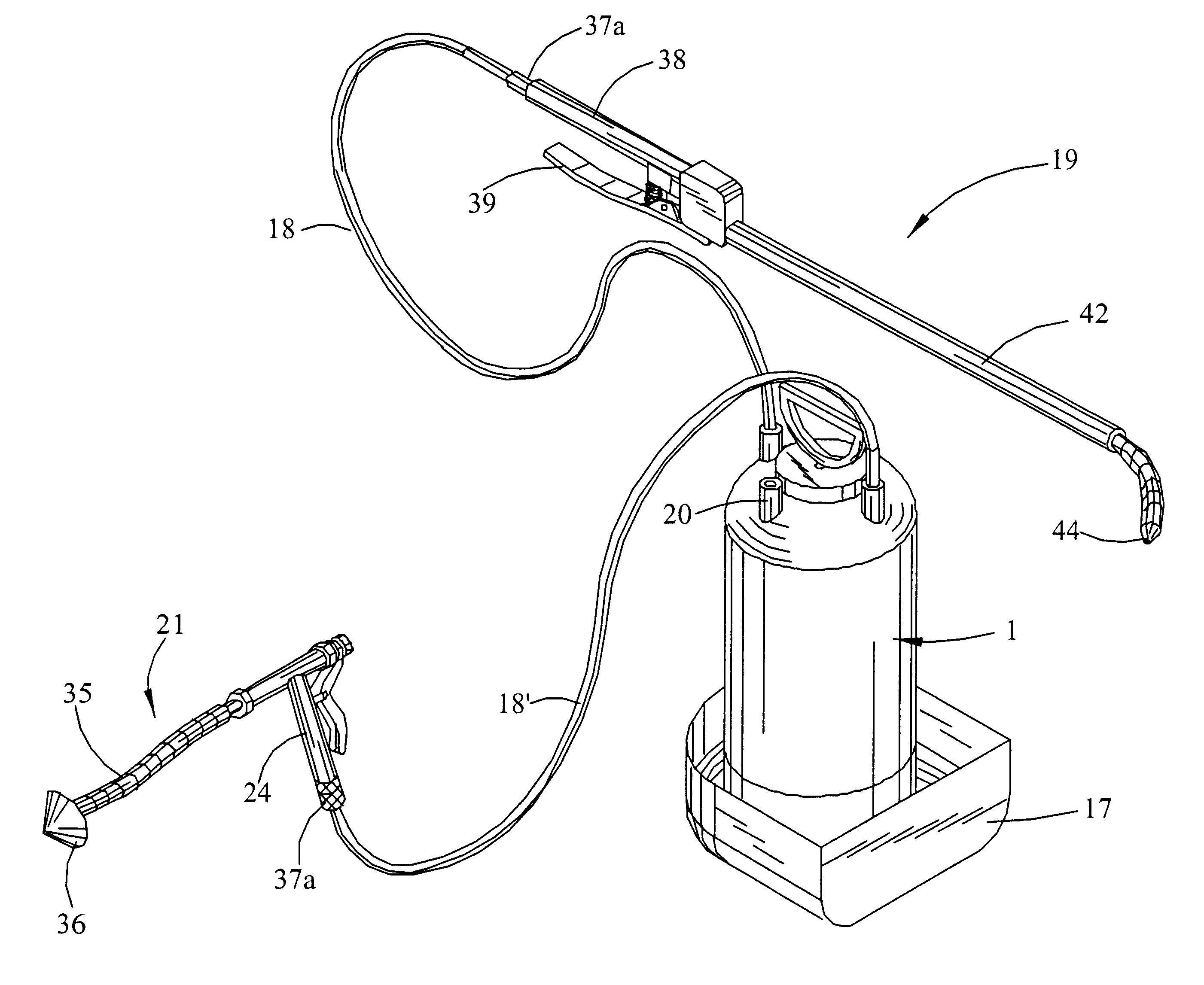
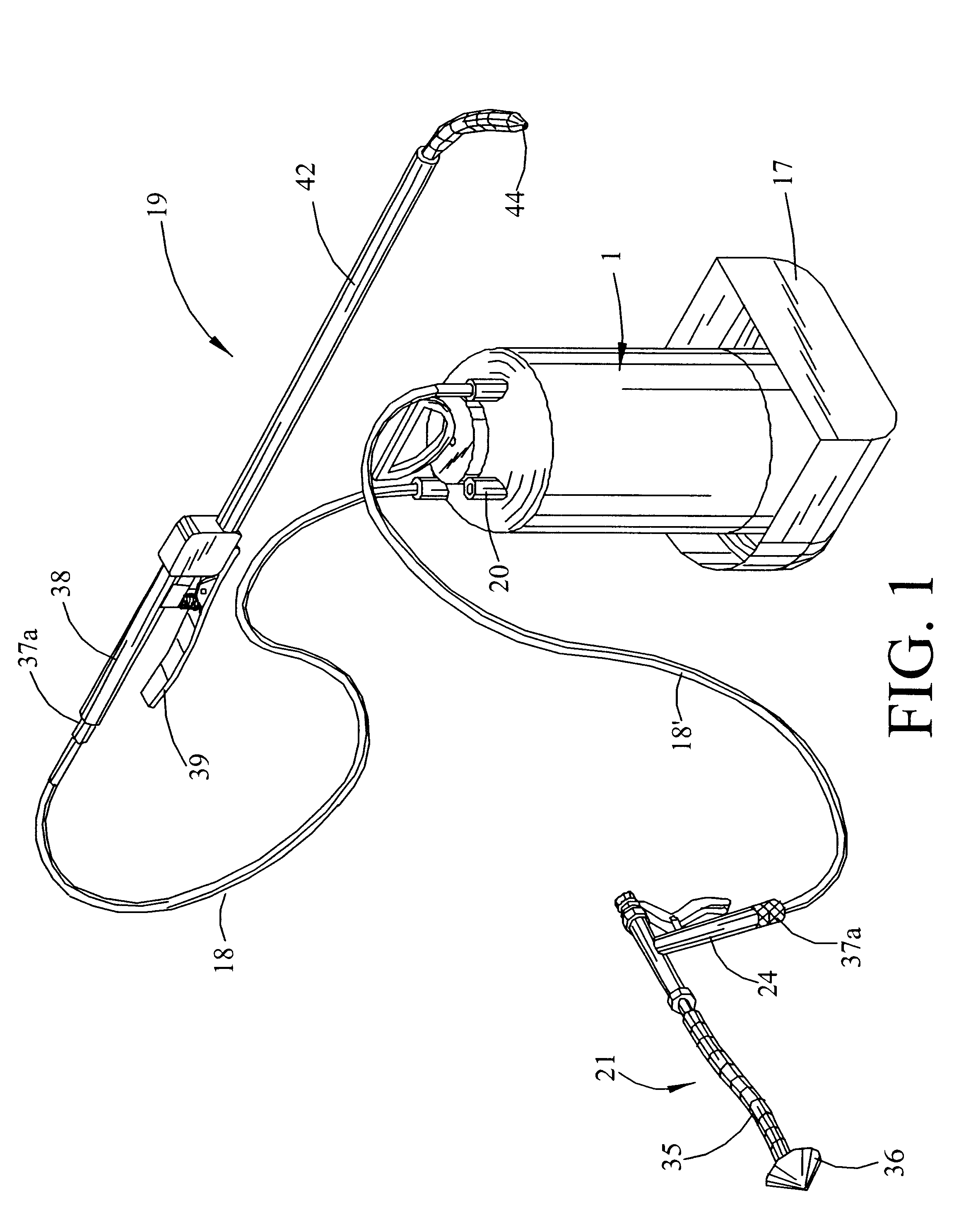
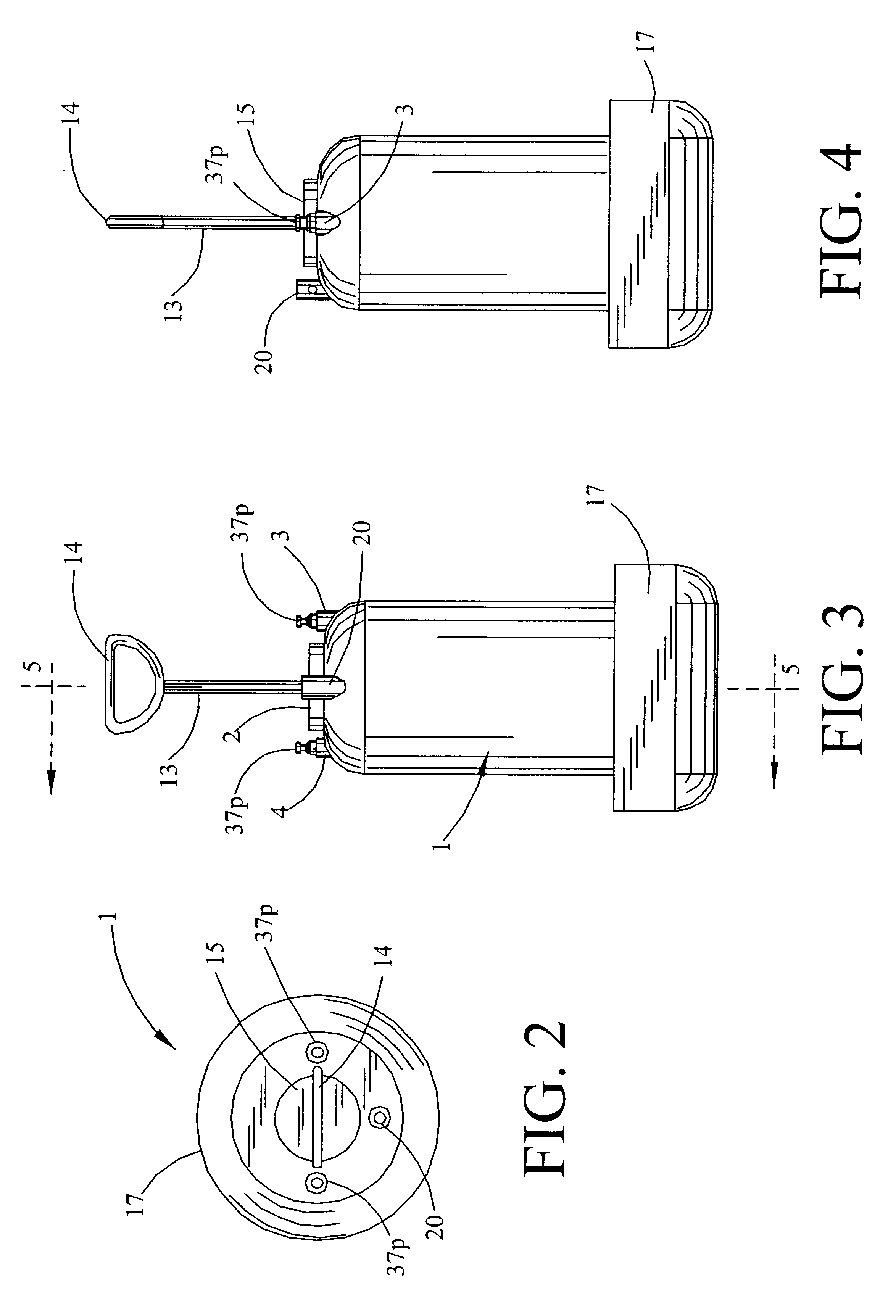
Multi-mode fluid injection system
InactiveUS6308899B1Easy to replaceDifficult to accessHollow article cleaningFire rescueAir compressorGuide tube
A compact, highly portable, multi-mode fluid injection system able to reach difficult to access places to efficiently service a variety of diameter pipes, tubing and related components. The system comprises a tank having a first port which allows access to the tank's upper contents and a second port which allows access to the tank's lower contents, a means for introducing liquid into the tank, a hand pump built into the tank to pressurize the tank and its contents, one or more applicators, and flexible hoses which connect the applicators to the first and / or second port to supply the applicators with the tank's contents. The system is capable of producing, alternatively, pressurized liquid or gas without an independently powered air compressor or consumable gas cartridges, and without having to empty and / or fill the tank. An onboard means for stowing the hose conduits, an injection gun applicator having a small travel-high flow valve with adjustable accumulation chamber, and applicators having stiff-flexible tips and tip extensions are also described.
Owner:MARKET GAP ANALYSIS GRP
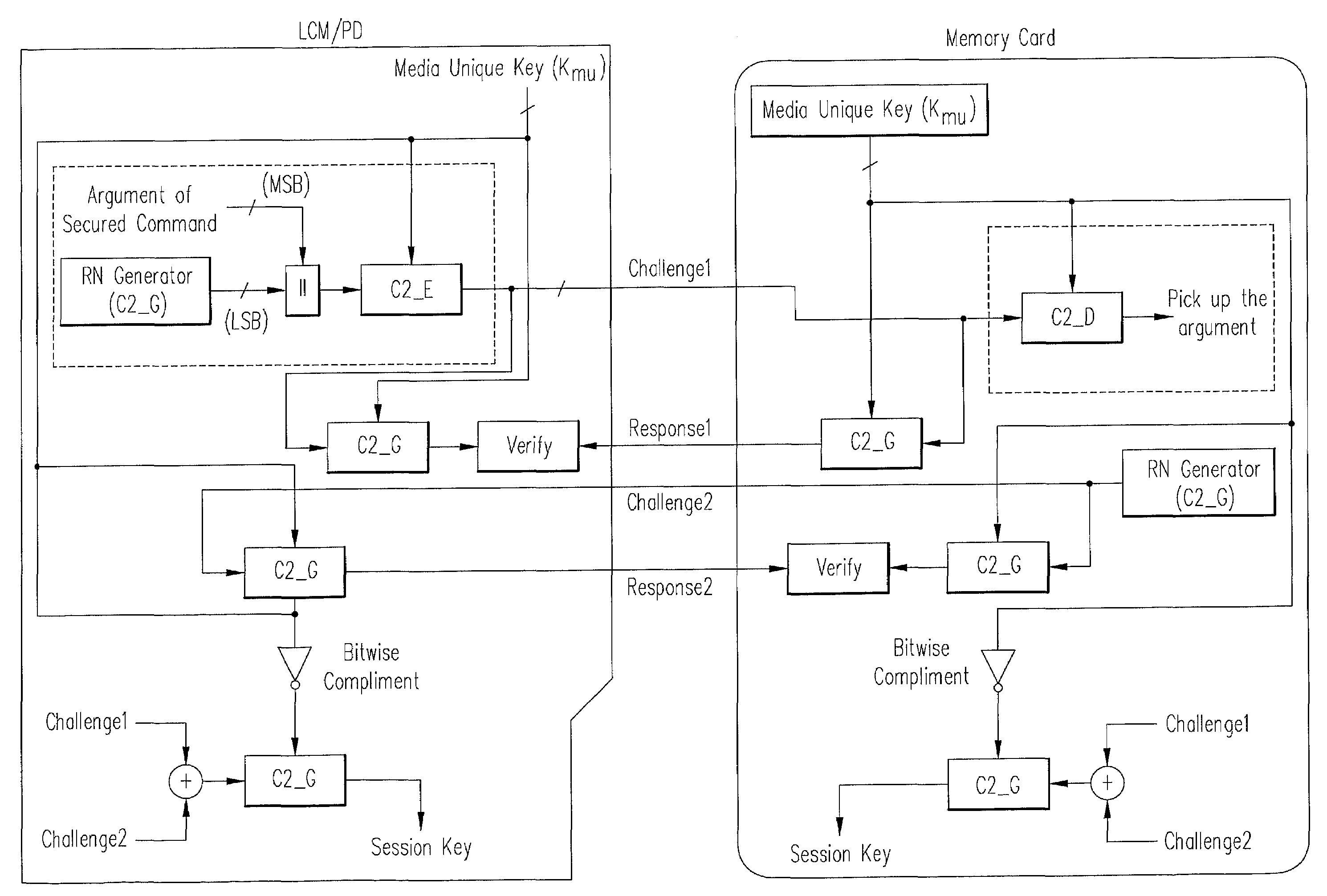
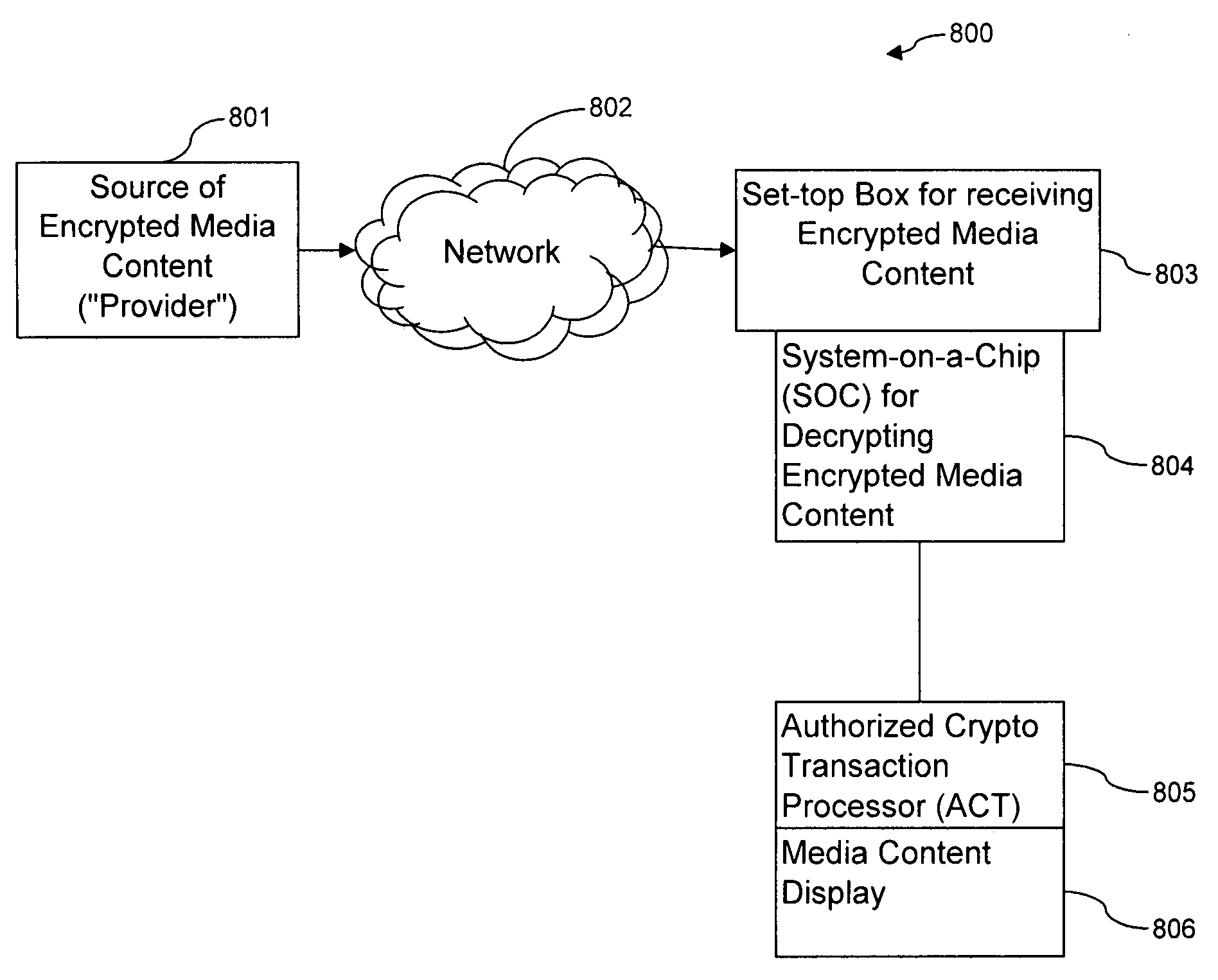
Apparatus and method for enhancing the protection of media content
InactiveUS20090060182A1Protect safetyMaintain securityCathode-ray tube indicatorsTelevision systemsLoudspeakerPersonal computer
An aspect of the current invention involves an apparatus and method for protecting media content from being read and copied by an unauthorized party. In one embodiment of the invention, this is accomplished by storing keys for decrypting encrypted media content on a secure memory device located in proximity to a computer processor. A secure memory device located in proximity to a computer processor allows for decryption keys to be sent to a user of the computer processor in advance of the user receiving an encrypted media content that will be decrypted with the decryption keys. With the secure memory device, the decryption keys can be stored indefinitely without an unauthorized party gaining access to them. Another embodiment of the invention allows for multiple media content providers to store their own decryption keys for their own encrypted media content simultaneously on a secure memory device located with a user's personal computer. A further embodiment of the invention involves using a secure memory device located with a means for displaying media content—such as a monitor or speaker—to allow for secure transfer of decrypted, decompressed media content from a computer processor used to play media content, a stand-alone media content player, or a set-top box media content player to a media content display
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
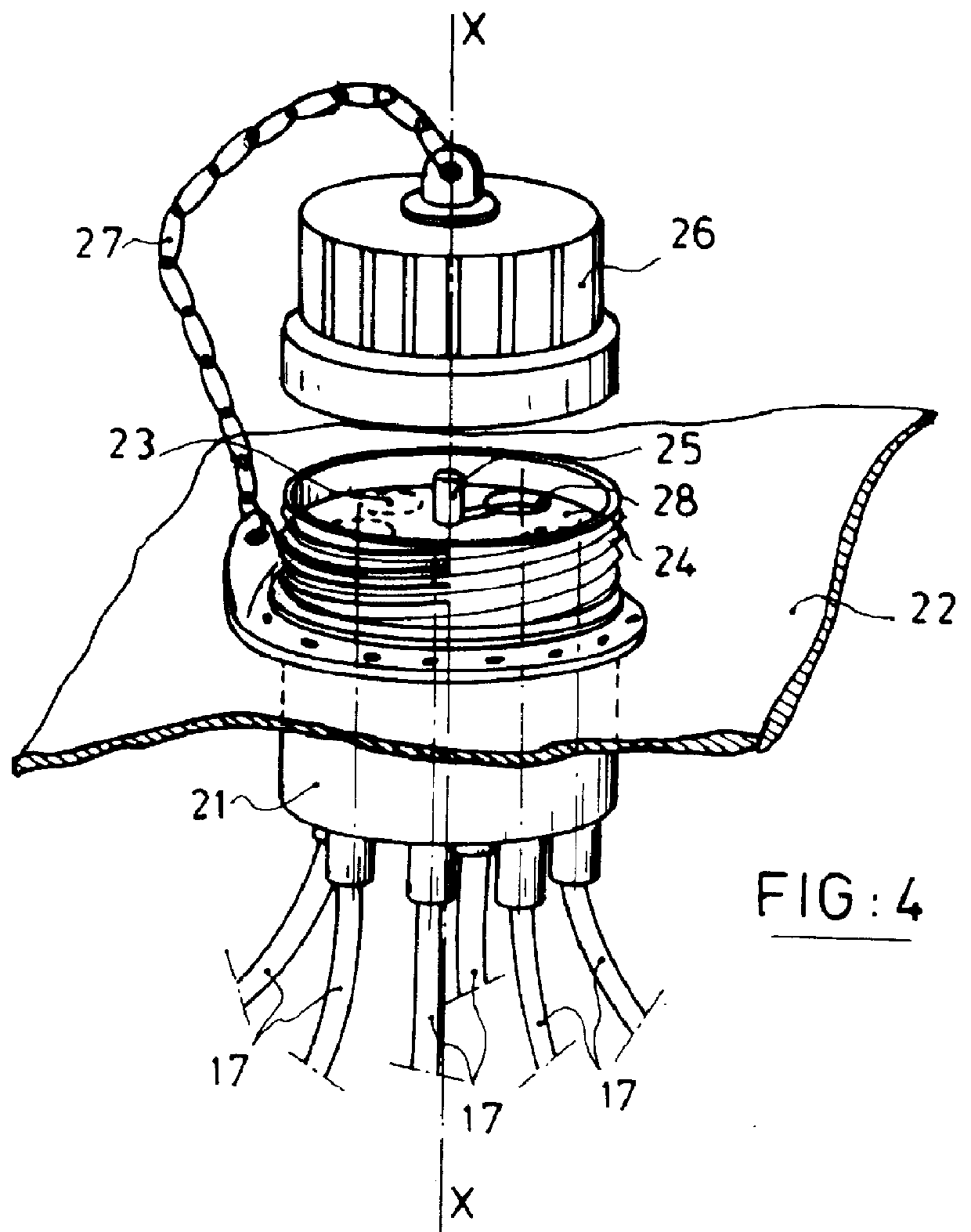
System for inspecting internal zones of a machine by optical fibre endoscopy
InactiveUS6011617ADifficult to accessSurgeryMaterial analysis by optical meansFlexible endoscopeEngineering
A system for inspecting internal zones of a machine, such as an engine, comprises an observation device having an optical fiber endoscope, and distribution and guide means including a network of flexible guide sheaths placed in the machine to define a number of different inspection routes along which the endoscope can be guided from an aperture in the machine wall to various predetermined critical internal zones. Preferably the system includes first electrical means implanted in each guide sheath and co-operable with second electrical means secured to the endoscope in order to detect the position thereof in the network and to transmit the position to a monitoring device outside the machine for monitoring and assisting the guidance of the endoscope in the network.
Owner:SNECMA MOTEURS SA
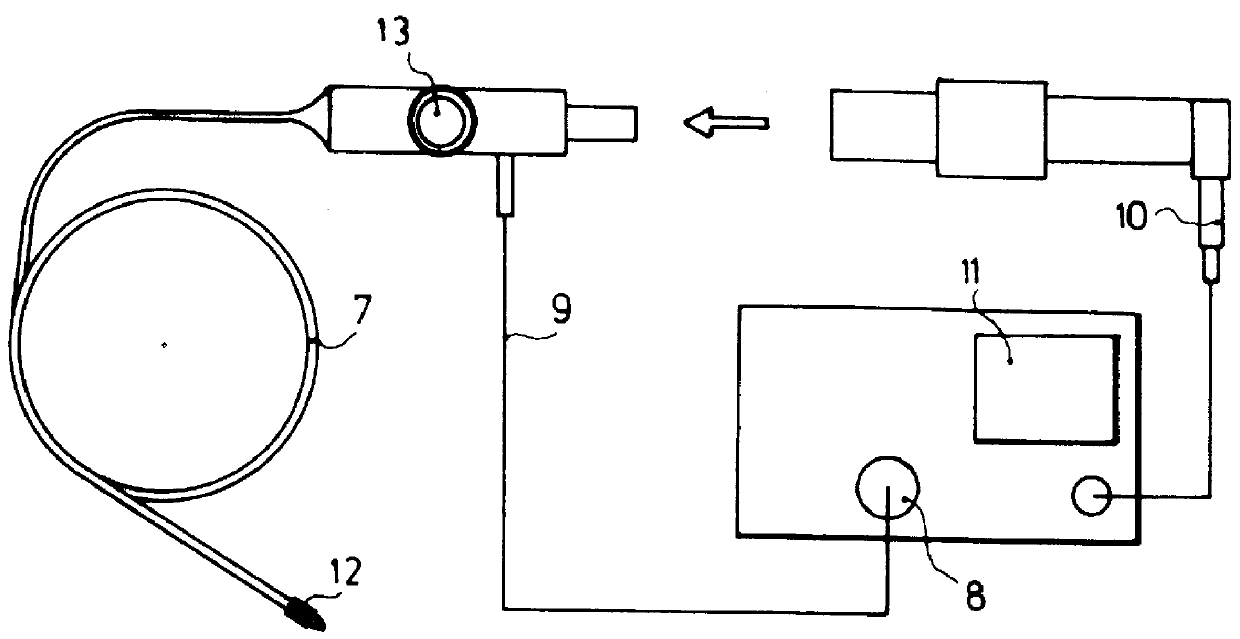
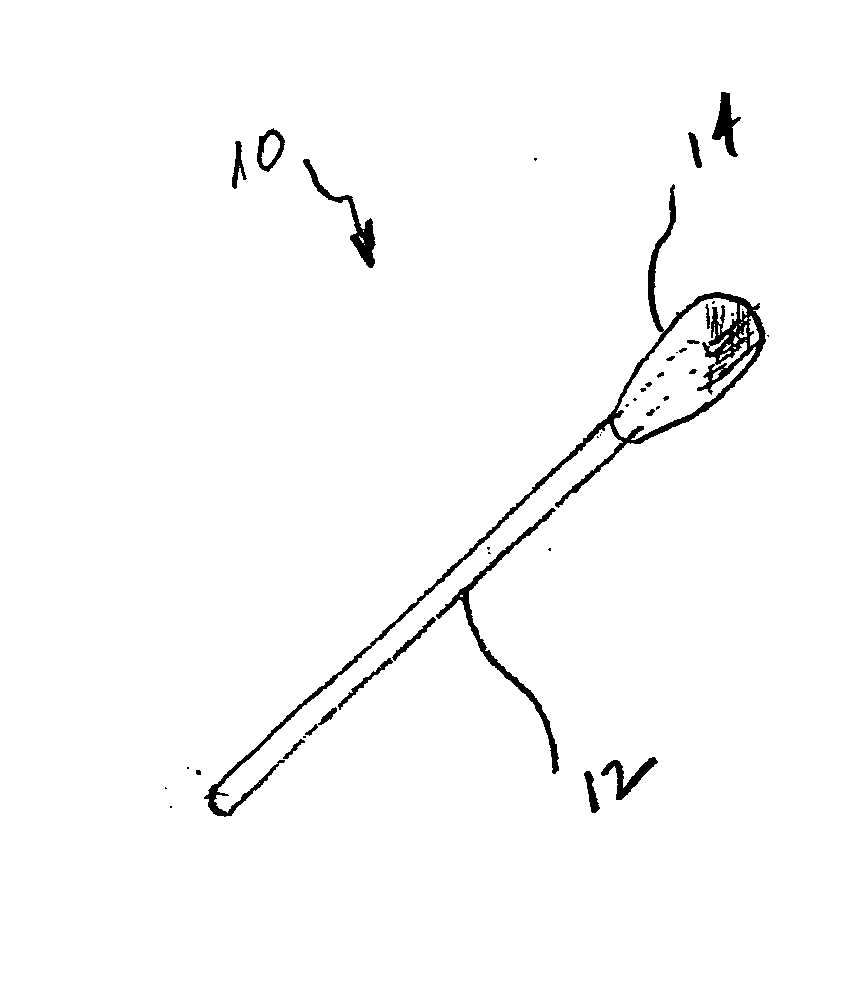
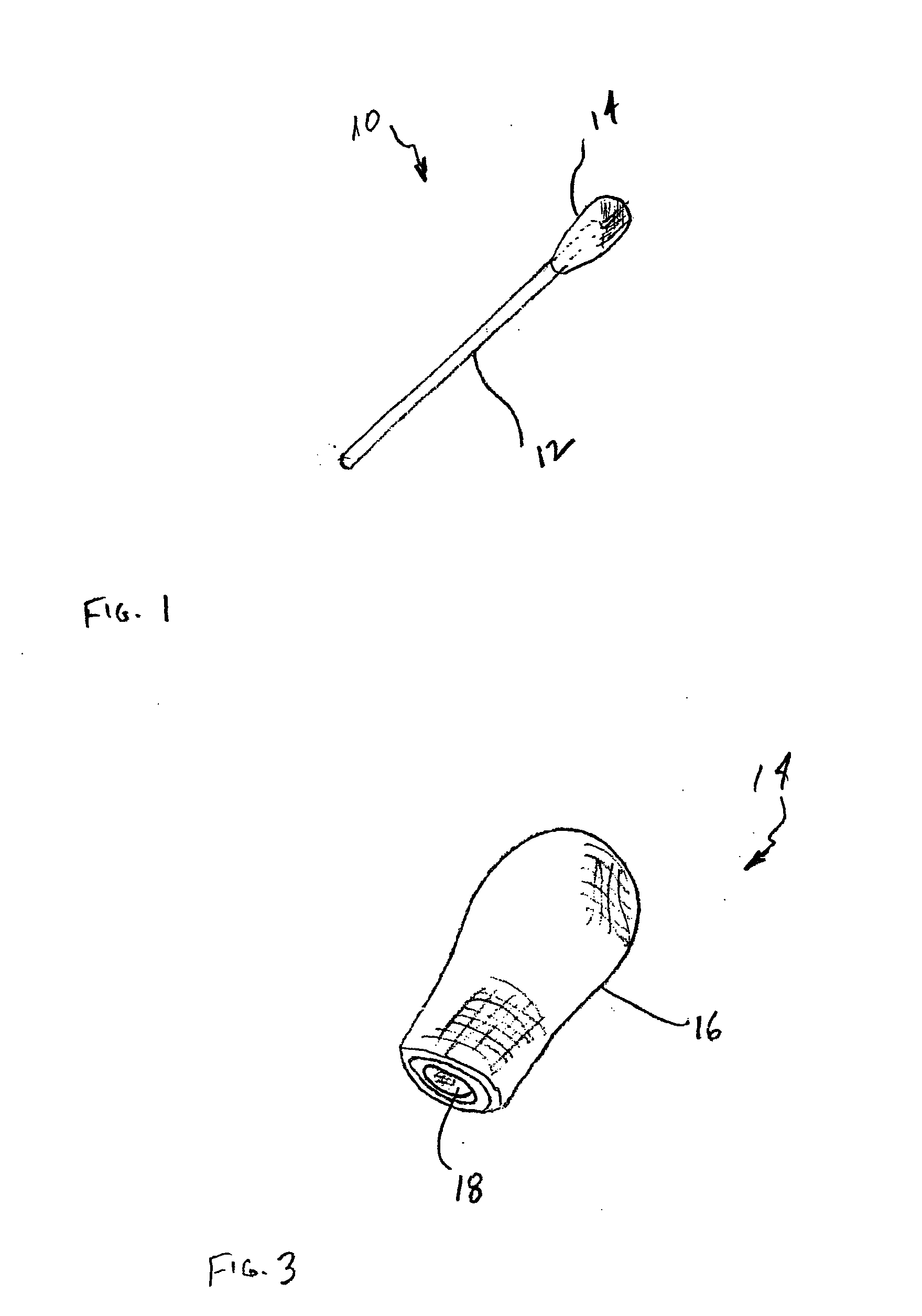
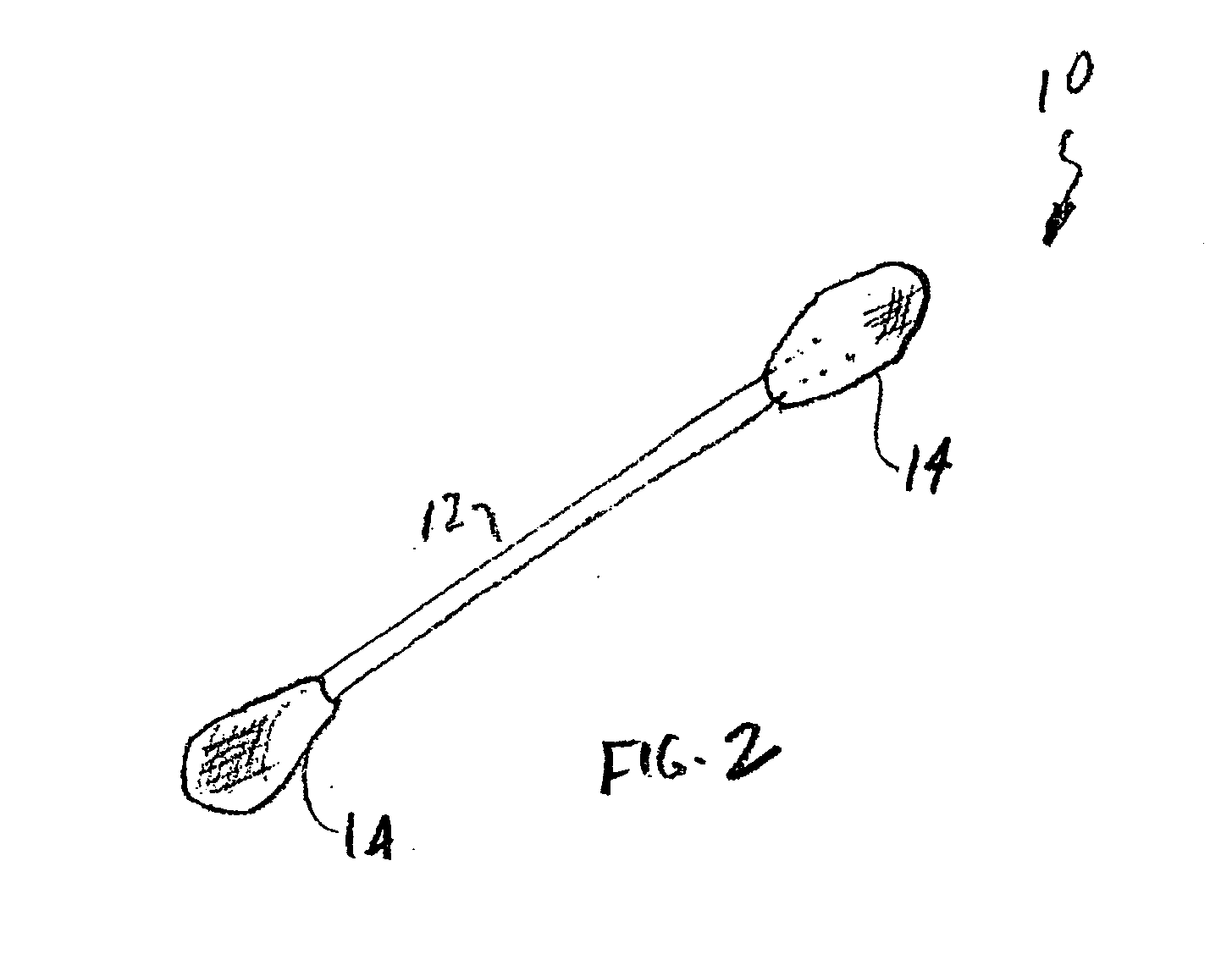
Swab device and kit for the delivery of blood clotting materials to a wound site
InactiveUS20070004995A1Easily woundGood coagulationPlastersMedical applicatorsMolecular sieveParticulates
A swab insertable directly into a wound or into a body cavity to treat a wound comprises an elongated member having material attached at one or both ends thereof. The material may be or may include a molecular sieve material such as zeolite. A swab for promoting the clotting of blood at a wound site comprises a frangible straw containing a molecular sieve material in particulate form and at least one contact pad attached to the straw. A kit for the treatment of a bleeding wound includes a swab (which may be a conventional swab or a swab having molecular sieve material attached at one or both ends), a carrier material, and a molecular sieve material in particulate form.
Owner:HORN JEFFREY L +1
Imaging system
InactiveUS9939628B2Imaging be cheapEffective lightingMechanical apparatusPlanar/plate-like light guidesLight beamWaveguide
An imaging system suitable to provide an image of a surface portion of an object is disclosed. The system includes a light source arranged to provide a light beam, at least a first optical waveguide having a first face and having a second face opposite to the first face, the first face having an incoupling surface. The optical waveguide includes an outcoupling surface, a first diffraction grating arranged on the optical waveguide, and an imaging subsystem arranged to the outcoupling surface. The first diffraction grating is arranged to outcouple at least a fraction of the light beam.
Owner:CSEM CENT SUISSE DELECTRONIQUE & DE MICROTECHNIQUE SA RECH & DEV
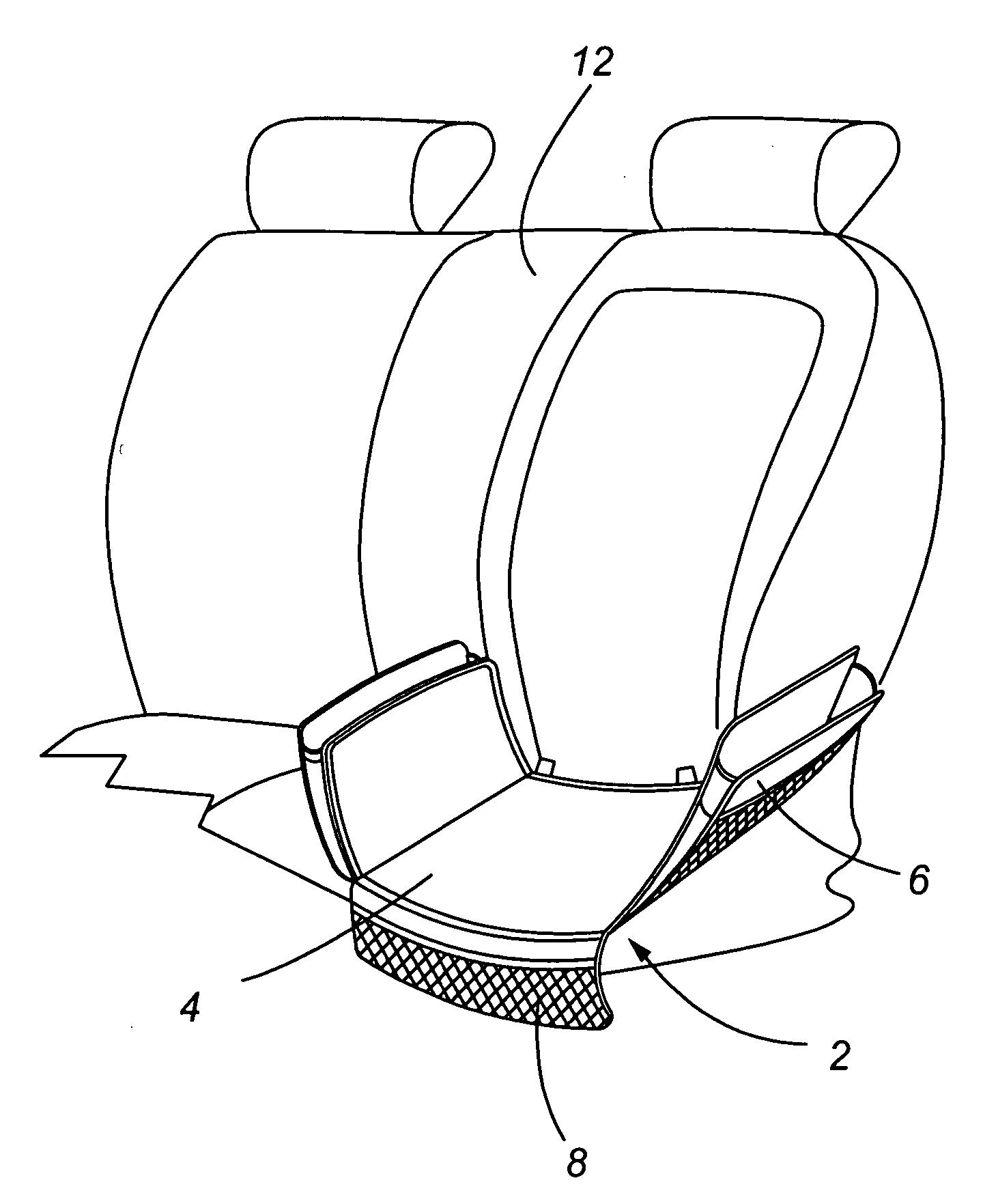
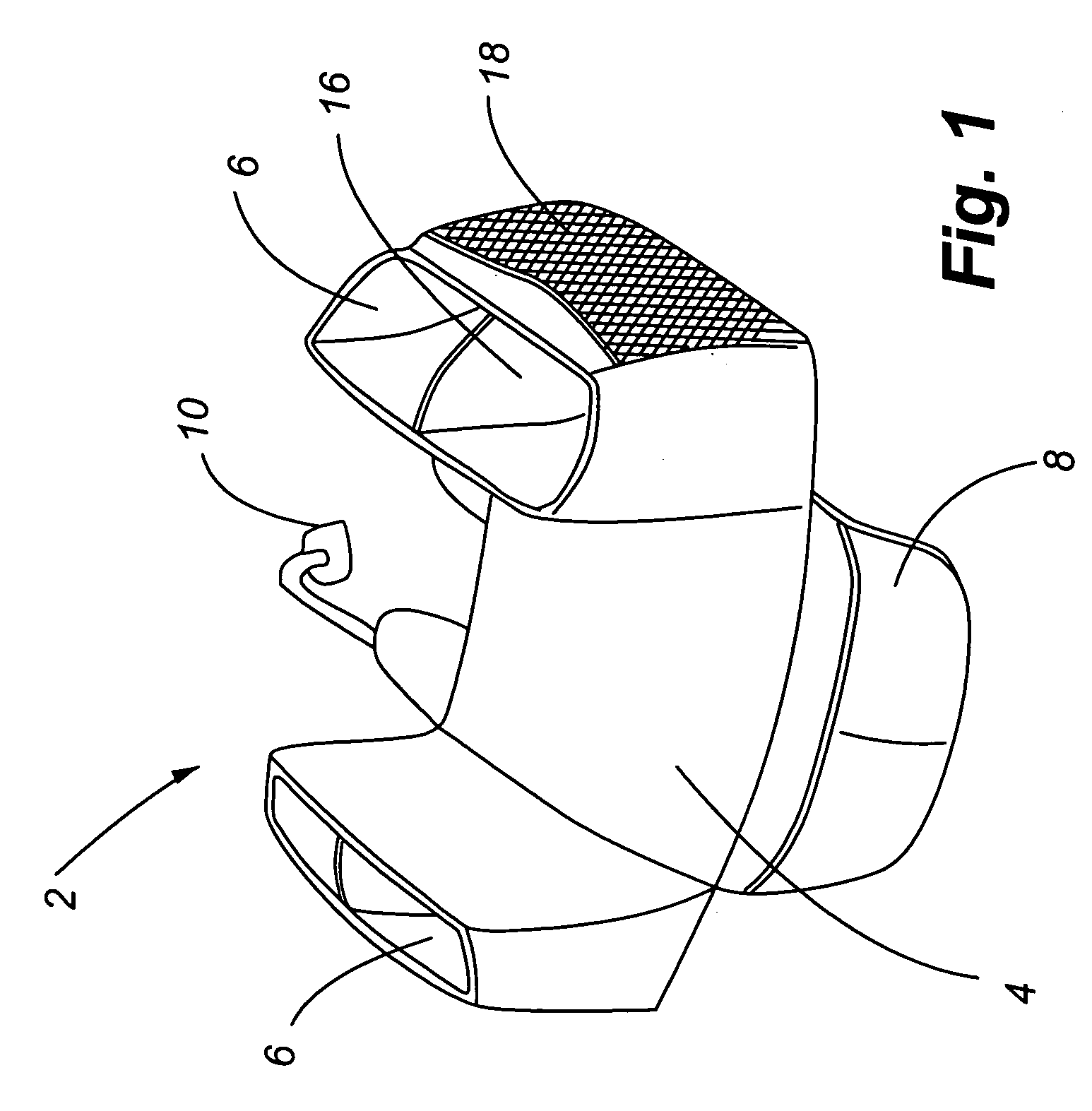
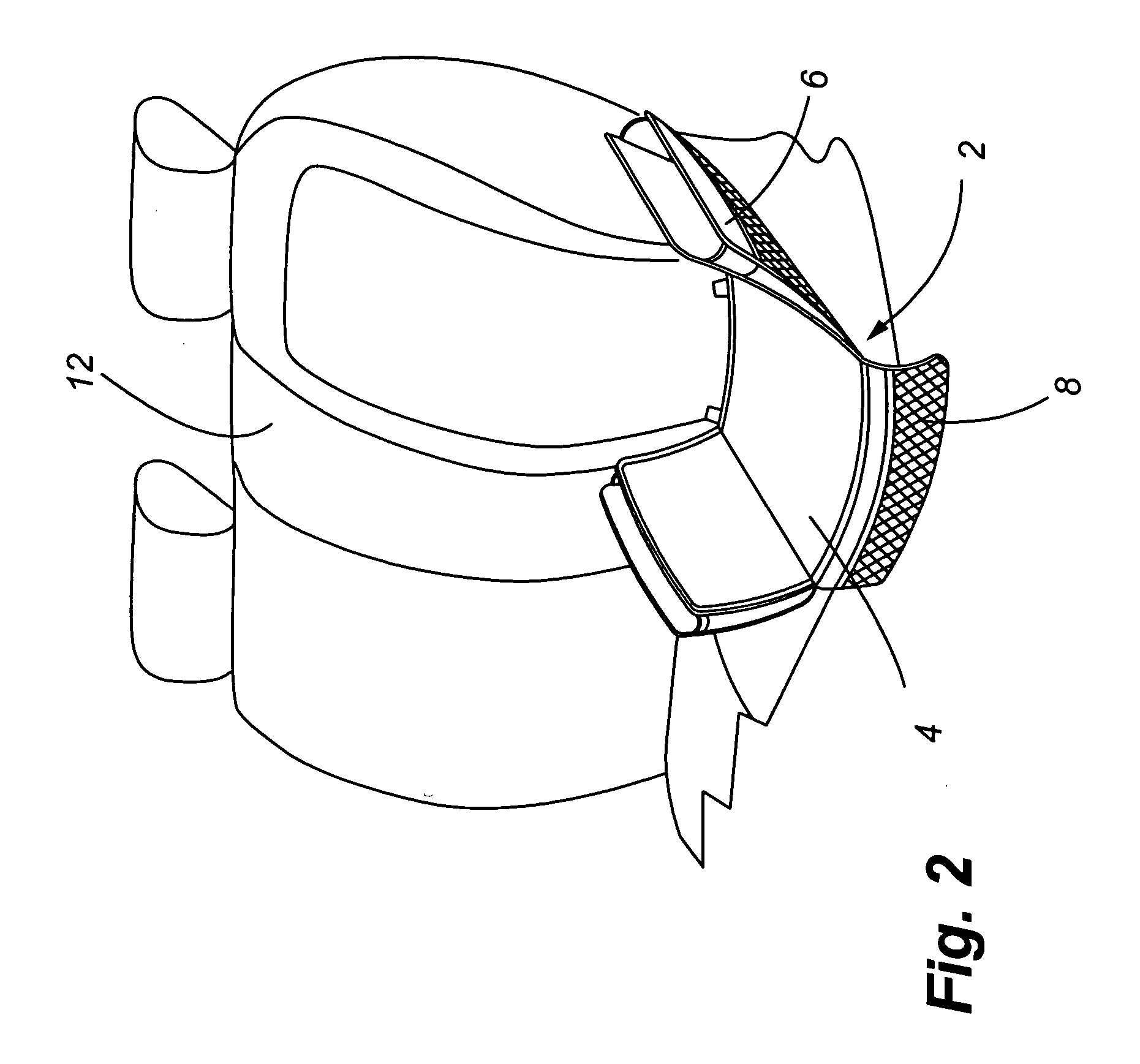
Child seat organizer for use in automobiles
InactiveUS20060049674A1Increase lifePrevent lifeSeat coveringsStoolsAutomotive engineeringAerospace engineering
A child seat organizer is provided for placement between a child safety seat and a vehicle seat, and which includes a barrier for placement on the vehicle seat that is adapted to receive the child safety seat and is easily secured to the vehicle seat to prevent unwanted movement. In addition, one or more storage compartments may be interconnected to the barrier and are located adjacent to the child safety seat when it is placed on the barrier.
Owner:CASE LOGIC
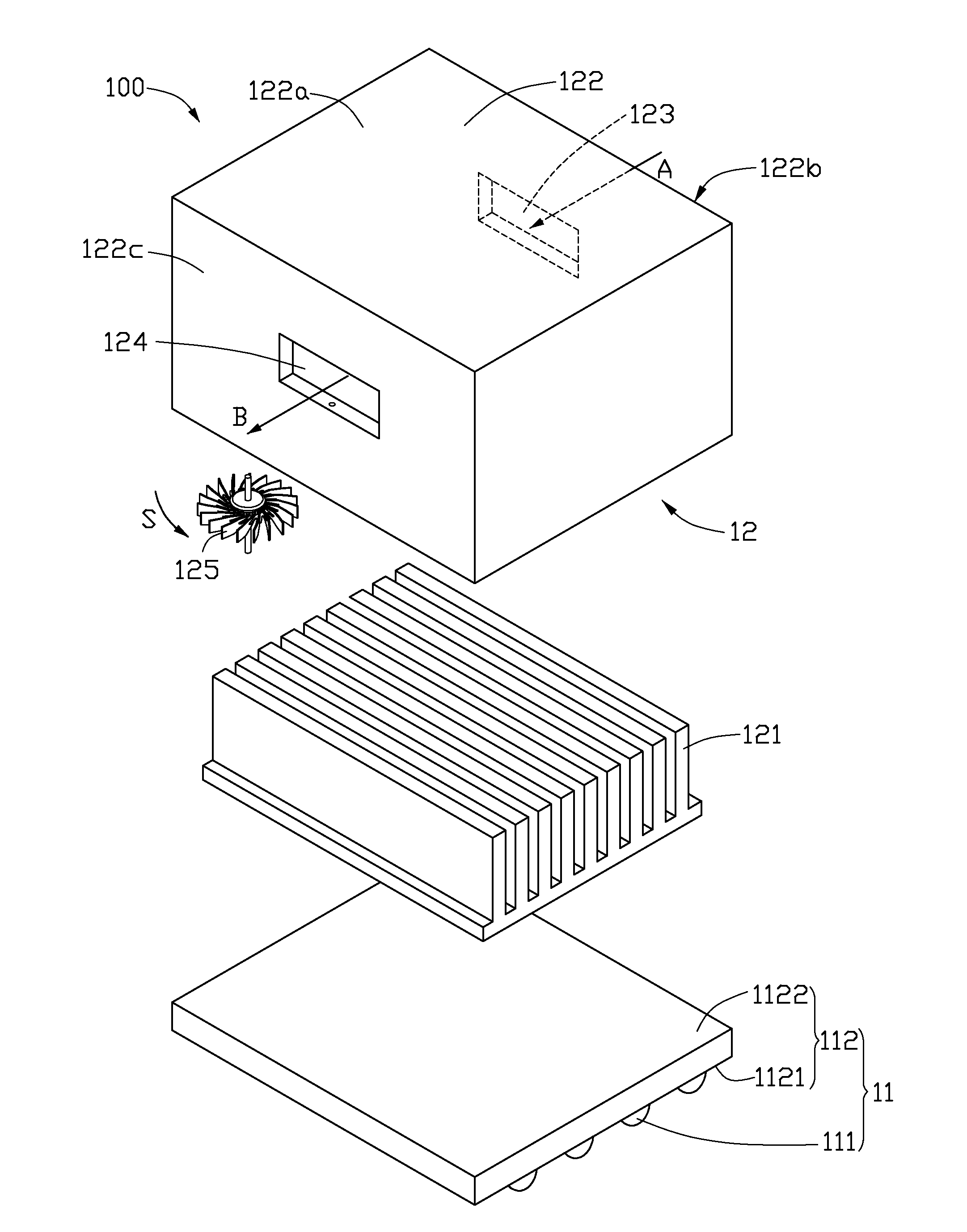
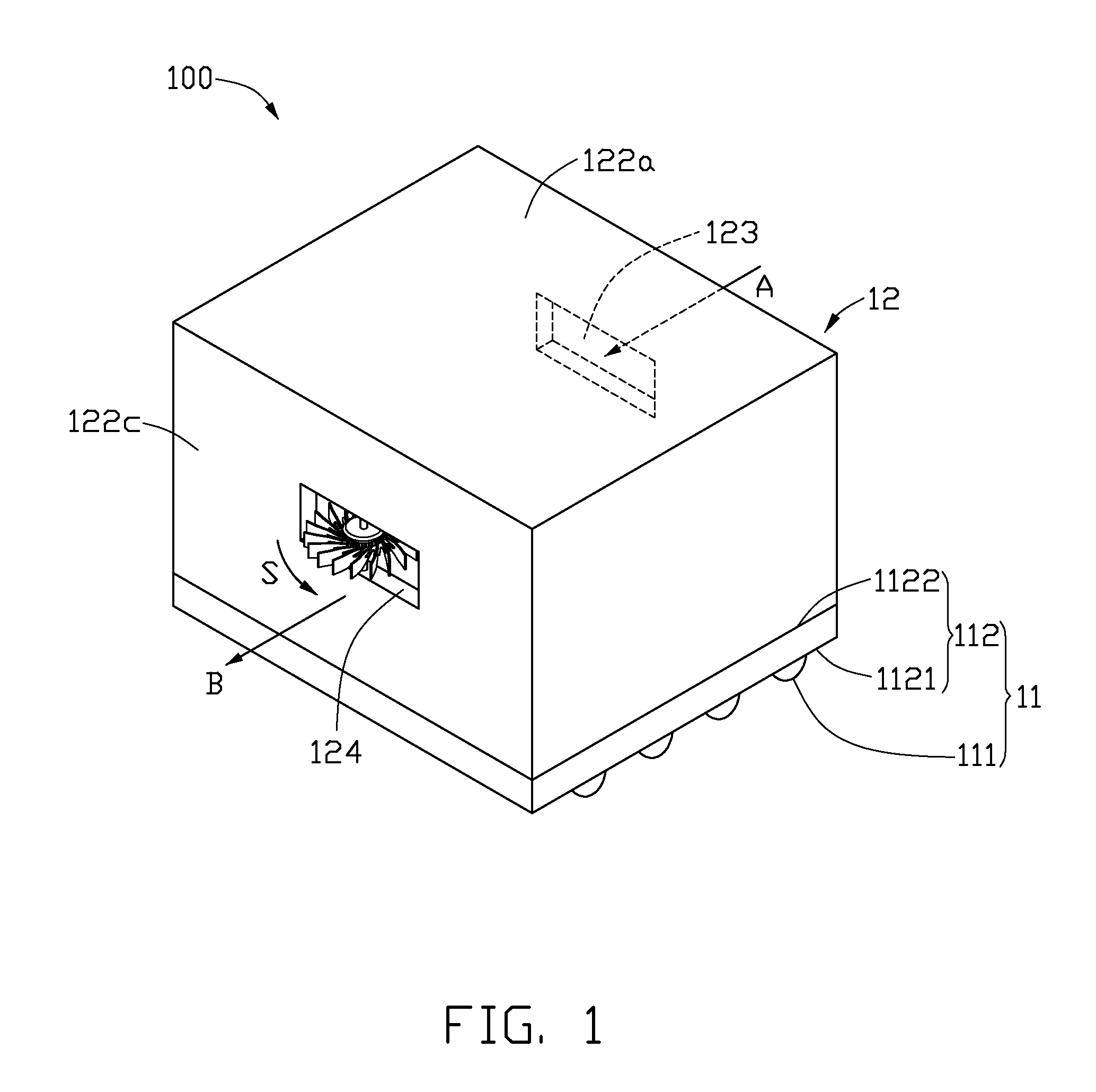
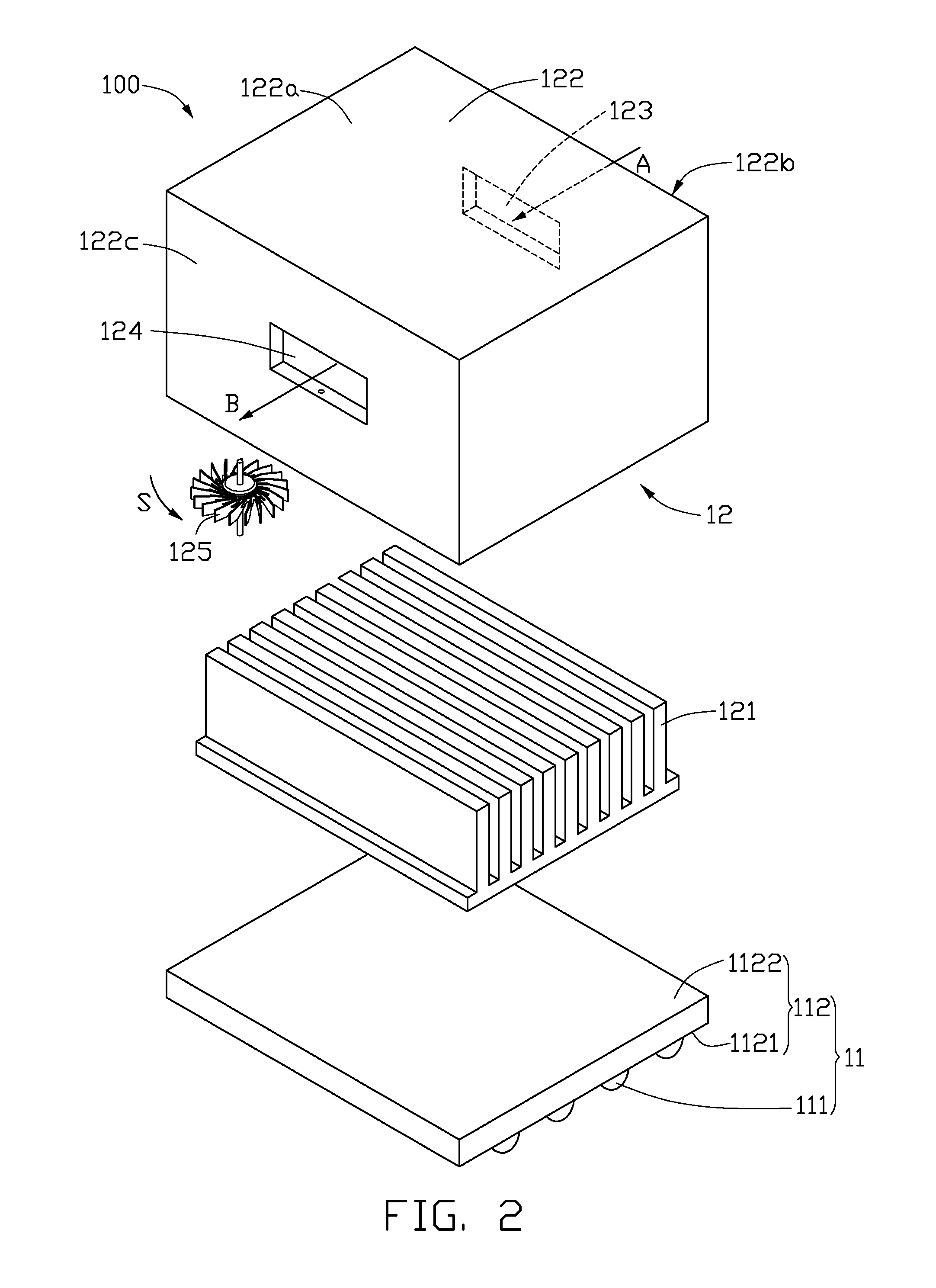
Illumination device
InactiveUS20100328949A1Difficult to accessImprove efficiencyPlanar light sourcesLighting support devicesEngineeringLight-emitting diode
An illumination device includes a light source and a heat dissipation device. The light source includes a base and at least a light emitting diode on the base. The heat dissipation device includes a fan for dissipating heat from the light source, and a hollow shell. The hollow shell has an inlet and an outlet defined thereon. The fan is located on the hollow shell, and the airflow from the fan is parallel to a rotation plane of the fan. In operation, air is impelled from the hollow shell by the fan, and heat from the light source is evacuated by airflow from the inlet to the outlet, and air pressure in the shell is reduced. Cool air flows into the hollow shell through the inlet.
Owner:FOXSEMICON INTEGRATED TECH INC
Method and apparatus for accessing secured electronic data off-line
ActiveUS20170116431A1Facilitate access control managementGood synchronizationKey distribution for secure communicationCryptography processingClient-sideElectronic data
Method and Apparatus for access secured electronic data are disclosed. According to one aspect, an off-line access mechanism in a client machine is activated to facilitate those users on the go to access secured electronic data. When a user decides to be away from a network premises or on a business trip, an off-line access request may be generated by the off-line access mechanism and forwarded to a server. In response, the server may grant the off-line access request to the user as well as the client machine from which the user will access the secured electronic data off-line. Depending on implementation, the AC may provide amended or tentative access rules, access privileges or user keys that will automatically expire when a predetermined time ends or become invalid the next time the client machine is connected to the server.
Owner:INTELLECTUAL VENTURES I LLC
Pet Toy with Multi-Function Modules
ActiveUS20180000048A1Quickly and effectively reboundDifficult to accessTaming and training devicesEngineeringCompanion animal
A pet toy includes an anchor member and at least one ring member connected thereto. The ring member has a noise making device. In one embodiment, the noise producing feature includes a squeaker protected within a housing disposed within the interior of the toy. In another embodiment, the noise producing feature includes multiple layers of material with one of the layers producing sound. When an outer shell of the ring member is deflected or compressed by contact, noise is produced by the noise making device.
Owner:STONE JOHN JAMES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com