[0010]The means for deterring access to the ACT may involve constructing the ACT to make it virtually impossible to
gain access to its stored data without disabling it sufficiently so as to render access to the data very difficult or virtually impossible. In one embodiment, the ACT is made difficult to access by making it so small that a
hacker will find it difficult to effectively tap into its circuitry. Difficulty of access to the ACT may also be enhanced by sealing the ACT, only exposing the
communication interface. In another embodiment, the ACT can be manufactured to break when an attempt is made to access the interior of the ACT. Alternatively, the ACT can be manufactured so that when it breaks the non-
volatile memory that is stored on it, including any keys stored in the memory or elsewhere in the ACT, is automatically erased. By combining two or more of these features, the security provided by the ACT is even further enhanced.
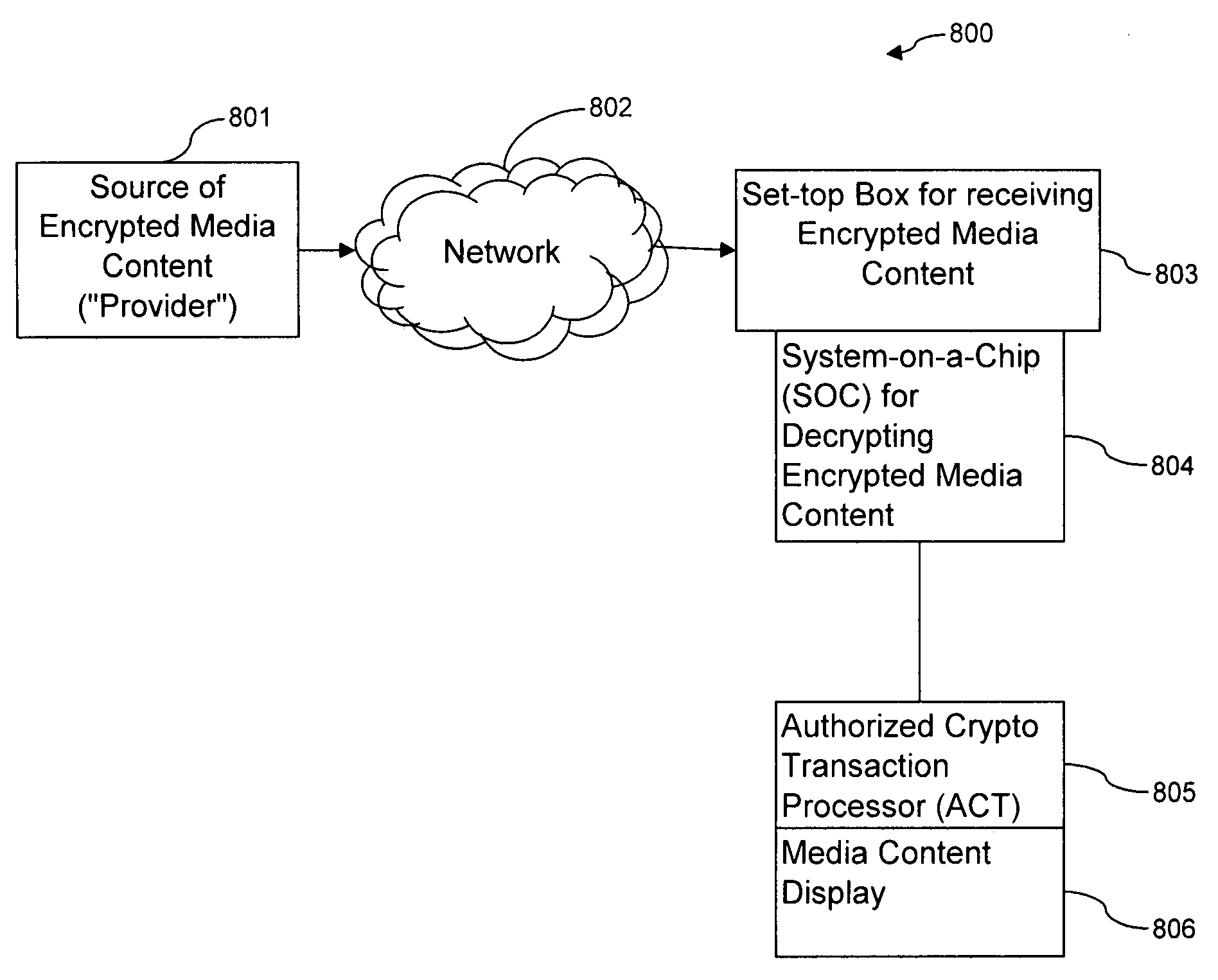
[0011]In a further embodiment of the ACT, it is directly attached to a secure
system-on-a-
chip (SOC), the SOC in turn being directly linked to a computer. An SOC, when attached to an ACT, adds to the functionality of the ACT in at least the following ways. After the proper
authorization is transmitted to the ACT by the SOC, such as presenting the ACT with player keys, the SOC receives the title keys from the ACT. The SOC uses these title keys to decrypt encrypted media content. To improve the decryption step, the SOC may have an input interface with a speed of at least approximately the
frame rate of the encrypted media content, such as a video. Additionally, the SOC may have an output interface with a speed of at least approximately the pixel rate of the decrypted, uncompressed media content.
[0013]Currently, when the media content is decrypted and uncompressed within a computer, a set-top box, or a stand-alone player, the decrypted and uncompressed media content is transferred to the display using
HDMI—a standard that is used to transmit data between the player and the display. HDCP is the
encryption protocol used for transferring this uncompressed media content from the player to the display. Unfortunately, HDCP is not as secure as is needed for insuring secure transfer of the encrypted media content to the display. The media content encrypted with this weak
encryption protocol can be intercepted and decrypted without
much difficulty. Therefore, the second and third of the exemplary embodiments—directly attaching the ACT to the media content display while the SOC is directly linked with the computer, or directly attaching the ACT to the SOC and directly attaching the SOC to the media content display—are advantageous because they allow for the media content to be more securely sent to the media content display.
[0014]The second embodiment of the ACT and SOC
system involves the SOC being directly linked within a computer, set-top box, or stand-alone player, while the ACT is in communication with the SOC, but is directly attached to the means for displaying the media content, such as a monitor for displaying media content. In the third embodiment, the ACT can be directly attached to the SOC while the SOC is directly attached to the means for displaying the media content. What both of these embodiments address is the weak link in the transfer of decrypted media content from a media content player to a media content display. Each of these embodiments enables the transmission of strongly encrypted or re-encrypted media content to the media content display—where it is securely decrypted by the powerful ACT-SOC
system—thereby more effectively protecting the media content during its transmission from the computer, set-top box or stand-alone player to the media content display.
[0016]Some specific aspects of this embodiment are now introduced. First, multiple providers can have their title keys stored simultaneously within the ACT. Currently set-top boxes are given to a user by a single provider, and only that provider is able to store its title keys on the set-top box. Second, with the ACT able to maintain the security of the title keys stored on it—whether encrypted or decrypted—even over extended periods of time, the sending of the title keys can be decoupled from the sending of the encrypted media content. The title keys can even be sent to the user's media content player or users media content display well in advance of the user receiving the encrypted media content. Also, the title keys can be held securely on the ACT and used multiple times. This gives added flexibility to the business relationship that can be established between the user and the media content provider. These options of sending the keys well in advance of the user playing the media content and keeping the keys for multiple uses are risky options with current computer processor models because, currently, the computer has no place to securely store the title keys. Therefore, currently the media content provider most often sends the keys as close as possible in time to the user's playing of the media content in order to minimize the length of time during which the title keys—once decrypted—are in the computer's memory. Likewise, in current systems, soon after the media content is decrypted with the decrypted title keys, these title keys are ideally erased in order to avoid a
hacker from getting access to them. As explained, the current invention enables separating in time the transmission of the keys from the transmission of the media content.
 Login to View More
Login to View More  Login to View More
Login to View More