Ransomware real-time detecting and defending method based on file request monitoring
A file request and real-time detection technology, applied in the field of system security, can solve problems such as difficulty in using protected hosts, neglect of file recovery, and difficulty in backup, achieving lightweight deployment, improving defense capabilities, and ensuring Recoverable effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The content of the present invention is described in more detail below:
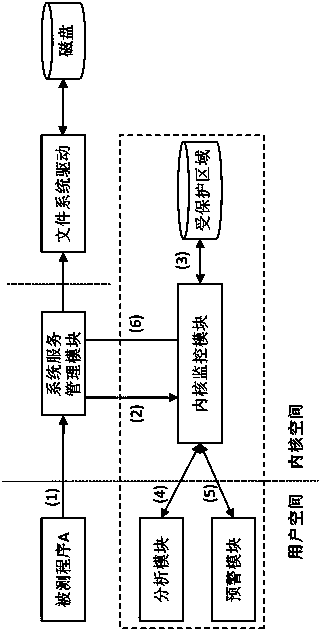
[0029] A schematic diagram of the implementation process of a ransomware real-time detection and defense method based on file request monitoring is attached figure 1 shown. Wherein the dotted line box is each constituent module that the invention comprises. A lightweight monitoring module exists in the kernel space. This module will combine with the system service management module to intercept and redirect the input / output request packet (IRP) of the program under test, record the write or delete operation of the file, and These file operations are managed and performed in the region. In addition, it was invented that there are daemon processes in the user space, which are respectively called the analysis module and the early warning module. The analysis module calculates the suspiciousness score of the tested program, and the early warning module is used to prompt the user of possible maliciou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com