Cyber attack early warning system
a cyber attack and early warning technology, applied in the field of cyber security, can solve the problems of network devices being targeted for attack by malware, influencing or attacking normal operations, and malware becoming a pervasive problem for internet users,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
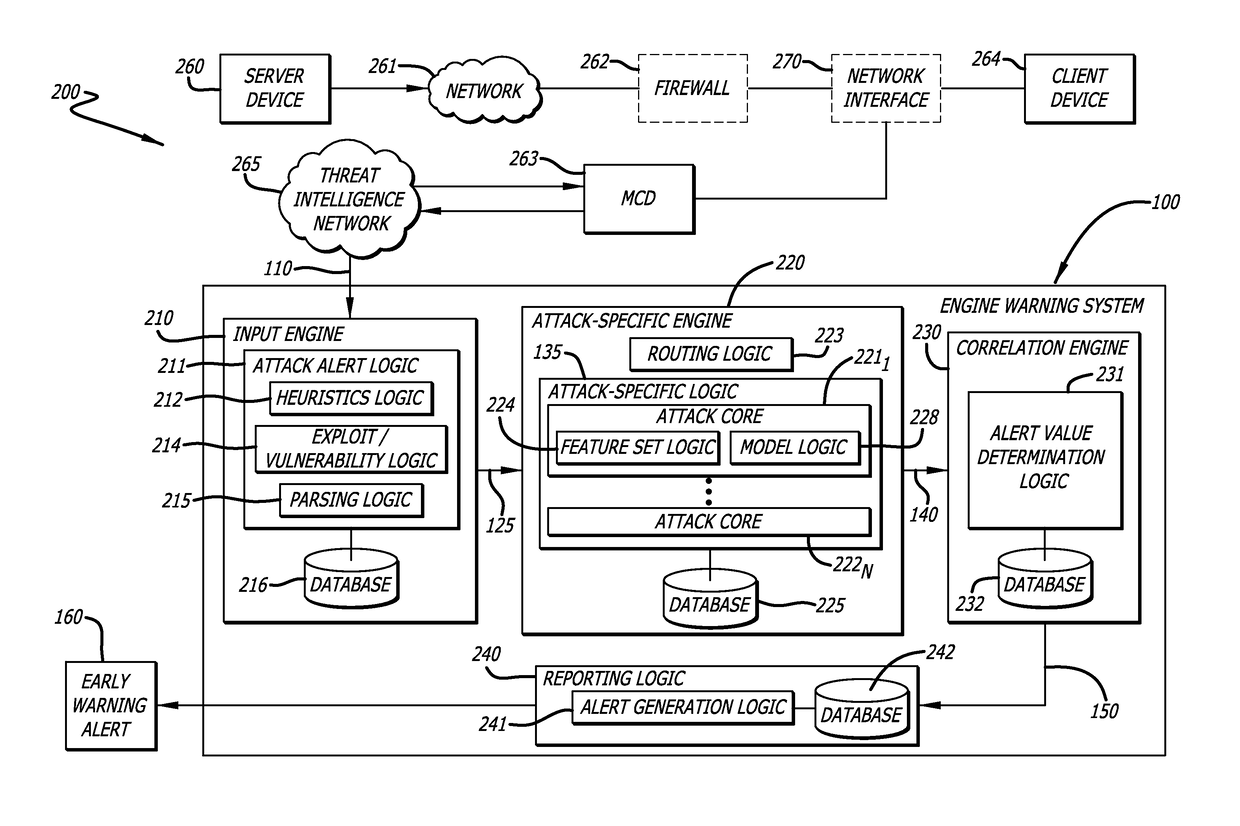
[0012]Embodiments of the present disclosure generally relate to a cyber attack early warning system that is configured to predict and notify probable targets of a potential malware attack prior to its occurrence.
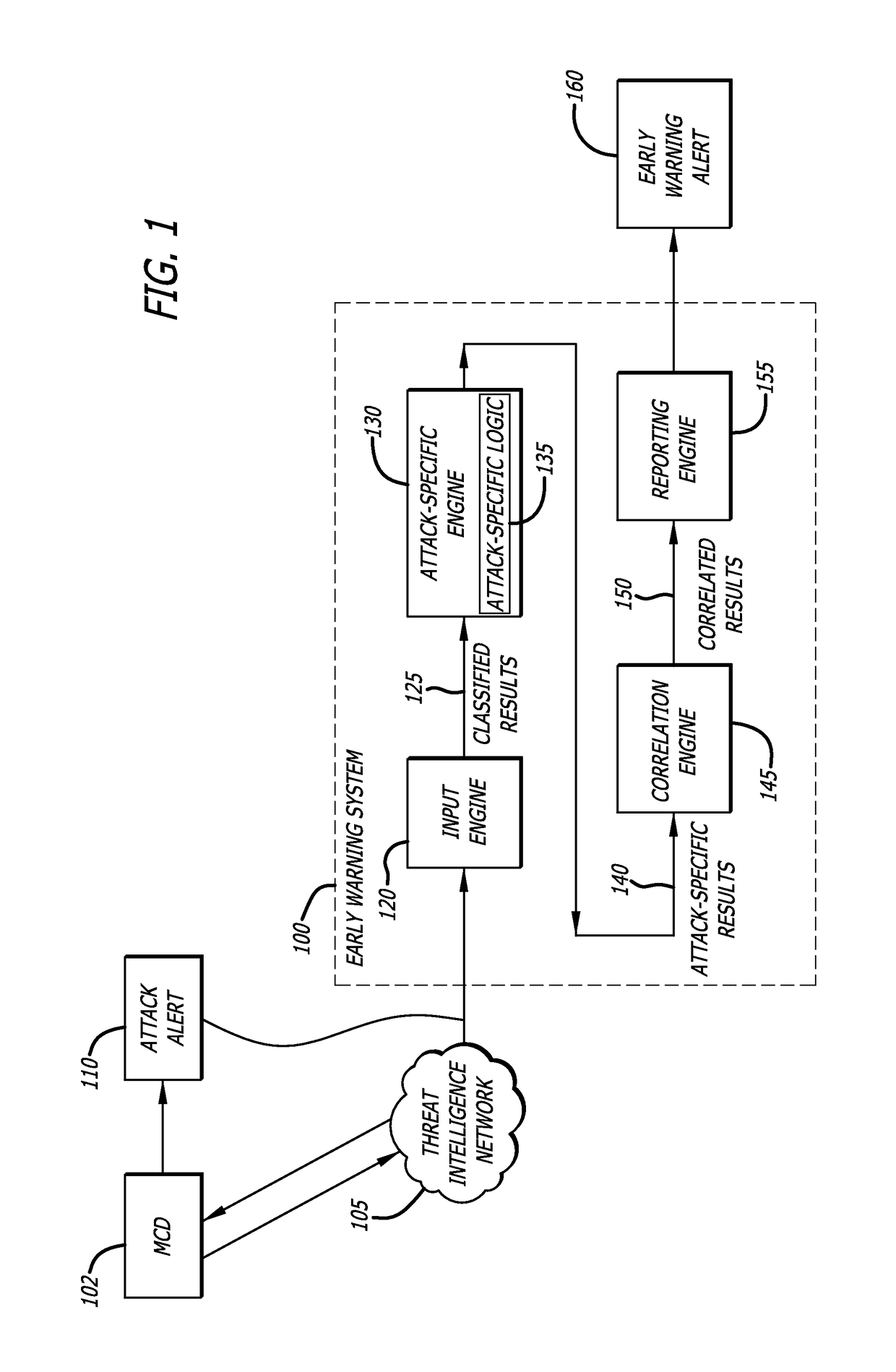
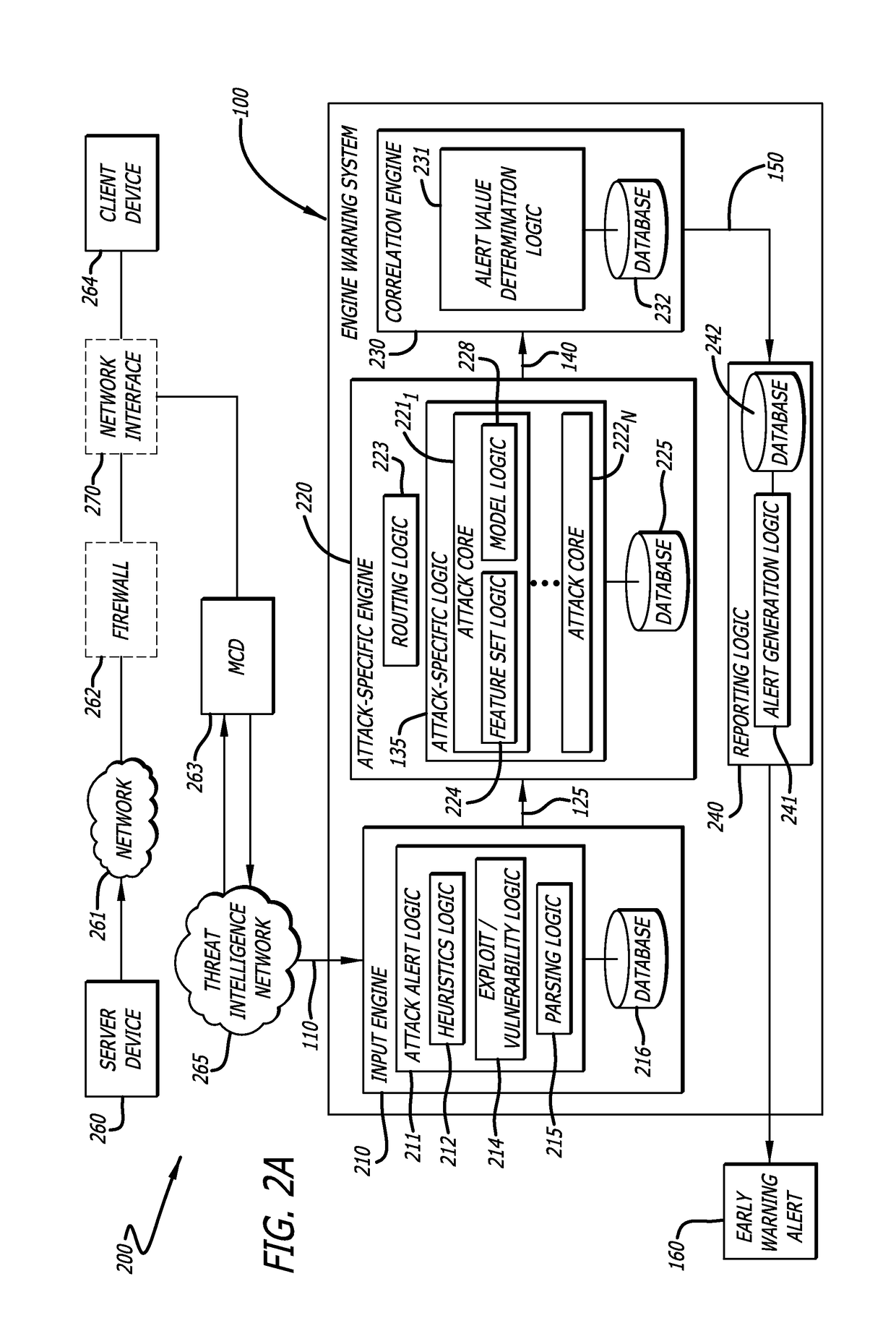
[0013]According to one embodiment of the disclosure, network traffic is analyzed such that malicious network traffic is filtered and preferably prevented from executing, using a remote source. Herein, upon detection of potentially malicious network traffic, the remote source is configured to generate an “attack alert” that is communicated to the cyber attack early warning system, which comprises an input engine, an expert engine, a correlation engine, and a reporting engine.
[0014]When the attack alert is received by the cyber attack early warning system, the attack alert is analyzed and classified. For example, the attack alert may correspond to any of various malware attack types, including without limitation Advanced Persistent Threats (APT), Point-Of-Sales attacks (POS), ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com