Threat intelligence-based network threat identification method and identification system
An identification method and identification system technology, applied in the field of network threat identification method and identification system based on threat intelligence, can solve the problems of inconvenient network attack traceability analysis, inaccurate judgment, and lack of correlation analysis, etc., to achieve convenient traceability and Post-processing, efficiency improvement, and low false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
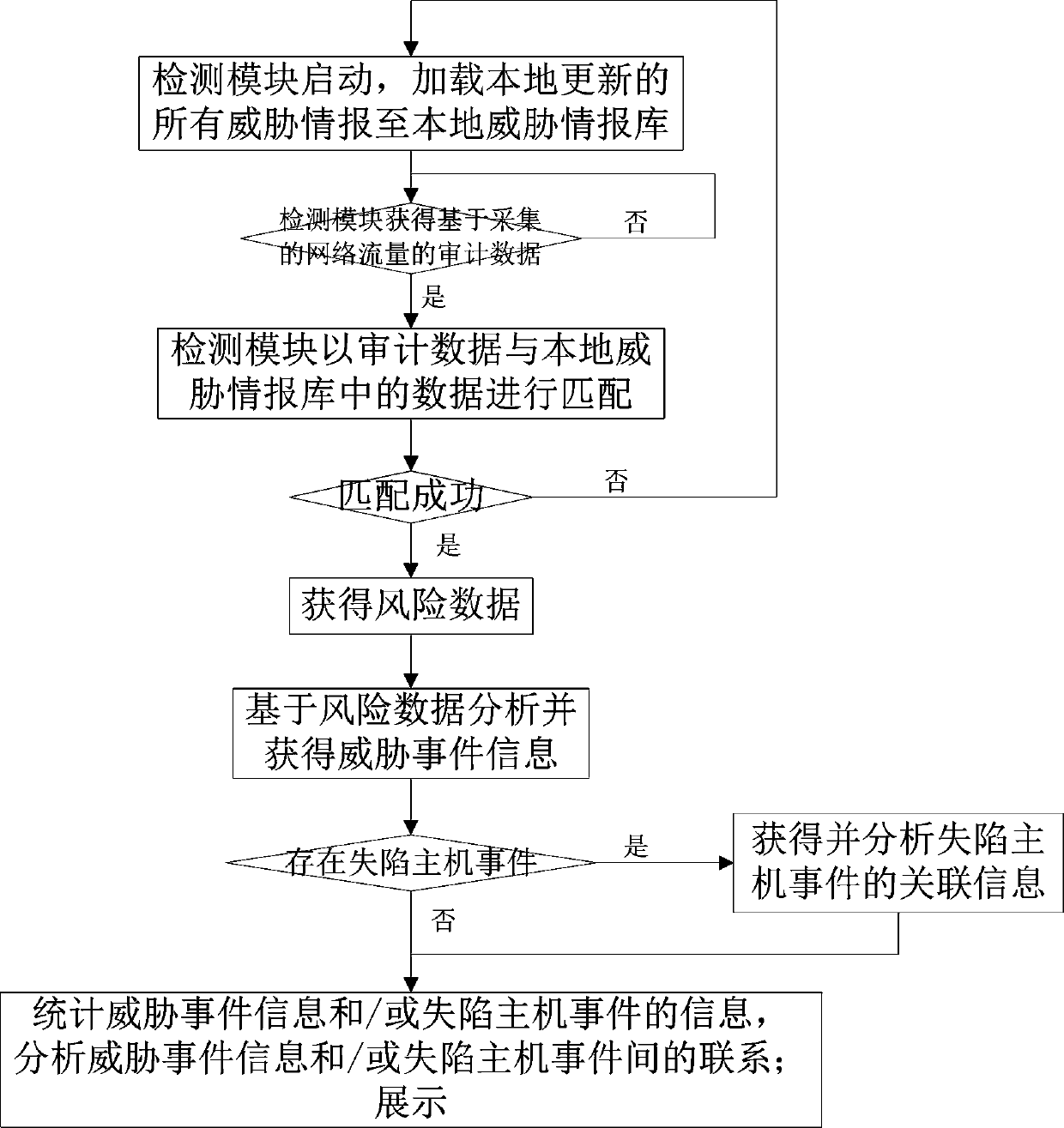
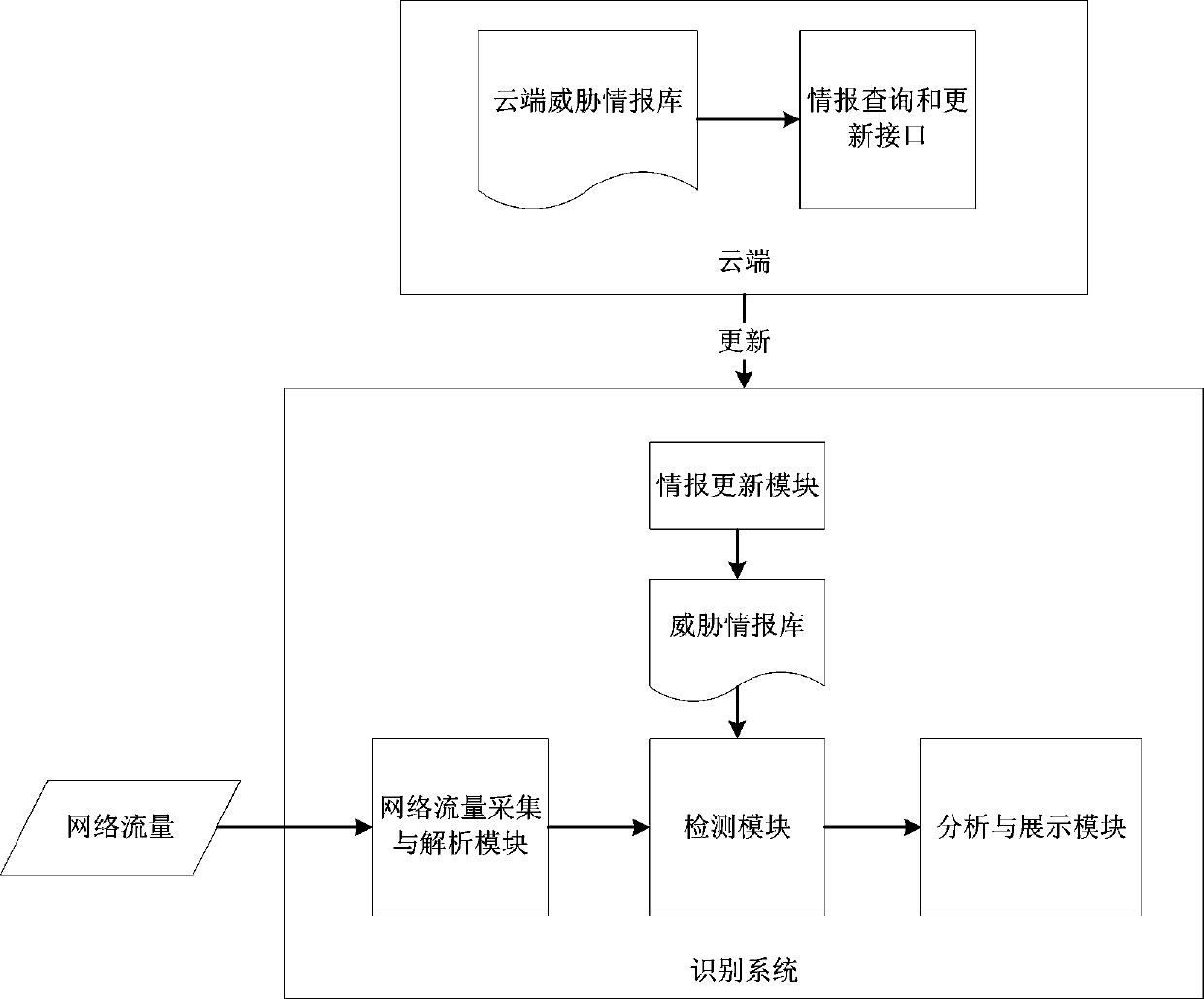
[0069] Example 1: A compromised host on the intranet periodically accesses a certain C&C domain name, and the attribution label of the domain name in the intelligence database is "malware", so it is necessary to check whether the access of the device is an operation of uploading data (after collecting data upload), whether to periodically try to download files (may be used by malware to update a certain component of itself), or to receive instructions for the next attack behavior.
Embodiment 2
[0070] Example 2: Multiple compromised hosts have accessed the same mining server (there is a flag in the threat intelligence database, which marks the domain name as belonging to the mining pool server), and they frequently interact with the server and send the same or similar requests, then it can be judged that these The device is controlled by an active mining botnet.
Embodiment 3
[0071] Embodiment 3: It is detected that a vulnerability exploit event has occurred in a compromised host in the protected network, and the host attempts to send a vulnerability exploit message to other devices in the same network, then analyze the subsequent network behavior of the compromised host, for example, the host may It has been controlled and used as a springboard to scan other devices in the LAN to obtain further information.
[0072] Step 6: Make statistics of threat event information and / or lost host event information, analyze the relationship between threat event information and / or lost host event; display.
[0073] In said step 6, the statistical information includes threat event information and lost host event information;
[0074] The threat event information includes the event type, threat type, number of attacked hosts, number of attacking hosts, number of event occurrences, first occurrence time and latest occurrence time of the threat event information in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com