A method of identity authentication based on n-dimensional sphere
A technology of identity authentication and user identity, applied in the field of identity authentication based on N-dimensional sphere, can solve problems such as complex technology, high cost, and obstacles to promotion and application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
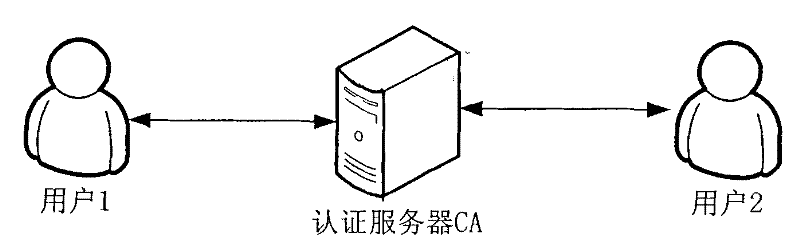
[0099] A typical identity authentication system architecture is as follows: figure 1 As shown, the system includes an authentication server (CA), and user 1 and user 2. The authentication server (CA) and each user are connected through the Internet.
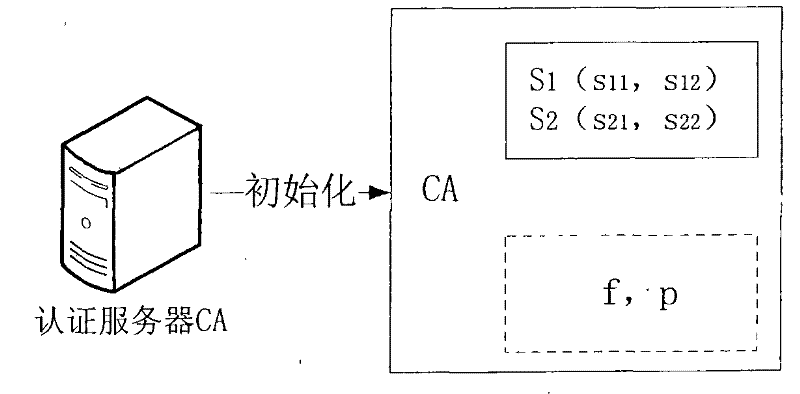
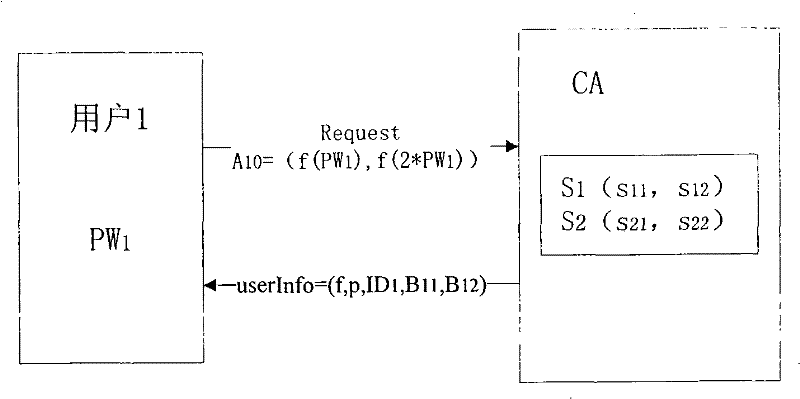
[0100] Such as figure 2 As shown in , after initialization, the authentication server (CA) sets relevant parameters, wherein the parameters in the solid line box are kept secret, and the dotted line boxes are public parameters. This embodiment selects the situation of N=2 to give a specific explanation, because in a 2-dimensional space, a "2-dimensional sphere" is actually a "circle", so in the following description, the term "2-dimensional circle" is used instead of "N Dimensional surface". As shown in the figure, the 2-dimensional vector S 1 and S 2 is a secret vector kept in secret (here, only a 2-dimensional vector is selected for simple explanation, and a higher-dimensional vector can be selected as a secret vector in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com