SDN-based SDP security group implementation method and security system
An implementation method and security group technology, which are applied in the SDN-based SDP security group implementation method and security system field, can solve problems such as destructive attacks, brute force cracking, and limited load capacity of a single point of SDP gateway, and achieve precise control, Strengthen security and prevent attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
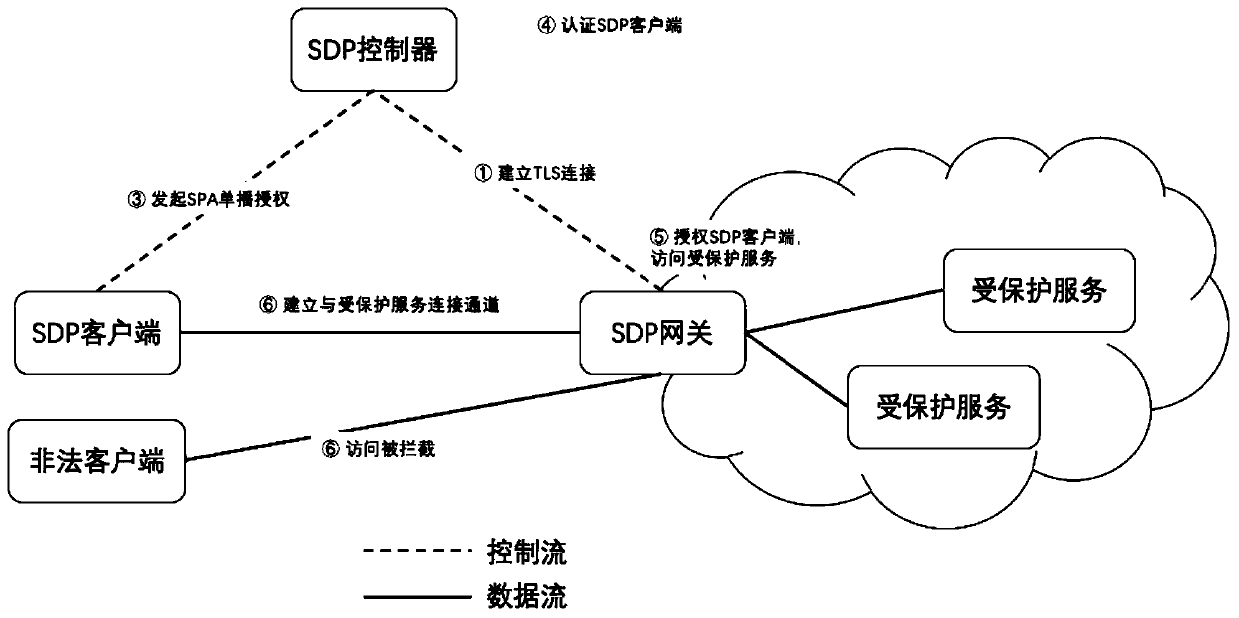
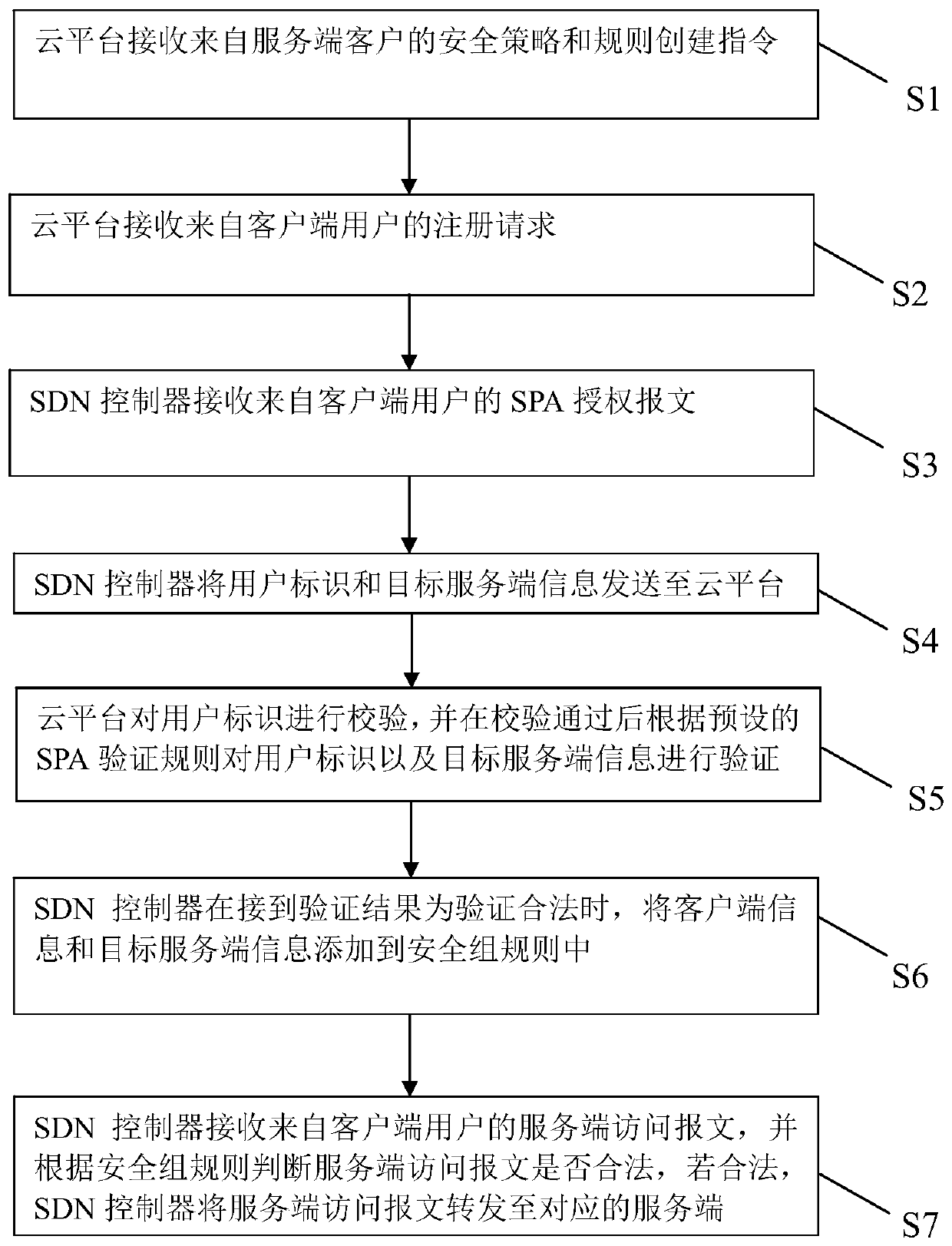
[0065] Such as figure 2 with image 3 As shown, this embodiment discloses a method for implementing an SDN-based SDP security group, the steps of which include:
[0066] S1. The cloud platform receives a security policy and rule creation instruction from a server client.
[0067] Specifically, the security policy indicates the network information of the protected server, including the IP address and port information of the server. Specifically, the cloud platform sends the security policy to the SDN controller, and the SDN controller generates SPA authorization message determination rules and server access message determination rules according to the security policy. The SPA authorization packet determination rule is used to determine whether any packet received by the SDN controller is an SPA authorization packet. The server access packet determination rule is used to determine whether any packet received by the SDN controller is a server access packet.
[0068] The secu...
Embodiment 2
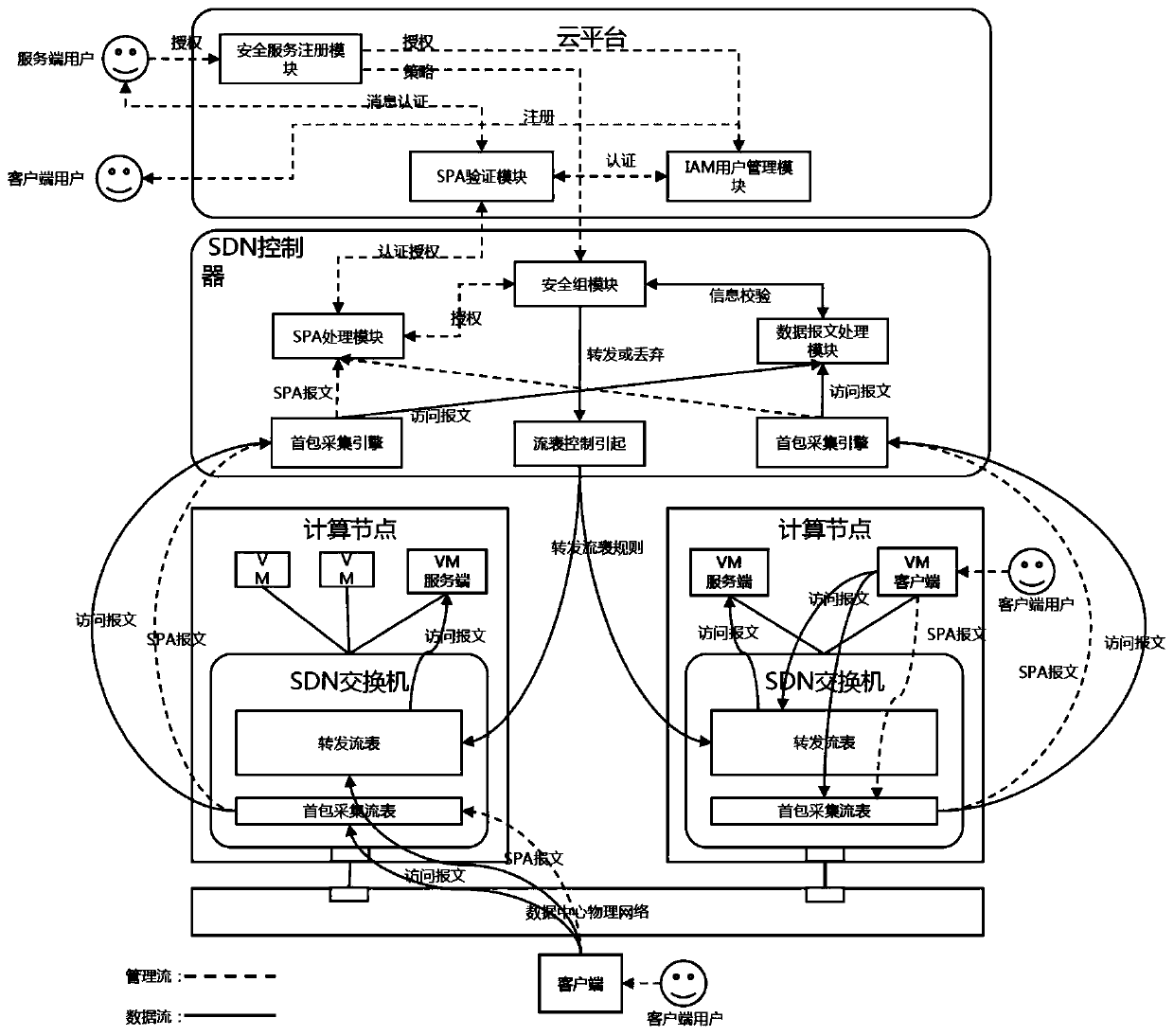
[0098] Such as image 3 As shown, this embodiment corresponds to the method for realizing the SDN-based SDP security group disclosed in Embodiment 1, and discloses a security system including a cloud platform, an SDN controller, and an SDN switch.
[0099] Specifically, the cloud platform includes a security service registration module, an SPA verification module, and an IAM user management module, and the SDN controller includes a first packet collection engine, an SPA processing module, a security group module, a data packet processing module, and a flow table control engine.
[0100] Specifically, the security service registration module is used to receive security policy and rule creation instructions from the server client. Specifically, the security policy indicates the network information of the protected server, including the IP address and port information of the server. Specifically, the cloud platform sends the security policy to the SDN controller, and the SDN con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com