Intrusion detection method and system based on honeynet arrangement, and storage medium
An intrusion detection system and intrusion detection technology, applied in the field of network security, can solve problems such as ineffective defense against unknown attack methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The principles and features of the present invention will be described below with reference to the accompanying drawings.
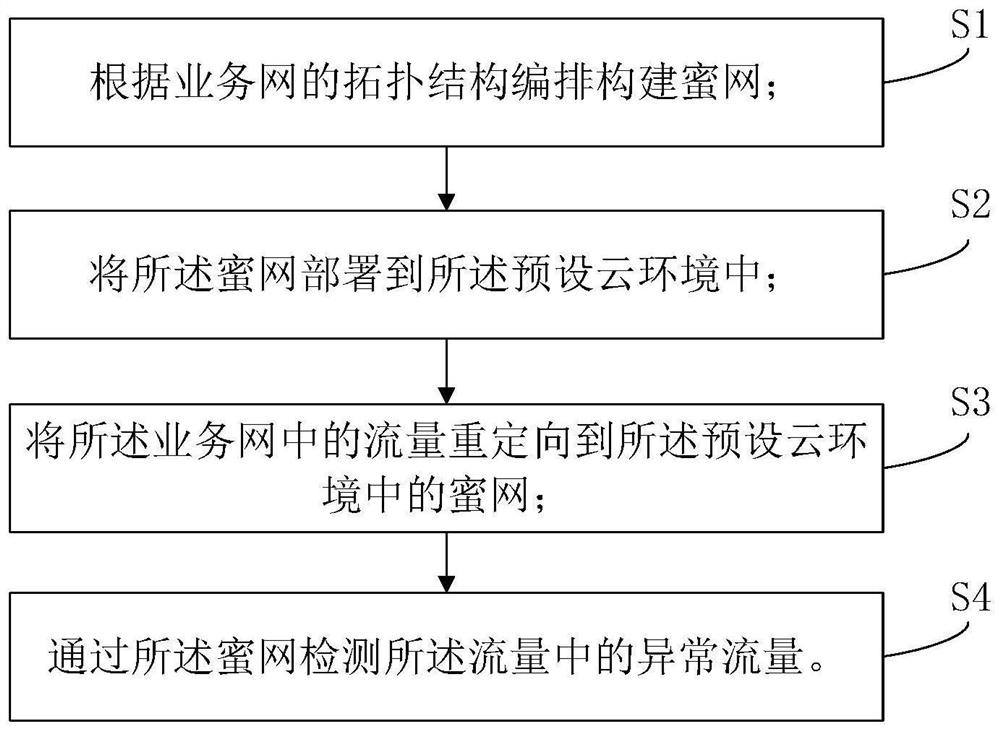
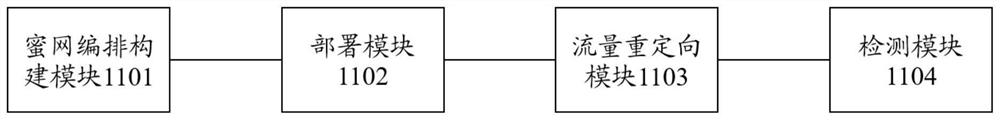
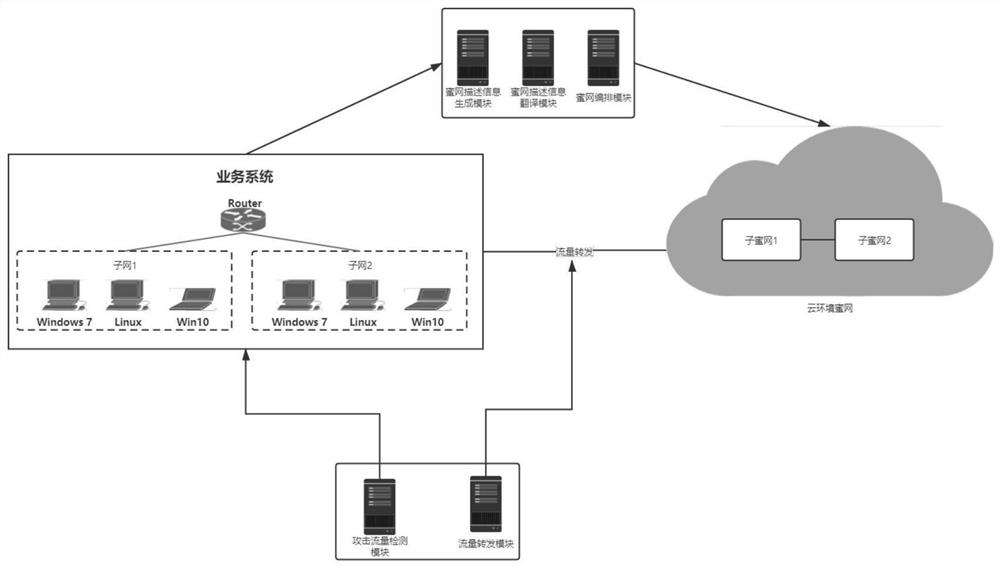
[0061] Such as figure 1 As shown, an intrusion detection method based on the embodiment of the present invention is provided, including: It is to be explained that honey network belongs to an active defense technology, and honey network is not trying to limit the access to the attacker, but The attacker interacts to identify the strategy and tools used. The vulnerability and monitoring system arranged in honeypots, attacked attackers, and recorded attack behavior, and further analyzing attackers' attack behavior and traceable attackers. The core of honey net is honeypot, honeypot can be divided into low-class honeypots, migratory honey tankers and high-level mutual honey. Low interactions and middle interactions are not a real computer system, but through the simulation of the program, it is very limited to the attacker's interaction, so it is not poss...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com