Method, system and equipment for defending attack message
A technology for attacking packets and packets, which is applied in the direction of transmission systems and electrical components, can solve problems such as impact, impact on user network access, exhaustion of NAT entry resources, etc., to achieve defense against attack packets, simplify network deployment, and reduce cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
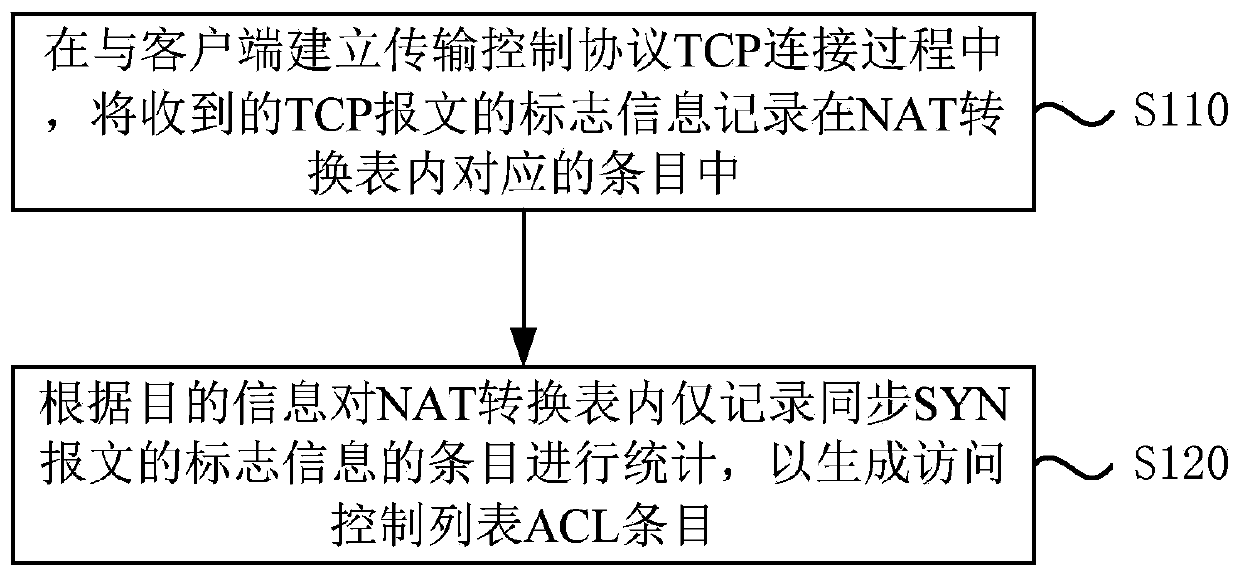
[0030] The first embodiment of the present invention provides a method for defending against attack messages, which is used in a NAT device. The NAT device includes a broadband access server BRAS. This embodiment uses the BRAS device as an example to describe the method in detail.
[0031] Specifically, the process of establishing a TCP connection between the client and the BRAS device includes 3 TCP message interactions:
[0032] 1) The client sends a synchronous (Synchronous, SYN) message to the BRAS device;
[0033] 2) The BRAS device responds to the client with a response (Synchronous Acknowledgment, SYNACK) message;
[0034] 3) The client sends an acknowledgment (Acknowledgment, ACK) message to the BRAS device.
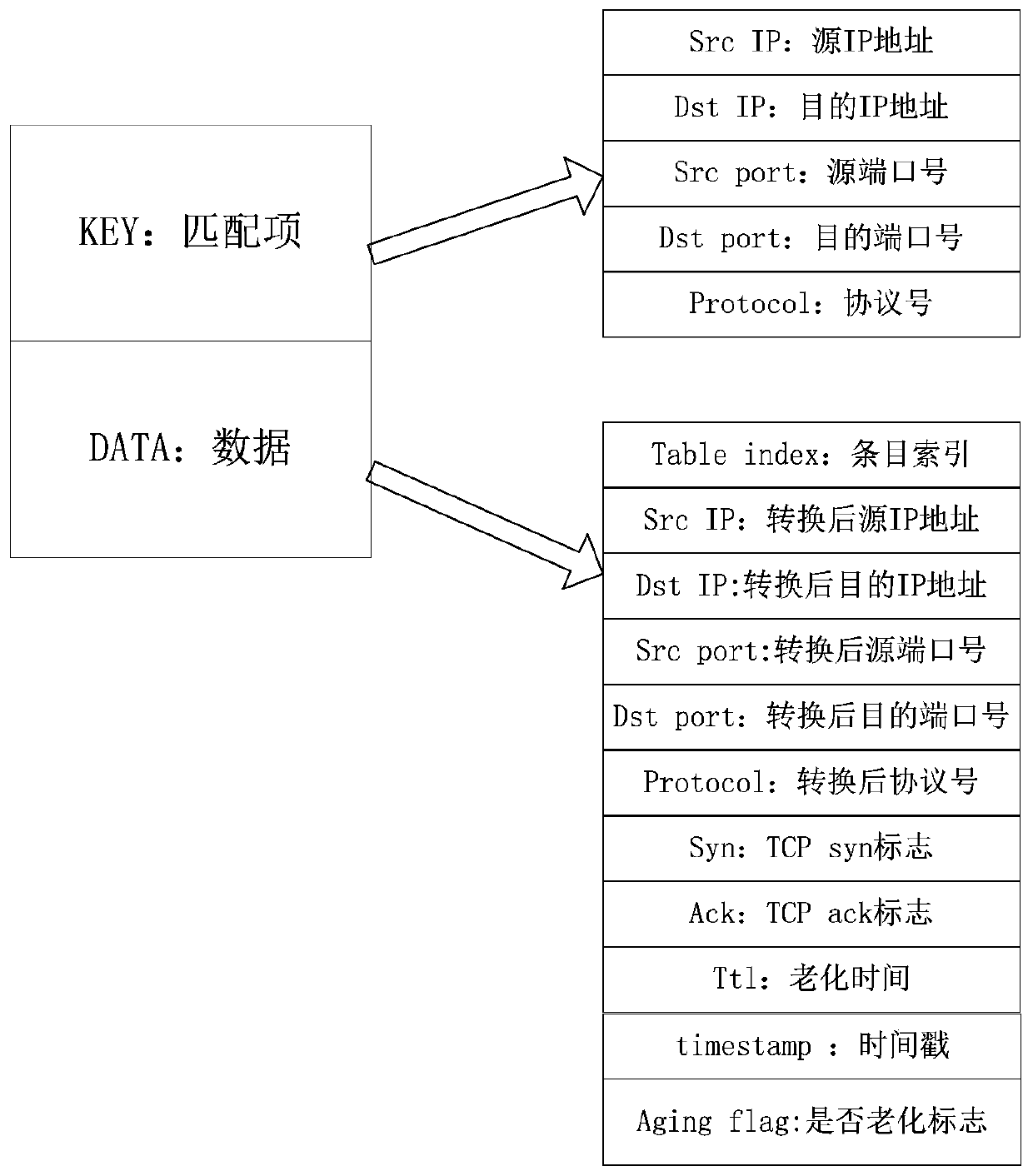
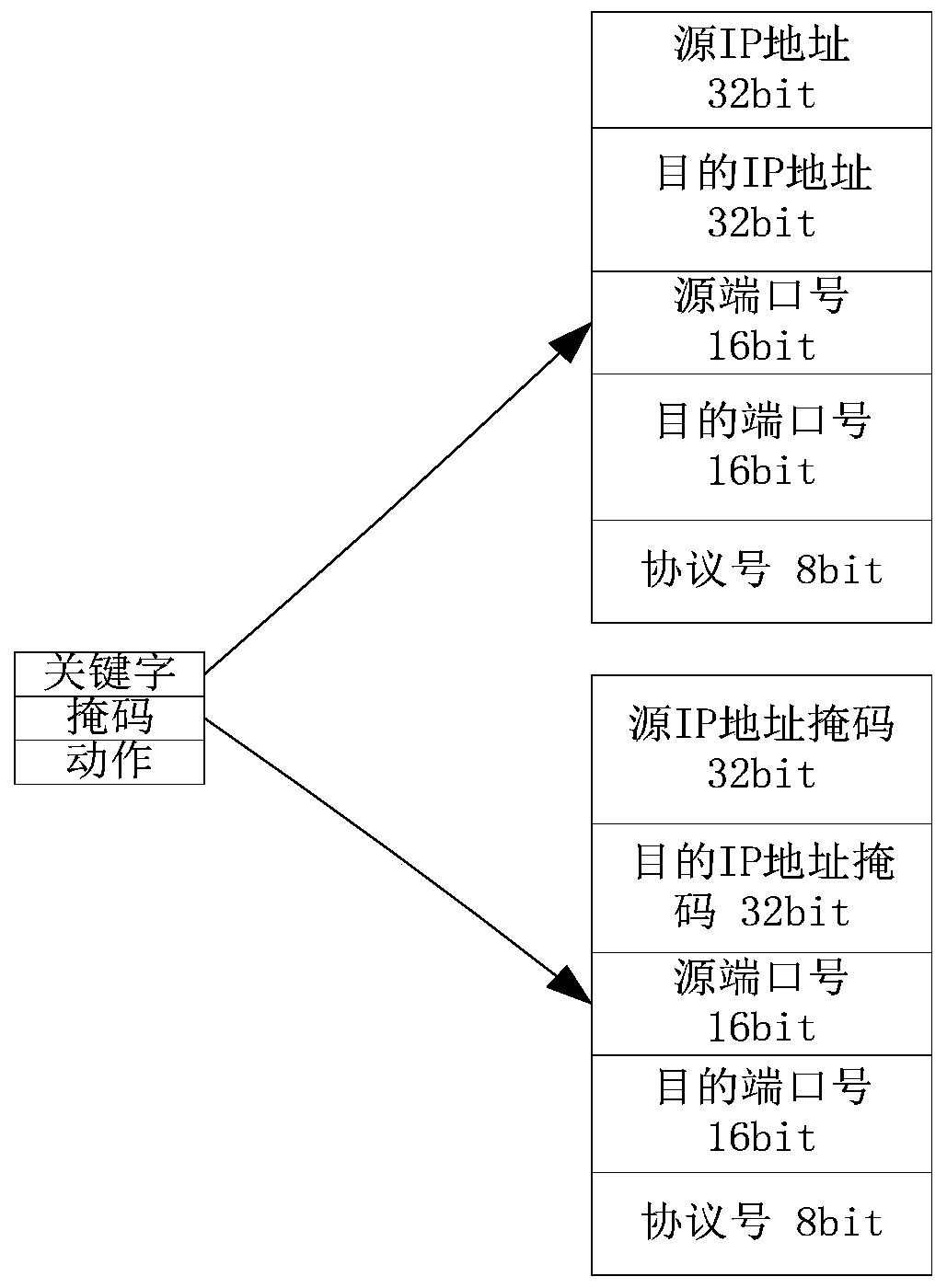
[0035] The above three message exchanges are the three-way handshake of the TCP connection. In the case of an attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com