Driven malware defence method and device
A malware-driven technology, applied in the field of computer security, can solve problems such as system crashes, imprecise judgment logic, and failure of security software functions, and achieve the effect of preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
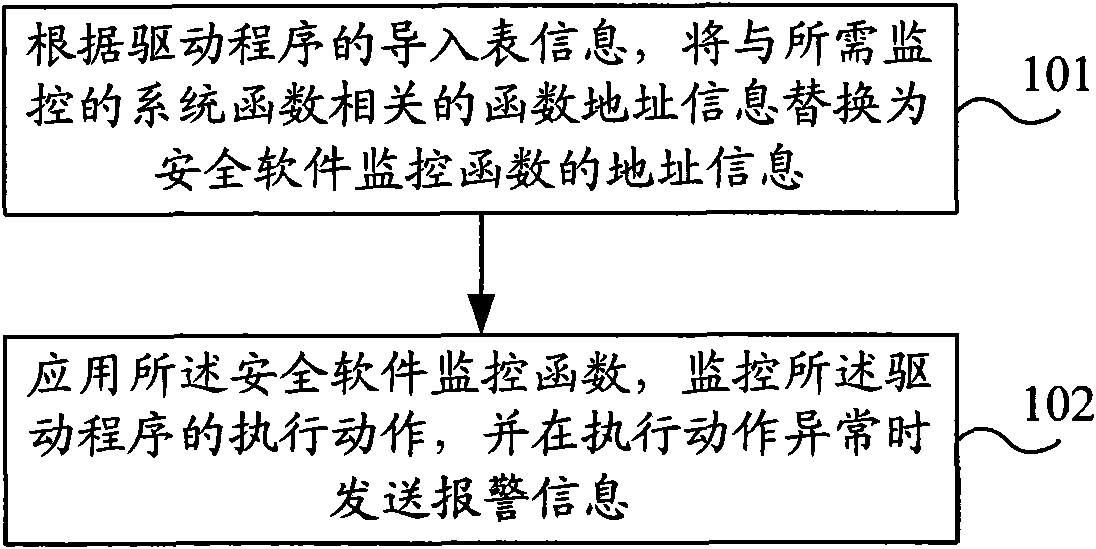
[0019] figure 1 It is a flow chart of the first embodiment of the drive-type malware defense method of the present invention, as figure 1 As shown, the method of the present embodiment includes:
[0020] Step 101, according to the import table information of the driver, replace the function address information related to the system function to be monitored with the address information of the security software monitoring function;
[0021] When the driver is loaded, there will be a point in time. At this point in time, the driver has been loaded into the system kernel, and the import table information of the driver is also obtained through parsing. The next step is to call the system function required by the driver. , so as to realize the driving function. Installing the safety software monitoring function at this point in time can replace the system function that the driver needs to call with the safety software monitoring function before the driver program is executed. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com