Process isolation and encryption mechanism based security disc model and generation method thereof
A technology of security, confidentiality and process isolation, applied in the field of information security, it can solve the problems of network leaks, inability to enforce centralized management of confidential documents, and application failures, and achieve the effect of solving compatibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described in detail below with reference to the drawings and specific embodiments.
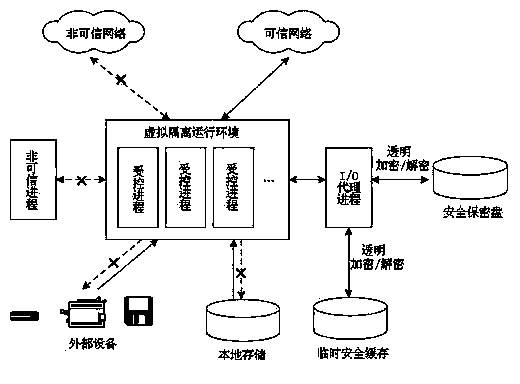
[0022] The secure and confidential disk model based on the process isolation encryption mechanism, its structure is as figure 1 As shown, it includes a virtual isolation running module, an I / O agent process encryption / decryption module, and a secure disk.
[0023] Among them, the virtual isolation operation module is used to filter untrusted networks, trusted networks and external devices to obtain trusted processes. Once the trusted process accesses the data files in the safe and confidential disk, the state of the trusted process immediately changes to controlled Process, the controlled process is forced to run in a virtual isolated operating environment; in this virtual isolated operating environment, the controlled process’s access to the data files on the secure and confidential disk and the data files outside the secure and confidential disk are in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com