End-to-end safety control method for wireless sensor network and internet intercommunication
A wireless sensor and interconnection communication technology, applied in the field of computer networks, can solve the problems of weak sensor nodes, inability to provide Internet remote terminal privacy protection, failure to implement access control and resist DoS attacks, etc., to achieve enhanced access control and privacy protection , reduce energy consumption, and resist DoS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
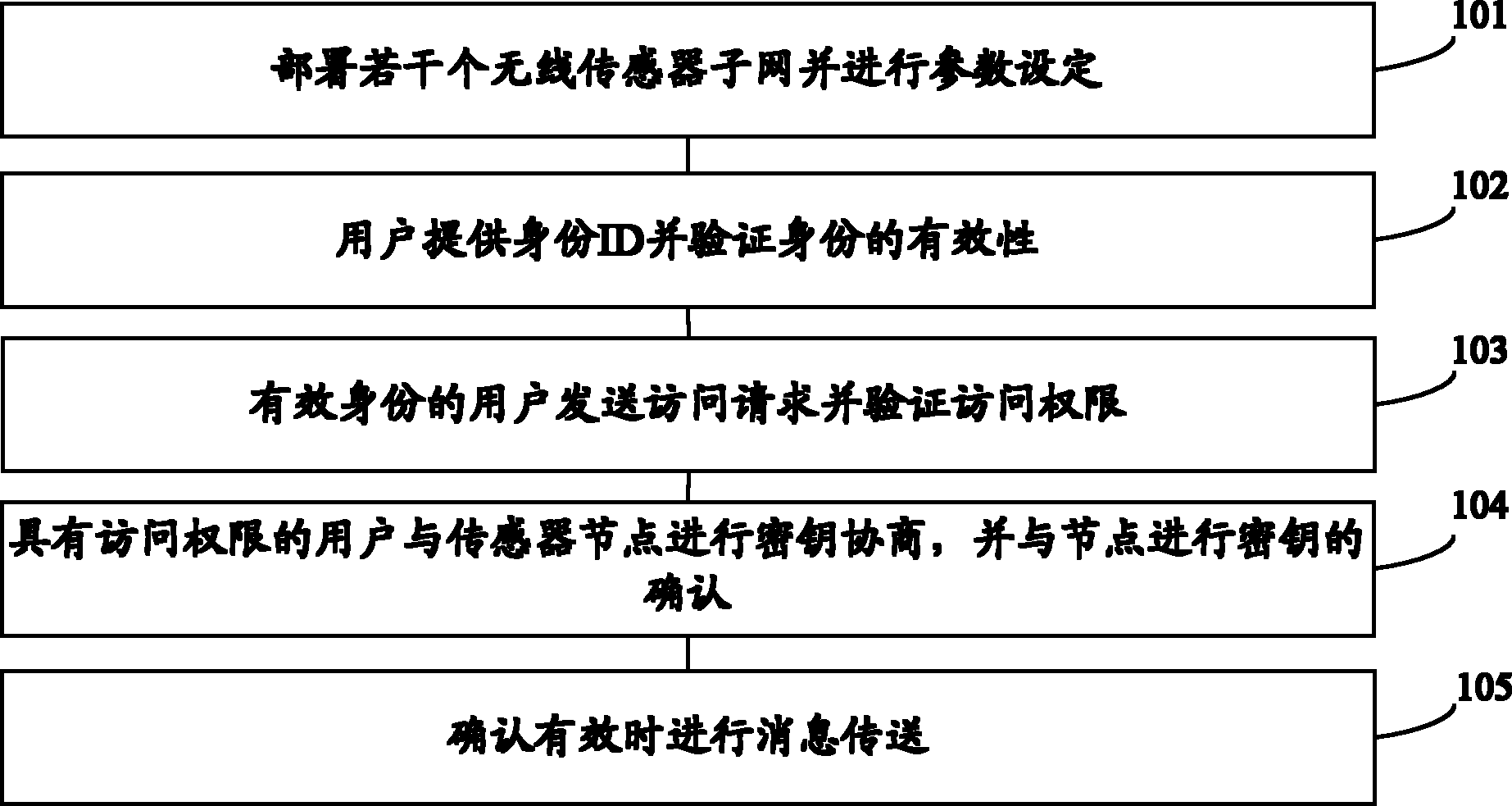
[0024] refer to figure 1 Shown is a schematic flowchart of an end-to-end security assurance method for interconnecting communication between a wireless sensor network and the Internet, including:
[0025] S101, deploying several wireless sensor subnets and setting parameters;
[0026] S102, the user provides an identity ID and verifies the validity of the identity;
[0027] S103, the user with a valid identity sends an access request and verifies the access right;
[0028] S104, the user with the access authority negotiates the key with the sensor node, and confirms the key with the node;
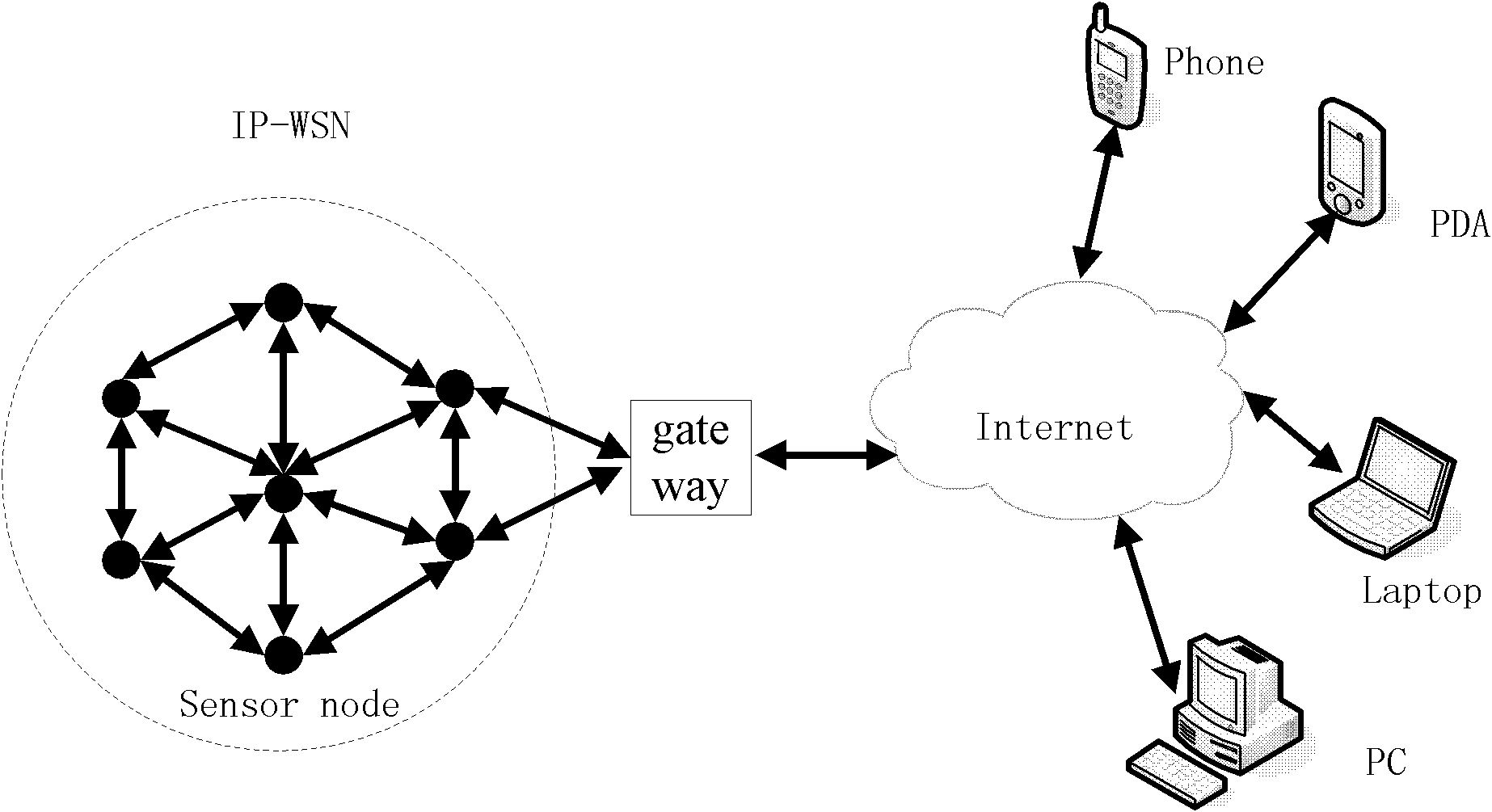
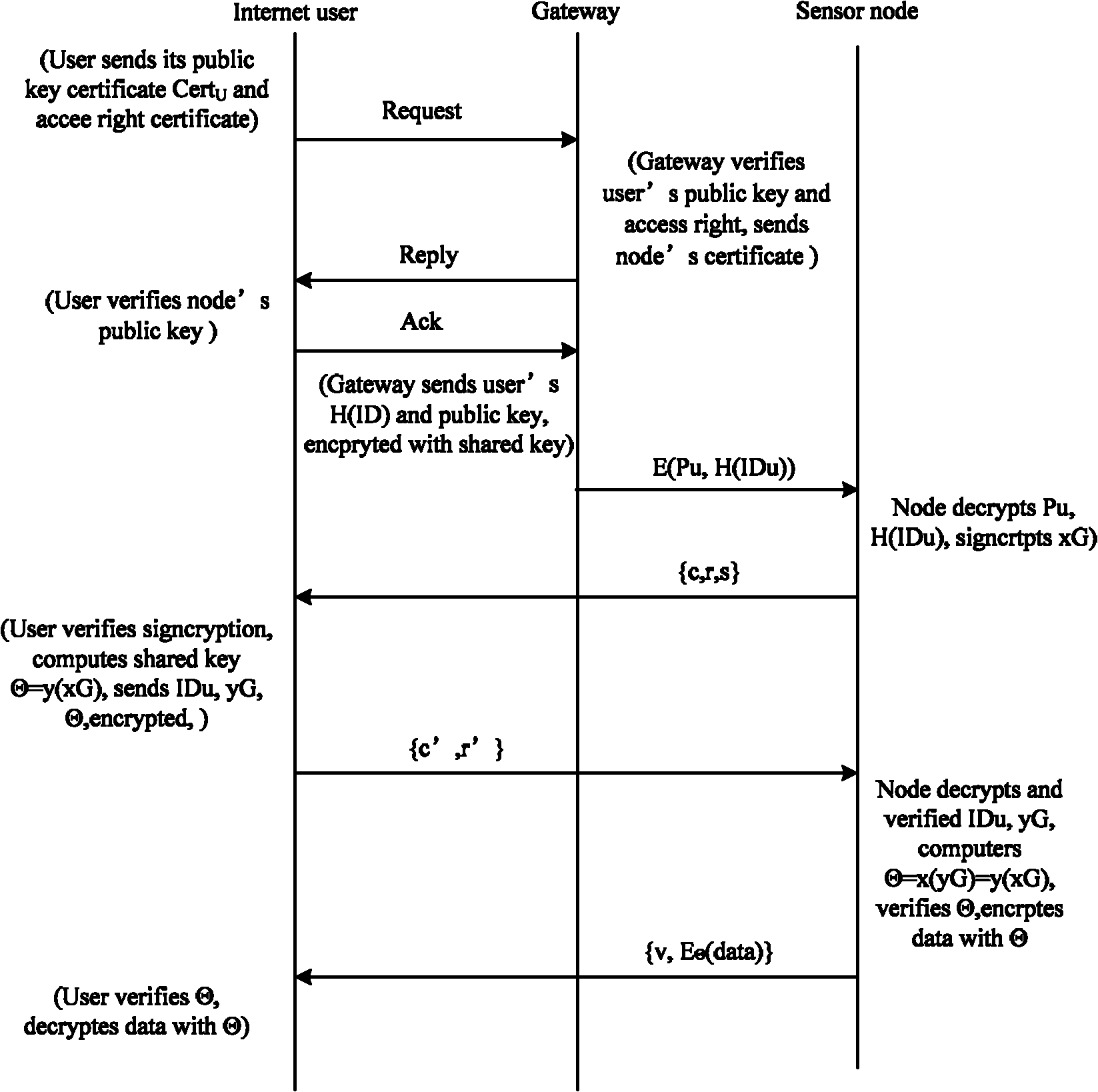
[0029] S105, message transmission is performed when the confirmation is valid. specific reference figure 2 Take user U accessing node i through a remote terminal device as an example.
[0030] 1) Deployment phase
[0031] The service provid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com