Method and system for providing end-to-end security solutions to aid protocol acceleration over networks using selective layer encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
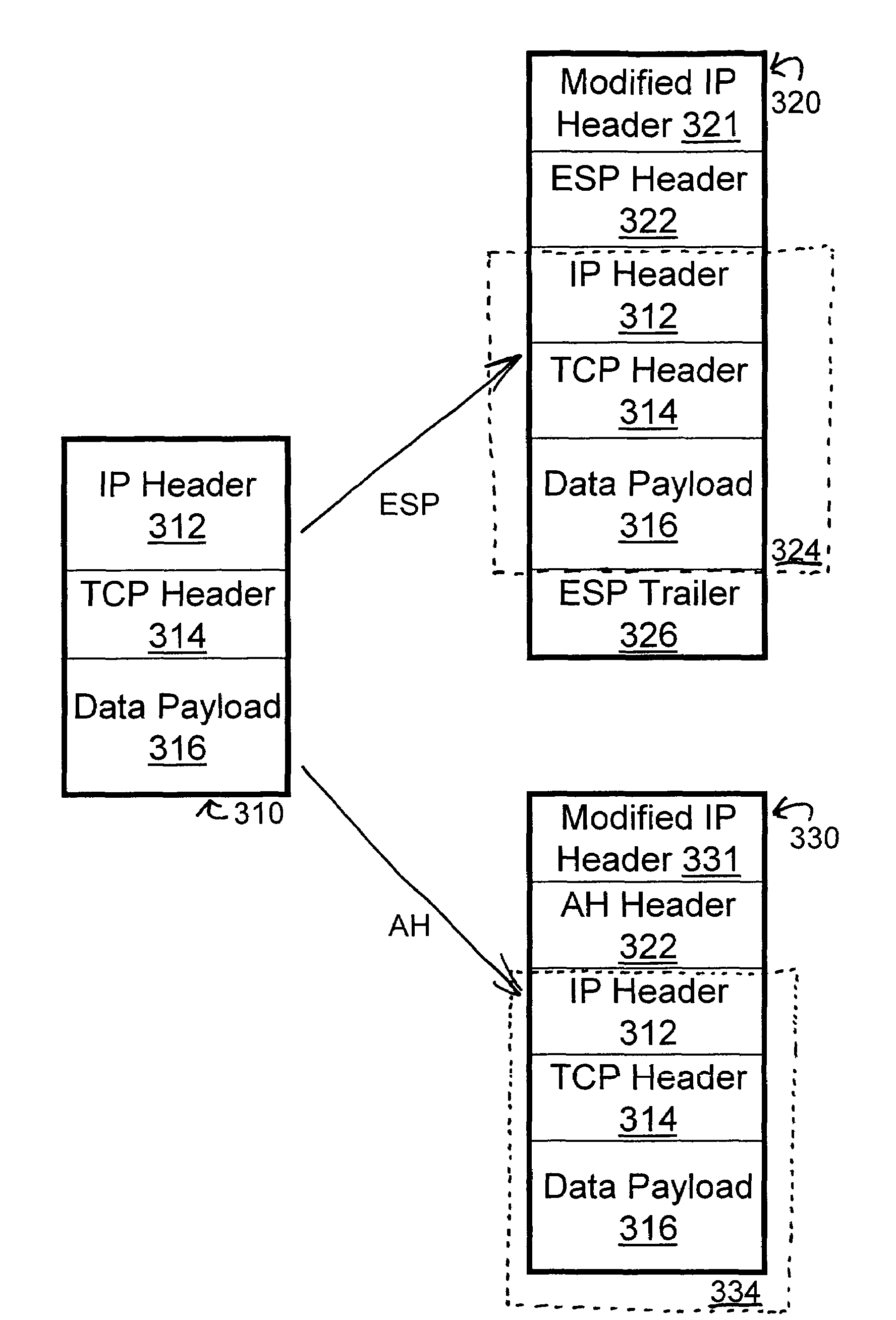
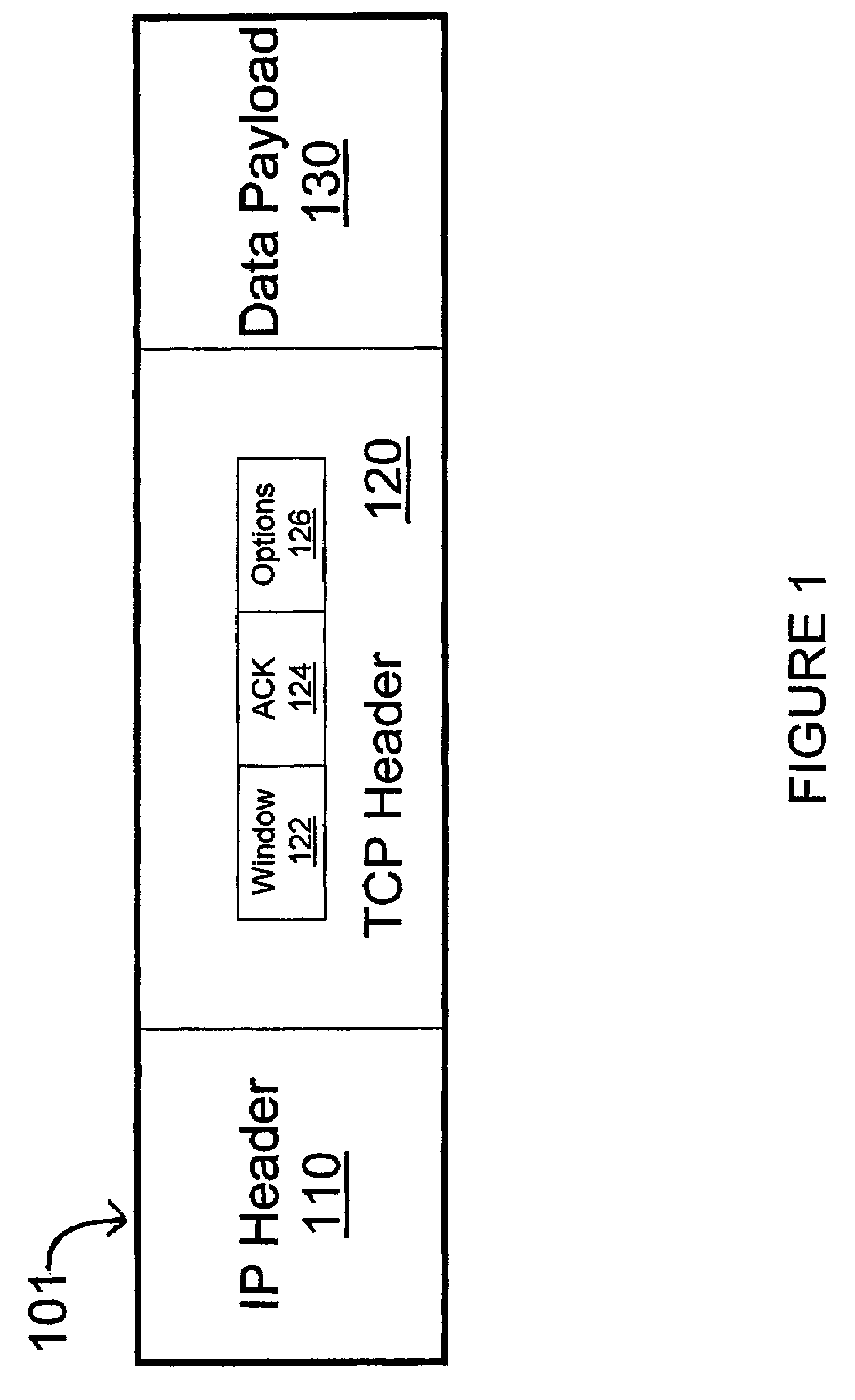
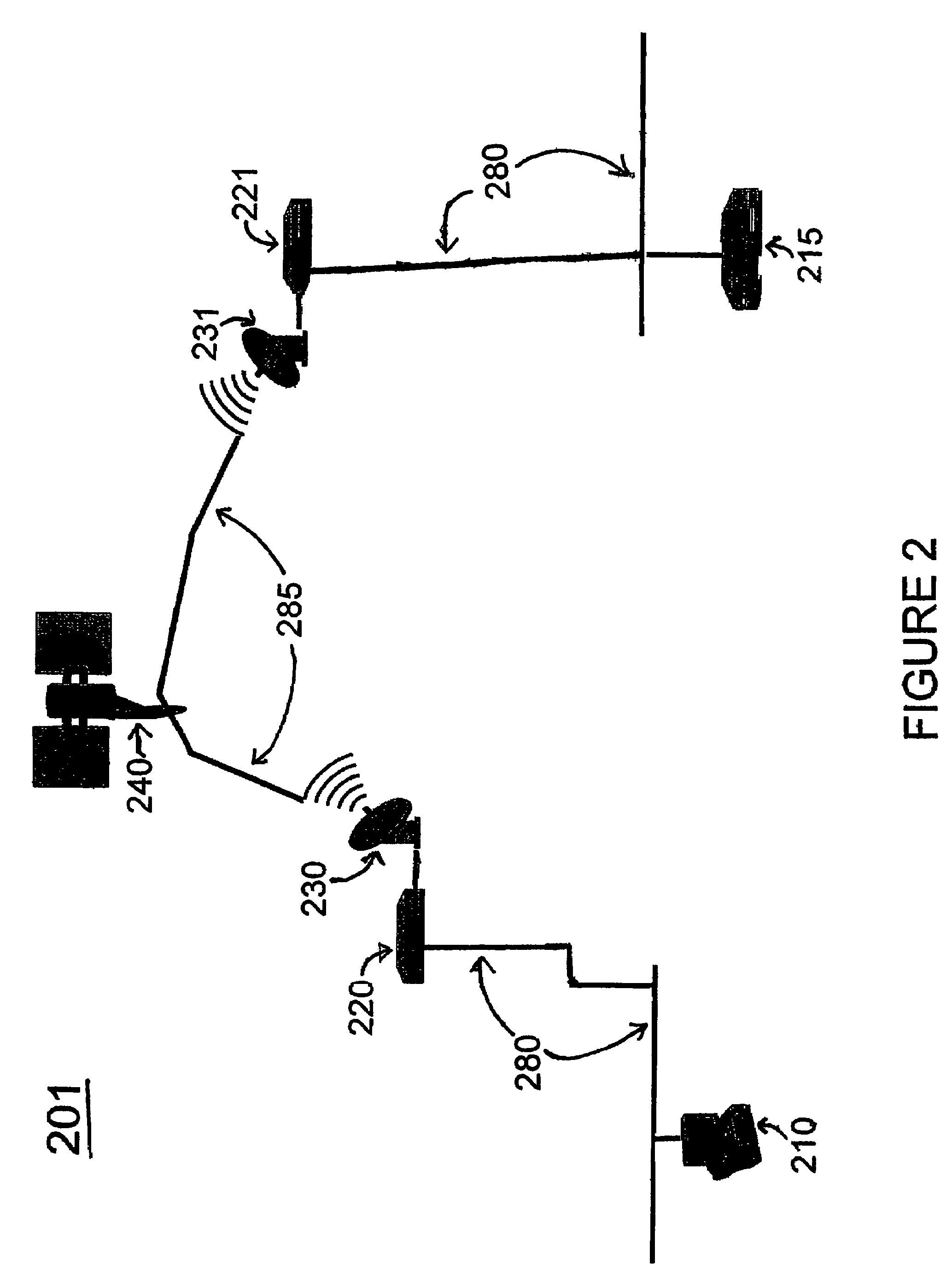
[0039]The present invention is now described in more detail herein in terms of various exemplary embodiments. This is for convenience only and is not intended to limit the application of the present invention. In fact, after reading the following description, it will be apparent to one skilled in the relevant art(s) how to implement the following invention in alternative embodiments. Moreover, the present invention can be implemented using software, hardware or any combination thereof as is known to one of ordinary skill in the art.
[0040]The present invention meets the above-identified needs for simultaneous high throughput and encryption by providing a system, method, and computer program product for Selective Layer Encryption (SLE) within all networks that experience some degree of latency. Such networks can include, but are not limited to satellite communications, cellular data service, terrestrial networks that experience some degree of signal latency such as the Internet, a rad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com