Uniform resource locator (URL) encryption and validation method for mobile internet user resource access and device provided with the same
A technology of mobile Internet and user resources, which is applied in the field of URL encryption for mobile Internet user resource access, verification methods and devices thereof, and can solve the problems of low security performance and easy cracking of encryption technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
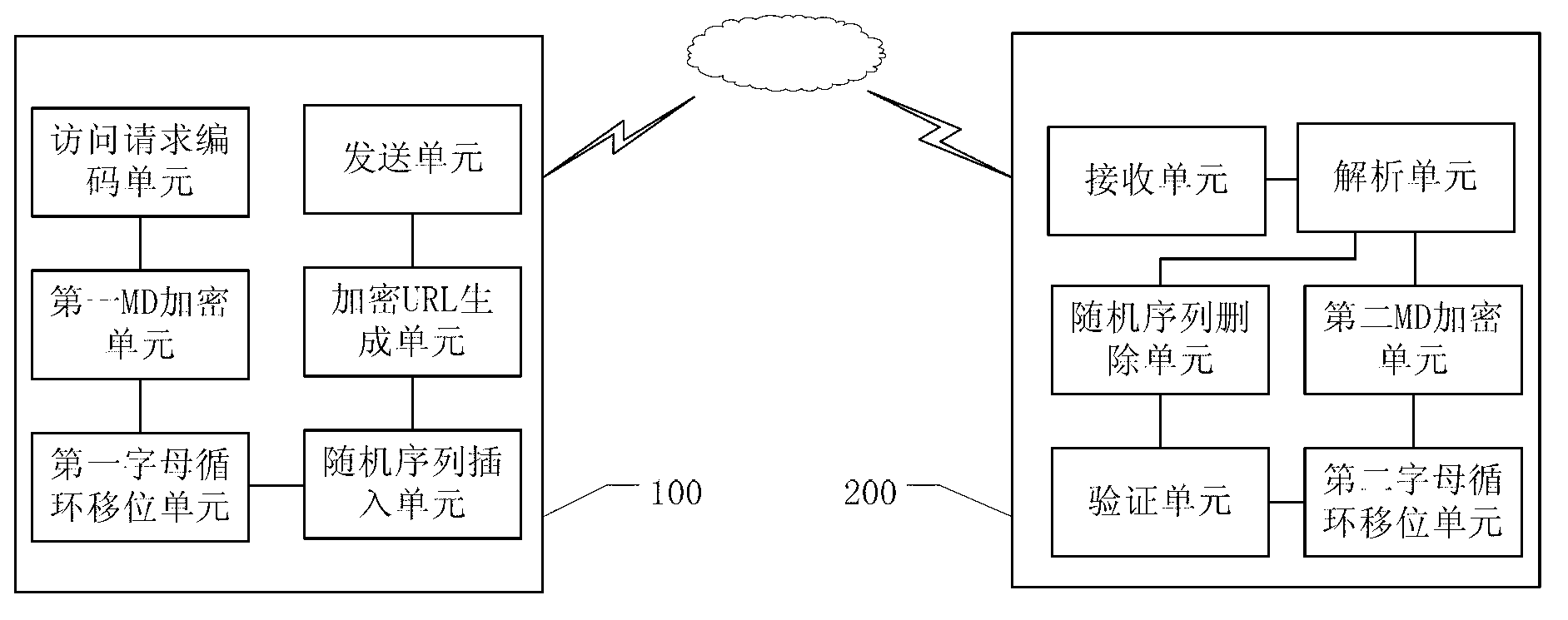
Image
Examples
Embodiment 1
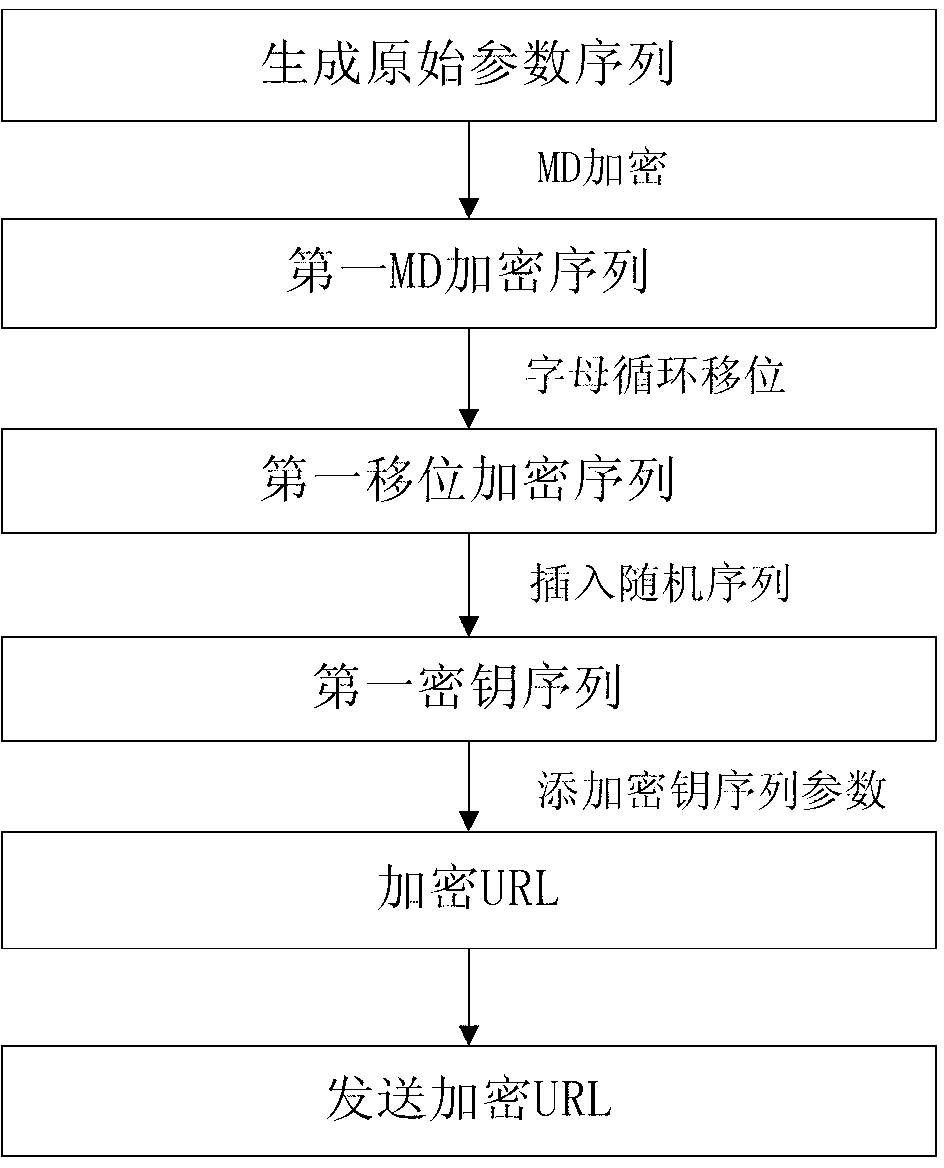
[0048] figure 1 It is a schematic diagram of implementing URL encryption at the client end according to the first embodiment of the present invention.
[0049] Such as figure 1 As shown, the present embodiment is a specific example in which a mobile Internet user requests a certain picture resource from a China Unicom operator, and the method for encrypting the client URL of the mobile Internet user's resource access includes the following steps:
[0050] Step 1. Respond to the user's resource access request, obtain the request parameter set S, and generate the original parameter sequence originalString of the resource access request.
[0051]Among them, the request parameter set can include the following parameter groups: phoneNumber represents the user's mobile phone number, productCode represents the package service code, imageID represents the image serial number, timestamp represents the current timestamp... In addition, the request parameter set can also include an impl...
Embodiment 2
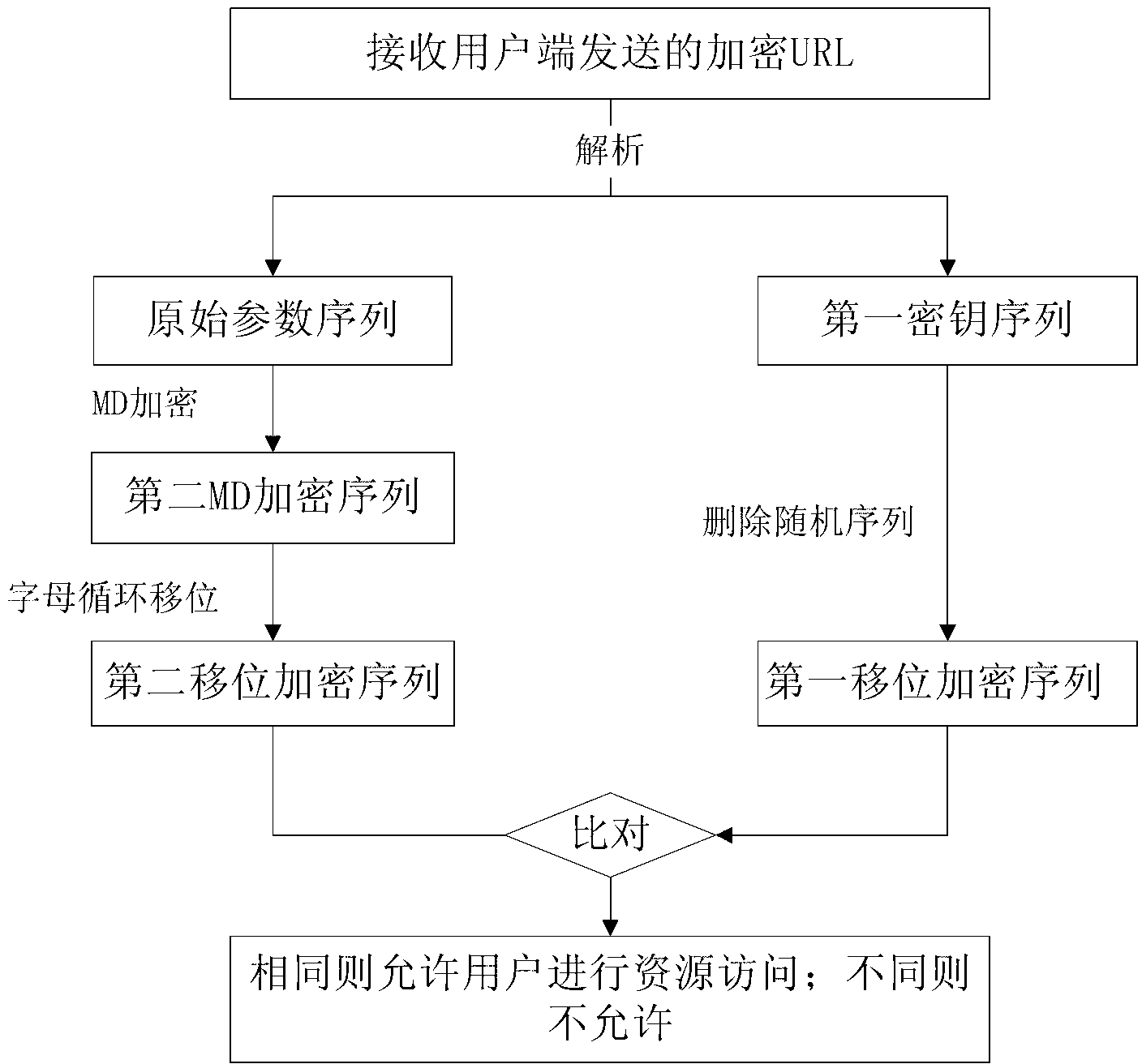
[0080] Corresponding to Embodiment 1, when the encrypted URL is sent to the content providing terminal, the content providing terminal encrypts the request parameter using an encryption method similar to that of the client, and then compares it with the secu_KEY transmitted in the form of the URL transmission parameter, and then determines Whether the input URL has been tampered with, see this embodiment for details.
[0081] Such as figure 2 As shown, the URL verification method of the content providing terminal in this embodiment includes the following steps:
[0082] Step 1. The content providing terminal receives the encrypted URL sent by the client;
[0083] In this embodiment, the encrypted URL received by the content providing terminal is:
[0084] http: / / www.10010.com / submit.do?phoneNumber=18888888888&productCode=bycl&imageID=837134×tamp=20121211152106345&secu_KEY=ee9d749c56a9e84accb714fb911cabcfa58c3.
[0085] Step 2. Parsing out the original parameter sequen...
Embodiment 3
[0096] This embodiment is a specific example in which a mobile Internet user requests a certain content providing website (music.m-po.com) to access a certain song resource. The method for encrypting the URL of the mobile Internet user's resource access includes the following steps:
[0097] Step 1. Respond to the user's resource access request, obtain the request parameter set, and generate the original parameter sequence originalString of the resource access request.
[0098] Same as Embodiment 1, in this embodiment, when the user requests song resource access, the request parameter set will also be obtained according to the resource access request of the user, and the original request parameter set will be generated according to the specified parameters pre-agreed between the user end and the content providing terminal in the request parameter set. Parameter sequence originalString.
[0099] In this embodiment, the request resource serial number (songId=12345 for this embod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com