Patents
Literature
203 results about "Safety procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A safety procedure is a step by step plan of how to perform a work procedure. This is used in cases where deviation from the procedure could lead to injury or accident. The safety procedure is a document that is put together by groups within the organization, and is used as a template when performing a particular task on the job.
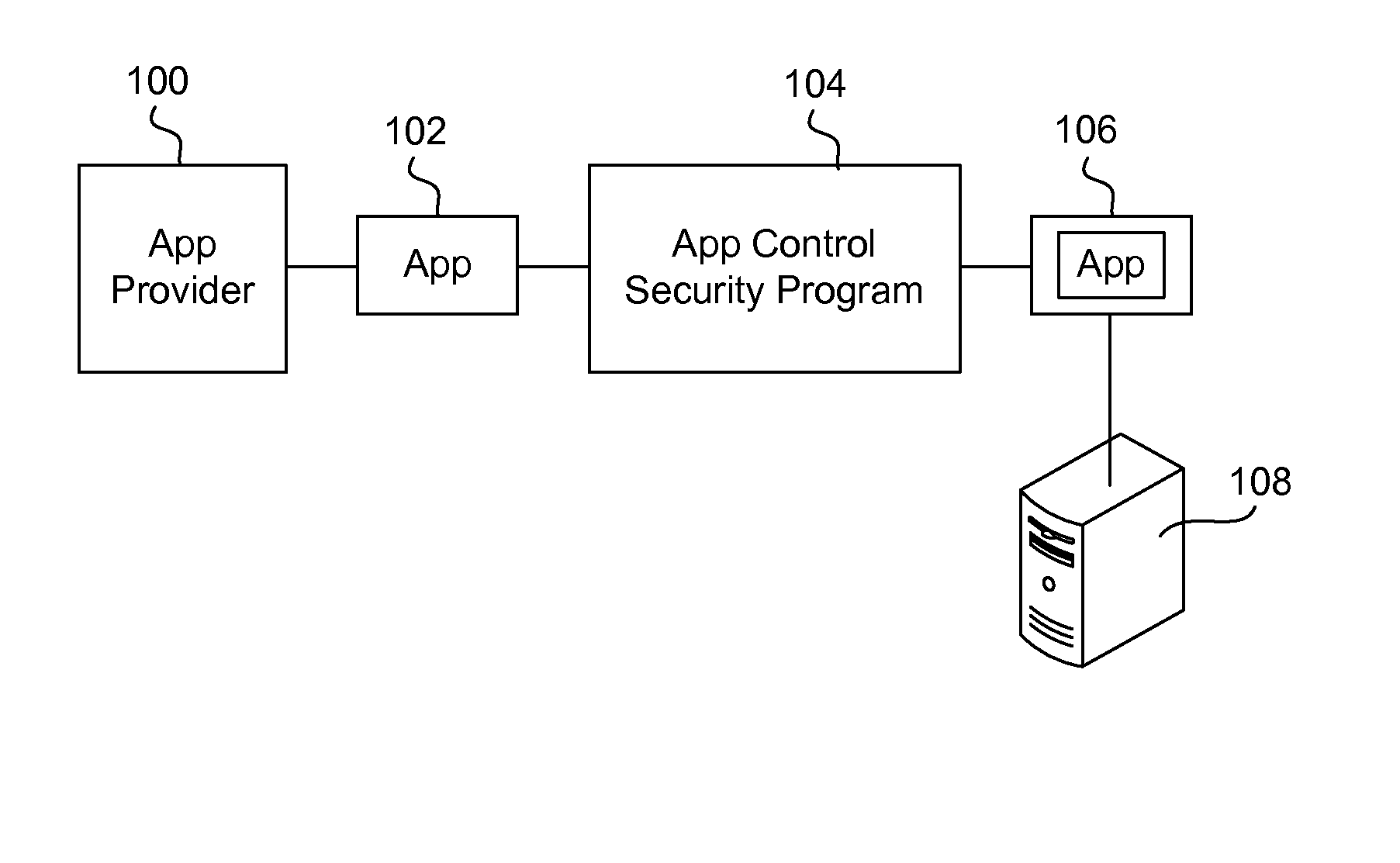
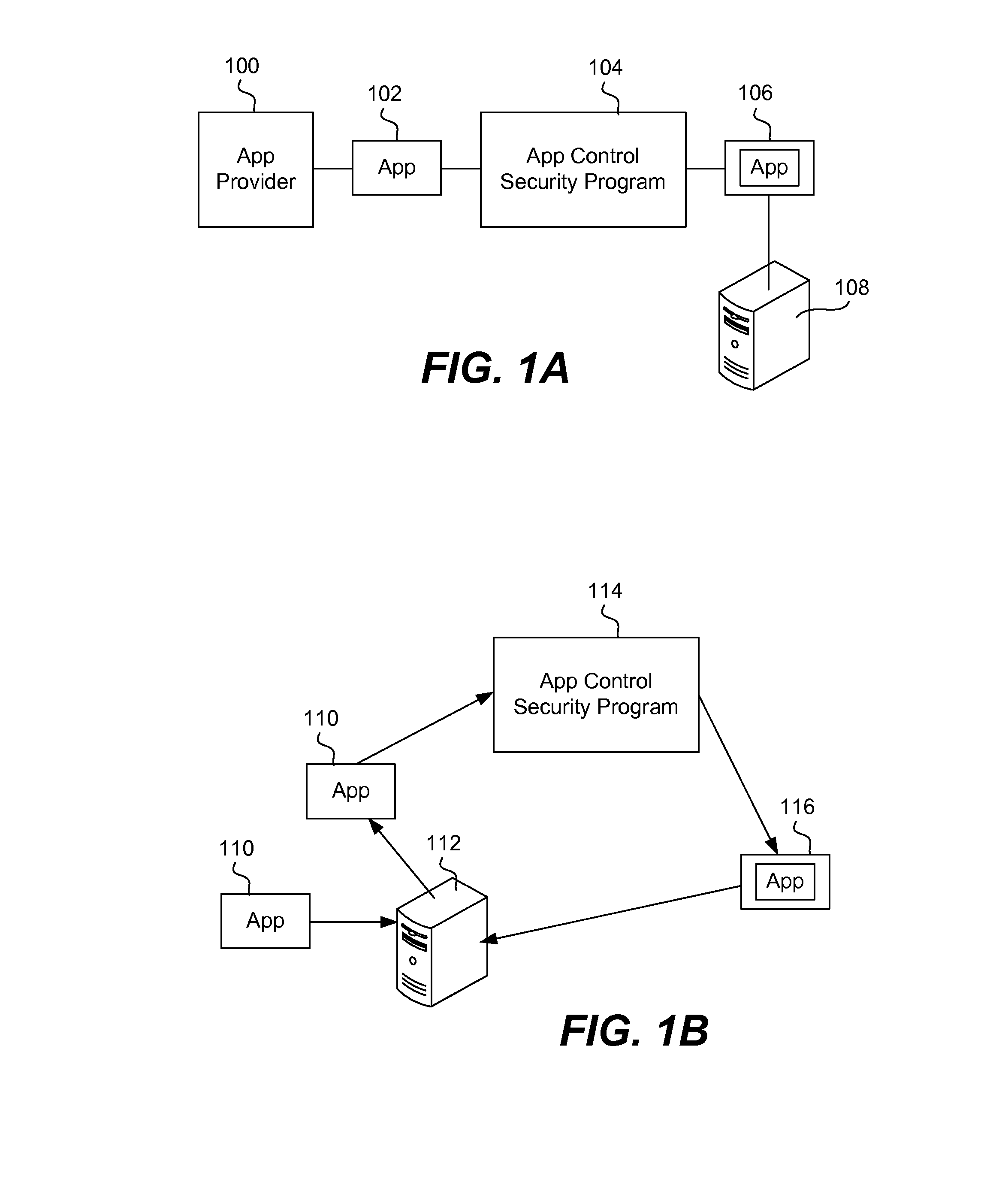
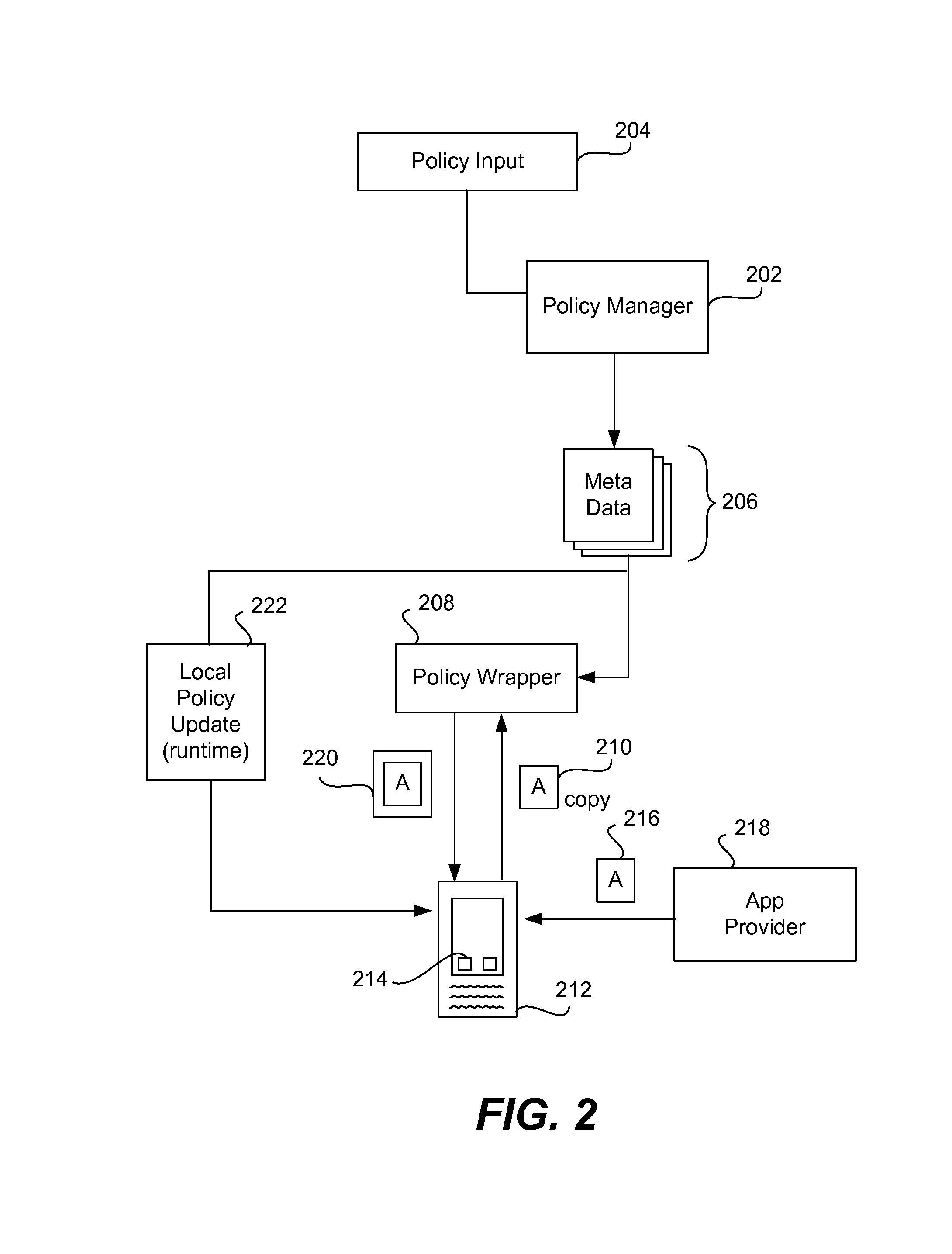
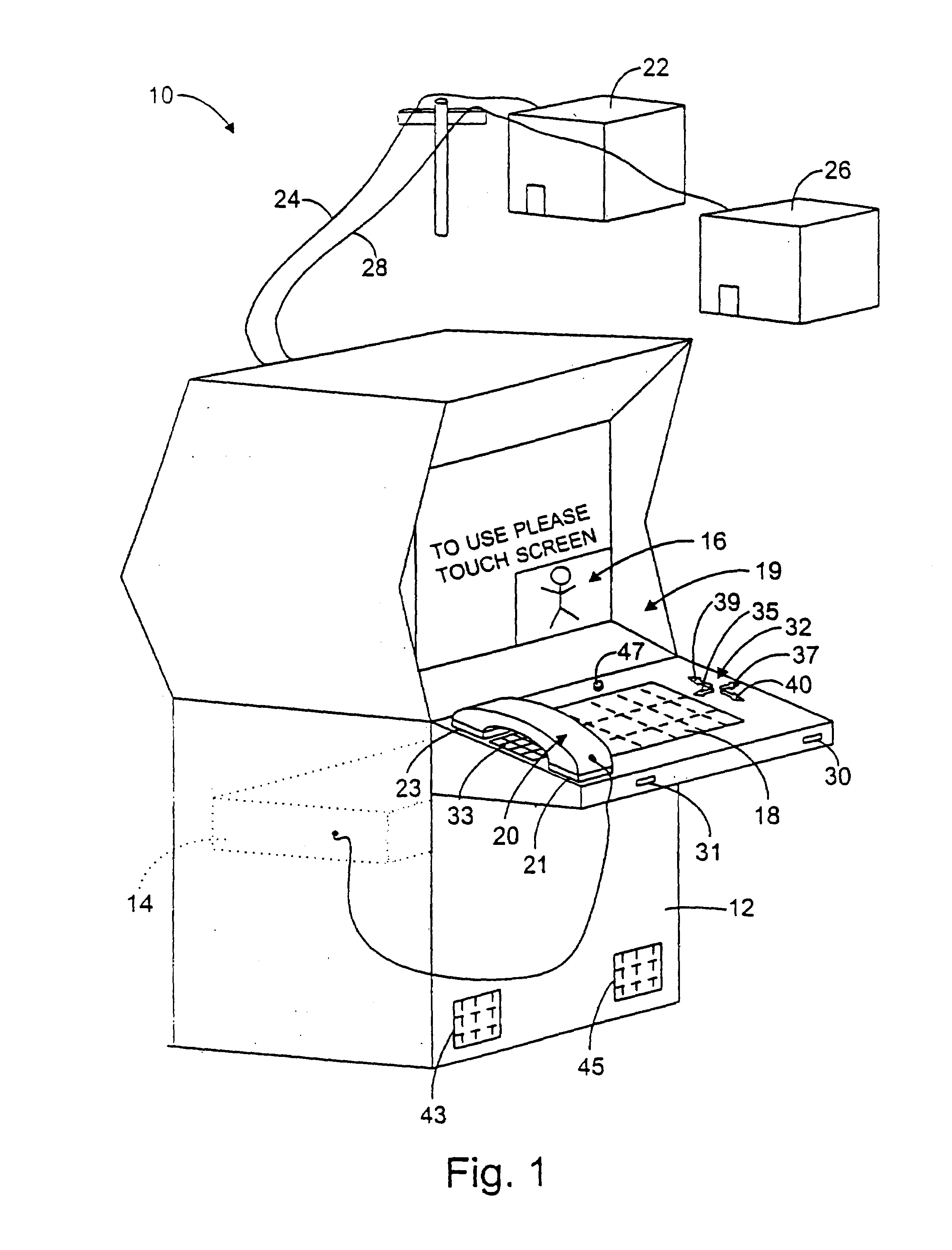
Securing and managing apps on a device
ActiveUS20120210443A1Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
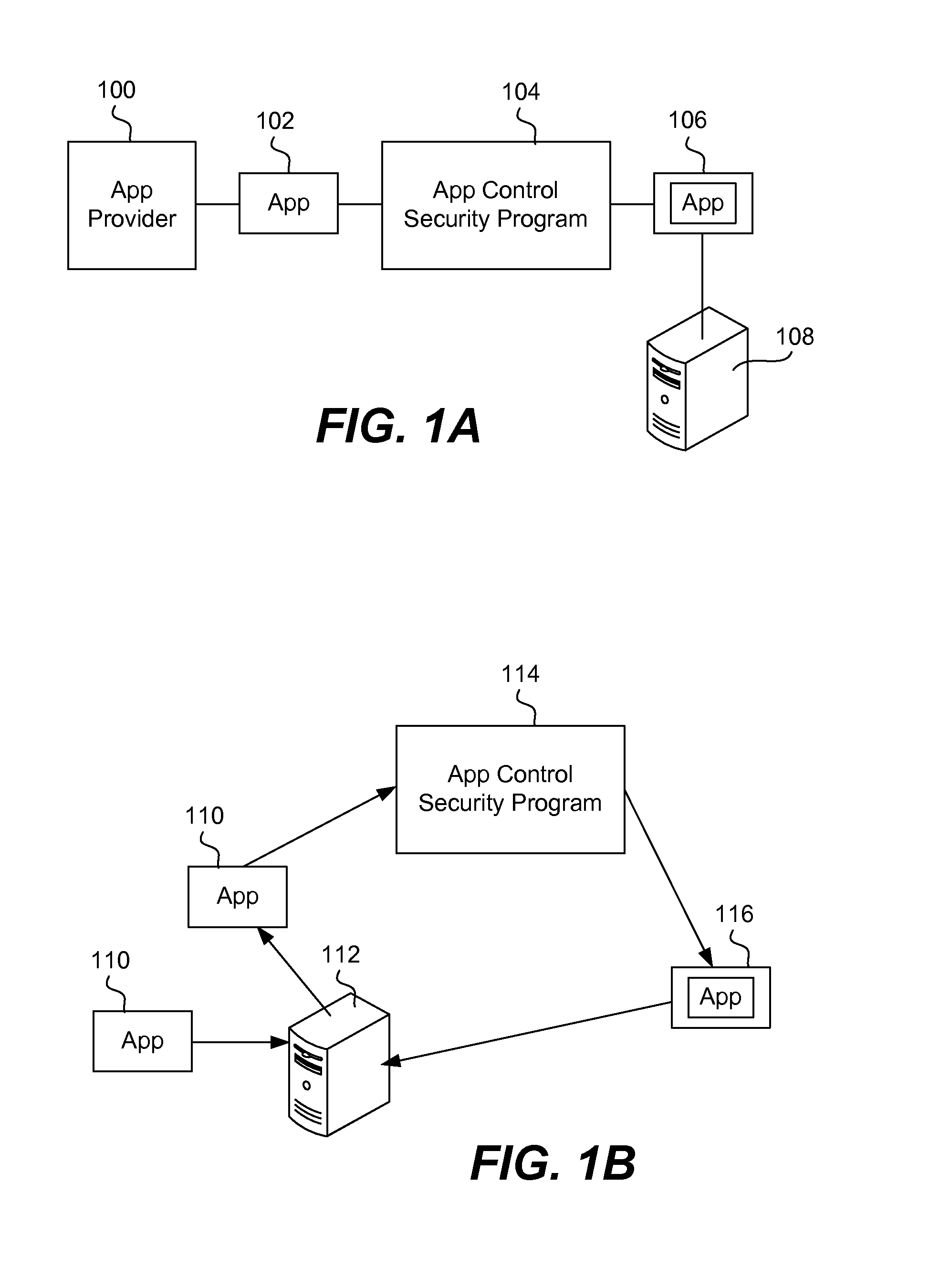
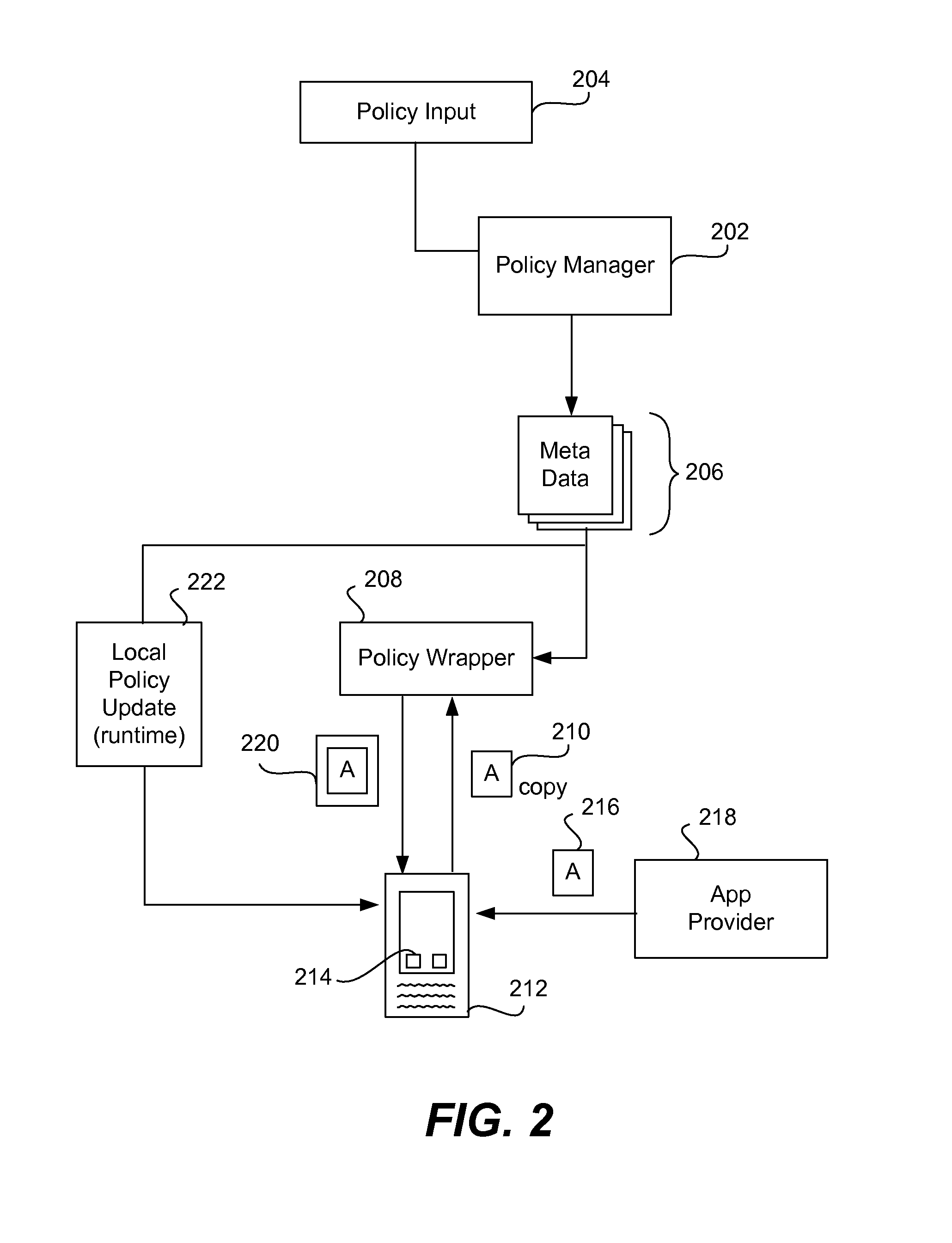
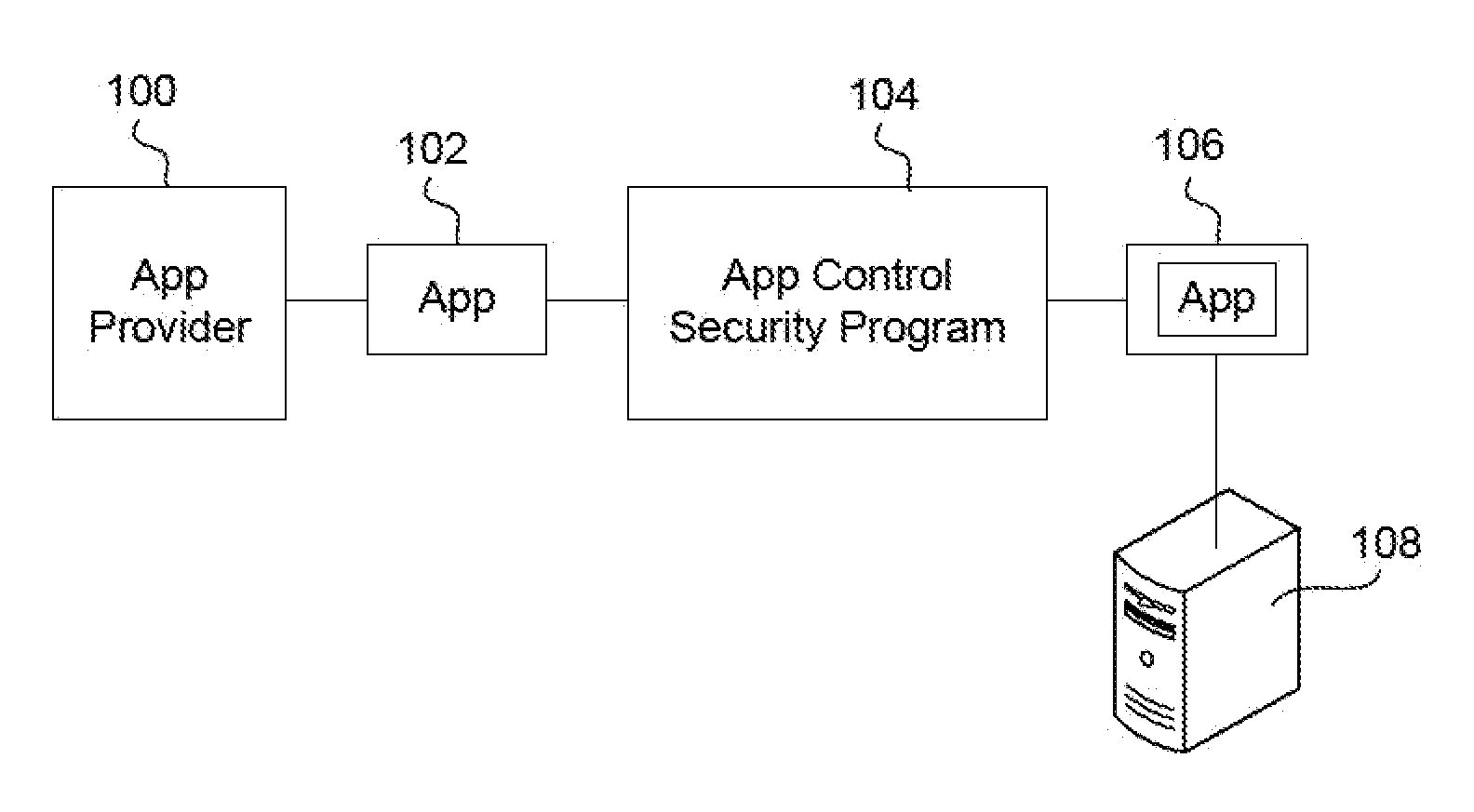
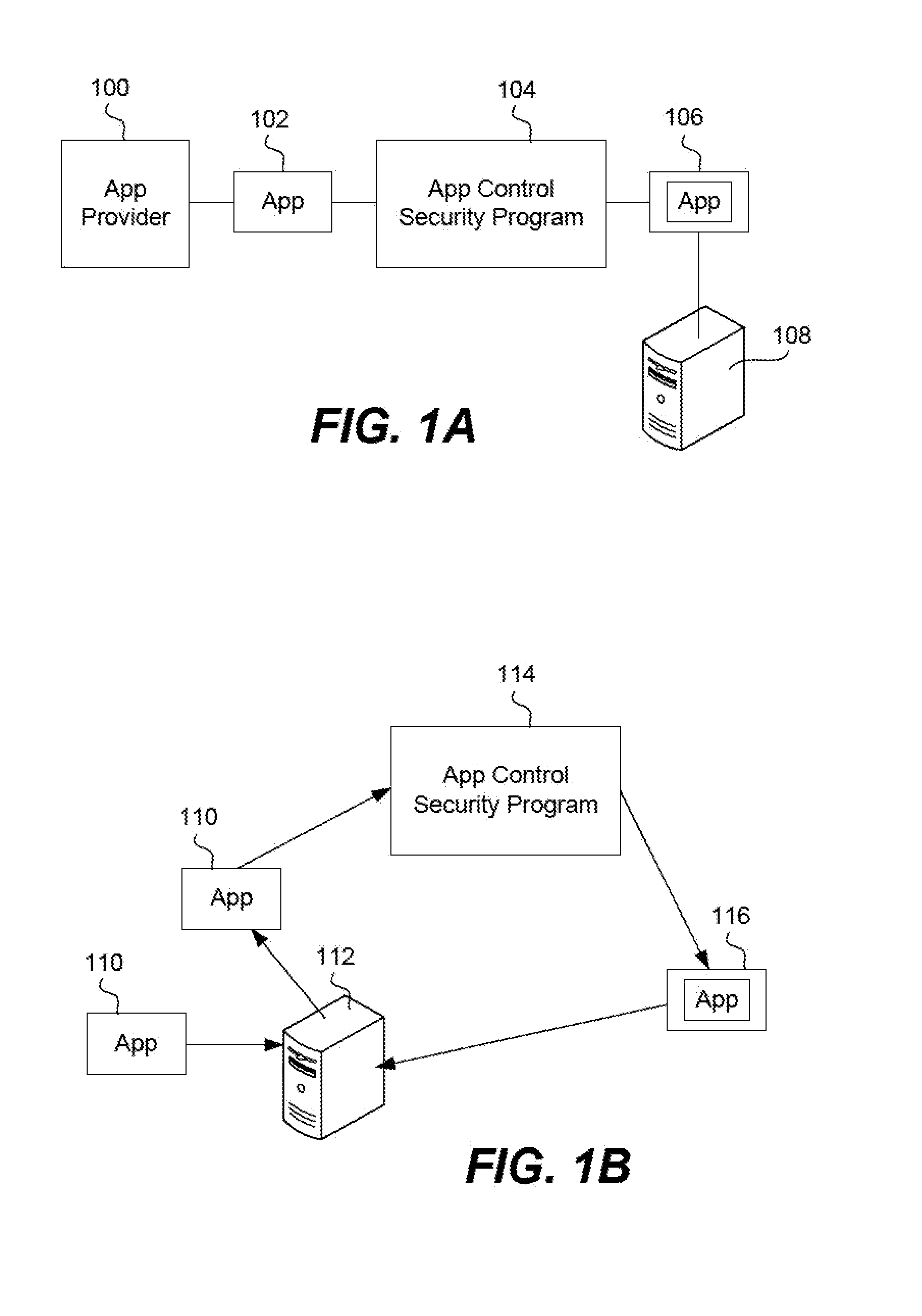
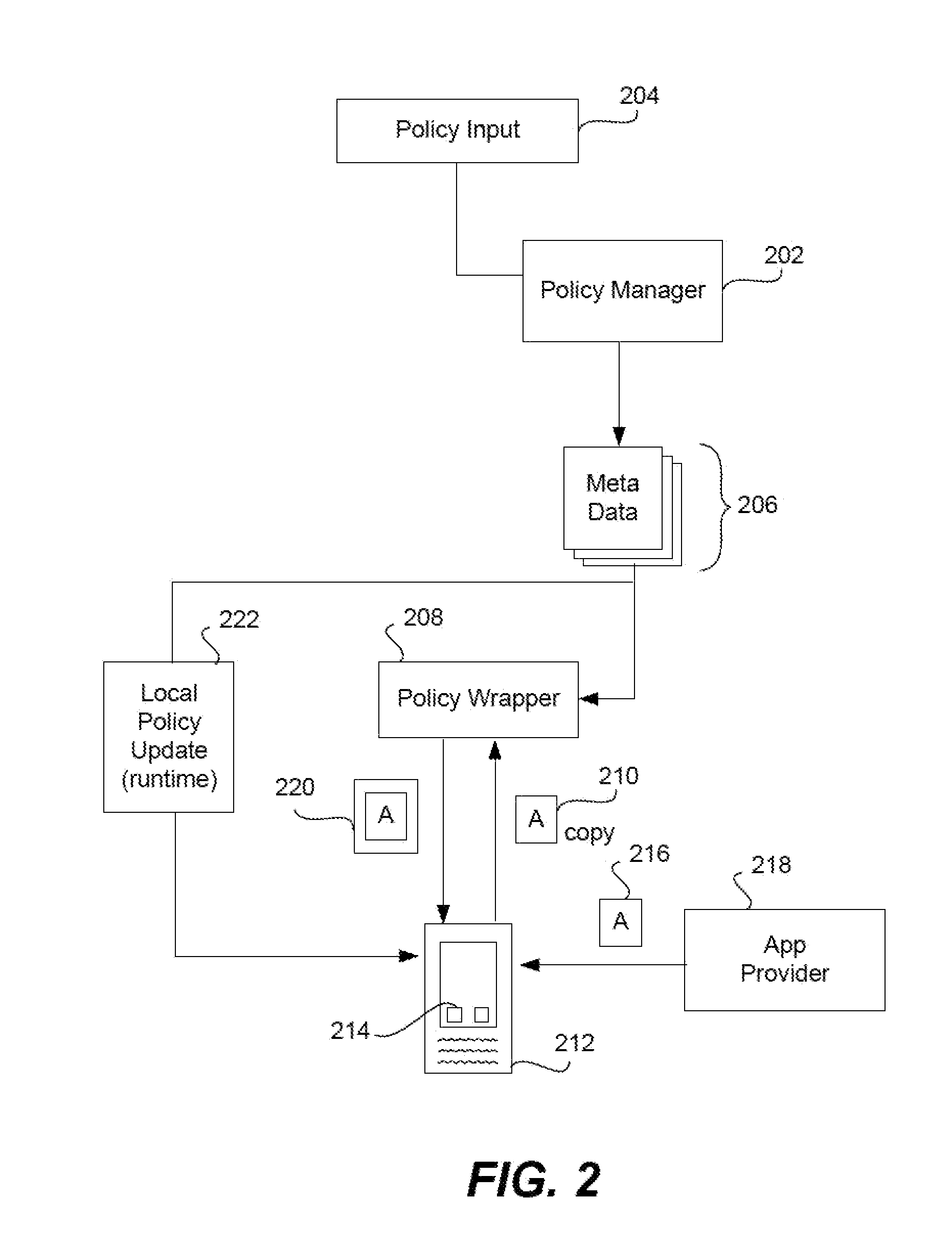
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Operating system extension to provide security for web-based public access services
InactiveUS7171686B1Improve securityDigital data processing detailsUser identity/authority verificationOperational systemPassword
Owner:RPX CLEARINGHOUSE
Security and driver identification system
InactiveUS8451105B2Facilitate communicationElectric signal transmission systemsImage analysisDriver/operatorTransceiver
A security and driver identification system for use within the commercial transportation industry and which can be applied to private vehicles. The central component of the system is a telecommunications mobile terminal located within the vehicle with primary capability being to positively identify driver and vehicle to facilitate transceiver wireless communications between vehicle and authorized personnel. The telecommunications mobile terminal is preprogrammed with wireless network number, and is accessible and security procedure implemented by biocell phone communication from authorized driver.
Owner:MCNAY JAMES HOLLAND
Geographical restrictions for application usage on a mobile device
ActiveUS20140208397A1Digital data processing detailsComputer security arrangementsOperational systemObject code
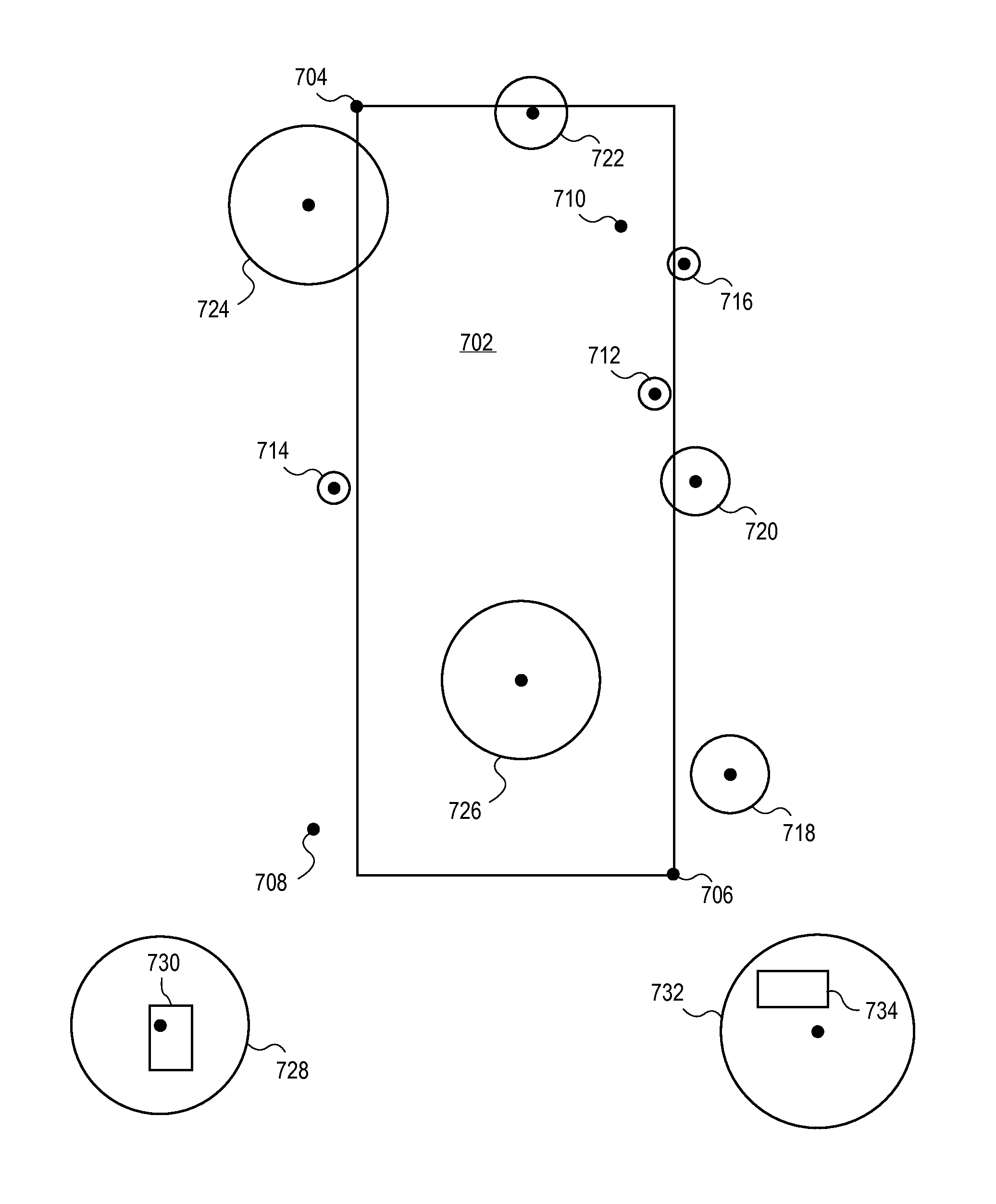
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smart phone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. App object code is substituted with security program object code, thereby creating a security-wrapped app. The app is provisioned with a geo-fencing policy which prevents execution of an app outside a pre-defined geographical area. If the device is within the defined area, the app is allowed to execute. The geographical area, such as a building or company campus, is defined using longitude and latitude coordinates and a location accuracy value. Device location is obtained using location / GPS services on the device.
Owner:BLUE CEDAR NETWORKS INC
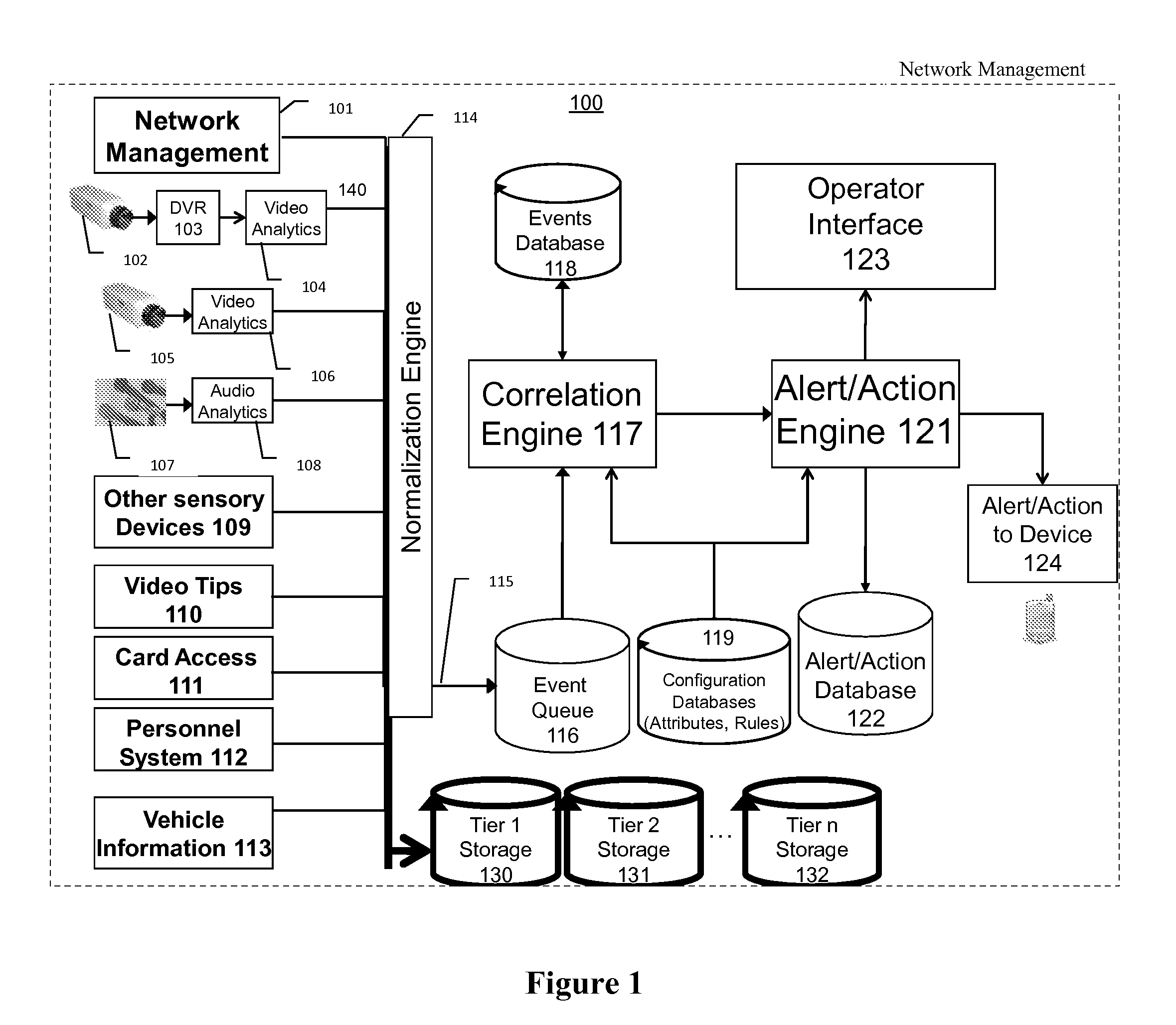
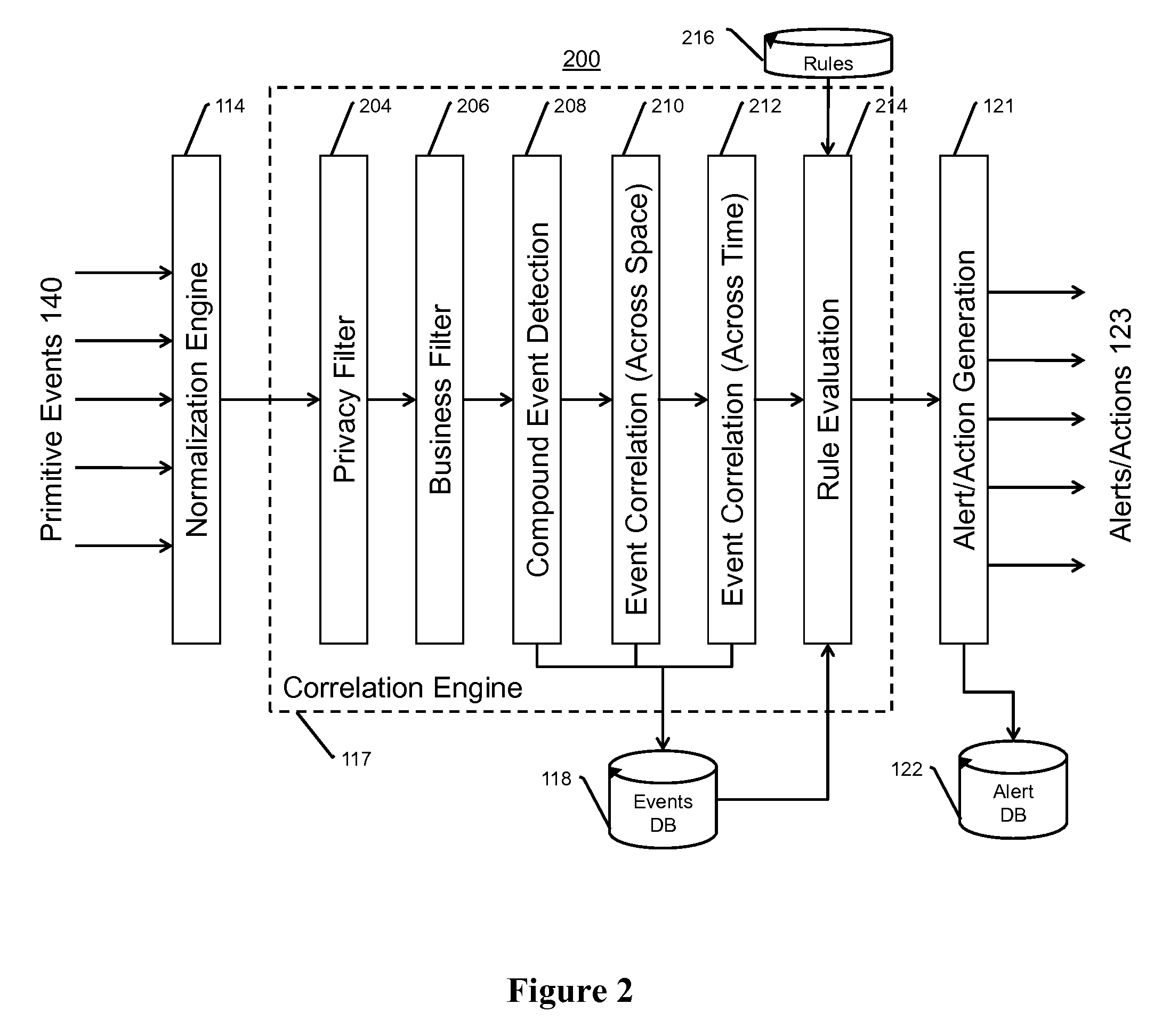
Audio analysis, storage, and alerting system for safety, security, and business productivity
ActiveUS20090002157A1Color television detailsClosed circuit television systemsNetwork managementComputer science
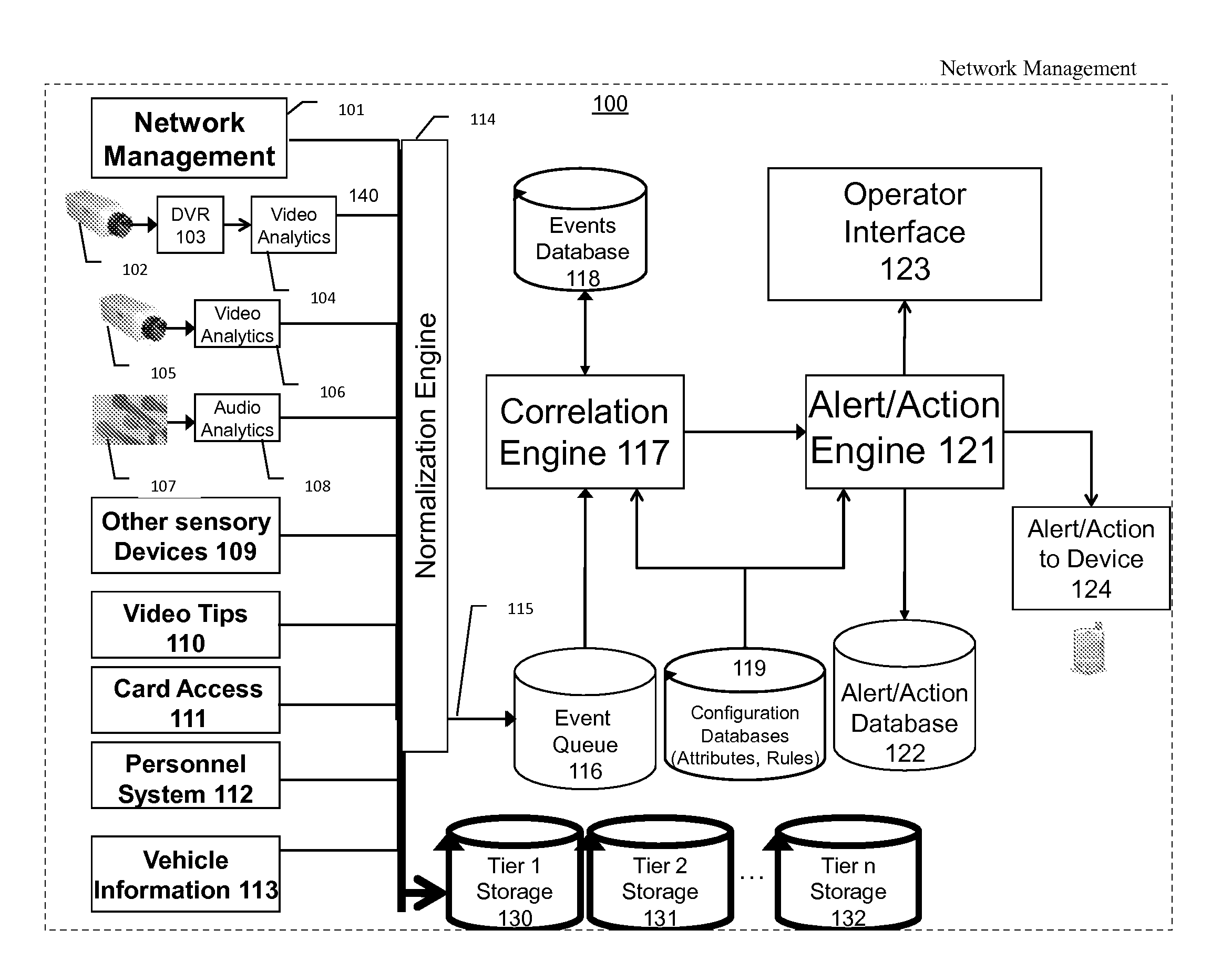
An audio surveillance, storage, and alerting system, including the following components: One or more audio sensory devices capture audio data having attribute data representing importance of the audio sensory devices. One or more audio analytics devices process the audio data to detect audio events. A network management module monitors network status of the audio sensory devices and generates network events reflective of the network status of all subsystems. A correlation engine correlates two or more events weighted by the attribute data of the device used to capture the data. Finally, an alerting engine generates one or more alerts and performs one or more actions based on the correlation performed by the correlation engine. This invention may be used to help fight crime and help ensure safety procedures are followed.
Owner:SECURENET SOLUTIONS GRP
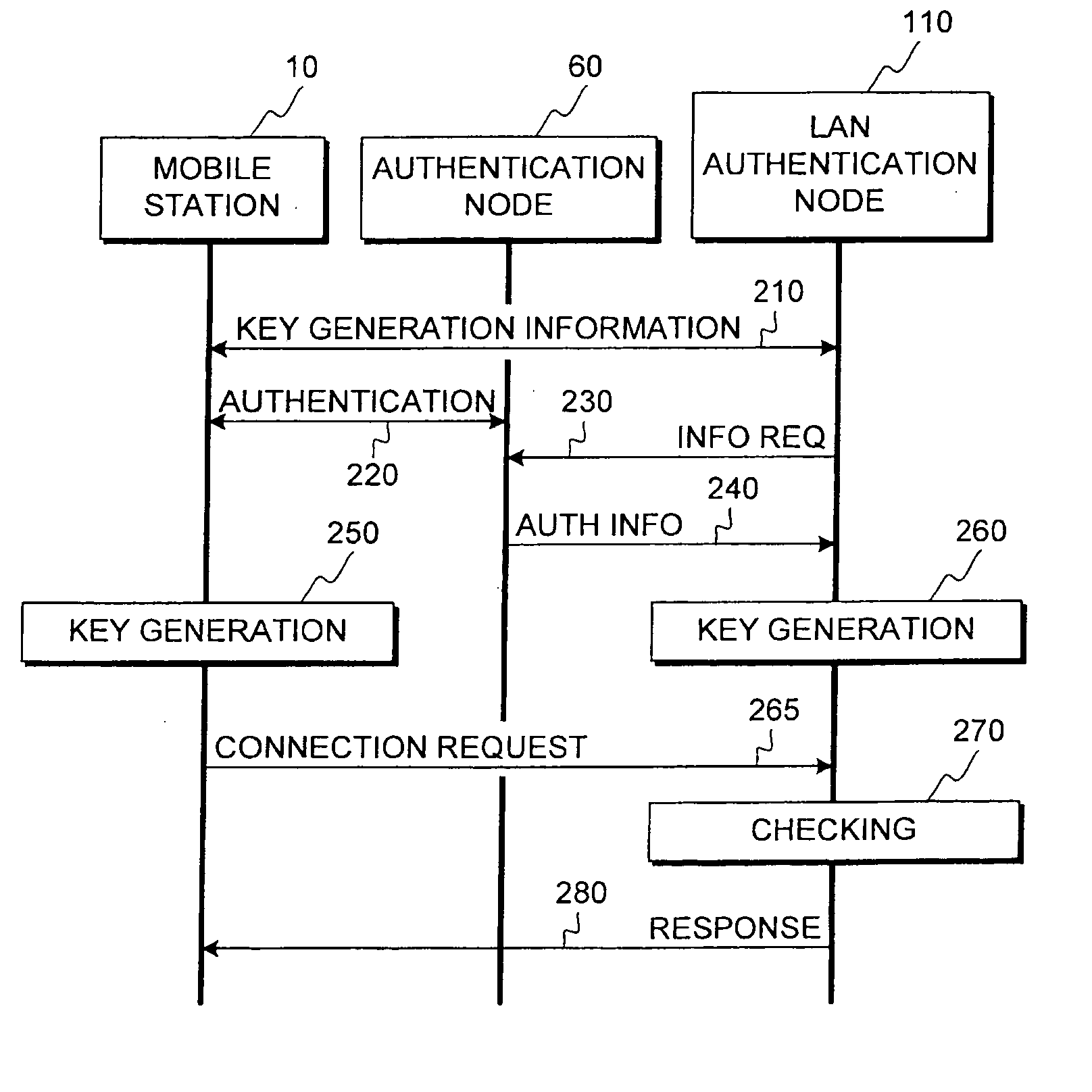
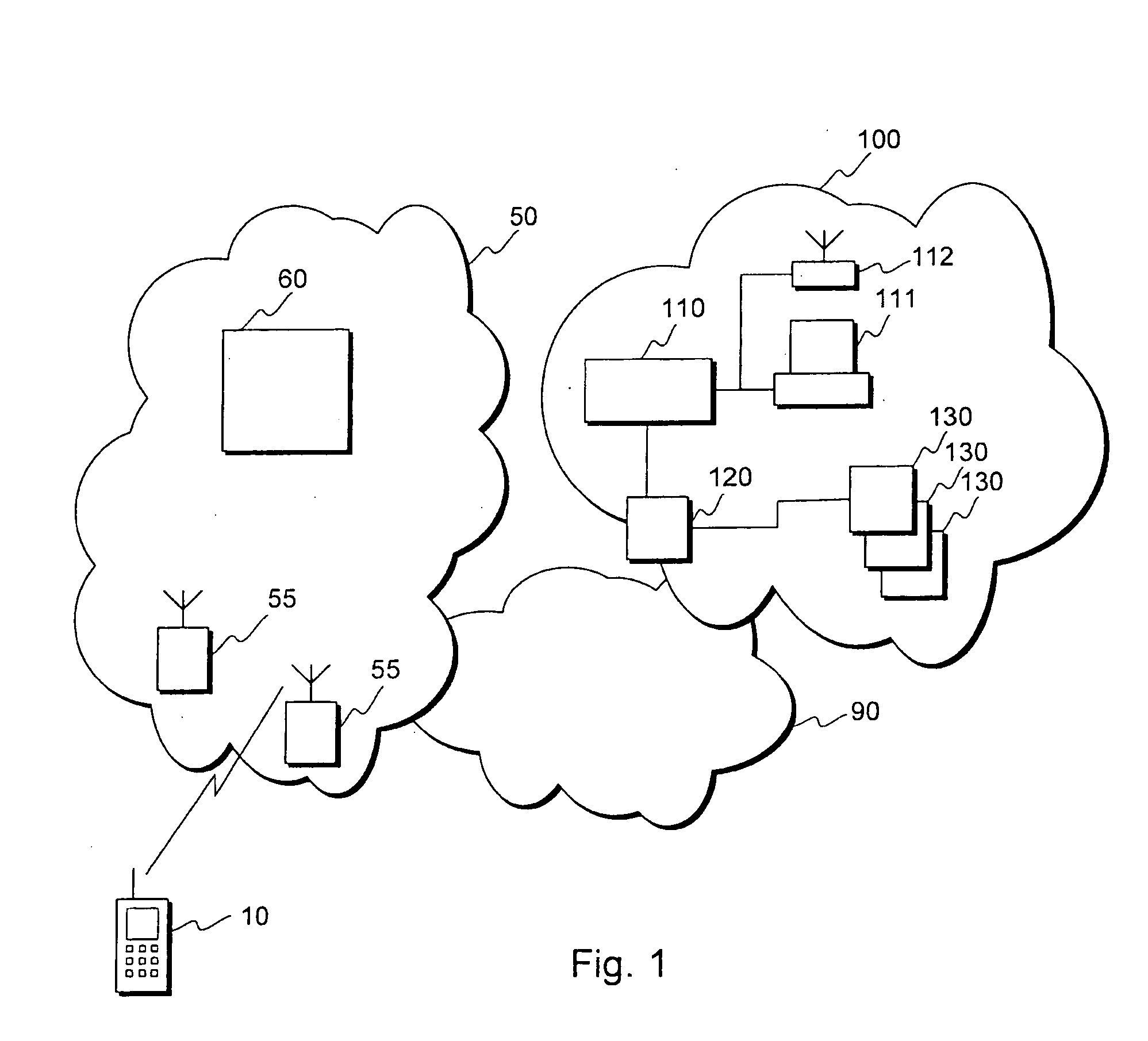
Method for producing key material
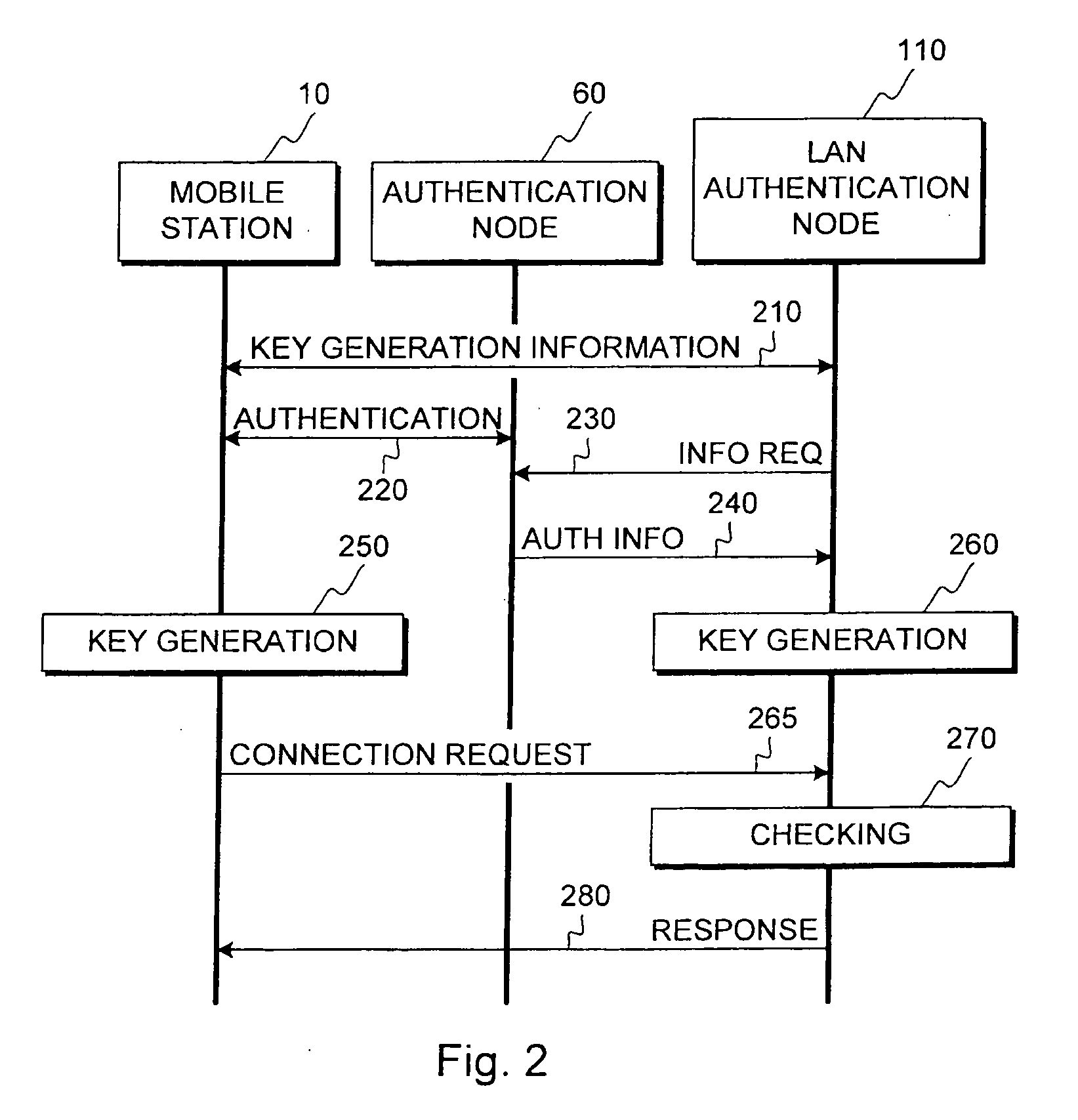
ActiveUS20060271785A1Key distribution for secure communicationUser identity/authority verificationCommunications systemMobile station
This invention relates to security procedures in a communication system, specifically to production of key material. The invention provides a method for producing key material in a highly secure way for use in communication with a local network of a company. The method uses authentication information obtained from the communication system and information exchanged locally between a mobile station and the authentication systems of the company to produce a communication key for use in authentication procedures or e.g. for signing and / or encrypting data.
Owner:NOKIA TECHNOLOGLES OY
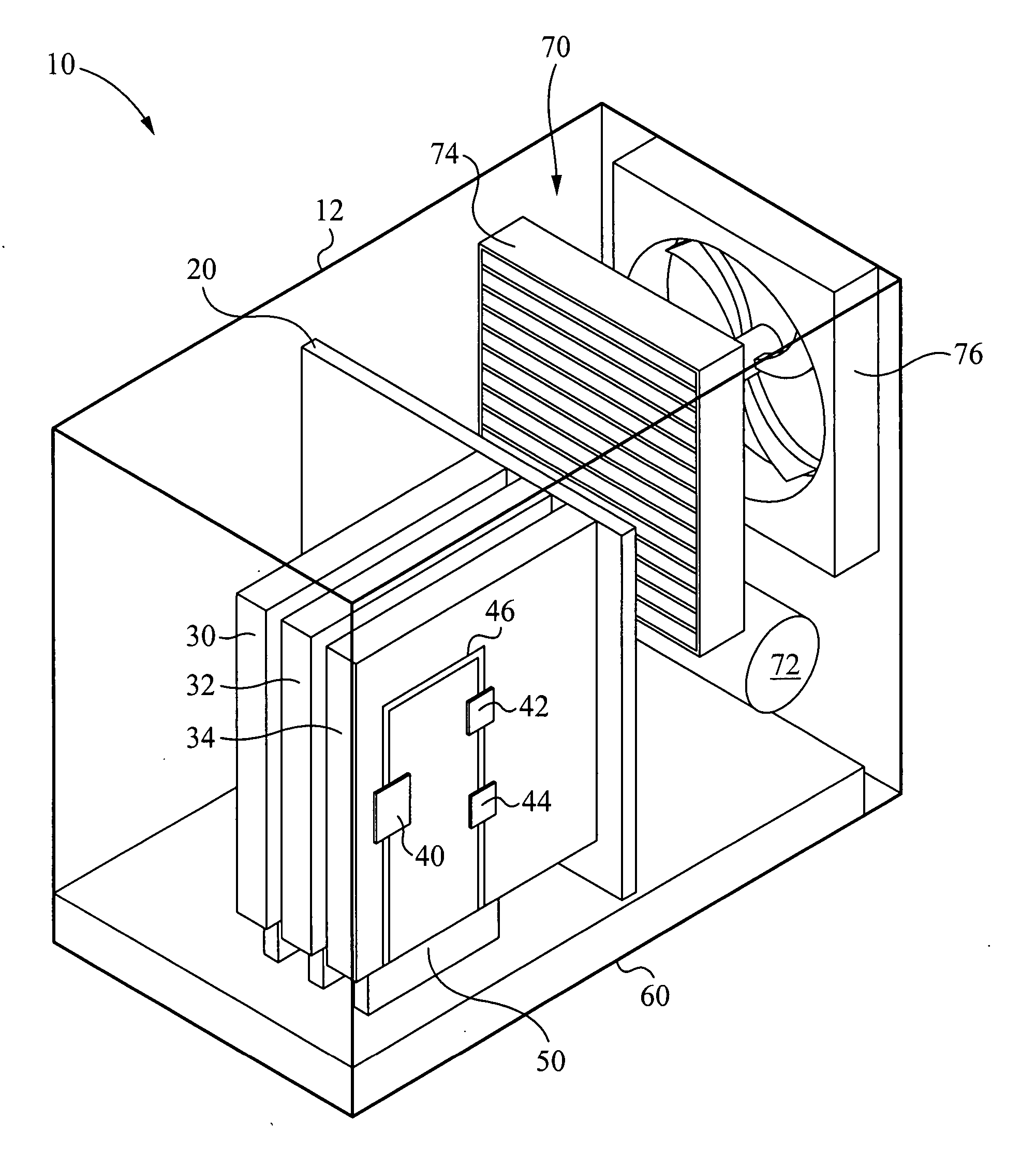
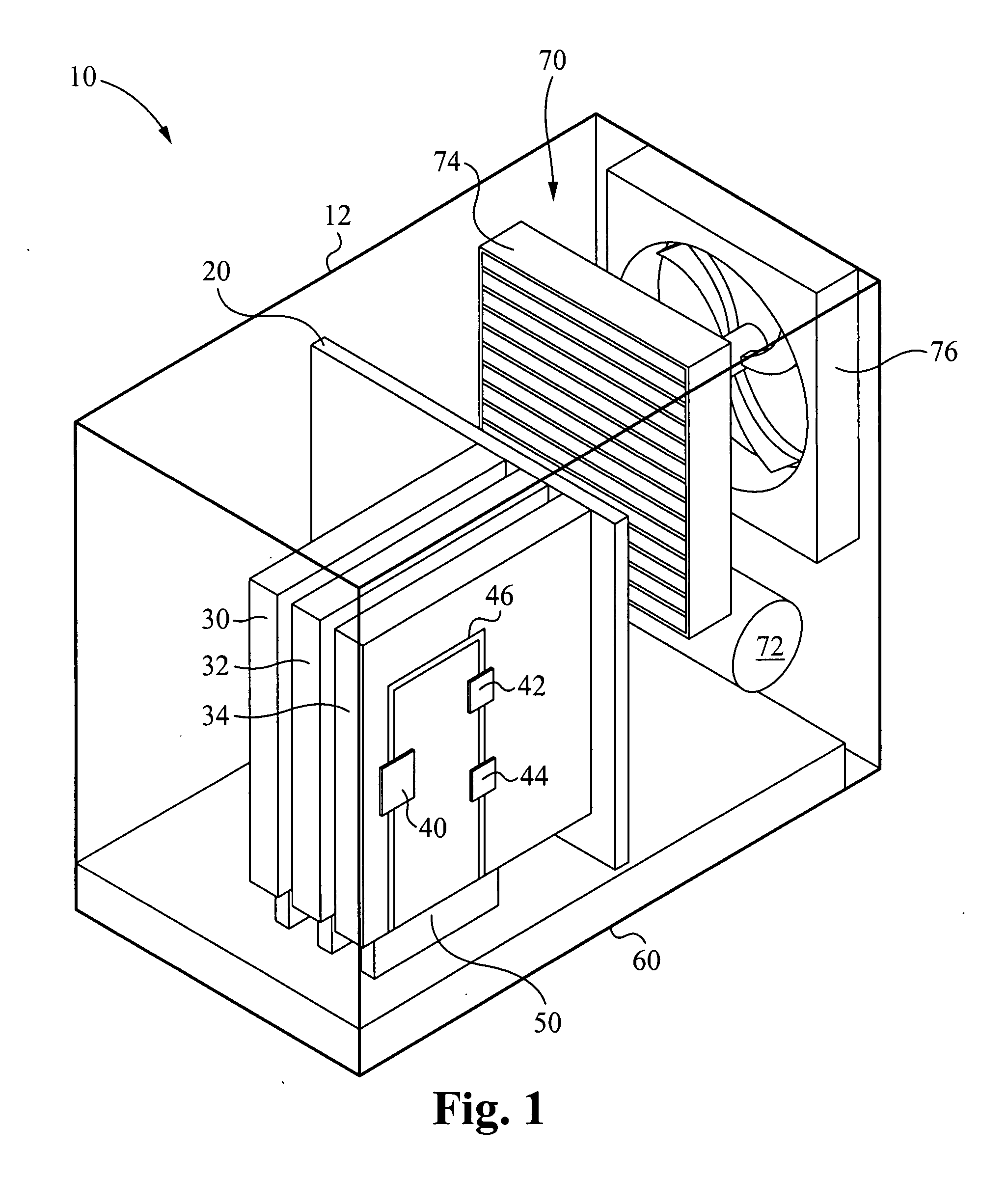
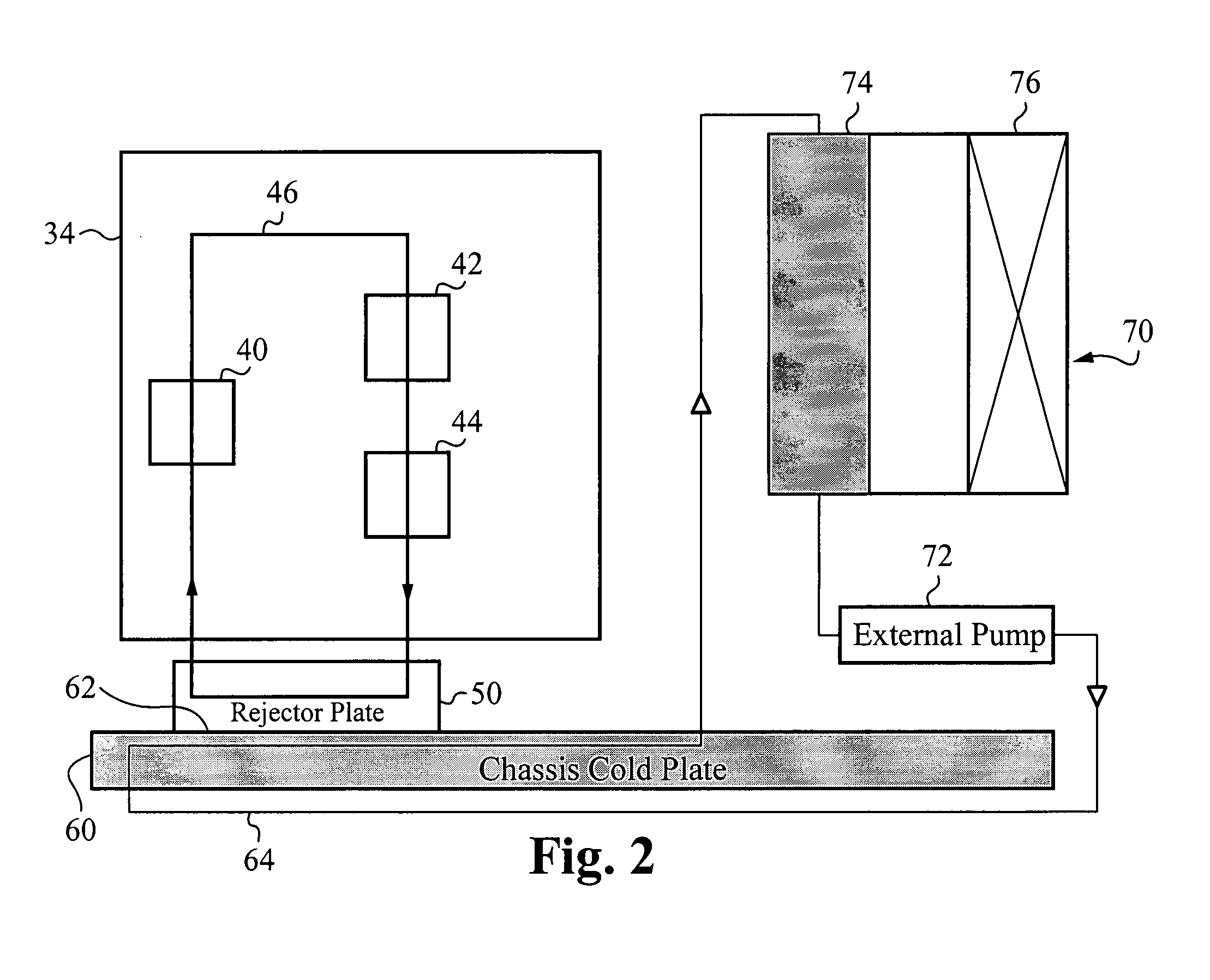
Liquid cooling loops for server applications
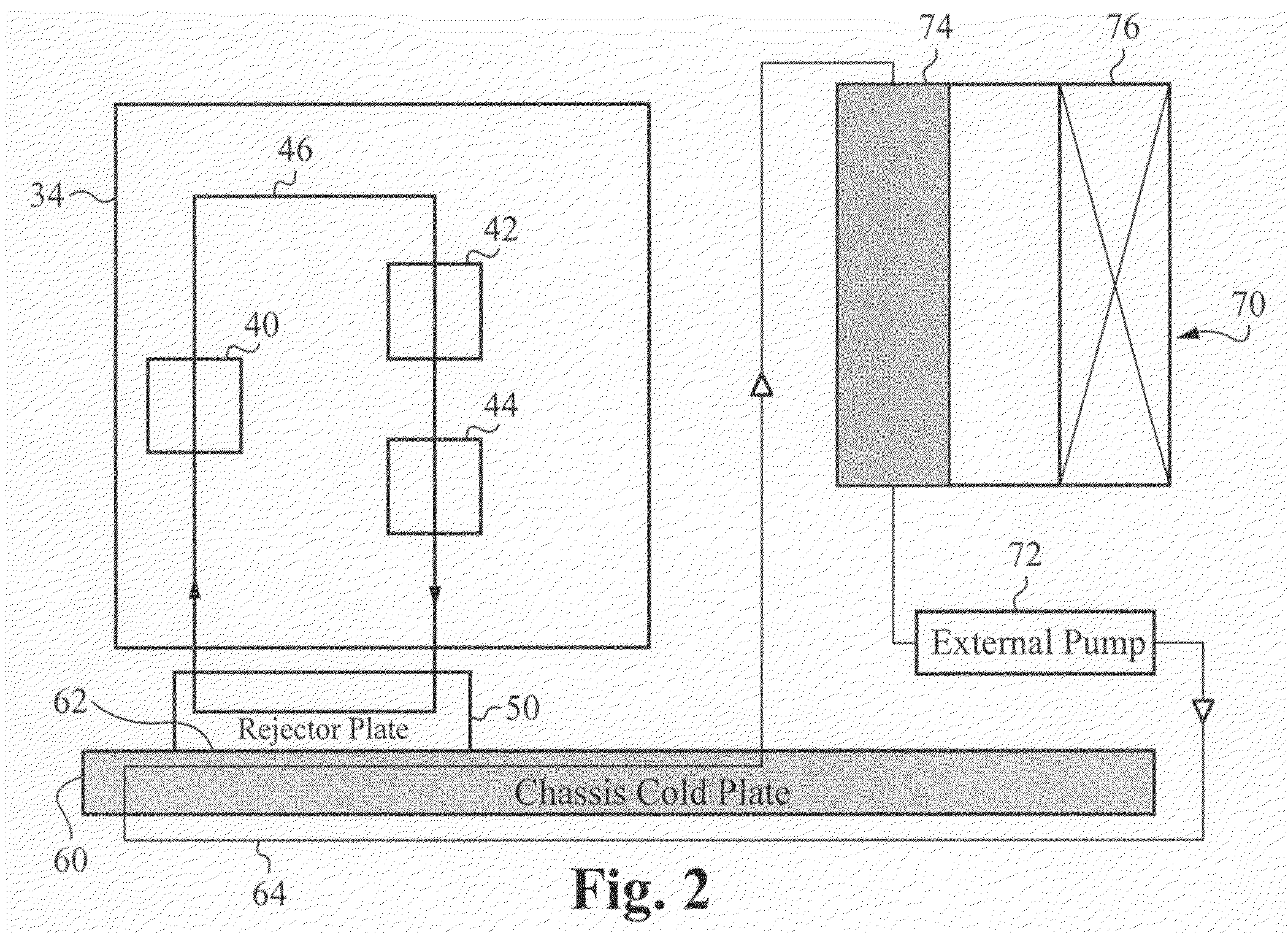
ActiveUS20070201210A1Reduce thermal resistanceIncrease surface areaSolid-state devicesFurniture partsElectricityLocking mechanism
A mounting system provides mechanisms and form factors for bringing a heat exchanger from a server rack into thermal contact with a heat exchanger from a electronics server. To ensure good thermal contact, pressure is applied between the two heat exchangers, the rejector plate and the chassis cold plate. The mounting mechanism used to engage and disengage the heat exchangers is configured to isolate the force applied to the two heat exchangers. The mounting mechanism includes an interlocking mechanism that prevents transfer of the applied force to the rest of the electronics server. Without isolating this force, the force is applied to the electronics server and / or the rack chassis, possibly disconnecting the electrical connections between the electronics server and the rack, as well as providing mechanical stress to the electronics server and the rack chassis. The mounting mechanism is also coupled to the electronics server locking mechanism such that the action of locking the electronics server into the rack causes the heat exchangers to engage in thermal contact. This is a fail safe procedure since no separate process is required to engage the electronics server cooling loop.
Owner:LIEBERT
VLAN router with firewall supporting multiple security layers
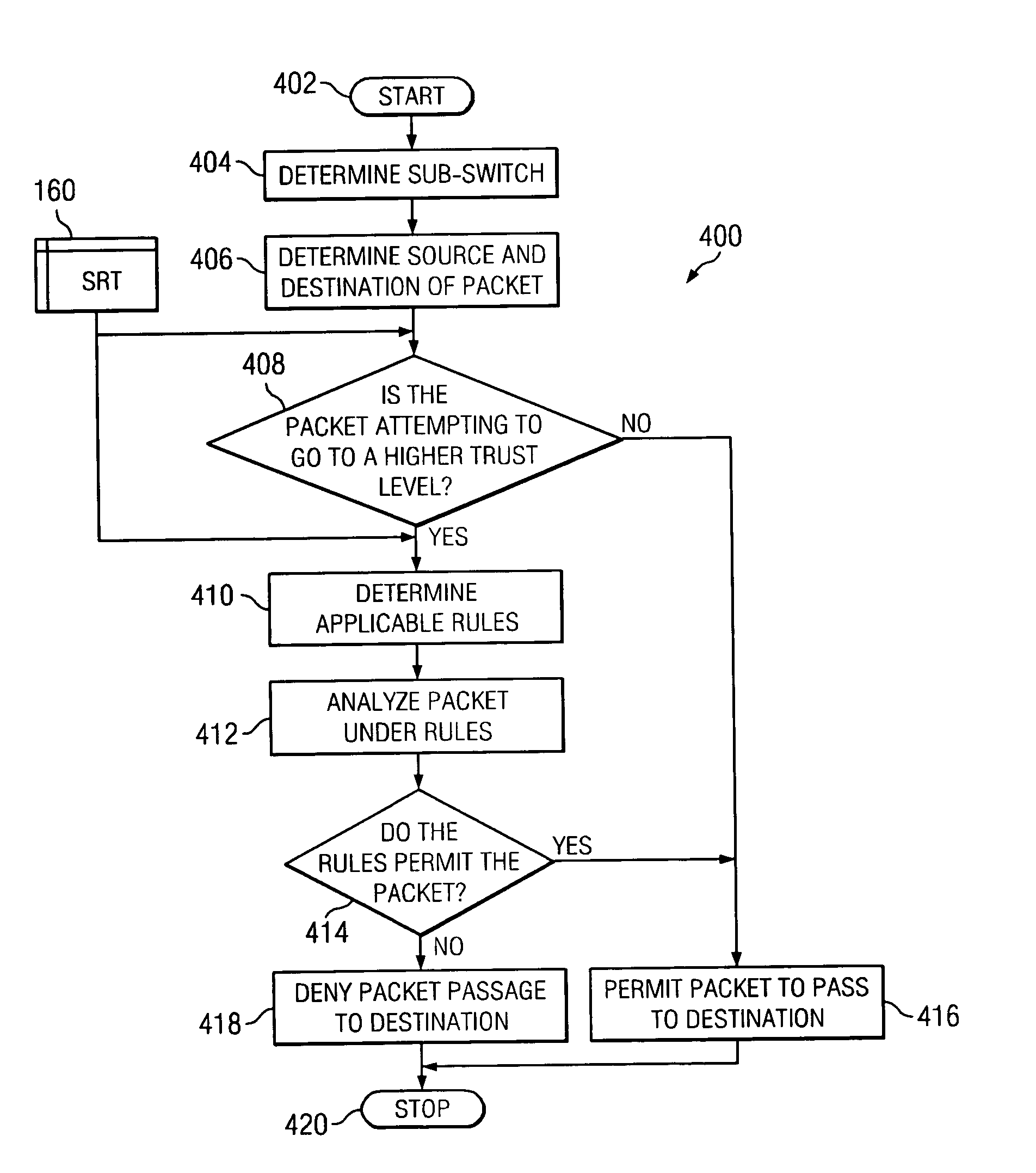
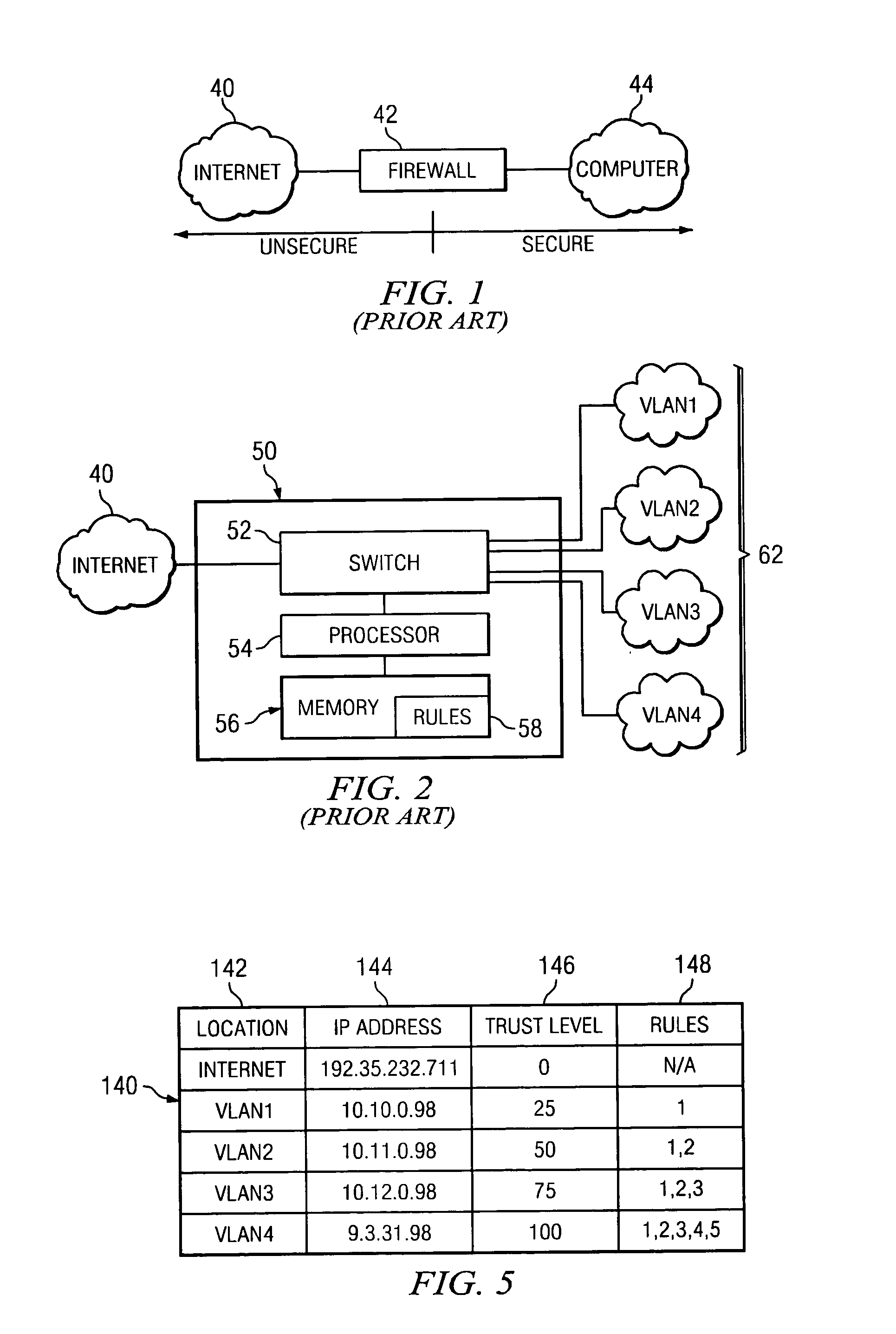
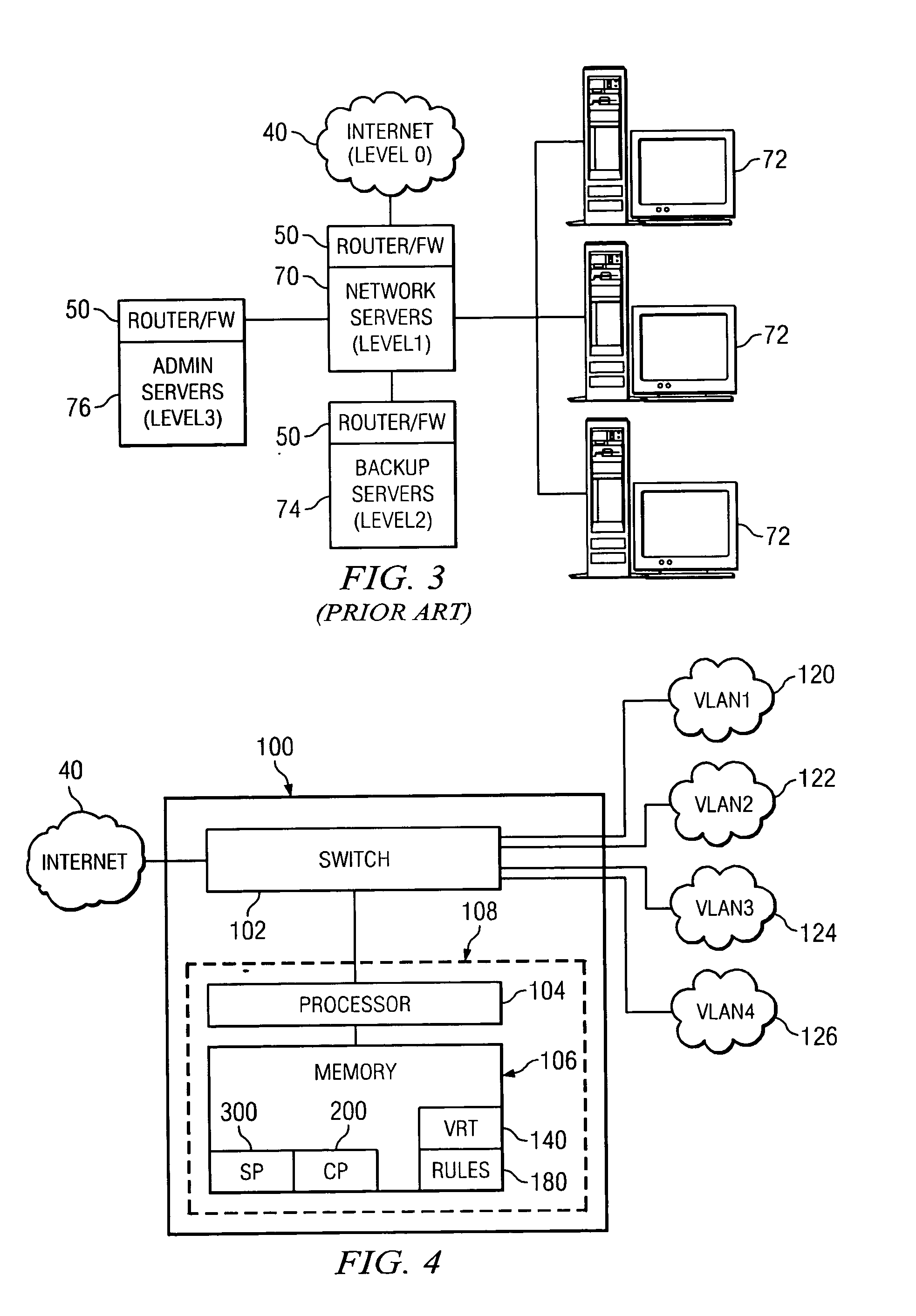
InactiveUS20050081058A1Eliminates redundant ruleShorten comparison timeDigital data processing detailsMultiple digital computer combinationsVirtual LANTrust level
A router containing a firewall capable of supporting a plurality of different security levels. The router of the present invention creates a plurality of Virtual Local Area Networks (VLANs) using a network switch. The VLAN Rules Table (VRT) allows a network administrator to designate a trust level for each VLAN. The trust level may be different for every VLAN and the administrator may designate different rules for each VLAN. The Security Program (SP) analyzes each packet passing through the firewall and determines if the packet is permitted under the rules for the VLAN trust level. An alterative embodiment in which the switch in the router is divided into a plurality of sub-switches is also disclosed. In the alternative embodiment, the firewall need only compare the packet to rules which were not applied in the lower trust levels, eliminating the redundant rules from the comparison process.
Owner:TREND MICRO INC
Systems and methods for insurance product pricing and safety program management
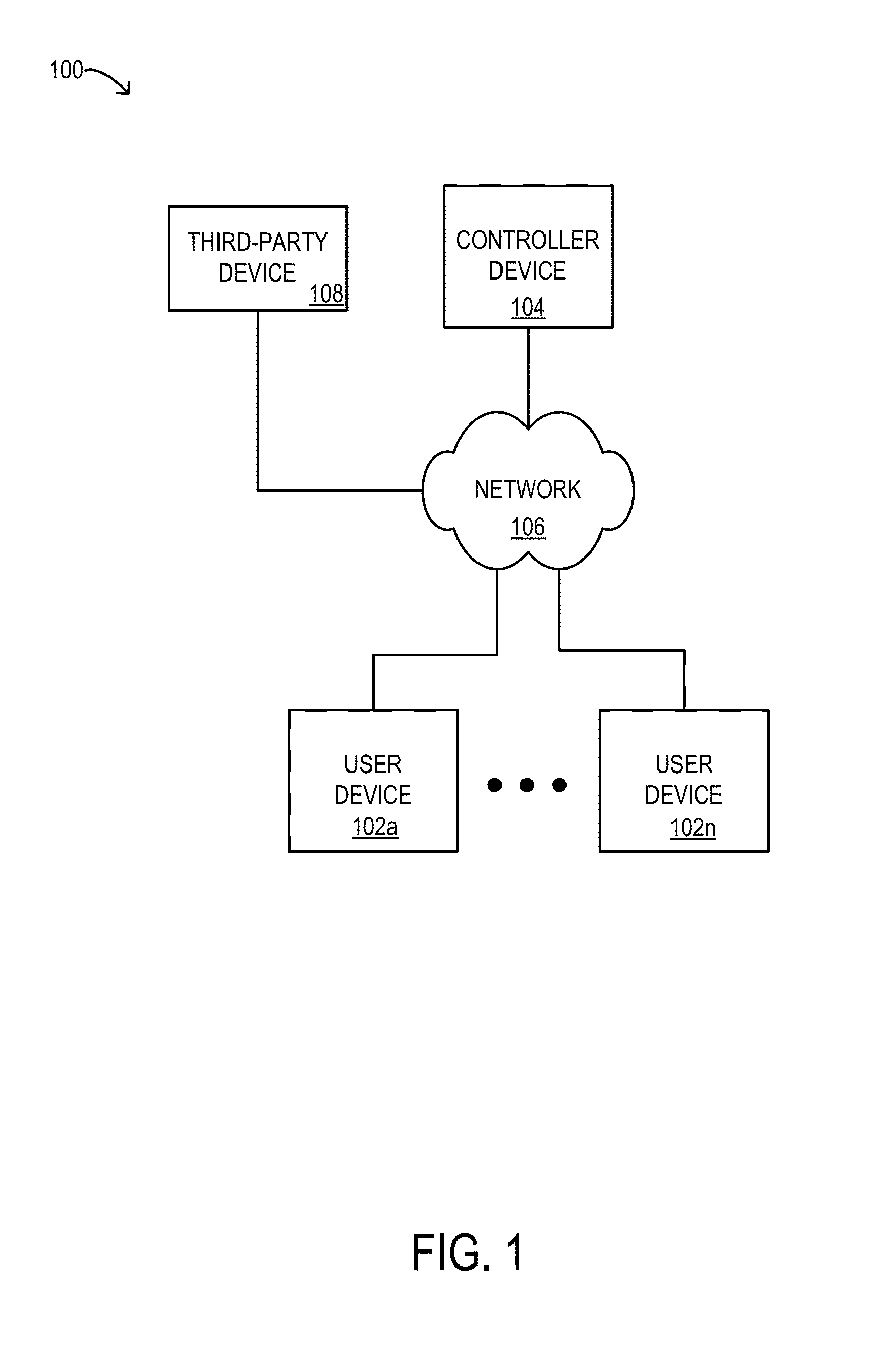
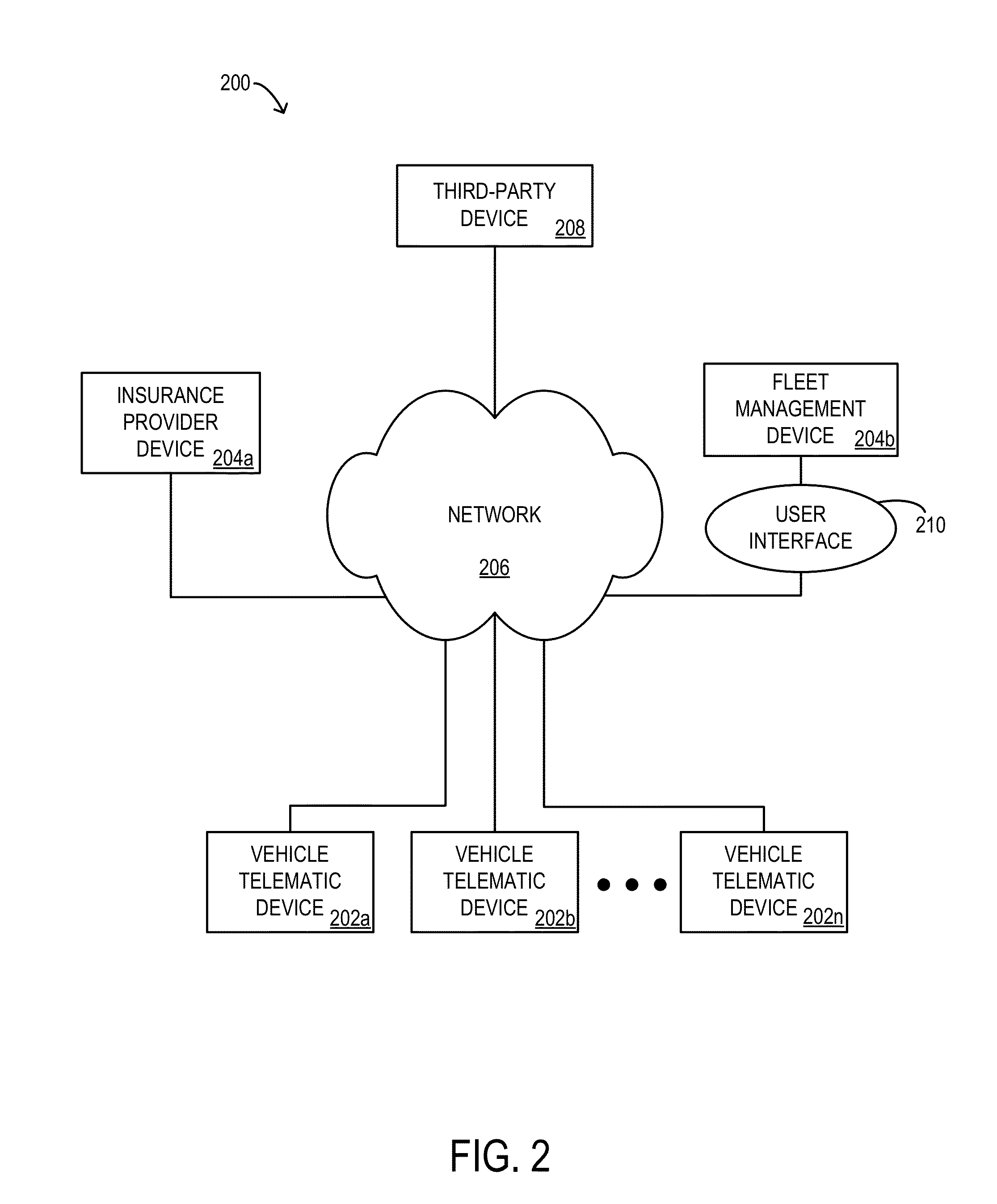
Systems, apparatus, interfaces, methods, and articles of manufacture that provide for insurance product pricing and safety program management such as, for example, utilizing vehicle telematics to determine product premiums, surcharges, and / or discounts and providing safety program management advice regarding how product pricing may be changed.
Owner:THE TRAVELERS INDEMNITY
Method and system of processing a plurality of data processing requests, and method and system of executing a program
InactiveUS6463480B2Avoid wastingImprove reliabilityProgram initiation/switchingProgram control using stored programsClient-sideComputer science
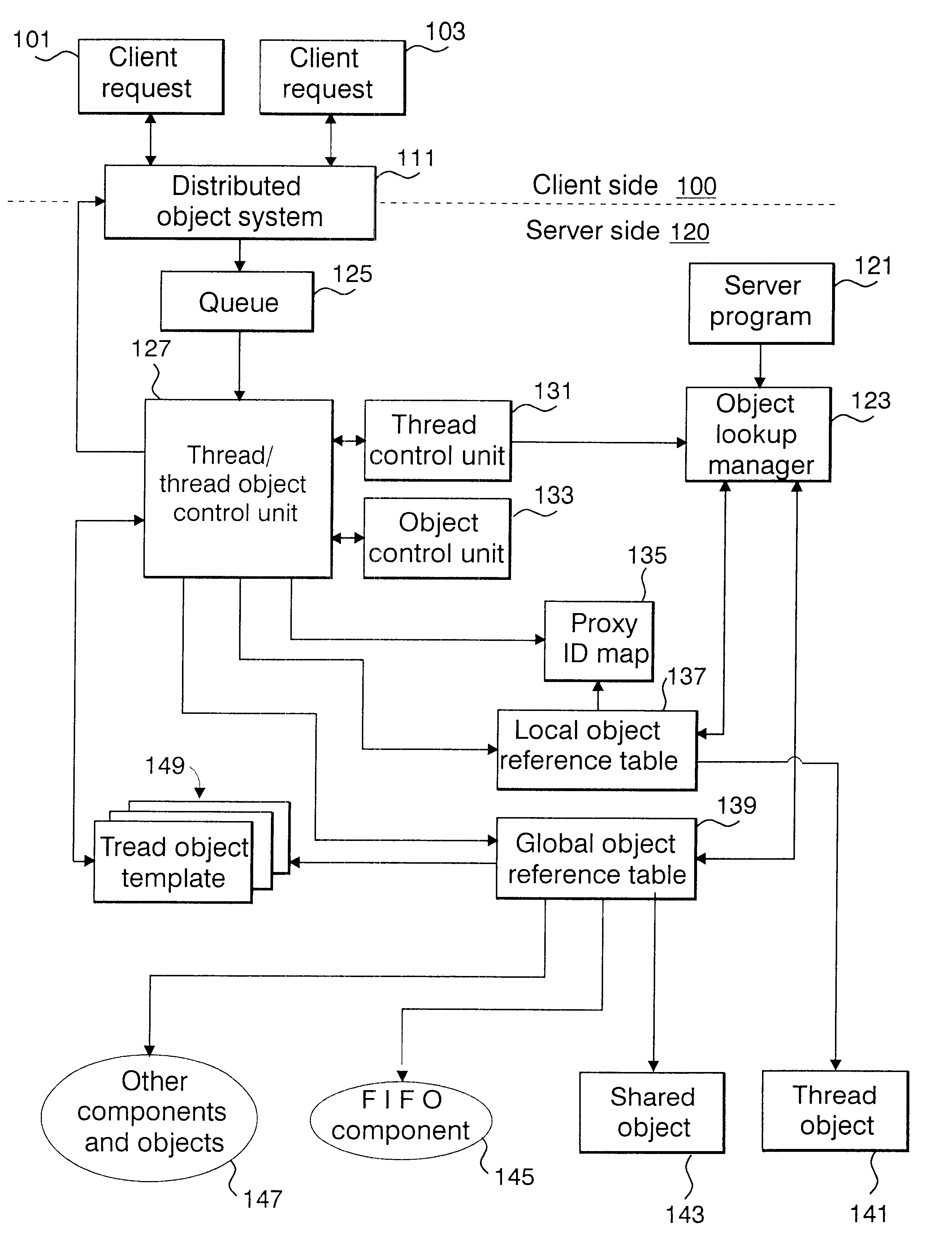
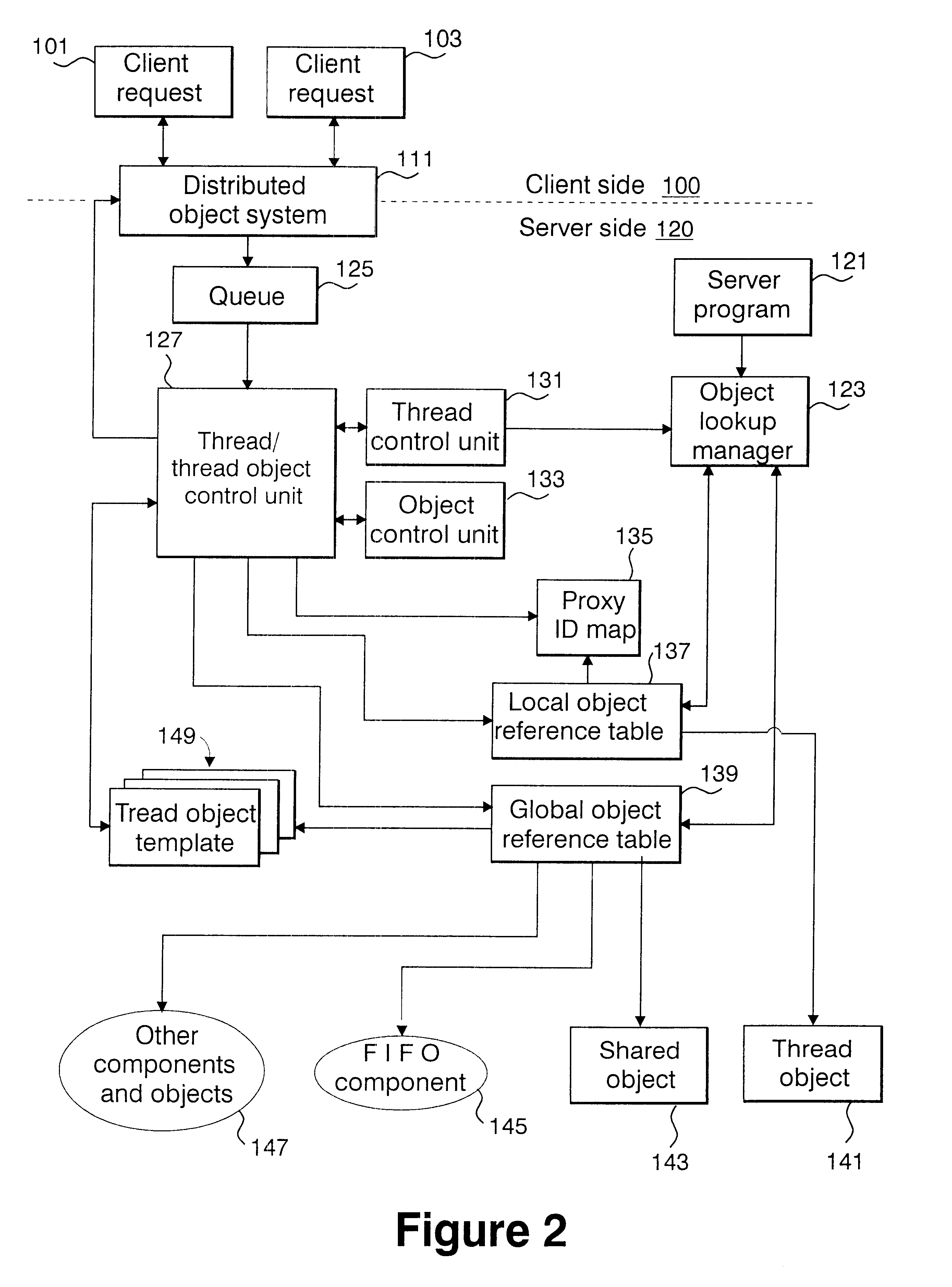
The present invention is directed to an environment in which a safe program having high thread isolation can easily be constructed, and the effective utilization of resources can be achieved when concurrently processing a plurality of client requests. More specifically, a client request 101 is transformed into a common format, and stored in a queue 125 in the form of packet information. A control unit 127 reads the packet information, and instructs a thread control unit 131 to create a thread. A thread object 141 referenced only from the created thread is created by copying a thread object template 149 prestored in the system. Client requests are divided into three types: creation of an object, utilization of an object method, and deletion of an object, and a thread is created only during the execution of a client request.
Owner:INT BUSINESS MASCH CORP
Ensuring network connection security between a wrapped app and a remote server
InactiveUS20130291086A1Digital data processing detailsComputer security arrangementsOperational systemData stream
A network connection between an app on a mobile device and a remote server is either enabled or denied based on whether a security wrapped app can verify that the connection is with a known and trusted server. The wrapped app uses a socket interception layer injected into the app code along with a trust store, also part of the wrapped app to determine whether a network connection attempted by the app should be allowed. The layer buffers relevant function calls from the app by intercepting them before they reach the device operating system. If the layer determines that a network connection is attempted, then it snoops the negotiation phase data stream to discern when the server sends a certificate to the app. It obtains this certificate and compares it to data in the trust store and makes a determination of whether the server is known and trusted.
Owner:BLUE CEDAR NETWORKS INC
System and method for lost data destruction of electronic data stored on portable electronic devices
ActiveUS20060021007A1Reduces and eliminates riskReduce dataDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. Rules relating to encryption, as well as other security procedures, can be defined and entered by an administrator with access to the server, and then disseminated to each of a plurality of clients that access the server.
Owner:BEACHHEAD SOLUTIONS
Scalable and flexible information security for industrial automation
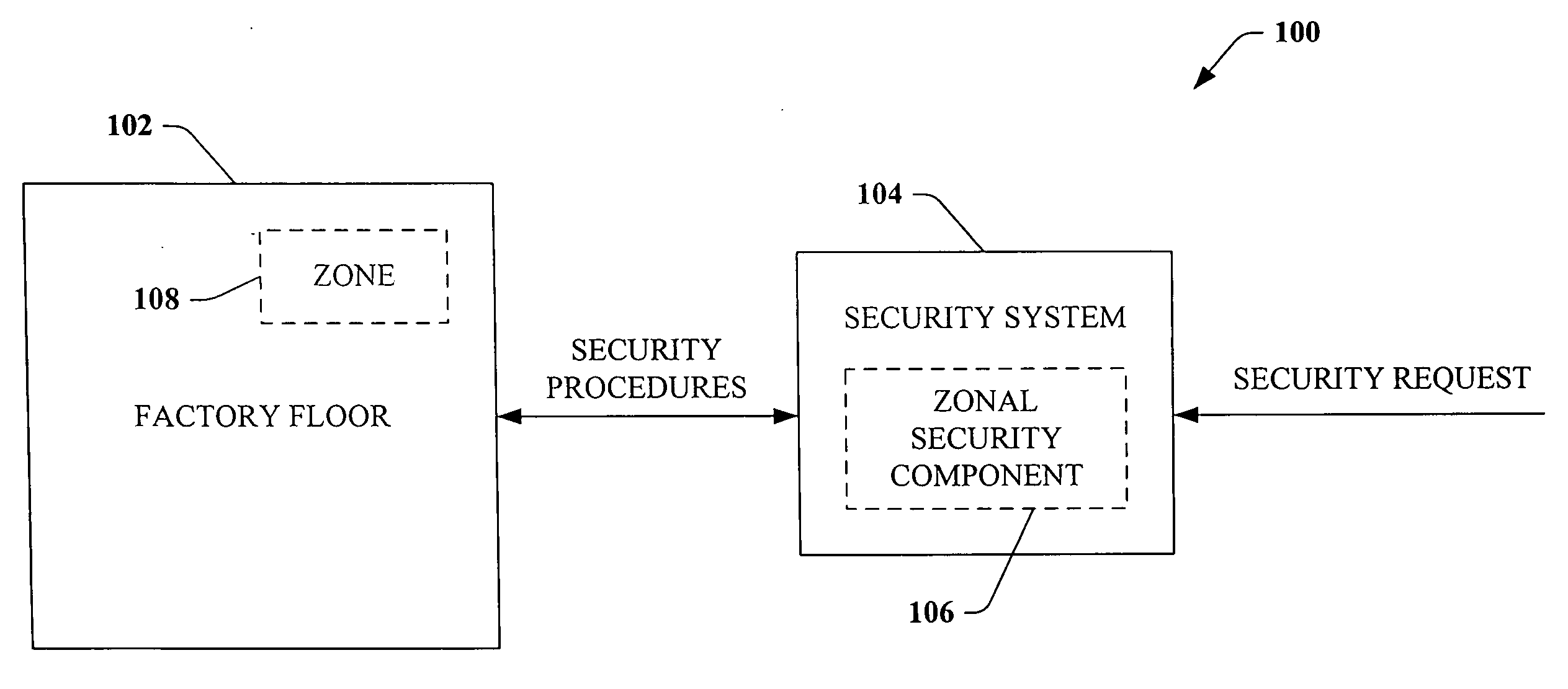
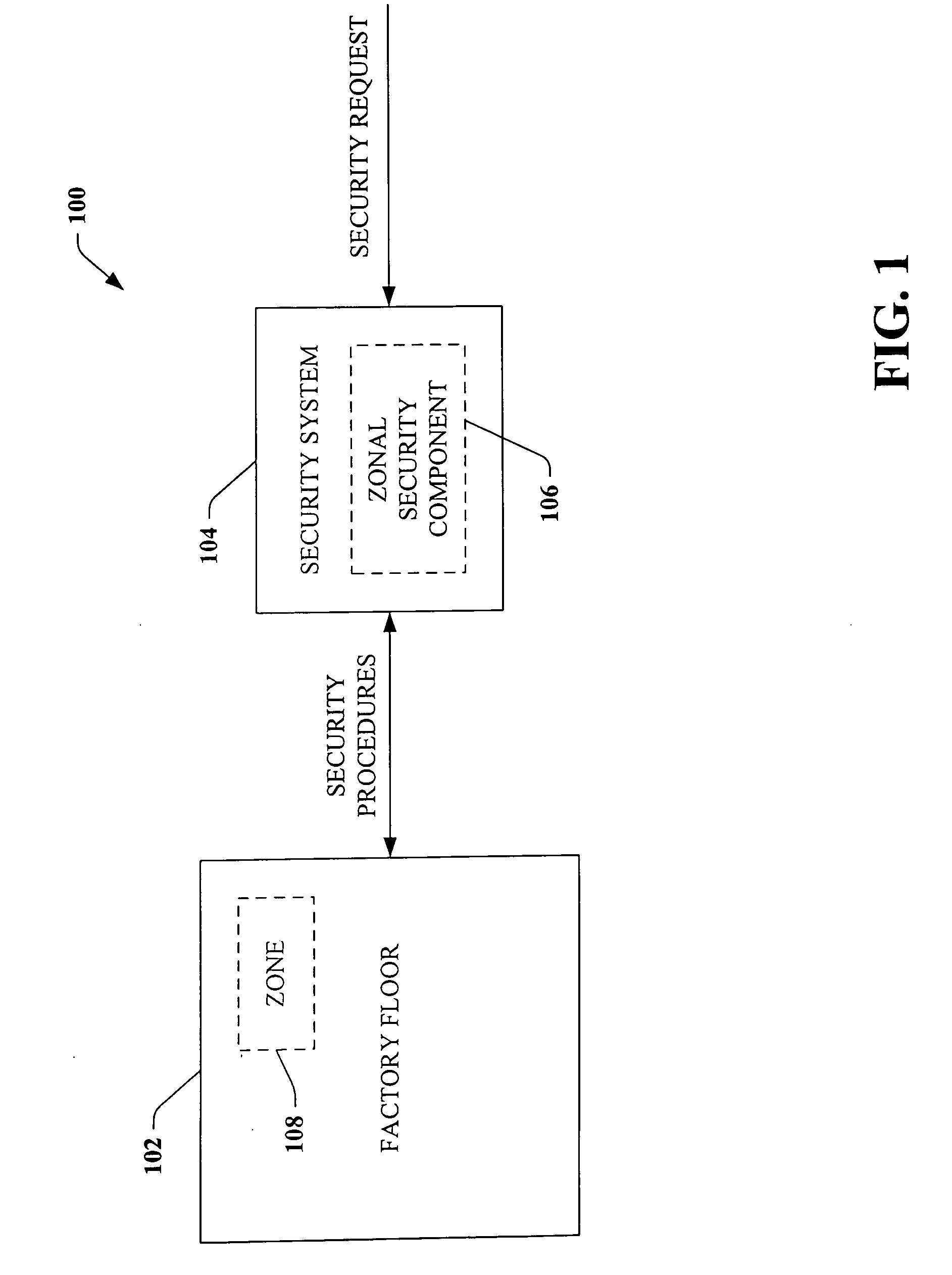
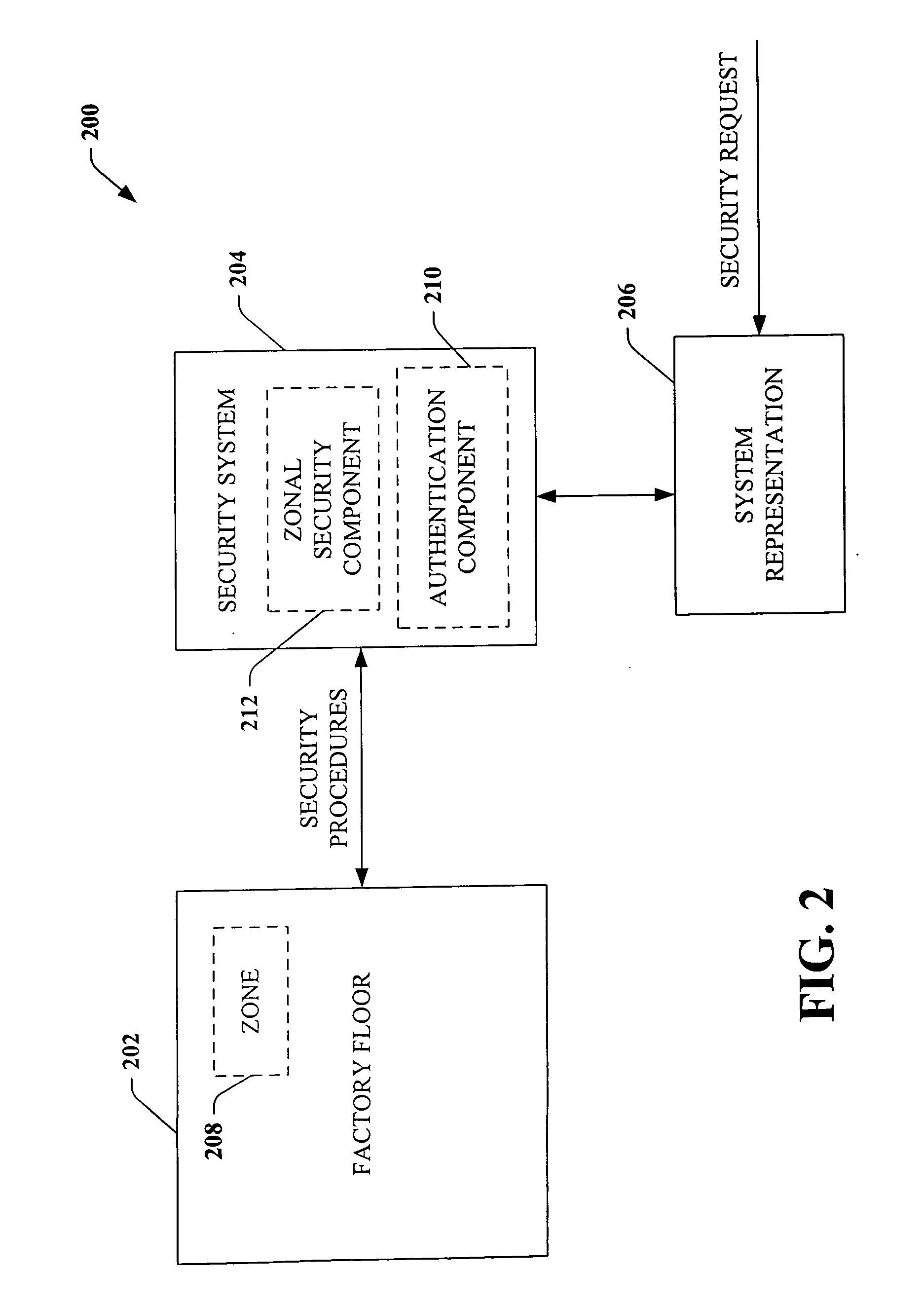
ActiveUS20060074917A1Compromising performance and throughput and securityImprove securityDigital data processing detailsTechnology managementSafe systemSafety procedure
A security system that relates to industrial automation security comprises a component that receives a request to modify security relating to a zone of a factory floor, the zone being less than an entirety of the factory floor. A zonal security component generates security procedures for the zone, the security procedures differ from security procedures implemented on the factory floor outside the zone.
Owner:ROCKWELL AUTOMATION TECH
Liquid cooling loops for server applications
A mounting system provides mechanisms and form factors for bringing a heat exchanger from a server rack into thermal contact with a heat exchanger from a electronics server. To ensure good thermal contact, pressure is applied between the two heat exchangers, the rejector plate and the chassis cold plate. The mounting mechanism used to engage and disengage the heat exchangers is configured to isolate the force applied to the two heat exchangers. The mounting mechanism includes an interlocking mechanism that prevents transfer of the applied force to the rest of the electronics server. Without isolating this force, the force is applied to the electronics server and / or the rack chassis, possibly disconnecting the electrical connections between the electronics server and the rack, as well as providing mechanical stress to the electronics server and the rack chassis. The mounting mechanism is also coupled to the electronics server locking mechanism such that the action of locking the electronics server into the rack causes the heat exchangers to engage in thermal contact. This is a fail safe procedure since no separate process is required to engage the electronics server cooling loop.
Owner:LIEBERT
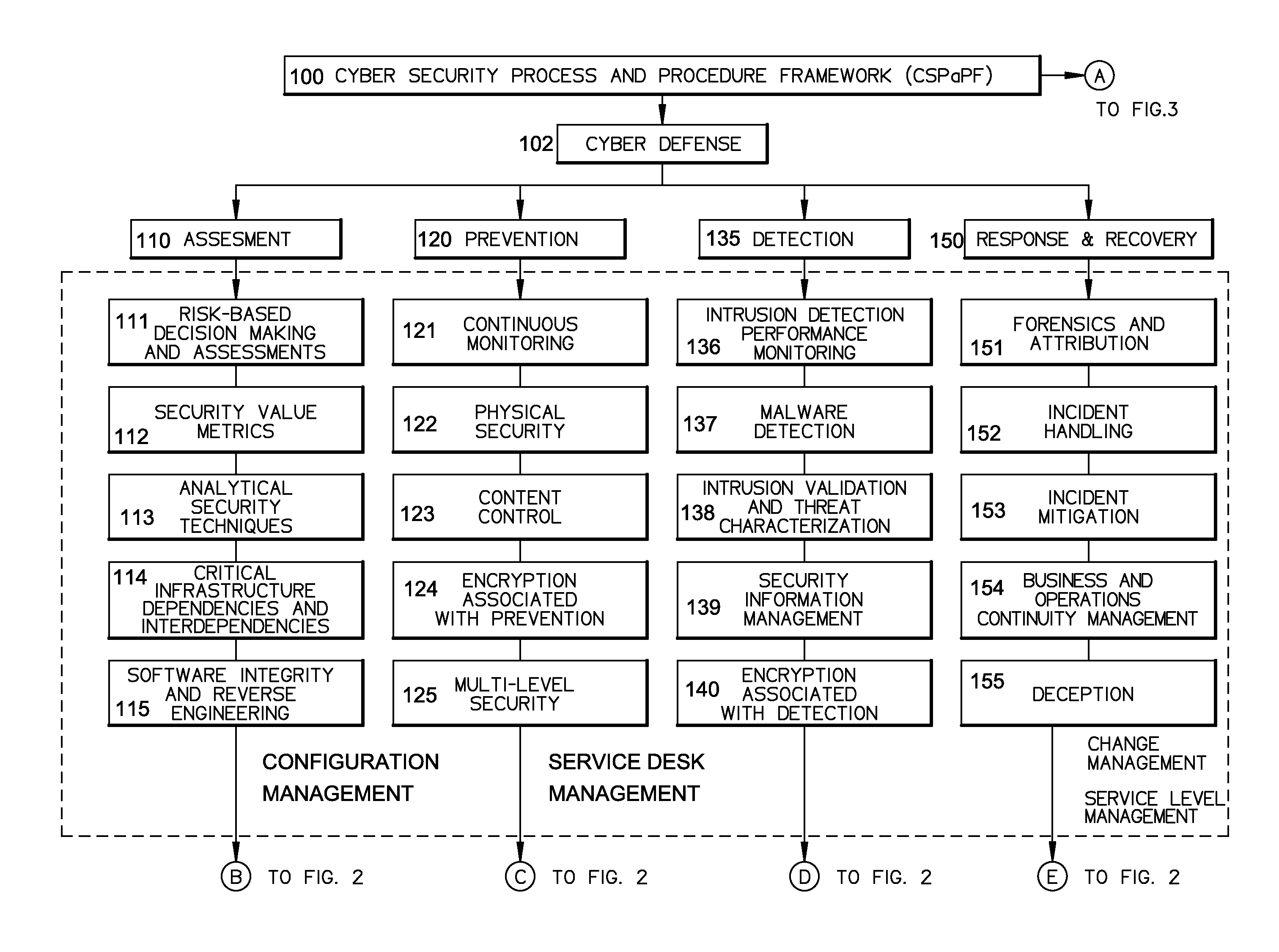
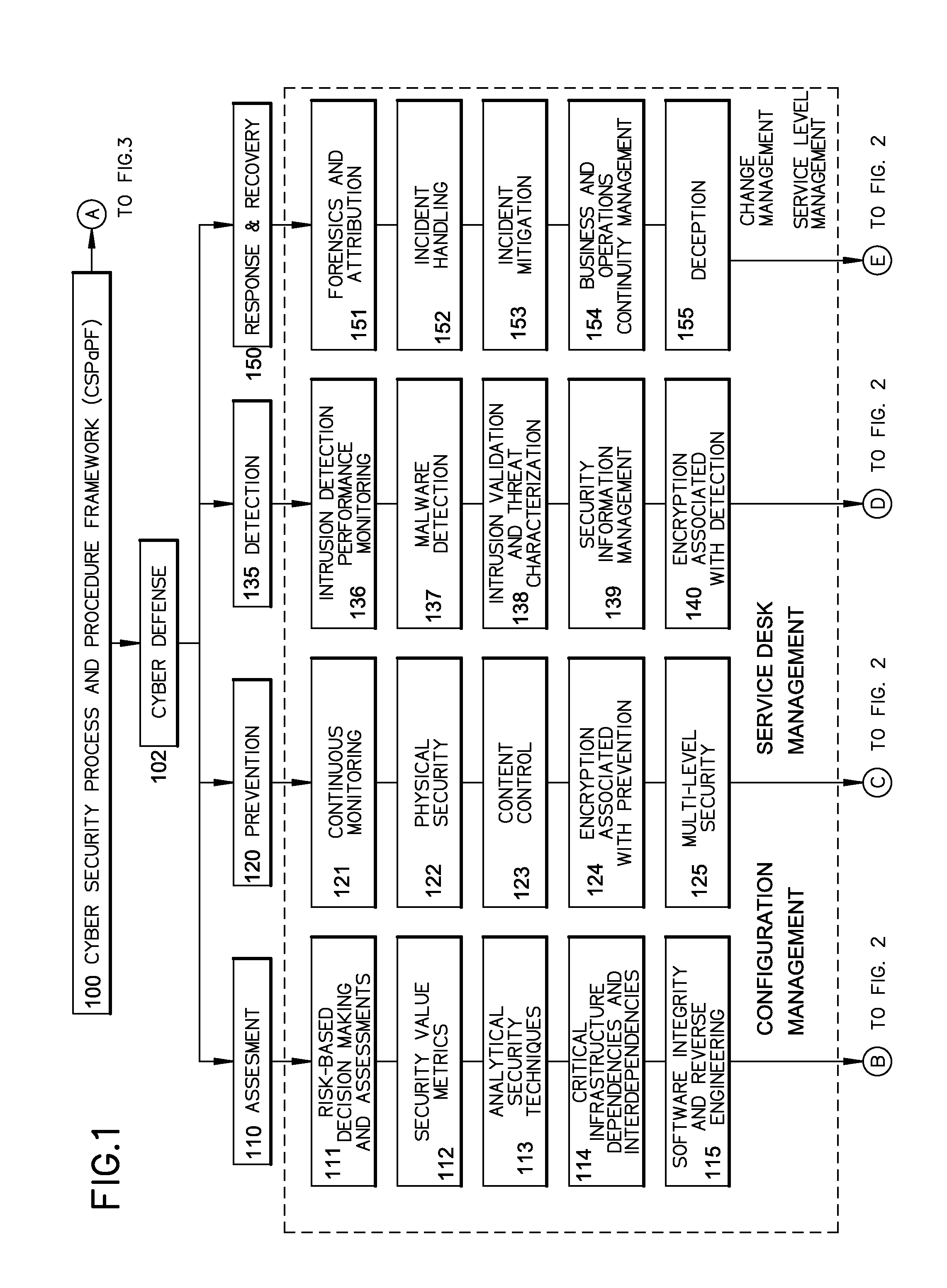
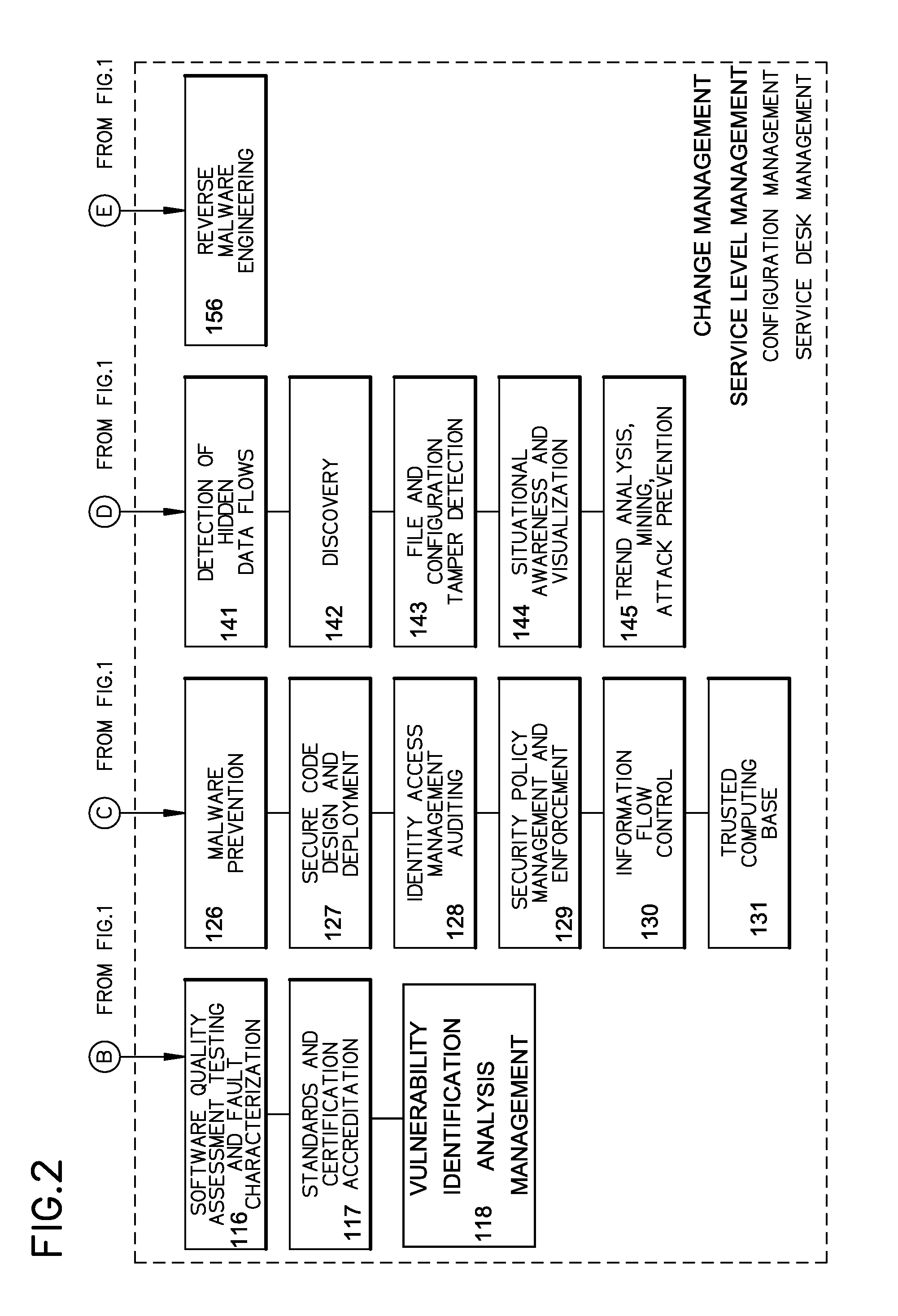
Method of providing cyber security as a service
InactiveUS20140259095A1Memory loss protectionError detection/correctionChange managementNetworked system
A cyber system including a method of providing cyber security as a service is provided. The cyber system may include an integrated architecture of defensive and offensive security procedures and processes that enable enterprises to practice safe, holistic security techniques. The plurality of cyber defense procedures may include a plurality of risk-based assessment procedures, a plurality of attack-prevention procedures, a plurality of detection procedures and a plurality of response and recovery procedures. The plurality of cyber offense procedures may include a plurality of cyber weapon procedures, a plurality of cyber Intelligence, surveillance and reconnaissance procedures, a plurality of information operations target exploitation procedures and a plurality of information operations attack procedures. The cyber system may also include a plurality of overlapping processes interconnecting the plurality of cyber offense procedures and plurality of cyber defense procedures. The plurality of overlapping processes may include a change management, a configuration management, a service desk and a service-level management. The change management may be structured within an enterprise for ensuring that changes in people, facilities, technology and / or processes are smoothly and successfully implemented to achieve lasting benefits. The configuration management may establish and maintain the consistency of a product's performance, functional and physical attributes with its requirements, design and operational information throughout its life. The service desk may provide the communication needs of the users, employees and customers. Service-level management may assess the impact of change on service quality and establish performance metrics and benchmarks.
Owner:BRYANT JAMES ALVIN
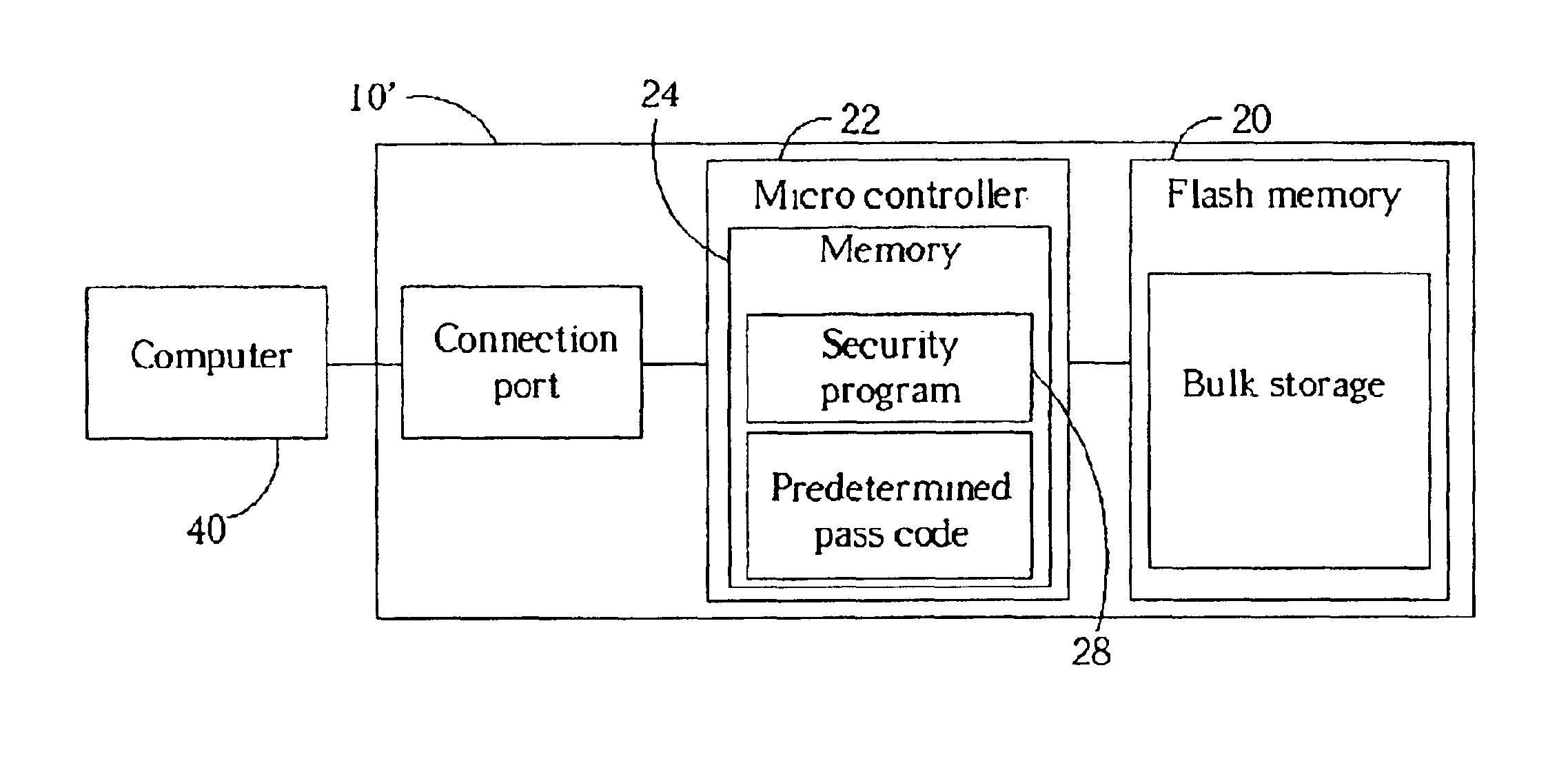
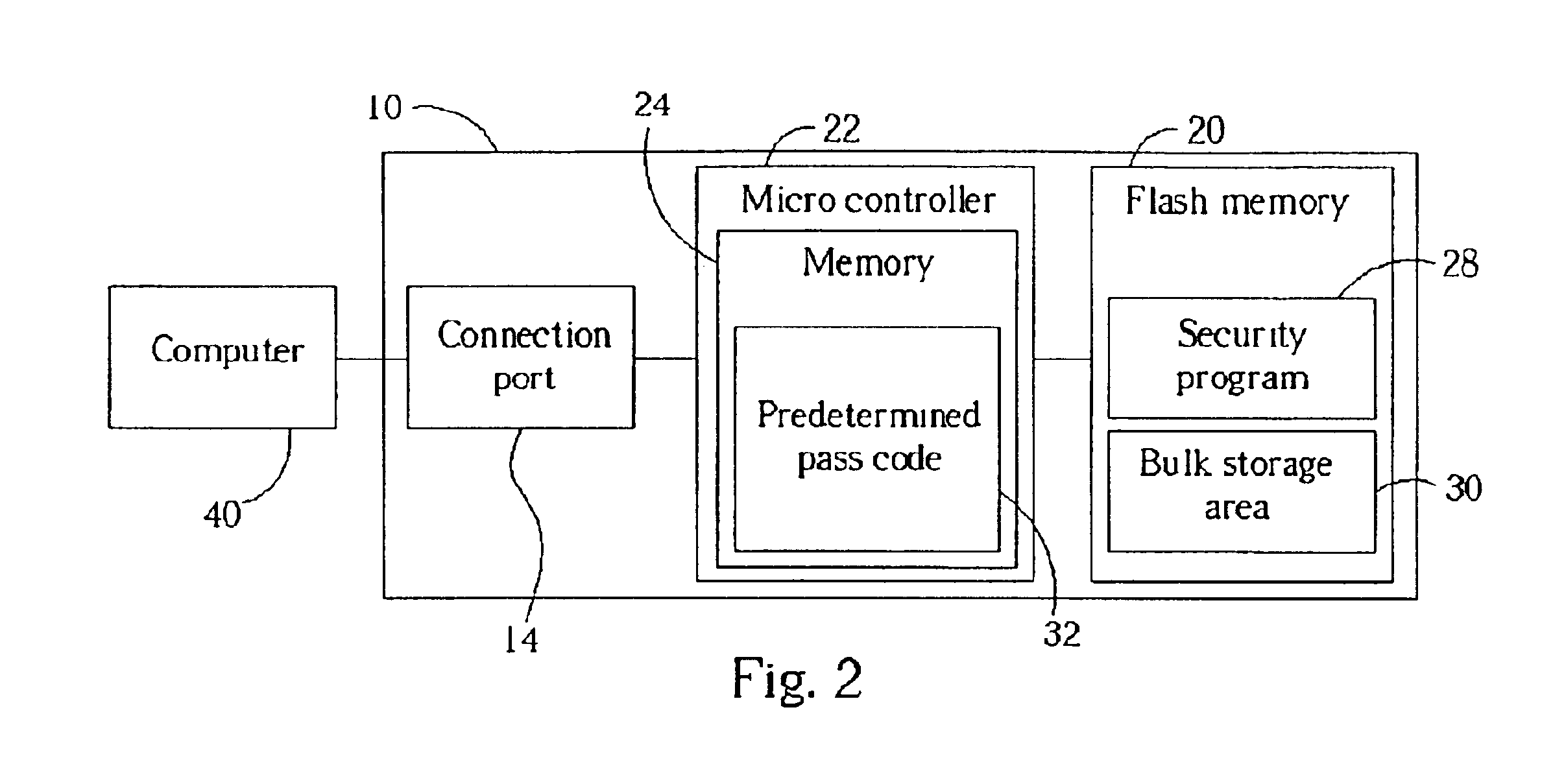
Secure flash memory device and method of operation
InactiveUS6904493B2Unauthorized memory use protectionHardware monitoringMicrocontrollerSafety procedure
A secure flash memory device includes a connection port, a microcontroller, a flash memory, and a security program. The security program provides pass code security between a computer connected to the connection port and the flash memory. The microcontroller controls the flow of data between the computer and the flash memory as allowed by the security program. The security program is stored in the flash memory or in the microcontroller and can be executed by the computer, when the microcontroller receives flash memory access requests from the connection port.
Owner:APACER
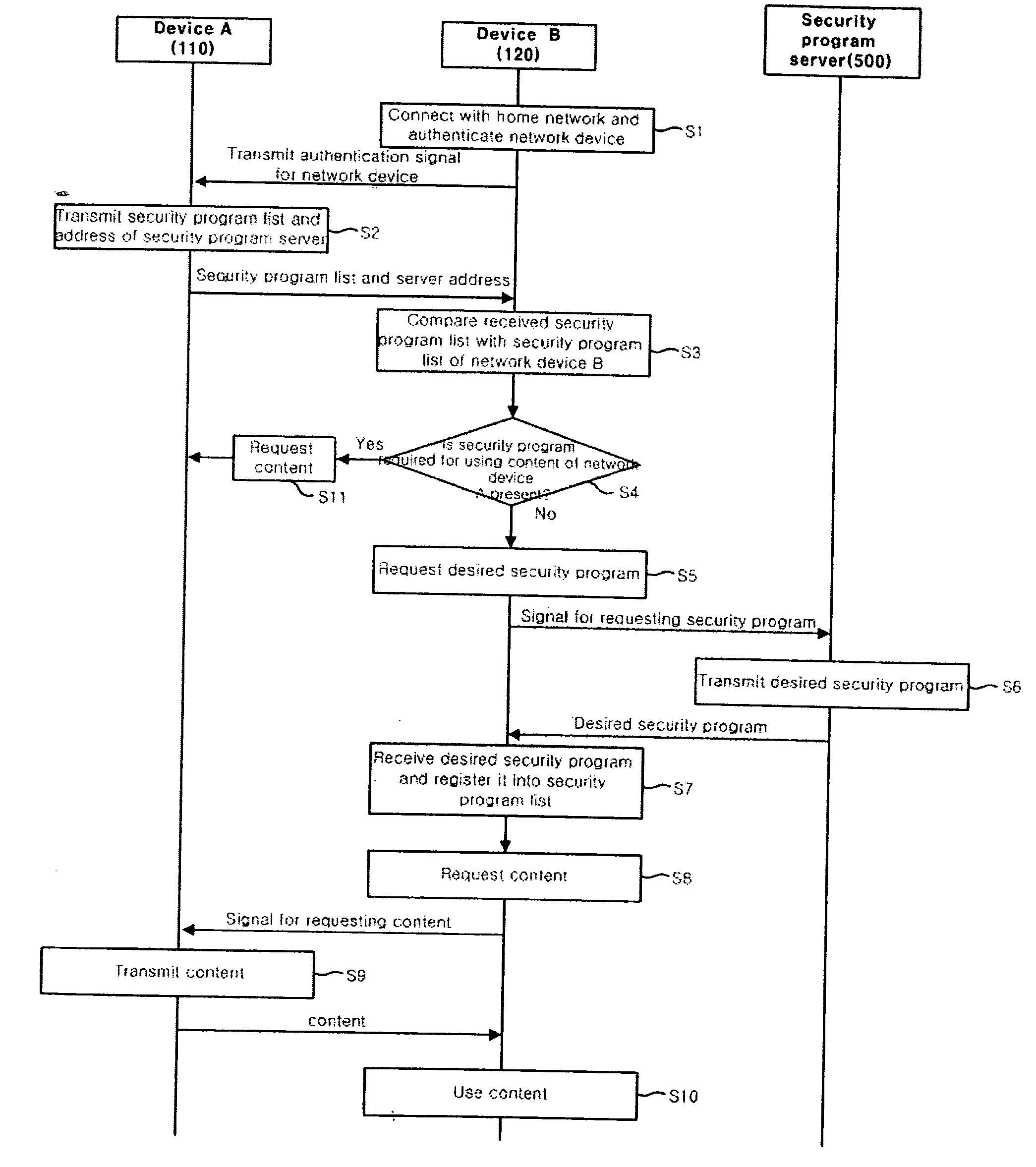
Network device and method for providing content compatibility between network devices having different respective digital rights management methods
ActiveUS20050022033A1Digital data processing detailsUnauthorized memory use protectionExchange networkComputer compatibility
The present invention relates to a network device and a method for providing content compatibility between network devices having different respective digital rights management methods. The method includes exchanging security program lists of the network devices, comparing the security program list of one network device with the security program list of the other network device based on the exchanged security program lists, and installing a security program required for using content of the other network device according to the comparison result. Accordingly, there is an advantage in that the network devices using the different respective DRM-based security programs can exchange content with one another and use the content of the other network device by using the predetermined security program update methods.
Owner:SAMSUNG ELECTRONICS CO LTD
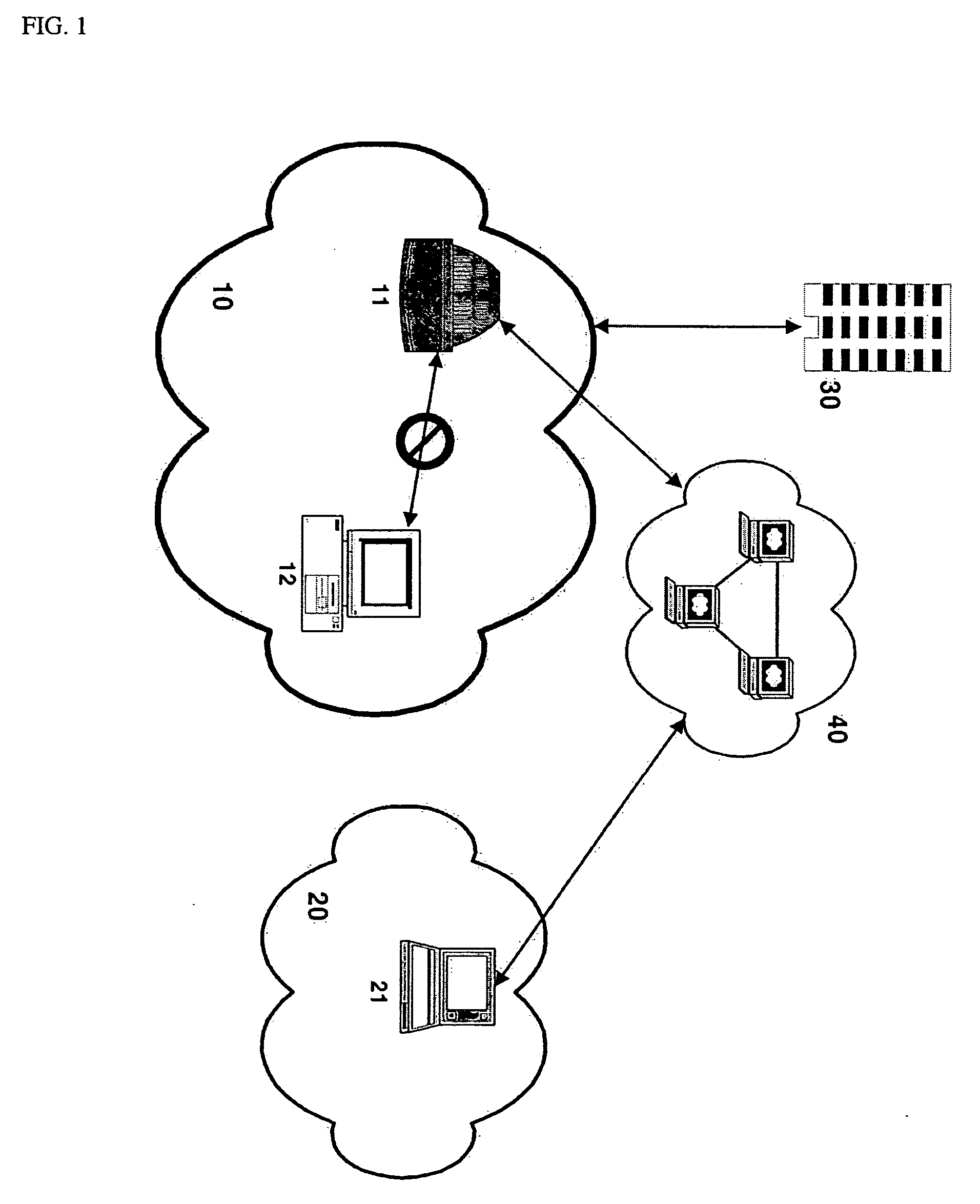
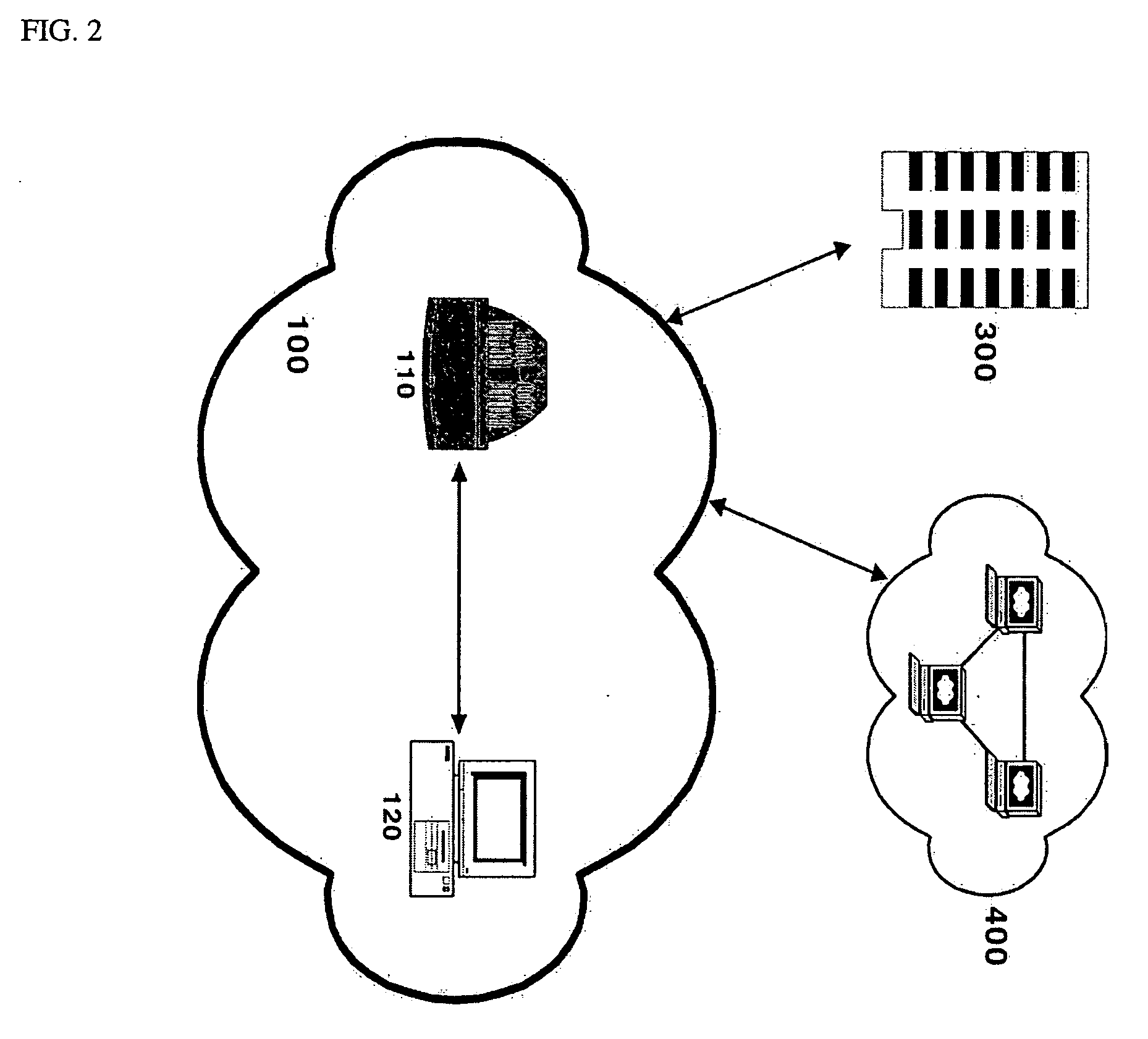
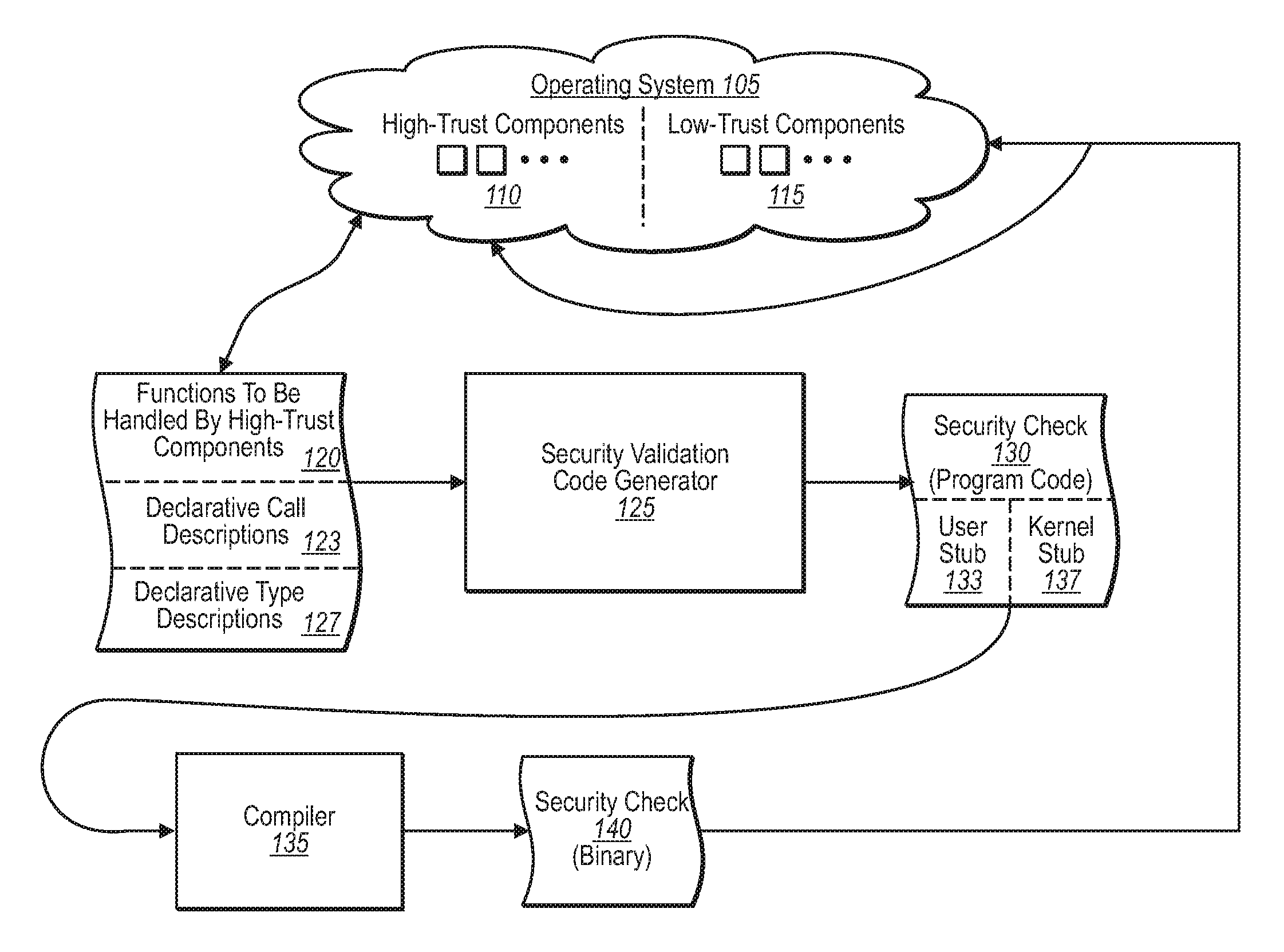
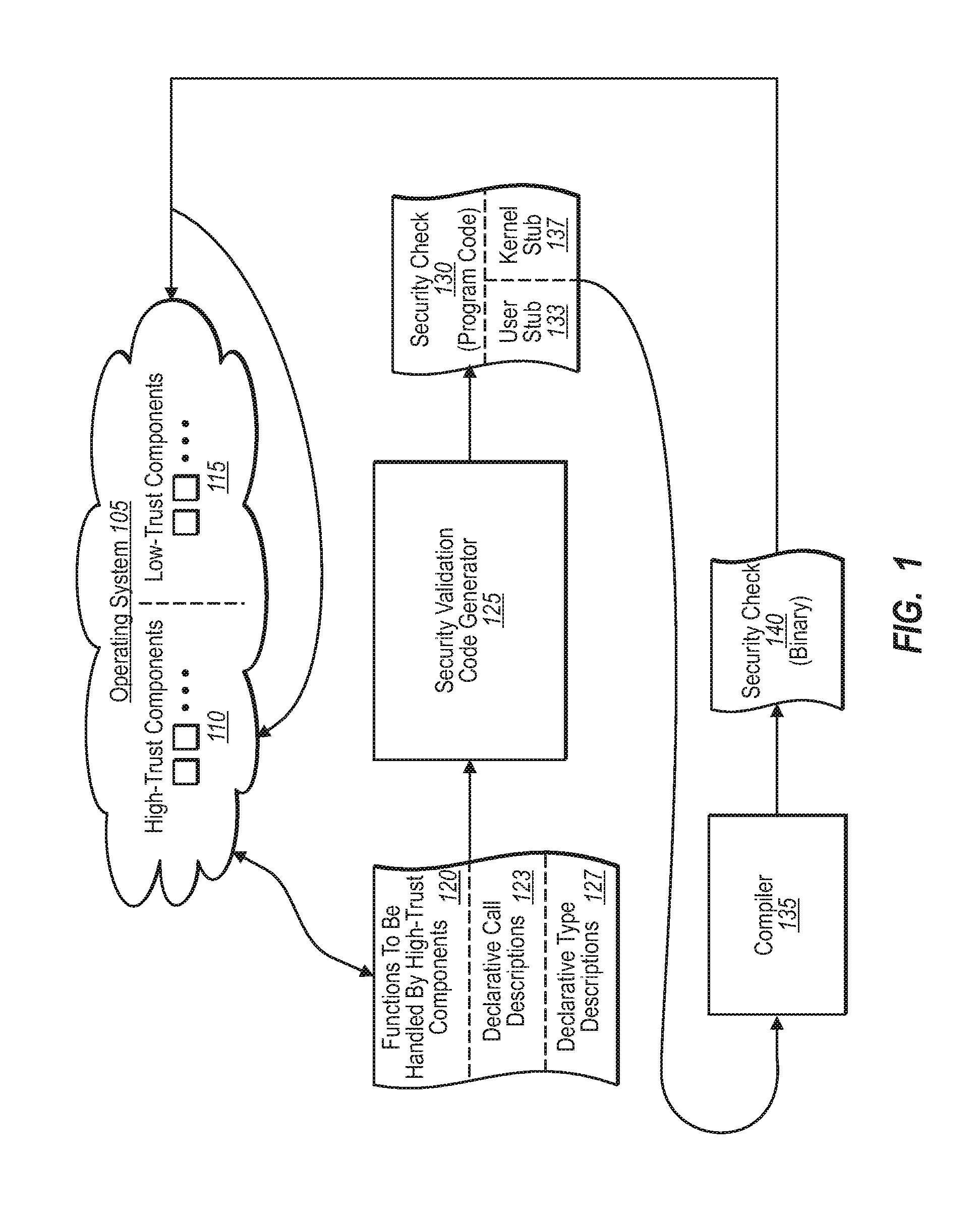
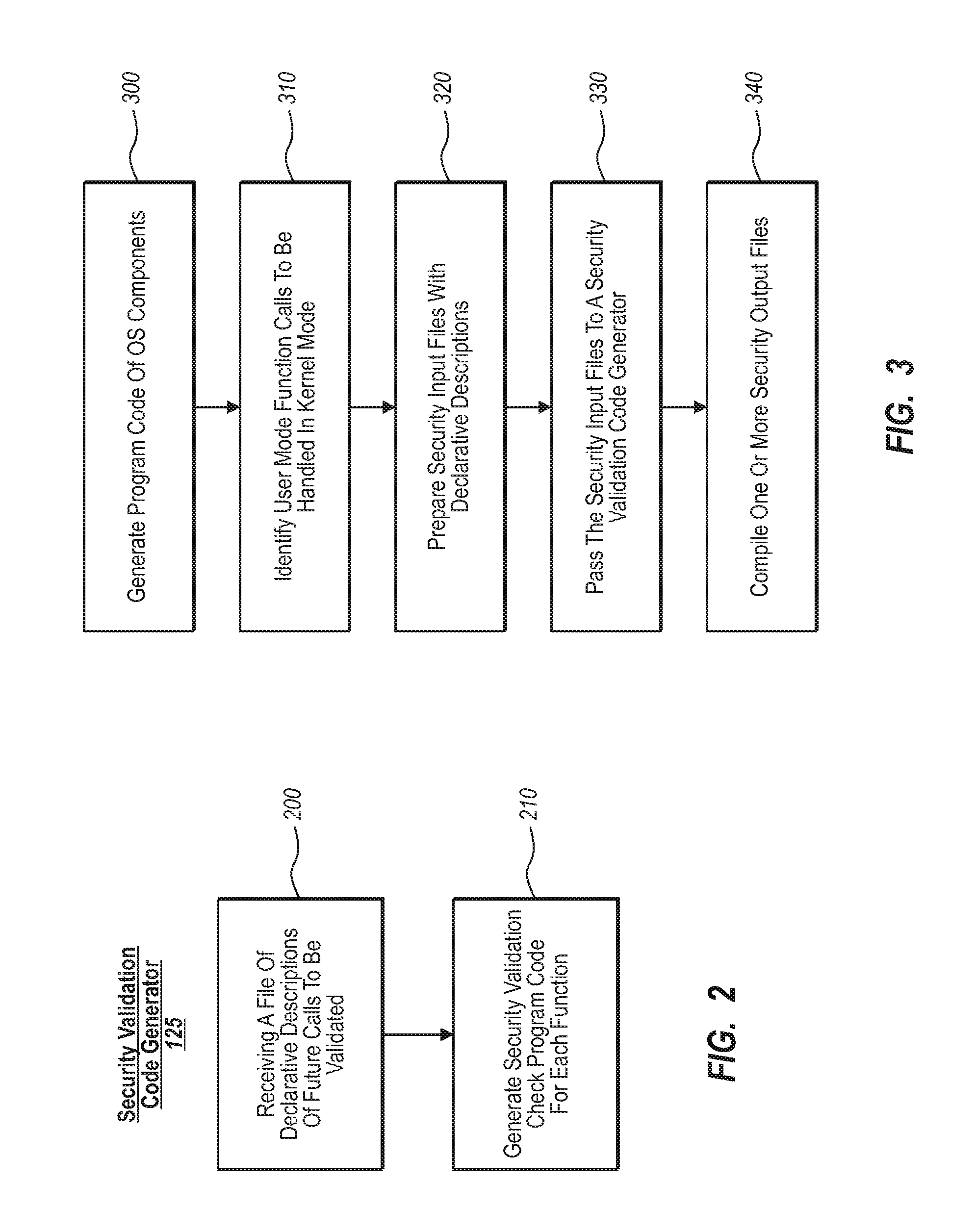
Generating security validation code automatically
InactiveUS20080127303A1Memory loss protectionSoftware engineeringProgramming languageOperational system
A security program code generator is configured to automatically generate program code used to perform one or more validation checks of components operating in user mode. In one implementation, for example, the program code generator receives one or more files that include declarative values and parameters regarding one or more function calls made by any user mode component. The program code generator then takes the file of declarative call descriptions and automatically generates a user mode stub and a kernel mode stub for each function call of interest to be handled by a kernel mode component. The file(s) that include the user mode stub and the kernel mode stub can then be compiled and linked into the operating system components.
Owner:MICROSOFT TECH LICENSING LLC
Method and device to improve the flying abilities of the airborne devices operator
InactiveUS20170148340A1Quality improvementLeast riskElectroencephalographyGeometric CADRadarThe Internet
A method and device used to improve flying education, and reduce pilot student hazard when passing from simulators to the real aircraft, by introducing an intermediary stage where a simulator and a model radio-controlled aircraft with similar features as original is used in a system with many participants, an instructor, flight monitors, command center, mission control, audience located remotely and taking part in the same action via internet telecommunication. The simulator is used to measure biometric parameters of the pilots, certify them, and also for gaming, having fail-safe procedures embedded. System contains a flight-monitoring network, using both goniometry and radar devices, placed on surface and airborne, using these devices as signal repeaters for extensions of communication. The system may be used in missions dangerous to human crews, and by the complexity of simulation it improves the flying, as well as to improve the piloting of RC aircrafts.
Owner:POPA SIMIL VICTOR +1
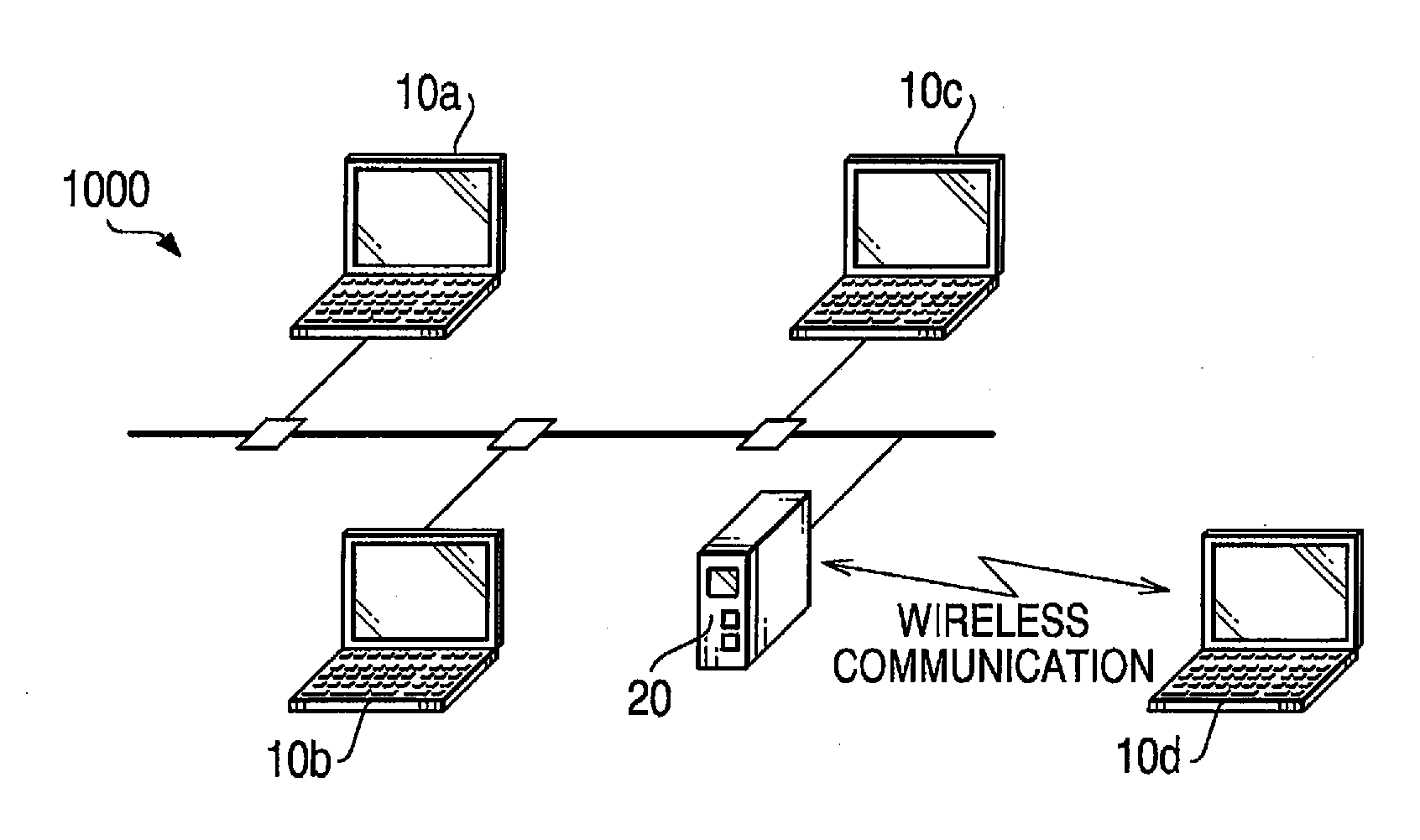
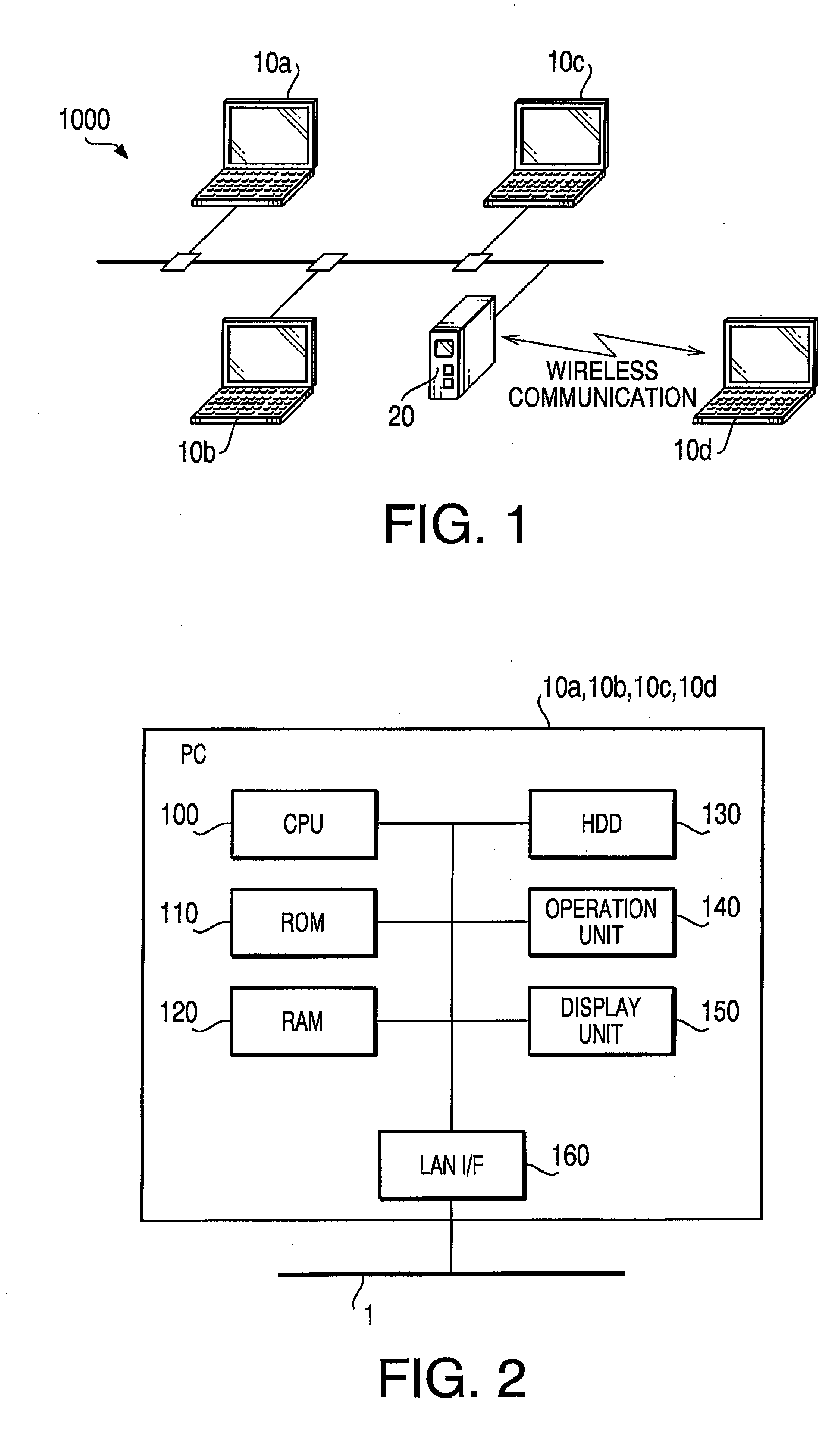
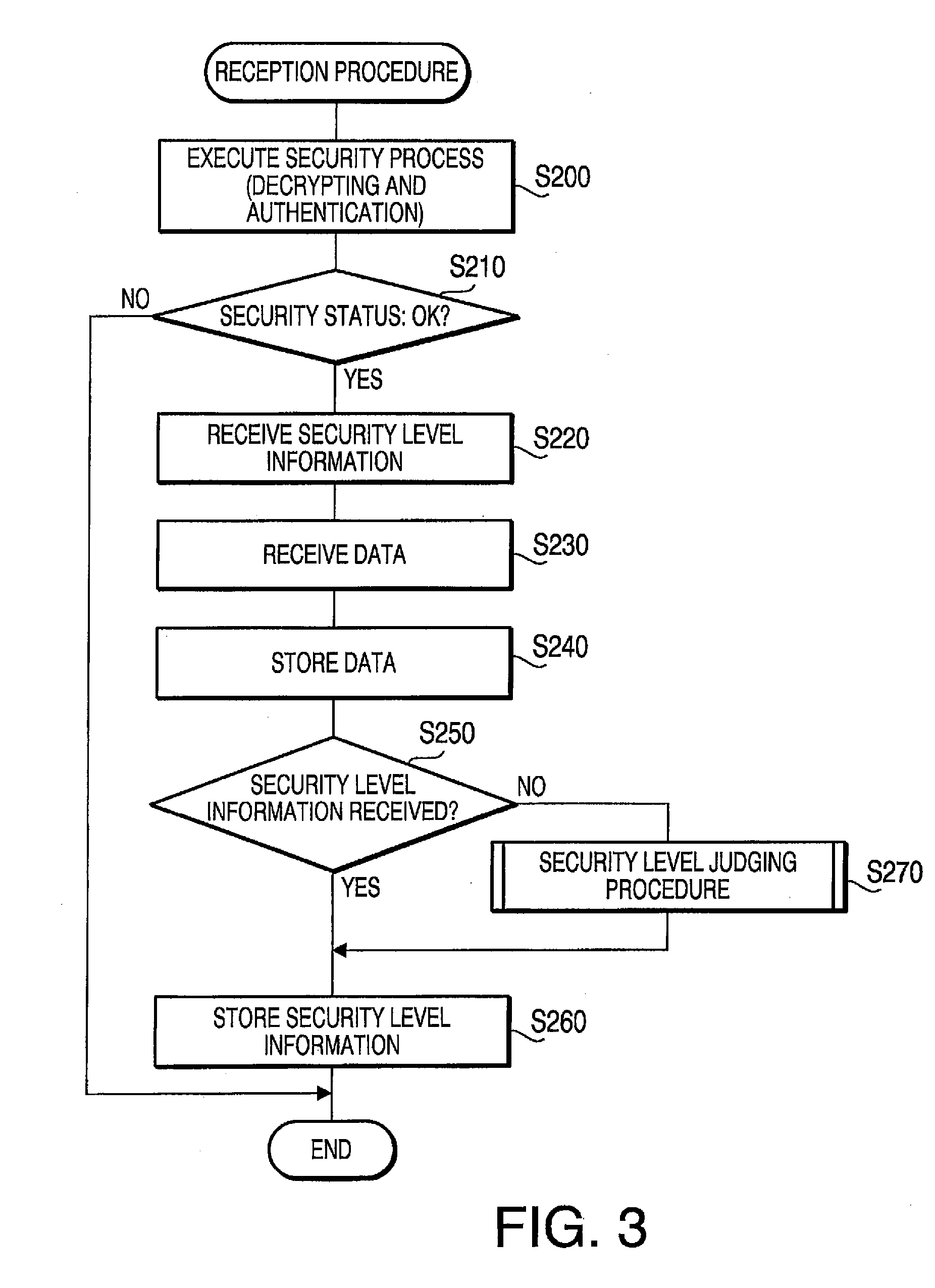
Communication Device, Communication System and Program
A communication device is configured to transmit data to which a predetermined security level is set to another communication device. The communication device is provided with a security level determining unit configured to determine a necessary security level to transmit the data in accordance with the security level set to the data, a security setting unit configured to re-set the security level that is determined by the security level determining unit to the data, a security procedure executing unit configured to apply a security procedure to the data so that a requirement of the security level set by the security setting unit is satisfied, and a data transmitting unit configured to transmit the data to which the security procedure has been applied.
Owner:BROTHER KOGYO KK
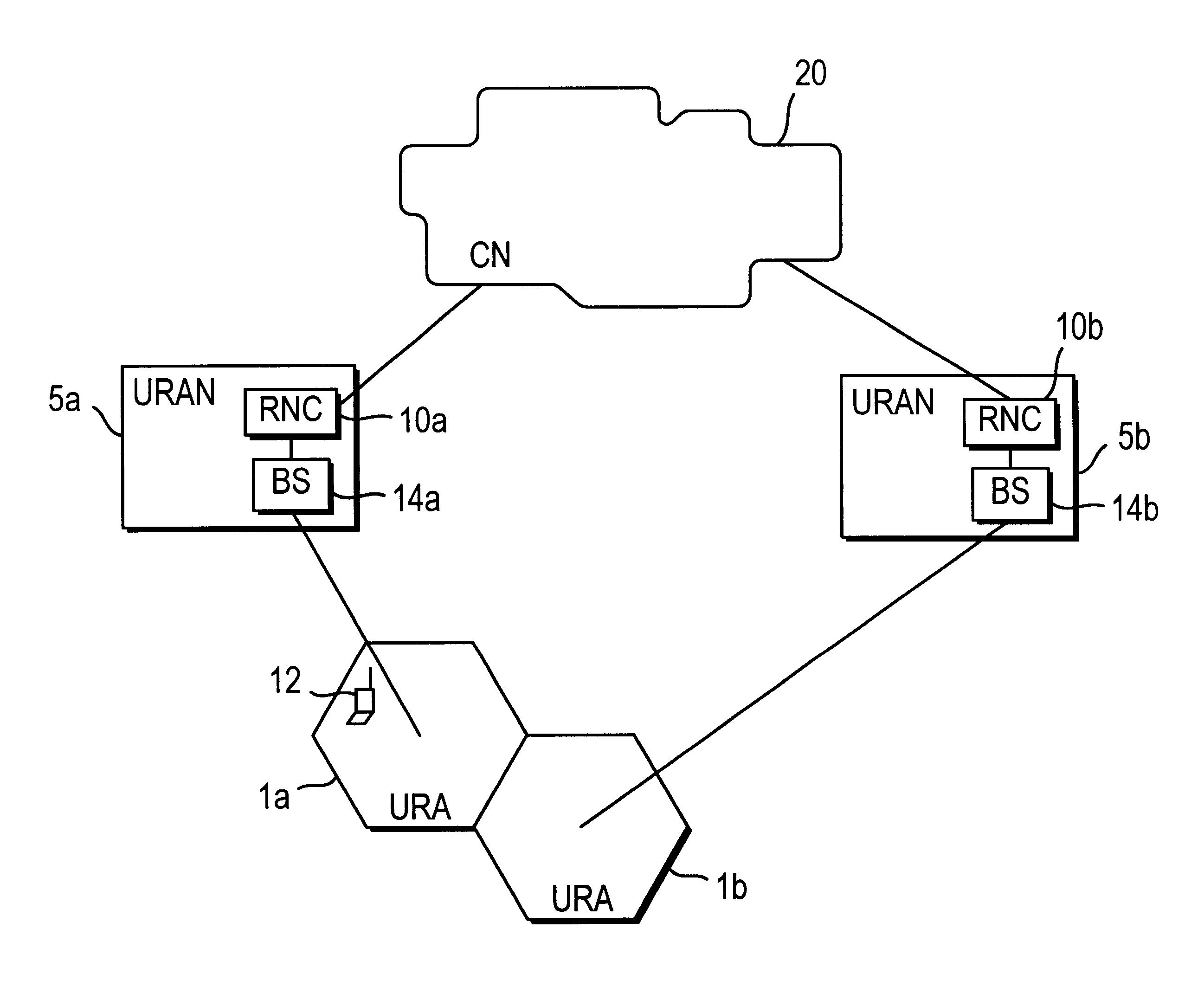
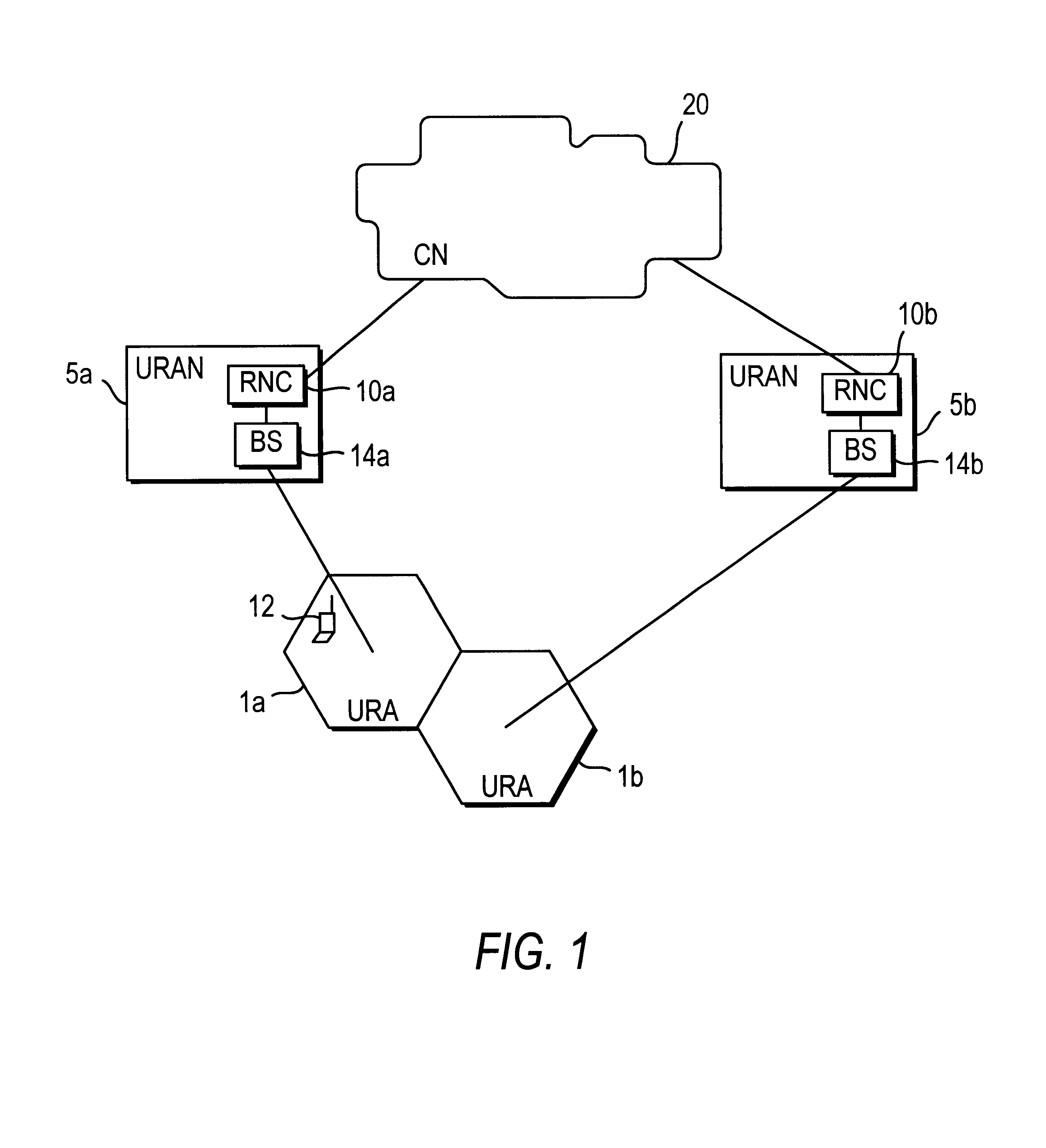
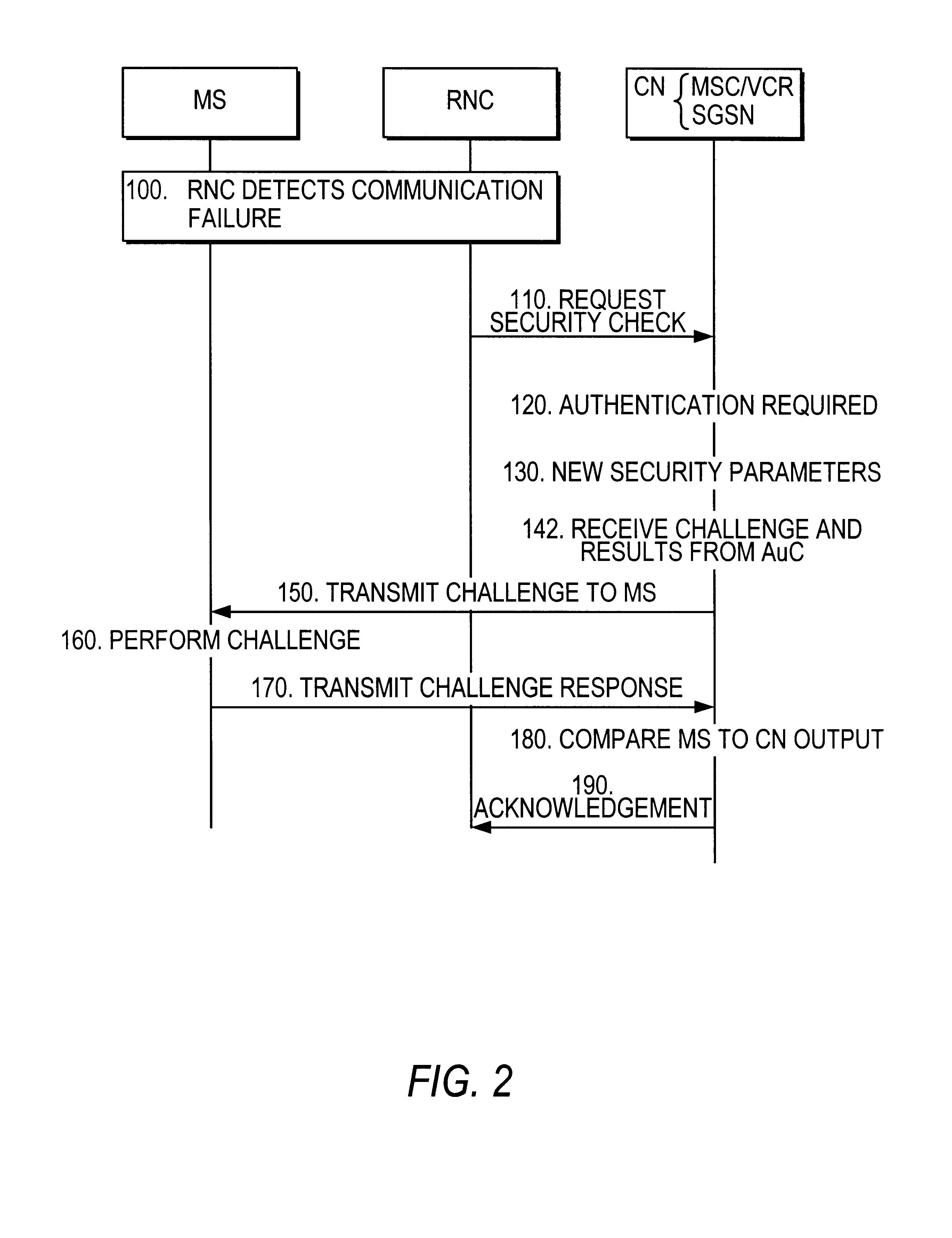
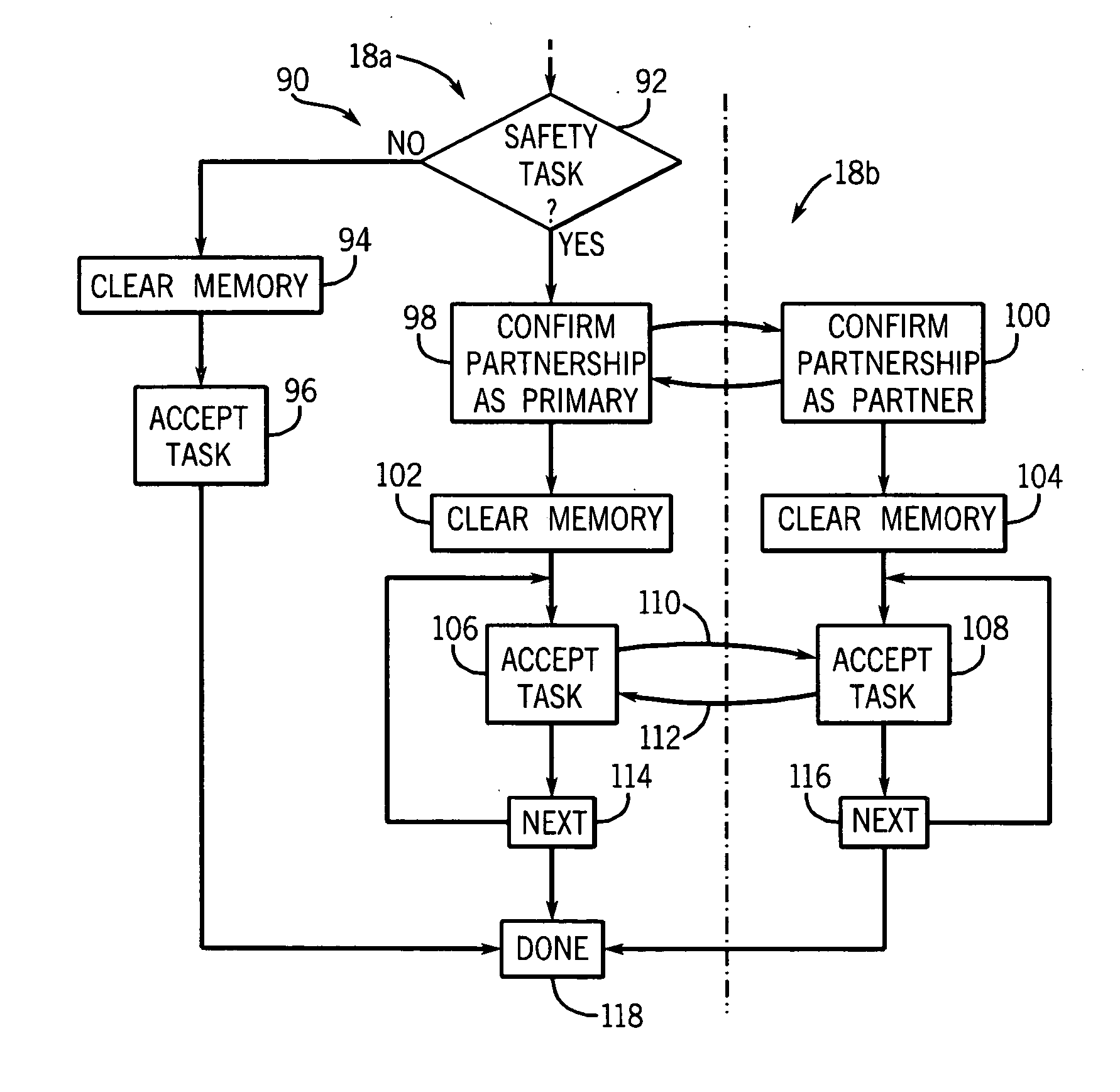
Security procedure in universal mobile telephone service
InactiveUS6763112B1Synchronisation arrangementUser identity/authority verificationRadio coverageMobile Telephone Service
A security procedure for a Universal Mobile Telephone Service (UMTS) mobile communication system includes detecting a communication failure between a Radio Network Controller (RNC) which controls radio coverage within a prescribed geographical area and a Mobile Station (MS) in the geographic area, authenticating the MS and setting a new security parameter in response to the communication failure. The security parameter to be changed may be a ciphering key CK or an integrity key IK. Moreover, the steps of authenticating and setting a new security parameter may be performed separately or simultaneously.
Owner:CORE WIRELESS LICENSING R L
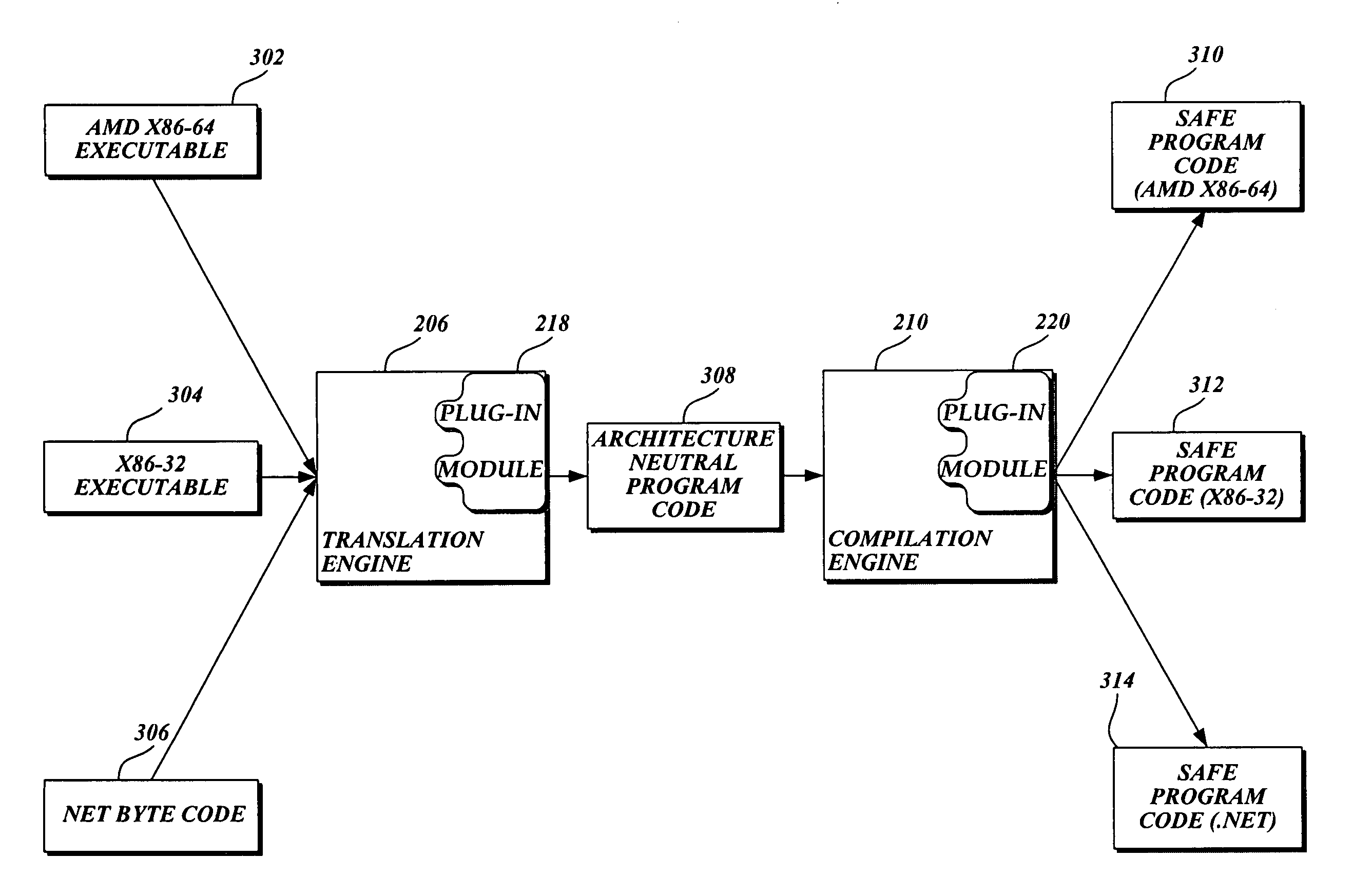
Proactive computer malware protection through dynamic translation
ActiveUS7636856B2Safely executedMemory loss protectionUser identity/authority verificationMalwareComputer memory
The present invention includes a system and method for translating potential malware devices into safe program code. The potential malware is translated from any one of a number of different types of source languages, including, but not limited to, native CPU program code, platform independent .NET byte code, scripting program code, and the like. Then the translated program code is compiled into program code that may be understood and executed by the native CPU. Before and / or during execution, the present invention causes a scanner to search for potential malware stored in memory. If malware is not detected, the computing device causes the CPU to execute the translated program code. However, execution and / or analysis of potential malware may be interrupted if computer memory that stores potential malware is altered during execution. In this instance, the potential malware now stored in memory is translated into safe program code before being executed.
Owner:MICROSOFT TECH LICENSING LLC
Safety controller providing for execution of standard and safety control programs
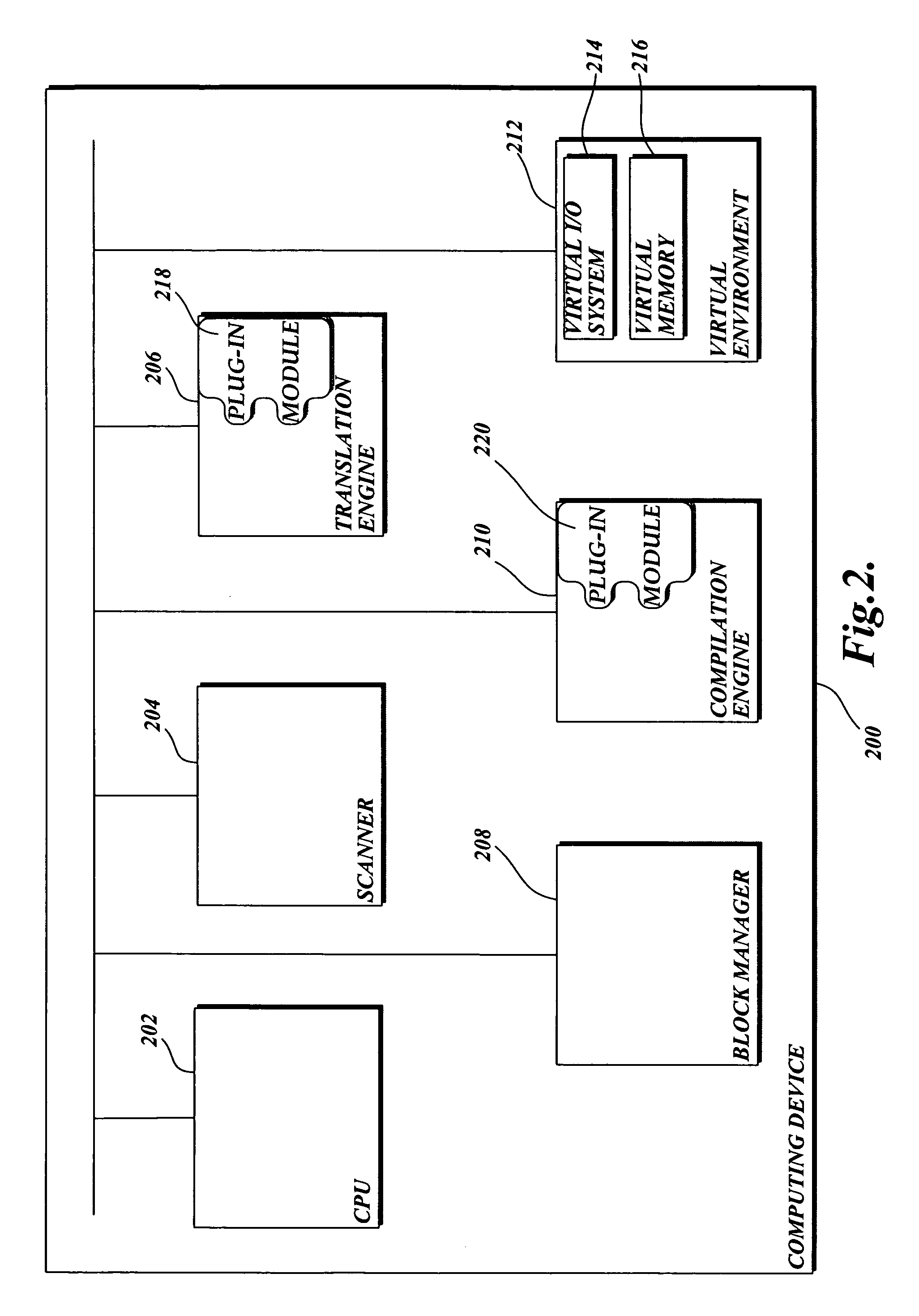
ActiveUS20050060606A1Reduced risk of corruptionEasy to detectProgramme controlSafety arrangmentsSafety controlComputer science
A safety controller may execute both standard and safety programs using shared architecture in which two processors symmetrically execute the safety program and check each other for errors, and one processor only executes the standard program to minimize undetected symmetrical corruption of the safety programs.
Owner:ROCKWELL AUTOMATION TECH
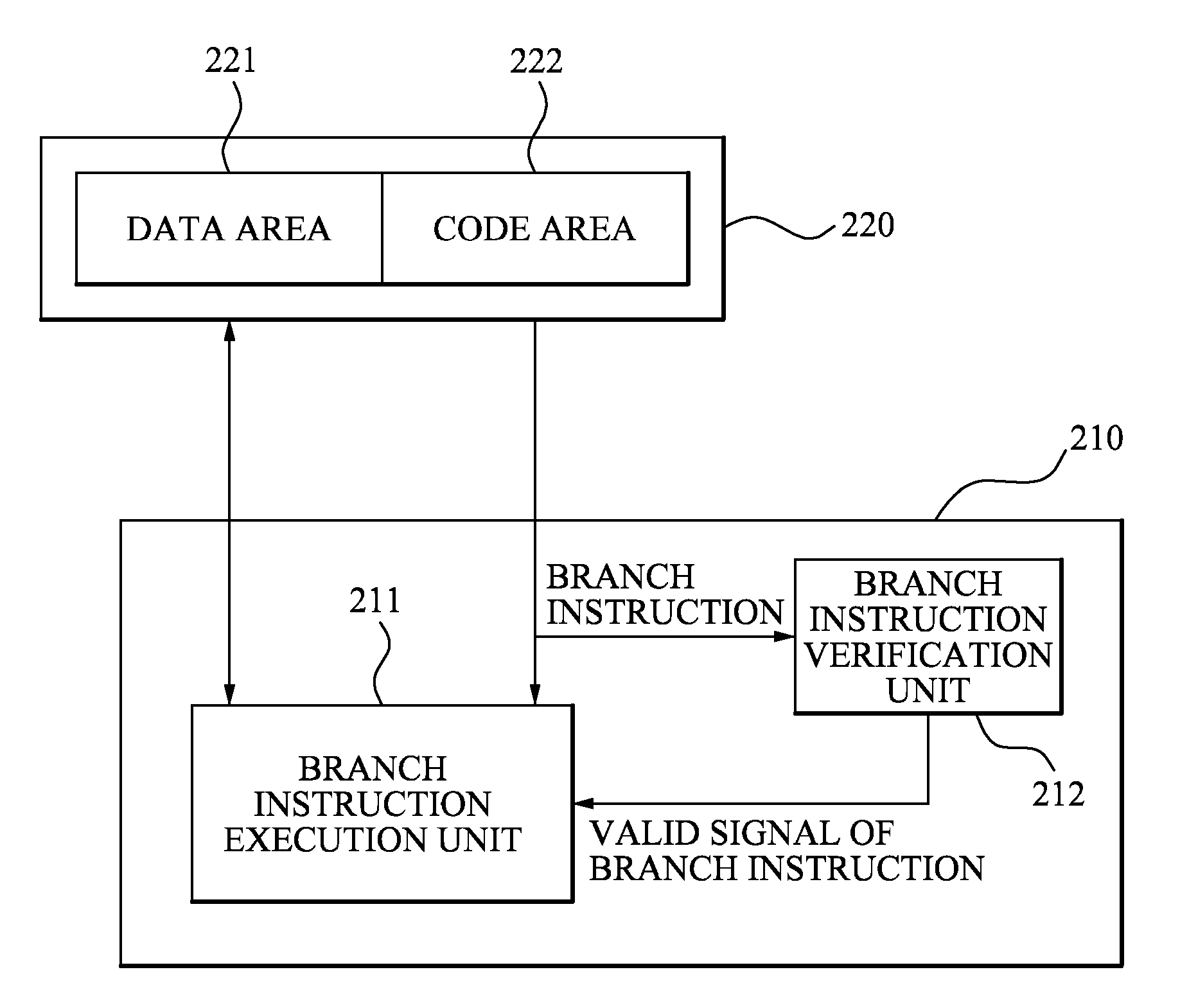
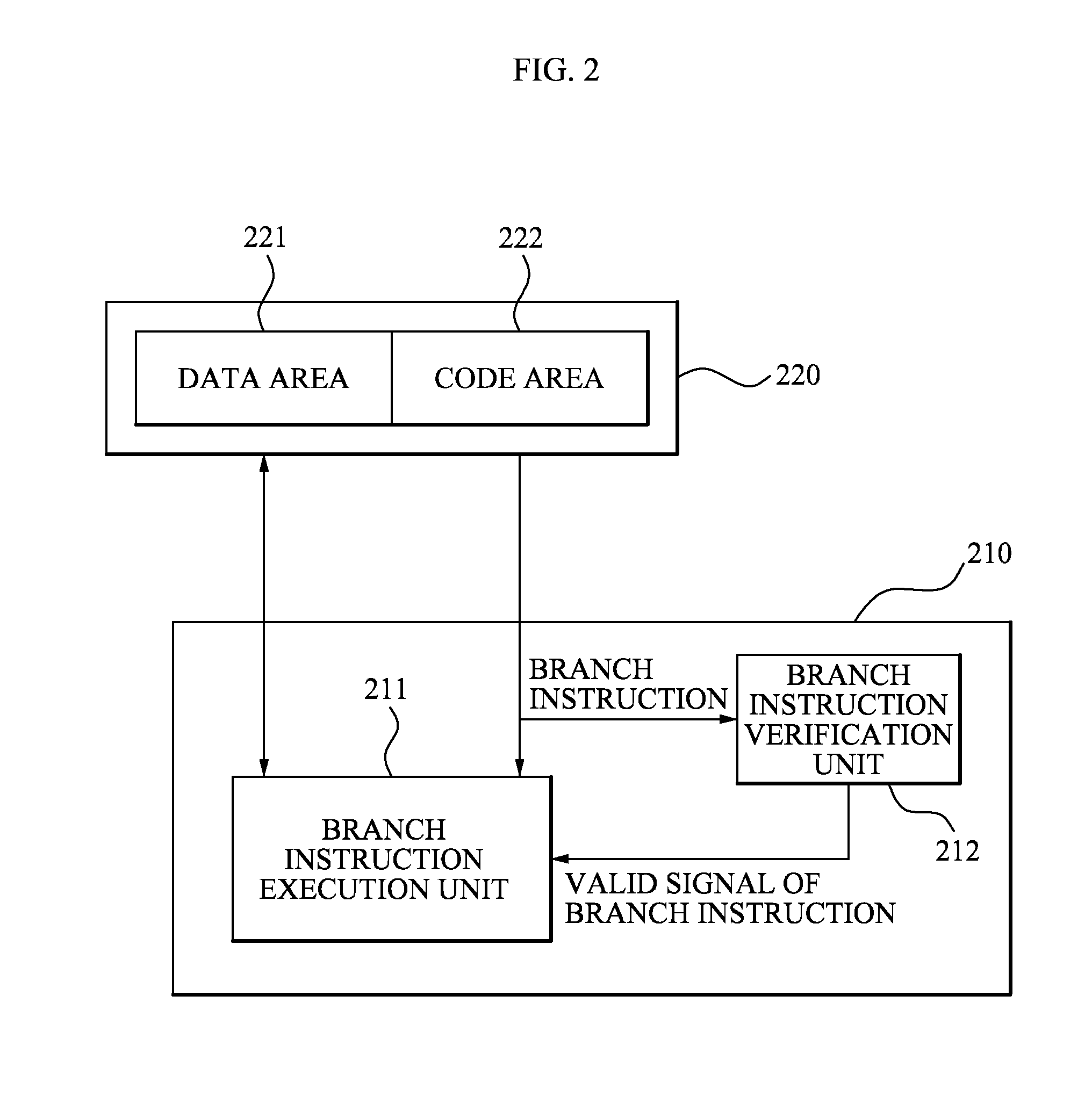
Central processing unit having branch instruction verification unit for secure program execution
ActiveUS20080256346A1Preventing a malicious behaviorDigital computer detailsInternal/peripheral component protectionParallel computingExecution unit
Provided are a central processing unit (CPU) and method for executing a branch instruction of a CPU, which can protect user's data by preventing an error due to a computer virus and a hacker is provided. The CPU includes: a branch instruction verification unit which verifies whether a branch instruction is valid; and a branch instruction execution unit which executes the branch instruction when the branch instruction is valid. The method includes: verifying whether the branch instruction is valid; and not executing the branch instruction when the branch instruction is invalid.
Owner:SAMSUNG ELECTRONICS CO LTD
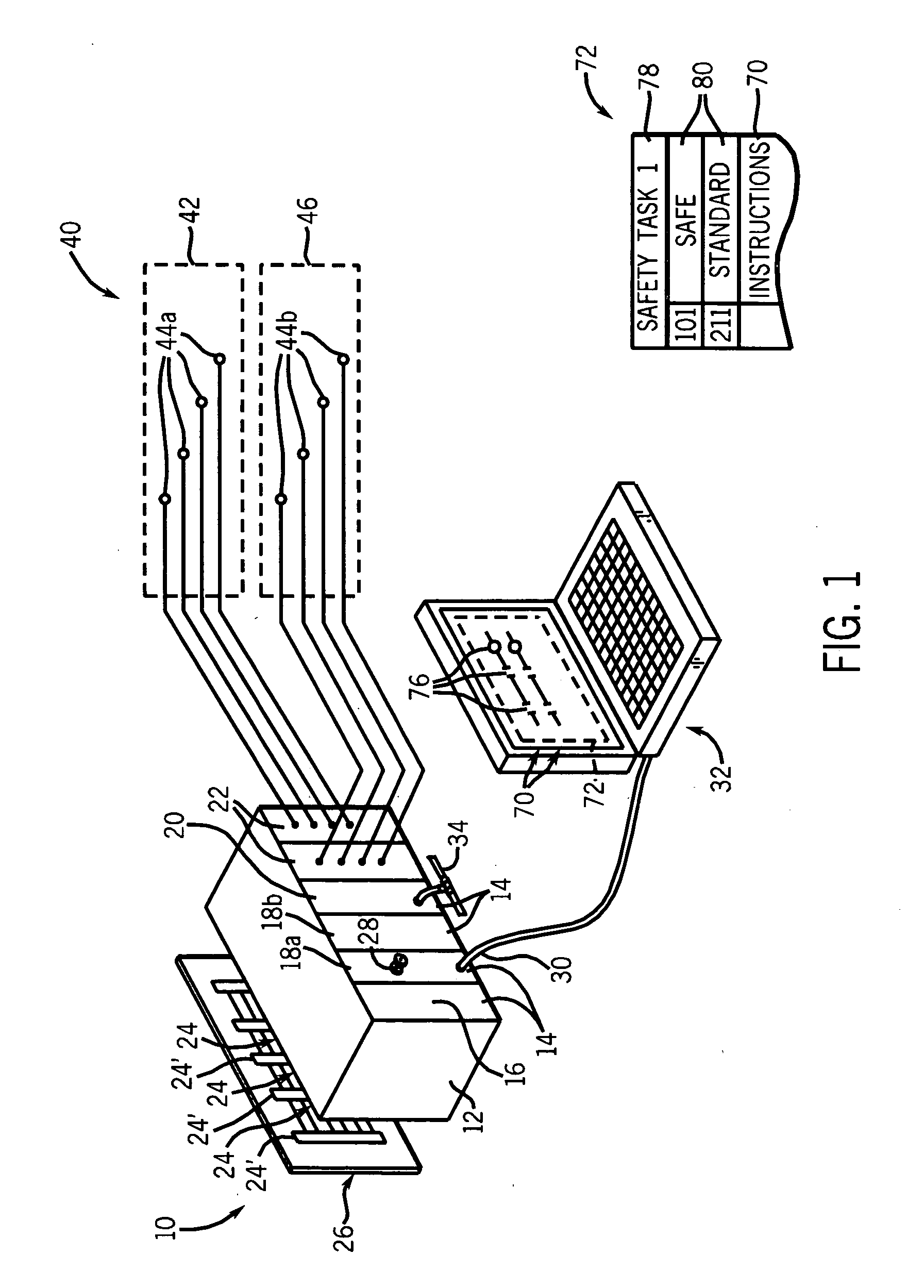
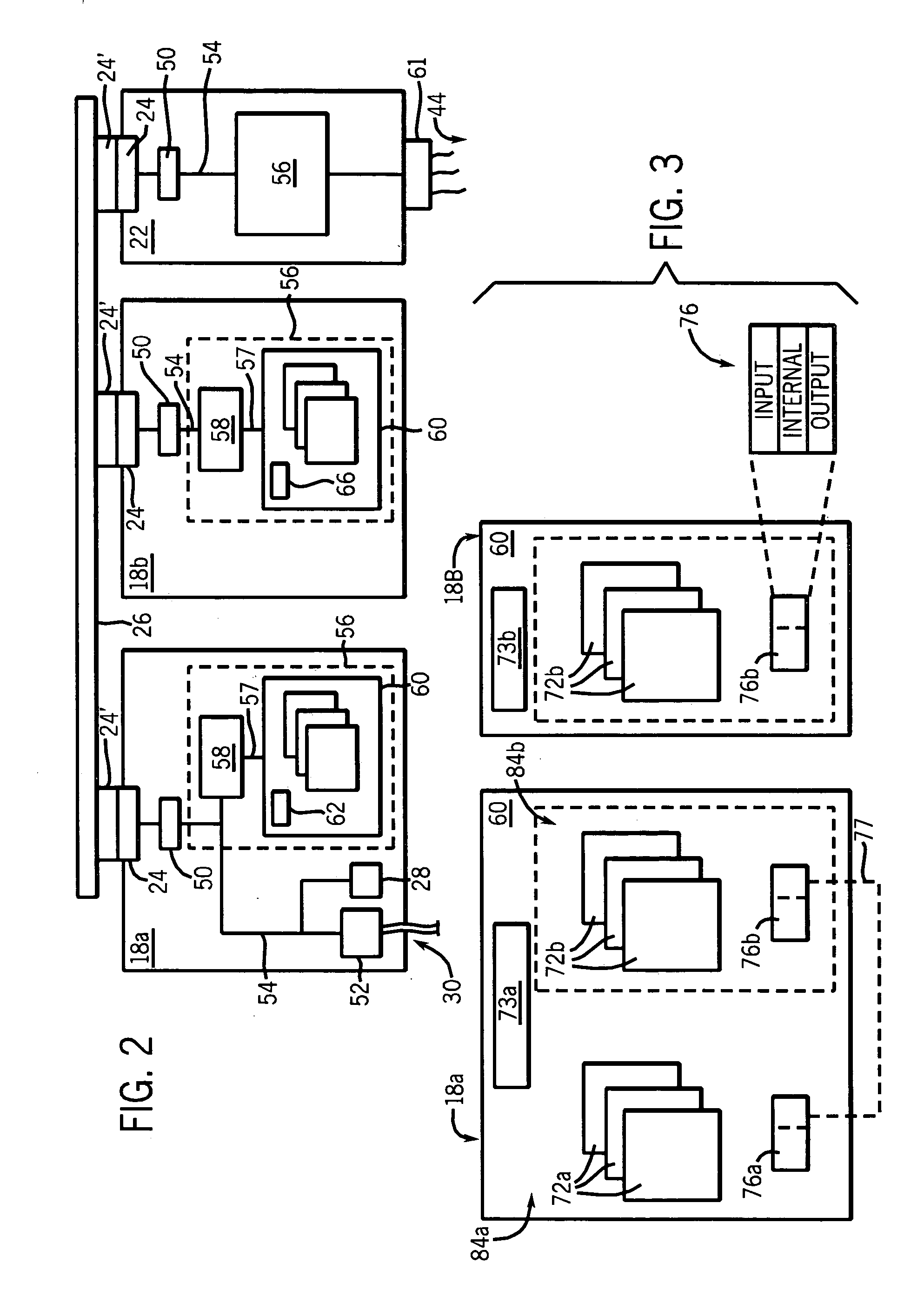
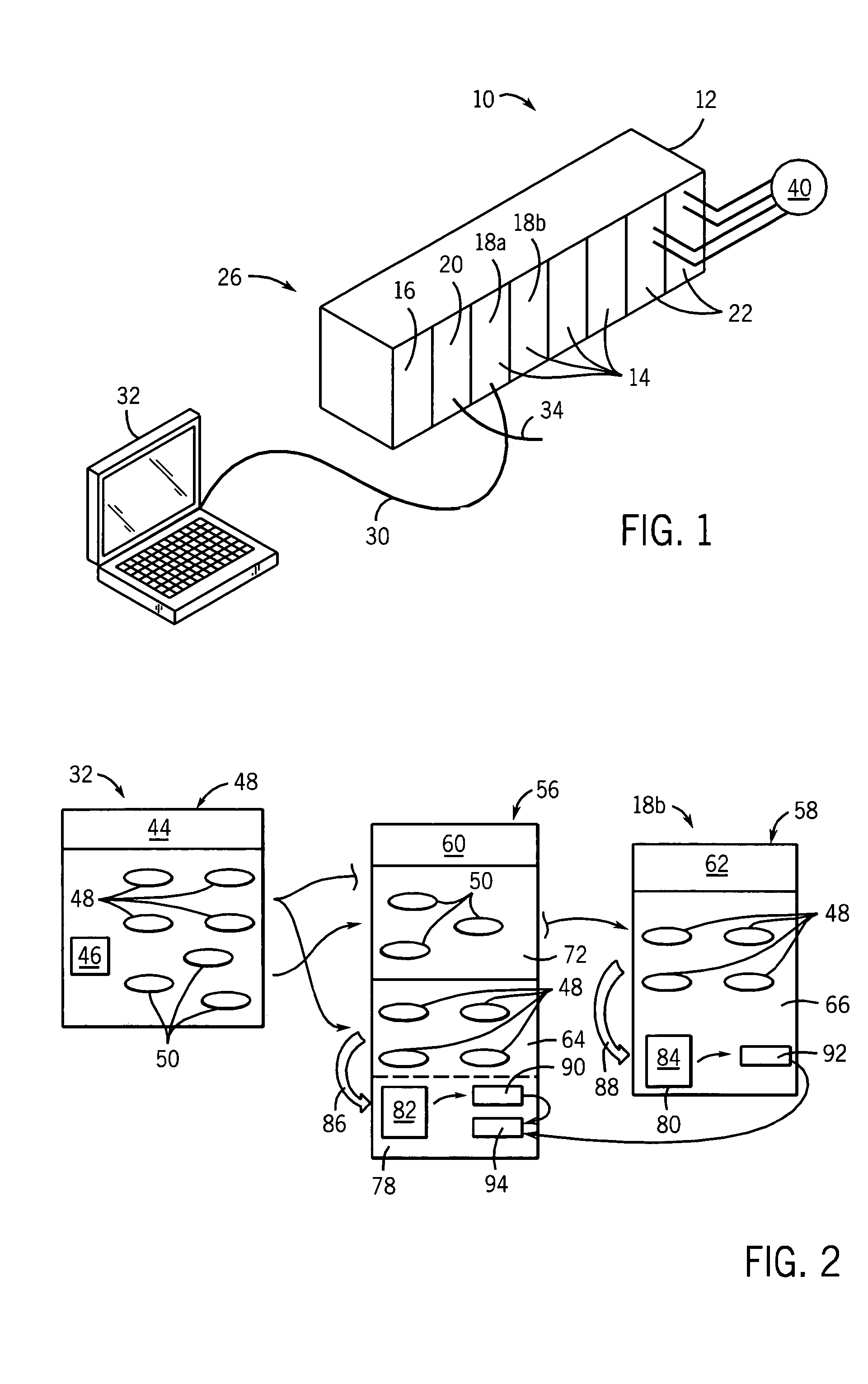
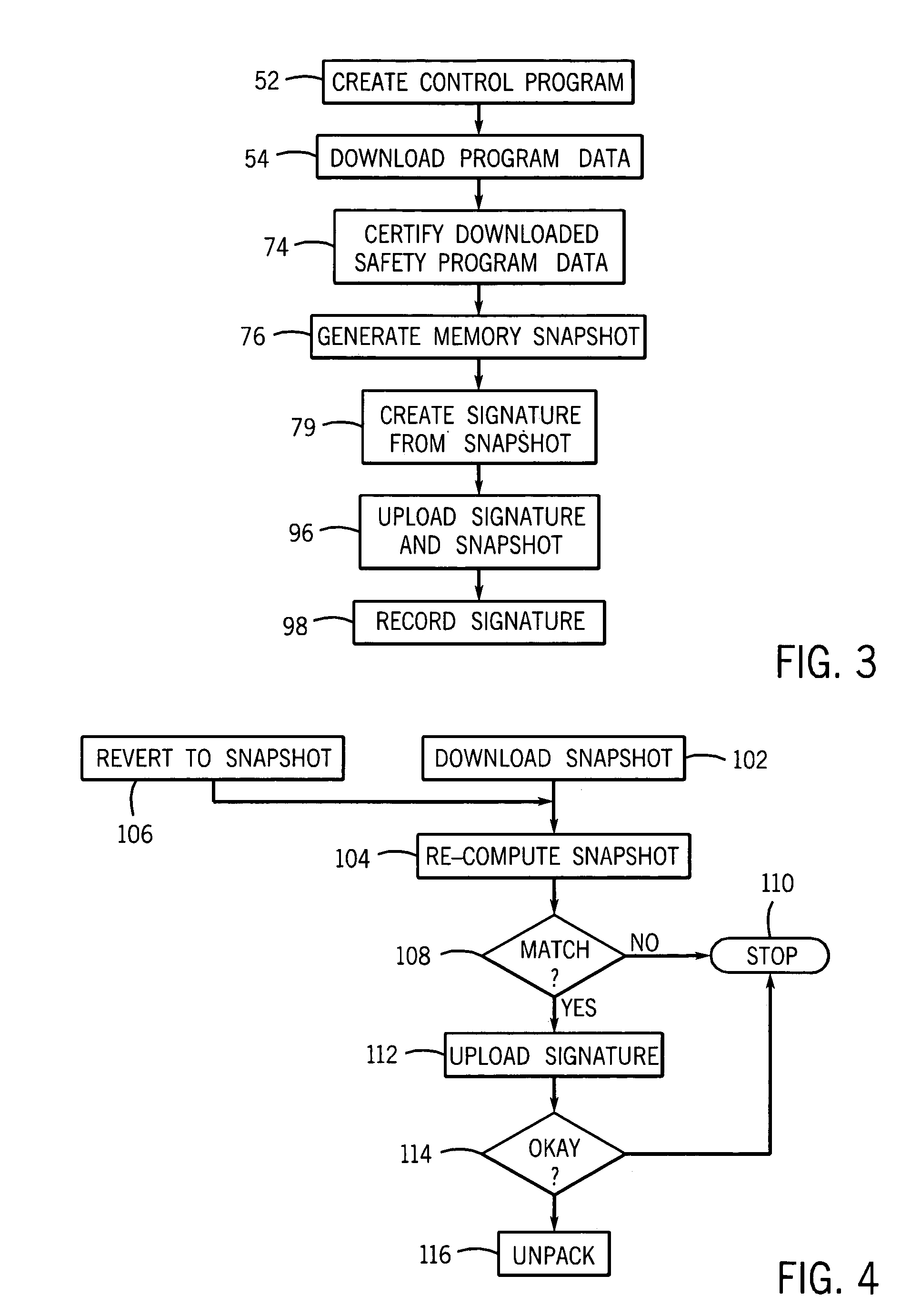
Safety controller providing rapid recovery of safety program data
ActiveUS7027880B2Avoid the needEasy to buildSafety arrangmentsComputer controlDigital signatureOperating system
Re-certification of a control program loaded in a safety controller is avoided through the use of a digital snapshot and digital signature, the snapshot providing a rapidly loadable memory image file and the signature providing a confirmation that the file loaded matches a previously certified copy so as to avoid the need for time consuming re-certification.
Owner:ROCKWELL AUTOMATION TECH
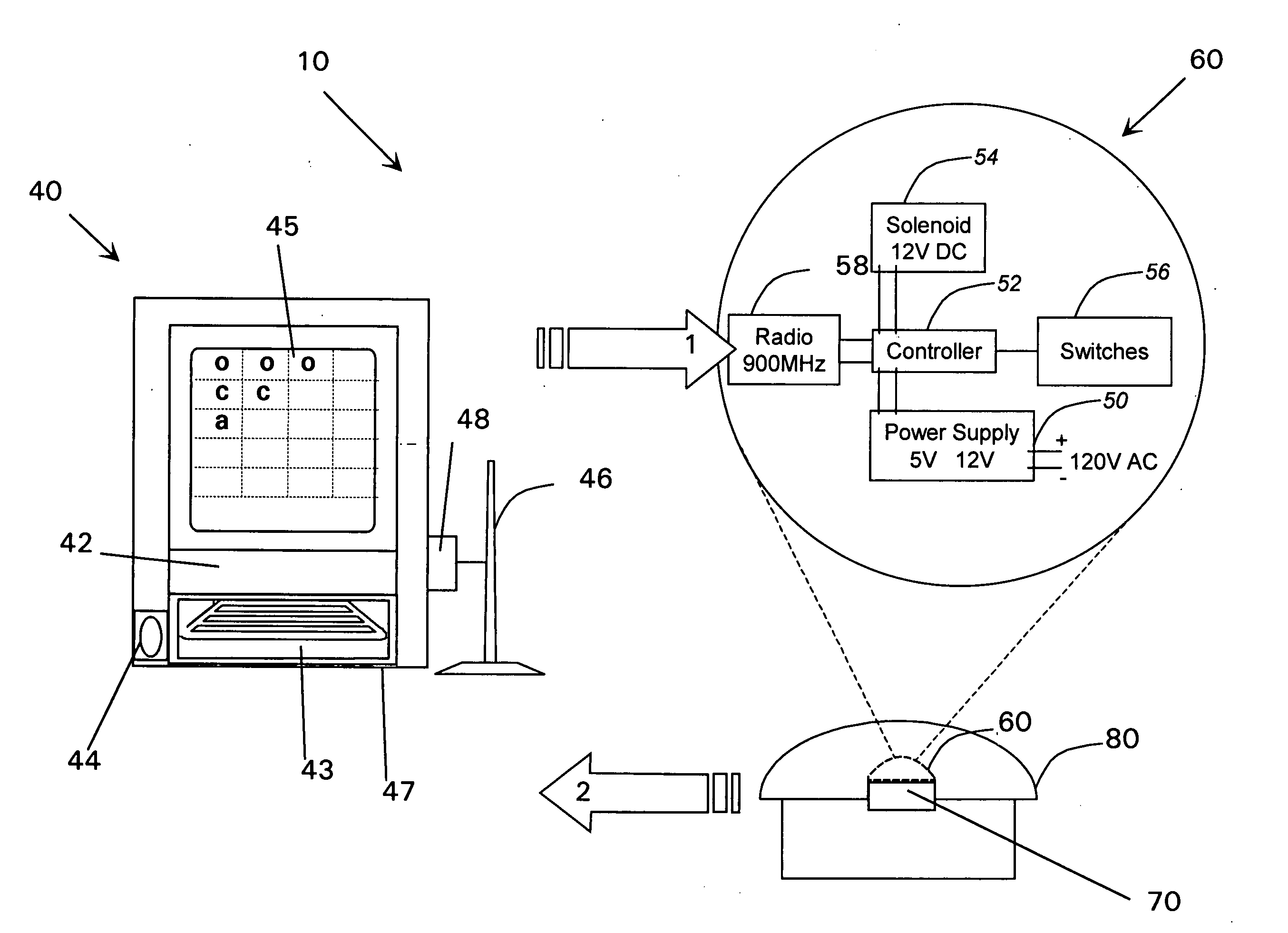
Gaming security system and associated methods for selectively granting access
ActiveUS20070046423A1Reduce the amount requiredNo reduction in securityElectric signal transmission systemsDigital data processing detailsInternet privacyManagement system
In various embodiments, the present invention provides a keyless management system for automating selective access to a lockable device and a method for selectively granting access. The system and method include the lockable device coupled to and secured by a security assembly; a processor remotely located from the device executing one or more algorithms operable for identifying a user, authorizing a predetermined level of command control based upon the identity of the user, receiving a command from the user to provide access to the device to at least one of the users and a third party, and translating the command into a form that may be received by the security assembly; a communications channel operable for communicating the translated command to the security assembly; and a controller proximately located to the device executing one or more algorithms operable for actuating the security assembly in response to the translated command, thereby providing access to the device to at least one of the users and a third party.
Owner:MARCON INT
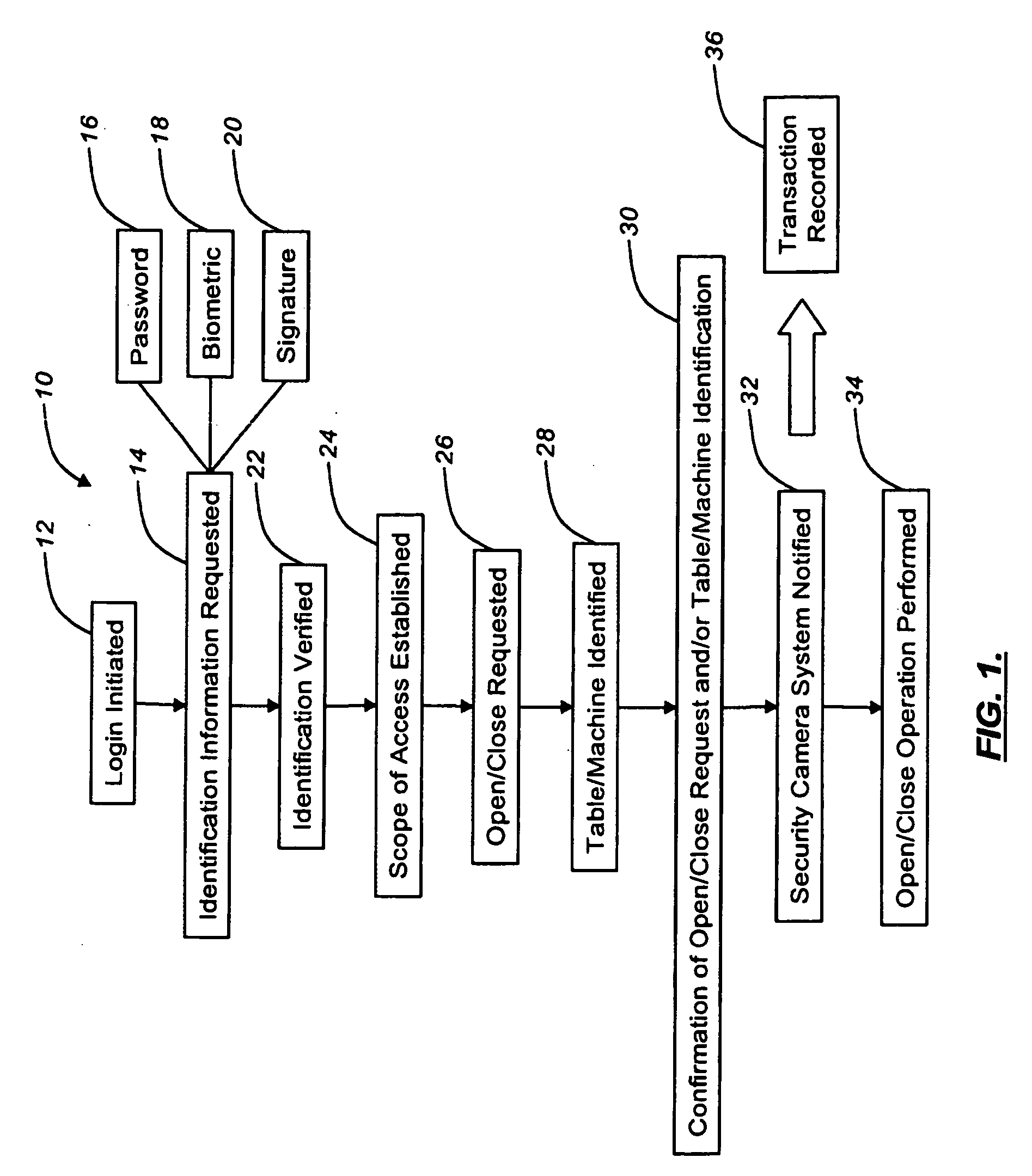
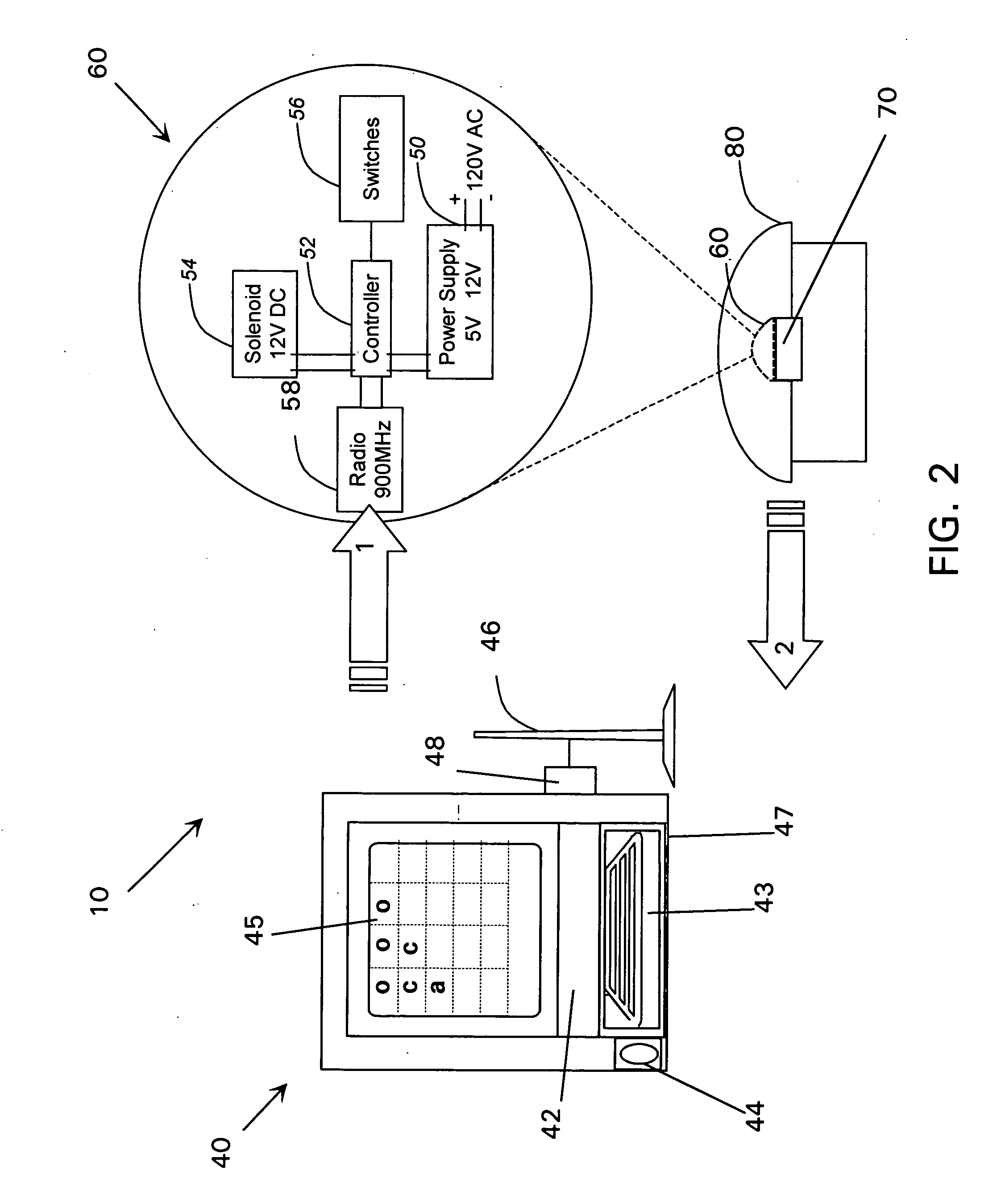
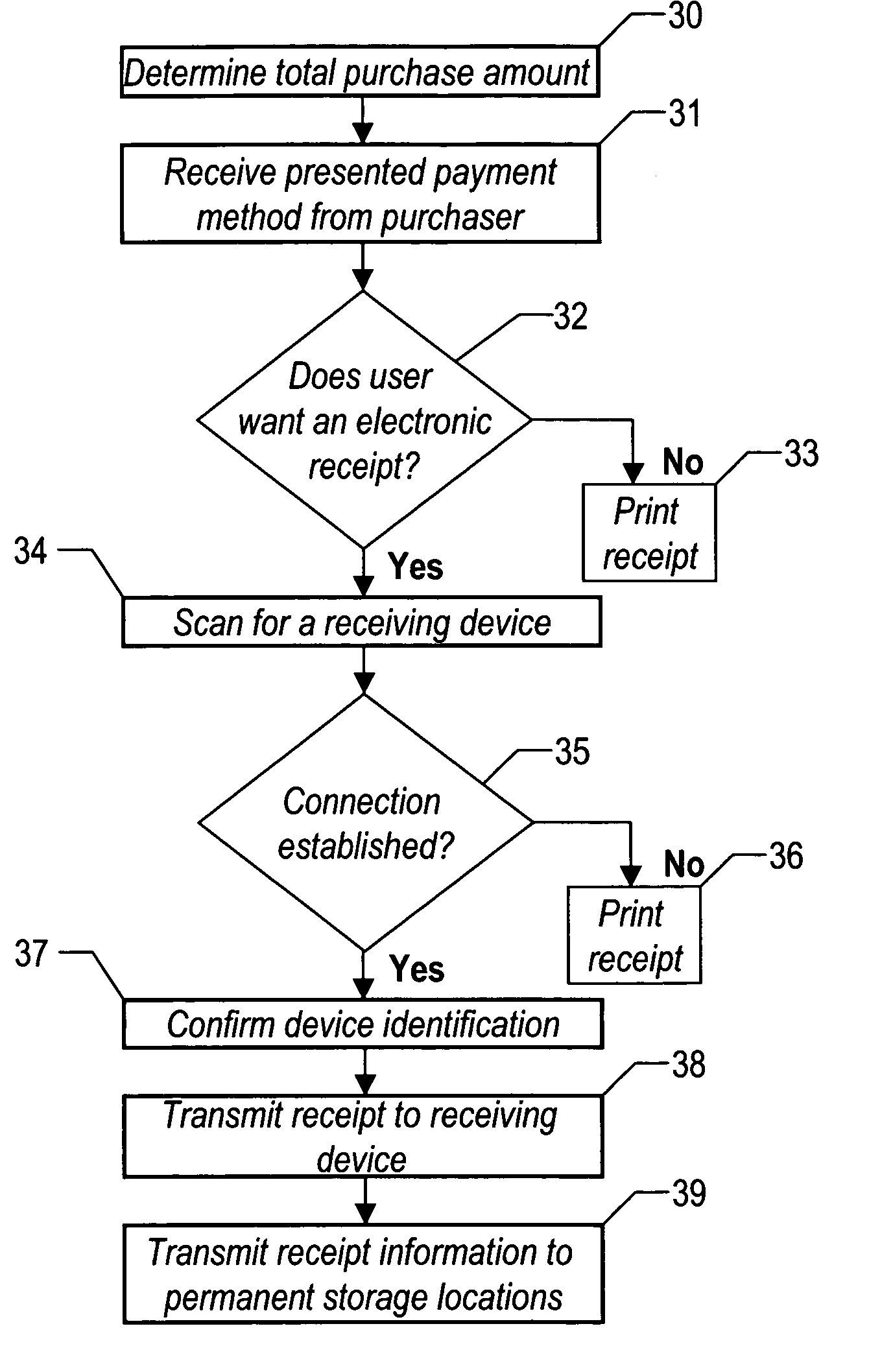
Method and system for dissemination of paperless transaction receipts in non-networked environments
Electronic transaction receipts in remote non-networked sales equipment are sent through infrared or radio frequency means to portable electronic devices such as personal digital assistants (PDA's) / smart cellular telephones that are in the possession of the consumer. These portable devices are possessed by the consumer and are in very close proximity to the POS device transmitting the information. Security procedures also verify the receiving device to avoid inadvertent transmissions and to provide addition security for the transmission. The information and records received by these portable devices may be stored and uploaded into other electronic media at the discretion of the consumer.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Rotating electric hand tool implement with safety routine
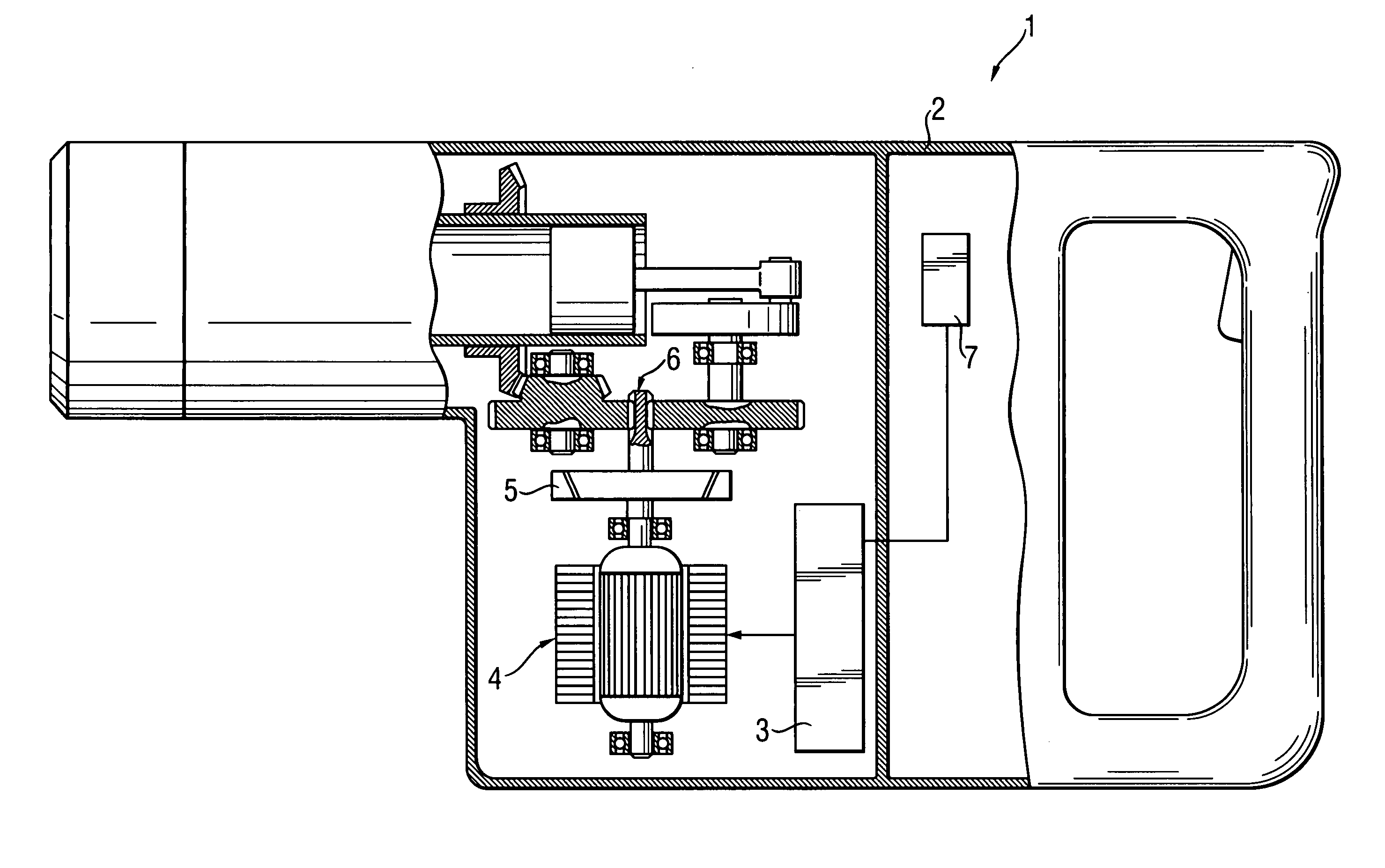
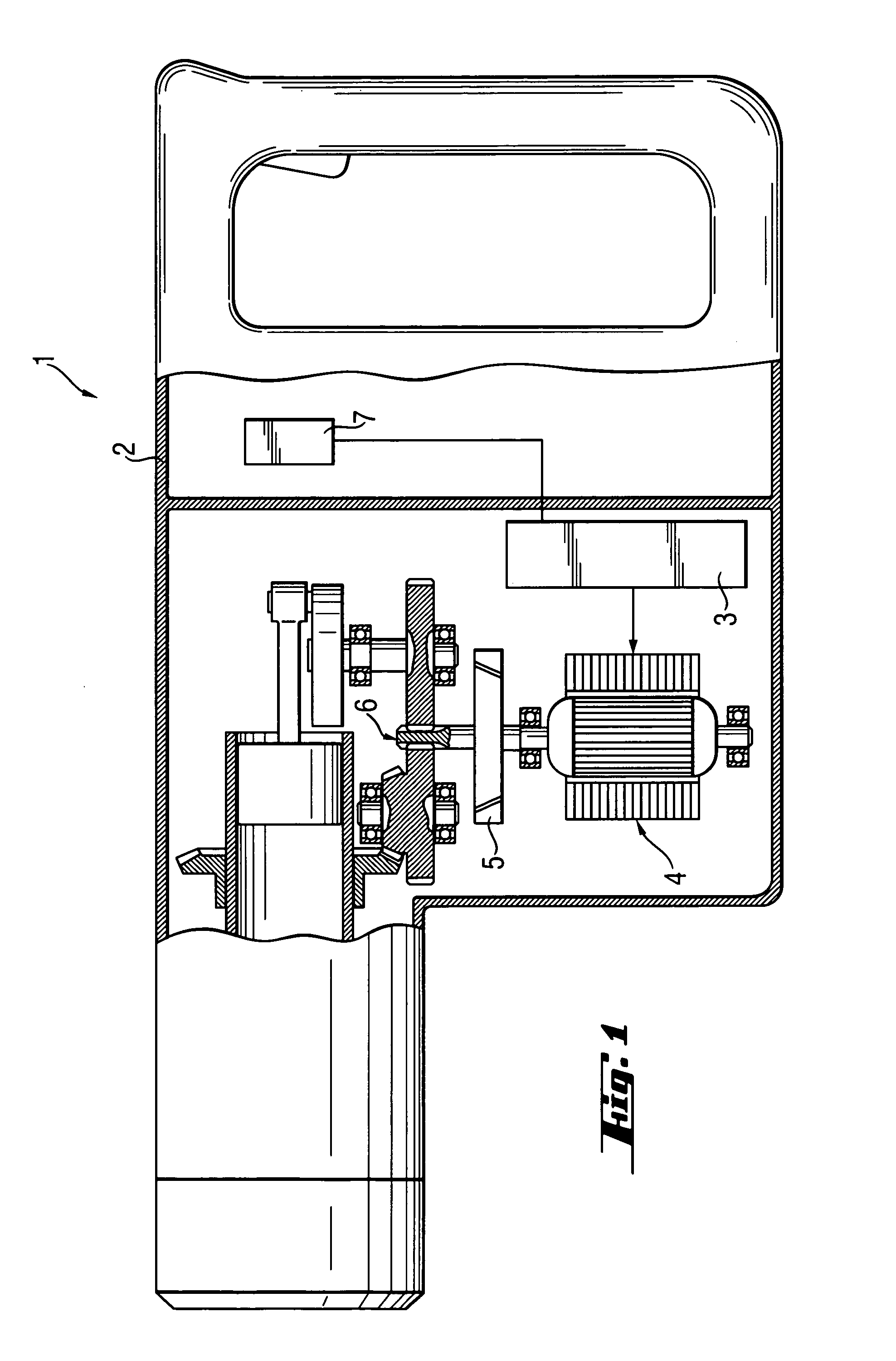
InactiveUS7011165B2Easy to separatePreventing excessively high twistingDerricks/mastsPortable percussive toolsMotor controlEngineering
An electric hand tool apparatus (1) for driving a drill-like tool, which carries out an at least partial rotational movement, has within a housing (2), an electric motor (4) without or free of collector and slip ring, the rpm of which can be controlled by motor control electronics (3), wherein an rpm-dependent clutch (5) for transferring the torque is disposed in a force transfer path from the electric motor (4) to a transmission (6). Optionally, to prevent an excessively high twisting of the housing (2), a sensor (7) is evaluated and the rpm of the electric motor (4) is reduced in order to sever the transfer of force by the rpm-dependent clutch (5).
Owner:HILTI AG
Security system, security method, and non-transitory computer readable medium
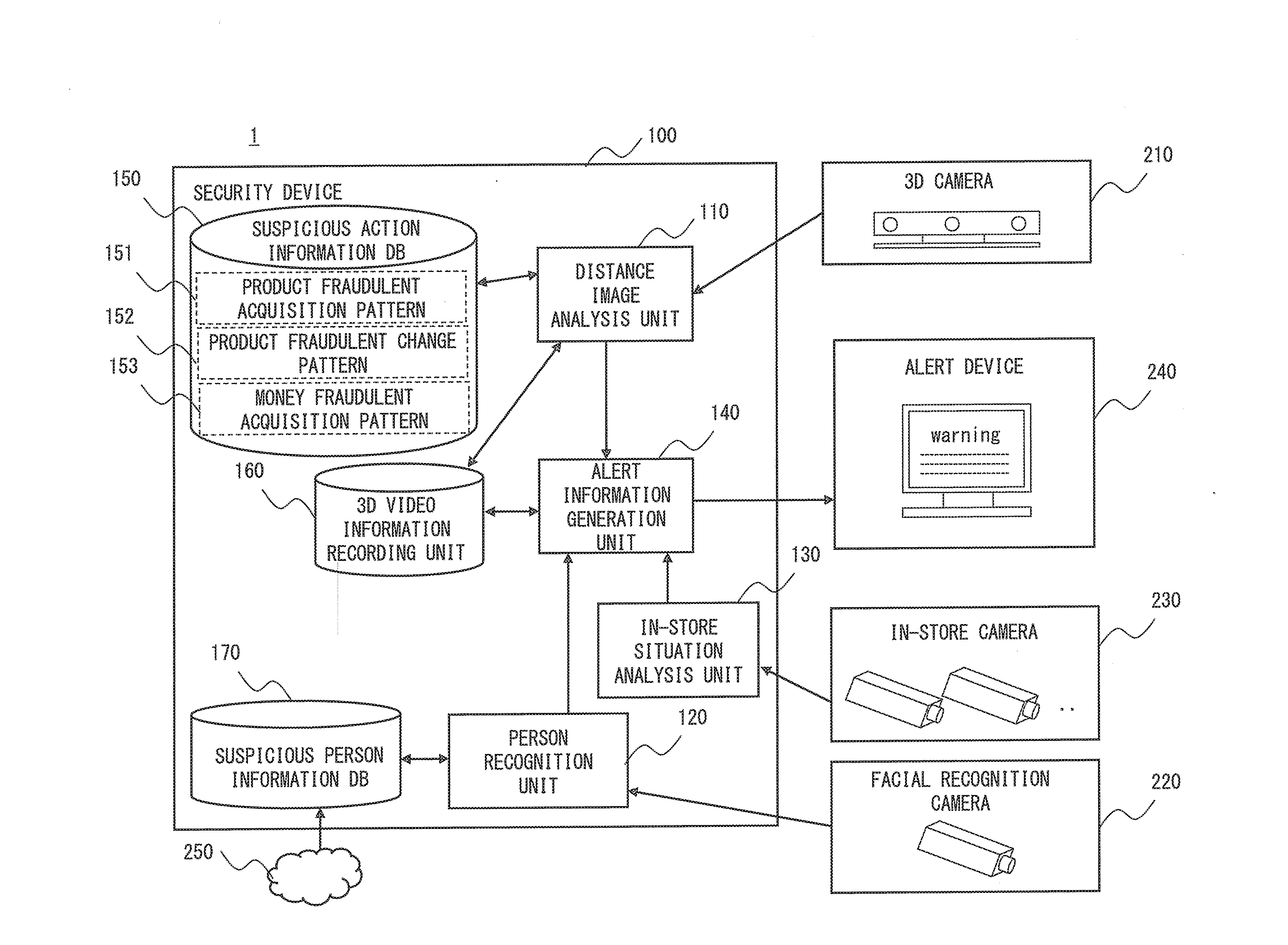
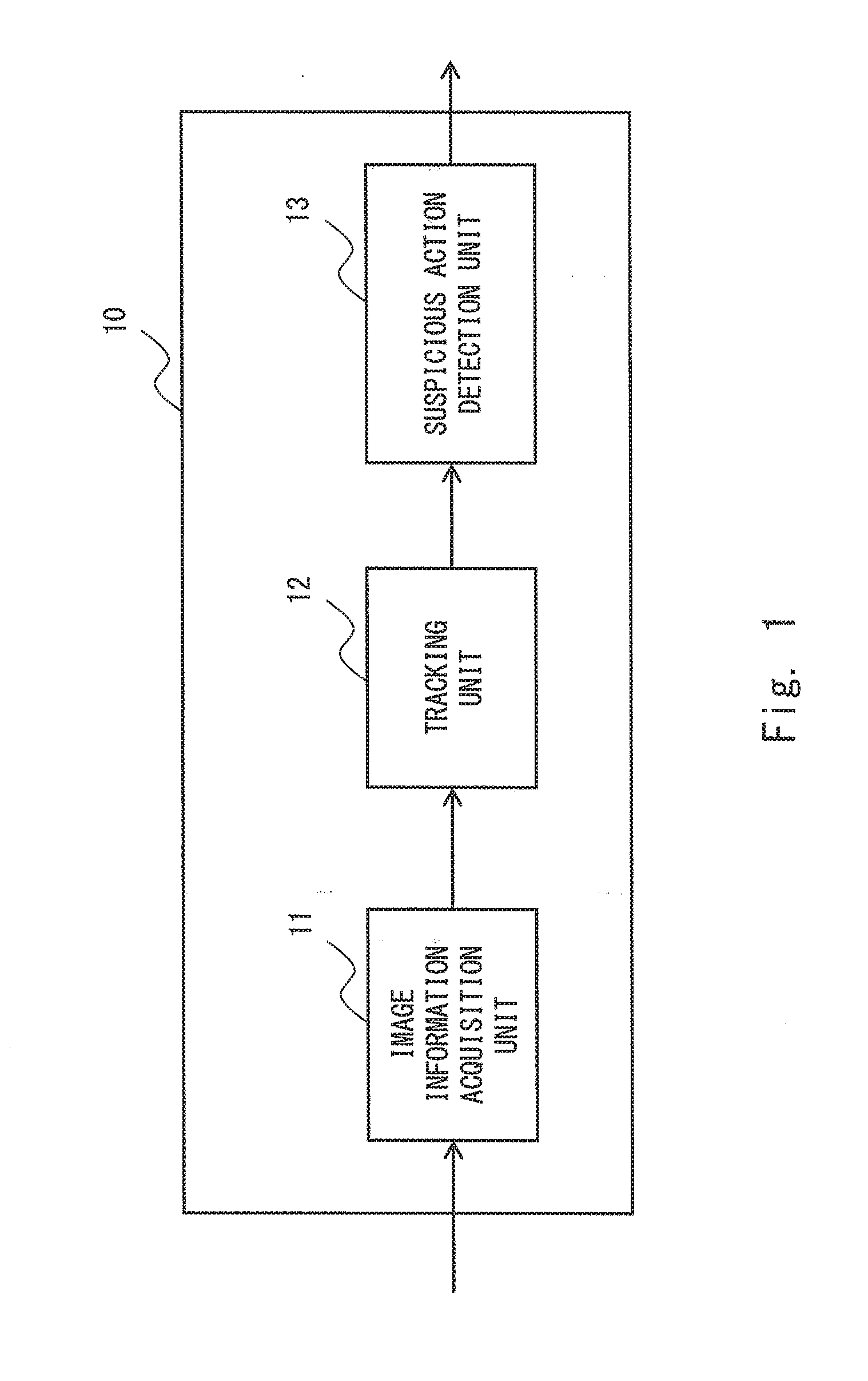
InactiveUS20160210829A1Accurate detectionImage analysisCharacter and pattern recognitionPattern recognitionSecurity system
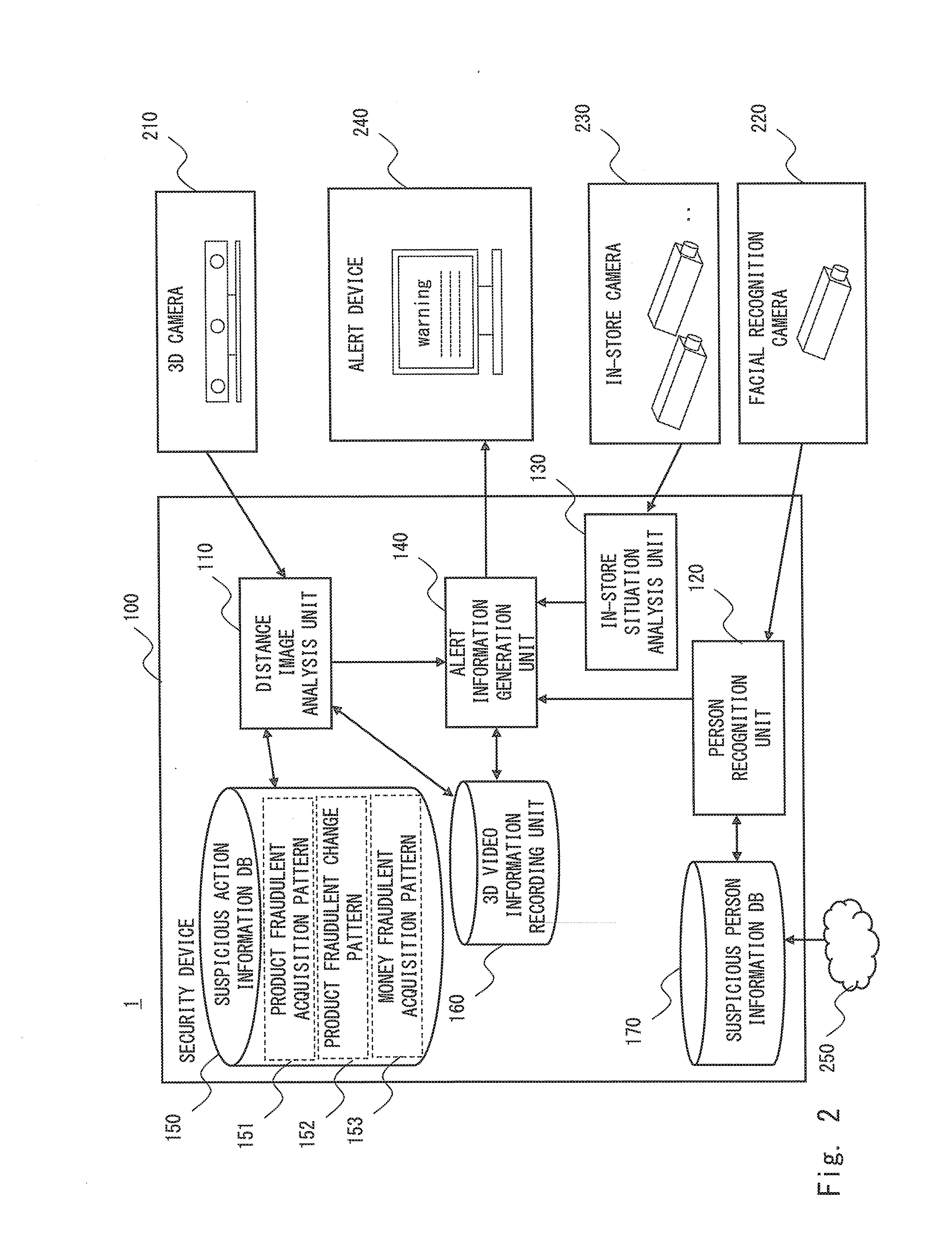
A security system (10) includes an image information acquisition unit (11) that acquires input image information on an image taken of a person in a store, a tracking unit (12) that tracks an action of a hand of the person based on the input image information, and a suspicious action detection unit (13) that detects a suspicious action of the person based on the tracked action of the hand. A security system, a security method, and a security program capable of accurately detecting a suspicious action are thereby provided.
Owner:NEC CORP
System and process for providing improved aircraft operational safety
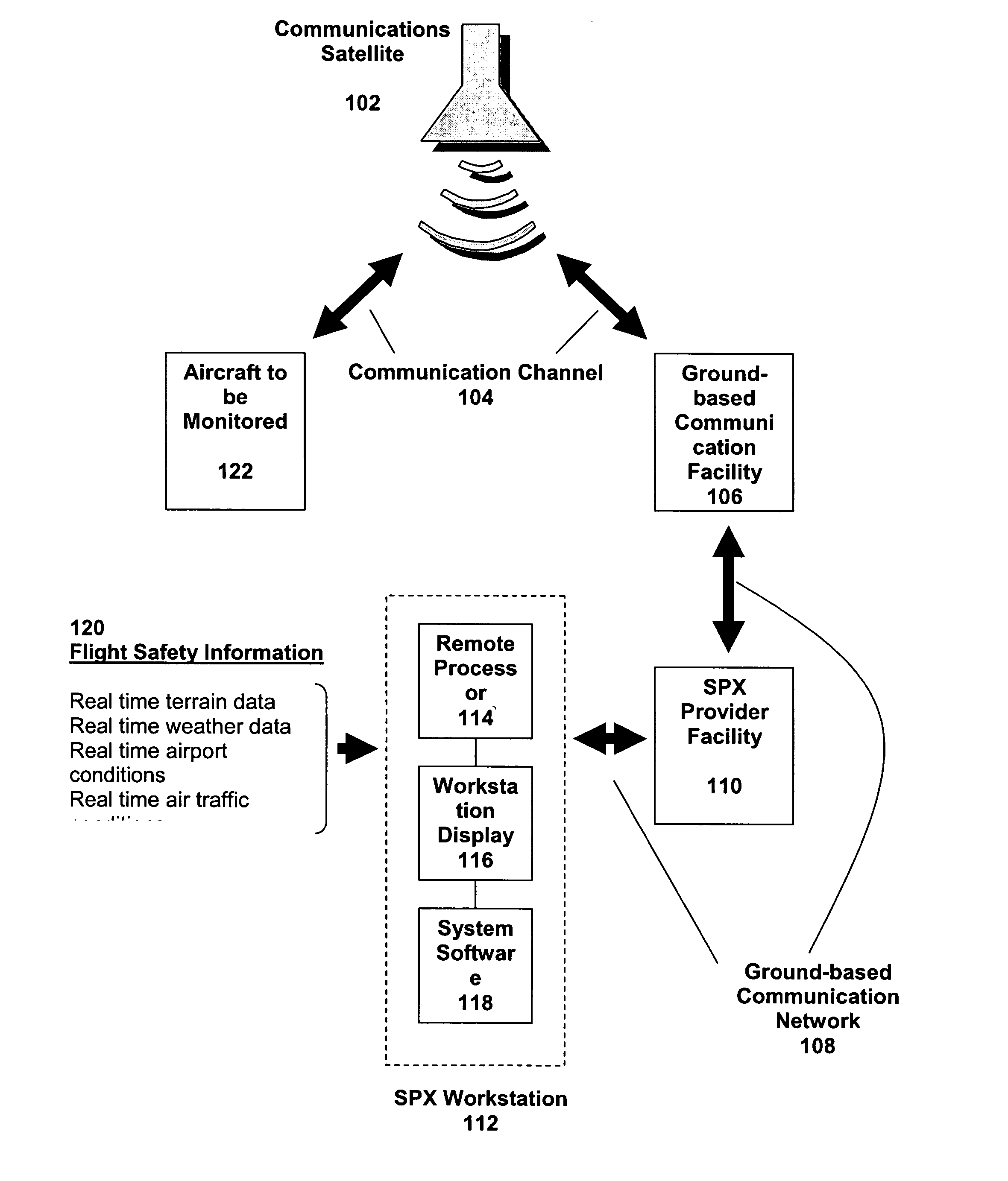
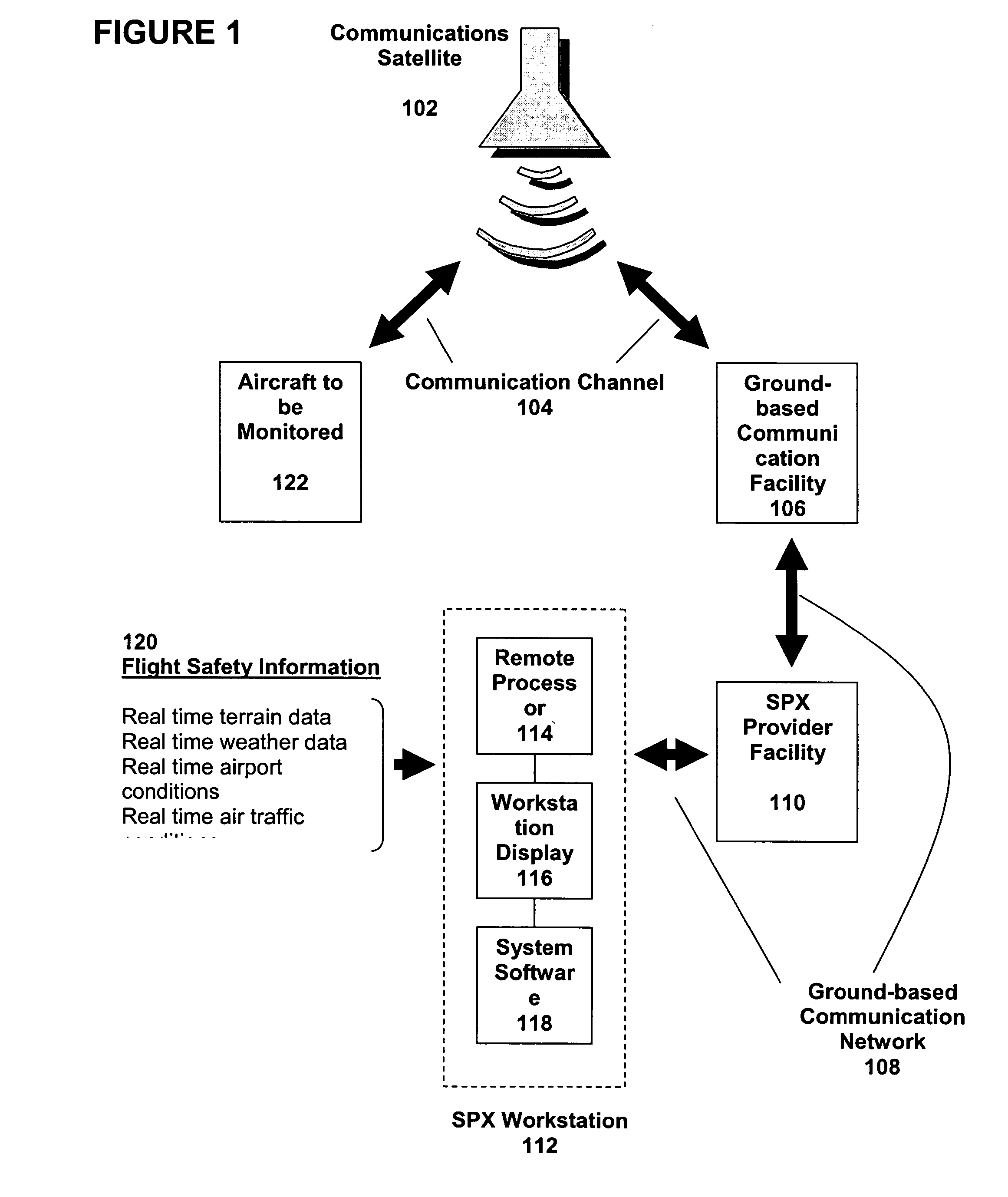
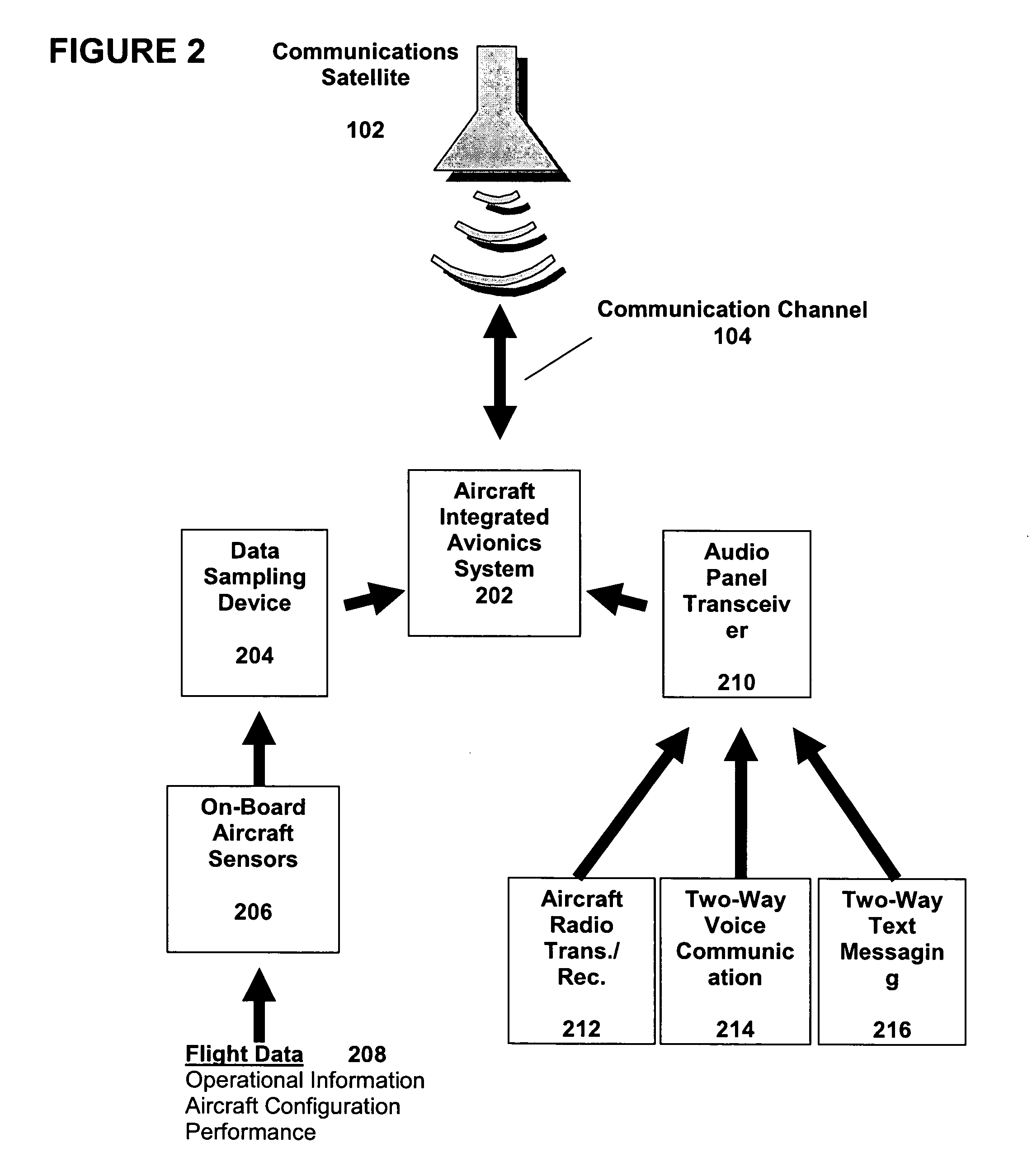
ActiveUS20060022845A1Operational safety is enhancedImprove flight safetyAnalogue computers for trafficRegistering/indicating working of vehiclesDriver/operatorWorkstation
The present invention relates to a system and a process for providing improved operational safety for aircraft. The system / process of the instant invention utilizes real-time, two-way transmission of voice and / or text and flight-critical data between an aircraft and a ground-based computer workstation, where transmitted information monitored and acted upon as necessary by a qualified flight safety person, e.g., a appropriately trained individual (including but not limited to a safety pilot or other person trained in safety procedures). This safety person can perform a number of functions that would enhance flight safety, such as reducing the workload of the primary pilot(s), assisting in the performance of routine checklists, monitoring communications with air traffic control, and advising the pilot in the aircraft on how to handle any in-flight situations that may arise. By providing many if not all of the advantages of a second or third pilot in the aircraft cockpit without imposing additional weight or space requirements on the aircraft, the system / process of the instant invention can increase flight safety while reducing the associated costs.
Owner:INNOVATIVE AVIATION SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com