Radio terminal security network and card locking method based on the ellipse curve public key cipher
An elliptic curve, public key cryptography technology, applied in radio/induction link selection arrangement, secure communication device, public key for secure communication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
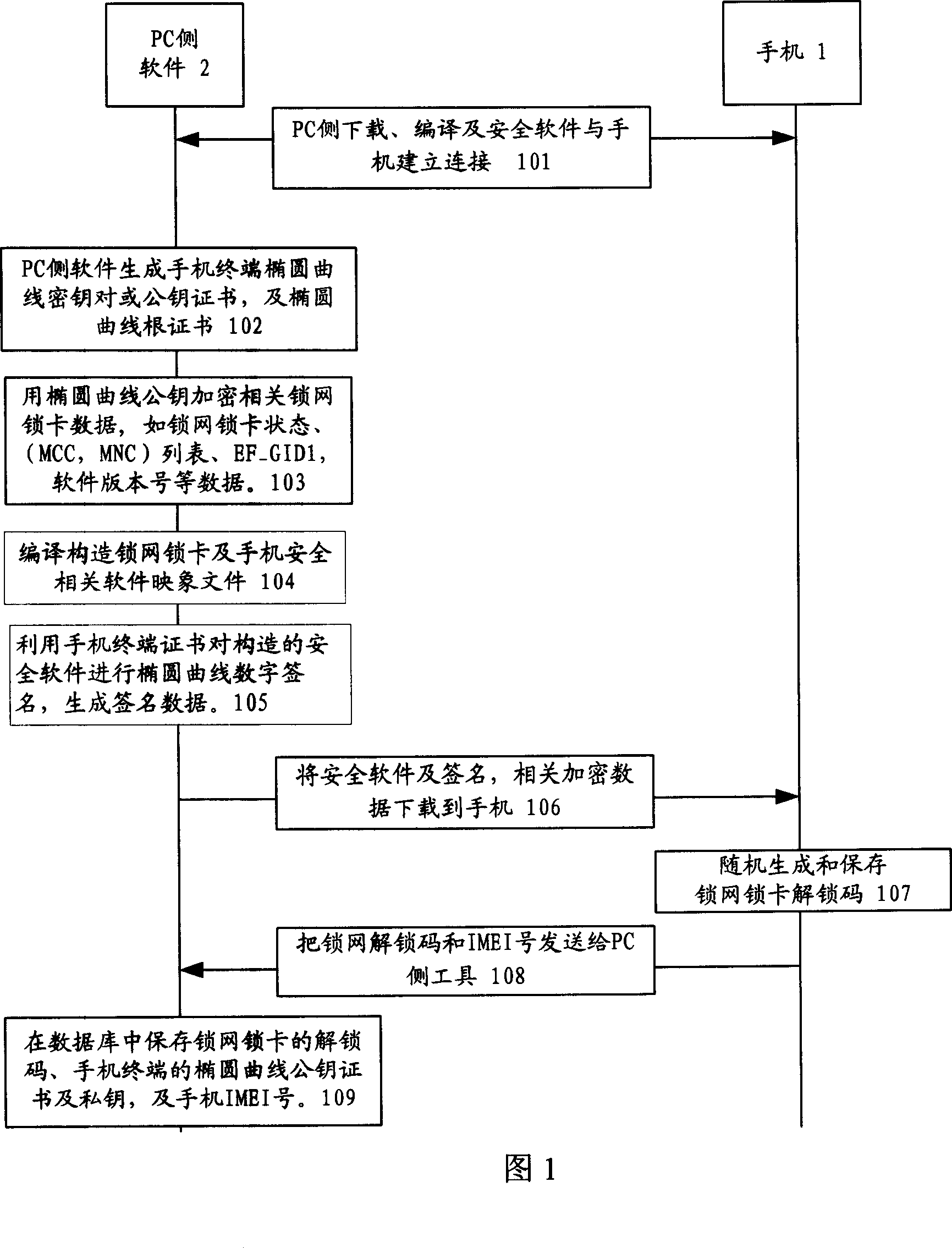
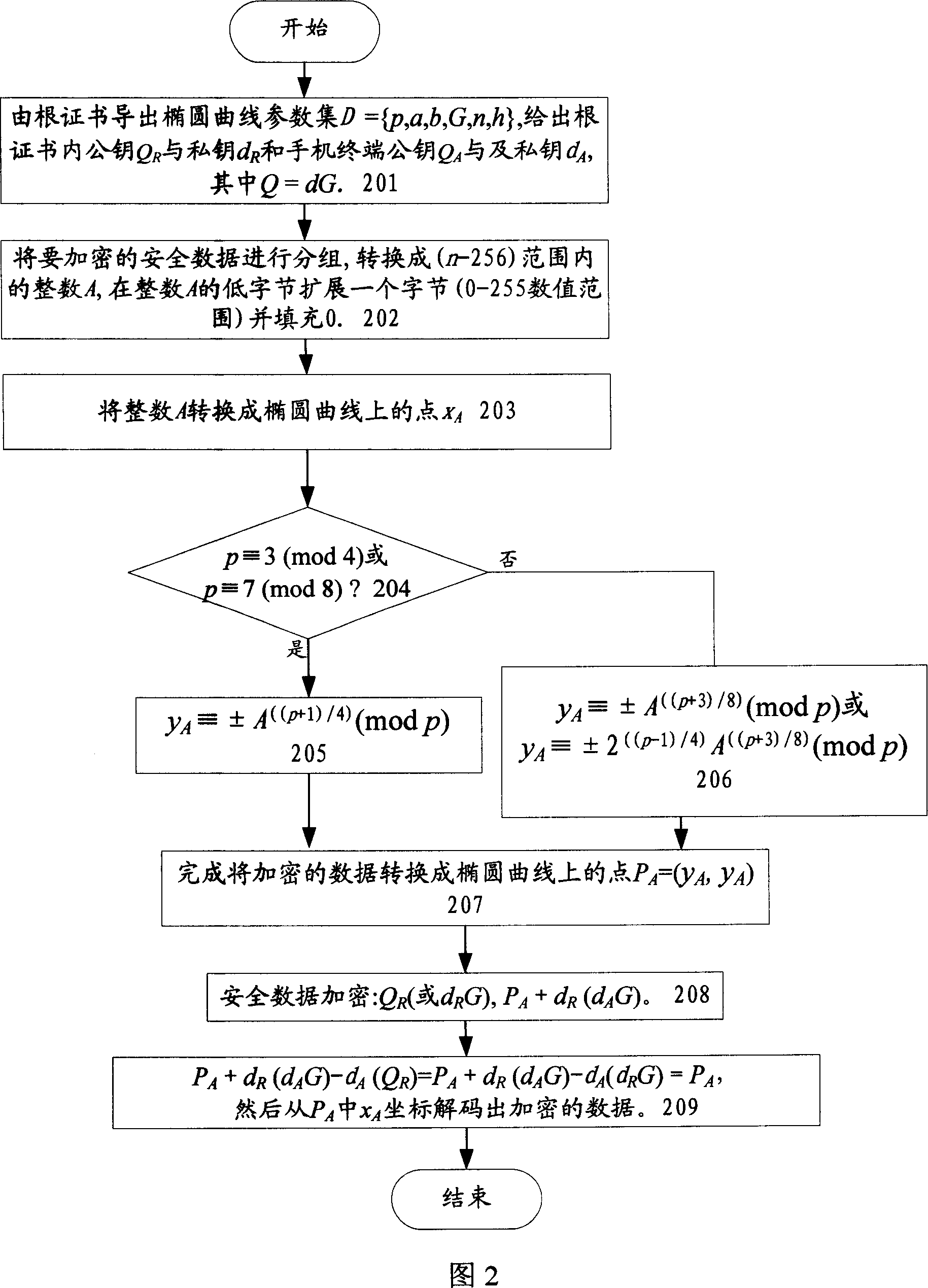
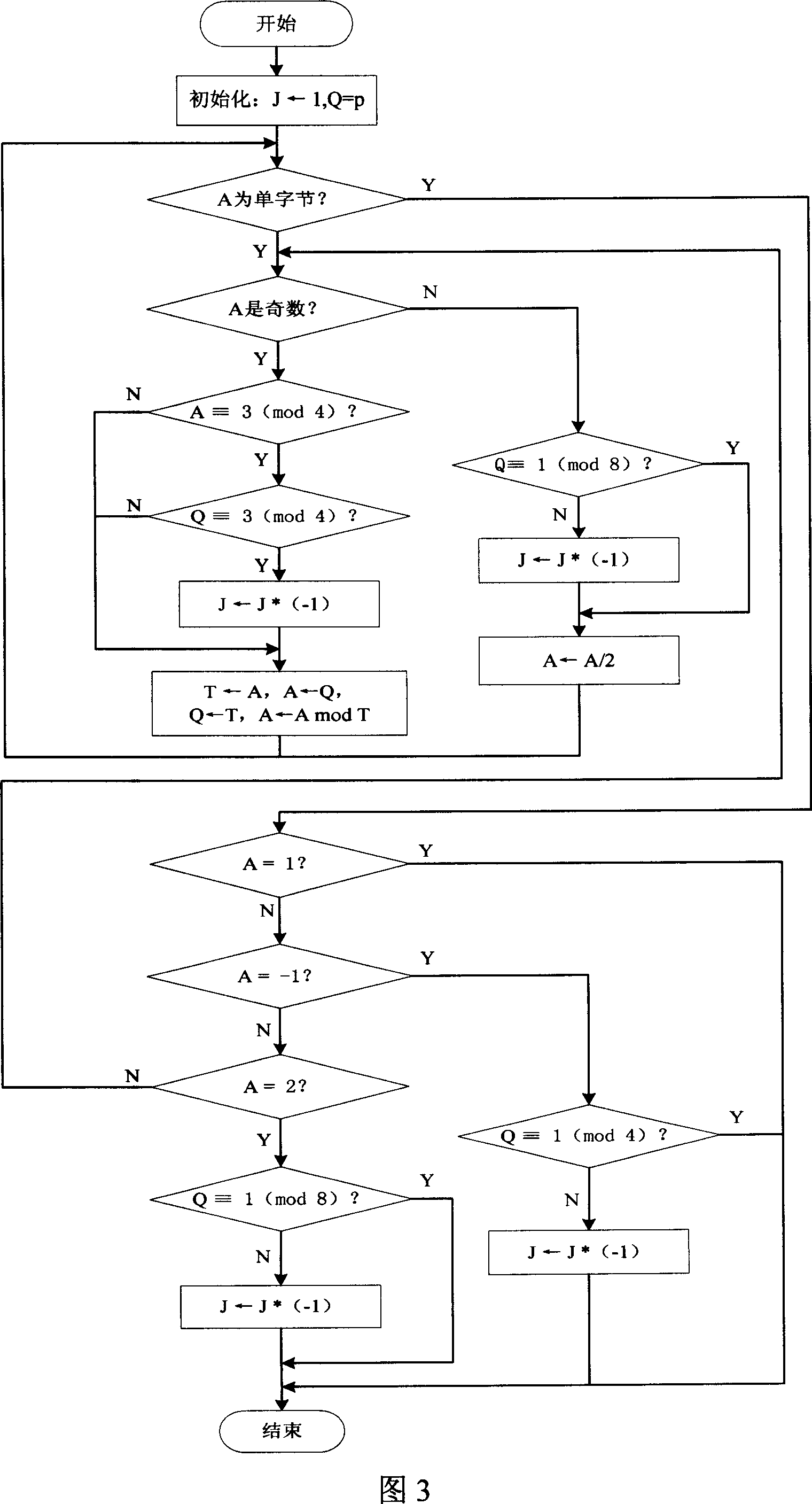
[0036] First, the key of the present invention is explained: (1) starting from the discrete logarithm of the elliptic curve, supplemented by an anti-collision hash function, utilizing the digital signature method of the elliptic curve public key certificate, realizing the method of locking the network and locking the card of the mobile phone, including the network locking of the mobile phone Lock card software authorized use confirmation, software integrity check, encrypted storage of relevant security parameters of lock network lock card, and methods of security realization of lock network lock card and safe unlocking of lock network lock card.
[0037](2) The security basis of the present invention is based on the discrete logarithm problem of elliptic curves. Given an elliptic curve E defined on a finite field GF(p), a point P∈E of order n and a point Q=kP, where 0≤k≤n-1, determine k. The elliptic curve discrete logarithm problem has provable security. Compared with the cur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com