Encrypting-decrypting method based on AES algorithm and encrypting-decrypting device
An encryption and decryption and algorithm technology, applied in the field of encryption and decryption technology, can solve the problems of unfavorable AES modularization, increased area overhead, large area overhead, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
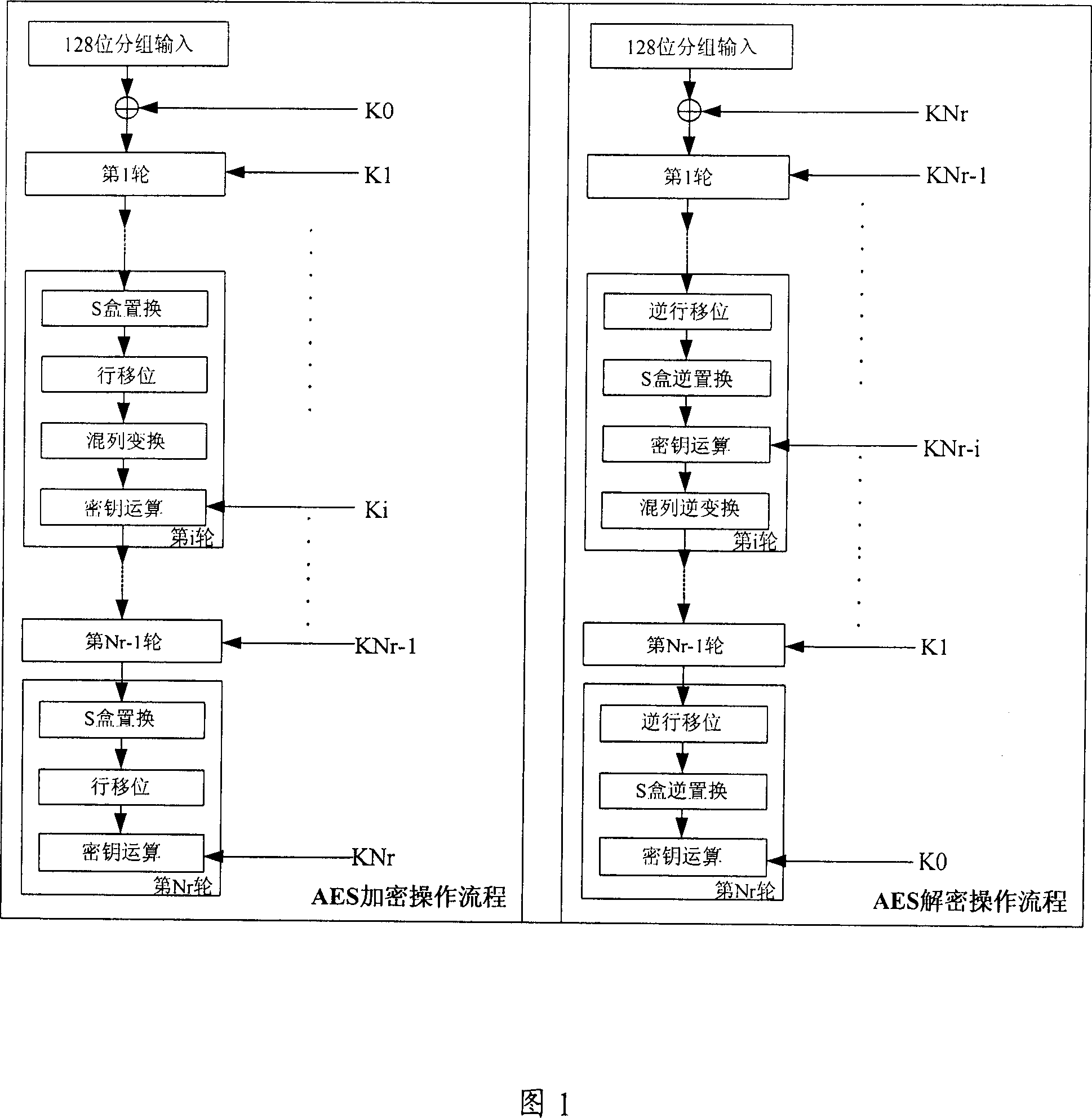
[0228] Optionally, the present invention also provides a second implementation of the encryption and decryption method based on the AES algorithm, referring to Figure 11, the specific implementation steps of the method are as follows:
[0229] First in step S200, the number of iterations Nr is set according to the key length, the key length can be 128 bits, 192 bits and 256 bits, correspondingly, the number of iterations Nr can be 10, 12 or 14;
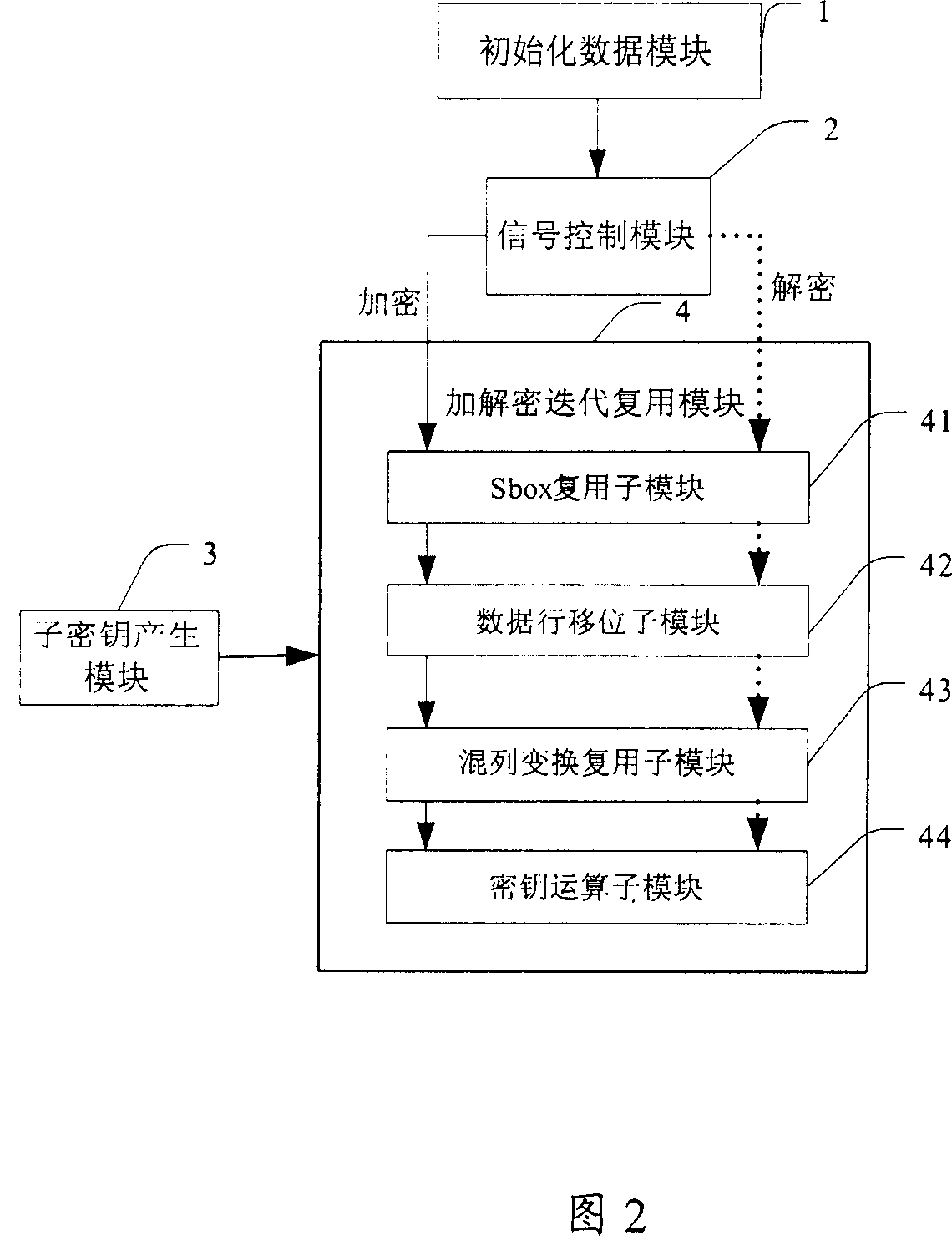
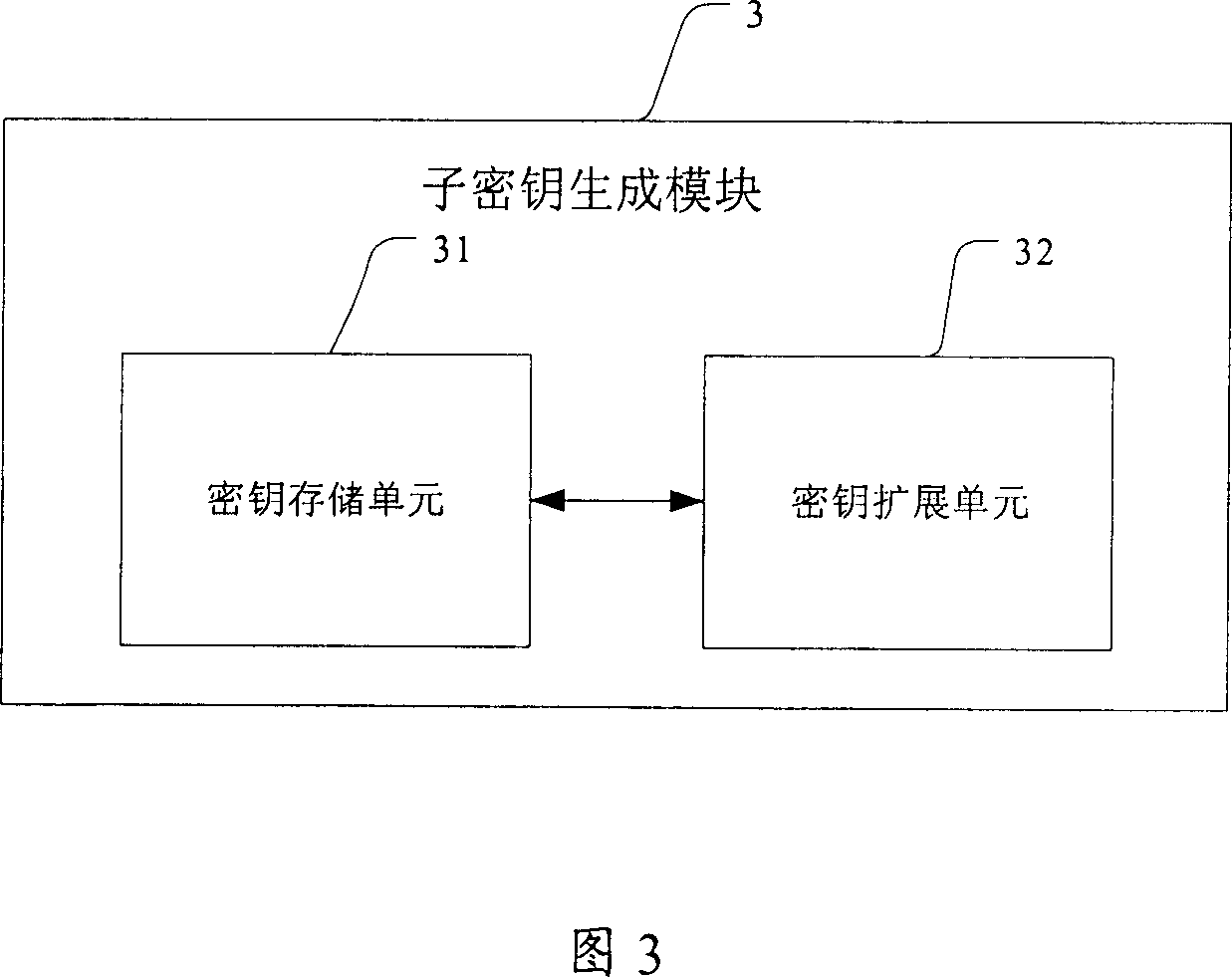
[0230] In step S201, dynamically generate sub-keys required for Nr encryption iterations or decryption iterations for key operations, it should be pointed out that this step runs through Nr encryption iterations or decryption iterations;
[0231] In step S202, the data to be encrypted or decrypted is initialized, that is, after the data to be encrypted or decrypted is input, before it performs the first round of key iteration, it is first combined with the subkey generated in step S201 The key is used to perform key operation operatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com