Mutual identifying key consultation method and system based on hidden common key certificate
A public key certificate, two-party authentication technology, applied in the field of two-party authentication key negotiation, can solve the problems of loss of shared key security, no PKG forward security, Smart protocol can not achieve complete forward security, etc. The effect of distribution difficulty, eliminating session key escrow issues, and improving overall efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
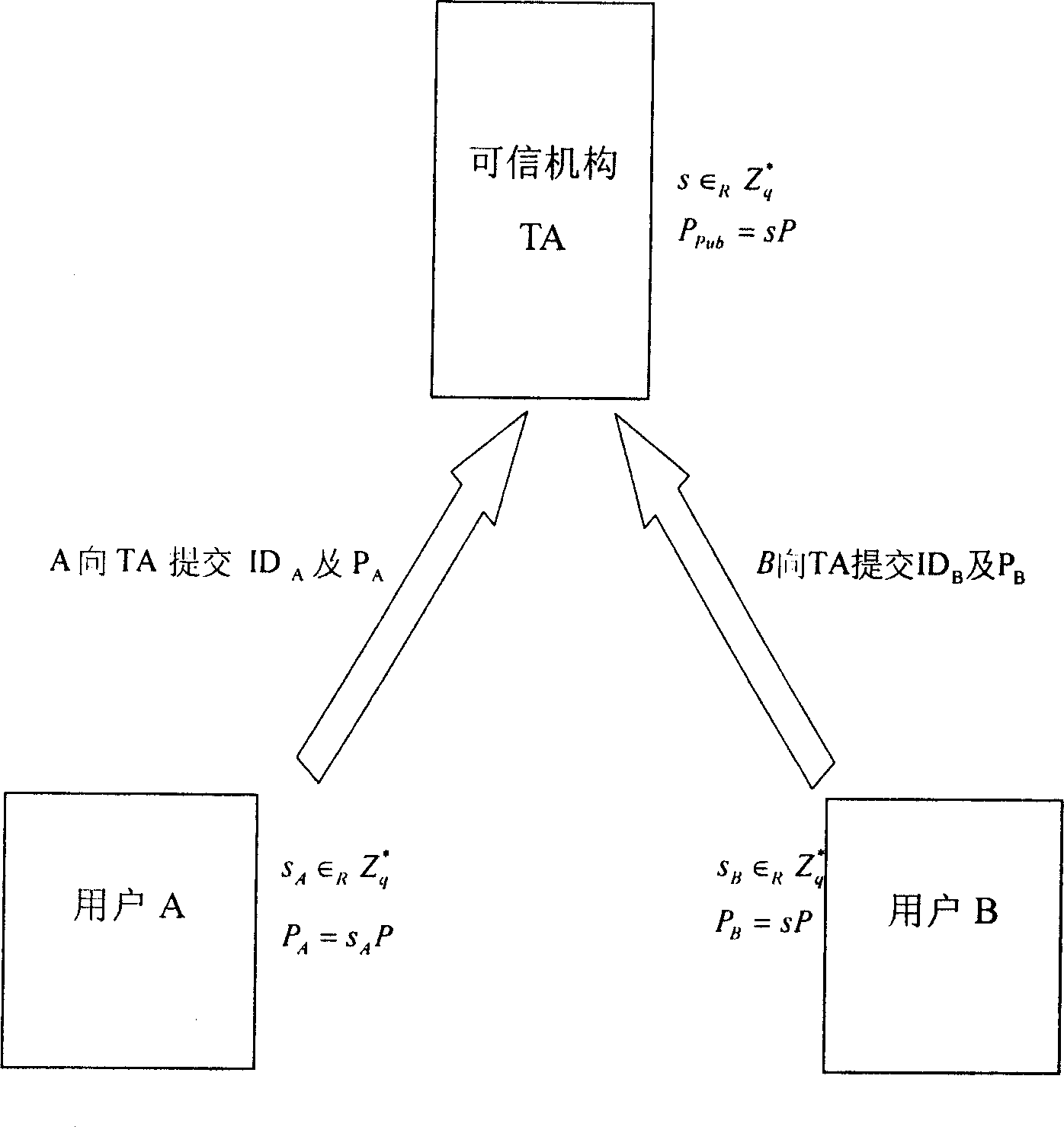
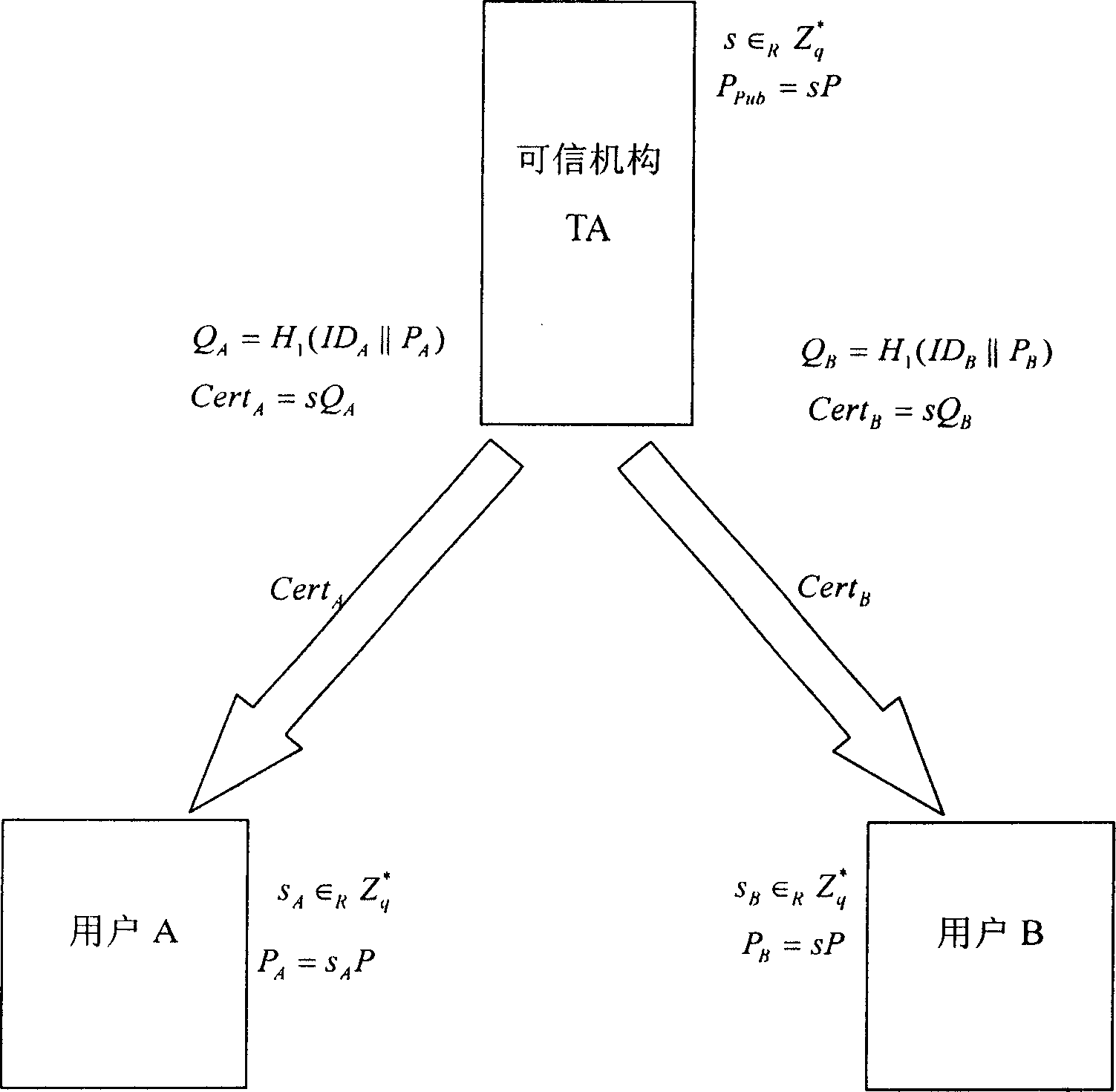
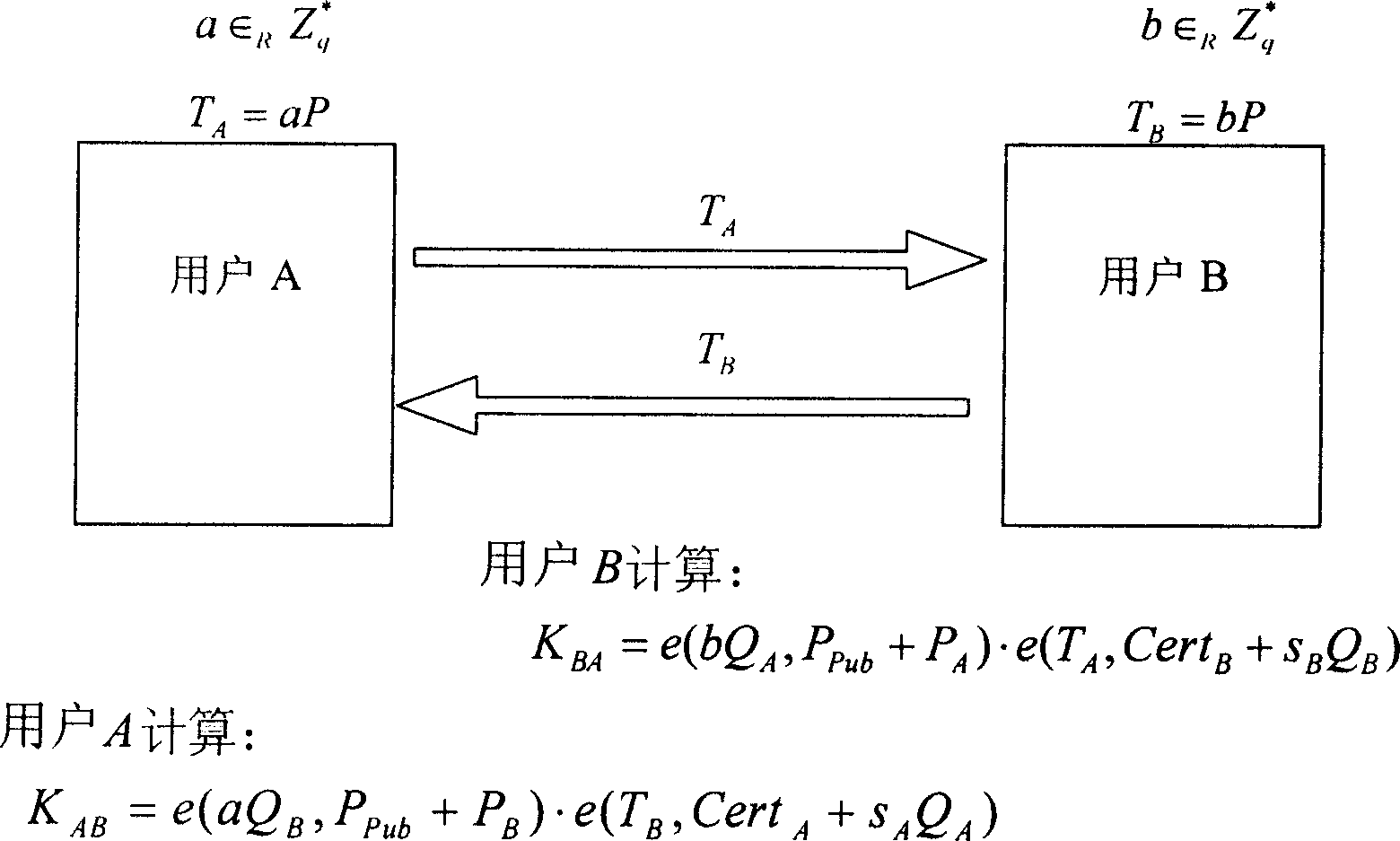
[0097] The present invention will be further described below in conjunction with the accompanying drawings.
[0098] Based on the public key of the traditional public key infrastructure PKI, the client needs to verify the public key of the client before using it, such as sending an encrypted message to a client or verifying its signature. And such a verification process must include the verification of the CA signature of the certificate authority. However, signature verification is generally a calculation process with a large amount of calculation.
[0099] In the process of the key agreement agreement, the method of the present invention adopts an implicit authentication public key, so that the user terminal does not need to carry out the public key authentication (that is, the verification of the CA signature) displayed before using the public key, which greatly reduces the The calculation burden on the user end improves the calculation efficiency of the user end during ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com