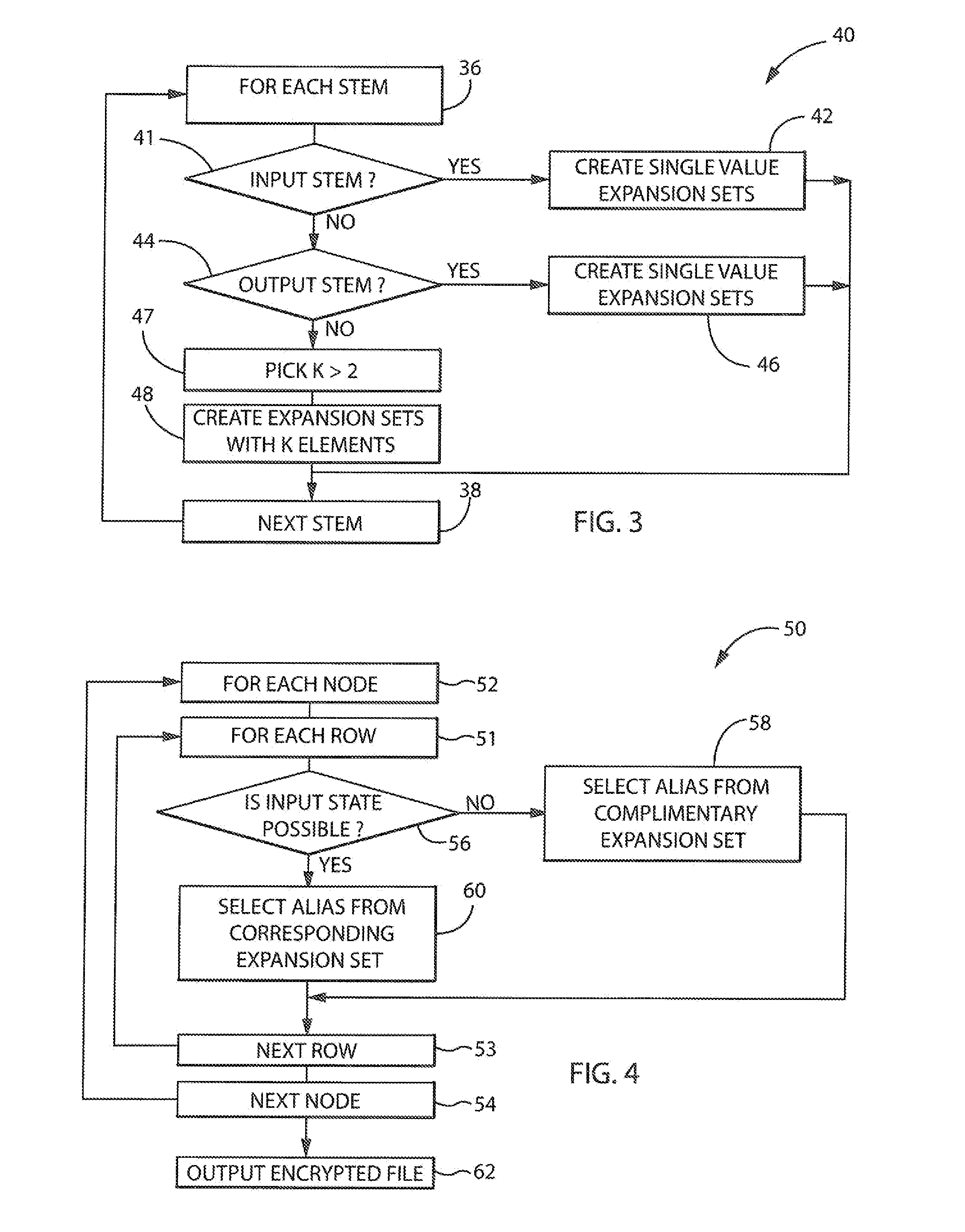
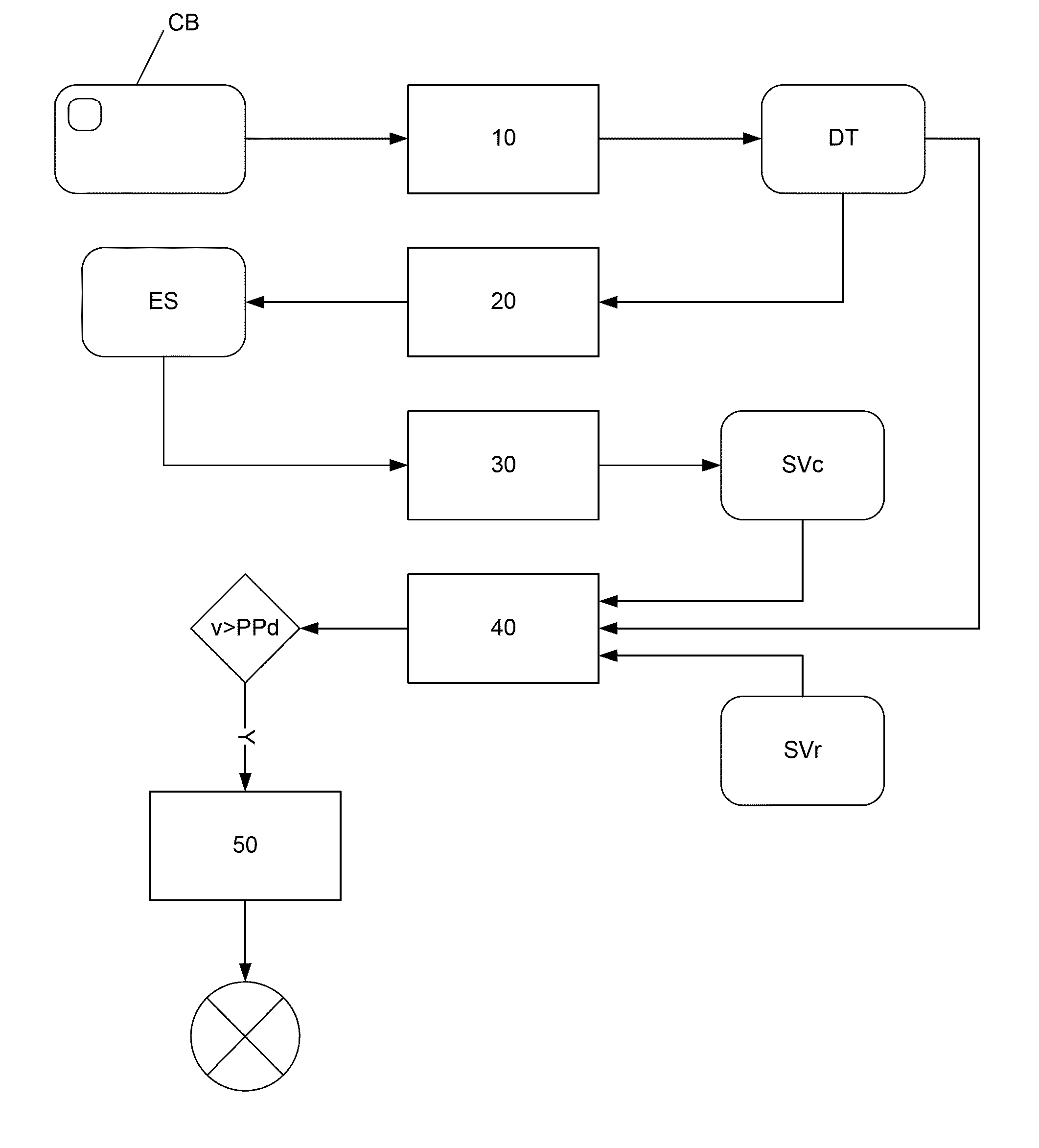
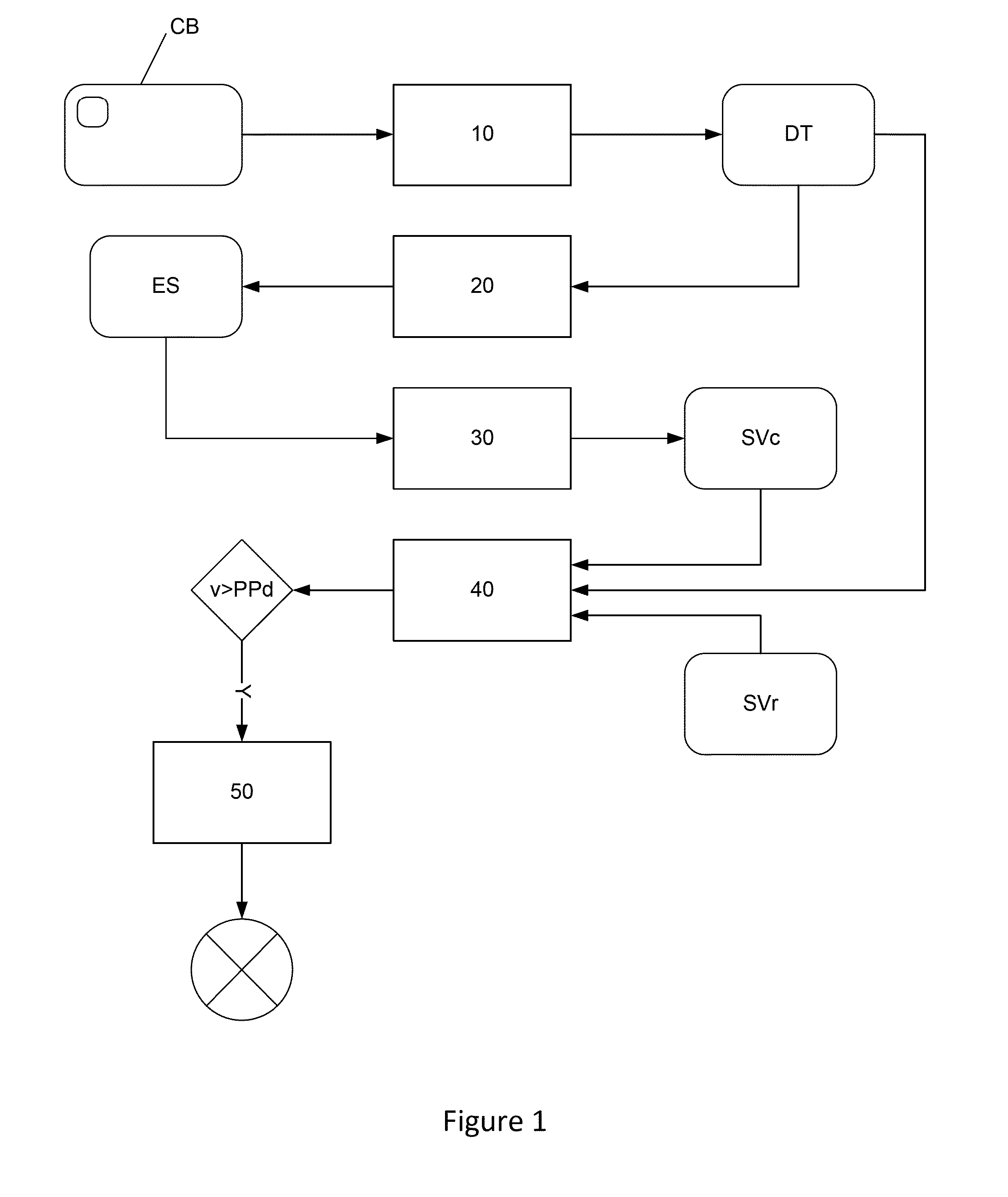
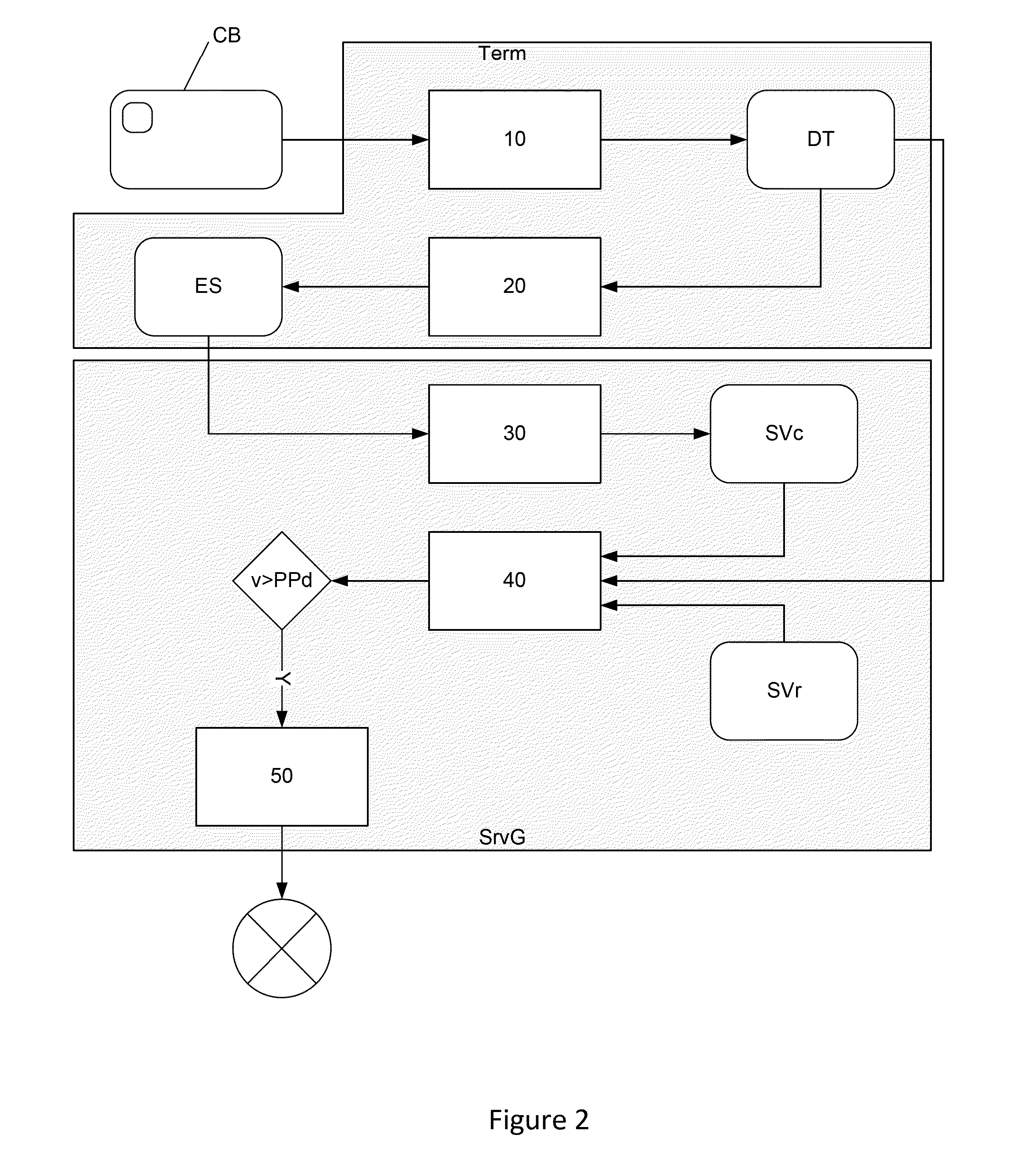
Patents
Literature
40results about How to "Preserving confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
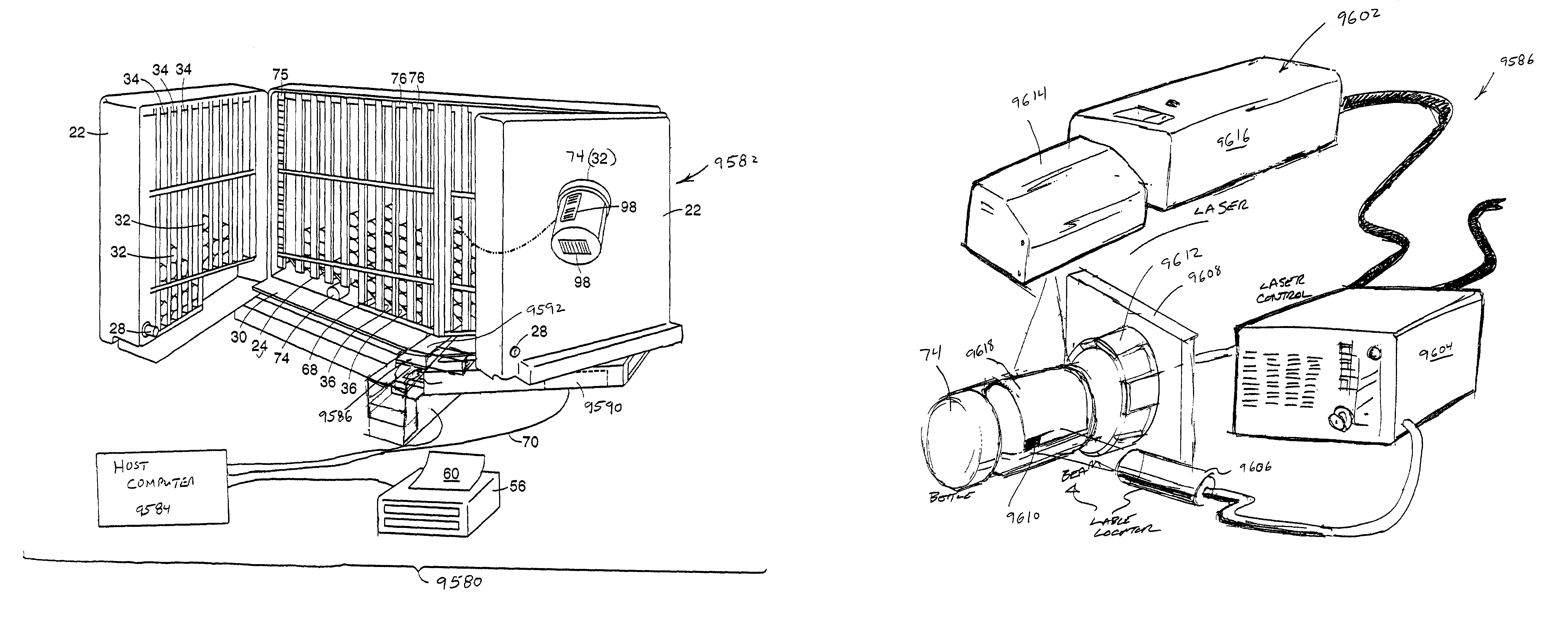
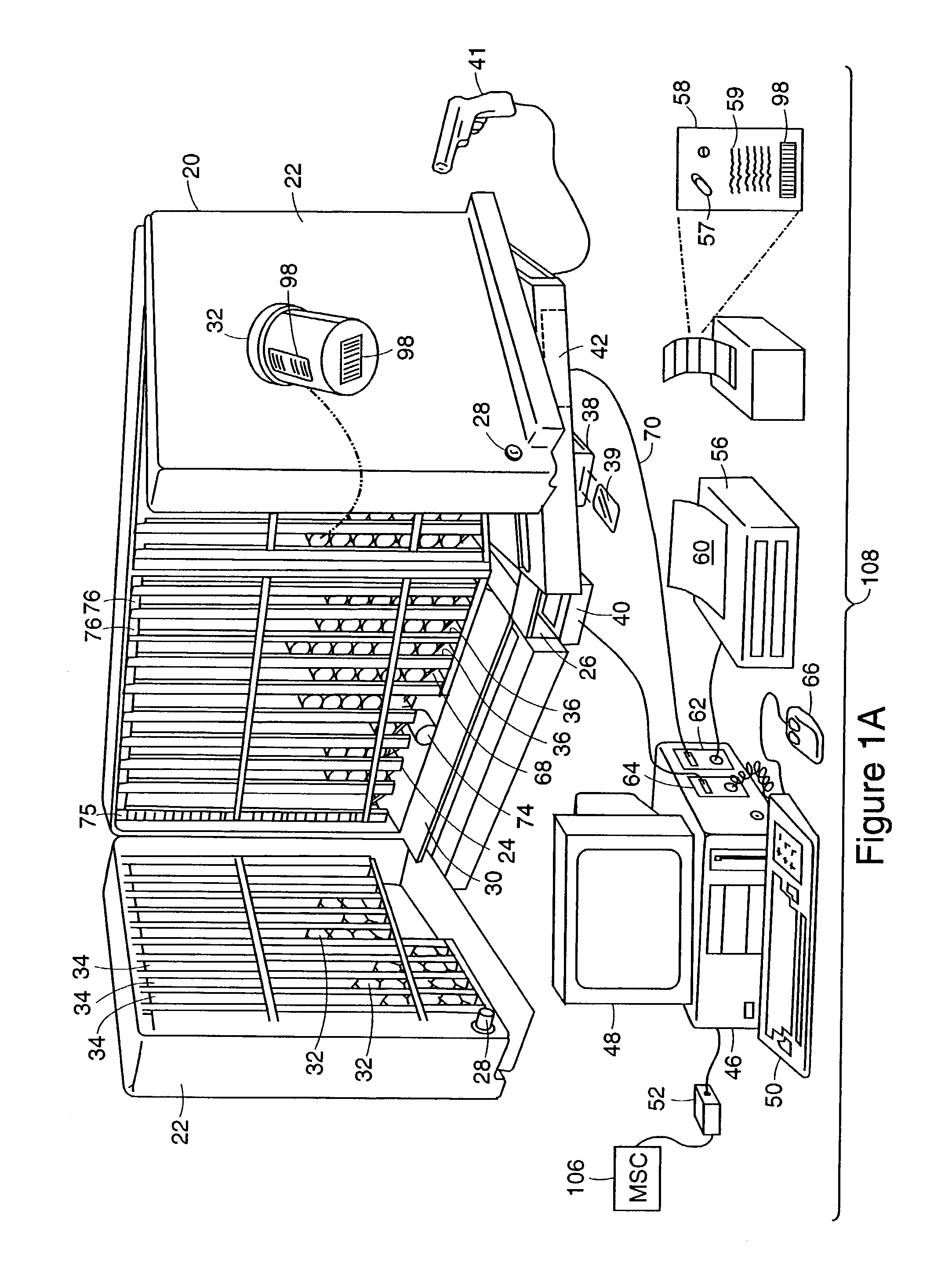
Systems for dispensing medical products
InactiveUS7006893B2Safe and convenientPreserving confidentialityControlling coin-freed apparatusDrug and medicationsCommunications systemMedical product
Owner:ARXIUM INC
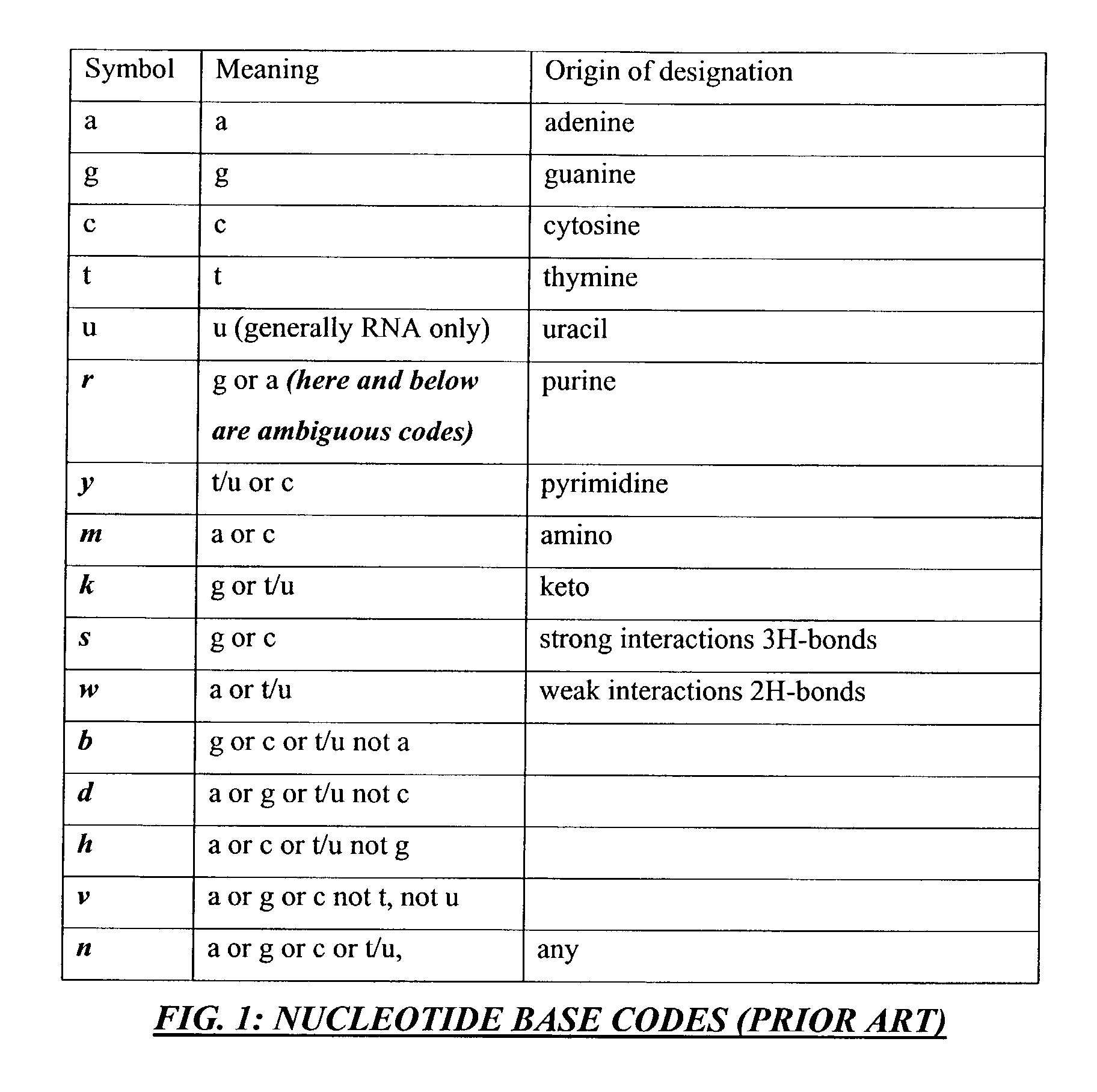
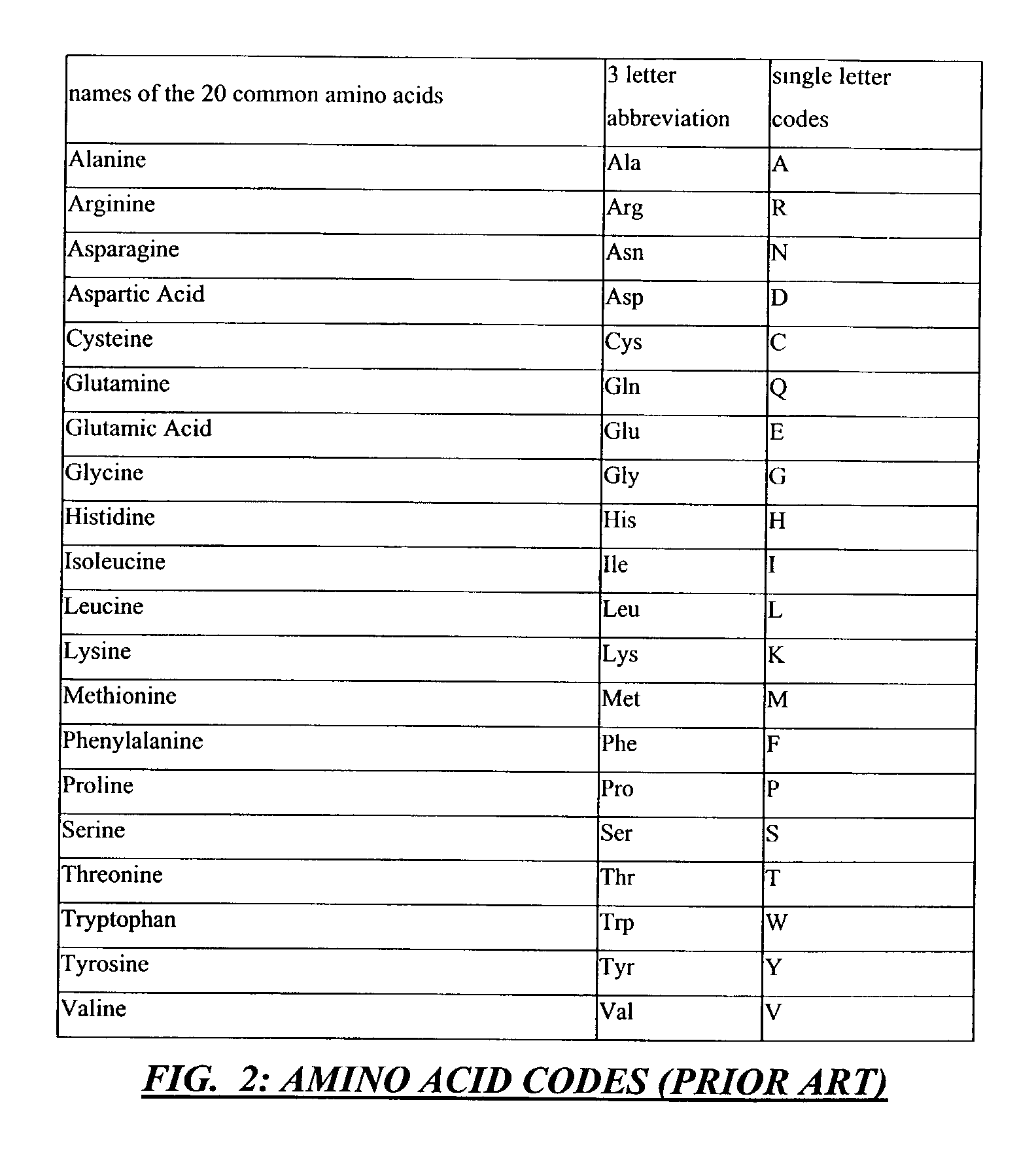
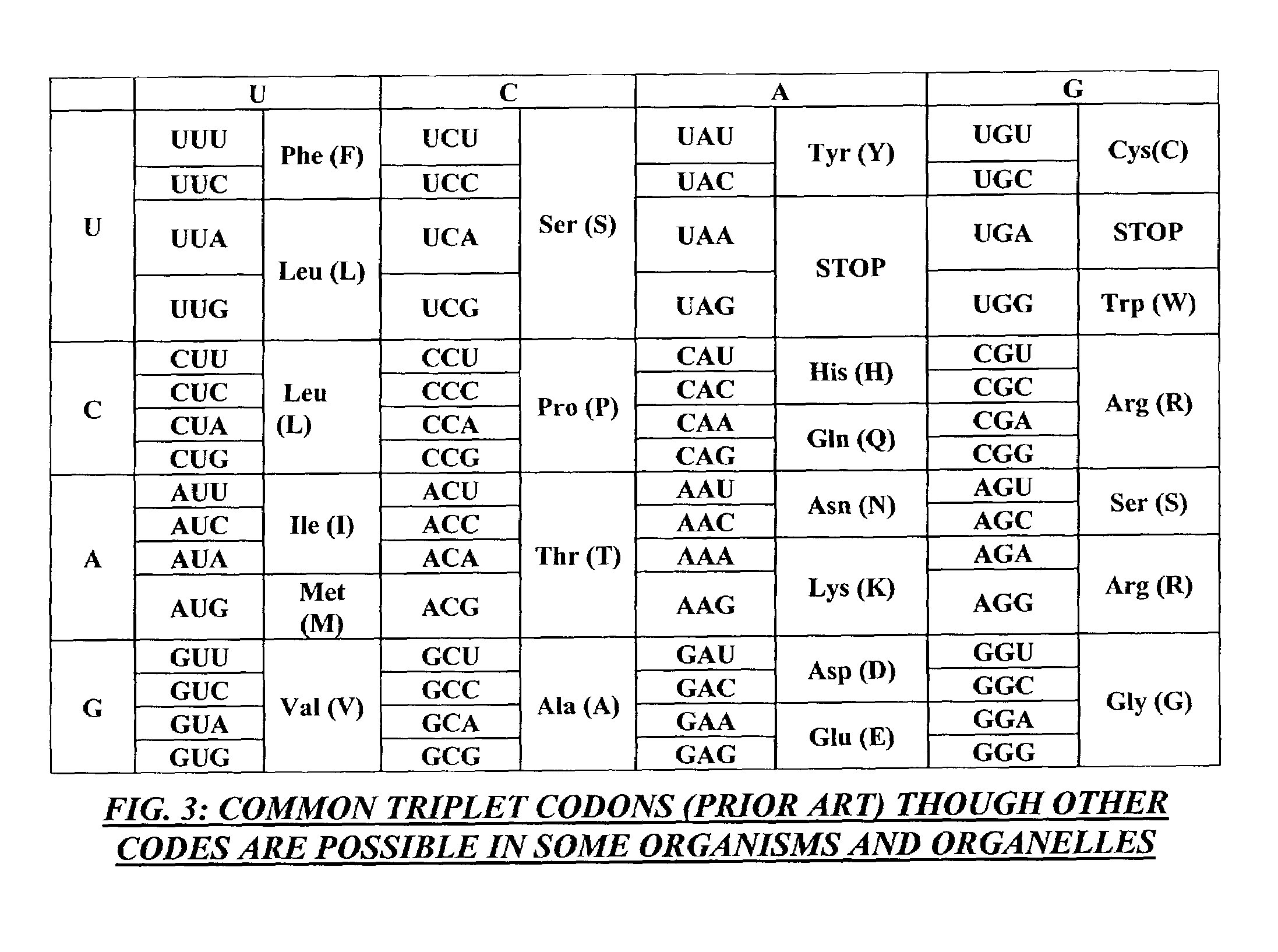
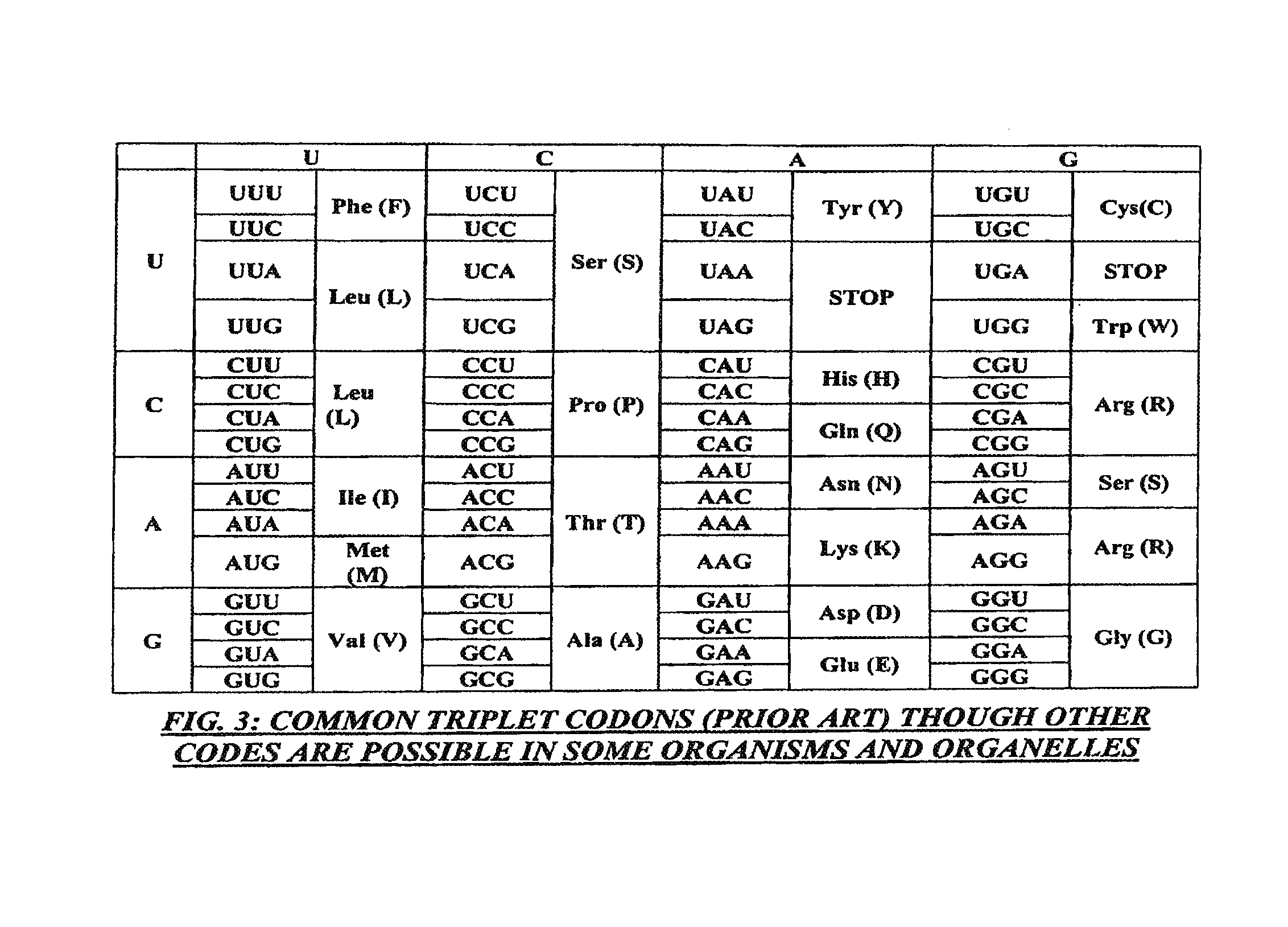
Method and apparatus for codon determining
InactiveUS7702464B1Efficiently determinedEfficient identificationBiological testingSequence analysisClient-sideData needs
Computer processing methods and / or systems for minimizing and / or optimizing data strings in accordance with rules and options. Minimized data strings can represent data sequences important in certain biologic analyses and / or syntheses. In specific embodiments, a request is generated by a user at a client system and received by a server system. The server system accesses initial data indicated or provided by the client system. The server system then performs an analysis to minimize the data needed for further reactions. In specific embodiments, a server can use proprietary methods or data at the server side while protecting those proprietary methods and data from access by the client system.
Owner:CODEXIS MAYFLOWER HLDG LLC
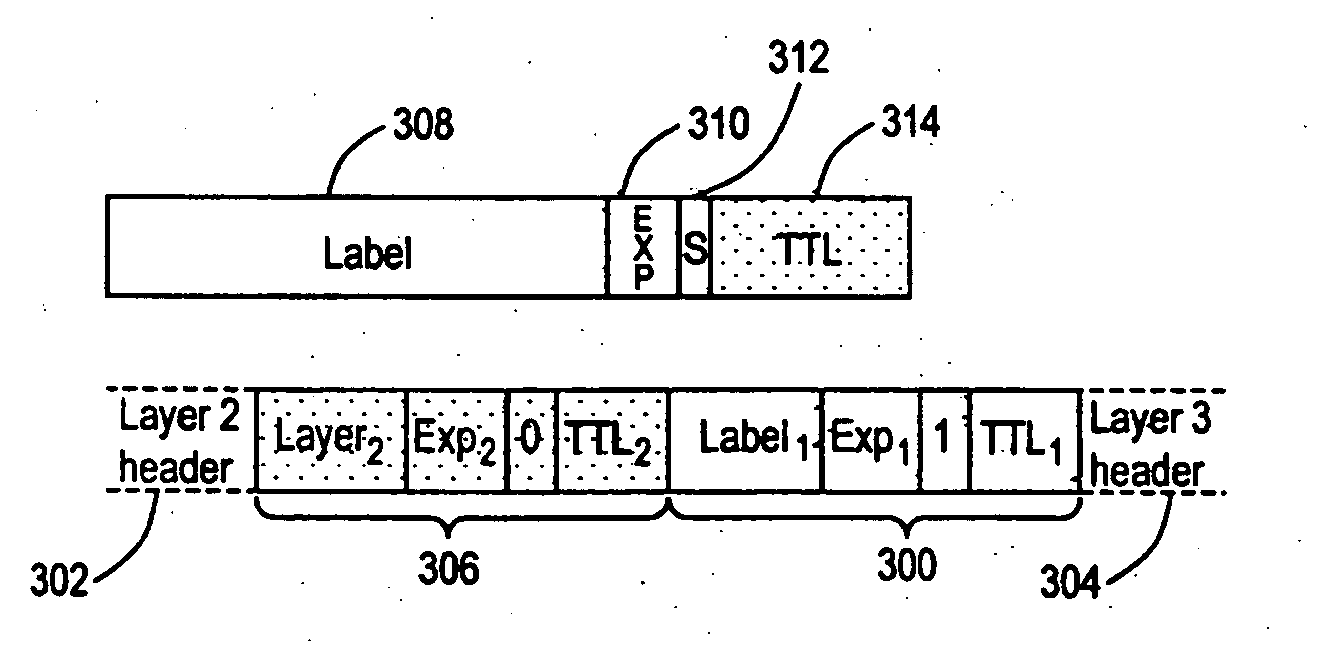
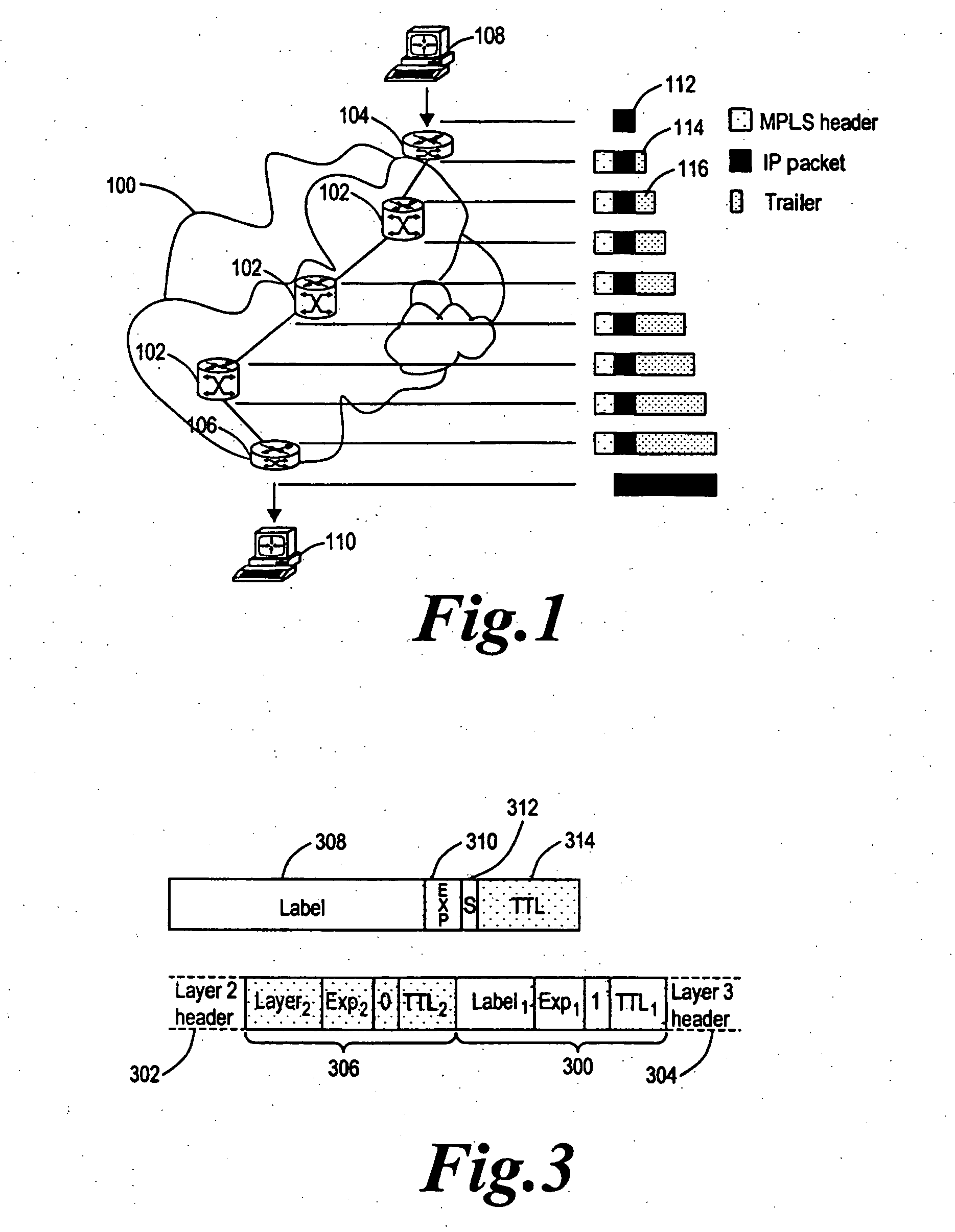
Method of generating a monitoring datagram
InactiveUS20050281259A1Improve accuracyPreserving confidentialityData switching by path configurationMonitoring statusNetwork generation
A method of generating a monitoring datagram for a predetermined network includes generating an initial datagram and encapsulating the initial datagram with a shim header, where the shim header has a first shim entry and a second shim entry, the first and second shim entries are associated with the predetermined network, the first shim entry is next to and follows the second shim entry, and where the first shim entry identifies the initial datagram as having a monitoring status.
Owner:AGILENT TECH INC
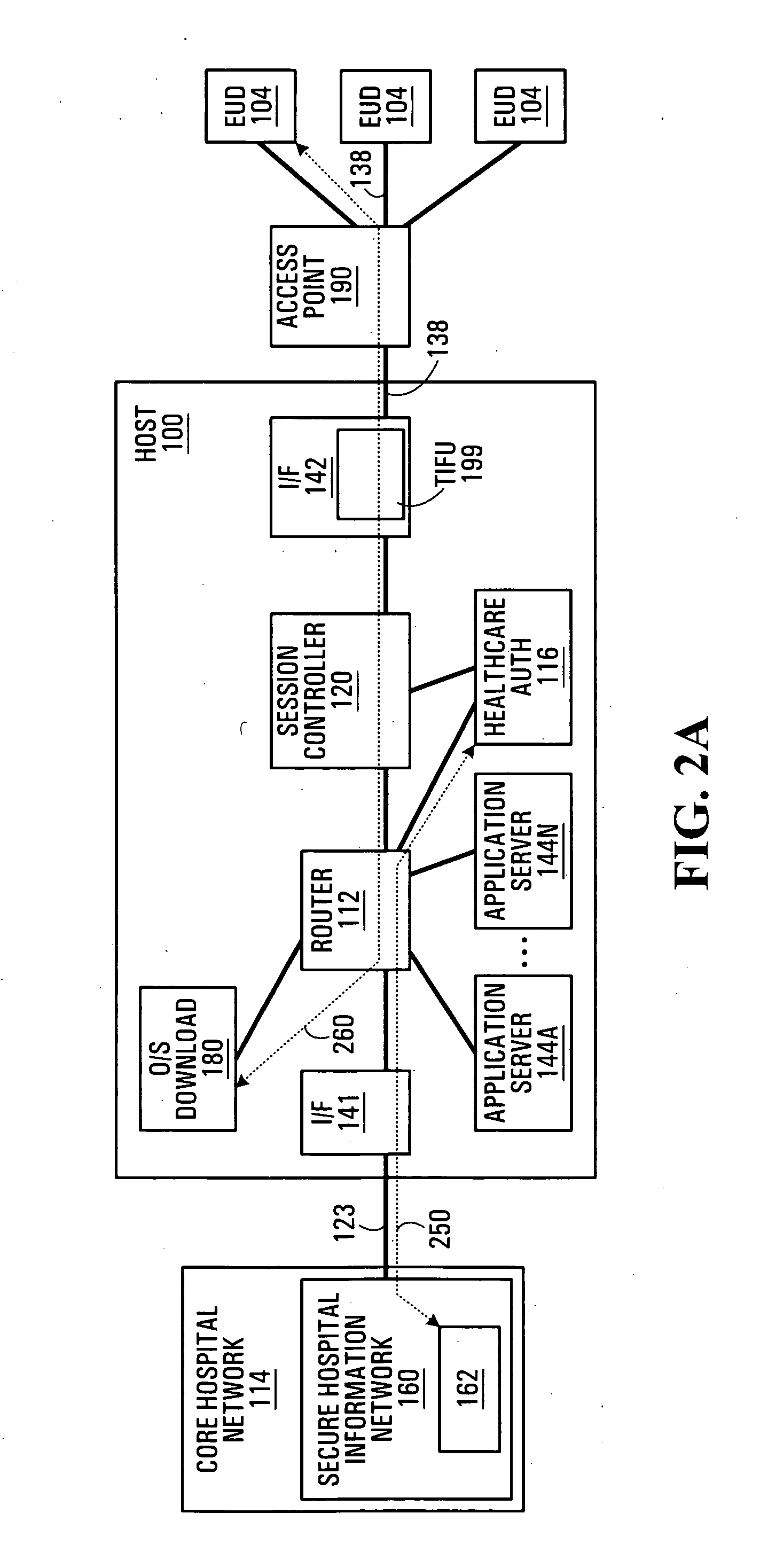
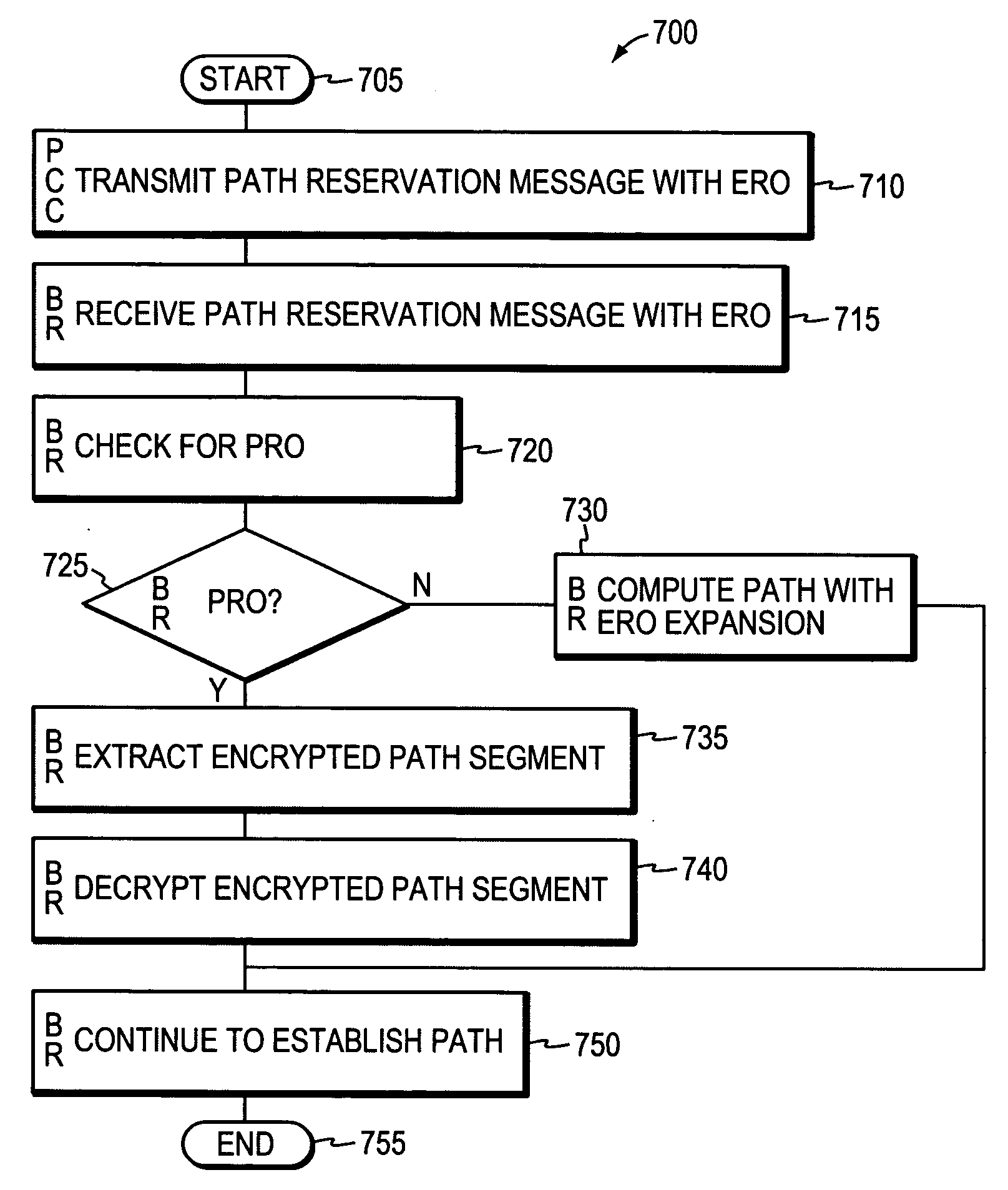
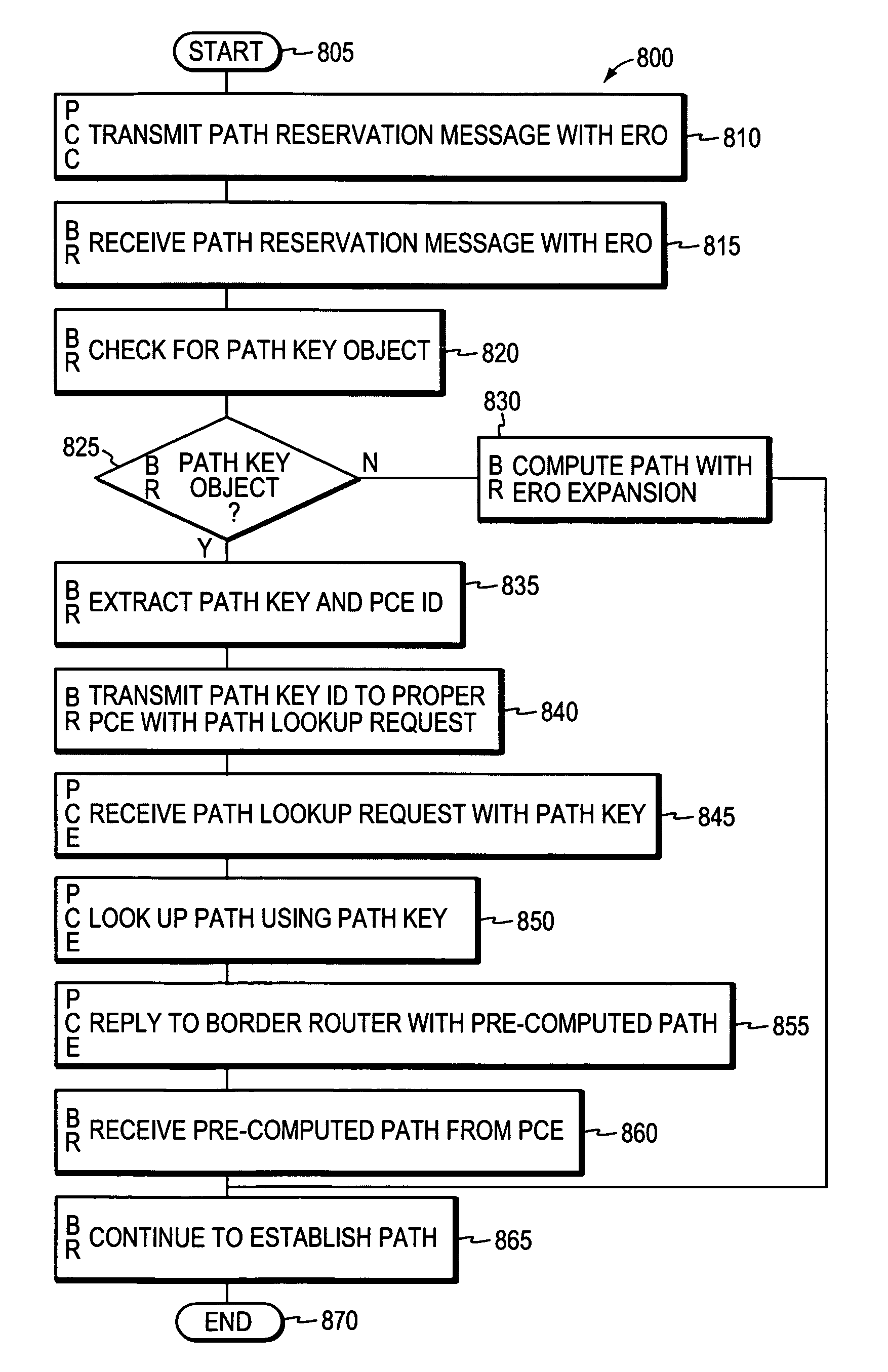
System and method for retrieving computed paths from a path computation element using a path key
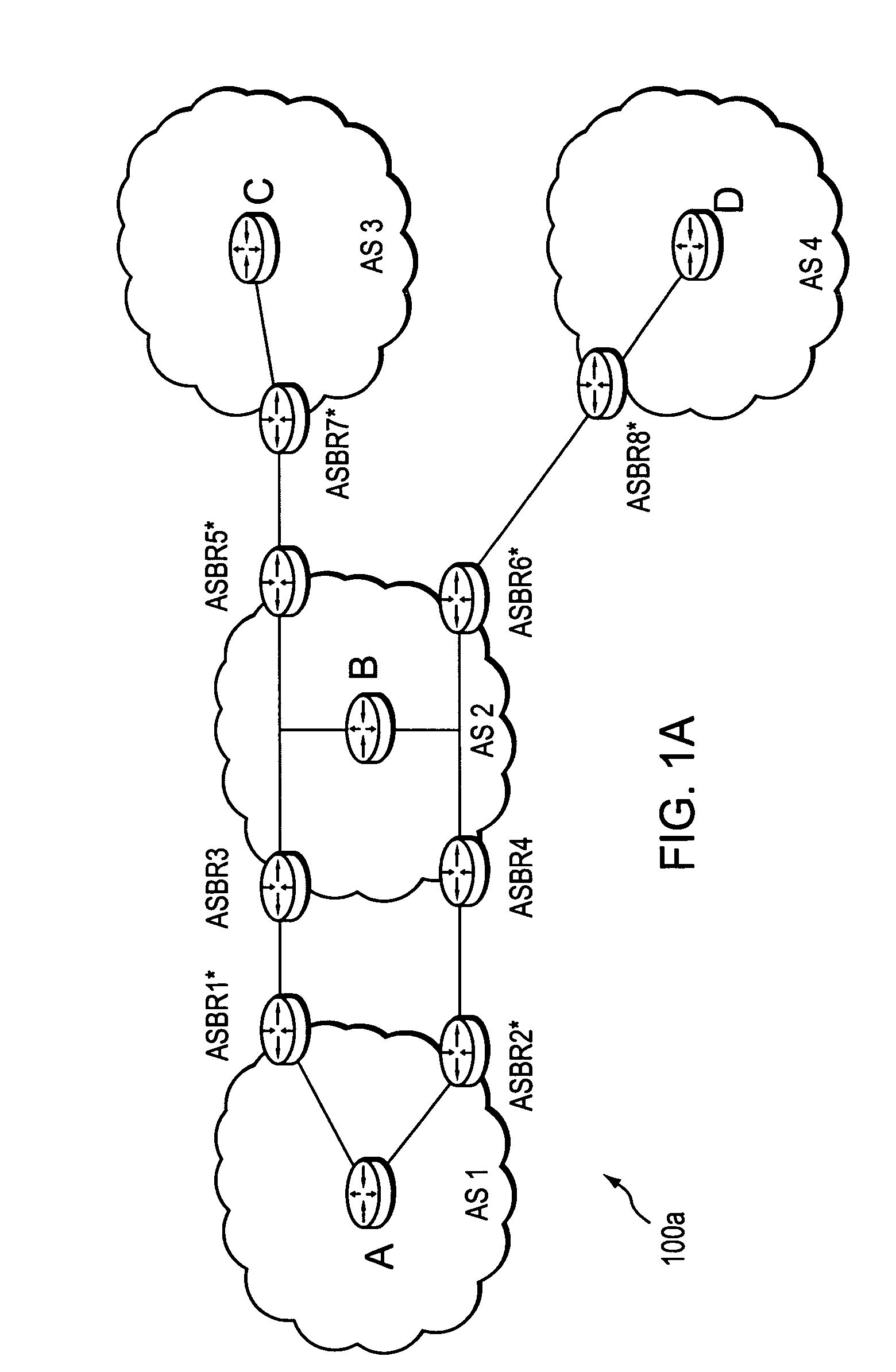
ActiveUS20060098657A1Computationally efficientPreserving confidentialityError preventionTransmission systemsTime segmentPath computation element
A technique retrieves computed path segments across one or more domains of a computer network in accordance with a stateful (“semi-stateful”) path computation element (PCE) model. The stateful PCE model includes a data structure configured to store one or more path segments computed by a PCE in response to a path computation request issued by a Path Computation Client (PCC). Notably, each computed path segment stored in the data structure is identified by an associated path-key value (“path key”). The path segment and path key contents of the data structure are temporarily saved (“cached”) at a predetermined location in the network for a configurable period of time.
Owner:CISCO TECH INC
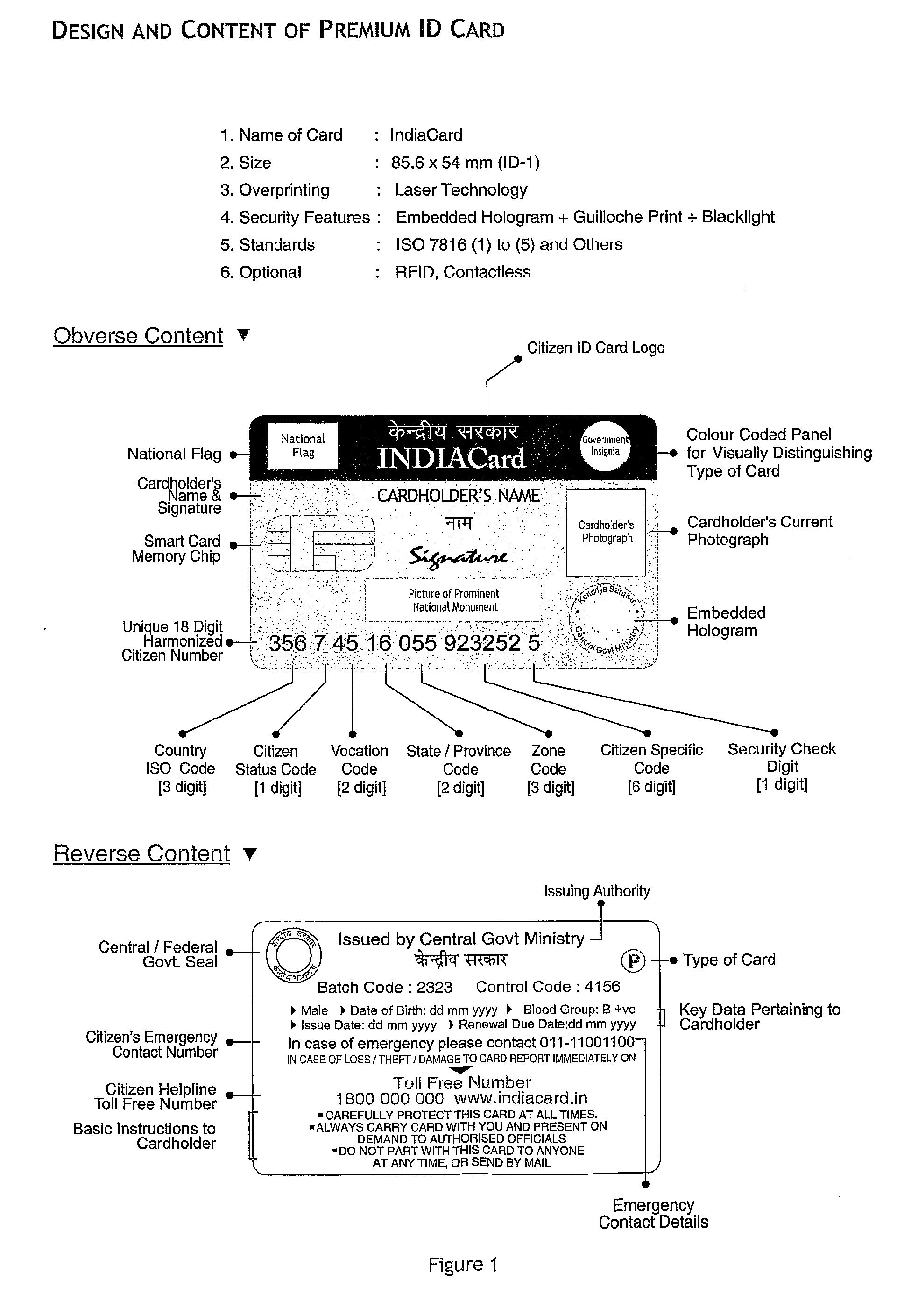
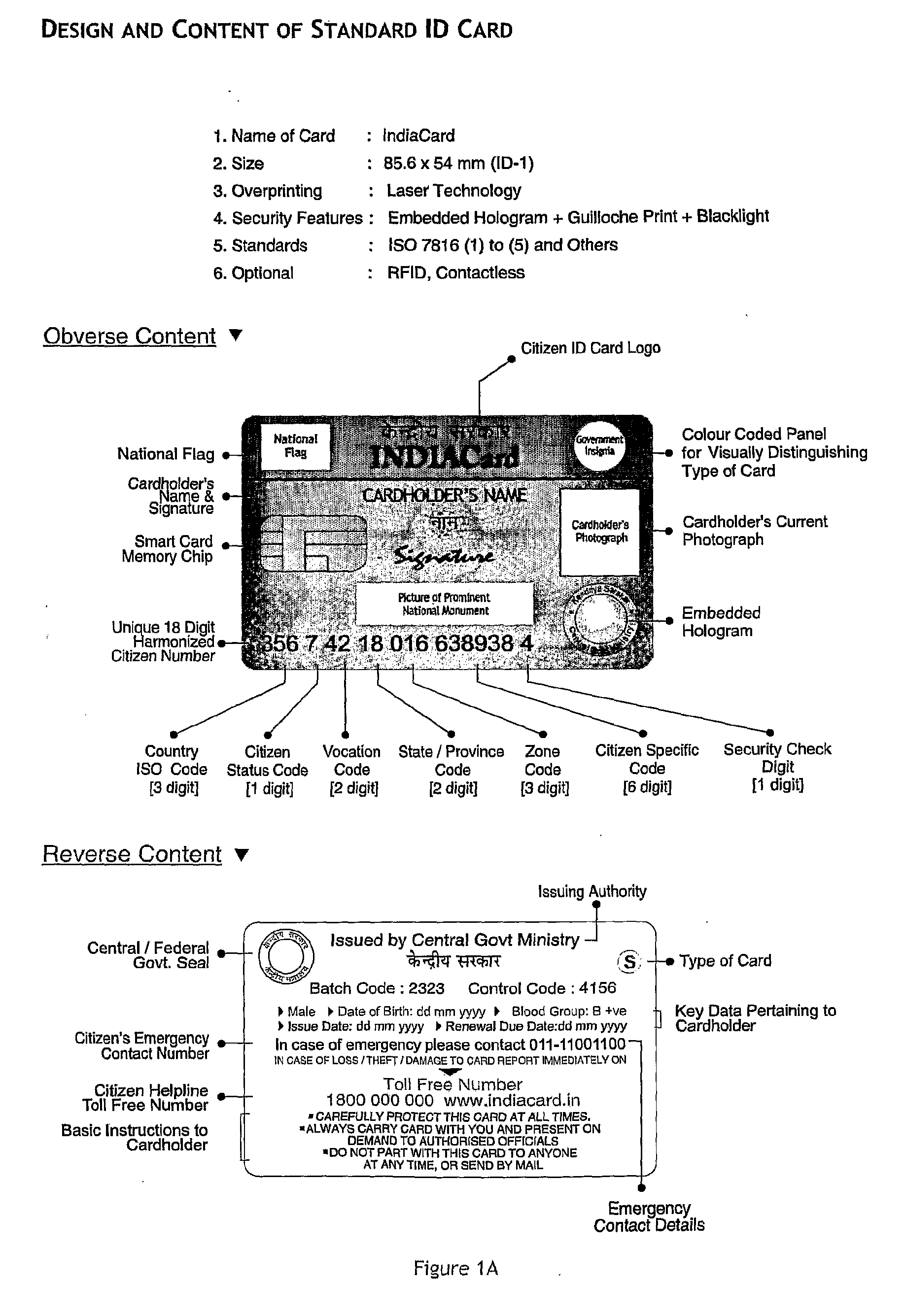
System and method of integrated national citizen identity management and e-governance
InactiveUS20110204142A1Effectively combat crimeEffectively combat terrorismOffice automationResourcesNational levelSmart card
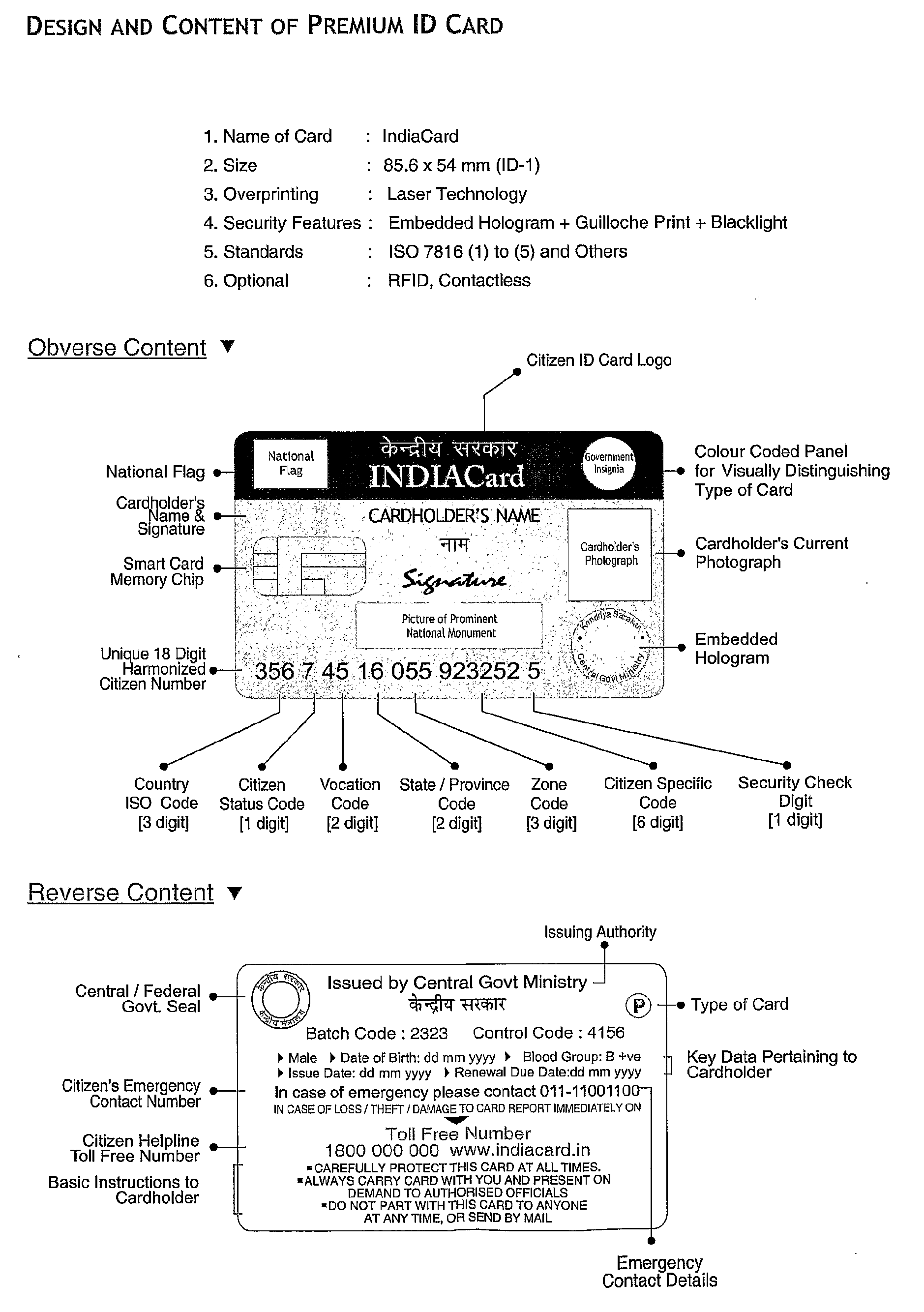
The instant invention relates to an integrated system and method of secure national citizen identity management and e-Governance—known as the CimeGo System®—using as the foundational platform a centralized national-level electronic database of all citizens known as the National Registry (NR) or Central Data Repository (CDR) (containing all relevant data including biometrics in uniquely designed formats, periodically updated) (and also separately for non-citizens) for national level identity management deploying secure smart cards bearing a single, unique scientifically derived identity reference allocated to each citizen valid for the lifetime of the citizen for all applications countrywide, replacing all multiple IDs presently in use. Dedicated India Card Centres (ICCs) across the country serve to rapidly complete citizens' enrolment procedures leading to card issuance and activation. Data stored on the card chip is ported from NR (CDR) and accessed by authorised personnel via card reader units located countrywide. Using the method offered under the instant invention, the NR also serves as the basis for operationalising a modern e-Governance programme with numerous advanced functionalities for efficient, facile bi-directional interaction between citizens versus government and other agencies, spanning a wide range of statutory and non-statutory applications. The Cimego® System facilitates efficient national administration, ensuring compliance by citizens with laid-down laws and national directives. The invention also helps to plan and monitor welfare measures to the populace and to maintain stringent levels of internal security and border regulation by means of the wide ranging actionable inputs and functional capabilities offered by the instant invention.
Owner:RAO CSS
Method and/or apparatus for determining codons
InactiveUS8457903B1Efficiently determinedEfficient identificationBiostatisticsProteomicsData needsClient-side
Computer processing methods and / or systems for minimizing and / or optimizing data strings in accordance with rules and options. Minimized data strings can represent data sequences important in certain biologic analyses and / or syntheses. In specific embodiments, a request is generated by a user at a client system and received by a server system. The server system accesses initial data indicated or provided by the client system. The server system then performs an analysis to minimize the data needed for further reactions. In specific embodiments, a server can use proprietary methods or data at the server side while protecting those proprietary methods and data from access by the client system.
Owner:CODEXIS MAYFLOWER HLDG LLC
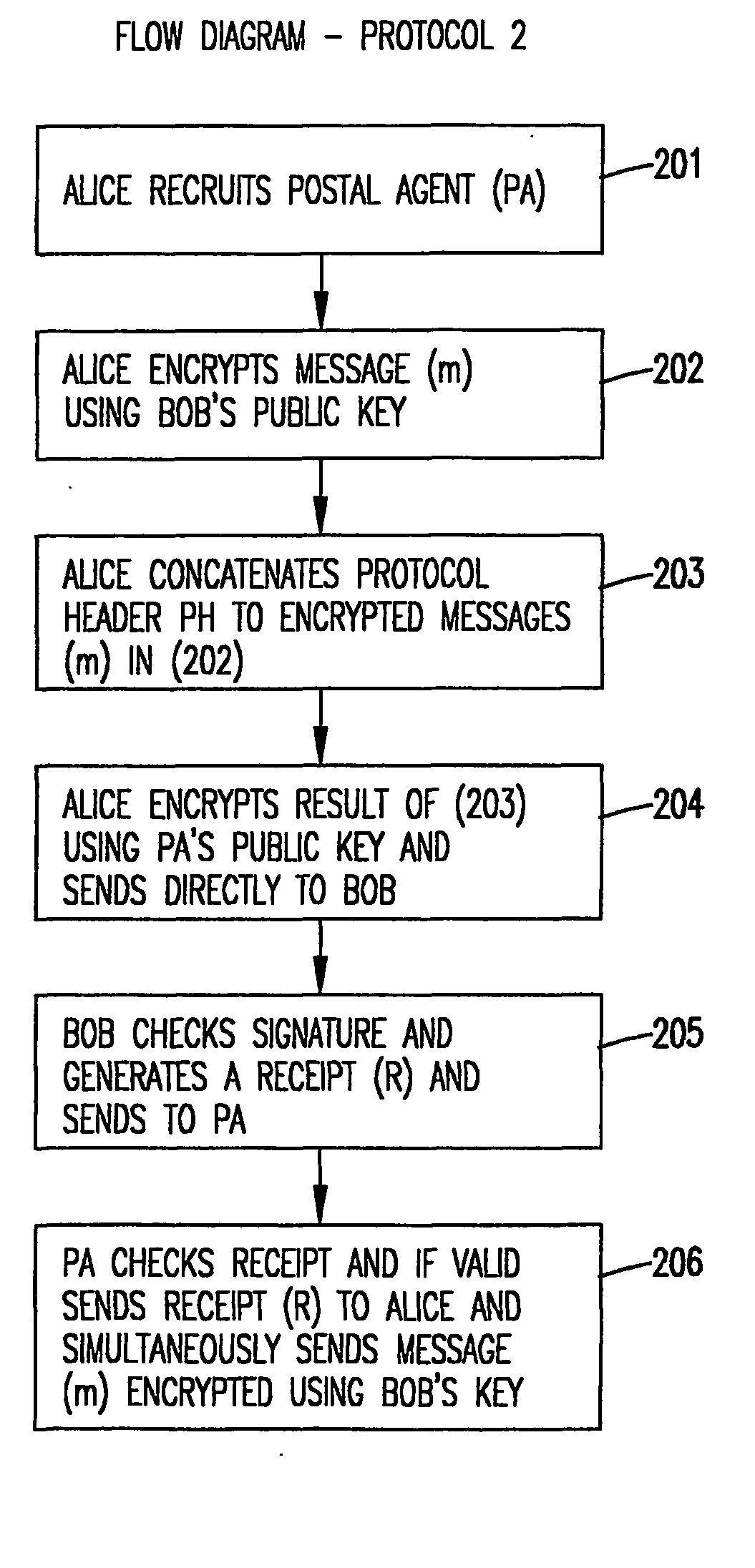
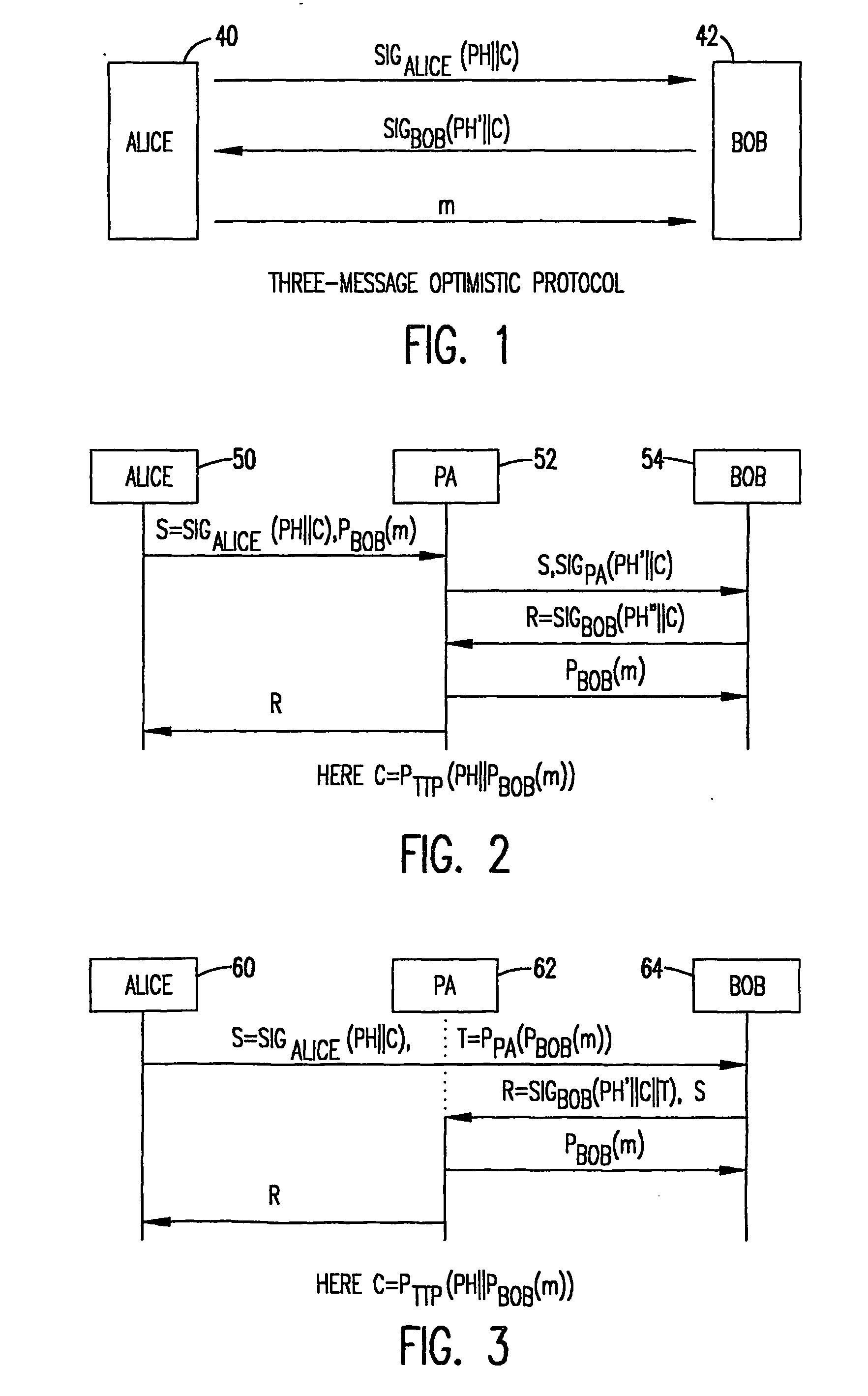
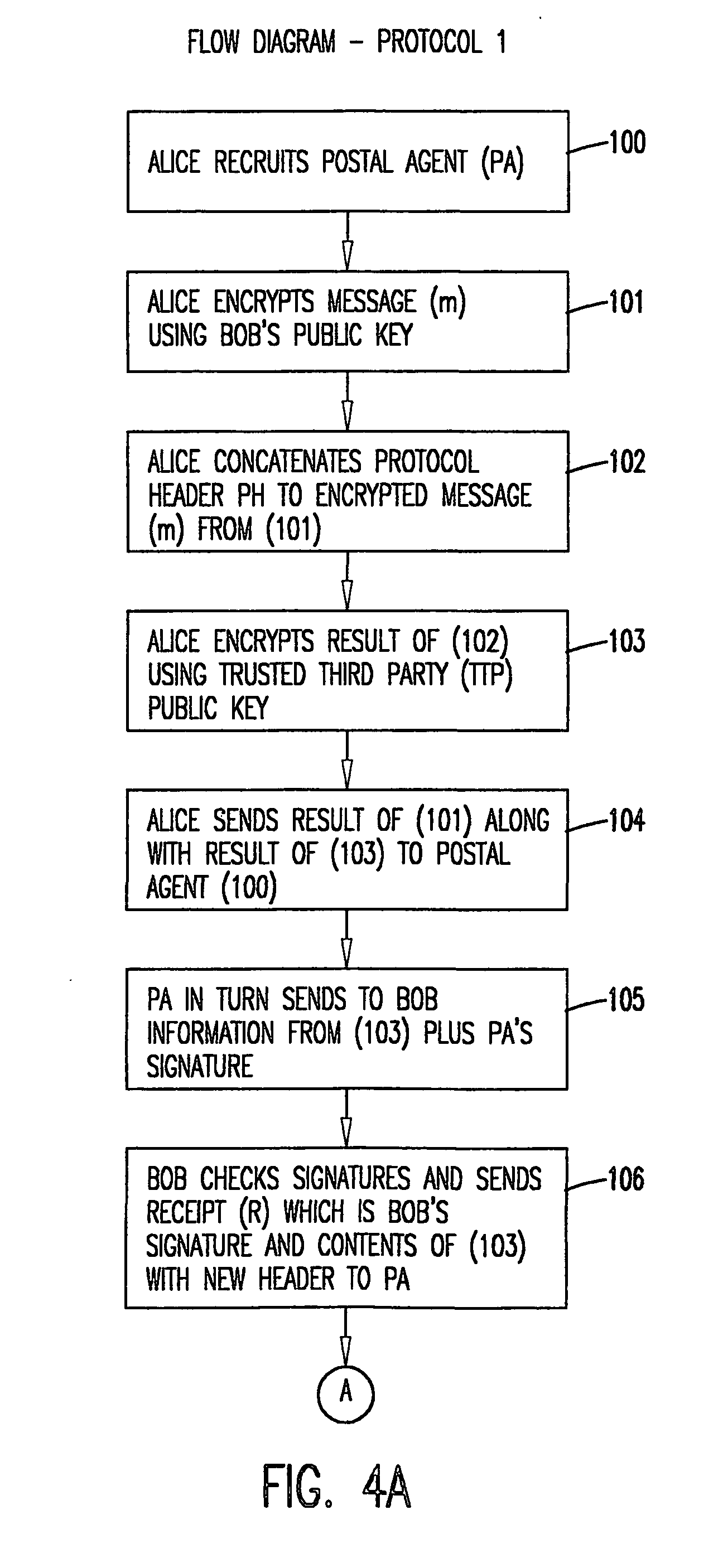
Intermediated delivery scheme for asymmetric fair exchange of electronic items
InactiveUS20040073790A1ConfidenceHard and expensiveKey distribution for secure communicationUser identity/authority verificationElectronic informationAsymmetry
A methodology and system is used to facilitate the exchange of valued electronic information in a confidential, fair, and efficient manner. Either of two protocols can be employed that used encryption and electronic signatures to effectively guarantee origin and identity of sender and receiver in the exchange of valued information and requires timely response by both sender and receiver. The protocols rely upon one or a plurality of postal agents (servers) to provide secured online exchange of the information by arranging an efficient validation of the required signatures and information being exchanged between the sender and receiver. In the event of a breakdown in the exchange between sender and receiver, the use of a trusted third party (TTP) allows for fair and pre-agreed arbitration based upon the encrypted information and electronic signatures of the sender and receiver. The method does not require the use of the TTP unless a dispute arises.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
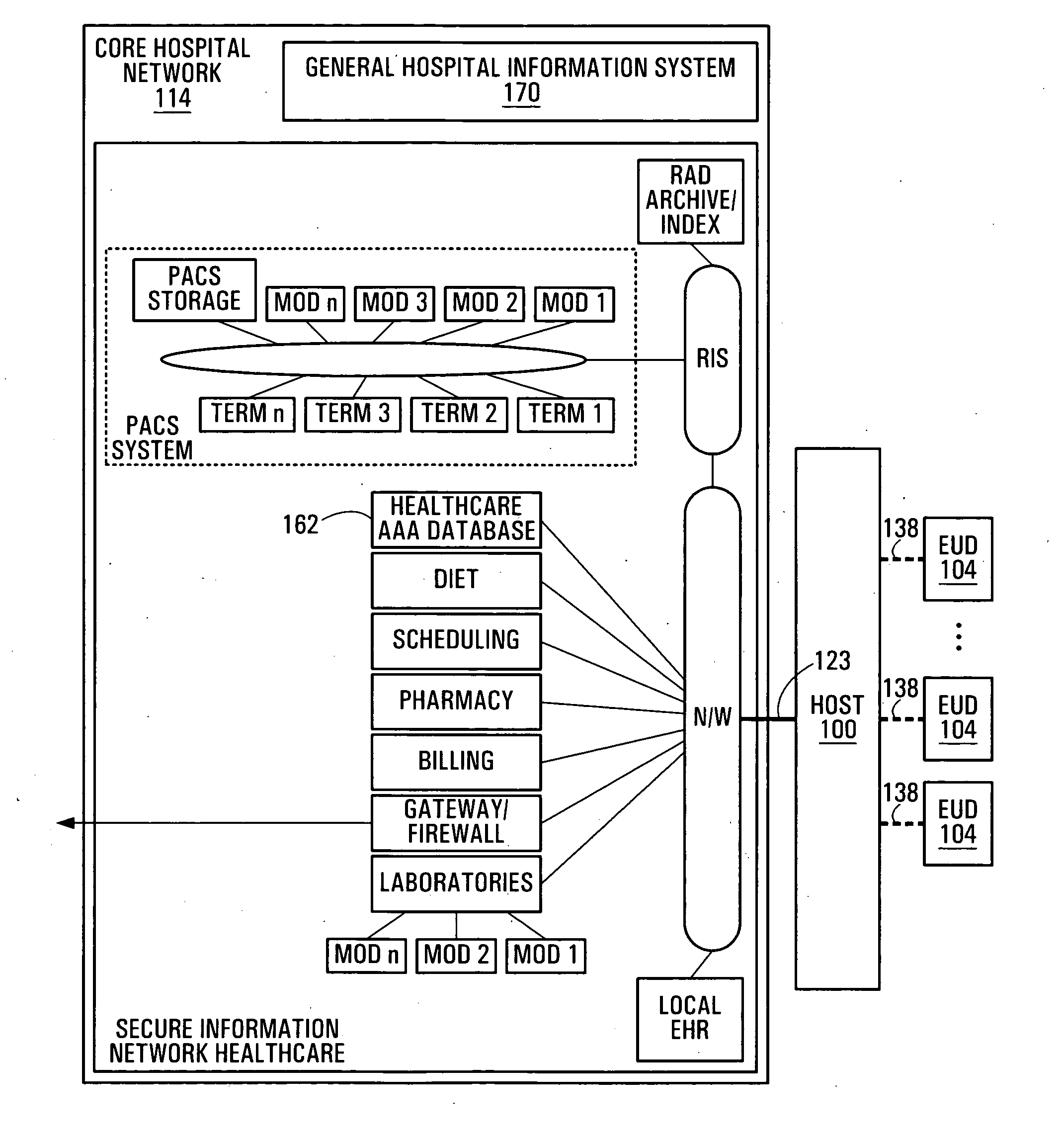
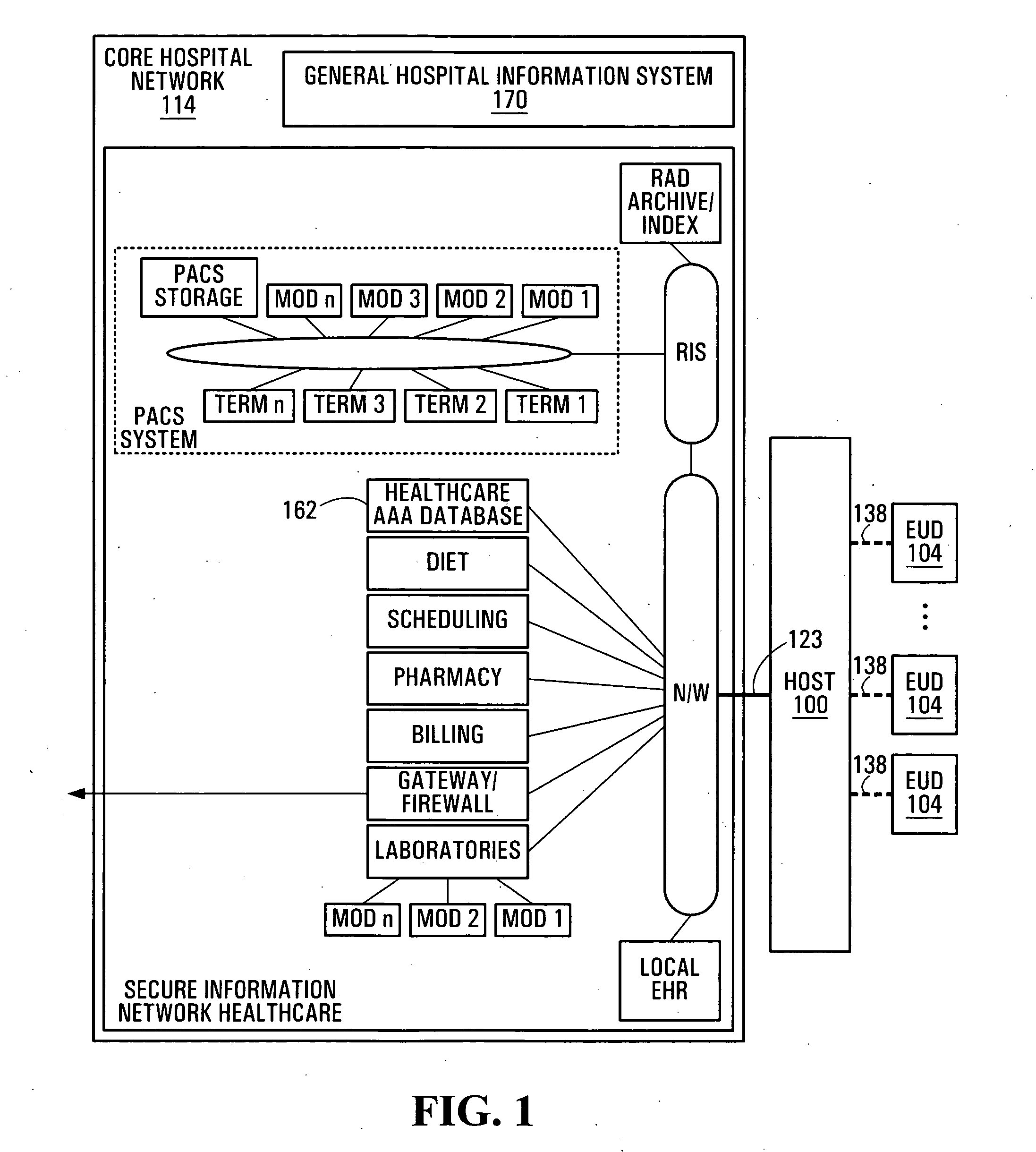
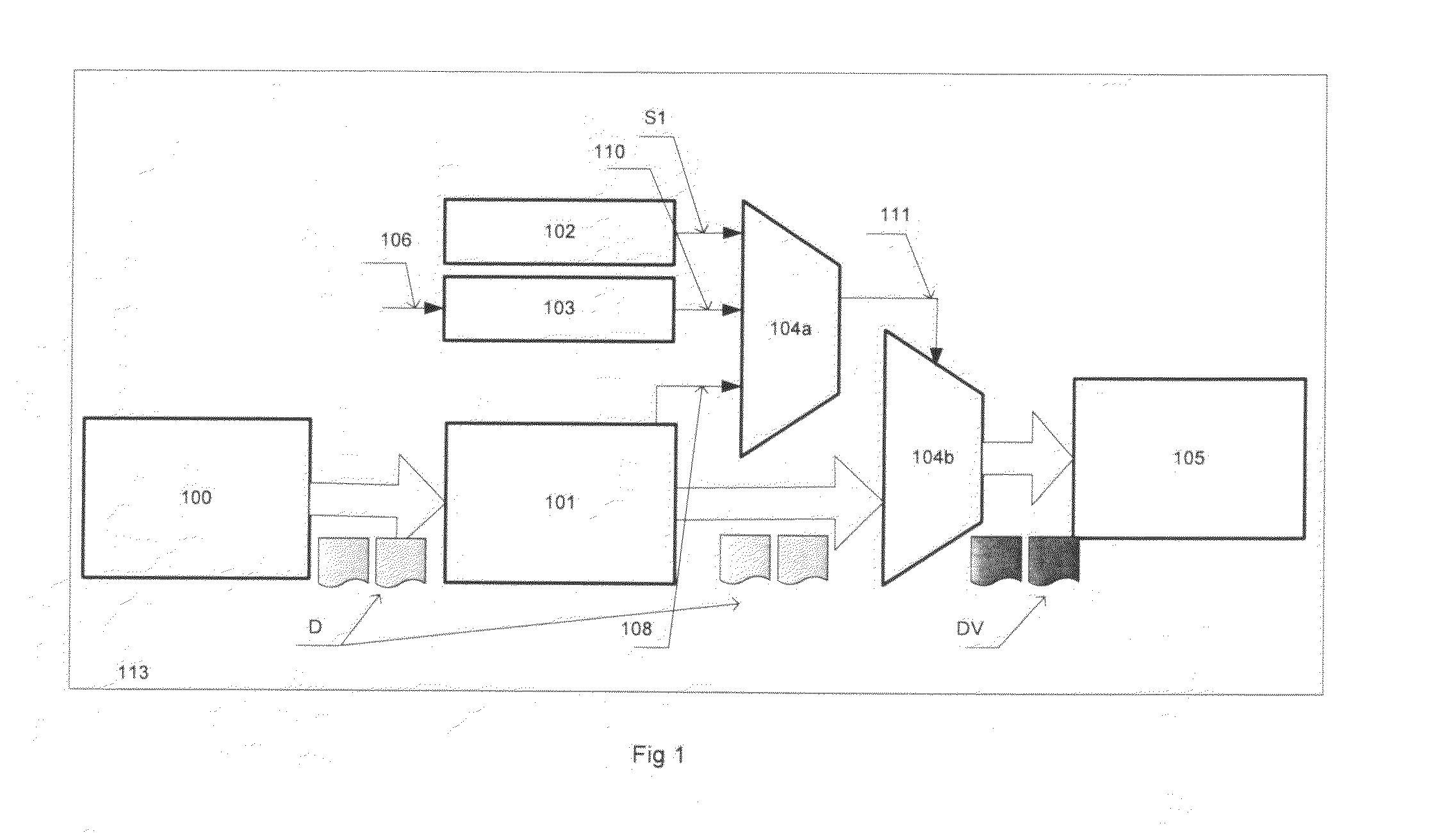
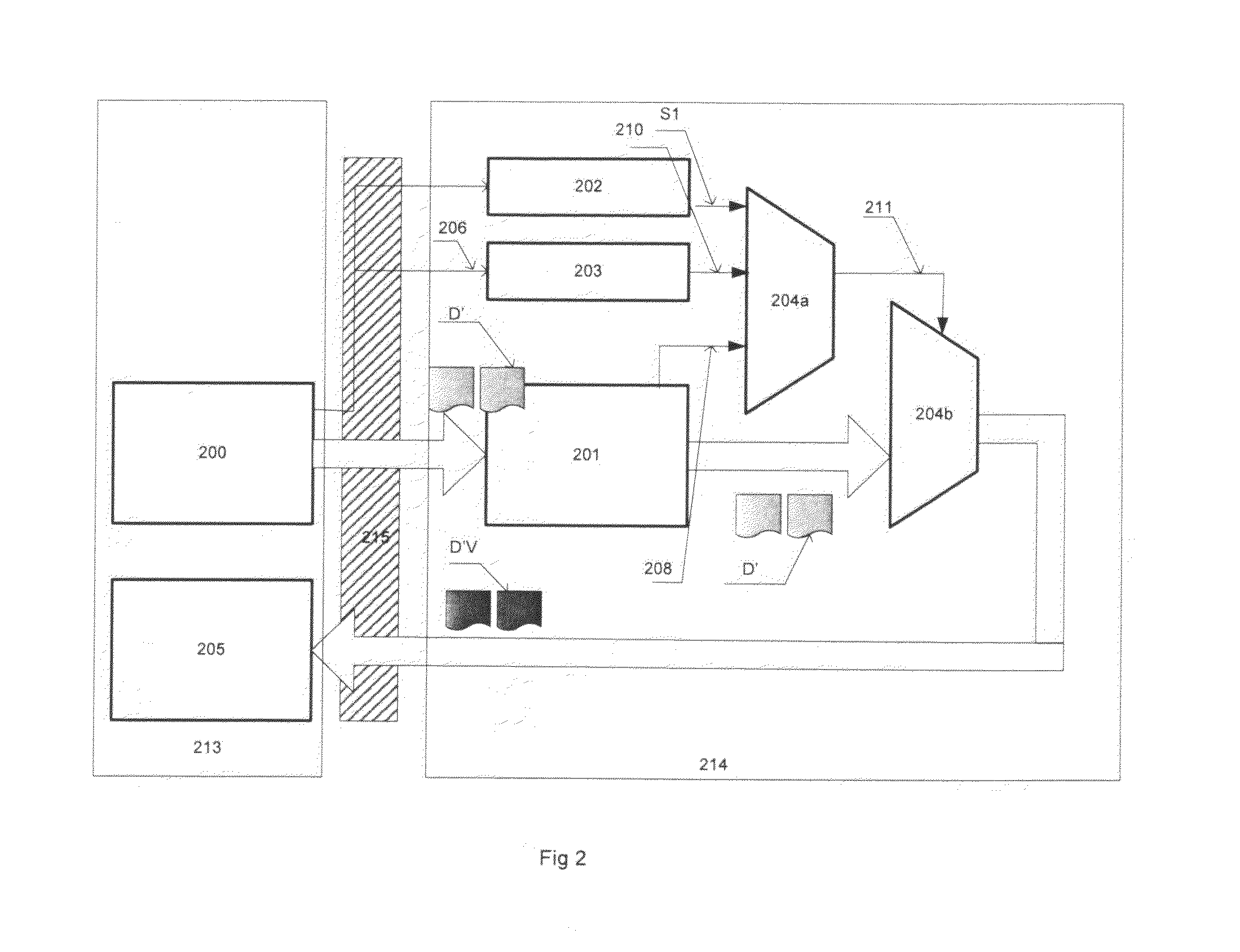
Systems and methods for preserving confidentiality of sensitive information in a point-of-care communications environment
ActiveUS20050223222A1Preserving confidentialityKey distribution for secure communicationUser identity/authority verificationComputer hardwareConfidentiality
A data processing apparatus comprises a memory store; a data bus connected to the memory store, the data bus being adapted for transporting data to and from the memory store; a processing entity operative to release read and write commands towards the memory store, the write command being accompanied by first data intended to be written to the memory store; and an encryption module communicatively coupled to the processing entity and to the data bus. Upon the processing entity releasing a write command accompanied by said first data, the encryption module encrypts, in accordance with an encryption key, said first data and send an encrypted version of said first data onto the data bus for writing into the memory store. The reverse operation is performed upon the processing entity releasing a read command.
Owner:AVAYA INC
System and method for retrieving computed paths from a path computation element using encrypted objects
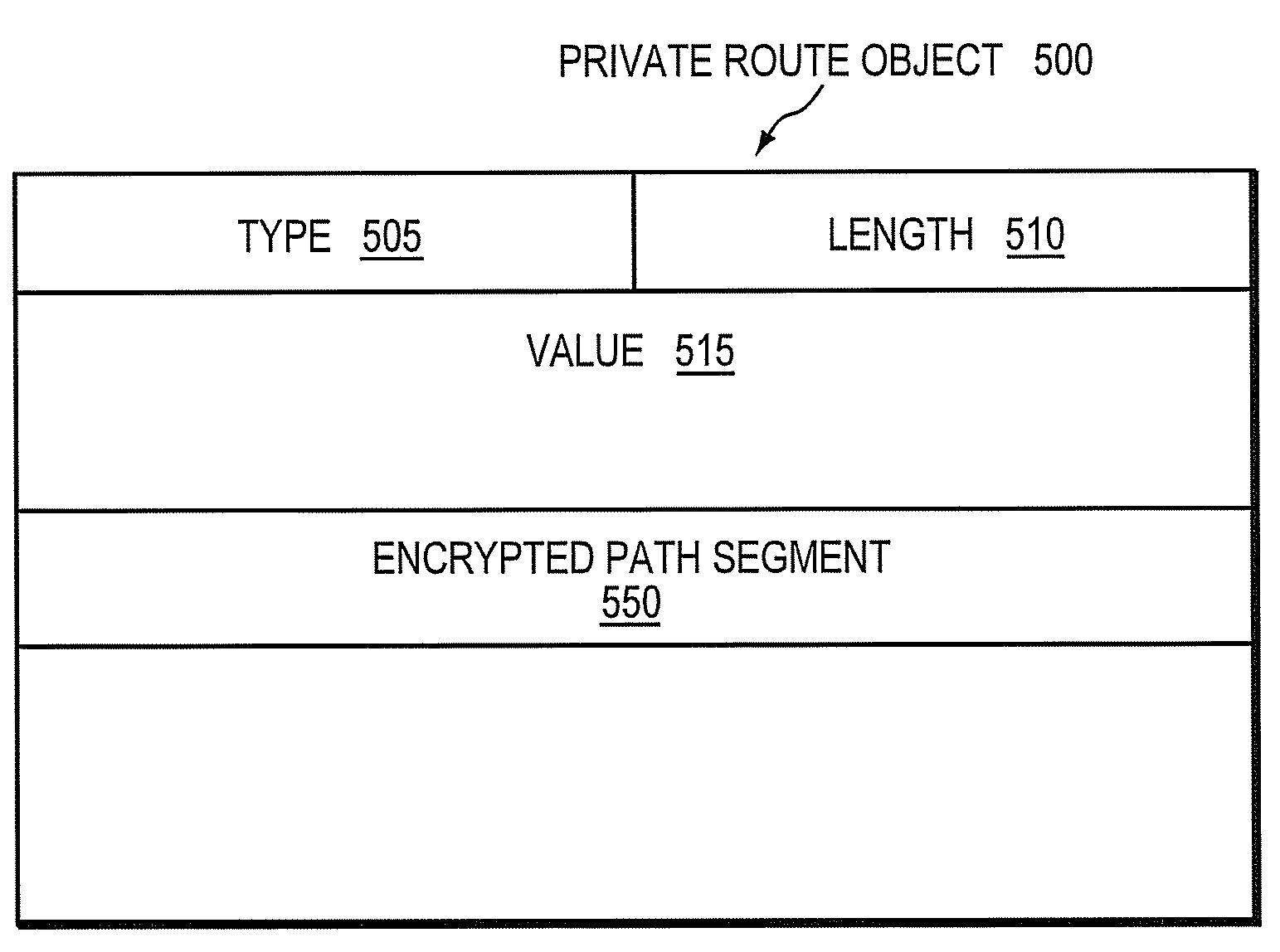
InactiveUS20060098587A1Computationally efficientPreserving confidentialityError preventionTransmission systemsConfidentialityPath computation element
A technique retrieves computed path segments across one or more domains of a computer network in accordance with a stateless Path Computation Element (PCE) model. The stateless PCE model includes one or more PCEs configured to compute one or more path segments through the domains in response to a path computation request issued by, e.g., a Path Computation Client (PCC). Notably, each computed path segment is encrypted as a data structure to preserve confidentiality across the domains. Each PCE then cooperates to return a path computation response, including the encrypted path segments and an explicit route object (ERO) containing compressed path descriptions of the computed path segments, to the PCC.
Owner:CISCO TECH INC
Ascending bid auction for multiple auctions
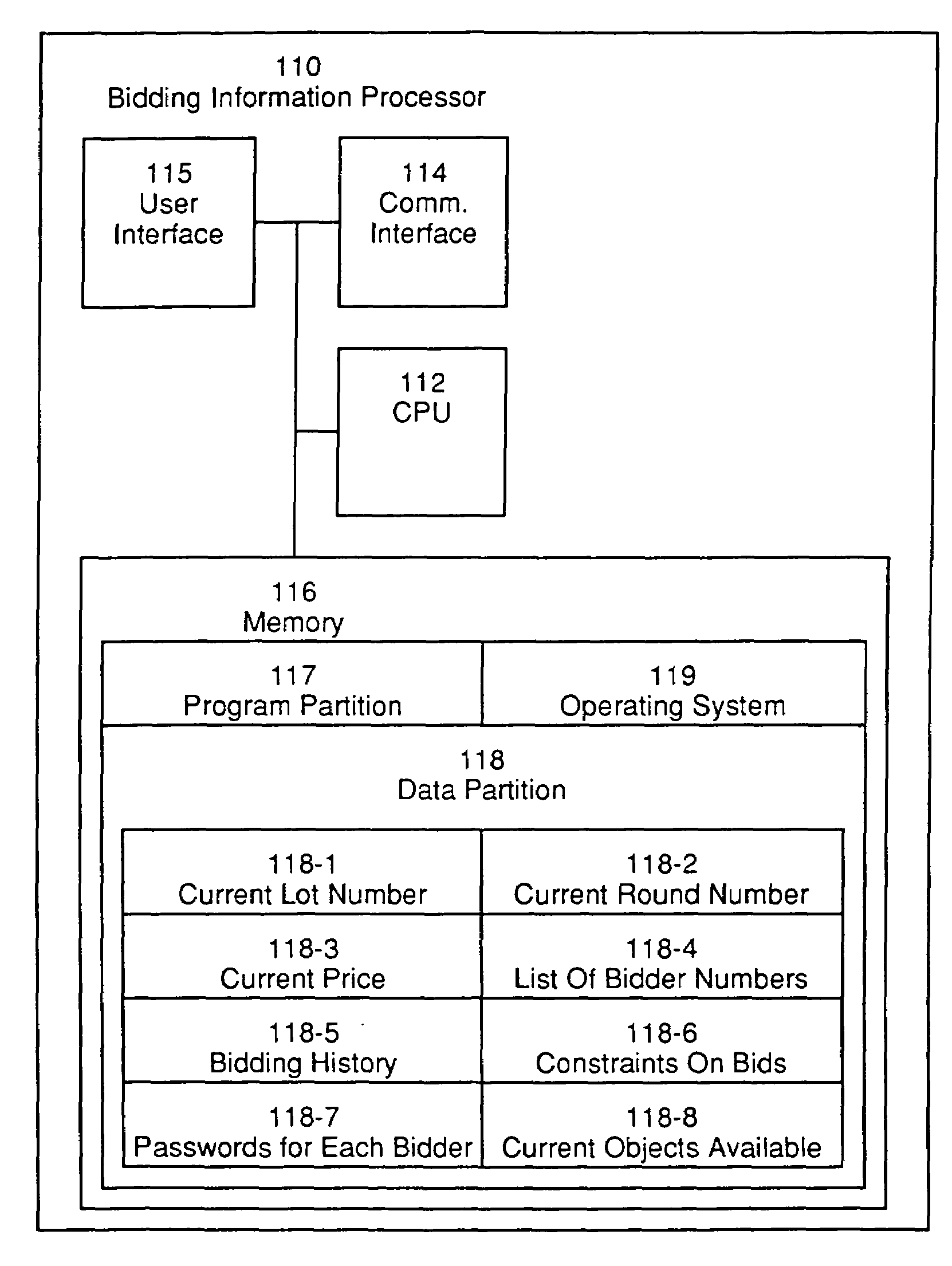
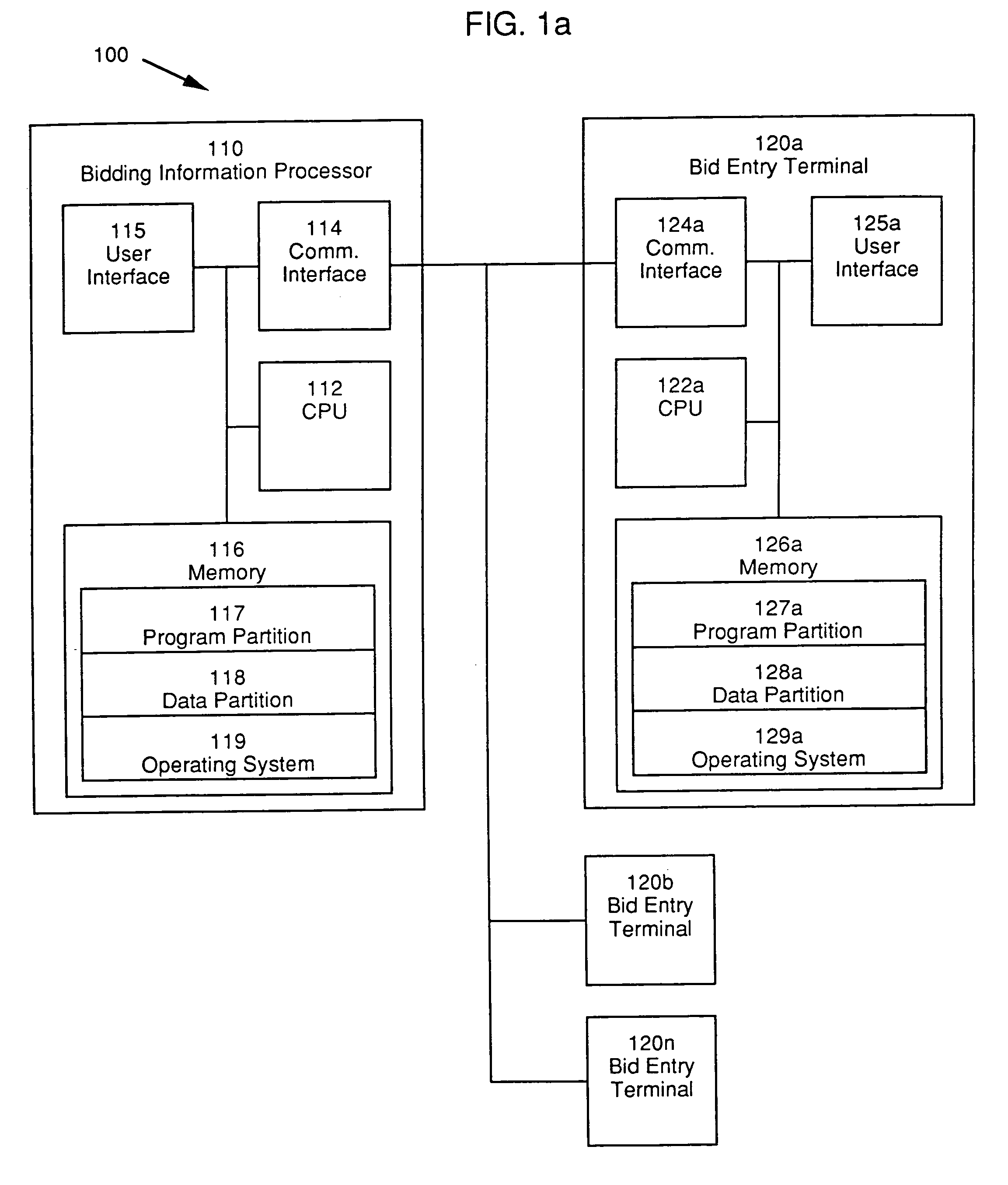
InactiveUS7337139B1Economical efficiency can be improvedImprove confidentialitySpecial service provision for substationFinanceOperational systemConfidentiality
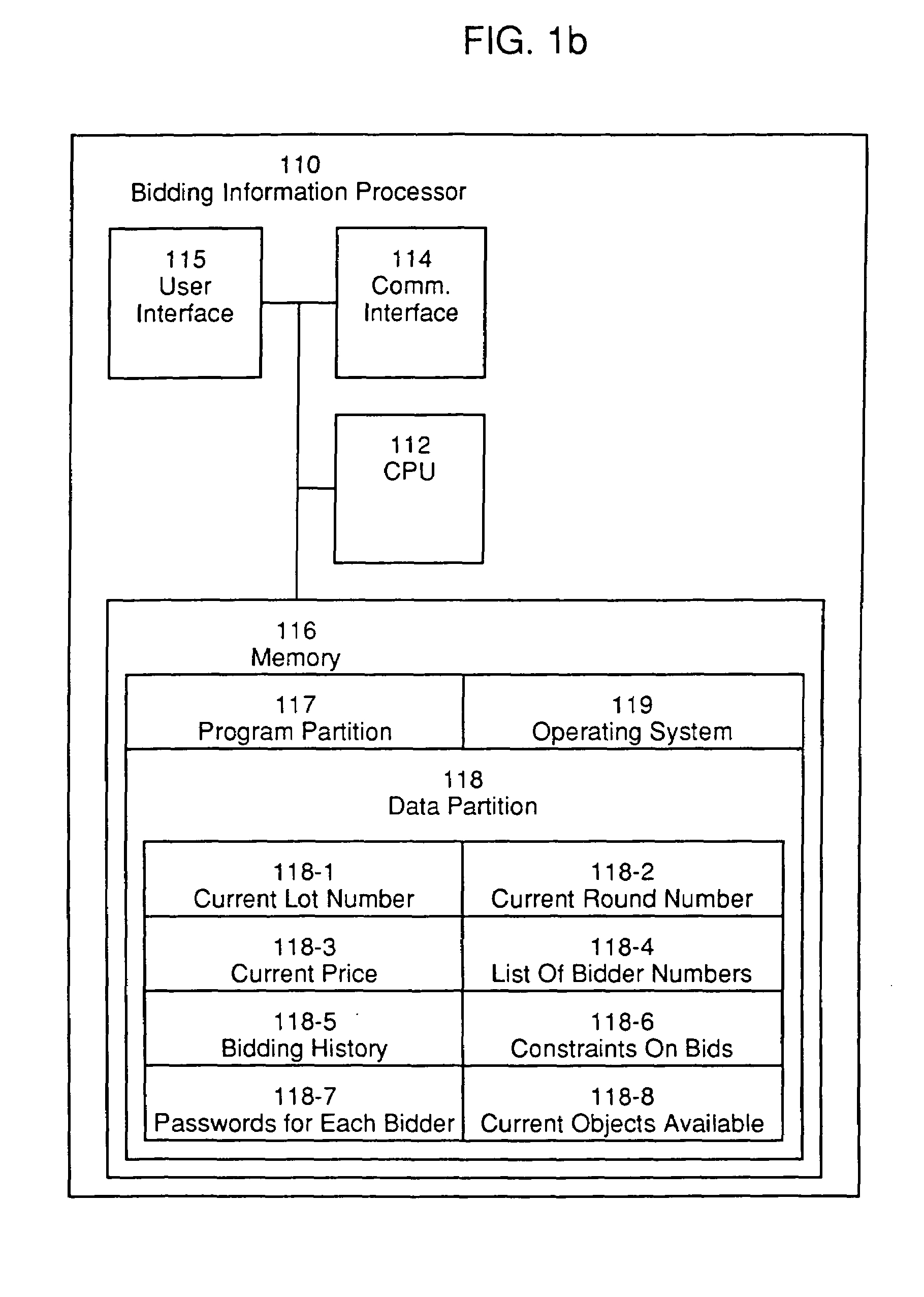
An automated system for conducting an auction and a method for operating the system. The system comprises a plurality of bid entry terminal and a bidding information processor communicatively coupled to the bid entry terminals. Bidders at the bid entry terminals observe displayed information and enter bids accordingly. The bidding information processor and the bid entry terminals communicate and process information in order to conduct an auction. The method involves conducting an auction in which the price paid by bidders is independent of their own bids, in which participants are provided with information concerning their competitors' bids as the auction progresses, and in which the confidentiality of high values is maintained. This provides the advantage of improving the economic efficiency of the auction design over the existing art.
Owner:EFFICIENT AUCTIONS
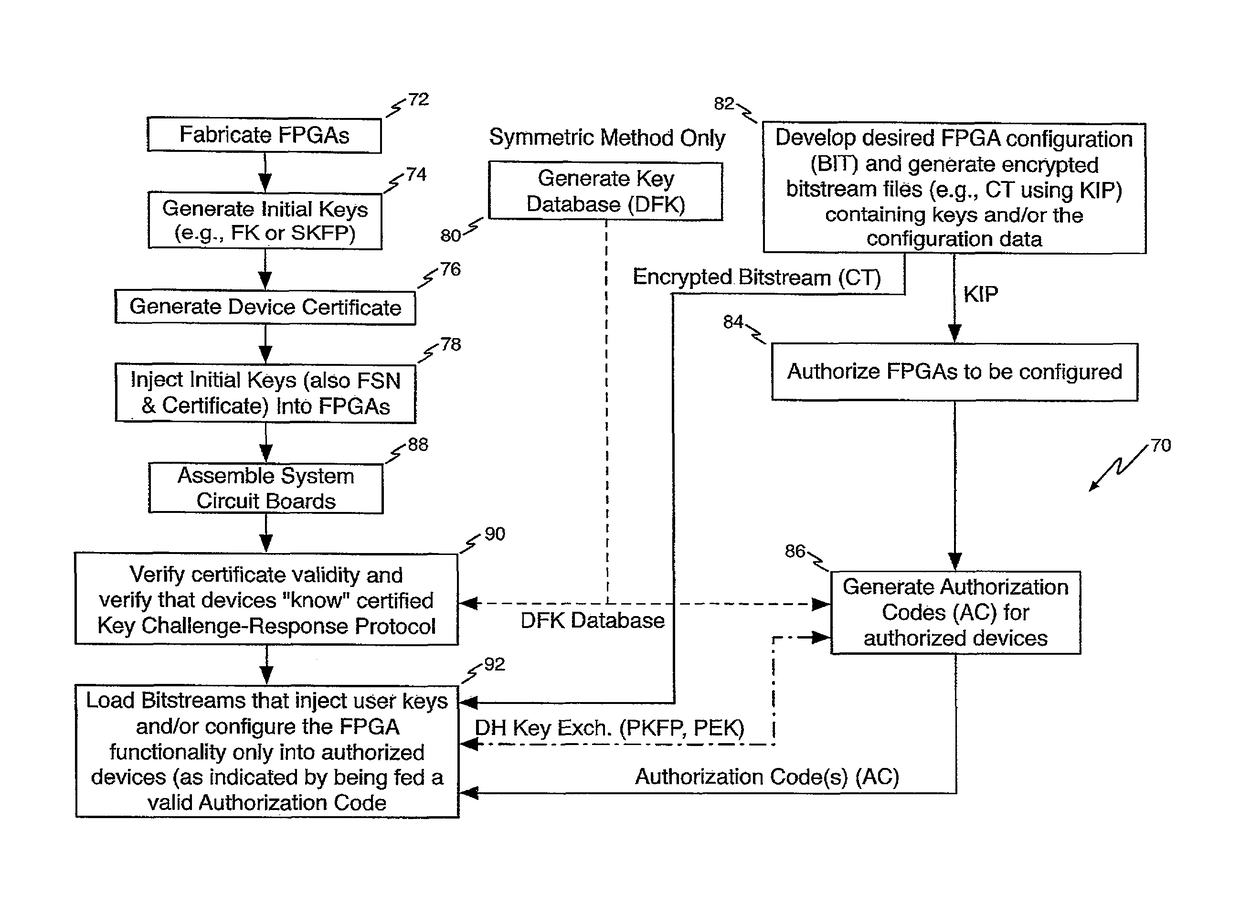
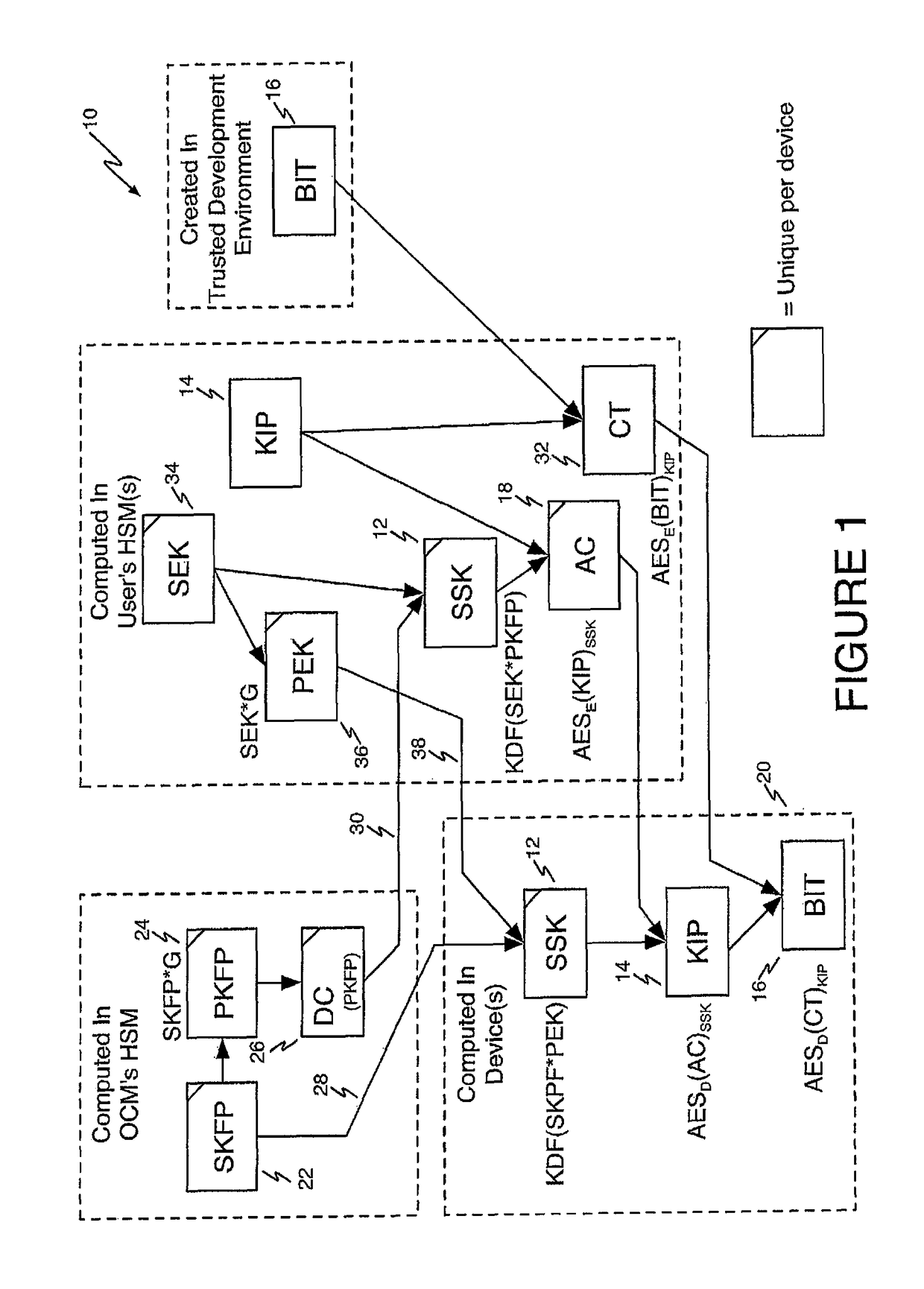
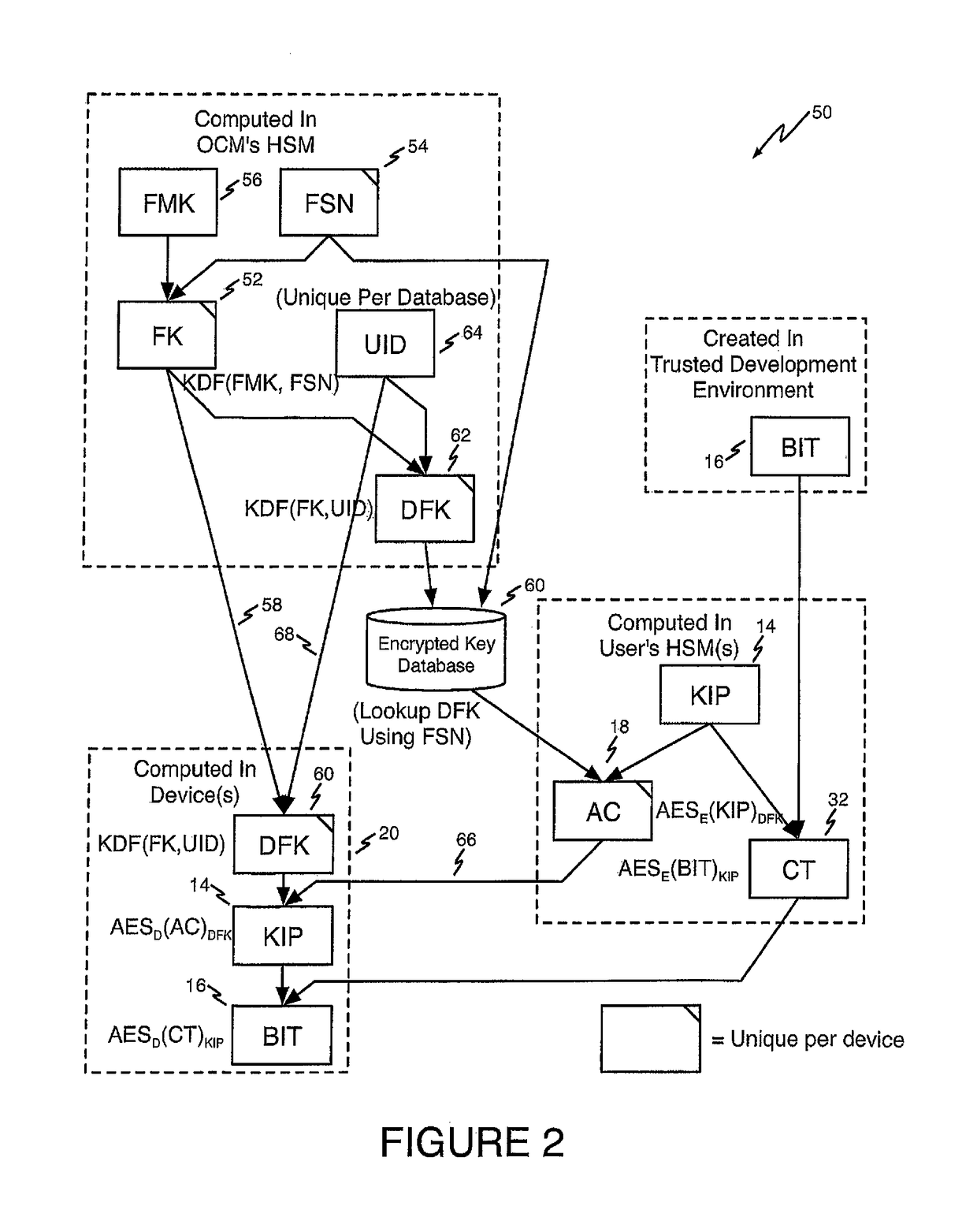
Method of Improving FPGA Security Using Authorization Codes
ActiveUS20150100793A1Protect the loadPreventing overbuildingUser identity/authority verificationUnauthorized memory use protectionAuthorizationOperating system
A method for securely programming a population of authorized FPGAs includes defining the population of authorized FPGAs, generating an encrypted configuration bitstream for the population of authorized FPGAs, generating an individual Authorization Code for each FPGA in the population of authorized FPGAs, feeding the individual Authorization Codes into the FPGAs in the population of FPGAs, feeding the encrypted configuration bitstream into all of the FPGAs in the population of FPGAs, and in each FPGA using the Authorization Code to decrypt the encrypted configuration bitstream to program the FPGA.
Owner:AYRLETT +1
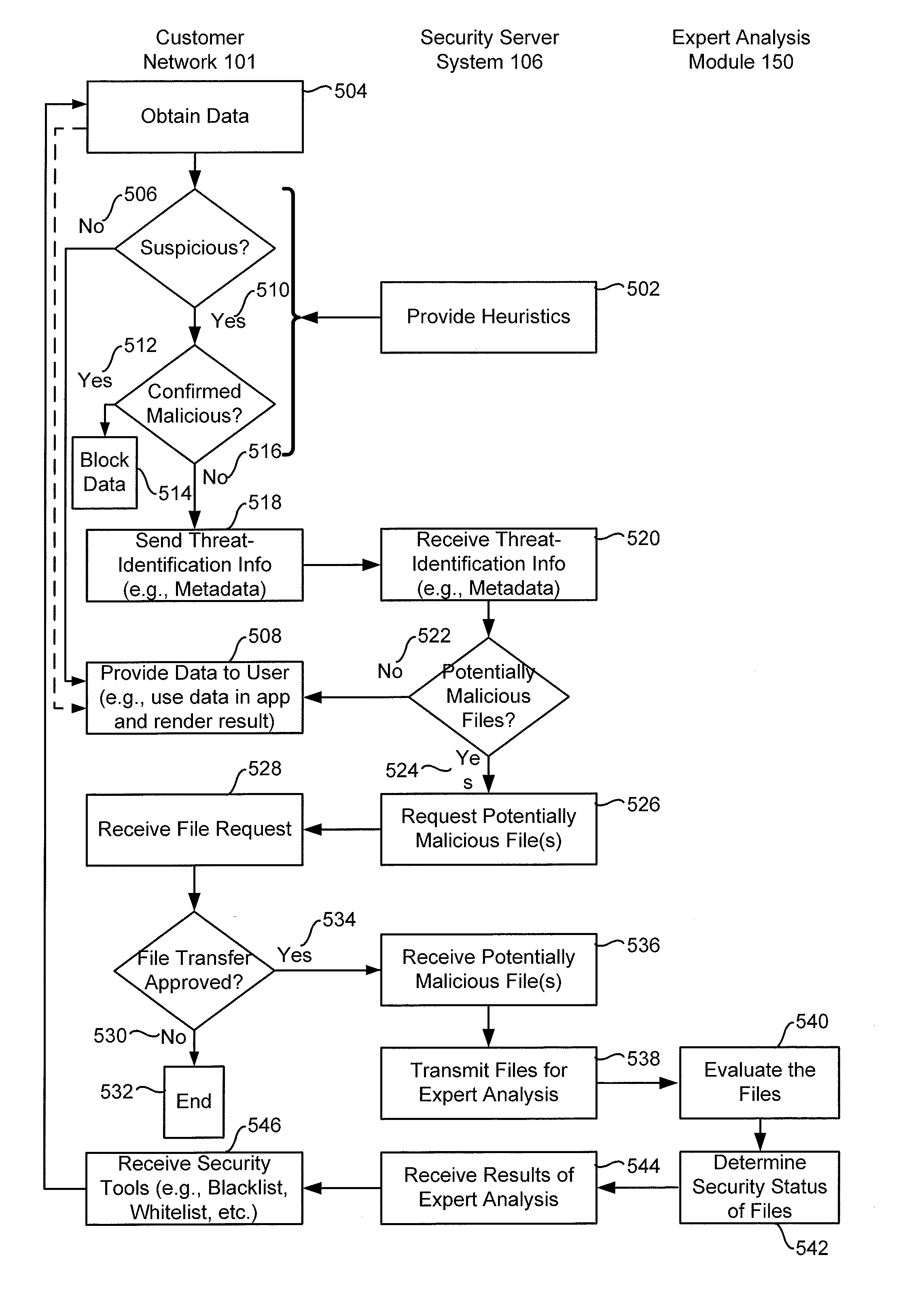
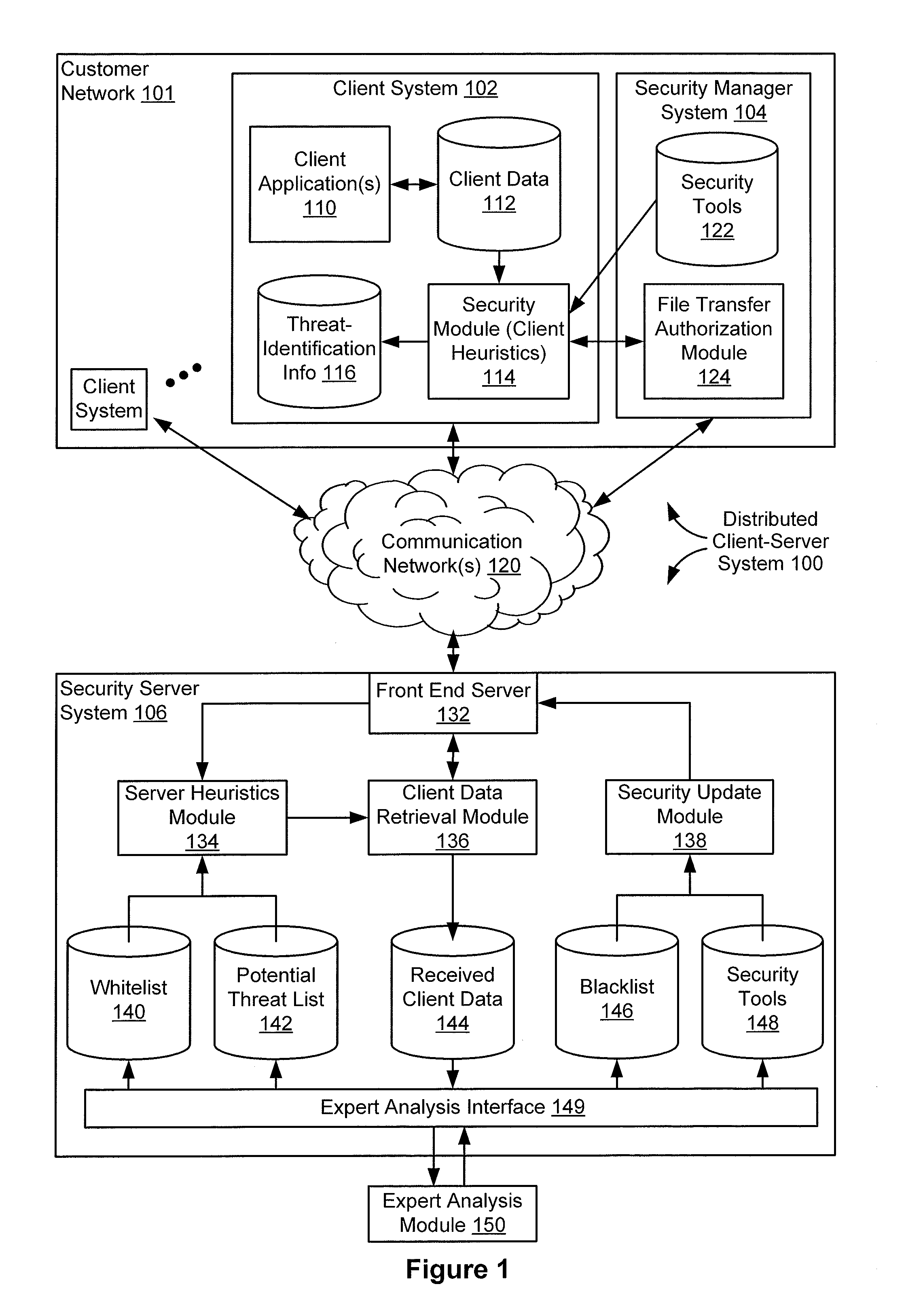
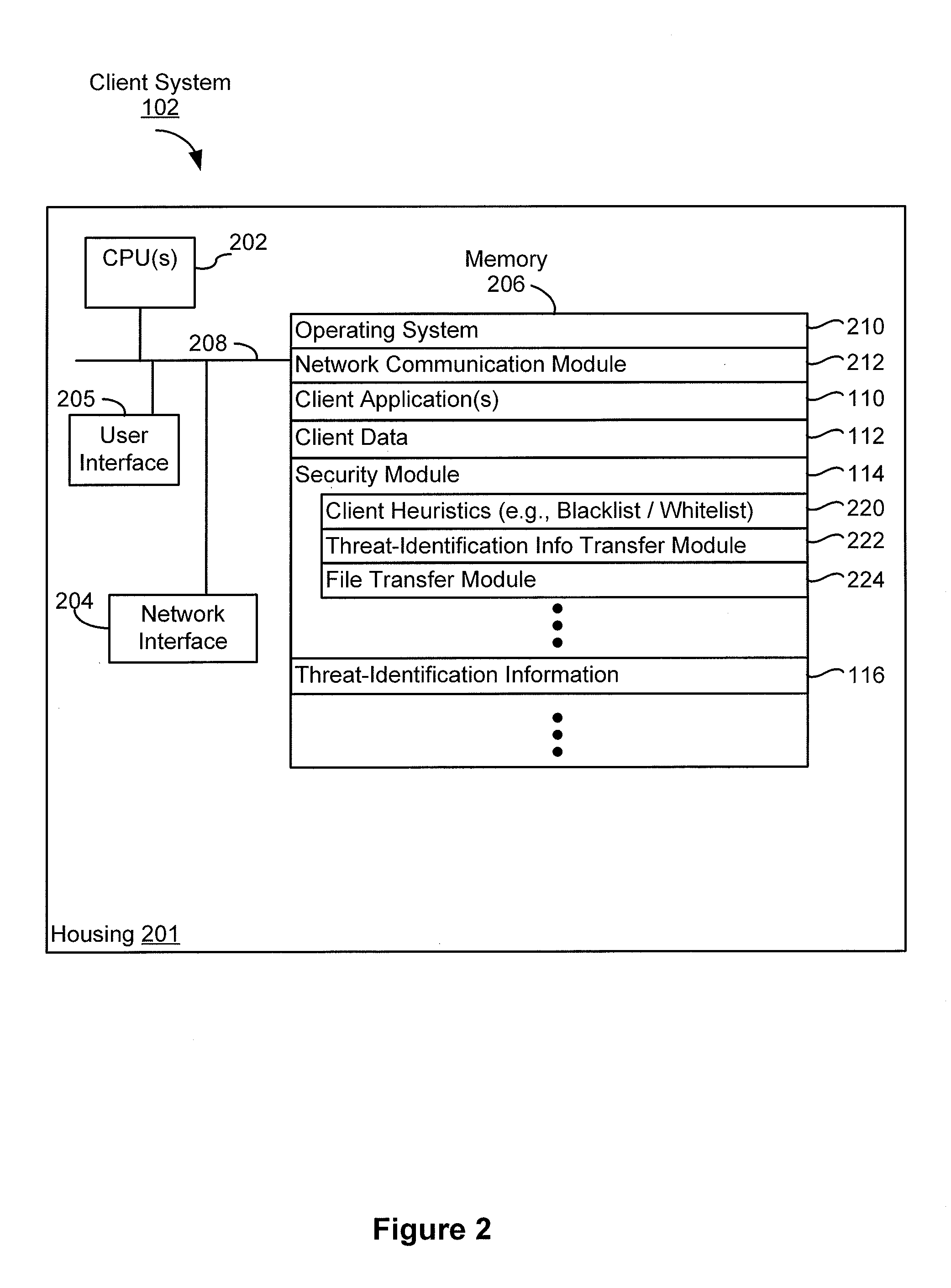
Determining a security status of potentially malicious files
ActiveUS8739287B1Time for detection become longLong response timeMemory loss protectionError detection/correctionConfidentialityAuthorization
A server system that includes one or more processors and memory receives, from a client, metadata for a plurality of suspicious files for which the client was unable to conclusively determine a security status. The server system also analyzes the metadata using threat-identification information to identify potentially malicious files and requests authorization to receive the potentially malicious files from the client. In response to the request, upon authorization for the server system to receive the potentially malicious files, the server system automatically receives one or more potentially malicious files from the client that were authorized based on a confidentiality level of the potentially malicious files. After receiving the one or more potentially malicious files, the server system analyzes the potentially malicious files using threat-identification information available at the server system and provides, to the client, an indication of the security status of the one or more potentially malicious files.
Owner:AO KASPERSKY LAB
Process and apparatus for automatic retrieval from a database and for automatic enhancement of such database
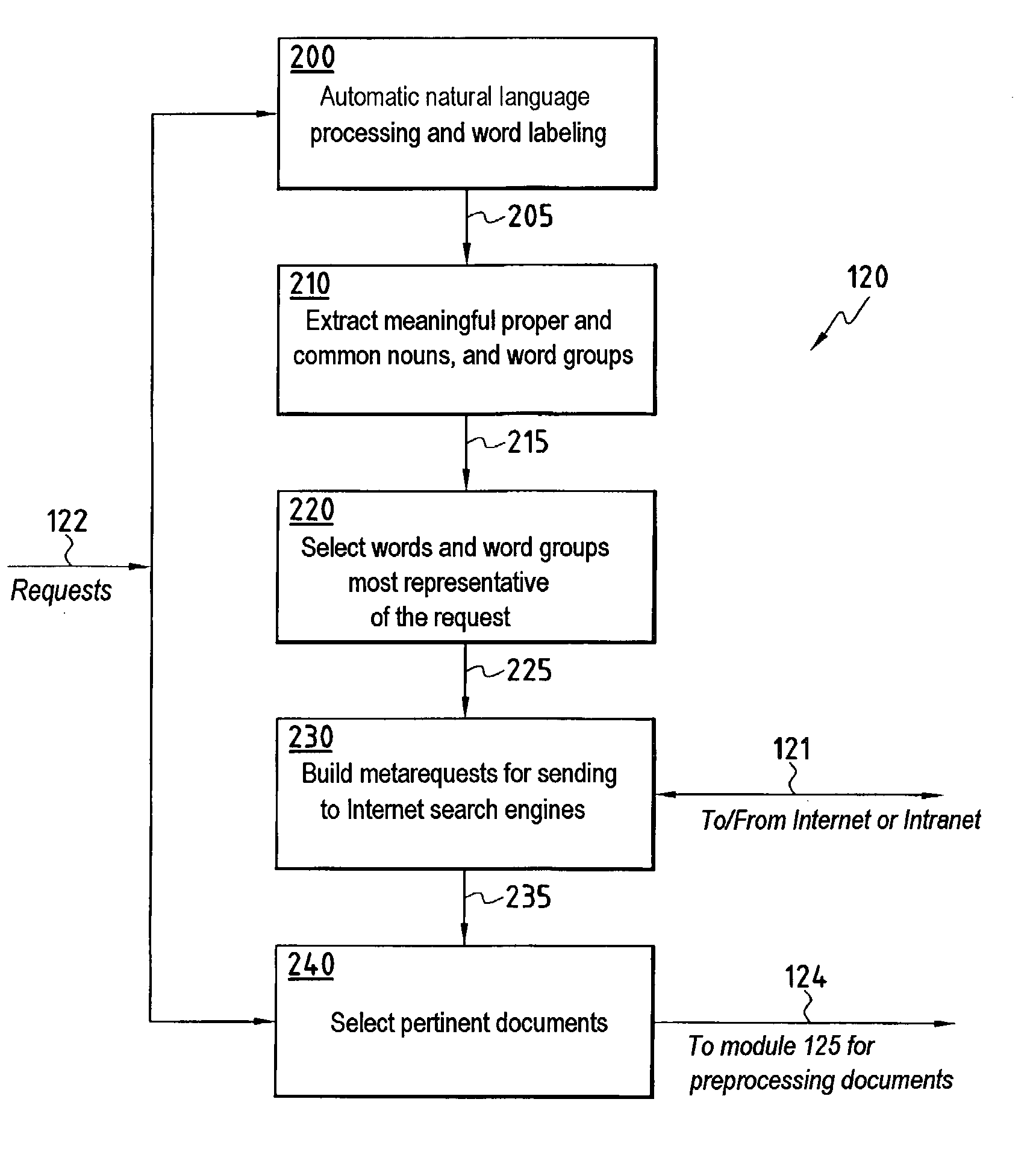
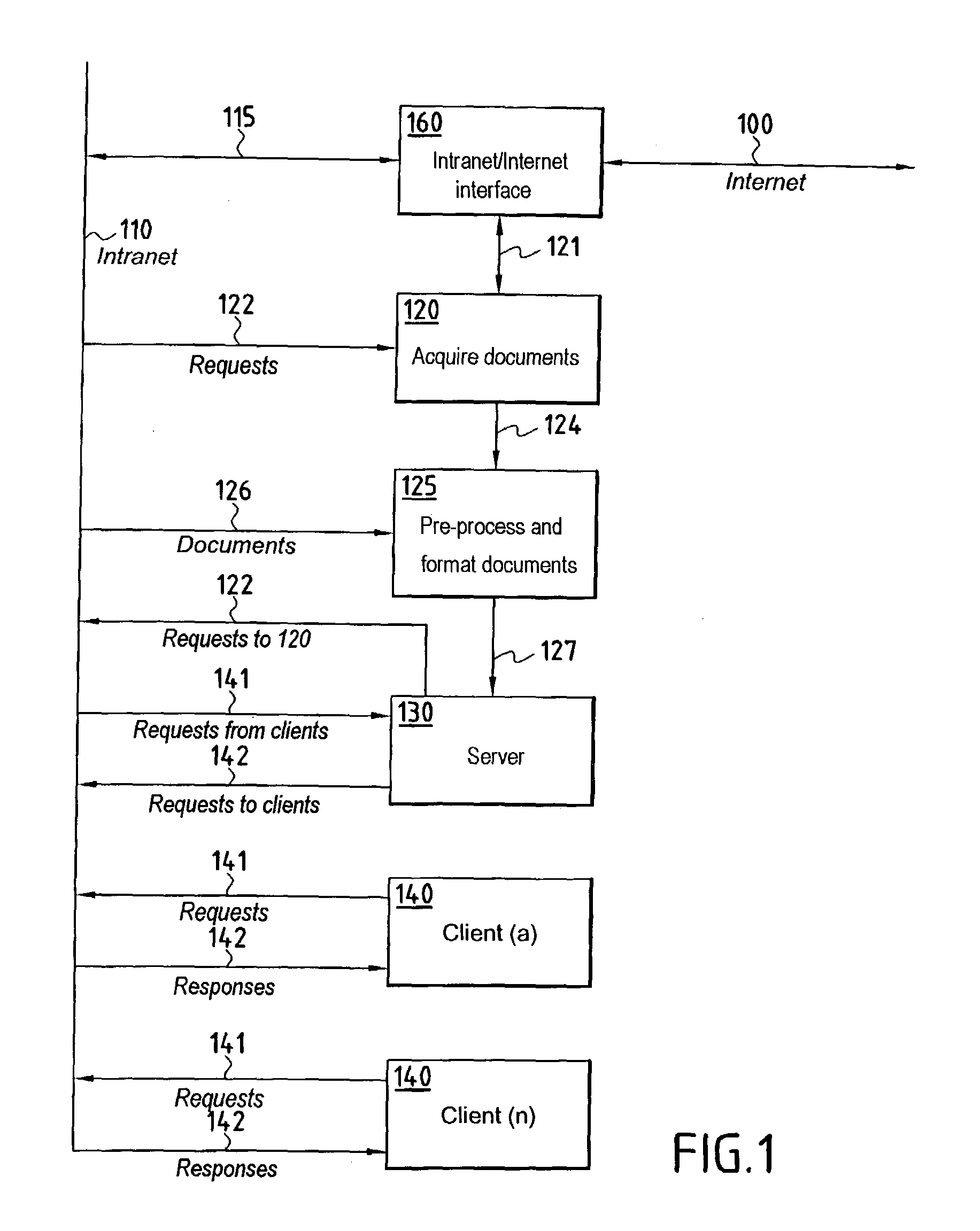
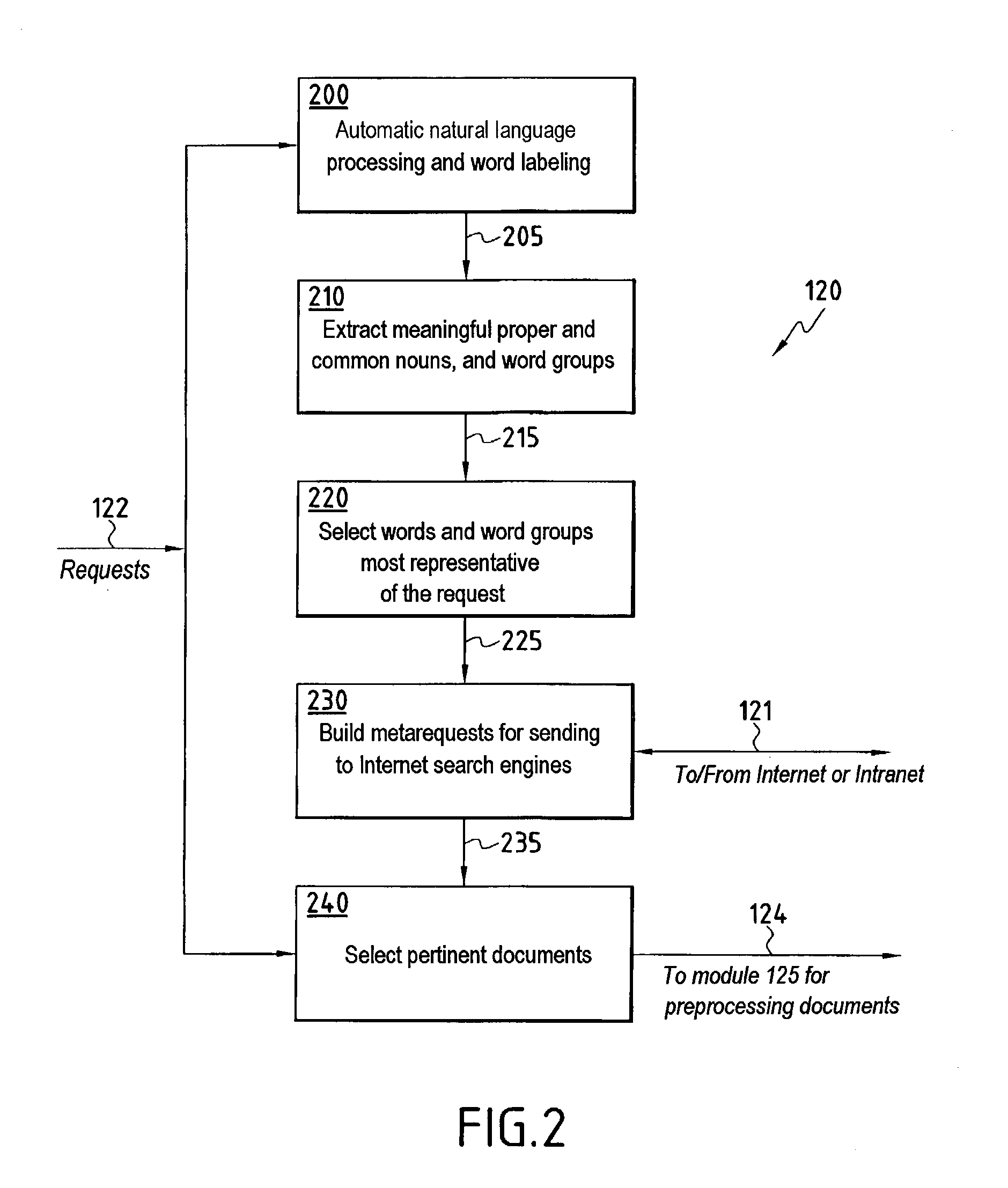
InactiveUS20030204500A1Easy accessSimple systemWeb data indexingSpecial data processing applicationsInformation searchingDocumentation
The system comprises an interface for acquiring an initial request in natural language, which request is sent to a server of a main database, a storage memory for storing information searching methods, specialized modules for implementing searching methods, a module for responding to the initial request to produce metarequests, said module comprising a unit for extracting the most meaningful words or expressions from the initial request, a search engine for accessing an additional database, a unit for processing the metarequests in order to adapt them to the search engine, a unit for sending the processed metarequests to the search engine giving access to the additional database in order to obtain additional documents corresponding to the initial request, and a unit for transmitting additional documents to the specialized module for processing and formatting which then transmits processed and formatted information to the server in order to enrich the main database.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES +1
System and method for retrieving computed paths from a path computation element using encrypted objects
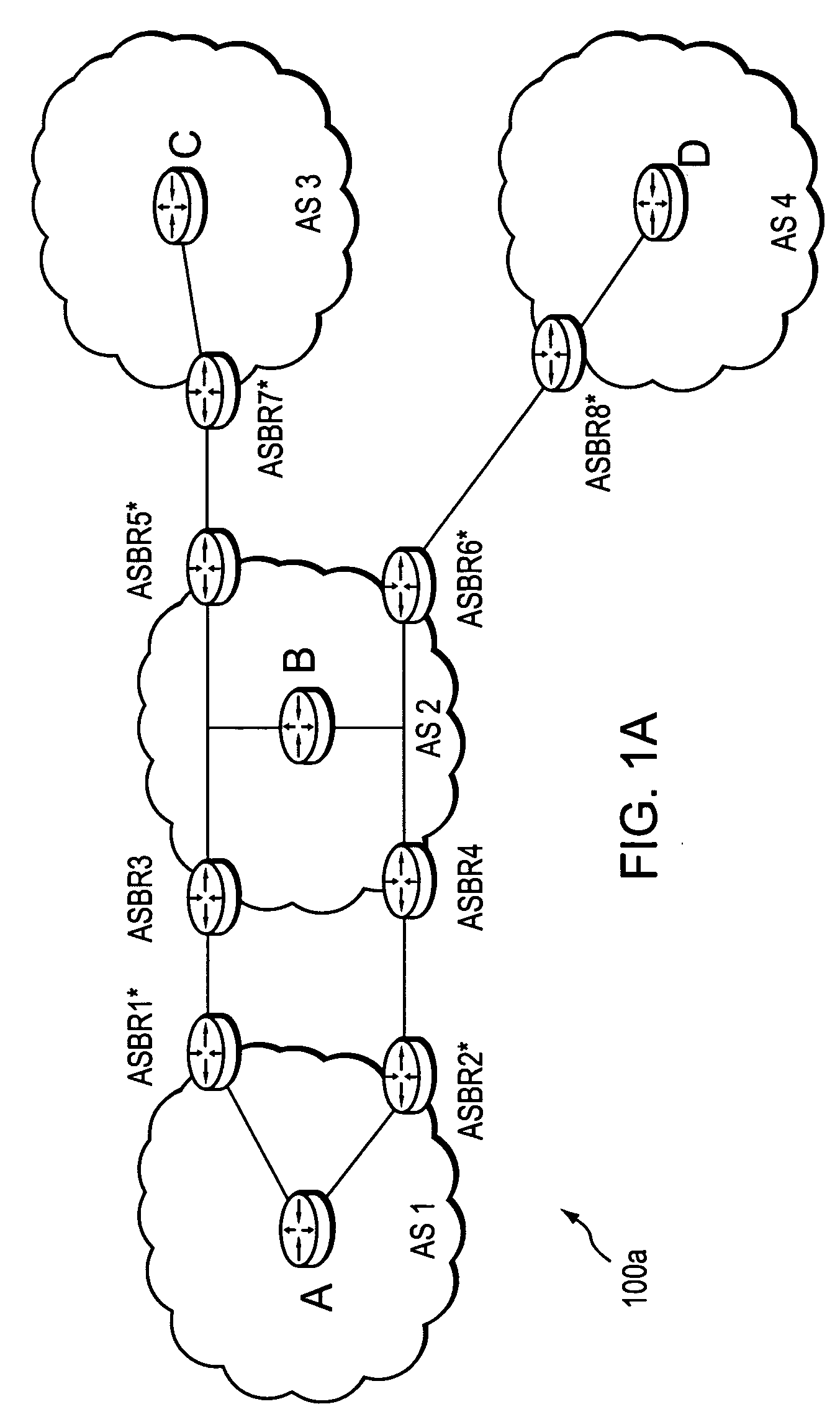
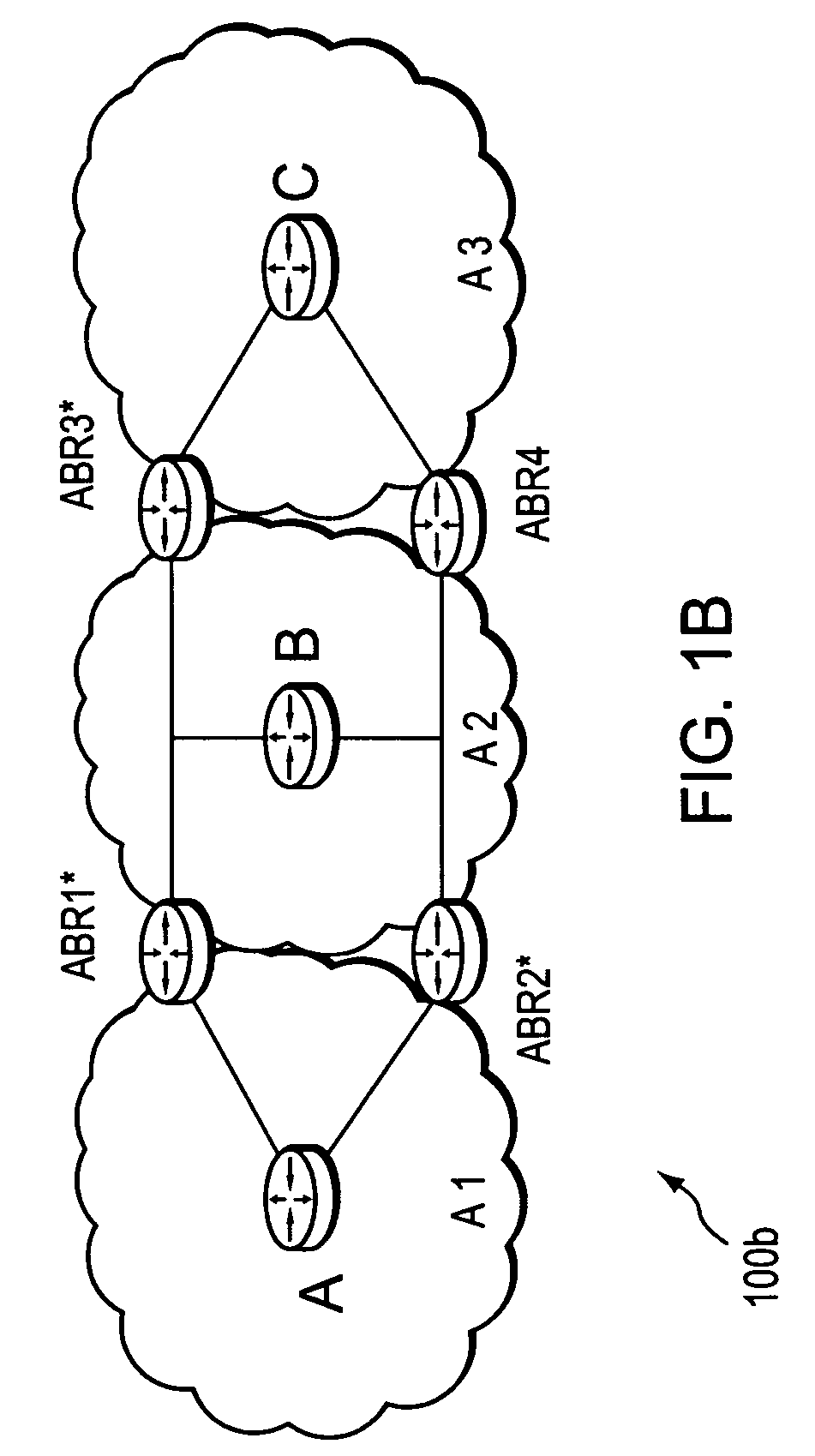
InactiveUS7496105B2Preserving confidentialityPreservation of computed path diversityError preventionTransmission systemsConfidentialityPath computation element
A technique retrieves computed path segments across one or more domains of a computer network in accordance with a stateless Path Computation Element (PCE) model. The stateless PCE model includes one or more PCEs configured to compute one or more path segments through the domains in response to a path computation request issued by, e.g., a Path Computation Client (PCC). Notably, each computed path segment is encrypted as a data structure to preserve confidentiality across the domains. Each PCE then cooperates to return a path computation response, including the encrypted path segments and an explicit route object (ERO) containing compressed path descriptions of the computed path segments, to the PCC.
Owner:CISCO TECH INC
Method of improving FPGA security using authorization codes
ActiveUS9672385B2Protect the loadPreventing overbuildingKey distribution for secure communicationUser identity/authority verificationAuthorizationOperating system
A method for securely programming a population of authorized FPGAs includes defining the population of authorized FPGAs, generating an encrypted configuration bitstream for the population of authorized FPGAs, generating an individual Authorization Code for each FPGA in the population of authorized FPGAs, feeding the individual Authorization Codes into the FPGAs in the population of FPGAs, feeding the encrypted configuration bitstream into all of the FPGAs in the population of FPGAs, and in each FPGA using the Authorization Code to decrypt the encrypted configuration bitstream to program the FPGA.
Owner:AYRLETT +1
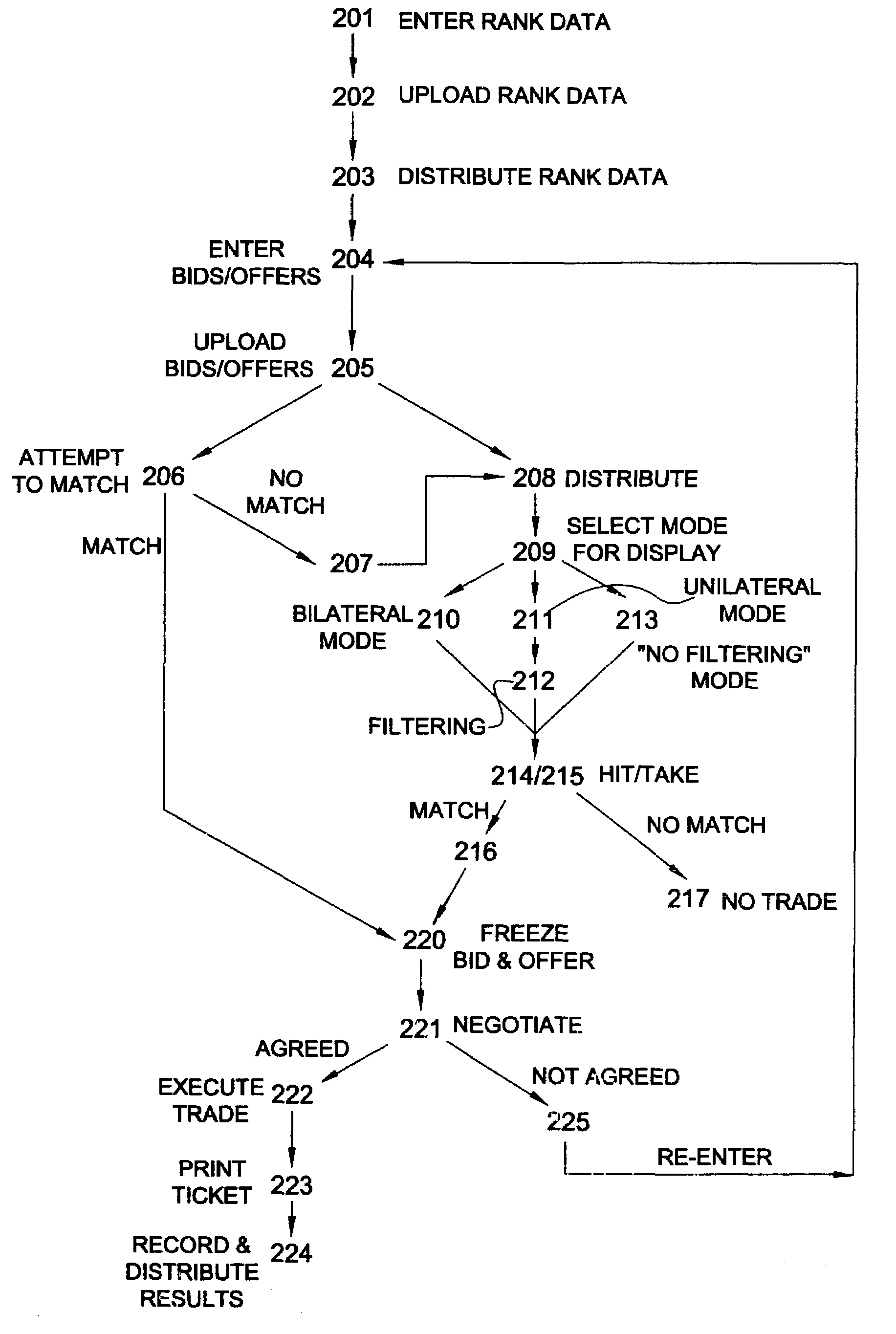
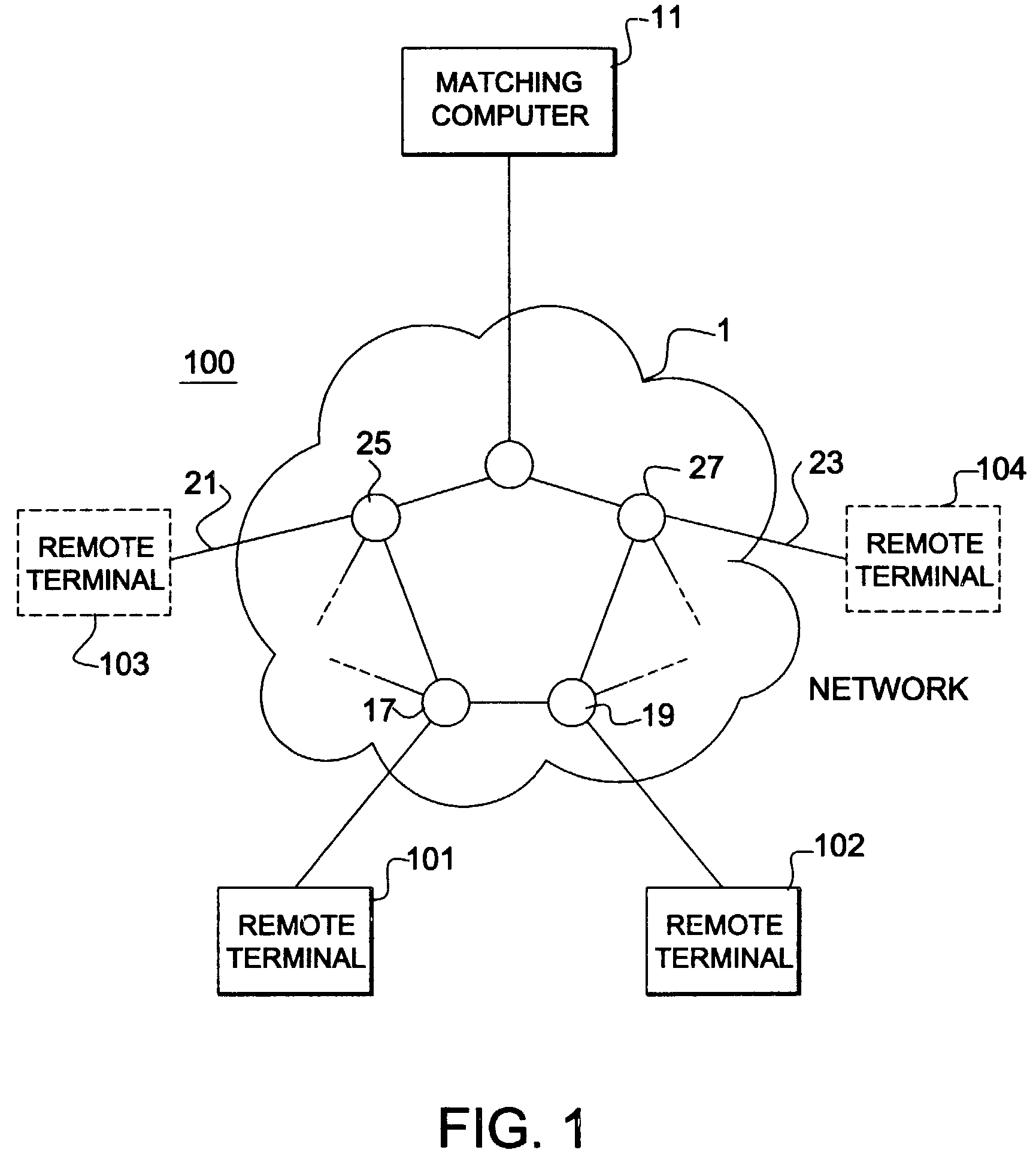
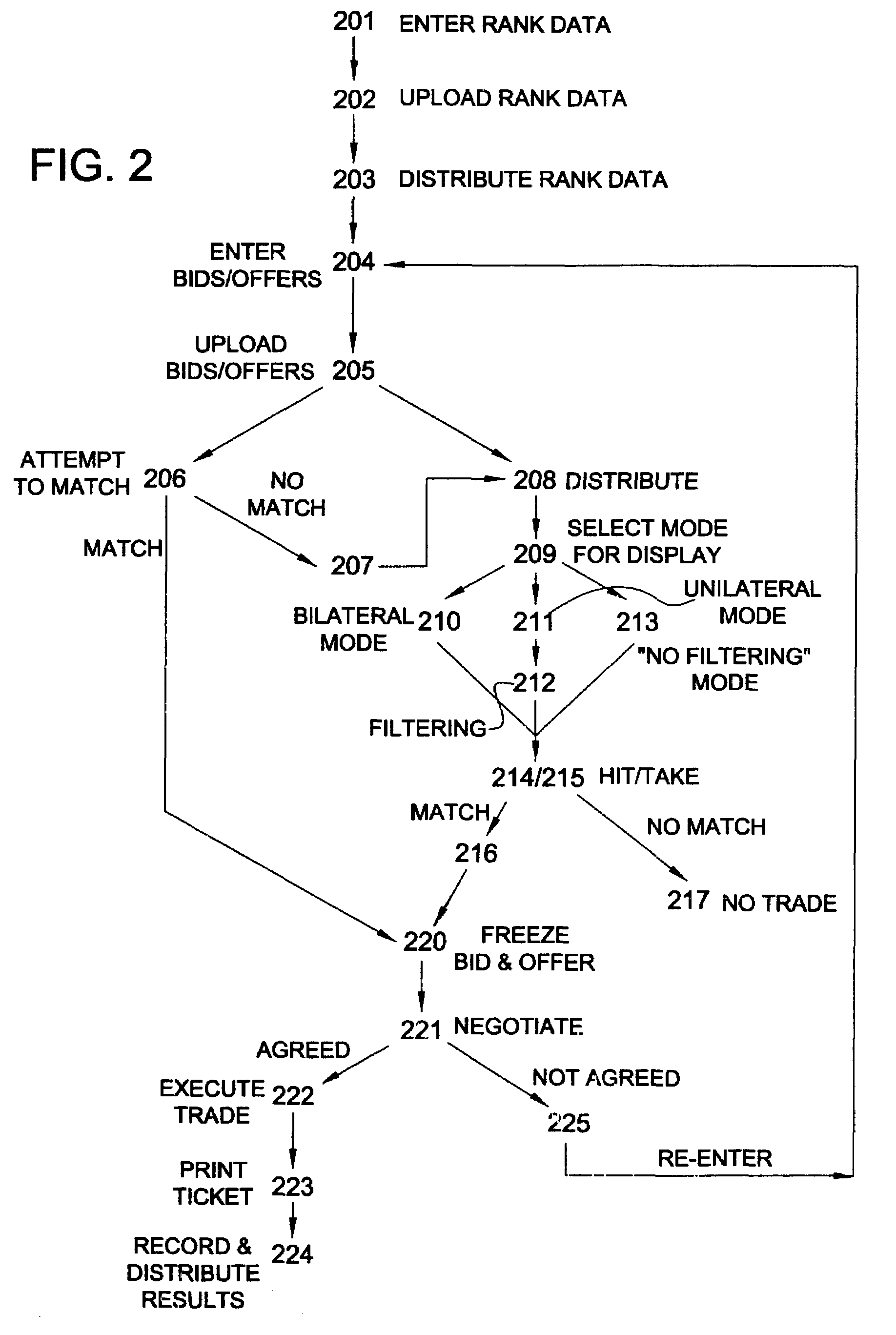
Negotiated matching system
A negotiated matching system includes a plurality of remote terminals associated with respective potential counterparties, a communications network for permitting communication between the remote terminals, and a matching station. Each user enters trading information and ranking information into his or her remote terminal. The matching station then uses the trading and ranking information from each user to identify transactions between counterparties that are mutually acceptable based on the ranking information, thereby matching potential counterparties to a transaction. Once a match occurs, the potential counterparties transmit negotiating messages to negotiate some or all terms of the transaction. Thus, the negotiated matching system first matches potential counterparties who are acceptable to each other based on trading and ranking information, and then enables the two counterparties to negotiate and finalize the terms of a transaction.
Owner:REFINITIV US ORG LLC
System and method for retrieving computed paths from a path computation element using encrypted objects
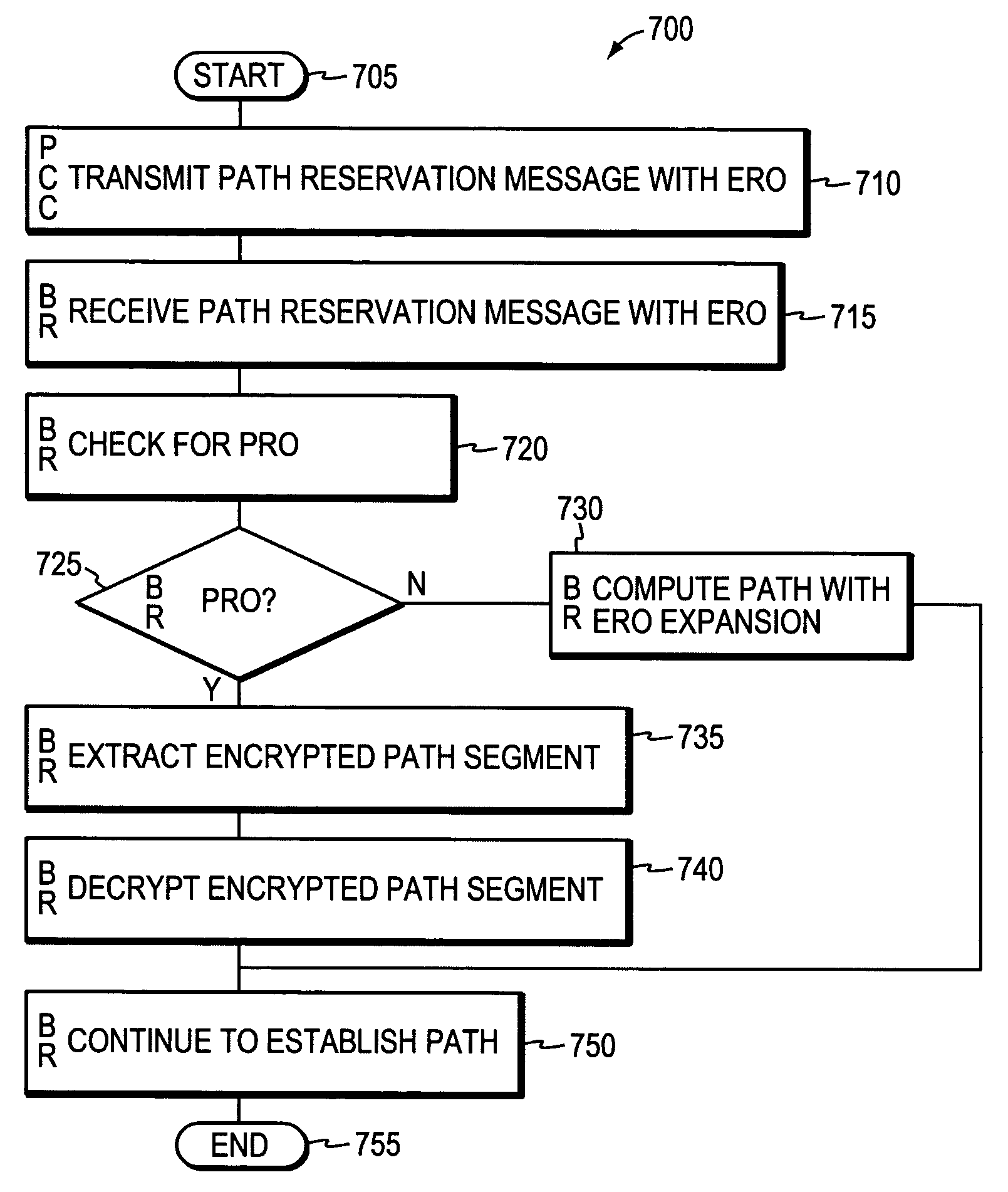
ActiveUS20090135841A1Preserving confidentialityPreservation of computed path diversityError preventionTransmission systemsPath computation elementClient-side
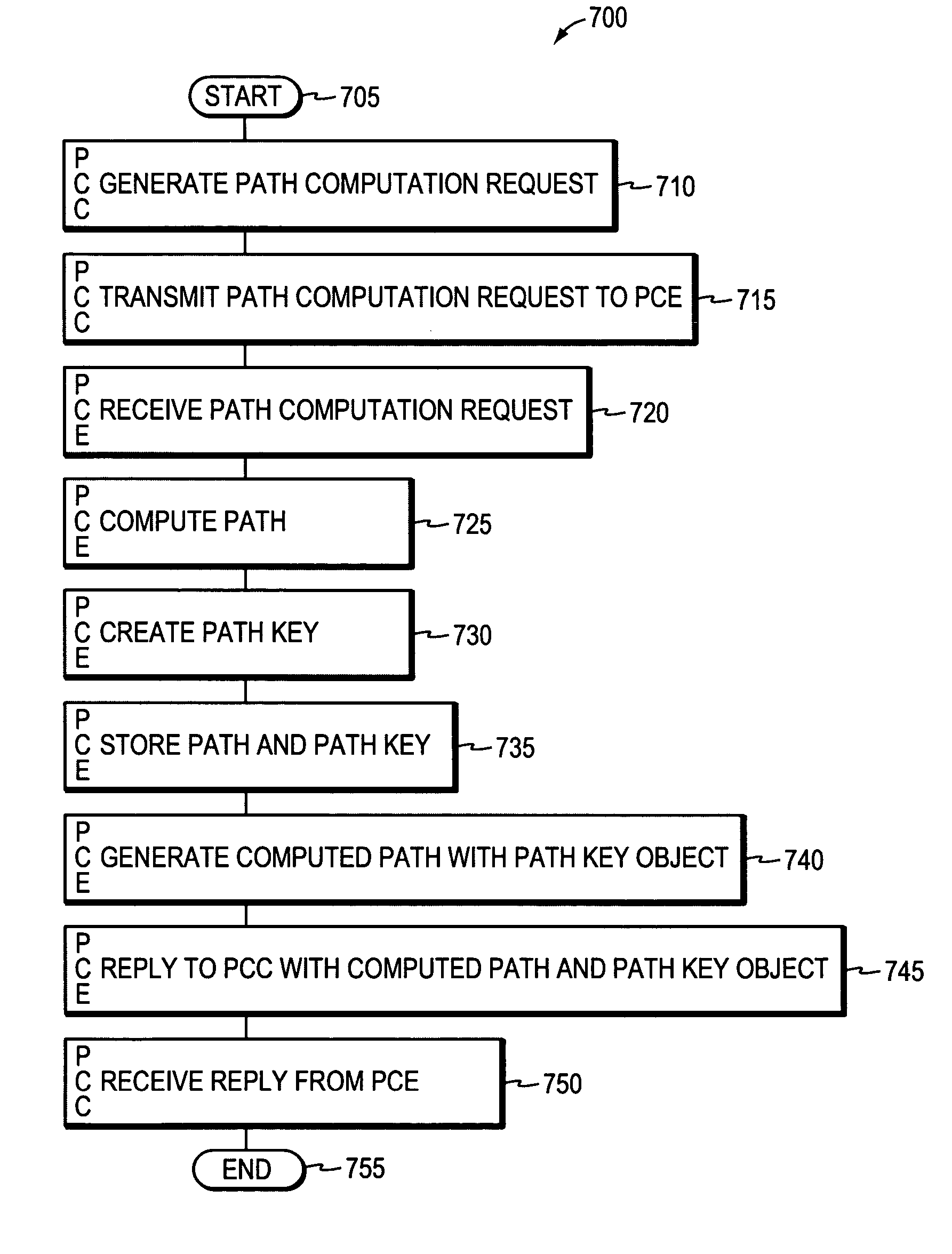
In one embodiment, a path computation client (PCC) generates a path computation request and transmits the path computation request to a path computation element (PCE). The PCC receives from the PCE a response including path segments defining a path, at least one of the path segments being an encrypted path segment that has been encrypted according to an encryption algorithm associated with a remote domain. The PCC then generates a path reservation message that includes the encrypted path segment. This is done without decrypting the encrypted path segment at the PCC. The PCC transmits the path reservation message to one or more nodes along the path, which may be capable of decrypting the encrypted path segment.
Owner:CISCO TECH INC
Heating container sleeve or tape
InactiveUS20060062948A1Rapid and convenient destructionPreserving confidentialityStampsWrappers shrinkageMicrowaveConfidentiality
The present invention is a container sleeve or alternatively a pressure sensitive tape having coated thereon or therein an energy receiver material which heats in response to microwave energy. The container sleeve or pressure sensitive tape substrate can be advantageously employed with conventional thermally imaging record materials in the form of a label, such as used on prescriptions, to facilitate preserving patient information confidentiality by obscuring information when contacted with microwave energy.
Owner:APPLETON PAPERS INC
System and method for retrieving computed paths from a path computation element using a path key
ActiveUS7558276B2Preserving confidentialityPreservation of computed path diversityError preventionFrequency-division multiplex detailsPathPingPath computation element
Owner:CISCO TECH INC
Method and apparatus for simplified research of multiple dynamic databases
InactiveUS20020091907A1Confidentiality of operationOperation resultWeb data indexingDigital data processing detailsDynamic databaseEngineering
A method and apparatus assembles multiple databases from different remote sources, performs research using the database specified using an easy-to-use user web interface and indentifies whether results are relevant and notifies the user of relevant results. As the database change, the research may be automatically performed on the changed portion of the database, and relevant results identified. The user is then notified of relevant results as they are incorporated into the databases.
Owner:HITACHI LTD
Remotely debugging metadata of filesystem without accessing user data of filesystem
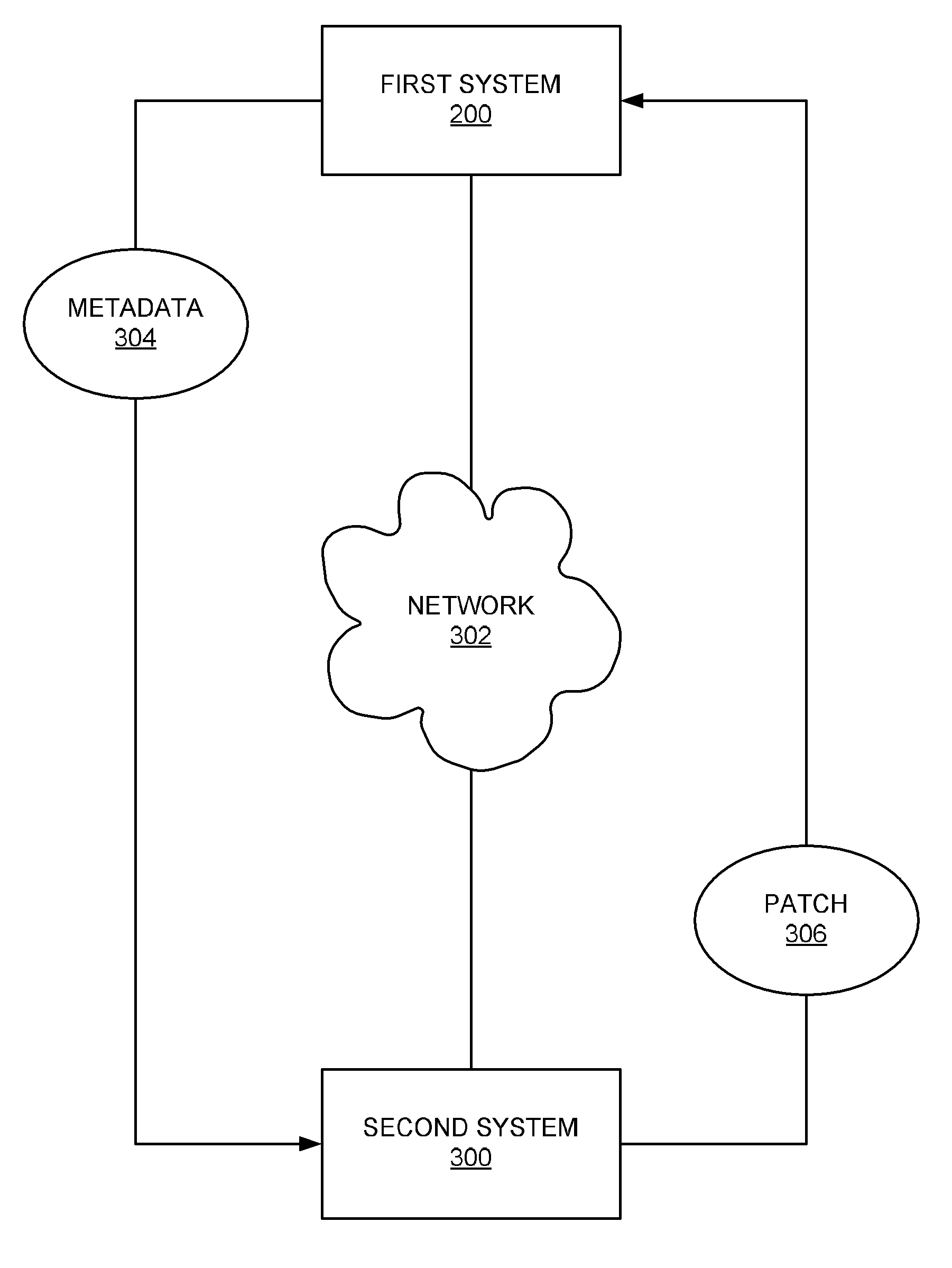
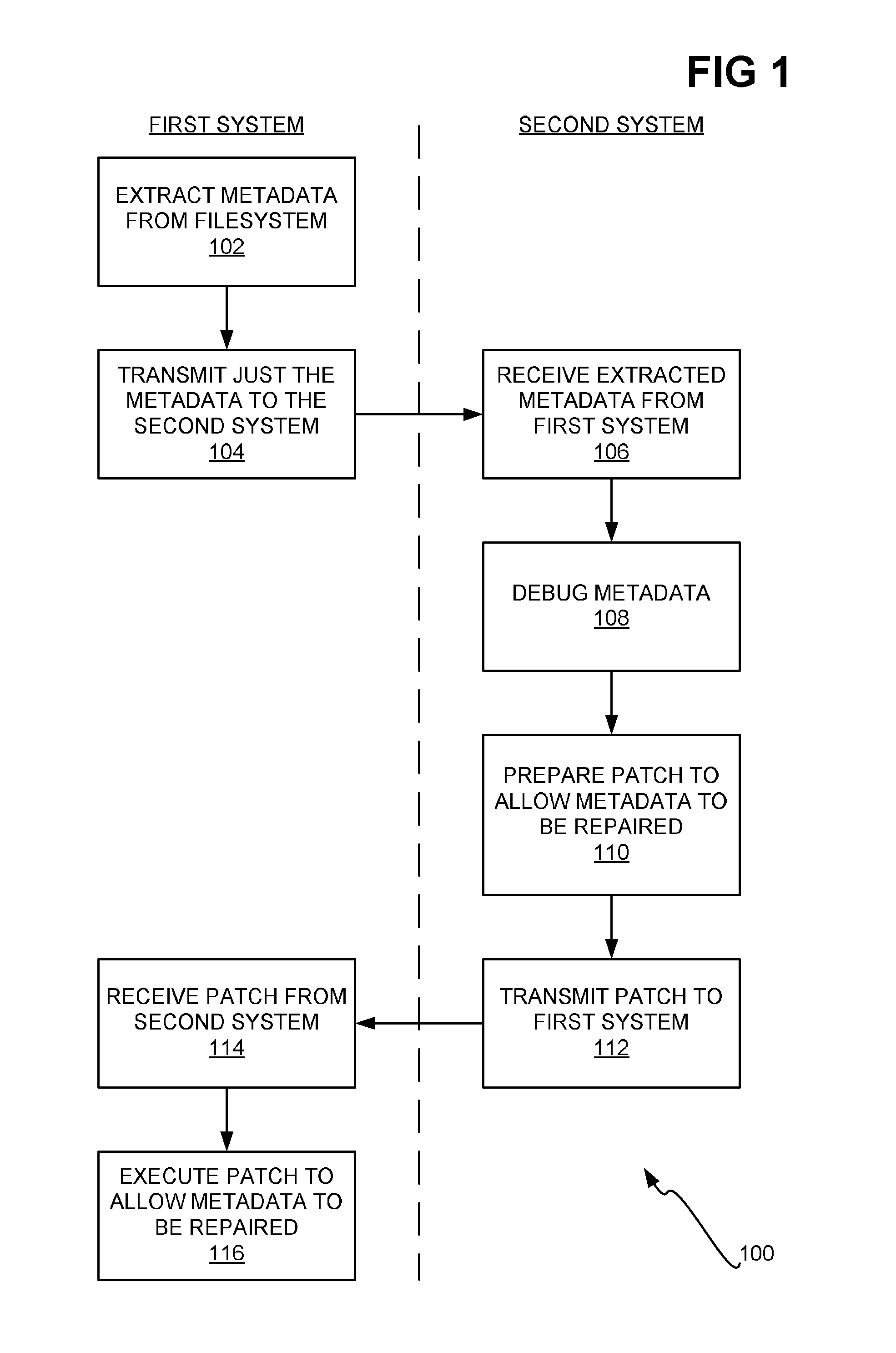
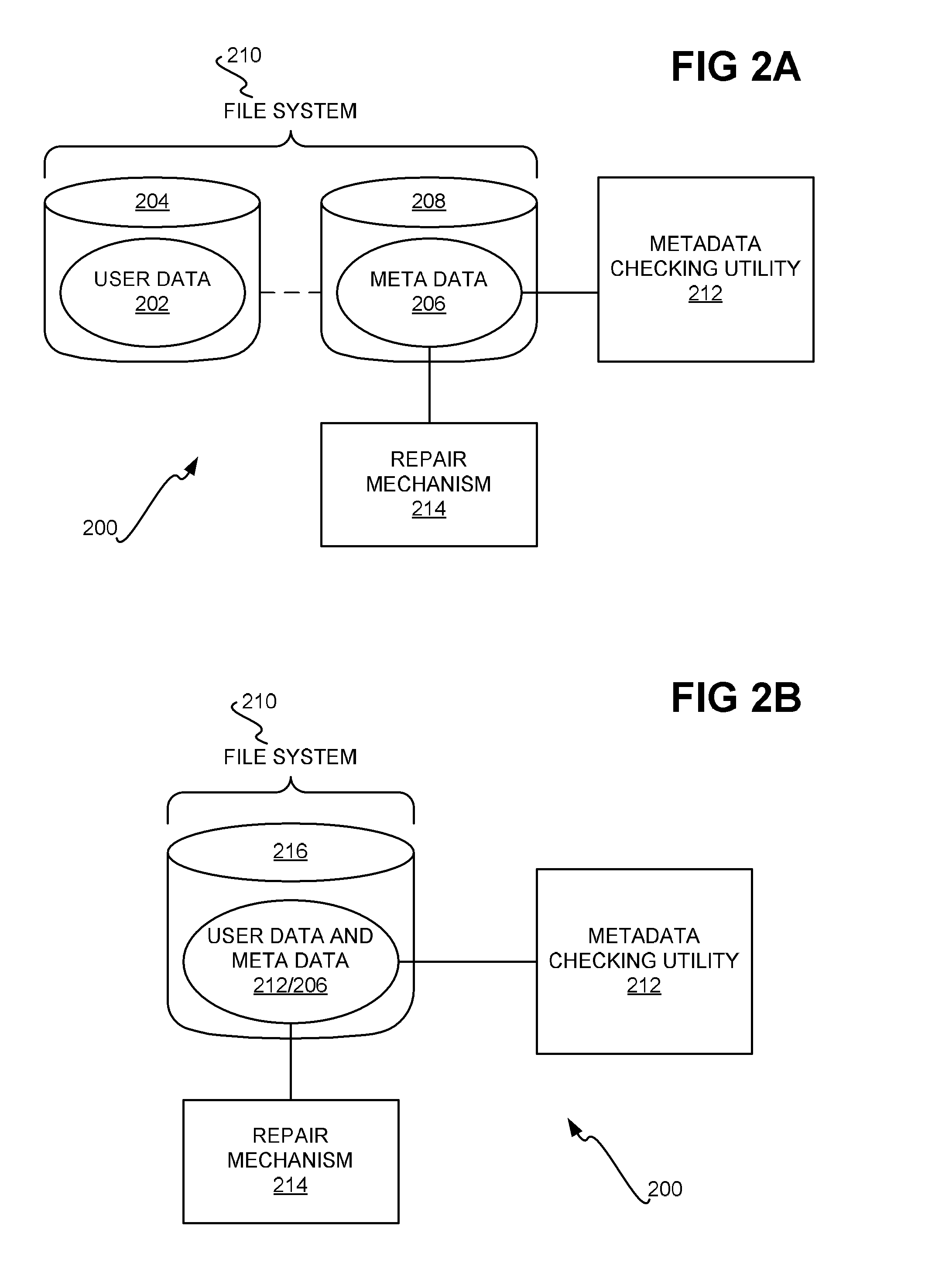
ActiveUS20090077003A1Preserving confidentialityDirect accessFile system administrationNon-redundant fault processingFile systemComputer science
Metadata is extracted from a filesystem of a first system. The filesystem includes user data and the metadata. The metadata relates to the user data and is corrupt. Just the just the metadata extracted from the filesystem is transmitted from the first system to a second system. The second system receives the transmitted metadata, and loads this metadata to create a dummy namespace reflecting the metadata. The second system debugs the metadata, and prepares a patch based on this debugging. Execution of the patch allows the metadata to be repaired so that the metadata is no longer corrupt. The patch is transmitted from the second system to the first system for execution at the first system to allow the metadata to be repaired at the first system so that the metadata is no longer corrupt at the first system.
Owner:IBM CORP
Stimulus/response-based binding of identifiers across information domains while maintaining confidentiality
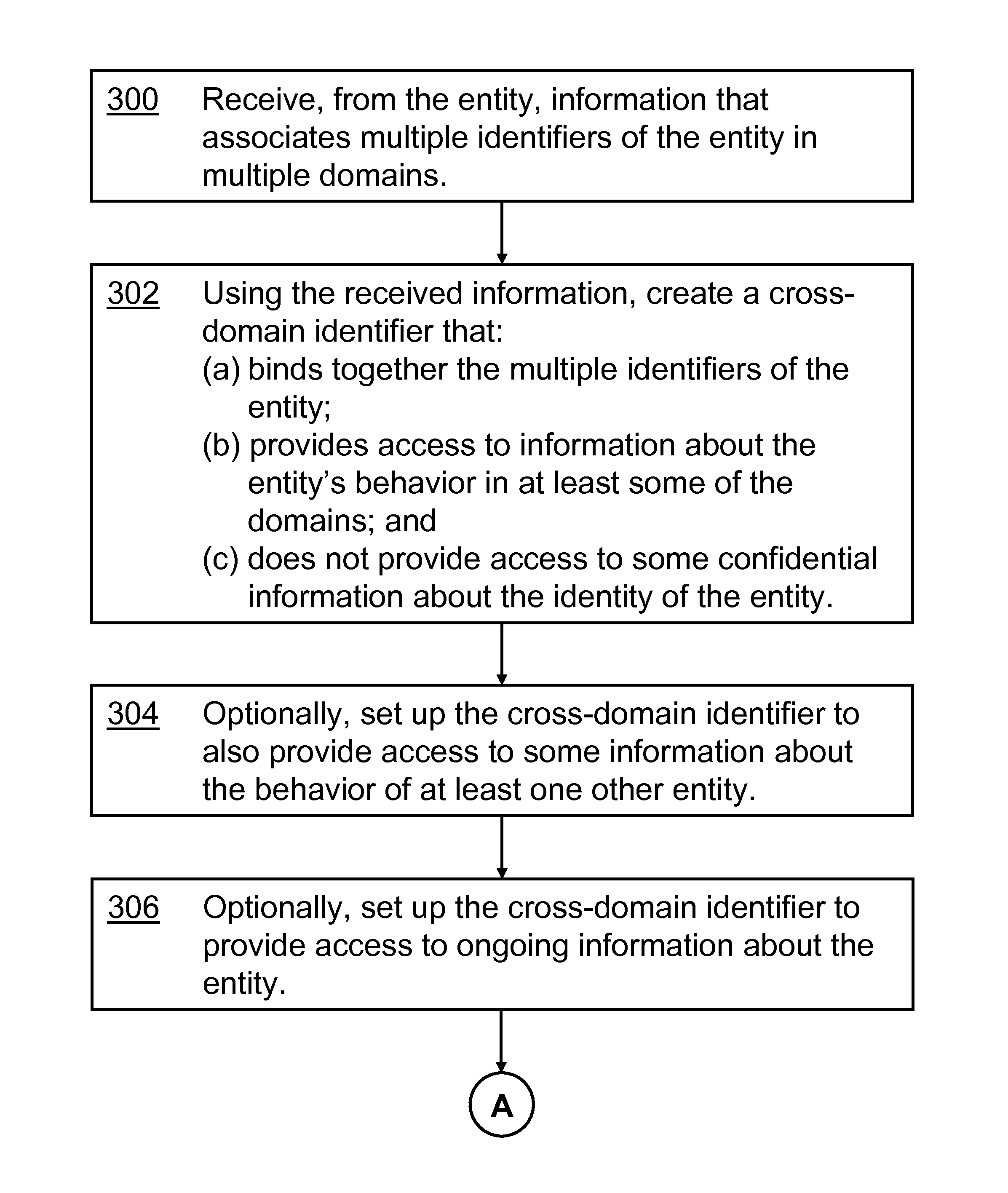
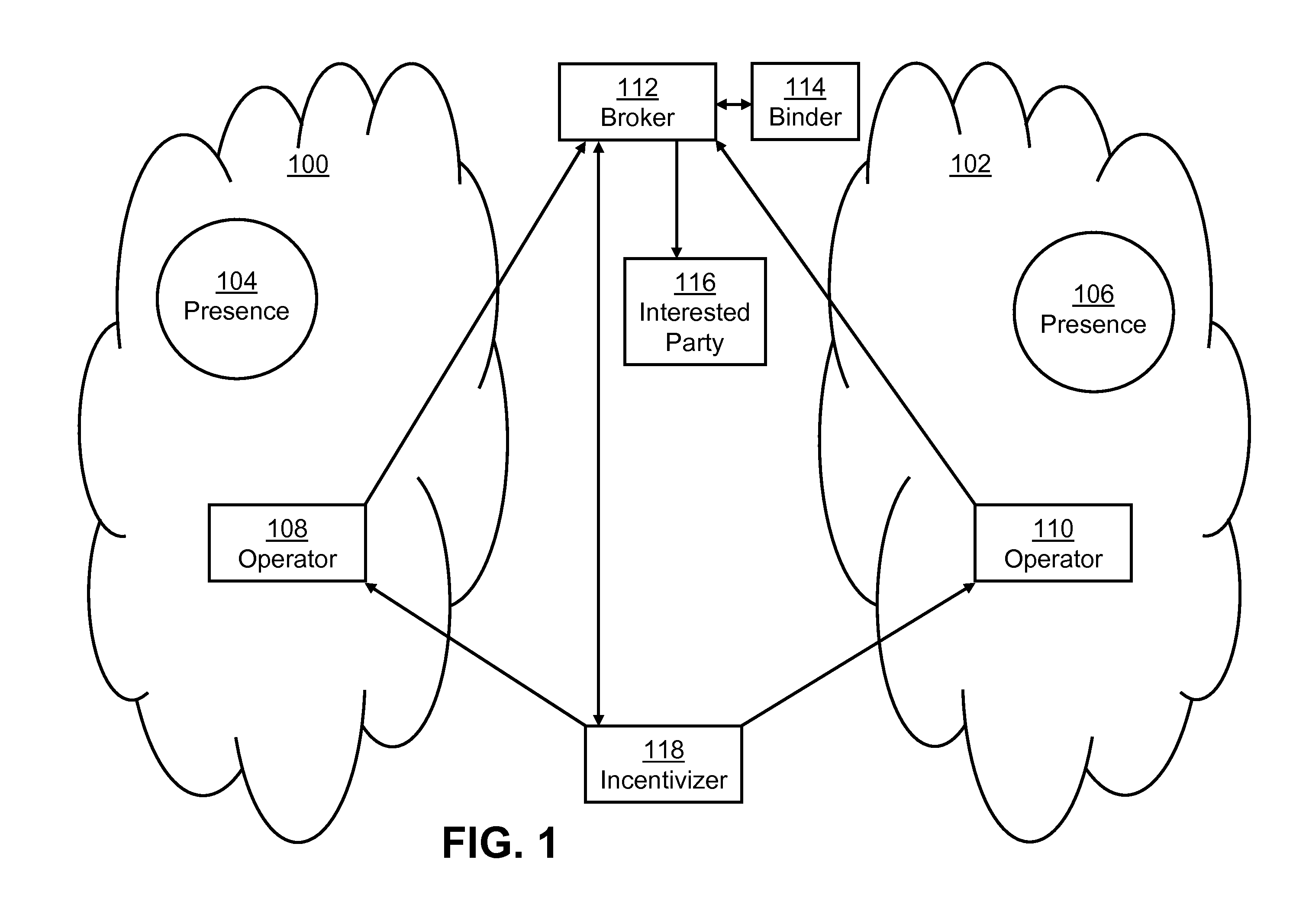
Disclosed are methods for extracting and using information about an entity that has a presence in a number of information domains. The entity has separate identifiers in each of several domains. Various techniques are described that bind together the identifiers of the entity across the domains. The results of the binding are provided to an interested party that can review information extracted about the entity's behavior in the multiple domains. The interested party is not given access to information that would compromise the confidentiality of the entity. A trusted broker has access to information about the behavior of the entity in the several domains. The broker analyzes that information and provides the analysis to the interested party, again without compromising the confidentiality of the entity. An “incentivizer” works with the broker to extract from the domains information that would be useful in binding together the different identifiers of the entity.
Owner:MOTOROLA SOLUTIONS INC
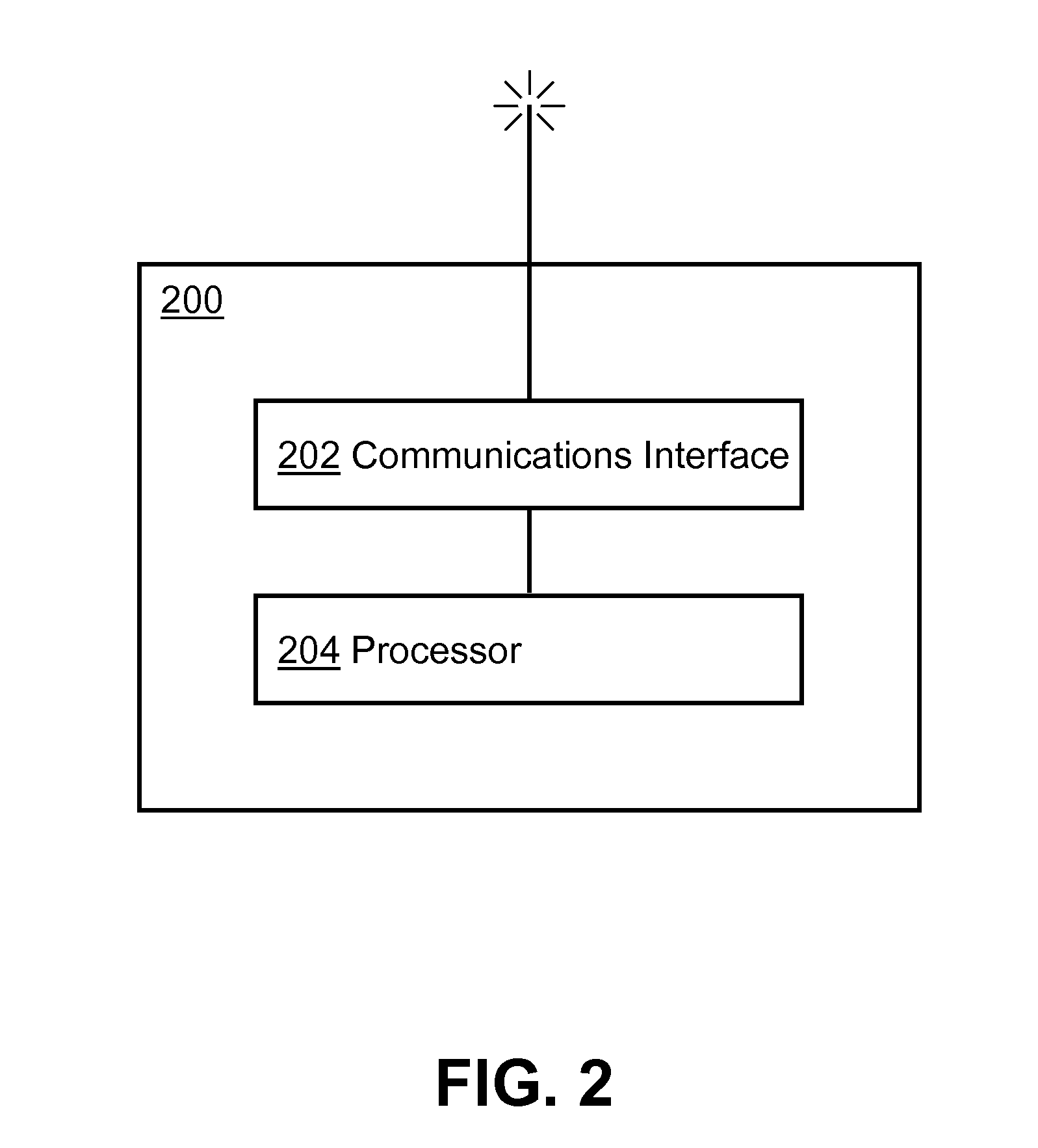
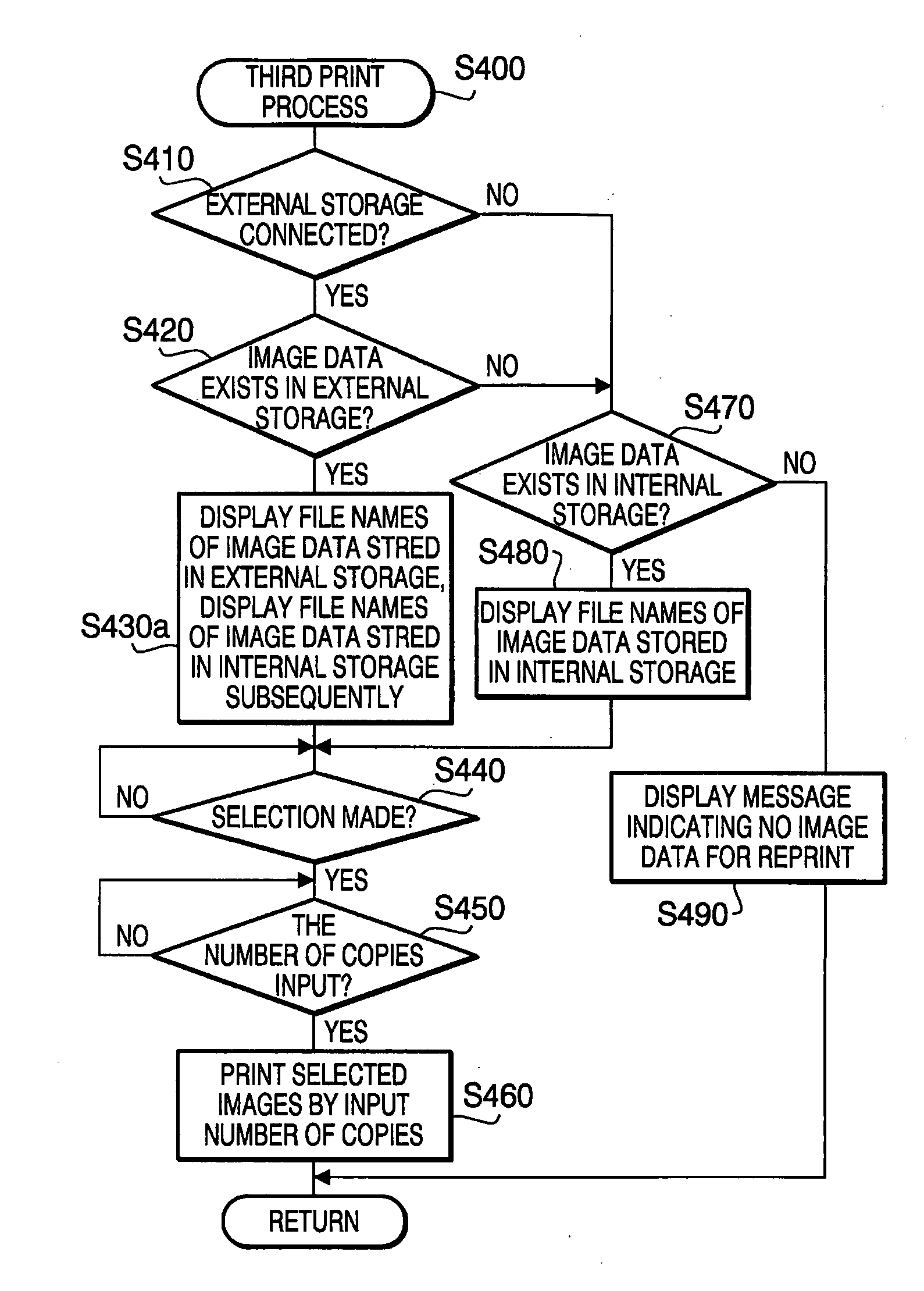
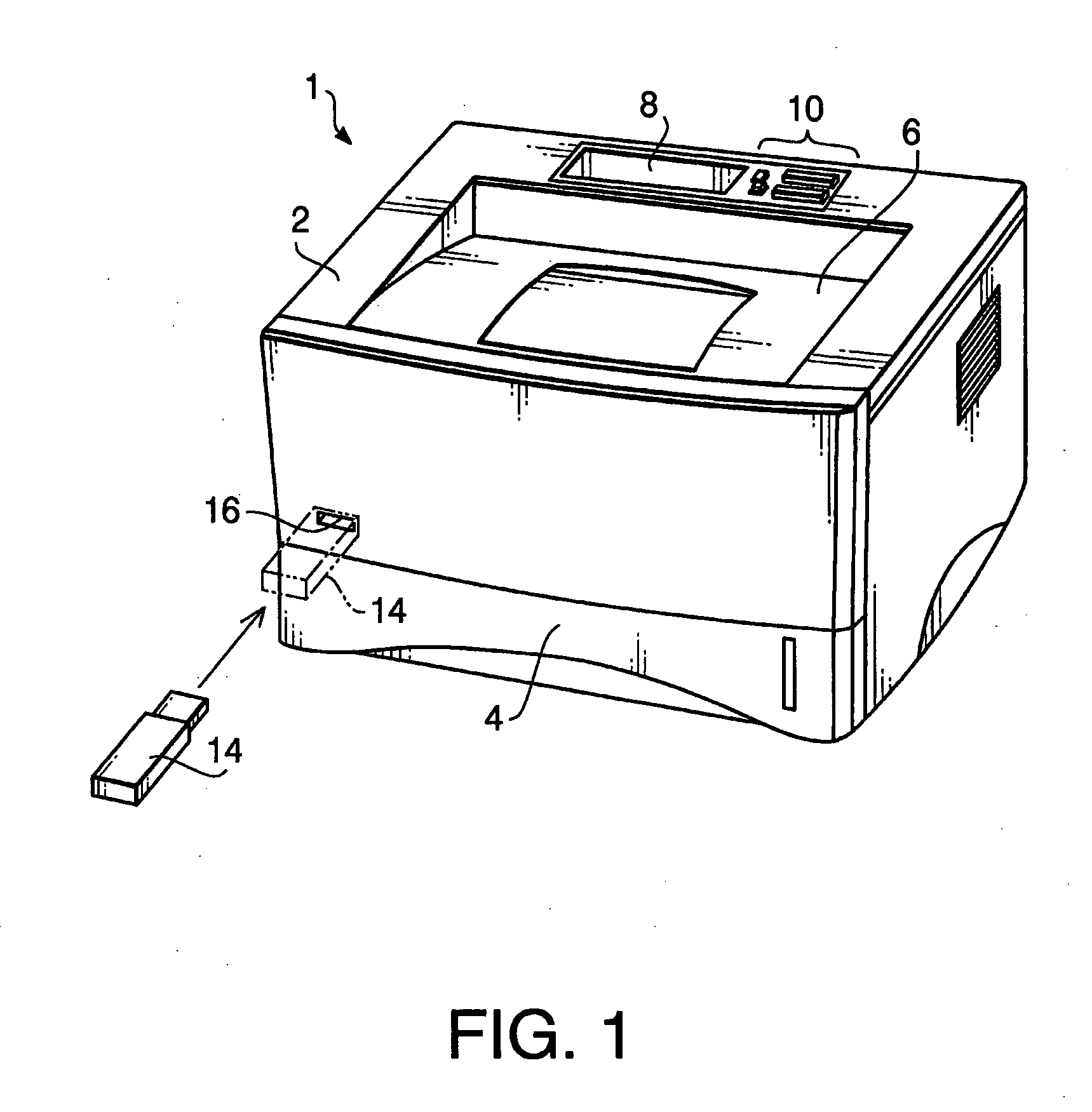
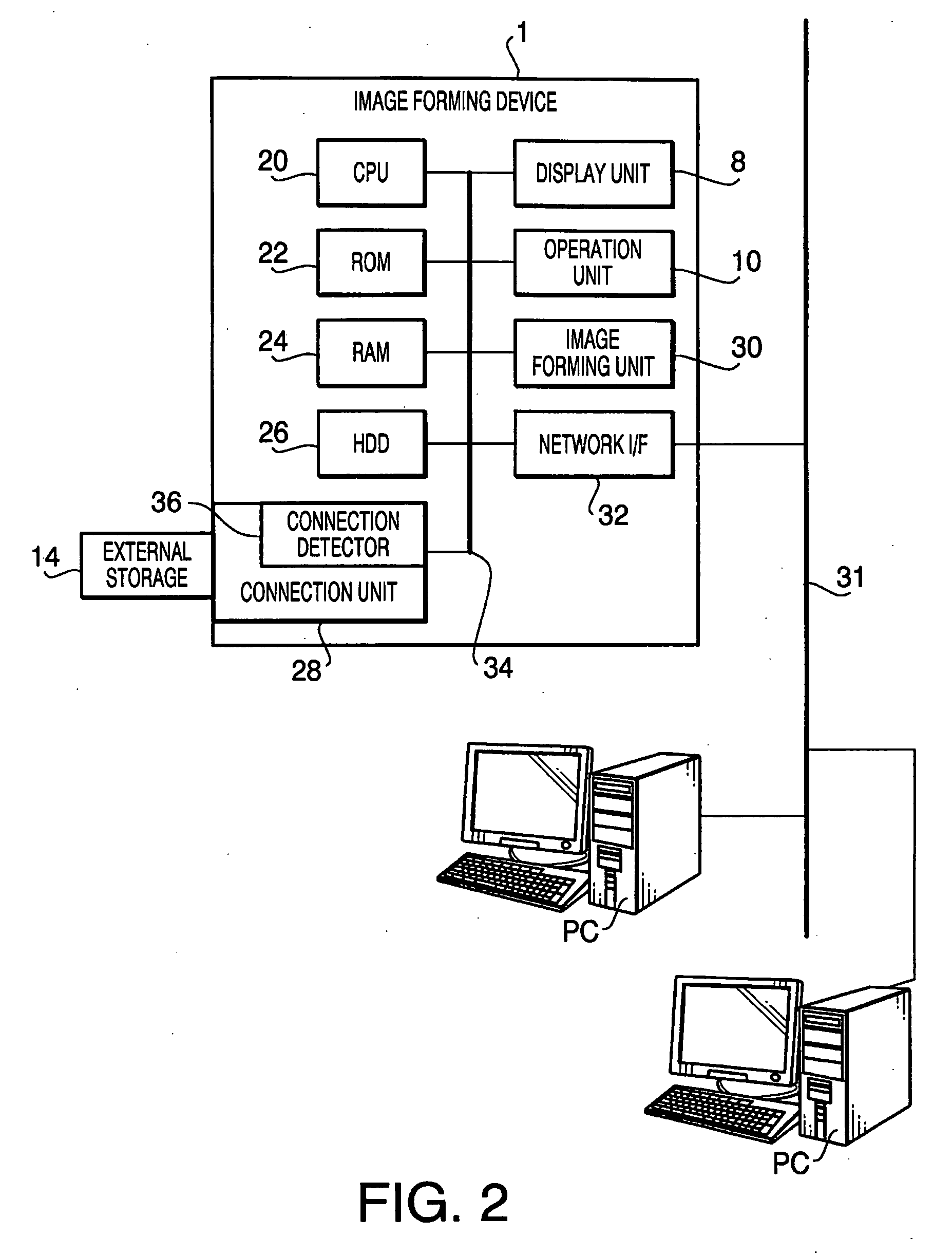
Image forming device
ActiveUS20080198413A1Extended waiting timePreserving confidentialityDigital computer detailsVisual presentation using printersPeripheralControl equipment
An image forming device is provided with an external storage, a printing unit, a storage controlling unit configured to store the image data in the external storage or an internal storage. The storage controlling device stores the image data developed from the print data retrieved from the print data stored in the external in the external storage, while stores the image data developed from the print data transmitted from the external device in the internal storage. At least file names of image data stored in the external storage on the displaying unit are displayed for selection when the external storage is connected to the image forming device, and file names of image data stored in the internal storage are displayed when the external storage is not connected to the image forming device. A reprinting unit performs a reprinting operation based on the selected image data.
Owner:BROTHER KOGYO KK
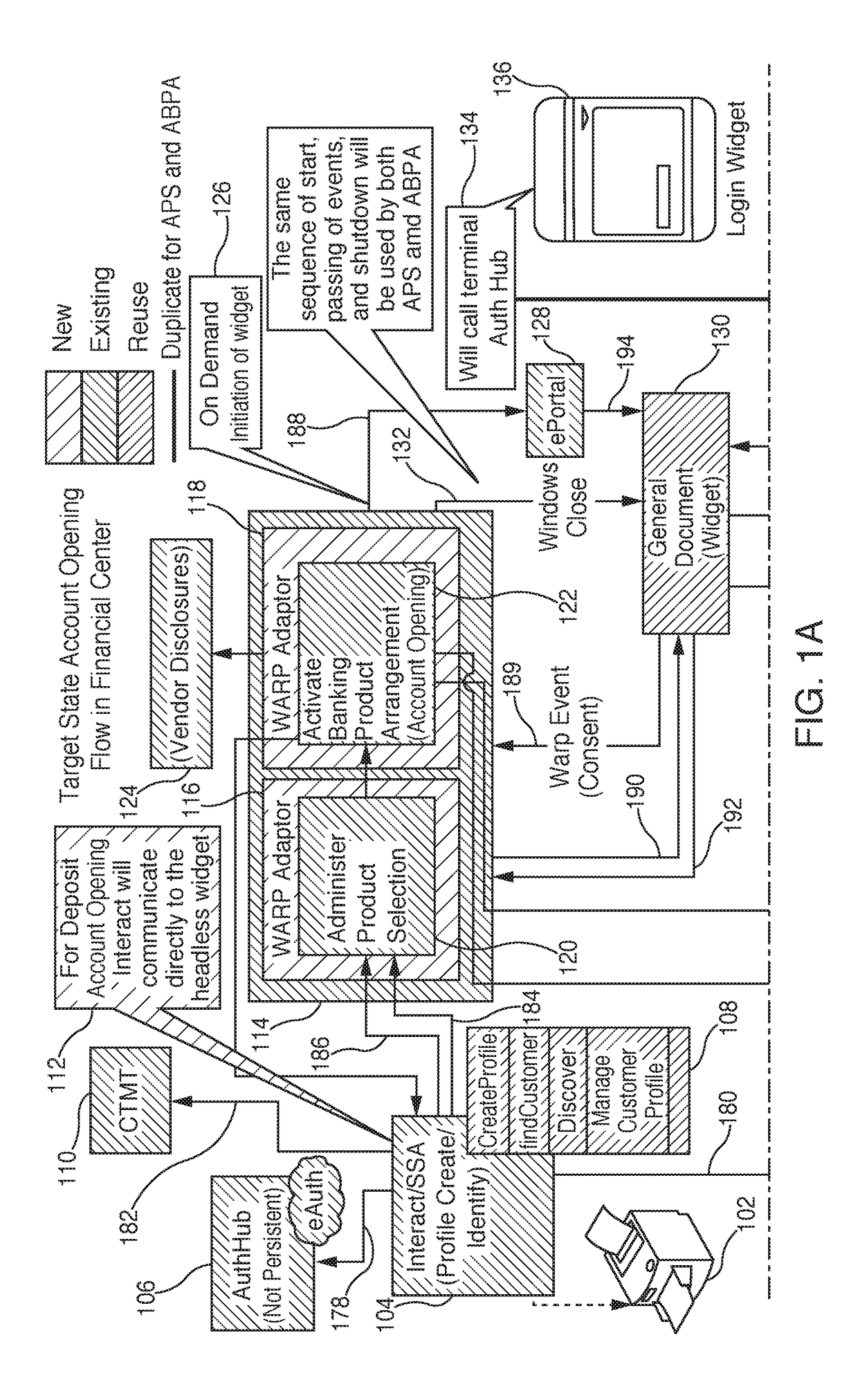
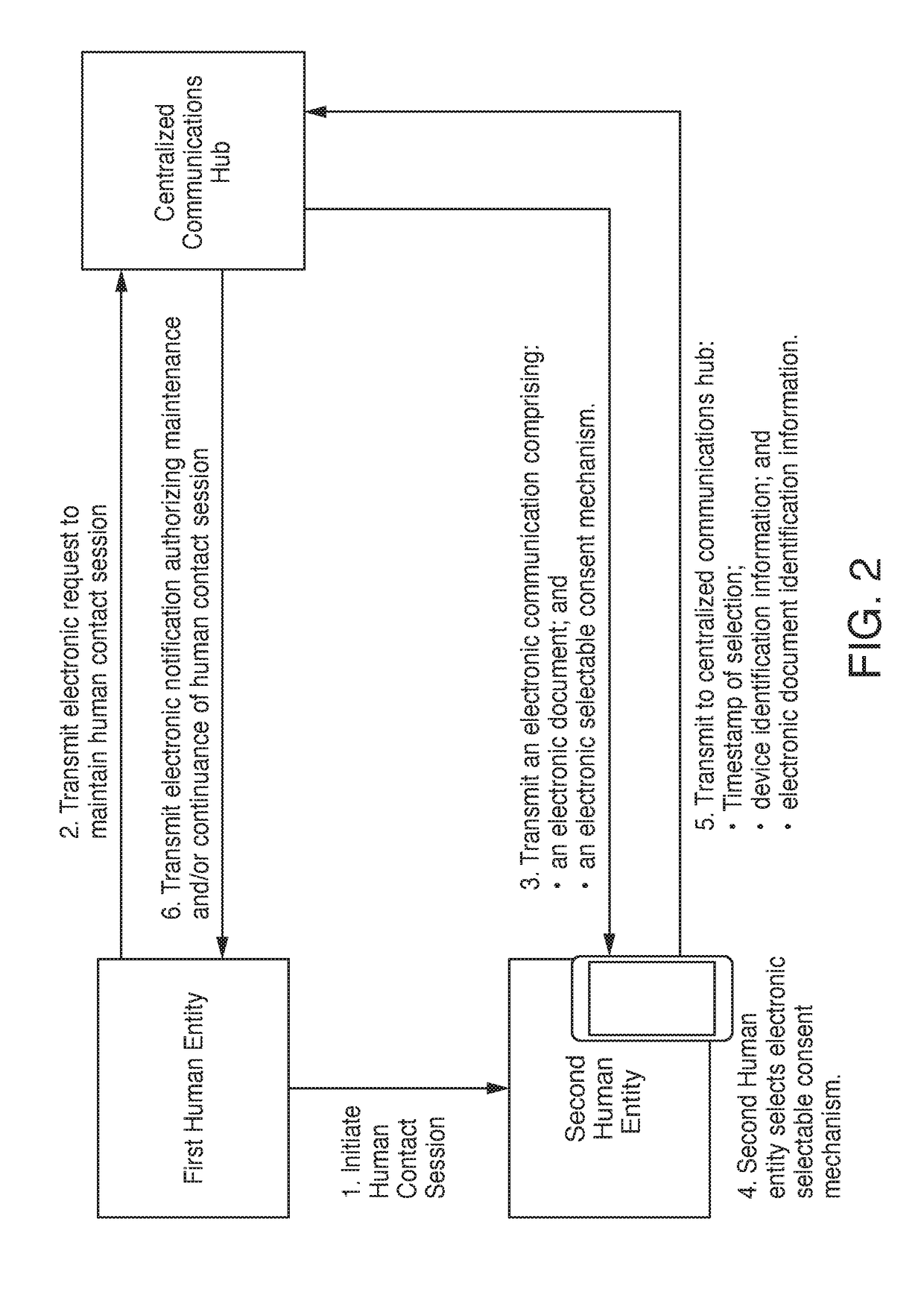
Real-time, electronically-executed consent receipt and documentation systems
InactiveUS20190012751A1Preserving confidentialityImprove securityMedical communicationData processing applicationsElectronic documentDocumentation procedure
Methods for receiving and documenting real-time, electronically-executed consent is provided. Methods may include initiating a human contact session between a first human entity and a second human entity. Methods may include transmitting a first request from a mobile device associated with the first human entity to a communications hub. The communications hub may transmit electronic documents and one or more electronic consent mechanisms to a mobile device associated with the second entity. The second entity may review the electronic documents and consent and / or agree to the information and / or requirements included in the electronic documents using one or more of the electronic consent mechanisms. Upon receipt of the consent and / or agreement at the communications hub, the communications hub may transmit an electronic notification of the received consent and / or agreement to the first human entity. The first human entity may continue the human contact session upon receipt of the agreement.
Owner:BANK OF AMERICA CORP
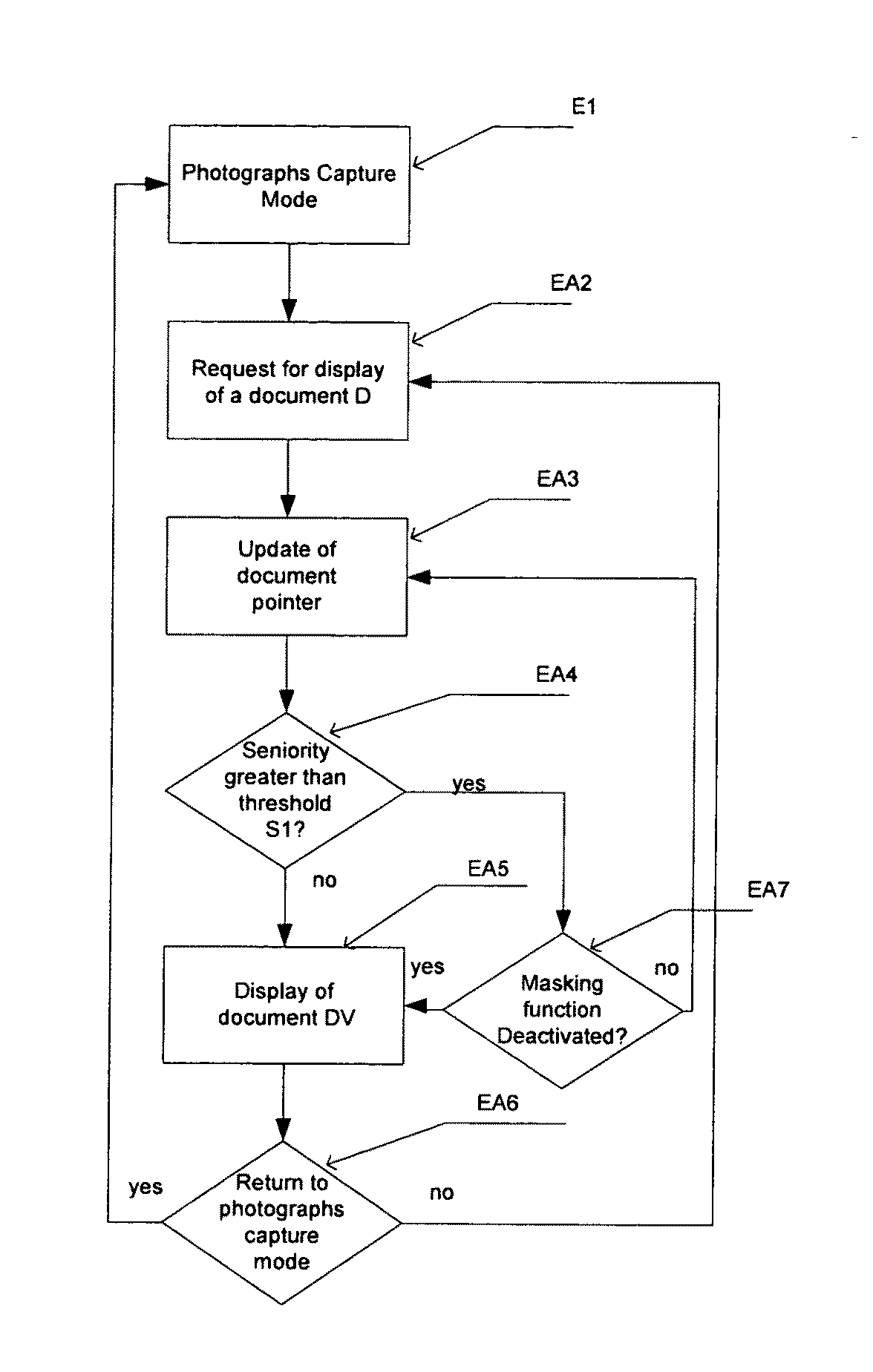
Display device and method aiming to protect access to audiovisual documents recorded in storage means
ActiveUS20100169983A1Accurate separationPreserving confidentialityDigital data processing detailsAnalogue secracy/subscription systemsAudiovisual documentComputer hardware
The invention relates to a display device and method aiming to protect access to audiovisual documents recorded in storage means.The device comprises means for:setting a masking threshold of said documents,masking recorded documents the seniority of which in said storage means is greater than said masking threshold.
Owner:INTERDIGITAL CE PATENT HLDG
Encrypted Digital Circuit Description Allowing Circuit Simulation
ActiveUS20150188661A1Protect intellectual propertyObscures design and operationInternal/peripheral component protectionSecret communicationComputer hardwareTruth value
A system for creating protected functional descriptions of integrated circuits provides an encrypted functional description that allows the integrated circuit to be simulated with respect to producing outputs for given sets of inputs without identification of the constituent components of the integrated circuit such as the logical gates making up the integrated circuit. The encrypted functional description may include encrypted truth-tables describing the generic gates of the integrated circuit, the encrypted truth-tables securing the function of each logical gate by including multiple redundant table entries mapped to alias values of Boolean logical states and erroneous table entries.
Owner:WISCONSIN ALUMNI RES FOUND
Method for Securing a Transaction Performed by Bank Card
ActiveUS20150199690A1Easy to usePreserving confidentialityProtocol authorisationComputer hardwareData stream
A method is provided for securing a transaction made by bank card, the transaction involving a remote provision, by a user, of data existing in a bank card in his possession. The method includes: obtaining data existing in the bank card to be used, called textual data; obtaining at least one portion of the textual data in the form of an audio data stream, called a sound sample, resulting from reading the data existing in the bank card to be used; computing a current voice signature from said sound sample; comparing said current voice signature with a reference voice signature pre-recorded and associated with the textual data of the bank card; and when the reference voice signature differs from the current voice signature by a value greater than the first value defined by a predetermined parameter, for rejecting the transaction.
Owner:BANKS & ACQUIRERS INT HLDG
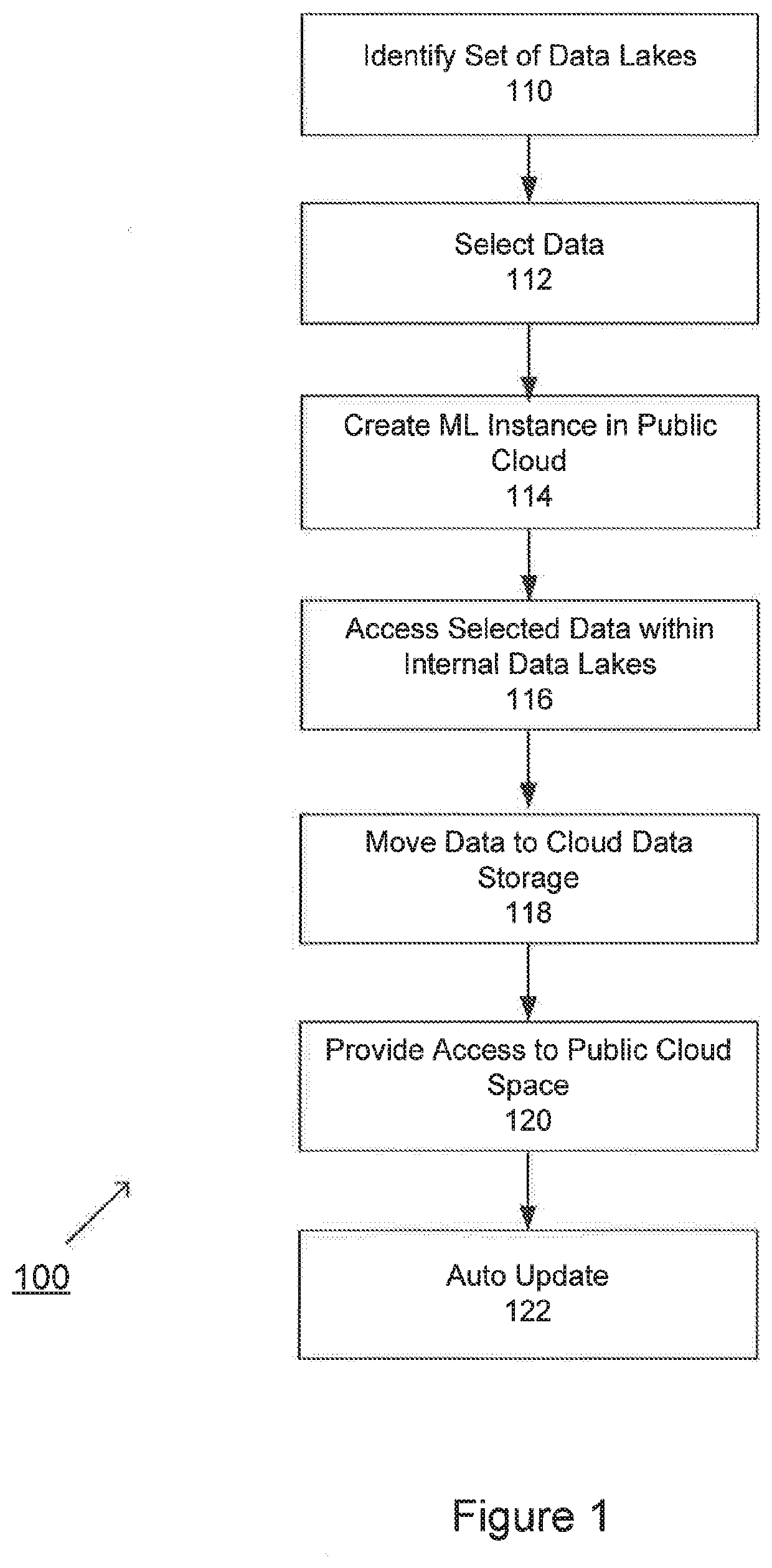
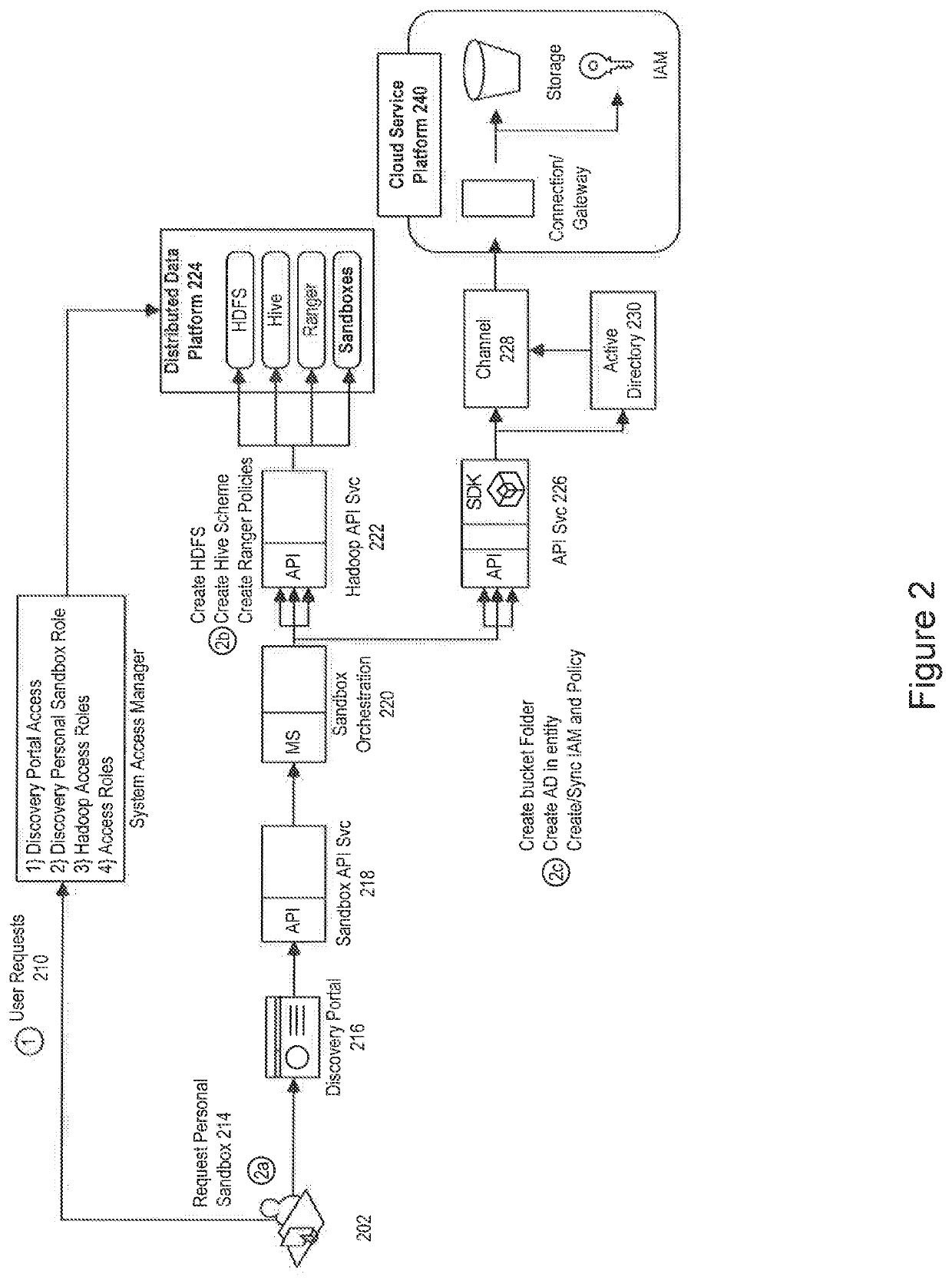
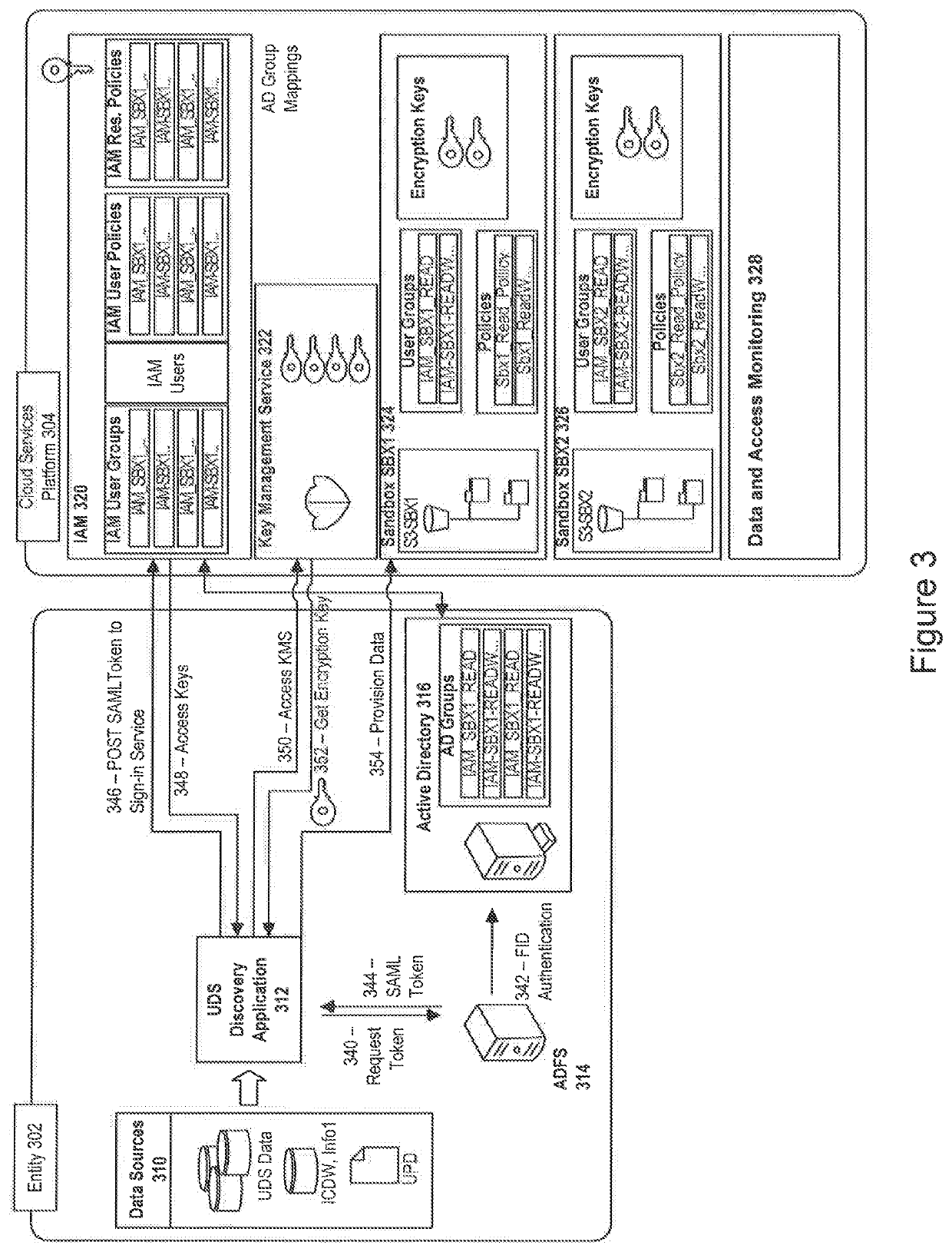
Method and system for implementing a cloud machine learning environment
ActiveUS20200151346A1Preserving confidentialityImprove data integrityDigital data information retrievalUser identity/authority verificationEngineeringArtificial intelligence
An embodiment of the present invention is directed to leveraging GPU farms for machine learning where the selection of data is self-service. The data may be cleansed based on a classification and automatically transferred to a cloud services platform. This allows an entity to leverage the commoditization of the GPU farms in the public cloud without exposing data into that cloud. Also, an entire creation of a ML instance may be fully managed by a business analyst, data scientist and / or other users and teams.
Owner:JPMORGAN CHASE BANK NA
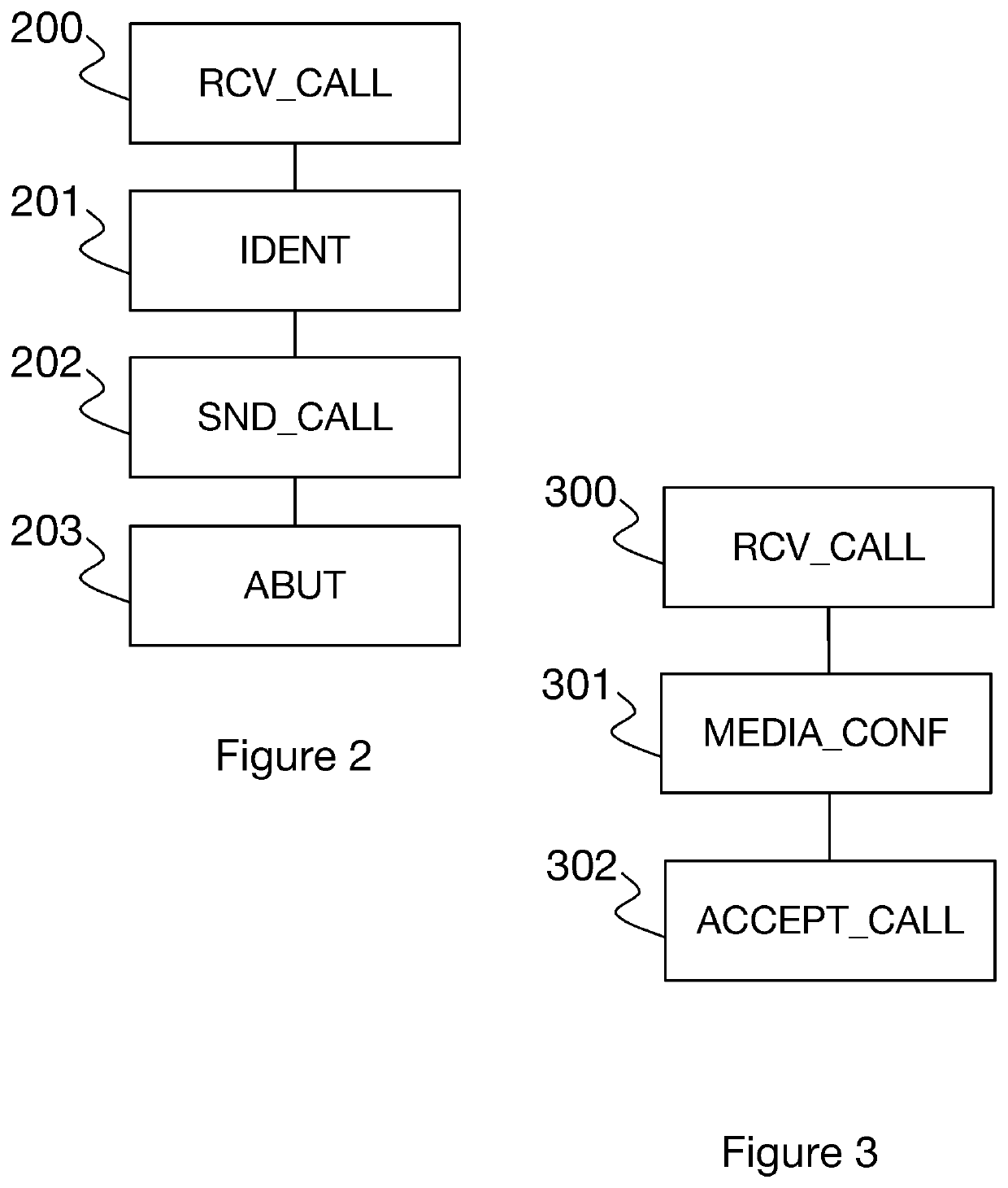
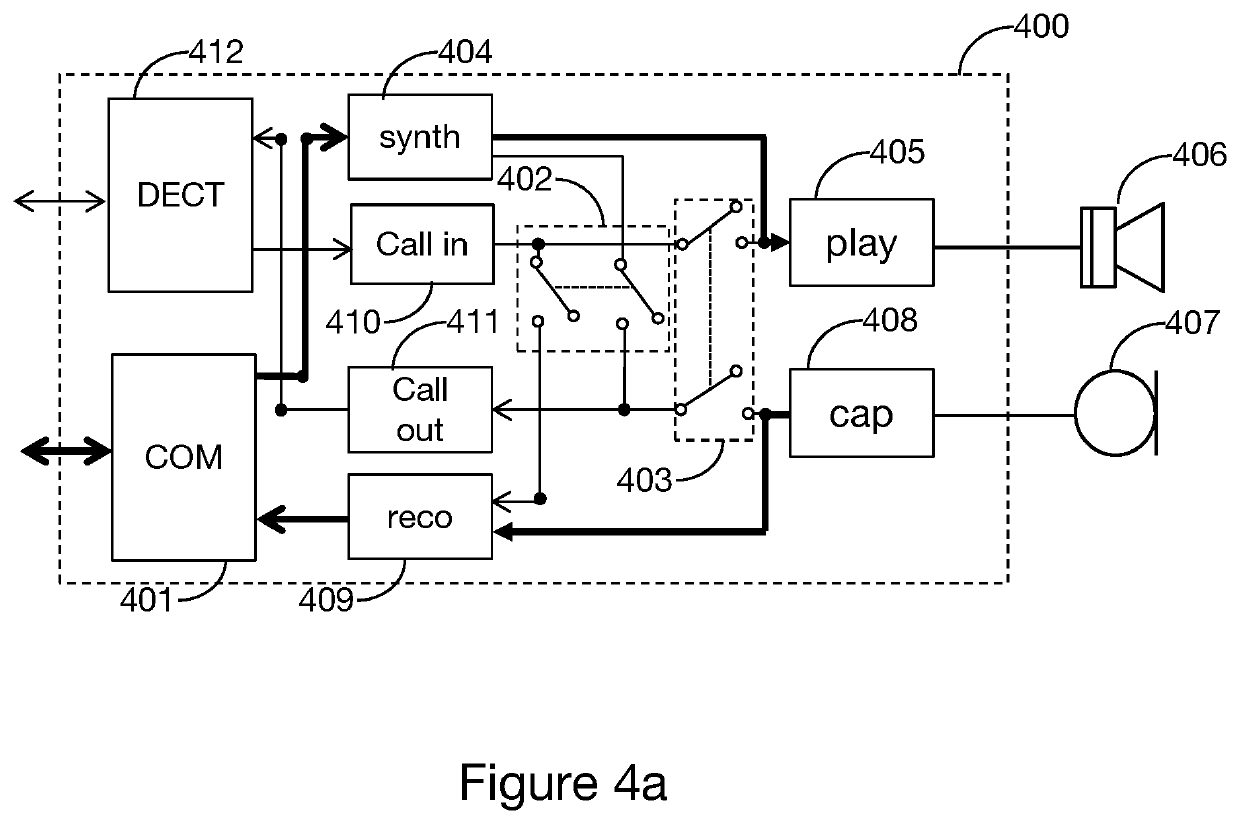
Method for achieving remote access to a personal voice assistant
ActiveUS20200168228A1Improve user experienceBetter user identificationInterconnection arrangementsAutomatic exchangesTelecom networkTelephone communication
A method for achieving remote access to a voice assistant suitable for setting up telephone communications with a communication terminal via a telecommunications network. The method includes: setting up a first communication with a caller terminal; obtaining, via the set-up communication, a datum identifying the voice assistant; transmitting a setup message for setting up a second communication to the identified voice assistant, the message containing at least one parameter suitable for activating a remote operating mode of the voice assistant; and connecting the first and second communications.
Owner:ORANGE SA (FR)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com