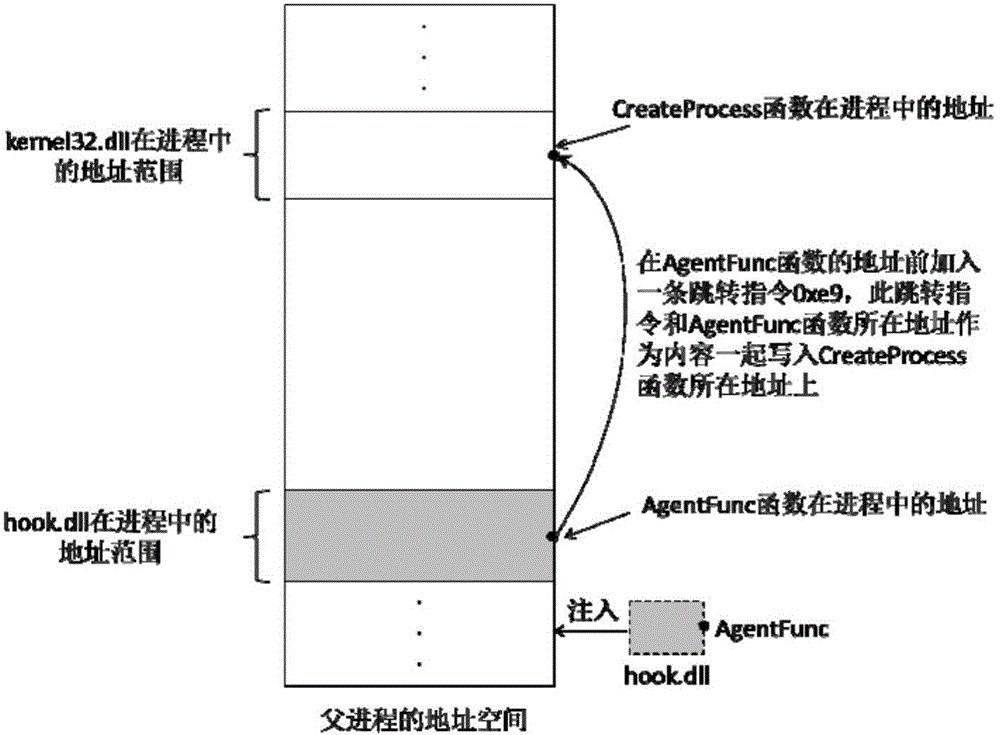
Method for remotely monitoring safety of application program
An application program and remote monitoring technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as inability to guarantee application program security, increase server load, and increase server load, so as to improve office efficiency, reduce load, and simplify processes Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with specific examples and accompanying drawings.
[0035] In this embodiment, the remote server and the database server are integrated into one server, Ubuntu14.04 is used as the operating system, and the database is MYSQL5.5; the client is a notebook computer equipped with Windows7 32-bit Professional Edition. The remote server and the client establish a connection through the HTTP protocol and complete data communication; the remote server directly accesses the database through the interface provided by the MYSQL server to complete data interaction.
[0036] A remote monitoring method for application security such as figure 1 shown, including the following steps:
[0037] Step 1: Establishing a trustworthy list of applications in the database server by using a remote server, and storing digital fingerprints of trustworthy applications in the trustworthy list of applications;
[0038] The digital fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com