Anti-vulnerability-exploitation method and system
A vulnerability and process technology, which is applied in the field of vulnerability prevention method and system, can solve the problems of high maintenance cost, user property security threat, failure to detect overflow vulnerabilities in time, and achieve the effect of ensuring stability and enhancing rapid response ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
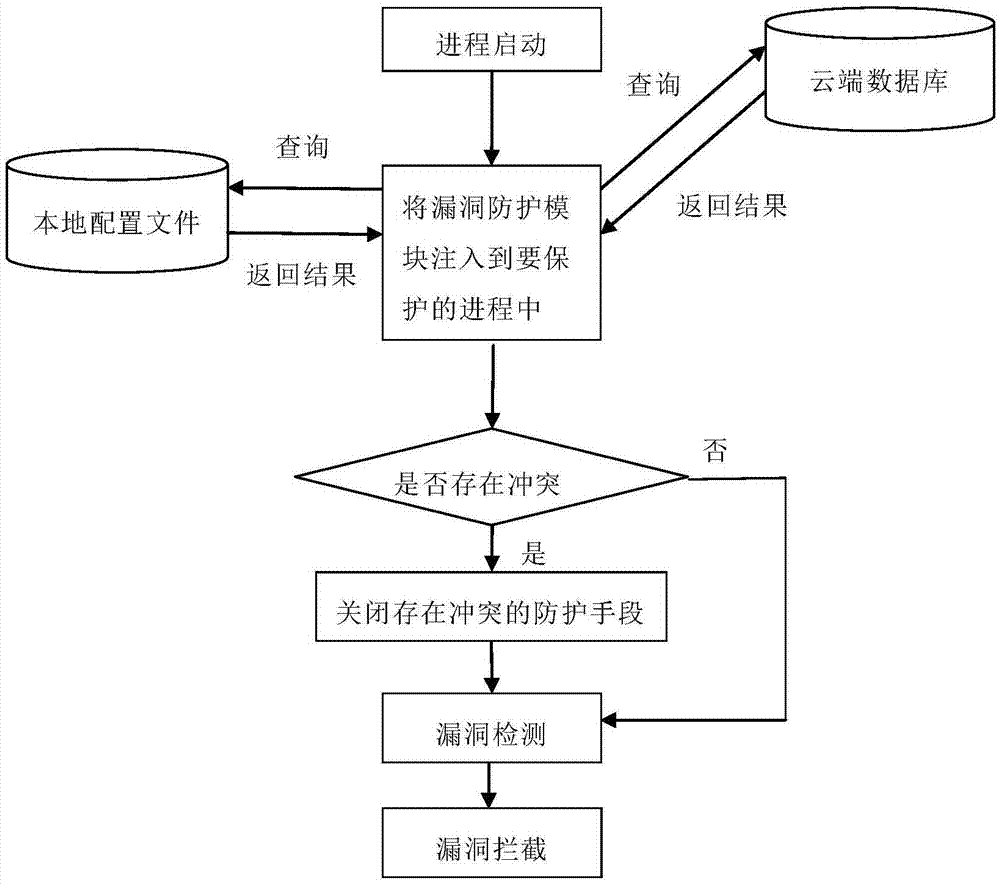
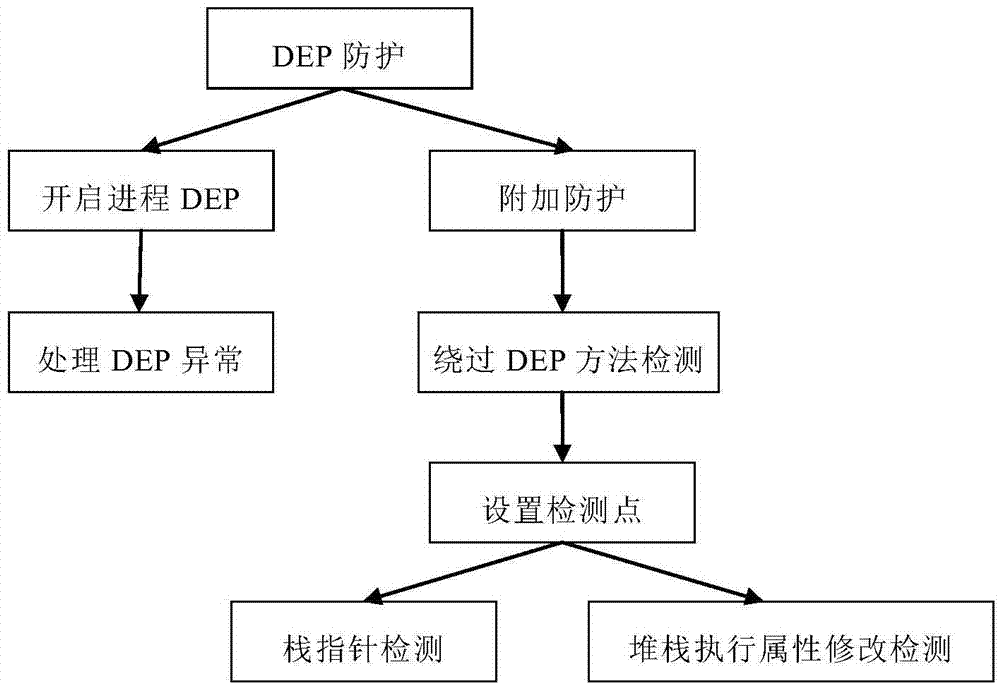
[0037] The present invention mainly detects whether the loophole is running or not based on some abnormalities generated by some methods and characteristics in the exploiting process of the loophole. Once these abnormalities are detected, the loophole will be prevented from running. This feature is not aimed at a specific loophole, so it is universal , as long as the vulnerabilities using similar methods can be detected.
[0038] In this embodiment, the present invention is described in detail by taking the process to be protected as an office word process and the vulnerabilities to be intercepted as some overflow vulnerabilities of office word as an example.
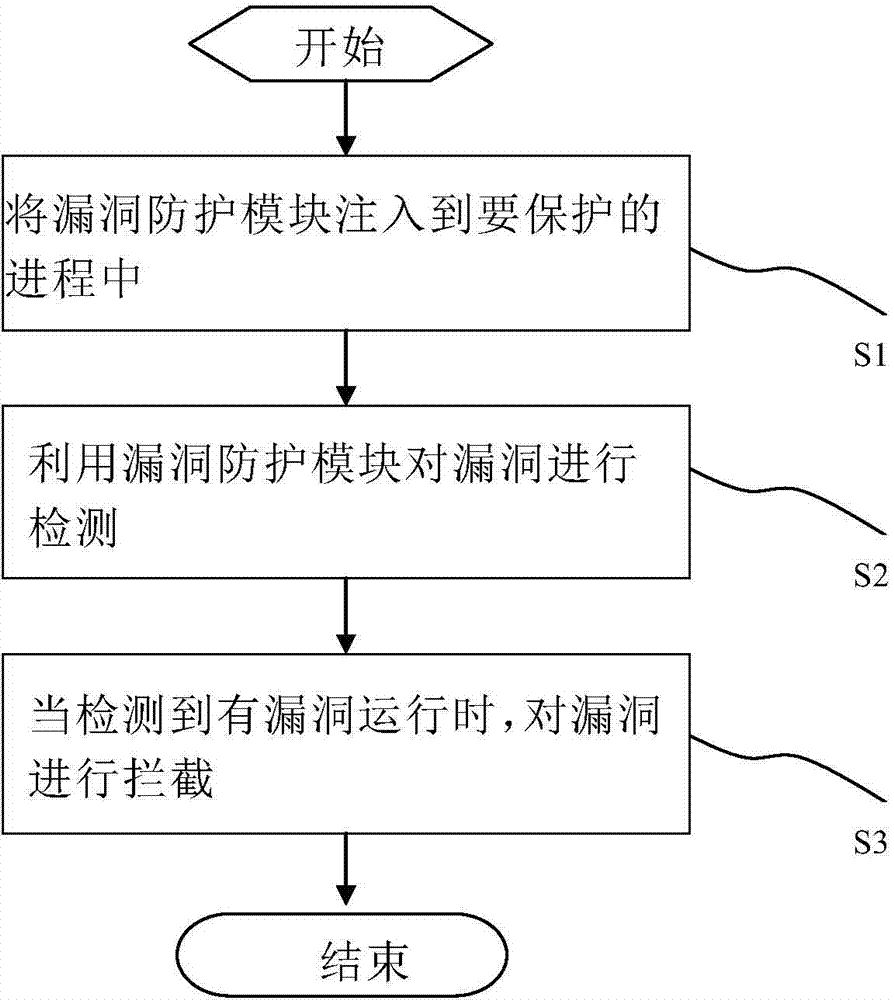
[0039] Such as figure 1 As shown, a vulnerability prevention method includes the following steps:
[0040] Step S1, injecting the vulnerability protection module into the process to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com