Scanning prompt method and device for software vulnerabilities
A software vulnerability and software installation technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as multiple security, hidden dangers, and consumption of computing resources, and achieve the effects of ensuring security, improving security, and reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
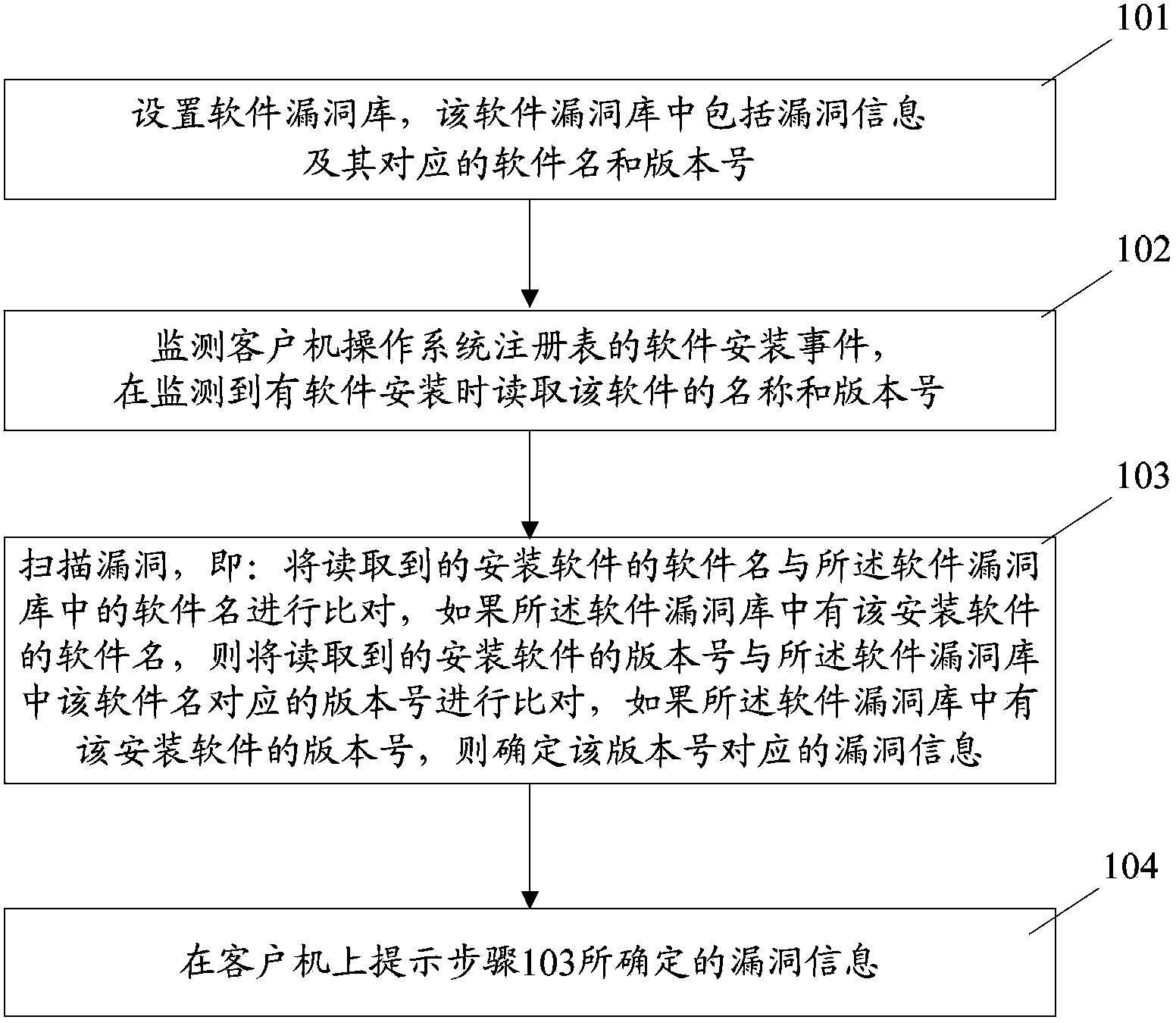
[0027] figure 1 It is a schematic diagram of the main flow of the scanning prompt method for software loopholes in the present invention, see figure 1 , the method includes:
[0028] 101. Set up a software vulnerability database, which includes vulnerability information and its corresponding software name and version number;
[0029] 102. Monitor the software installation event in the registry of the client operating system, and read the name and version number of the software when software installation is detected;
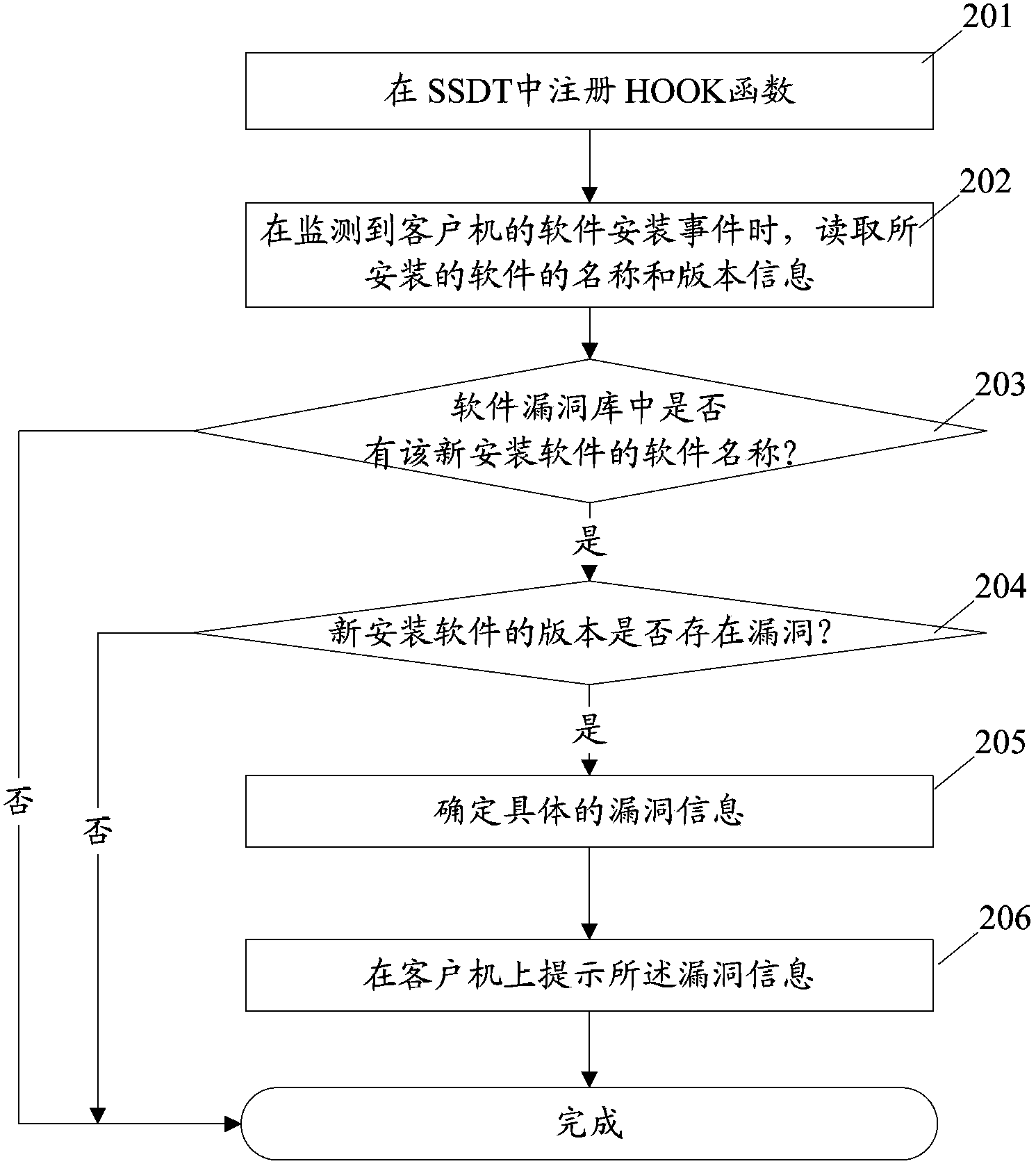
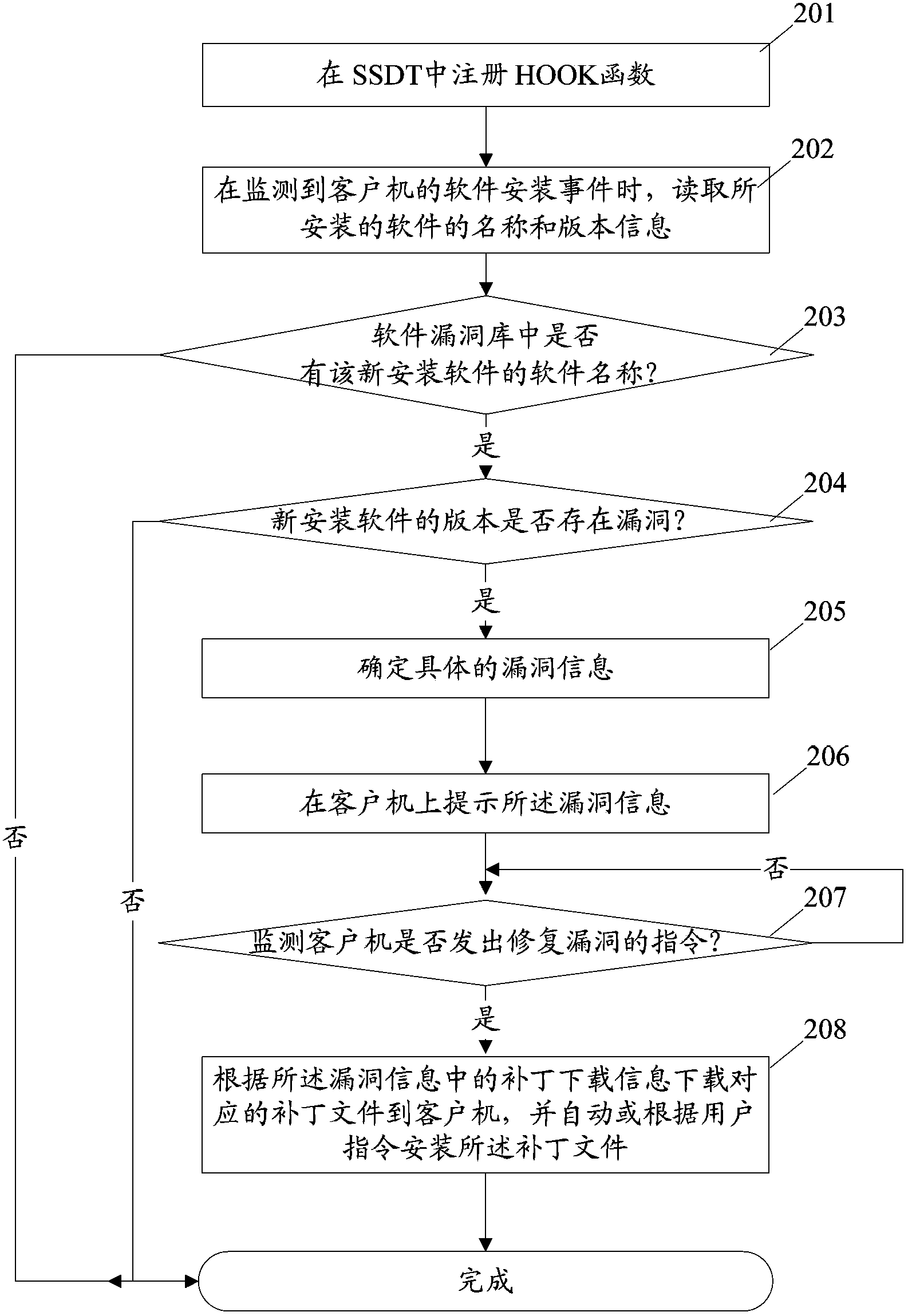
[0030] 103. Scan for vulnerabilities, that is: compare the read software name of the installed software with the software name in the software vulnerability library, if the software name of the installed software is in the software vulnerability library, then read The version number of the installed software obtained ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com