Method and device for detecting Web vulnerability scanning behavior
A vulnerability scanning and detection method technology, which is applied in the detection field of Web vulnerability scanning behavior, can solve the problems of missed scanning requests, false positives, and false negatives of anti-scanning mechanisms, so as to reduce false positives and false positives and improve accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
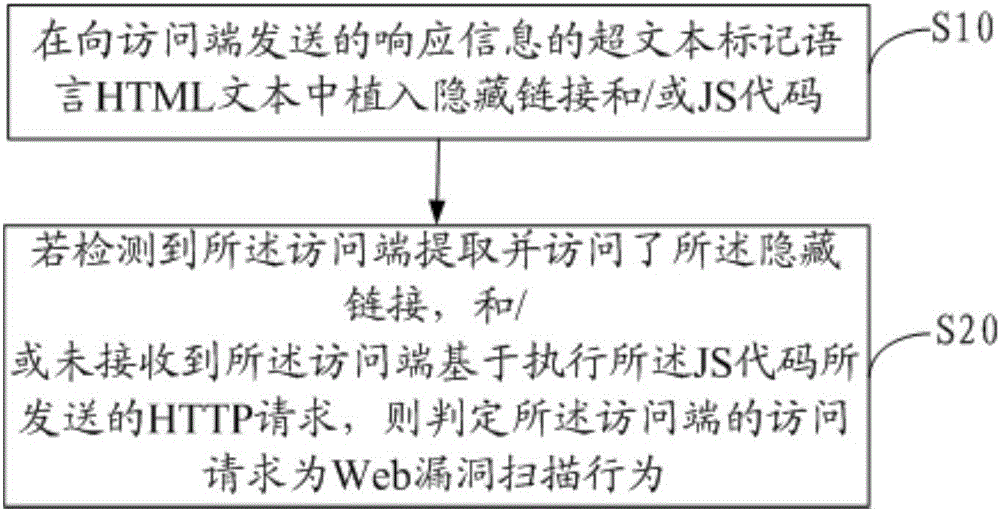
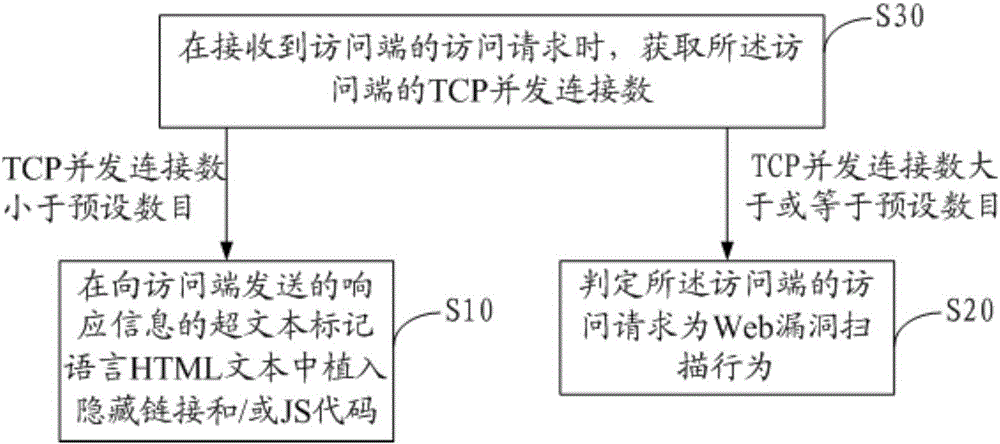
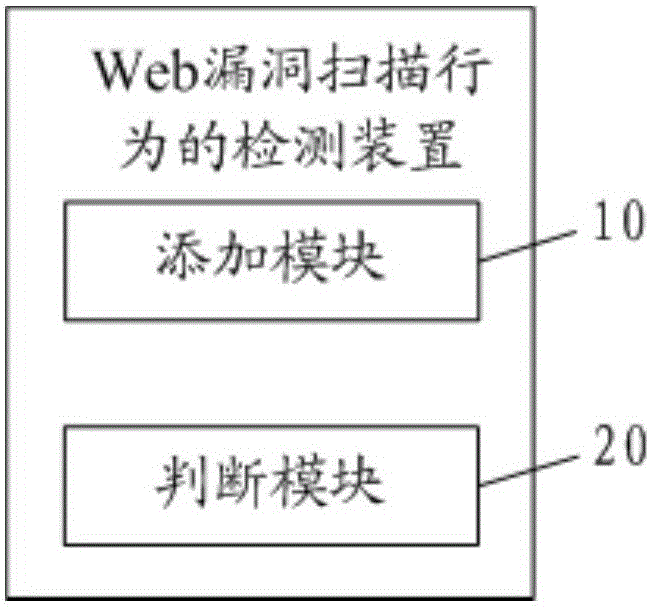
[0108] As an embodiment, the device also includes:
[0109] The second obtaining module is used to obtain the HTTP request frequency of the access terminal within a preset time interval if the number of concurrent TCP connections is less than a preset number;
[0110] The adding module 10 is further configured to embed hidden links and / or JS codes in the hypertext markup language HTML text of the response information sent to the access terminal if the HTTP request frequency is less than the preset frequency.
[0111] The judging module 20 is further configured to judge that the access request of the access terminal is a Web vulnerability scanning behavior if the HTTP request frequency is greater than or lower than the preset frequency.
[0112] Verify the sending frequency of the HTTP request at the access terminal within the preset time interval. If the frequency is greater than the frequency preset by the user, it is determined that the access request of the access terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com