Automatic vulnerability validation method
A verification method and vulnerability technology, applied in the field of information security, can solve problems such as the inability to perform verification loophole utilization, the vulnerability scanning system cannot provide evidence of the existence of loopholes, etc., to improve efficiency and automation, realize data exchange and utilization, and improve automation. degree of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The following will clearly and completely describe the technical solutions in the embodiments of the present invention in conjunction with the accompanying drawings in the embodiments of the present invention; All other embodiments belong to the protection scope of the present invention.
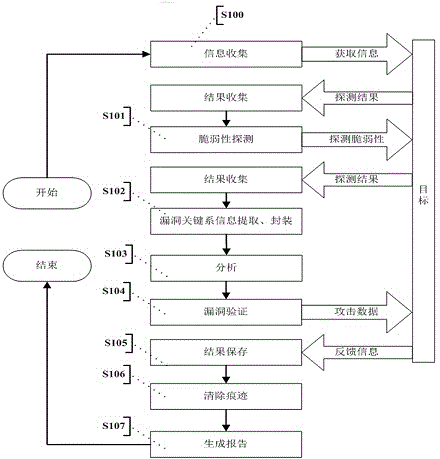
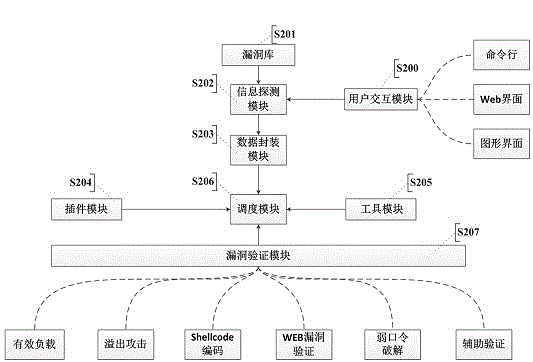
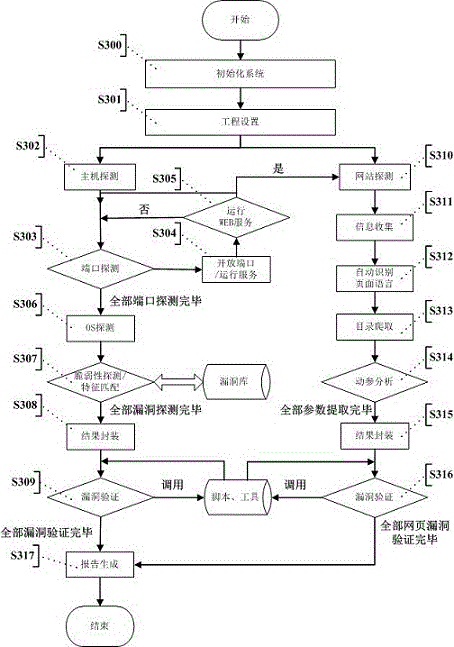
[0045] see figure 1 , is a schematic diagram of an automated vulnerability verification method provided by the present invention, and the specific implementation method is as follows.
[0046] S100: Collect information on the target. If the target is a host system, use active detection to identify the target operating system according to the operating system fingerprint, obtain the machine name of the target machine, and obtain the network topology; then perform port scanning, using TCP port scanning There are two modes of scanning and UDP port scanning; if the target is a web system, it will detect basic information such as the type of the target web server, service version number, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com