Vulnerability scanning system oriented to safety assessment and processing method thereof
A network security assessment and vulnerability scanning technology, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as rough algorithms, large errors in assessment reports, and no early warning function, so as to achieve accurate scanning report results and prevent intrusions. , the effect of accurate and authoritative network security assessment results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
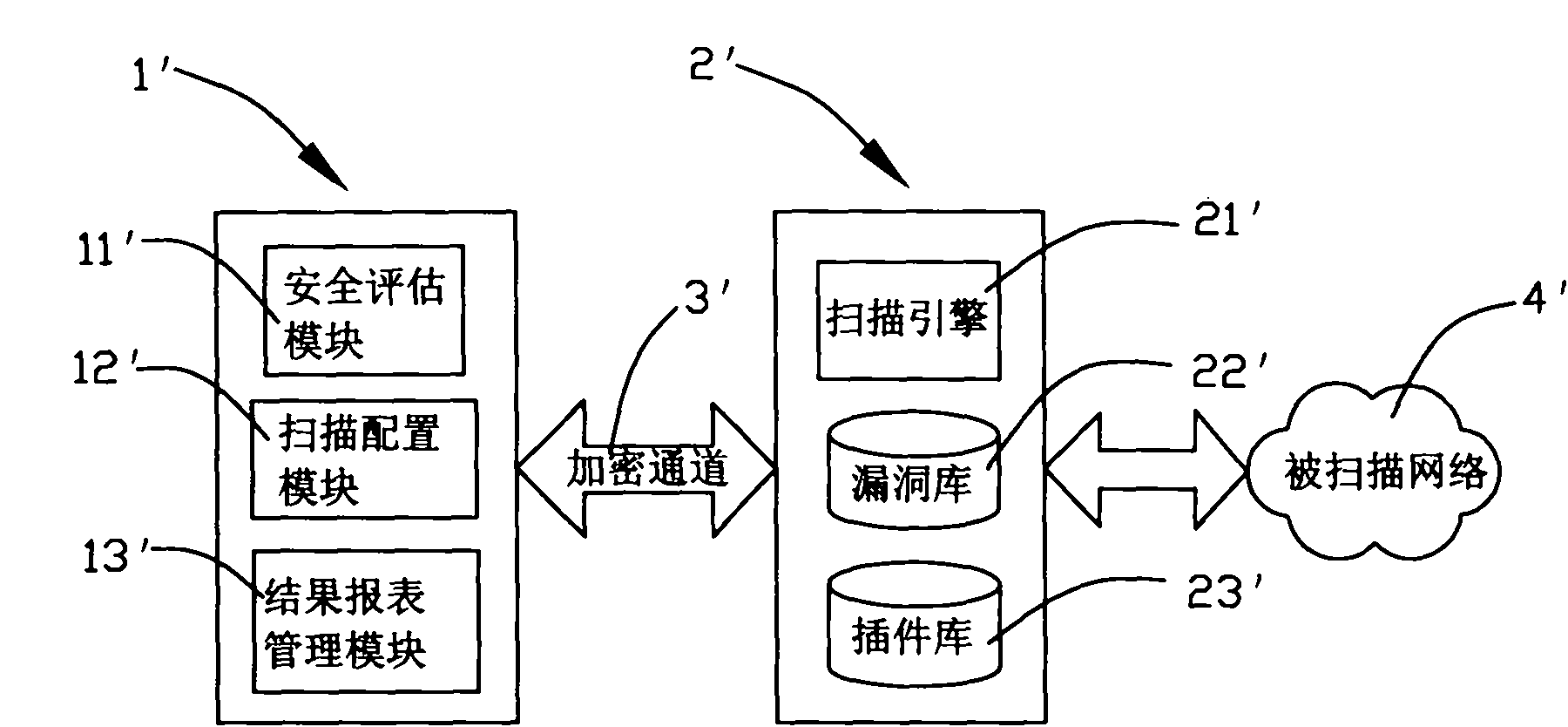
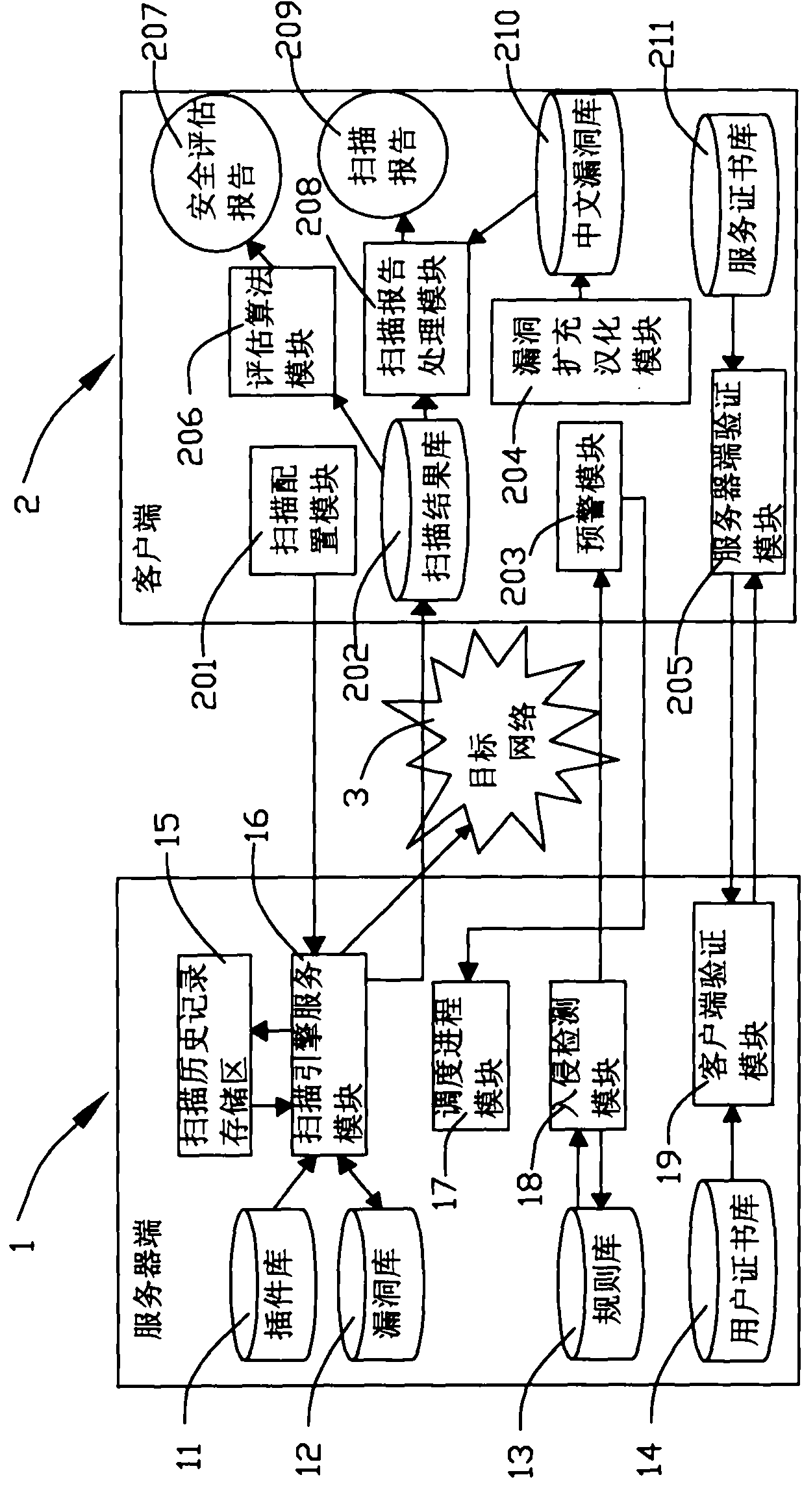
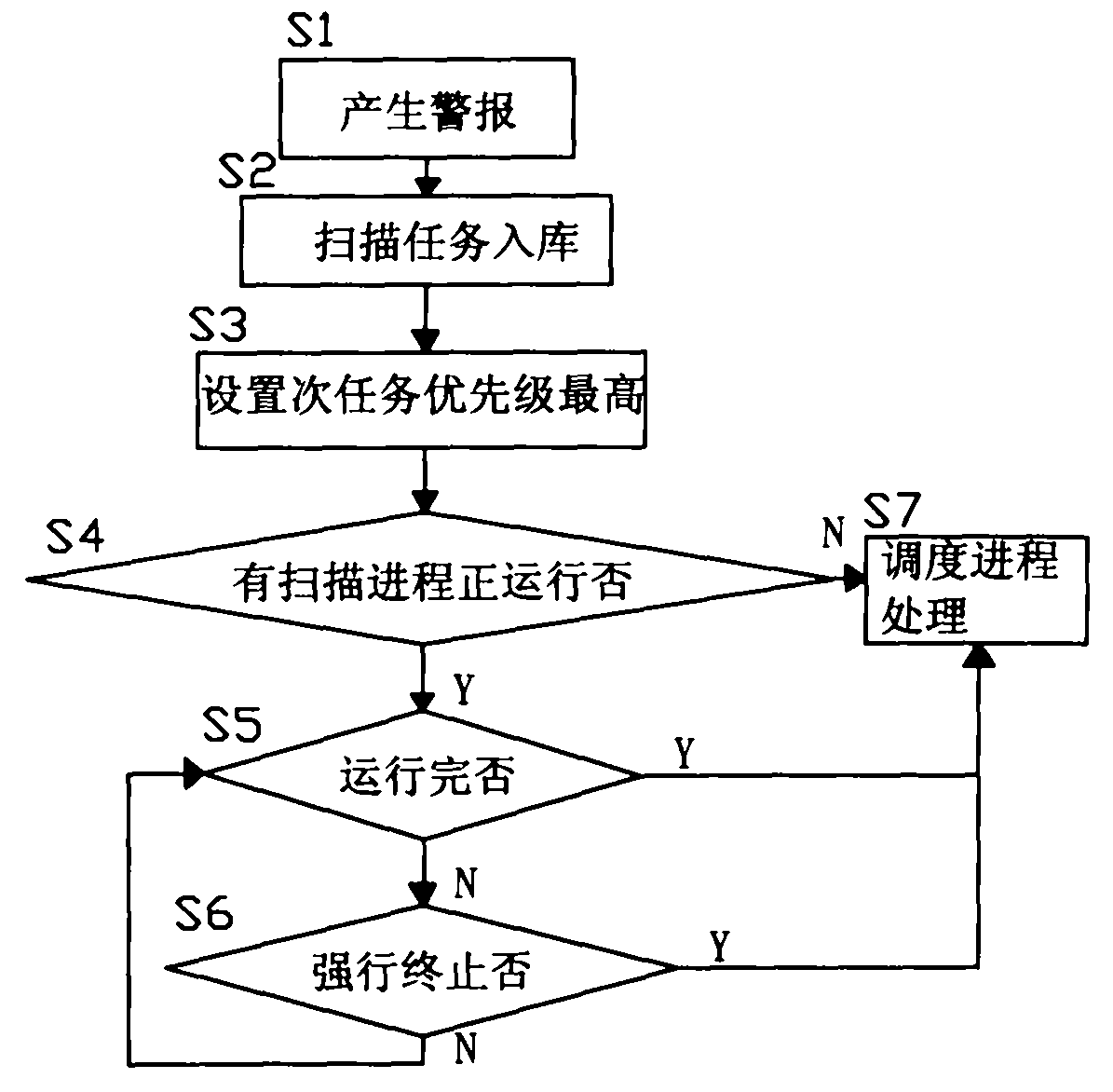
[0056] Examples, see figure 2 As shown, a kind of vulnerability scanning system oriented to network security assessment of the present invention, its vulnerability scanning system comprises server end 1 and client 2 adopting C / S structure, and this server end 1 runs on Unix or Linux platform, and this client end 2 Run on the Windows platform;
[0057] The server-side 1 includes:
[0058] The scanning engine service module 16 is used to accept the request of the client 2 and execute the scanning task; the main function of the scanning engine service module 16 is to be responsible for selecting a specific plug-in from the plug-in library according to user customization, coordinating the relationship between the scanning plug-ins, and executing The scanning program, which stores the results in the scanning history and is responsible for sending them to the client;
[0059] The client verification module 19 is used to accept the request of the client 2 to verify the client cert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com