Method and device for achieving function of security group
A security group and function technology, applied in the field of network communication, can solve problems such as system resource waste, system performance degradation, increased configuration workload, etc., to achieve the effect of avoiding waste and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the purpose, technical solutions and advantages of the present application clearer, the solutions described in the present application will be further described in detail below with reference to the accompanying drawings.
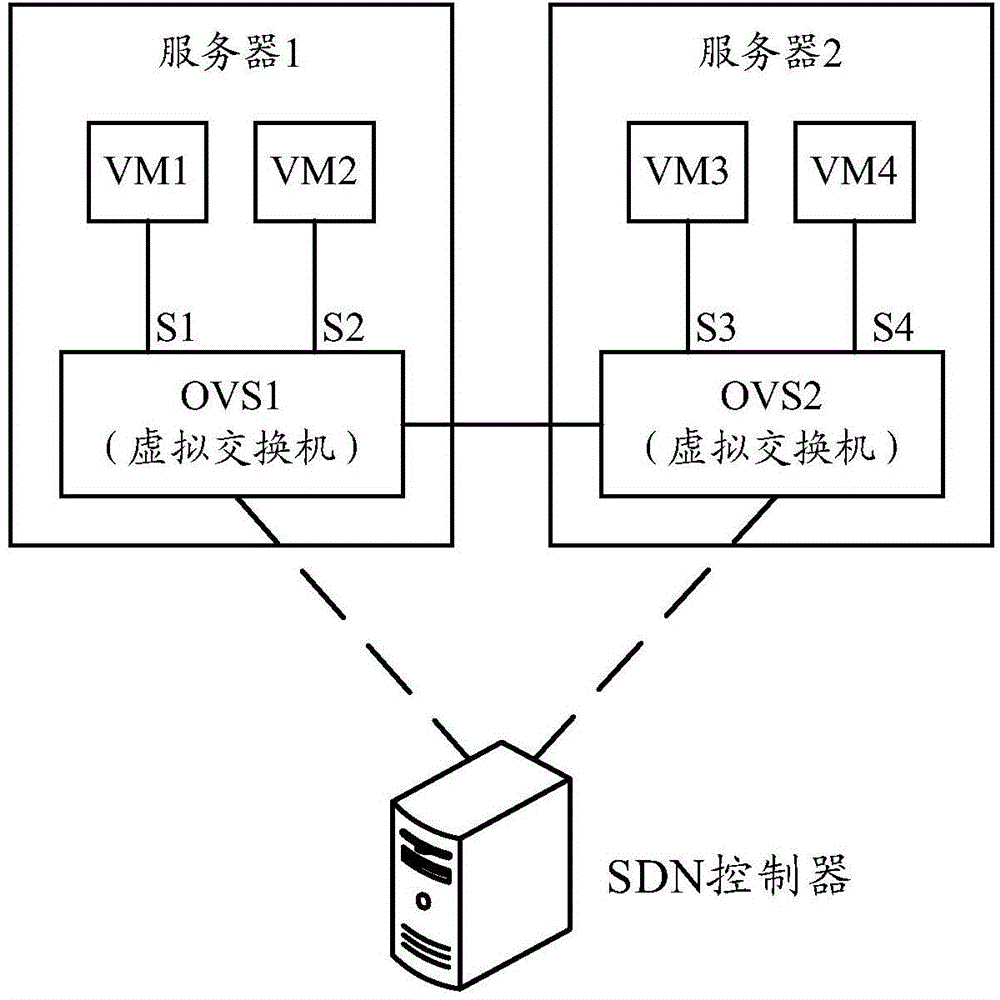
[0020] figure 1 Shown is a schematic diagram of the SDN network structure in the virtual environment. This SDN network comprises server 1, server 2 and controller, wherein, server 1 comprises virtual machine VM1, VM2 and virtual switch OVS1, and VM1 is connected on the port S1 of OVS1, and VM2 is connected on the port S2 of OVS1; Including virtual machines VM3, VM4 and virtual switch OVS2, VM3 is connected to port S3 of OVS2, and VM4 is connected to port S4 of OVS2. The controller instructs the virtual switch to process service packets according to the flow entry by delivering the flow entry to the virtual switch.
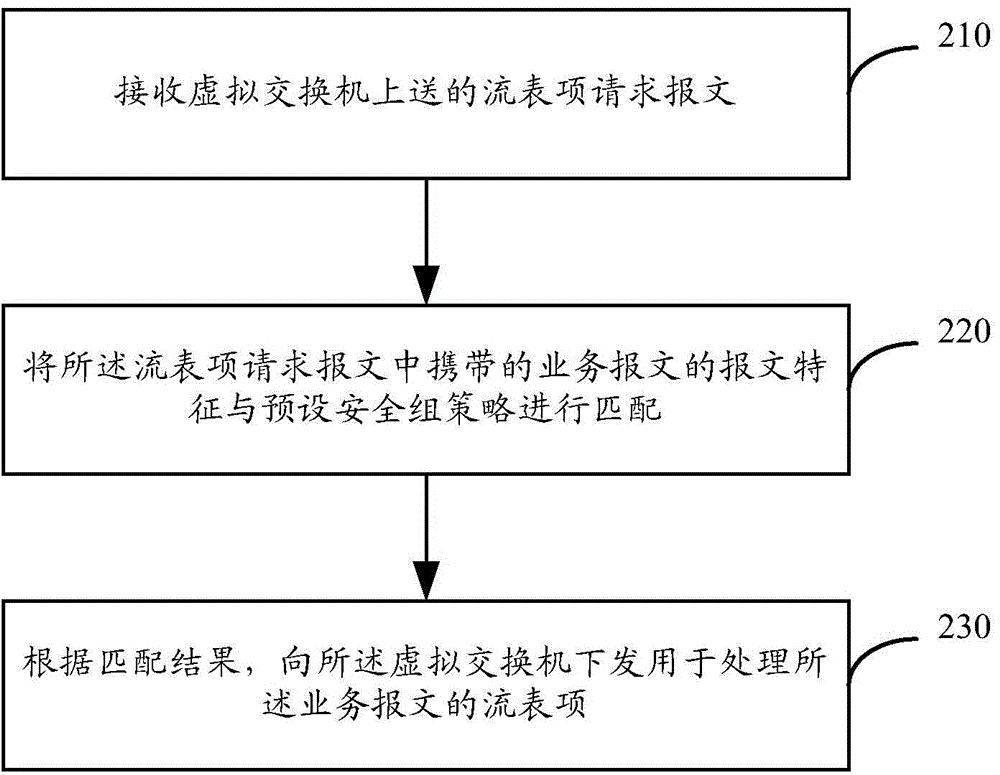
[0021] When implementing security group policies for service packets in an SDN network, the existing technical soluti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com