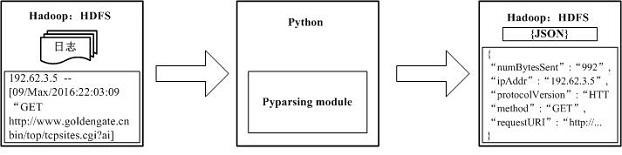
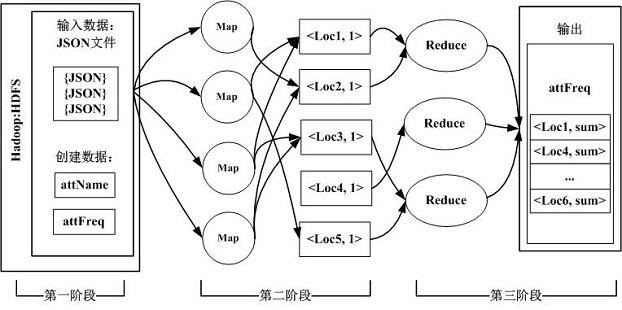
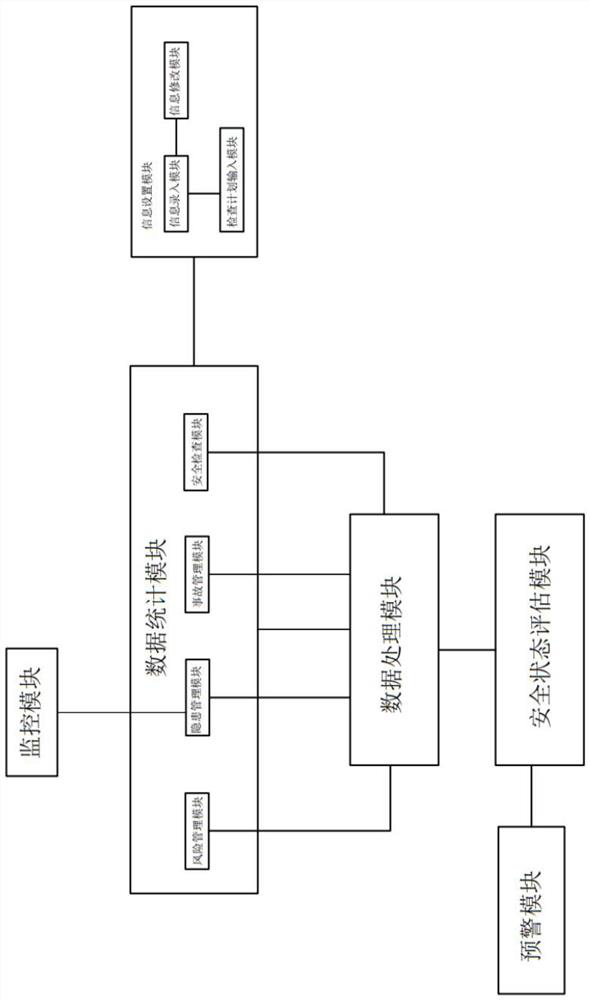
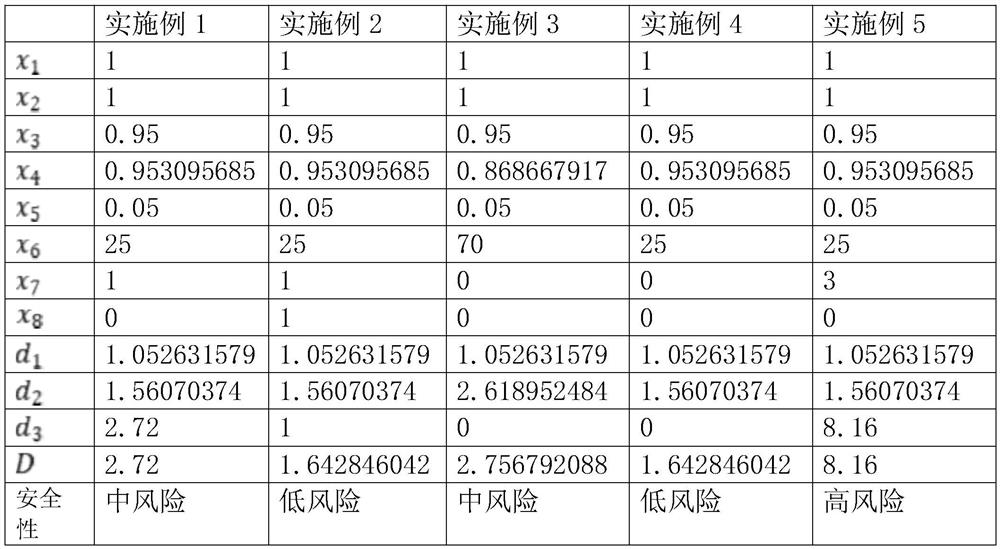
Patents
Literature
38 results about "Corporate security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Corporate security identifies and effectively mitigates or manages, at an early stage, any developments that may threaten the resilience and continued survival of a corporation. It is a corporate function that oversees and manages the close coordination of all functions within the company that are concerned with security, continuity and safety.
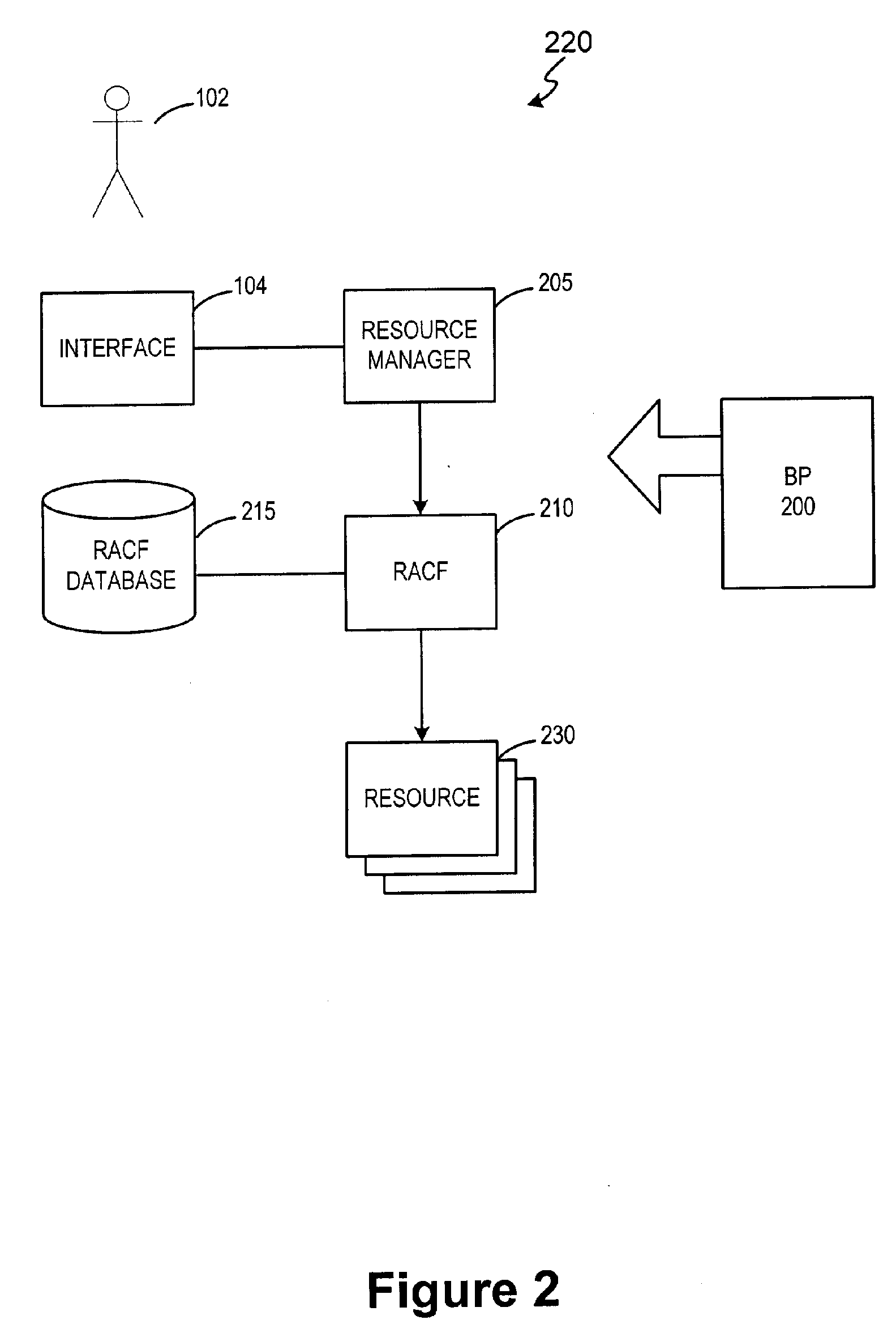
Method of assuring enterprise security standards compliance
ActiveUS20060156408A1Random number generatorsUser identity/authority verificationRisk impactSecurity compliance
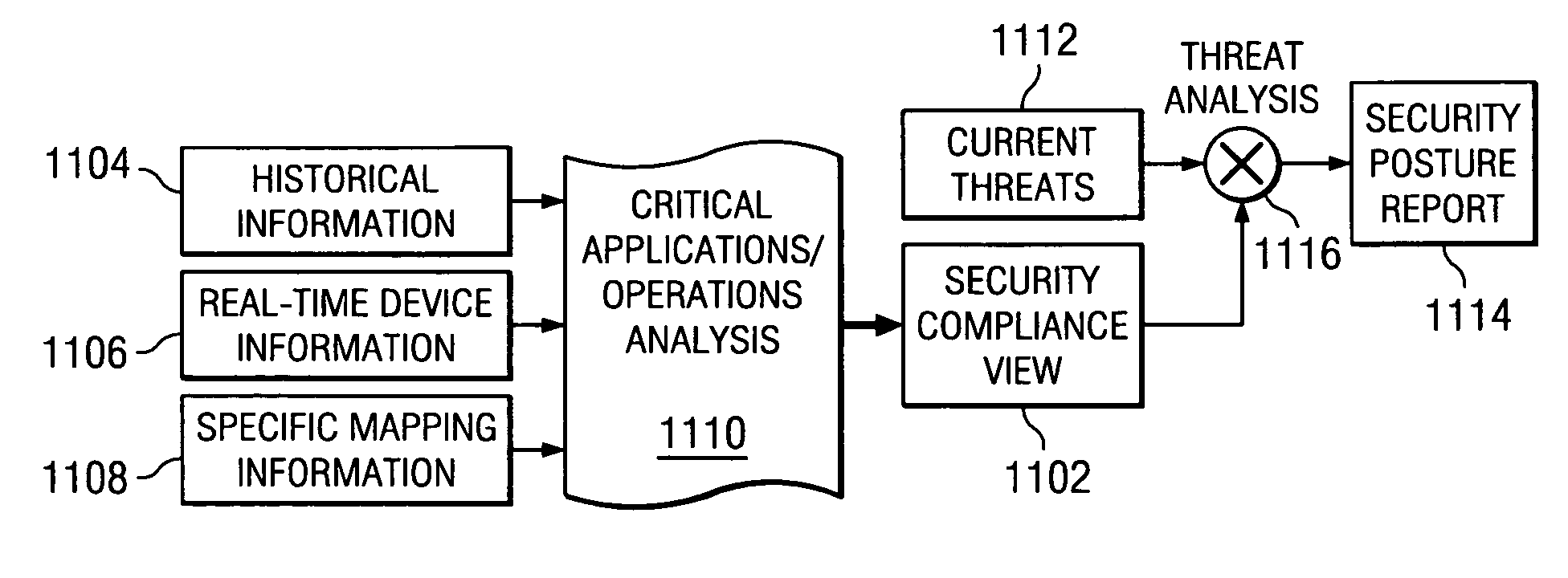
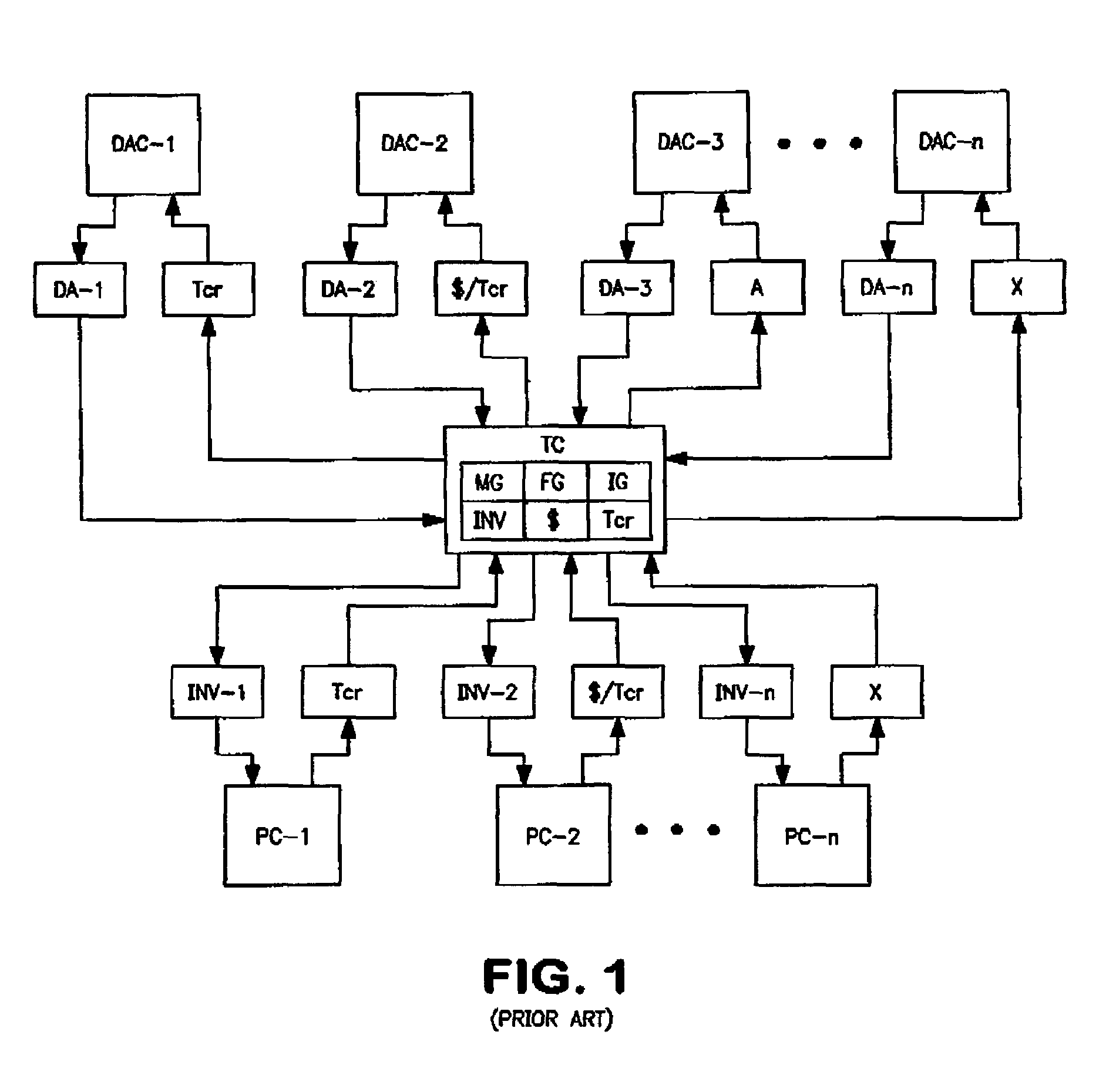
A method, apparatus, and computer instructions for providing a current and complete security compliance view of an enterprise system. The present invention provides the ability to gain a real-time security posture and security compliance view of an enterprise and to assess the risk impact of known threats and attacks to continued business operations at various levels is provided. Responsive to a change to an enterprise environment, a request, or an external threat, an administrator loads or updates at least one of a Critical Application Operations database, a Historical database, an Access Control database, a Connectivity database, and a Threat database. Based on a comparison of information in the databases against similar security data elements from company or external policies, the administrator may generate a Security Compliance view of the enterprise. A Security Posture view may also be generated by comparing the Security Compliance view against data in the Threat database.
Owner:TWITTER INC
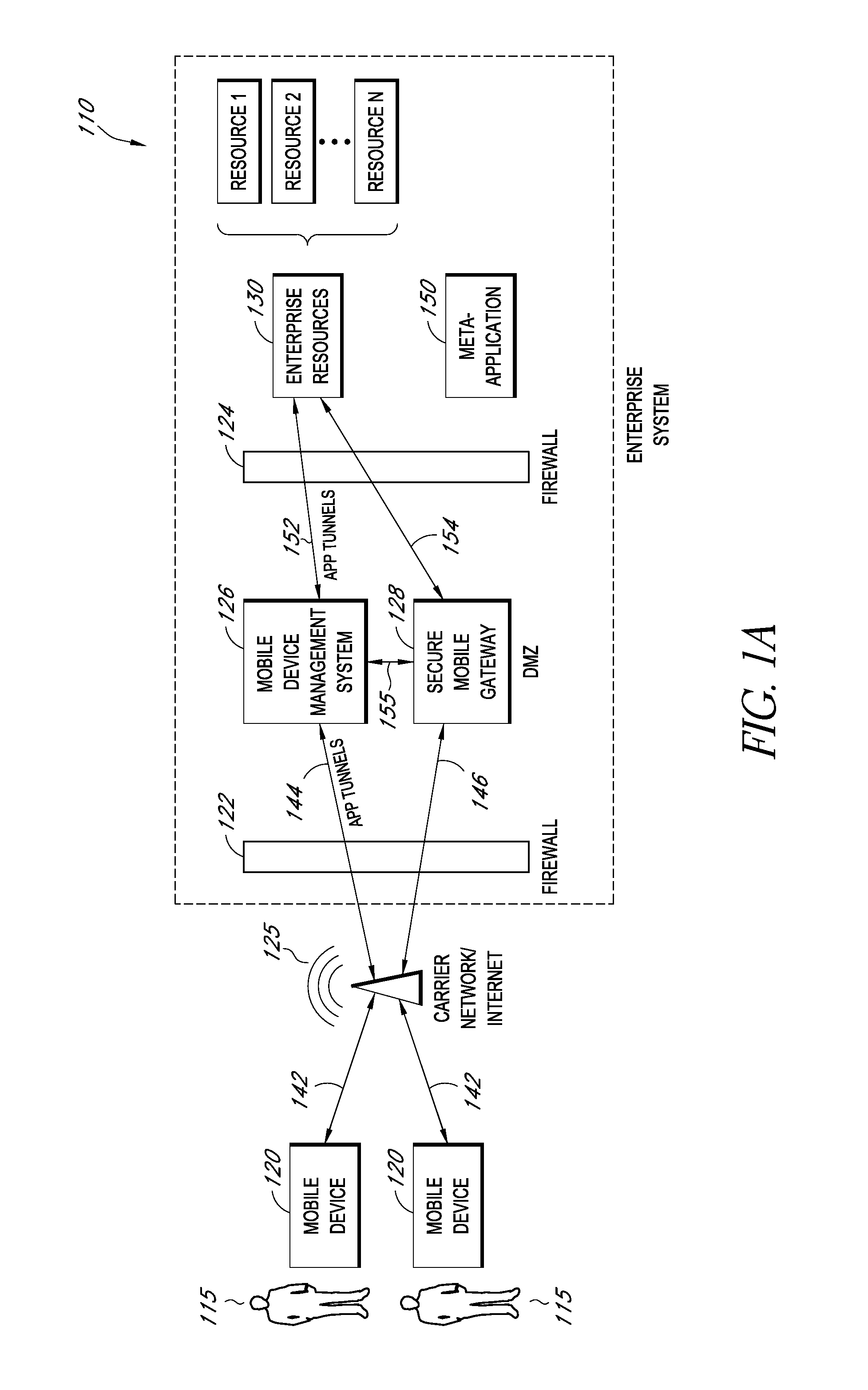
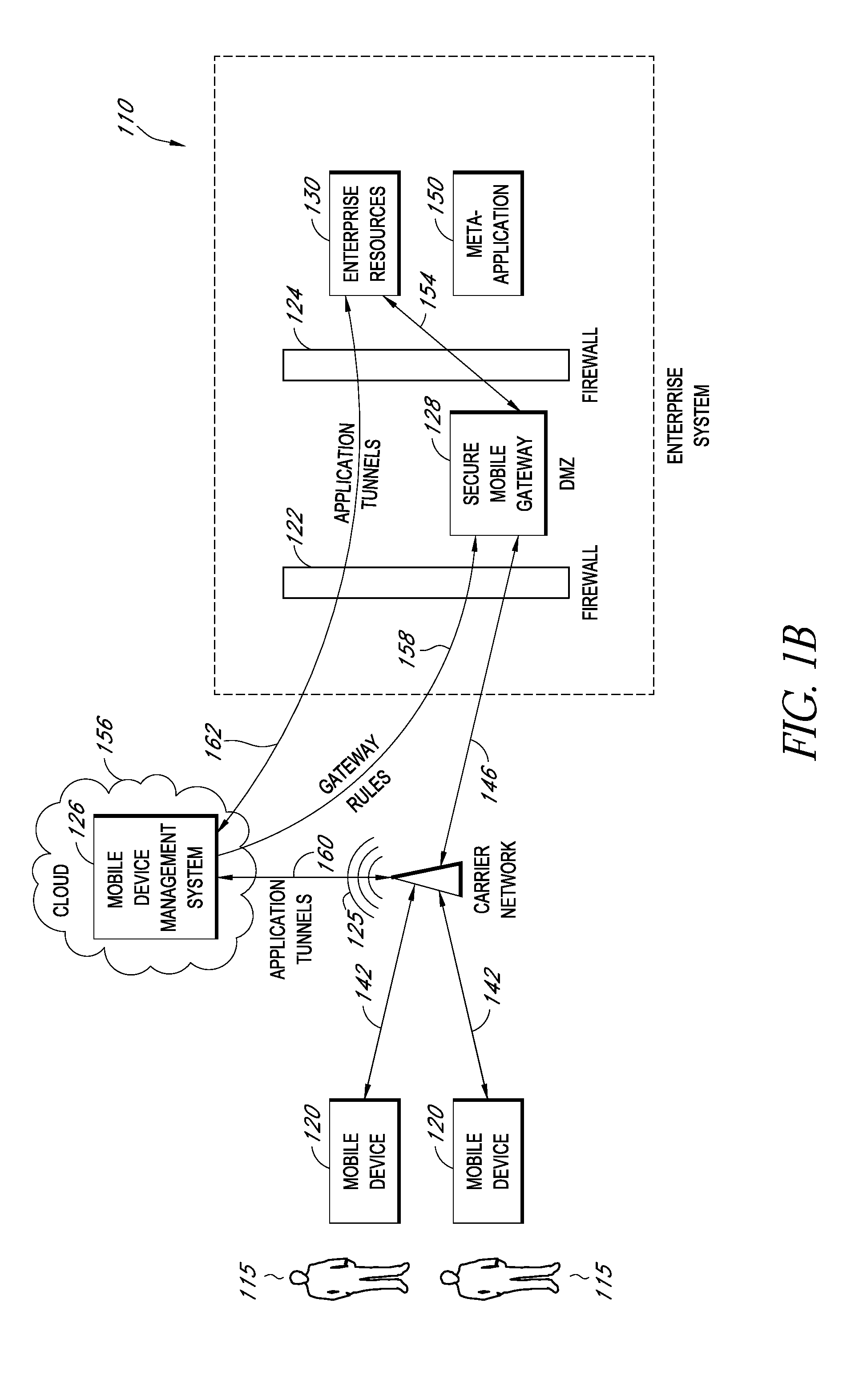
Modifying pre-existing mobile applications to implement enterprise security policies
ActiveUS20140007048A1Decompilation/disassemblyDigital data protectionApplication serverCorporate security
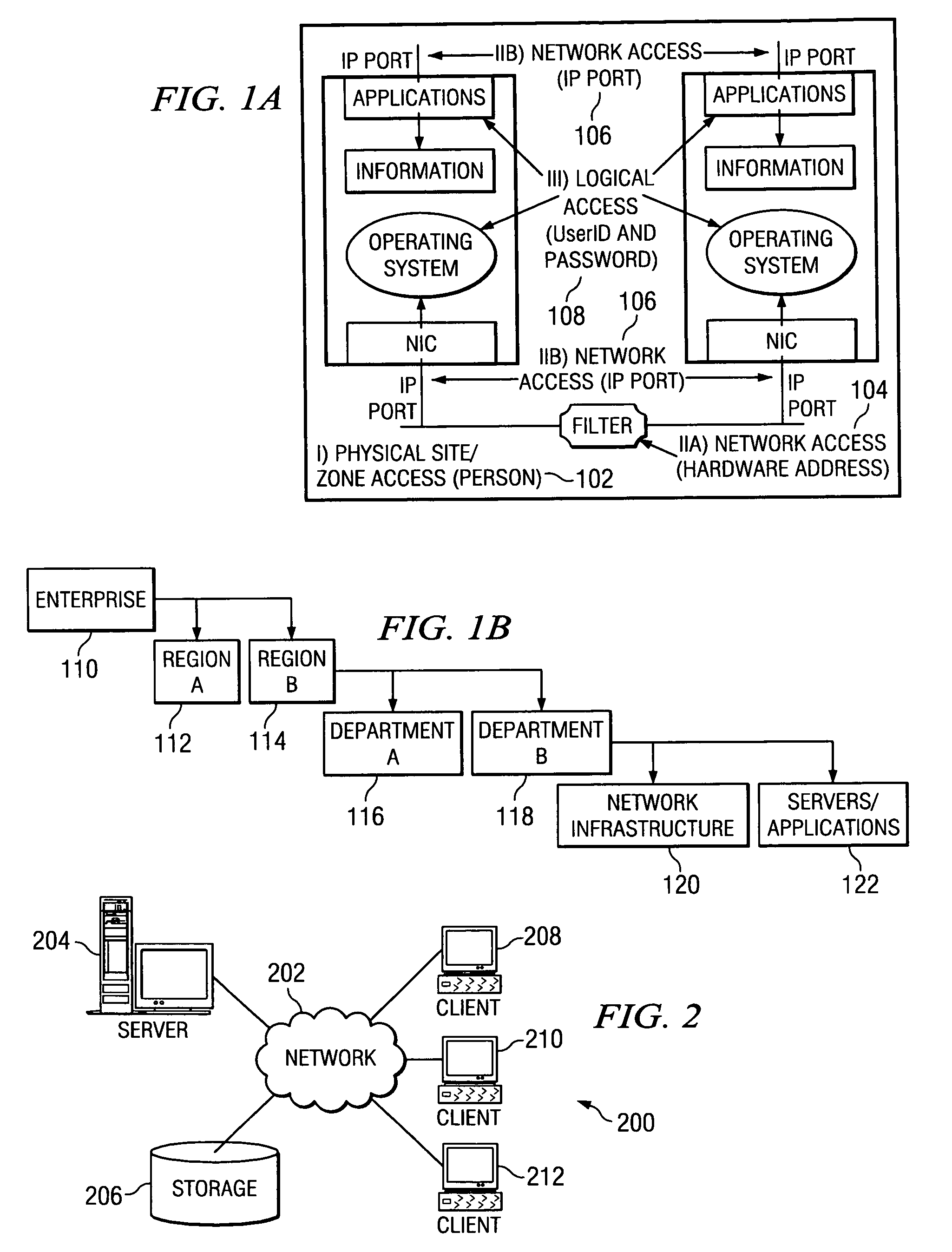
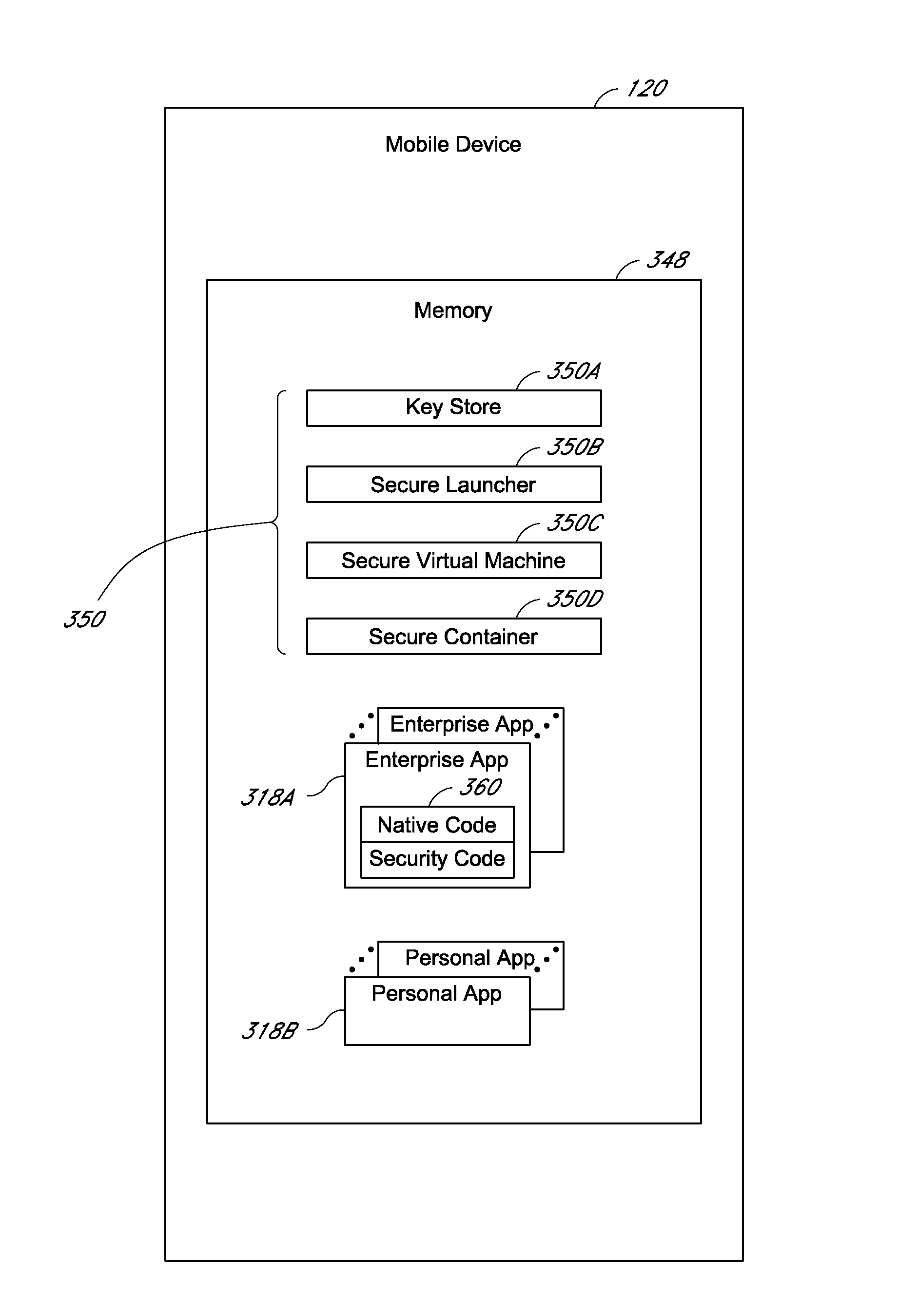
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
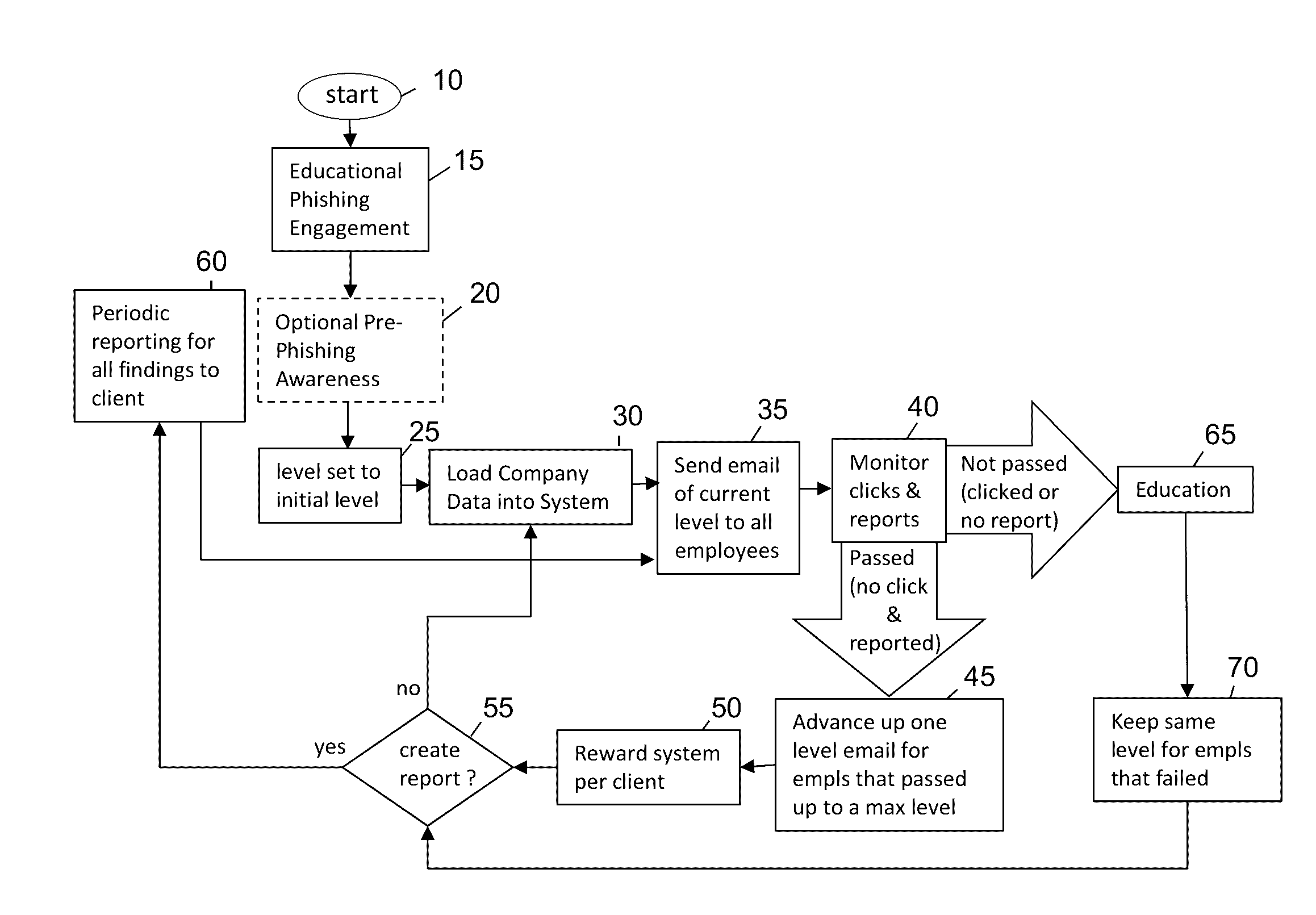
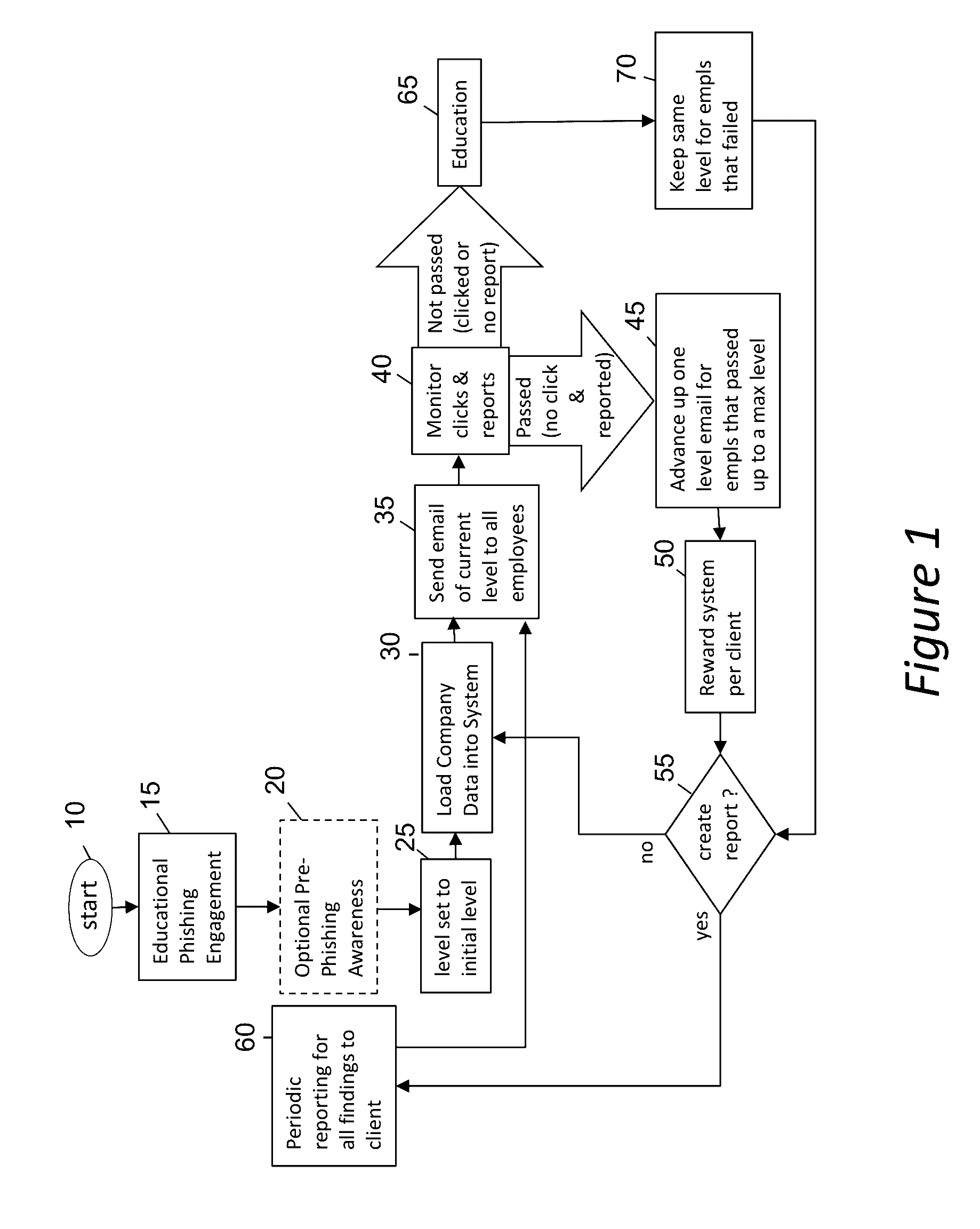
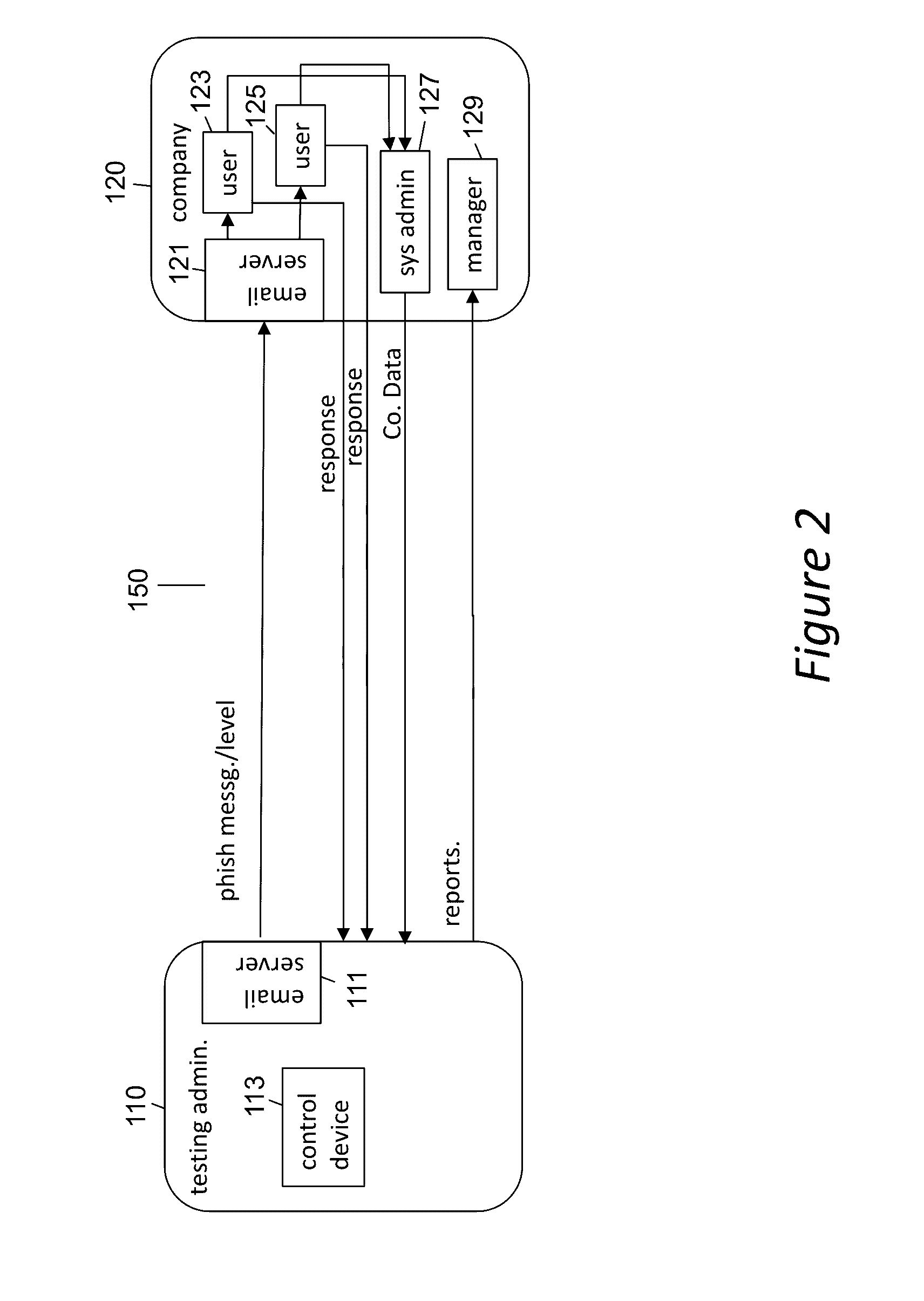
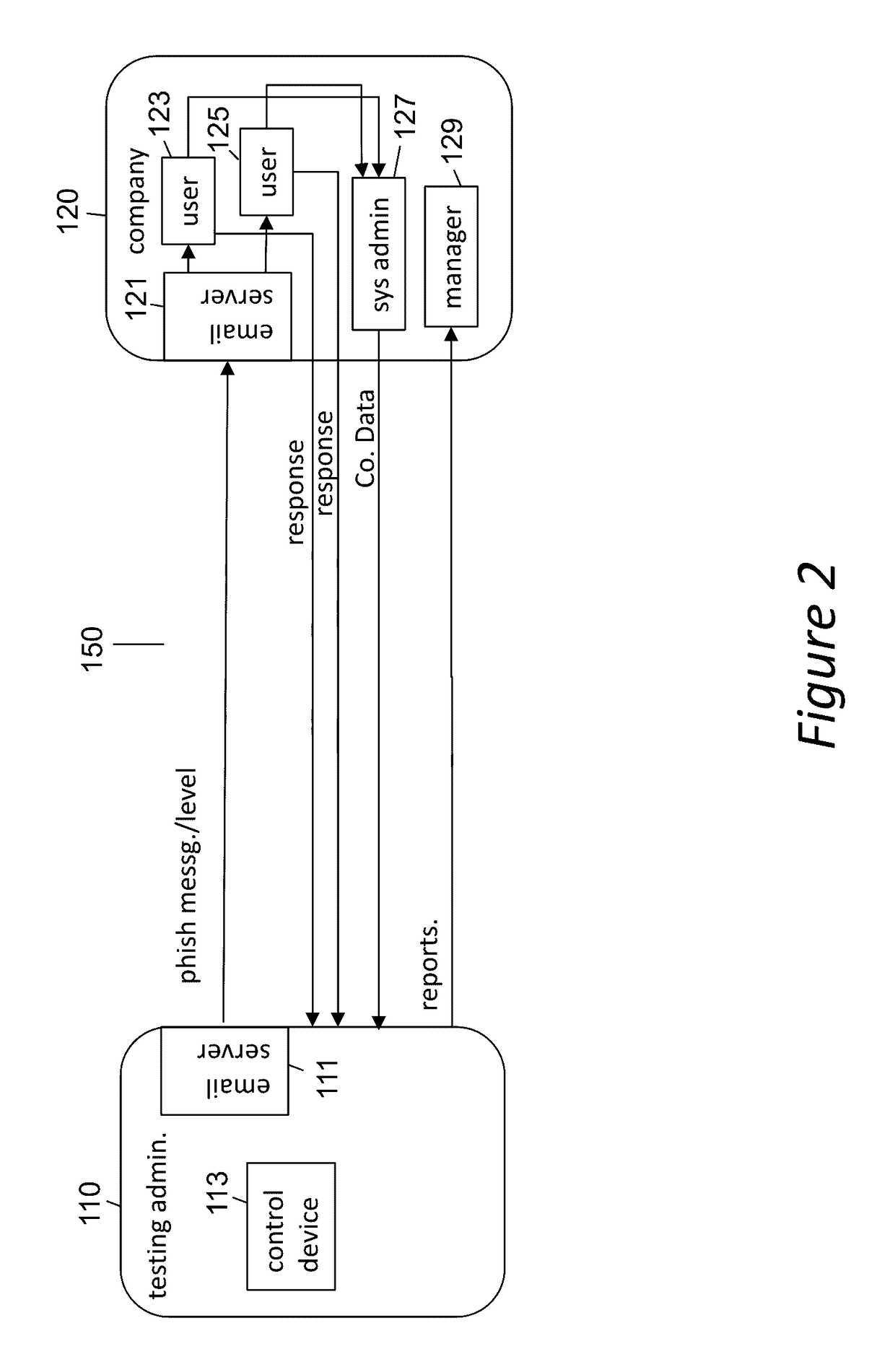
Phishing-as-a-Service (PHaas) Used To Increase Corporate Security Awareness
ActiveUS20160330238A1Increasing corporate information securityImprove the level ofData switching networksMaximum levelThe Internet
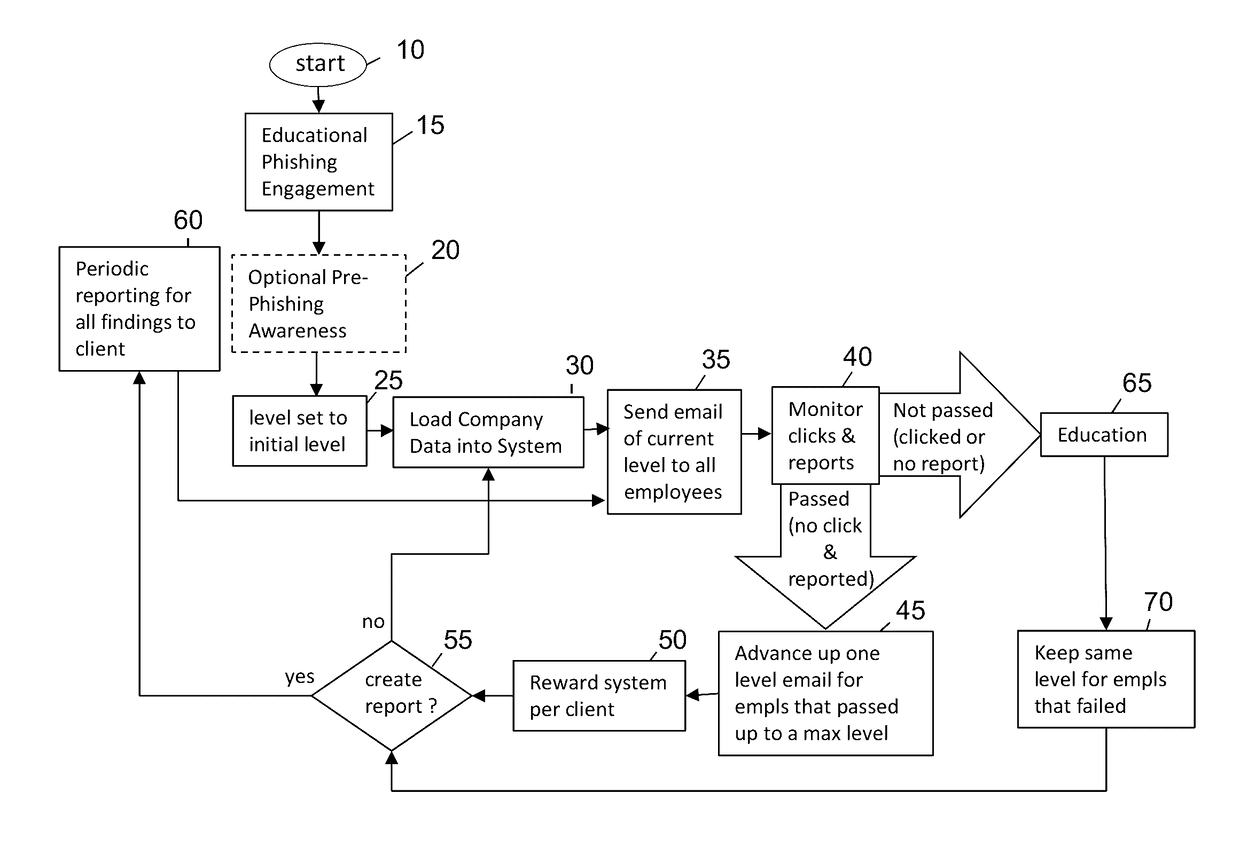
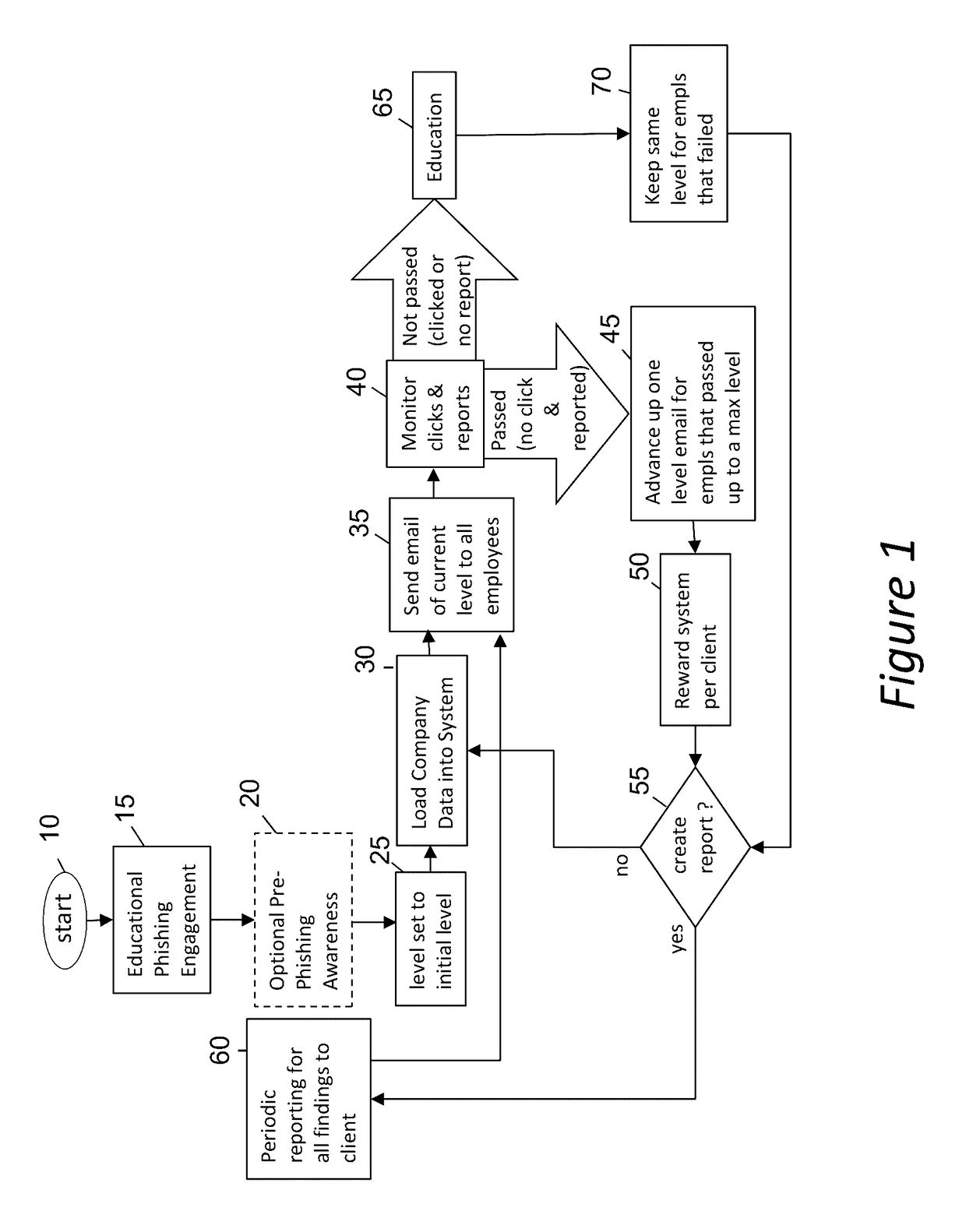
An enhanced system is provided through a network such as the Internet that provides integrated network security (phishing) testing and training. The current system increases corporate security of users that can receive and send electronic messages in an entity, by creating and storing a set of phish messages, each classified by a difficulty level. The electronic addresses of the users are acquired and stored. A current difficulty level is set for all users to an initial level. A phish message of the current difficulty level for a given user is selected and sent to the user. The system monitors if the user clicks on or reports the phish message. If the user does not click on the phish message and reports it, the user's current level is increased up to a maximum level. Those that do not pass the test are provided on-line education. The above steps are repeated for all users until the testing is completed providing targeted phishing education to those which need it most.
Phishing as-a-service (PHaas) used to increase corporate security awareness
ActiveUS9635052B2Increasing corporate information securityImprove the level ofData switching networksMaximum levelThe Internet
Owner:HADNAGY CHRISTOPHER J
Enterprise security monitoring system and method
InactiveUS20060136986A1Memory loss protectionDetecting faulty computer hardwarePush technologySecurity solution
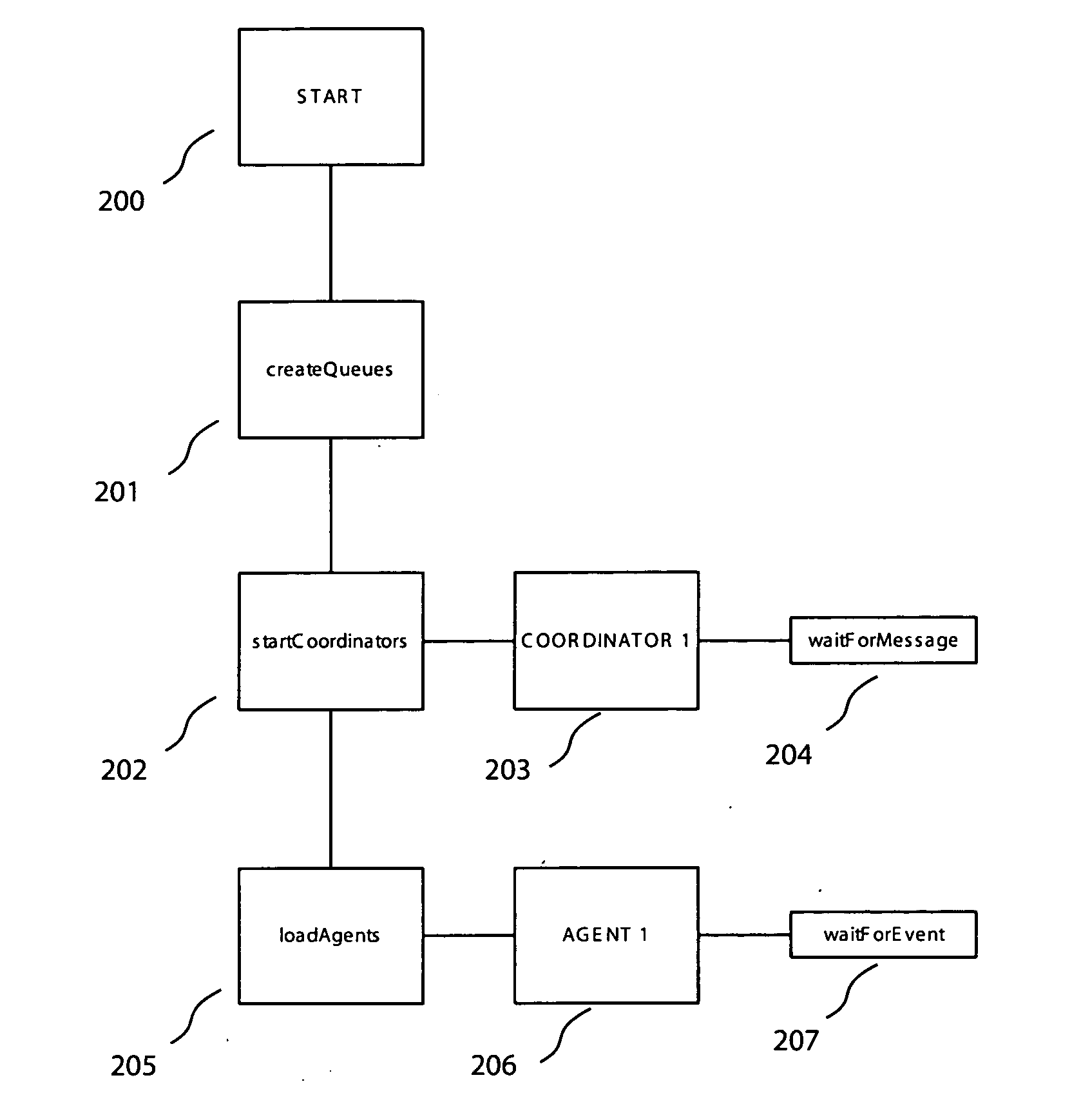
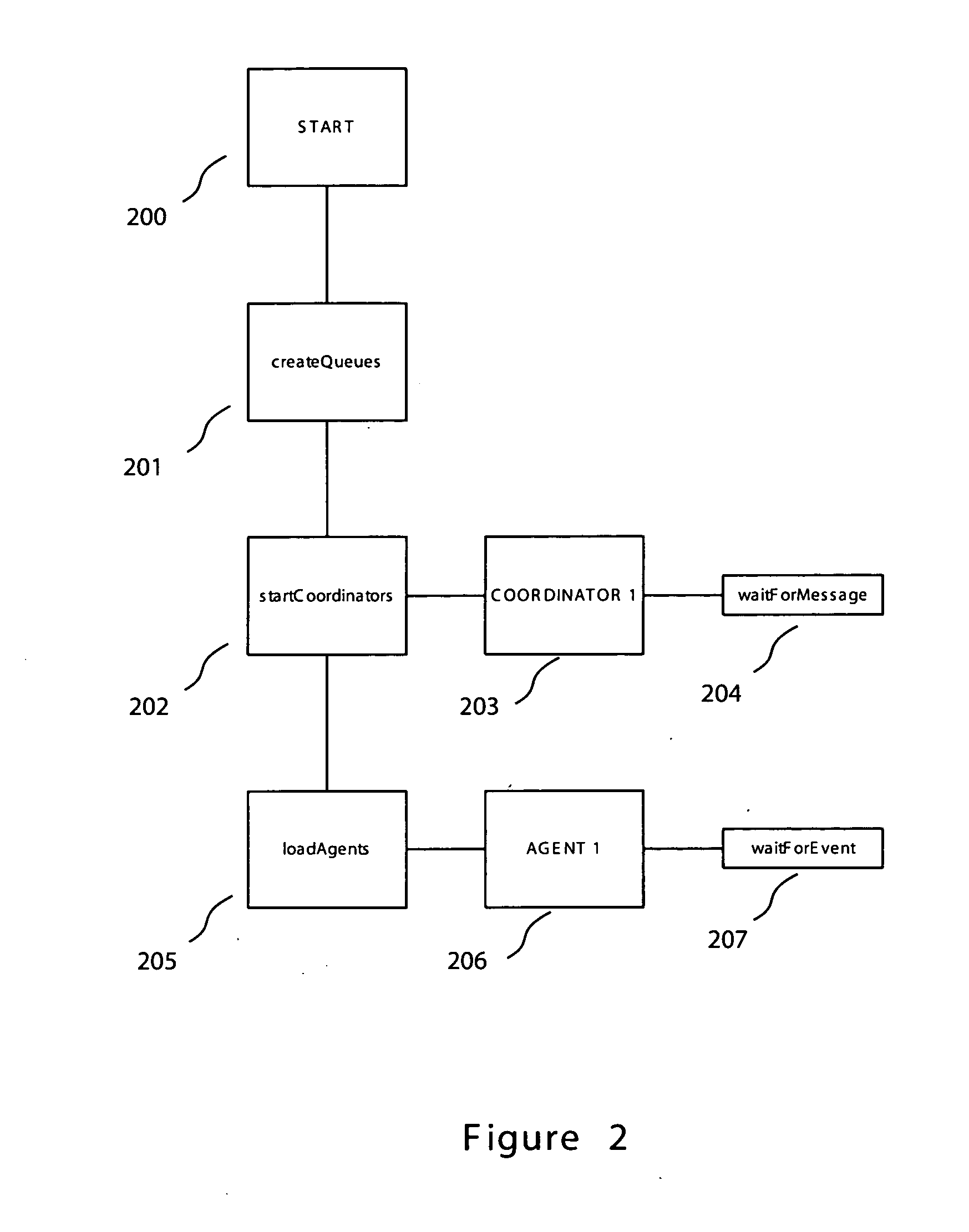
Embodiments of the invention provide an enterprise security solution wherein each network node itself enforces a predetermined security policy. In these embodiments, platform independent agents and coordinators run on any type of network node and require no central server to implement policy are utilized. With no requirement for access to a server, the security policy of a network node may be enforced without an operable network connection. Agents are responsible for monitoring, recording and reporting attempted violations of predetermined security policies of an enterprise. Agents may be general agents and may be written in a platform independent language or may be special agents that may comprise platform specific code whether written in a platform independent language or not. Coordinators are responsible for configuring, controlling and providing support services such as routing to the agents. Agent and coordinator functionality may be combined into one component if desired. Agents and coordinators are capable of terminating processes on network nodes that they are monitoring. A policy may be specific to a device, user, group or enterprise or any combination thereof. Agents and coordinators may be deployed via disks, via the network via push technologies, or via download from the network. After agents and coordinators have been installed on a network node the security policy is enforced and may not be terminated without administrator privilege. Embodiments of the invention may be controlled and administered remotely without technical support at each network node site from any location hosting an administrator. This allows for flexible administration that is not dependent on the location of the administrator. In addition, since network connections may become inactive, it is possible for an administrator to change locations while administering a network node.
Owner:ERGOMD +1
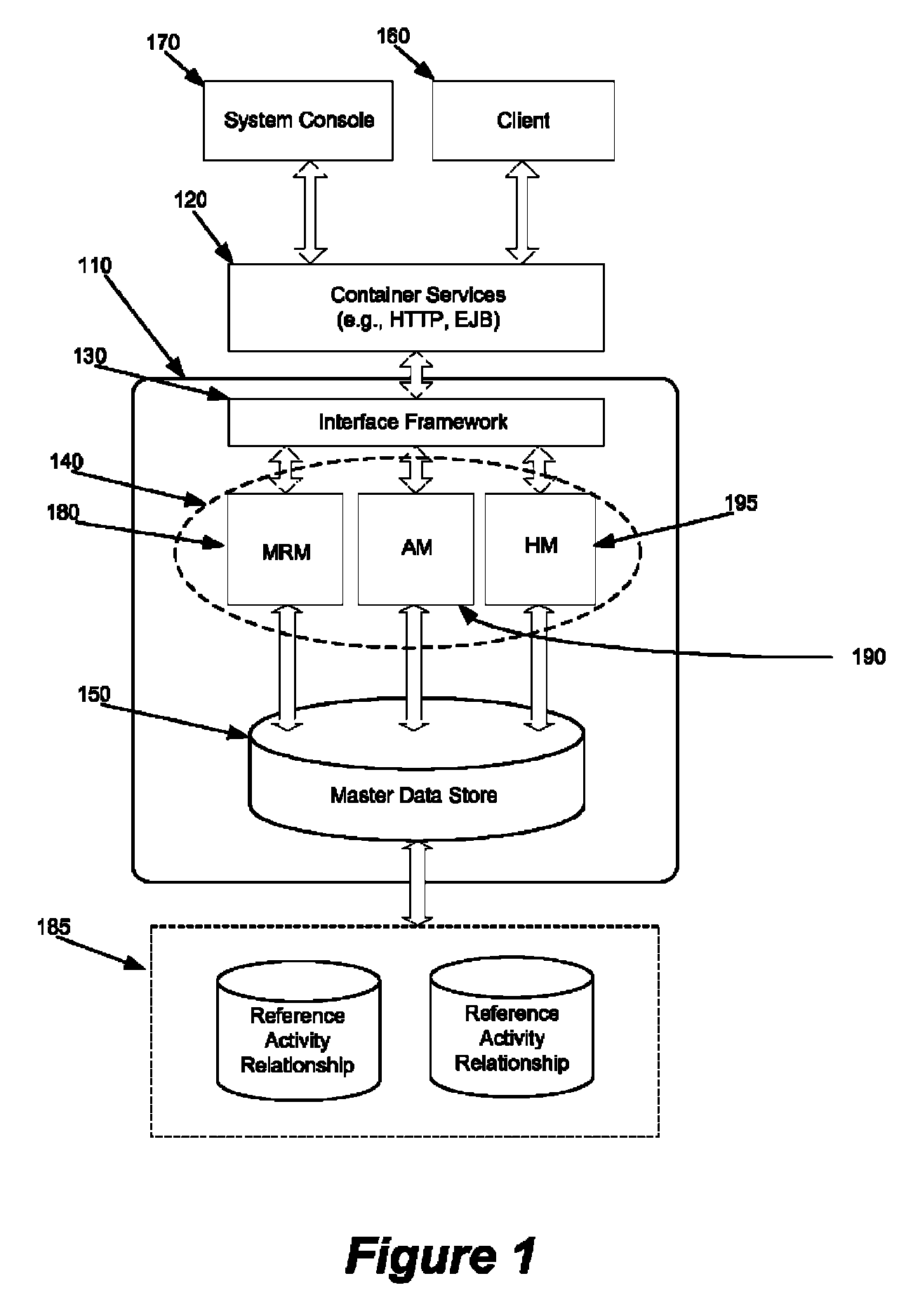
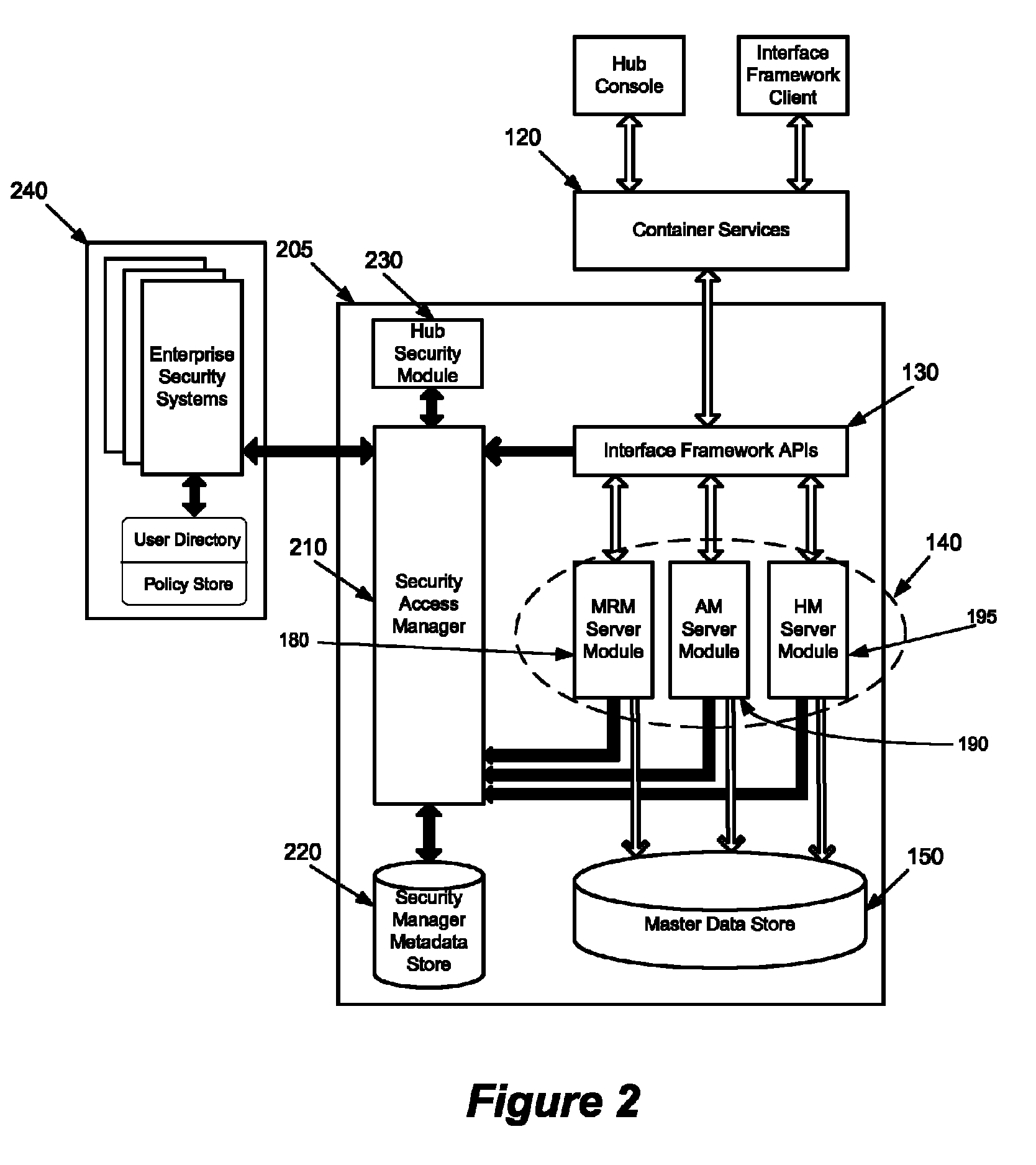
System and method for flexible security access management in an enterprise
ActiveUS8224873B1Digital data processing detailsComputer security arrangementsAccess managementAuthorization
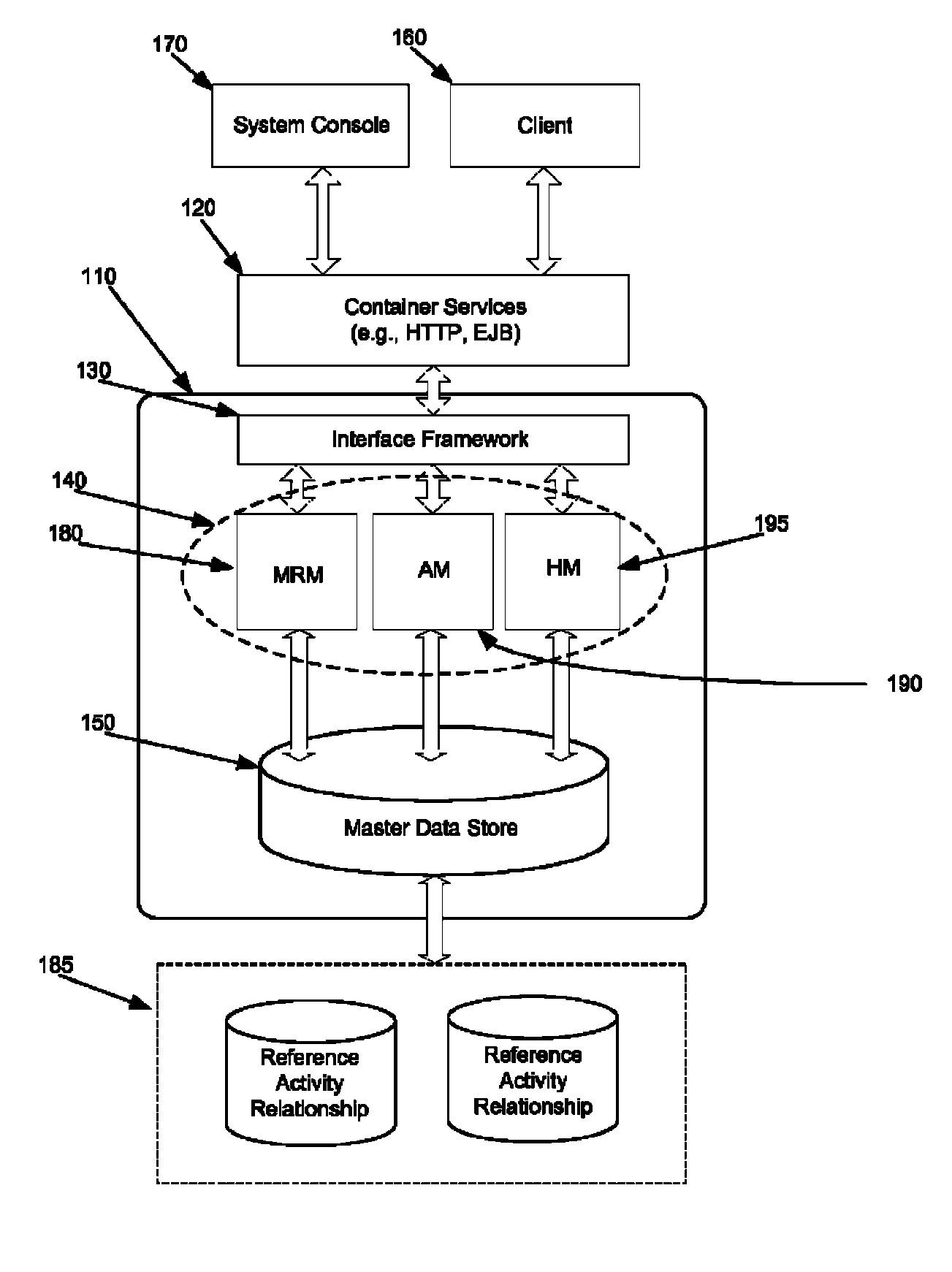
Some embodiments provide a method and system for flexibly managing access to enterprise resources. To flexibly manage security, some embodiments secure the enterprise resources and provide a security access manager (SAM) to control access to the secured resources. The SAM controls access to the enterprise and the secure resources through one or more configurable management modules of the SAM. Each management module of the SAM is configurable to facilitate control over different security services of an enterprise security hierarchy (e.g., authentication, authorization, role mapping, etc.). Specifically, each management module is configurable to leverage security services that are provided by different security systems. In some embodiments, the management module is configured to interface with one or more adapters in order to establish the interfaces, logic, and protocols necessary to leverage the security functionality of such security systems.
Owner:INFORMATICA CORP
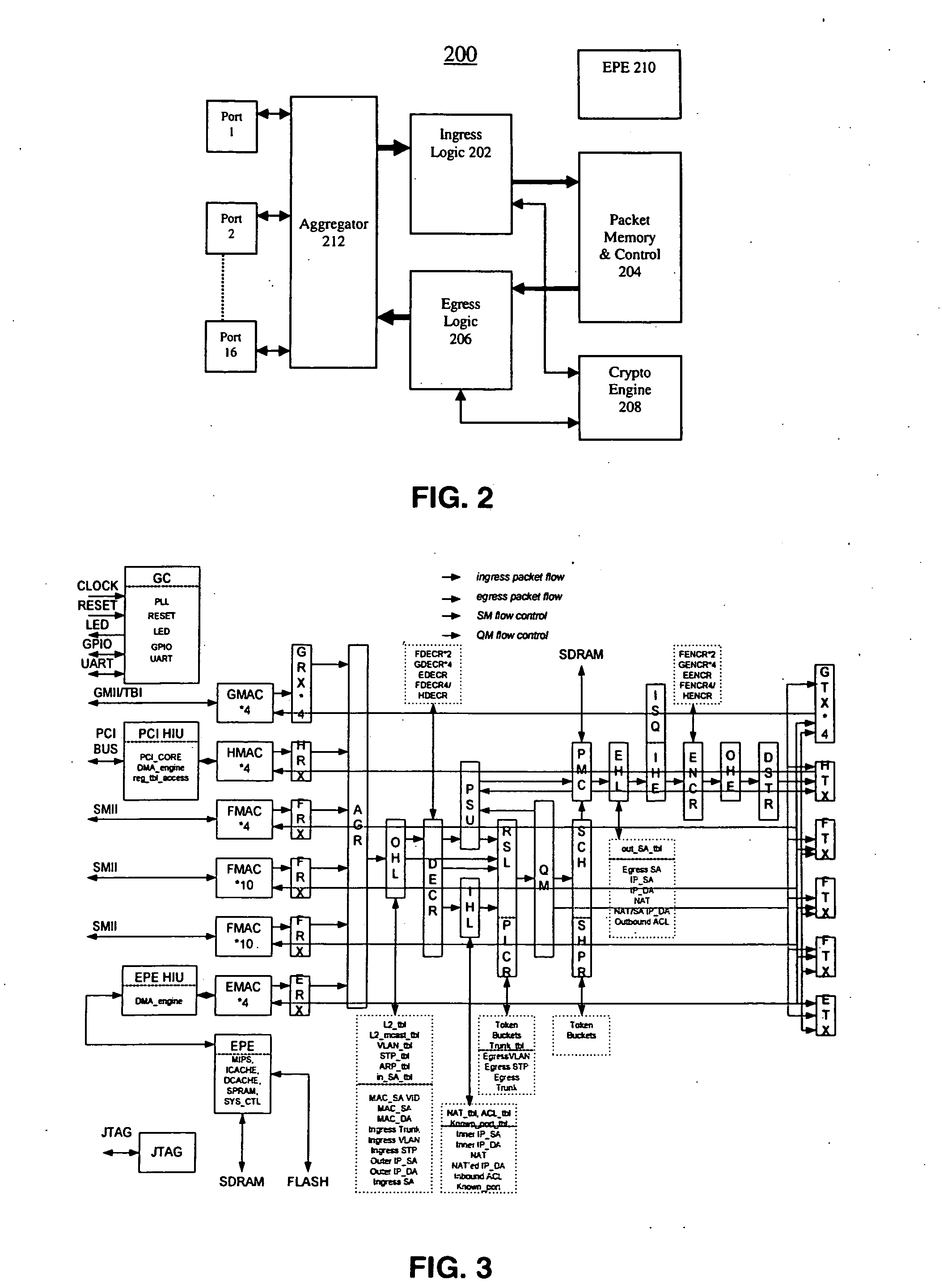
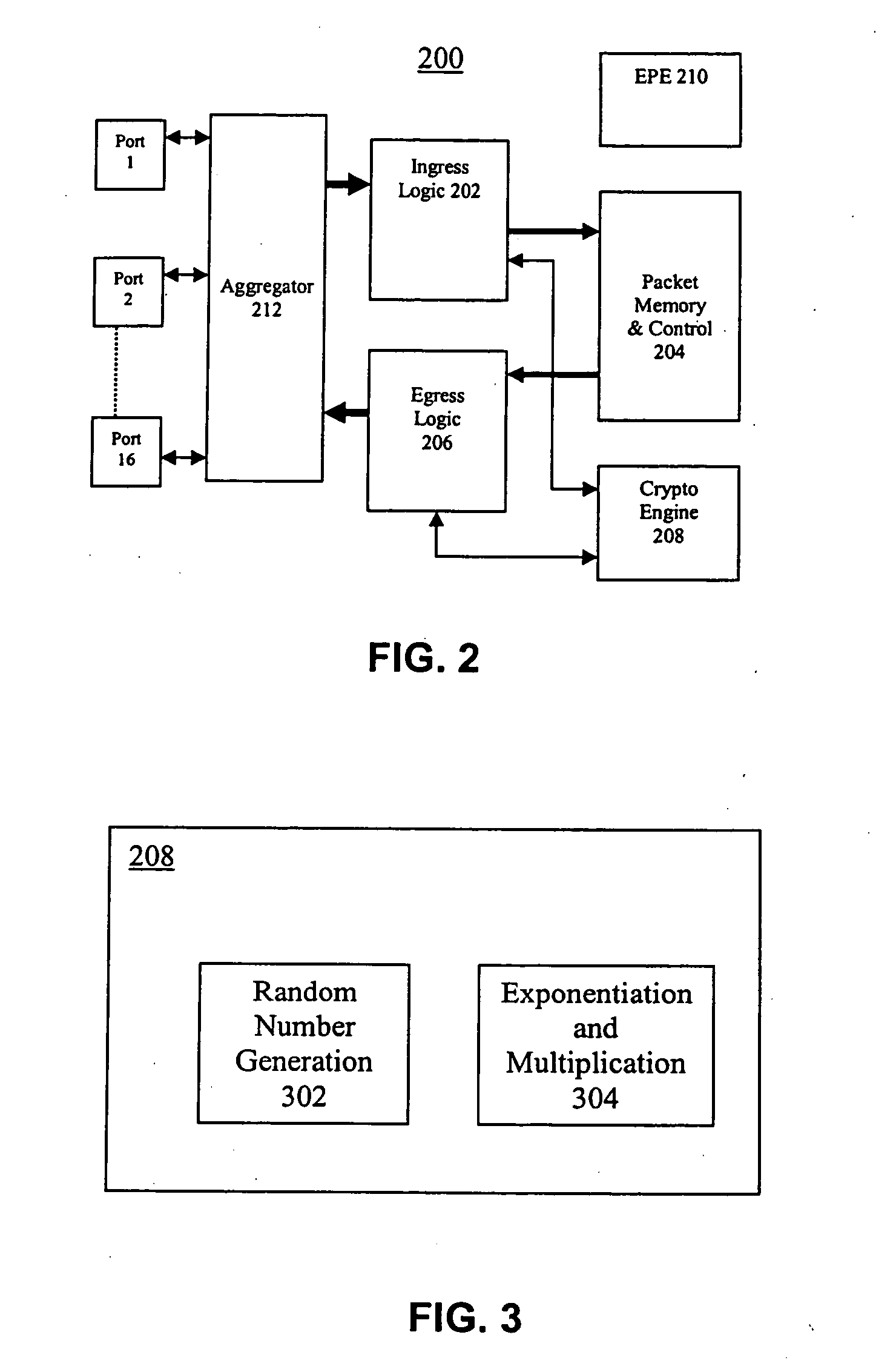
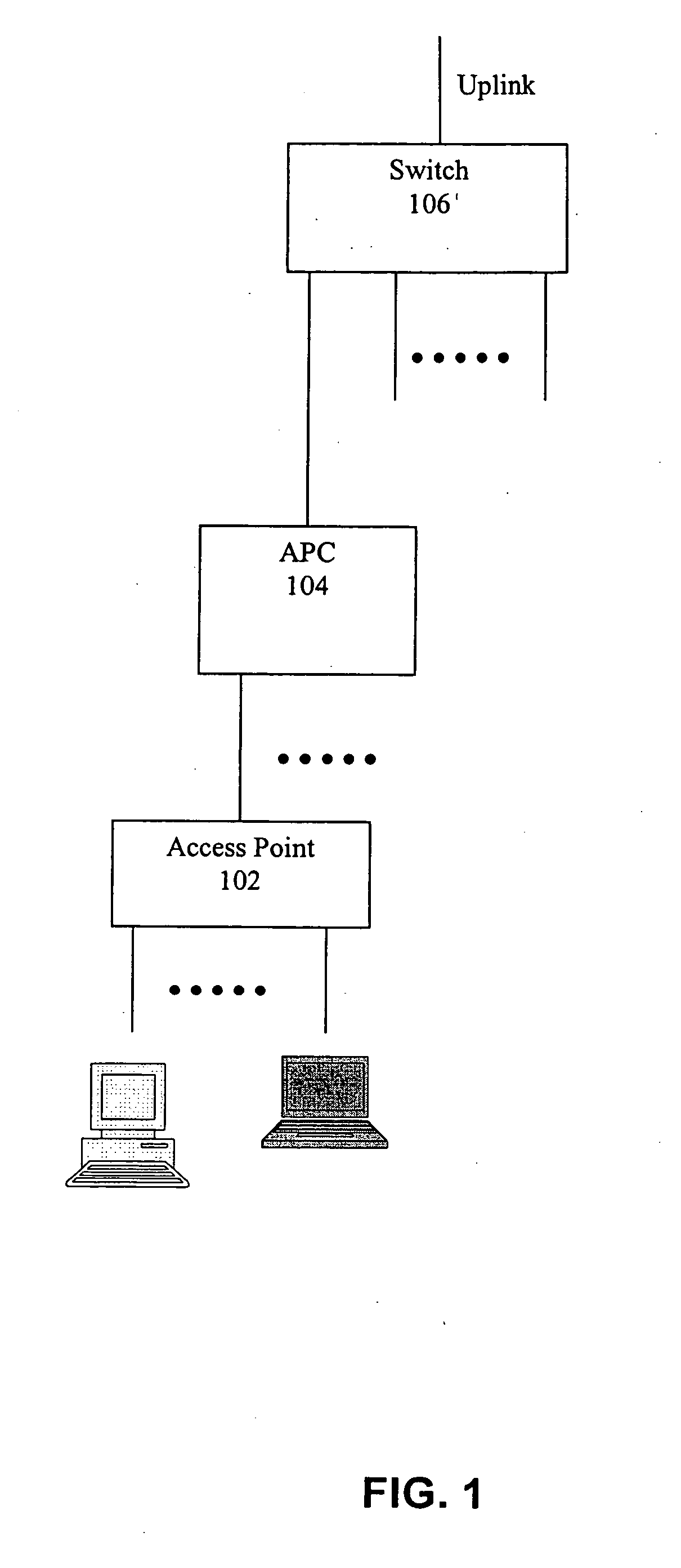
Unified wired and wireless switch architecture
An apparatus provides an integrated single chip solution to solve Switching / Bridging, Security, Access Control, Bandwidth Management—Quality of Service issues, Roaming—Clean Hand off, Anticipatory Load Management, Location Tracking, Support for Revenue Generating Services—Fine grain QoS, Bandwidth Control, Billing and management. The architecture is such that it not only resolves the problems pertinent to WLAN it is also scalable and useful for building a number of useful networking products that fulfill enterprise security in all possible combinations of wired and wireless networking needs.
Owner:SINETT CORP
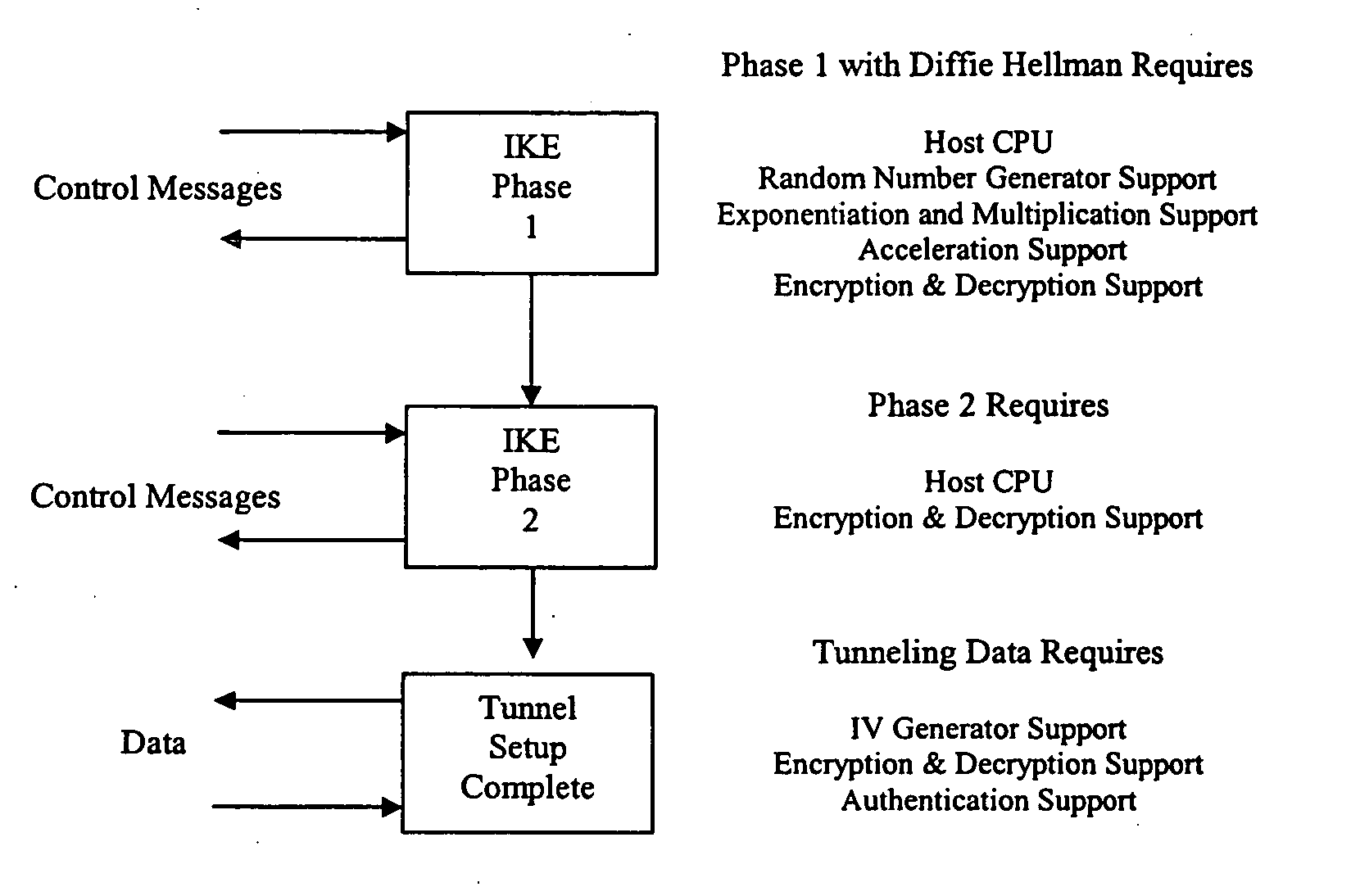
Hardware acceleration for Diffie Hellman in a device that integrates wired and wireless L2 and L3 switching functionality
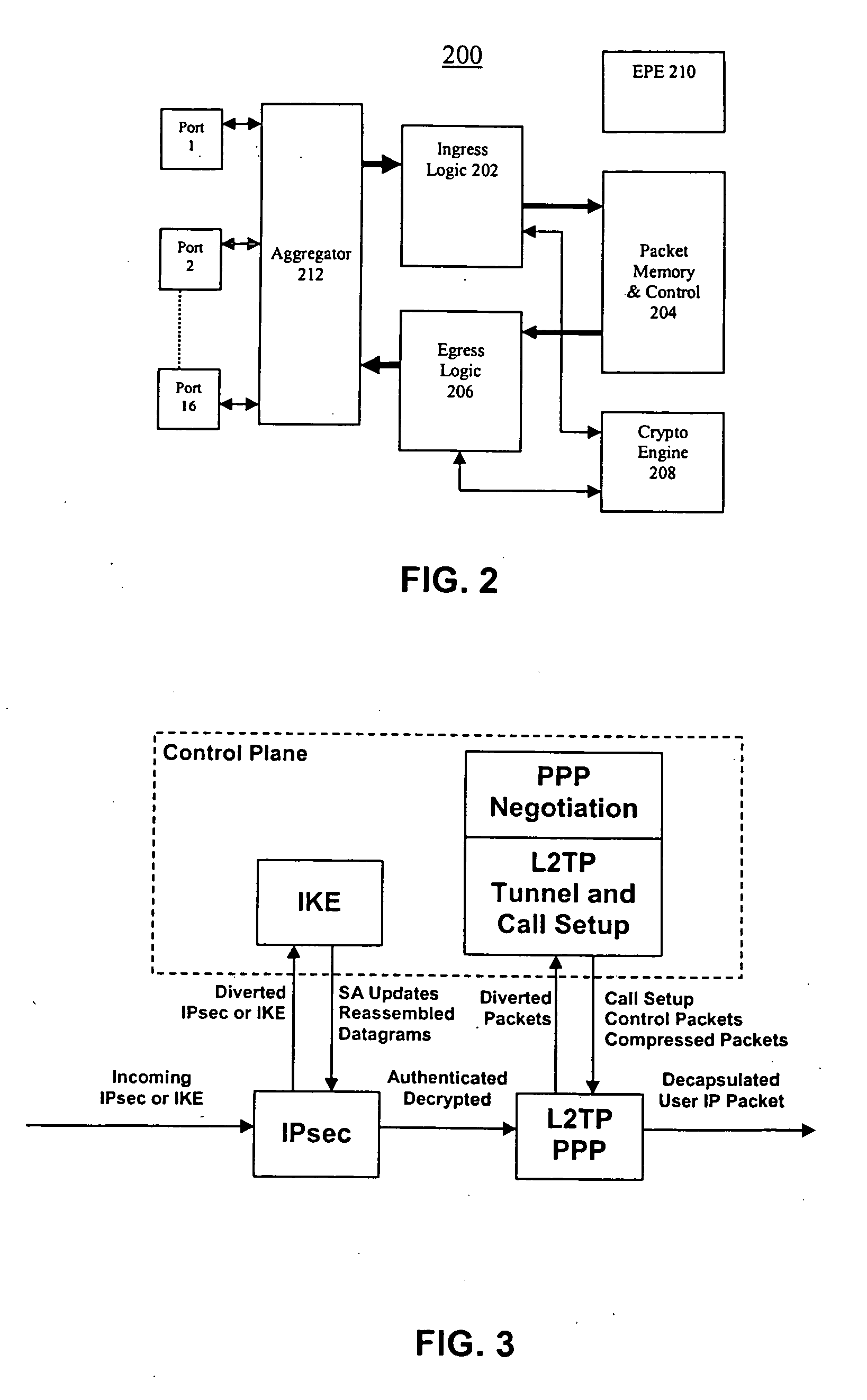
InactiveUS20050063543A1Reduce throughputKey distribution for secure communicationNetwork topologiesExtensibilityIPsec
An apparatus provides an integrated single chip solution to solve a multitude of WLAN problems, and especially Switching / Bridging, and Security. In accordance with an aspect of the invention, the apparatus is able to terminate secured tunneled IPSec, L2TP with IPSec, PPTP, SSL traffic. In accordance with a further aspect of the invention, the apparatus is also able to handle computation-intensive security-based algorithms such as Diffie Hellman without significant reduction in traffic throughput. The architecture is such that it not only resolves the problems pertinent to WLAN it is also scalable and useful for building a number of useful networking products that fulfill enterprise security and all possible combinations of wired and wireless networking needs.
Owner:SINETT CORP
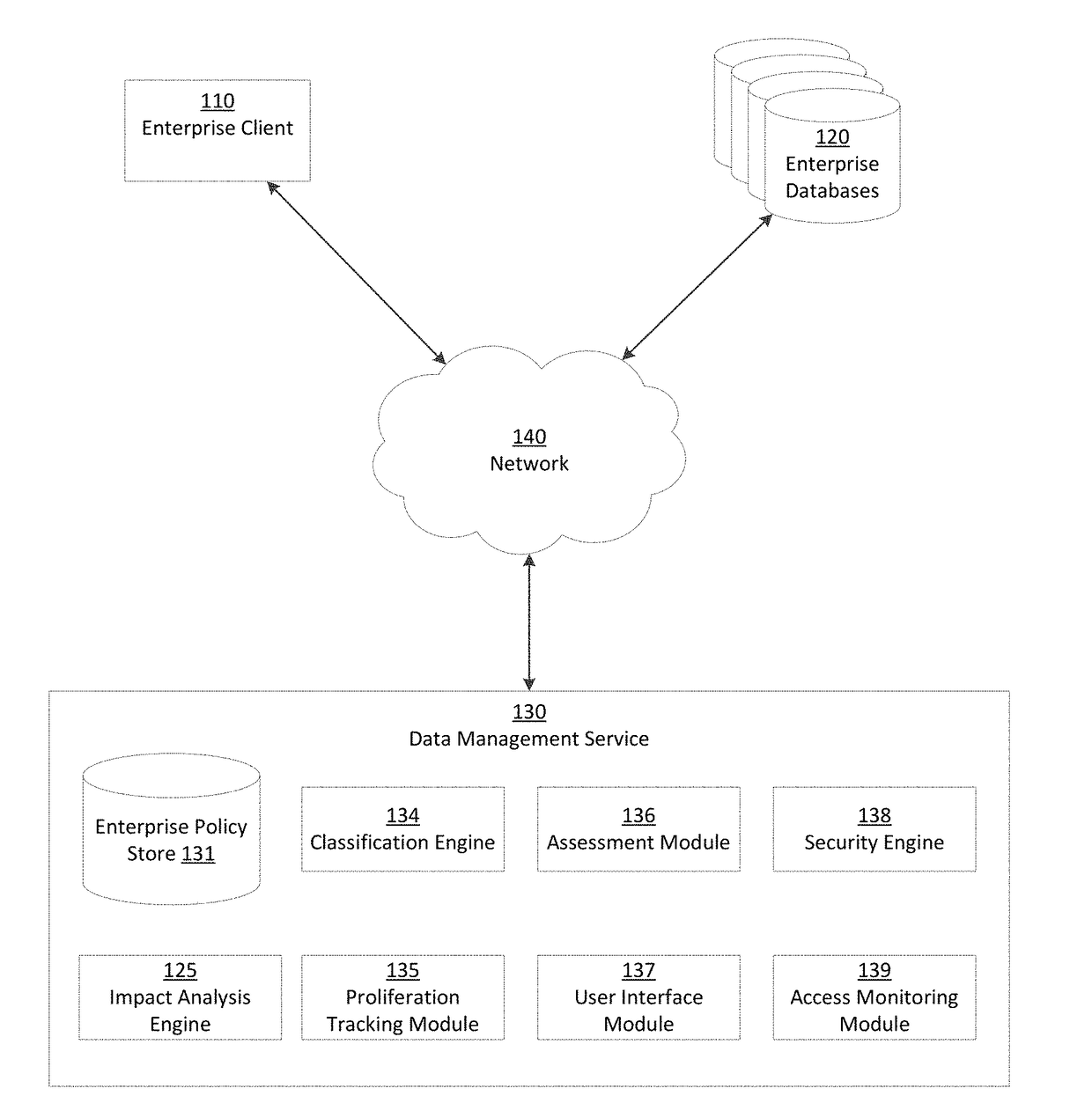
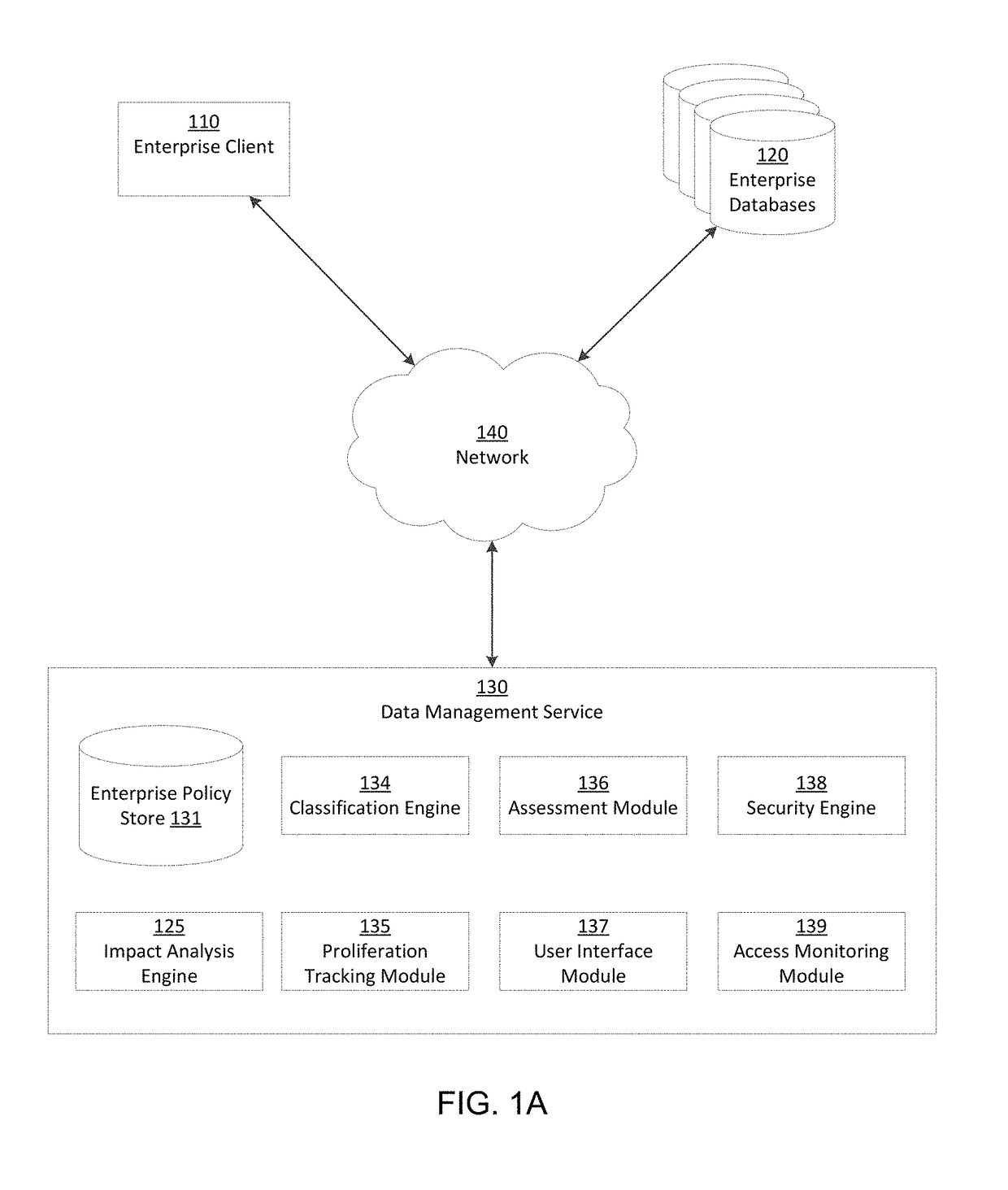
Assessment type-variable enterprise security impact analysis
ActiveUS9762603B2Easy to identifyReduce processDigital data information retrievalDigital data protectionCorporate securityData quality
A data management service identifies sensitive data stored on enterprise databases according to record classification rules that classify a data record as having a sensitive data type if the data record includes fields matching at least one of the record classification rules. Methods and systems rely on a set of impact factors each having a set of set of value bands representing a range for the impact factor and a corresponding value (between 0 and 1). The factors, ranges, and values all are customizable for an organization. Impact scoring calculations take into account each of the impact factors, and each is weighted to represent a specific risk perception or assessment type. A similar impact scoring is applied to data quality using volume of data as a key attribute of the quality.
Owner:INFORMATICA CORP
Hardware acceleration for unified IPSec and L2TP with IPSec processing in a device that integrates wired and wireless LAN, L2 and L3 switching functionality
InactiveUS20050063381A1Network topologiesData switching by path configurationExtensibilityWire speed
An apparatus provides an integrated single chip solution to solve a multitude of WLAN problems, and especially Switching / Bridging, and Security. In accordance with an aspect of the invention, the apparatus is able to terminate secured tunneled IPSec and L2TP with IPSec traffic. In accordance with a further aspect of the invention, the architecture can handle both tunneled and non-tunneled traffic at line rate, and manage both types of traffic in a unified fashion. The architecture is such that it not only resolves the problems pertinent to WLAN, it is also scalable and useful for building a number of useful networking products that fulfill enterprise security and all possible combinations of wired and wireless networking needs.
Owner:SINETT CORP
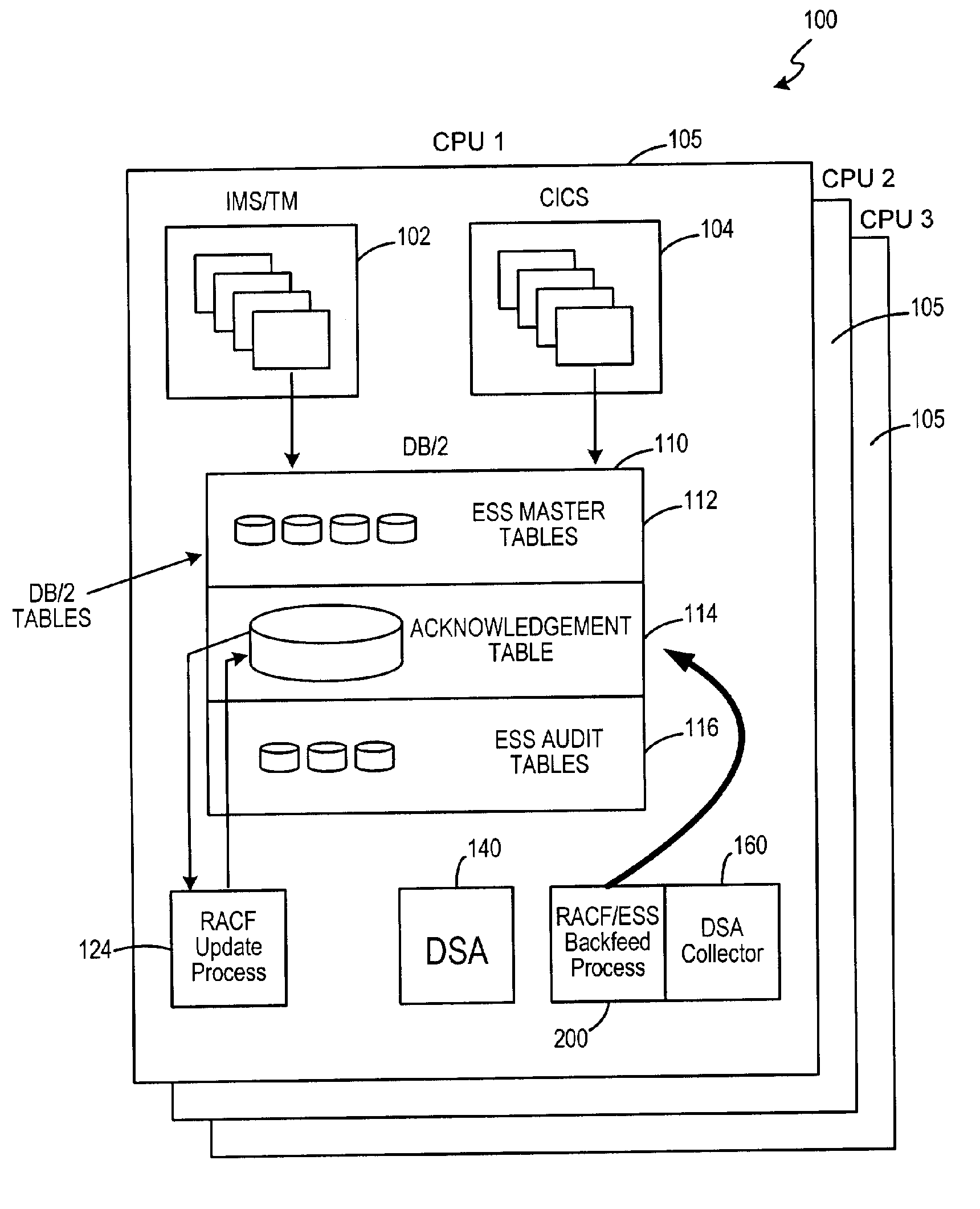
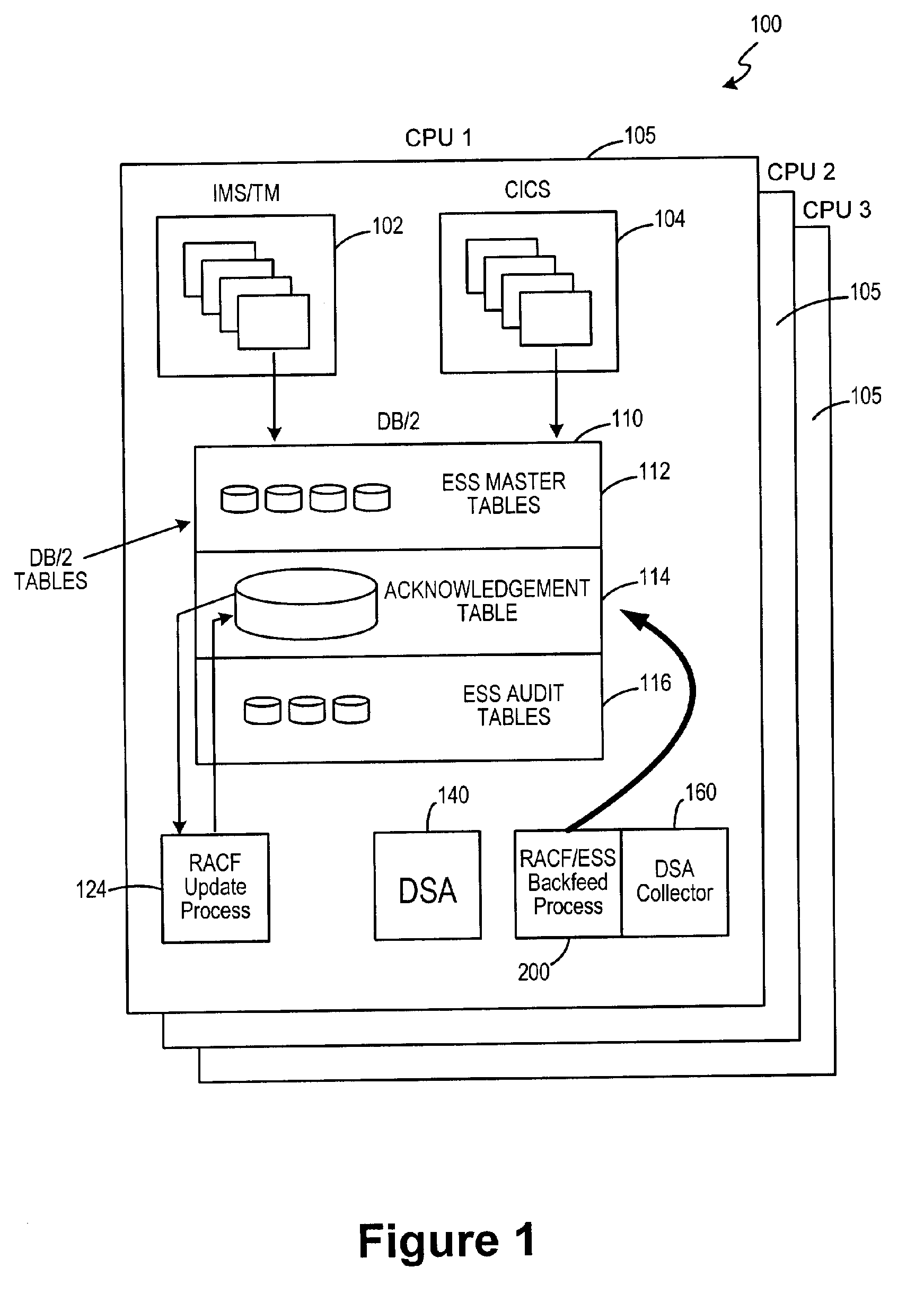
System and method for monitoring and ensuring data integrity in an enterprise security system
InactiveUS20060075488A1Memory loss protectionDigital data processing detailsThird partyData integrity
The invention facilitates monitoring and ensuring data security in security update information between software and hardware applications. The invention is achieved through an automated system that allows for substantial uniformity and substantially seamless security through a front-end system. The invention may use one or more third-party products to facilitate communication between computing platforms.
Owner:LIBERTY PEAK VENTURES LLC
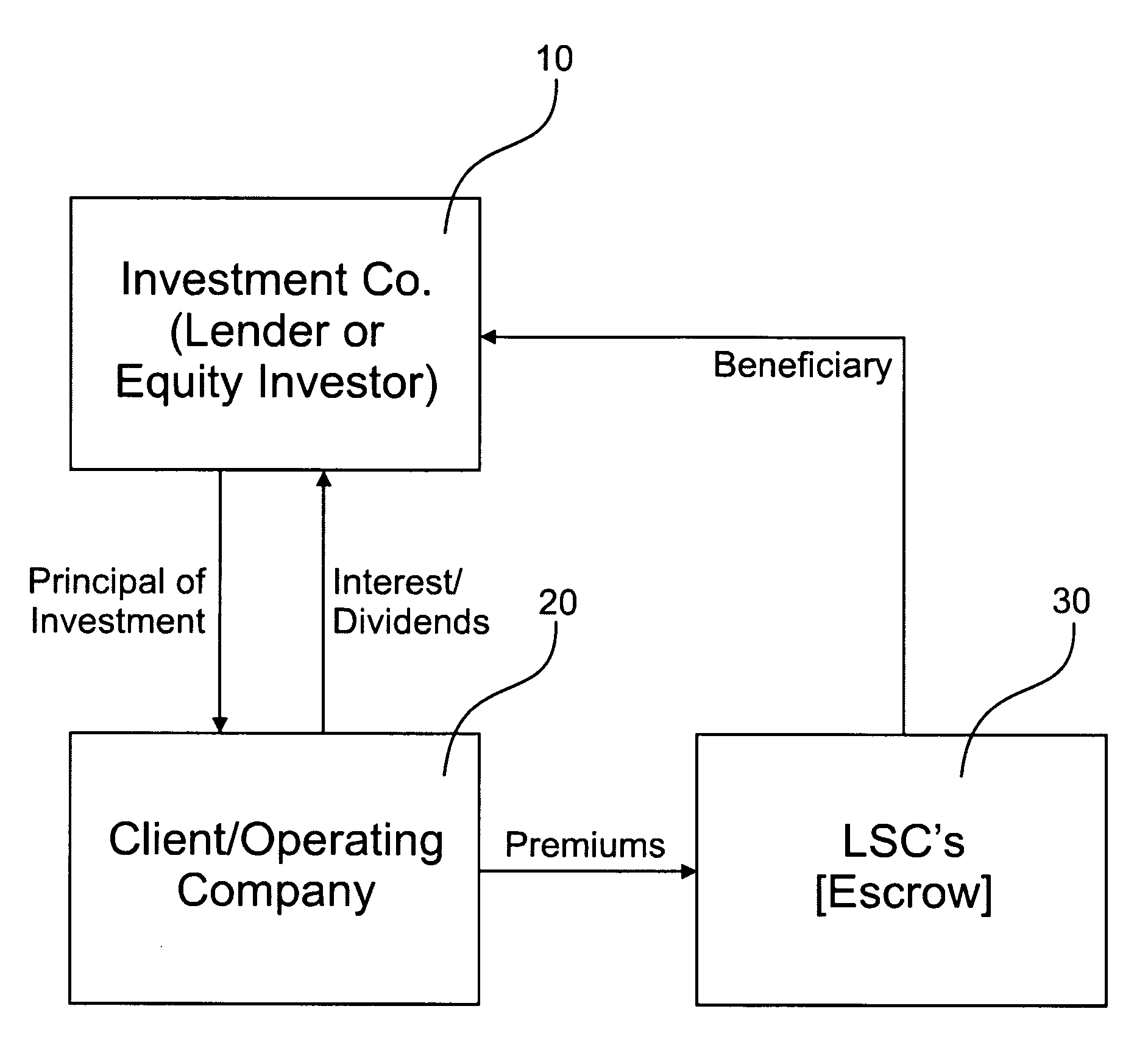
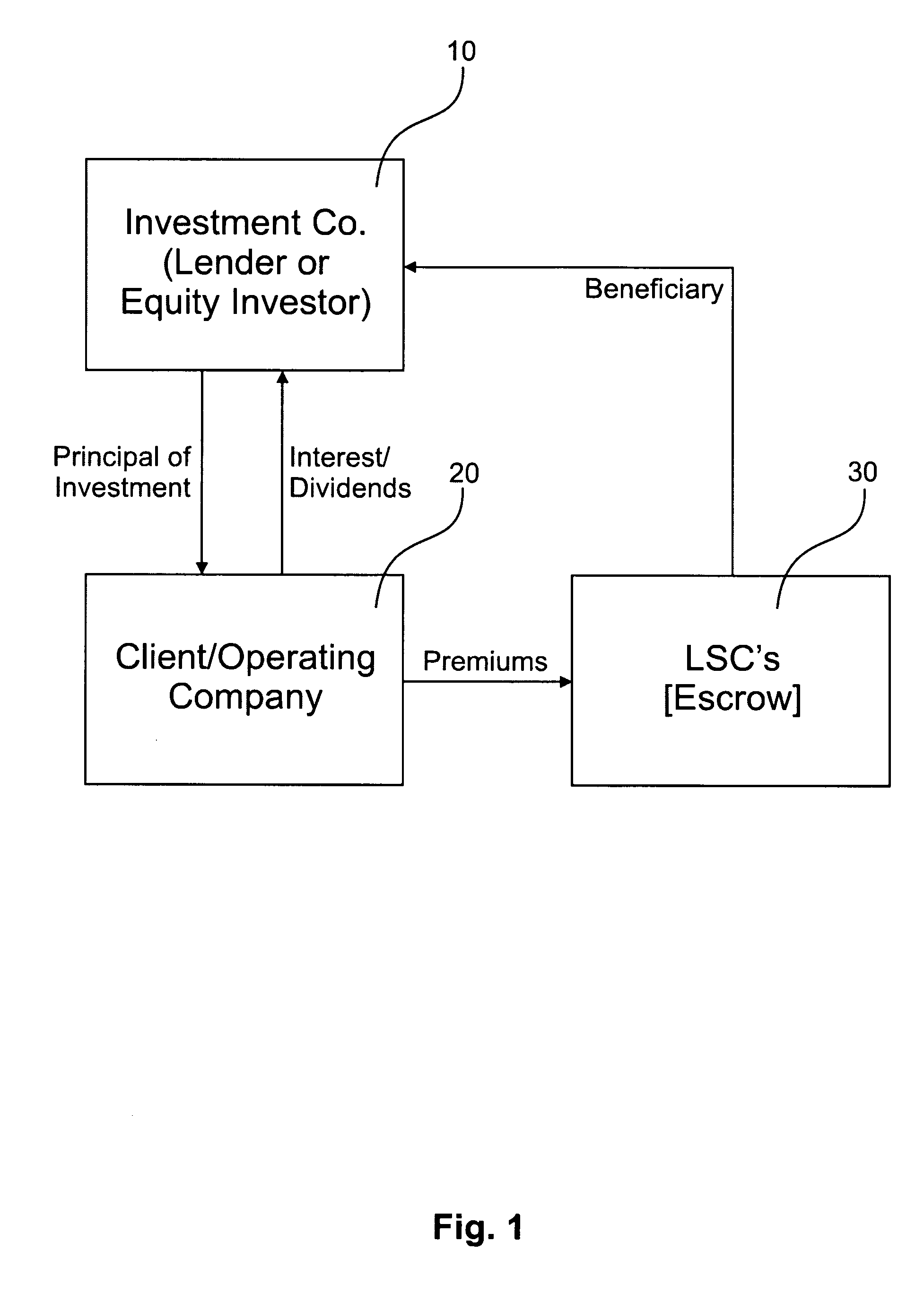
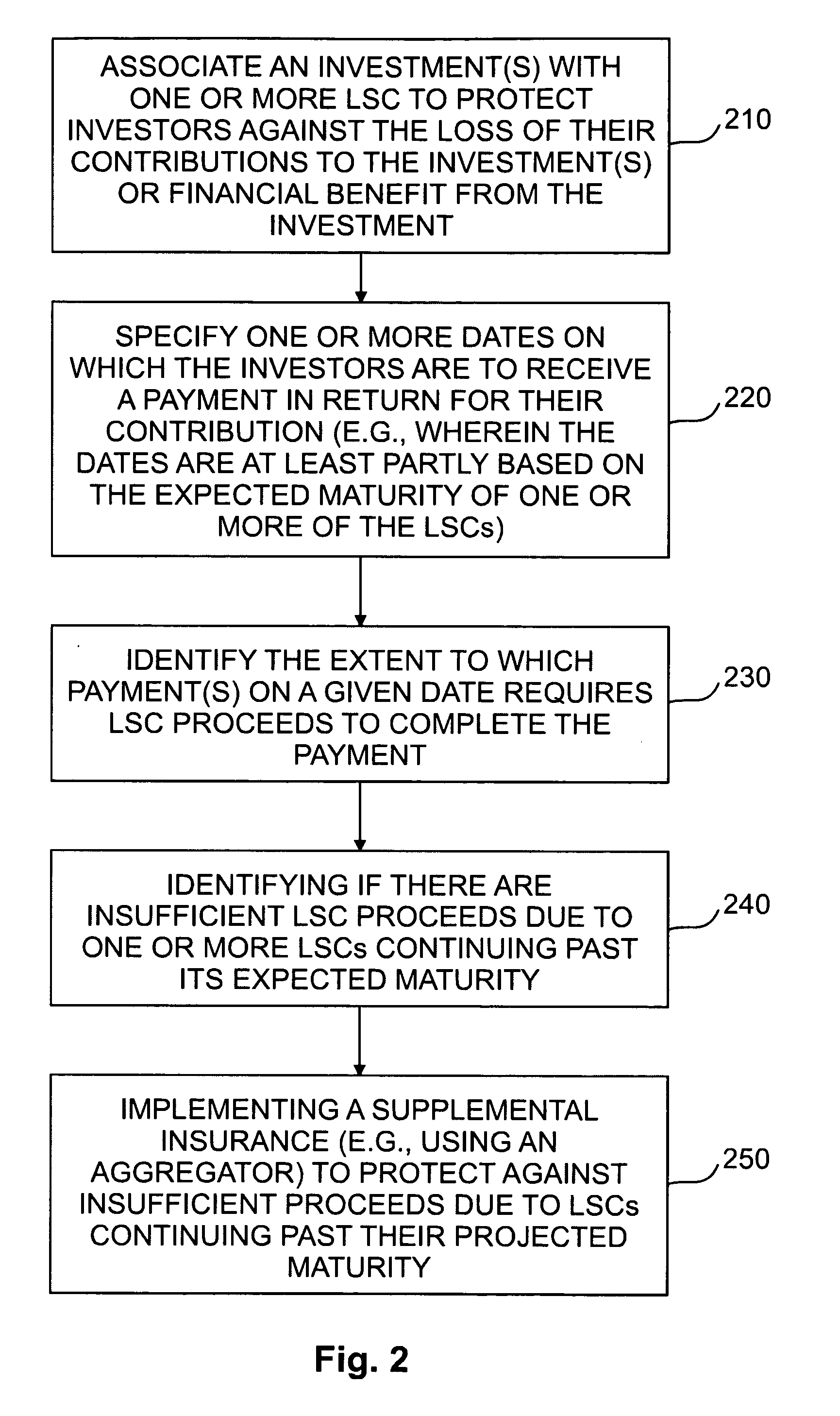
Life settlement contract based investment methods, systems, and products
Investment or financing methods, systems and products that involve LSC-backing. An investment company invests funds directly into an operating company, partially for unrestricted use by the operating company, and partially to finance a hedge to protect the principal of the invested funds. The restricted portion of the invested funds are used to purchase life settlement contracts (LSCs) in a face amount equal to a percentage of the total amount of funds invested. The LSCs may be part of a pooled fund covering multiple insureds or may be purchased on an individual basis. Structured financial products, different classes of corporate security or bond issues, high risk investment and rather investments in which a primary investment may be integrated with an LSC-based secondary investment. Computer equipment for providing a user interface, investment administration, and electronic trading are also provided.
Owner:BLAIR THOMAS CARLTON
System and method for supporting a security-trade financing service
InactiveUS7340432B1Promote growthMake up for deficienciesComplete banking machinesFinanceComputerized systemCorporate security
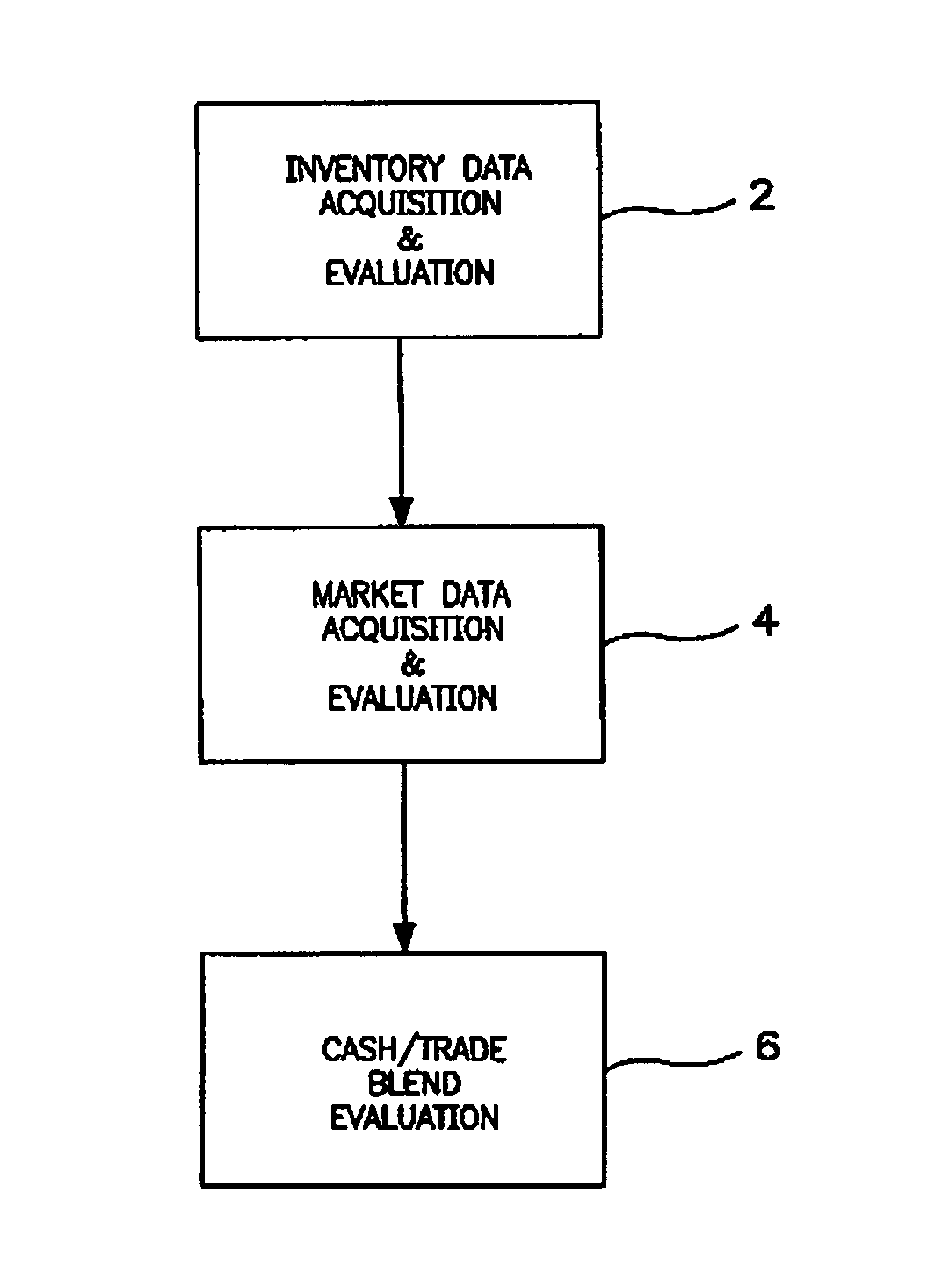
A system and method for supporting a security-trade financing service is disclosed, more particularly, wherein a method is implemented in a computer system containing at least one server including a storage device storing data bases, files, program routines and a communication network, comprising the programmed steps of: maintaining an inventory data base for the security-trade financing of the trading company.
Owner:ICON INT
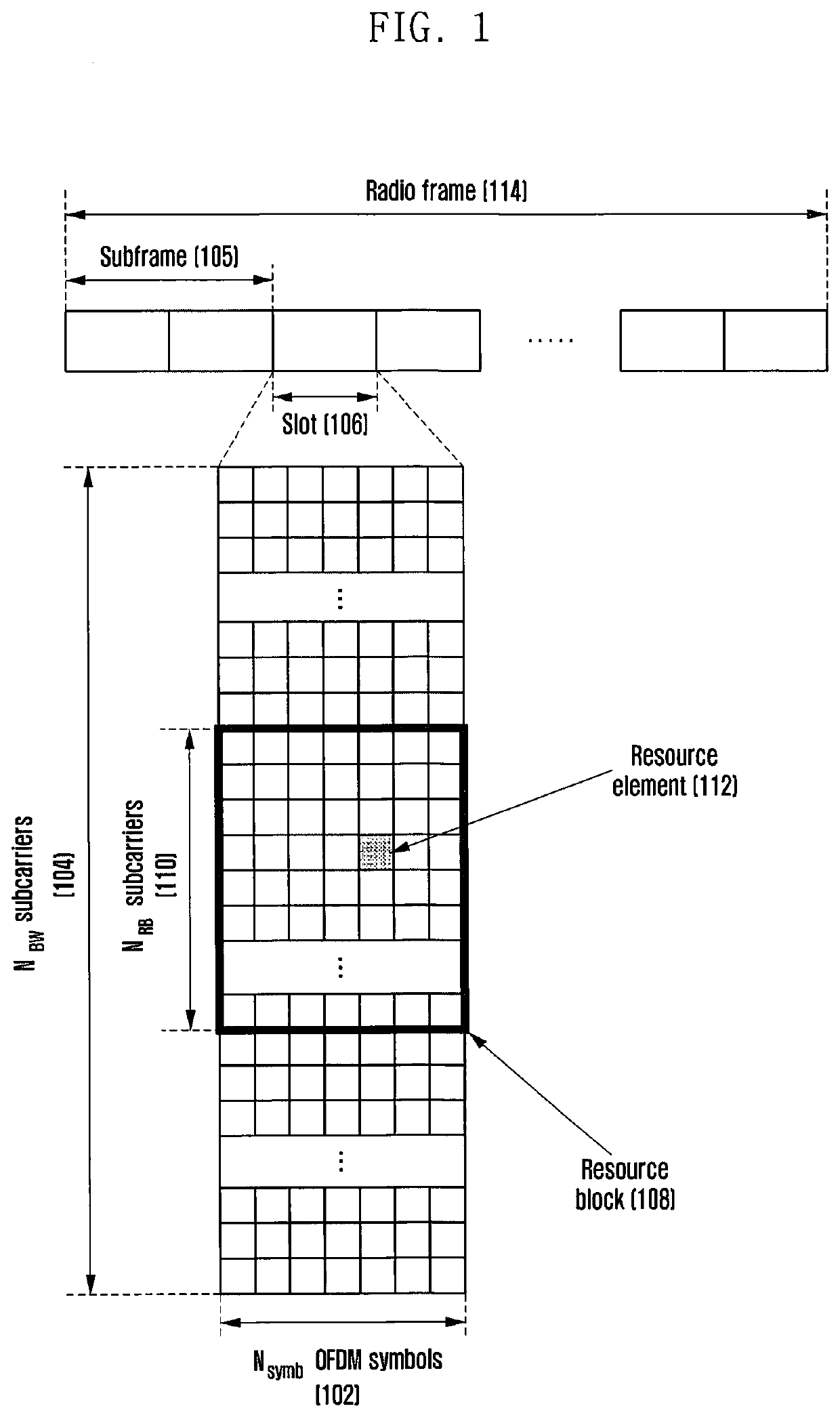
Method and apparatus for determining transport block size in communication or broadcasting system
ActiveUS20200213032A1Guaranteed normal transmissionEfficient receptionNetwork traffic/resource managementSignal allocationCommunications systemSmart city
The present disclosure relates to a communication technique that combines, with IoT technology, 5G communication system for supporting a higher data transfer rate than a 4G system, and a system therefor. The present disclosure can be applied to intelligent services, such as smart homes, smart buildings, smart cities, smart cars or connected cars, health care, digital education, retail businesses, security and safety related services, etc. on the basis of 5G communication technologies and IoT related technologies. Disclosed, in the present invention, are a method and an apparatus for determining the size of a transport block in a communication or broadcasting system.
Owner:SAMSUNG ELECTRONICS CO LTD
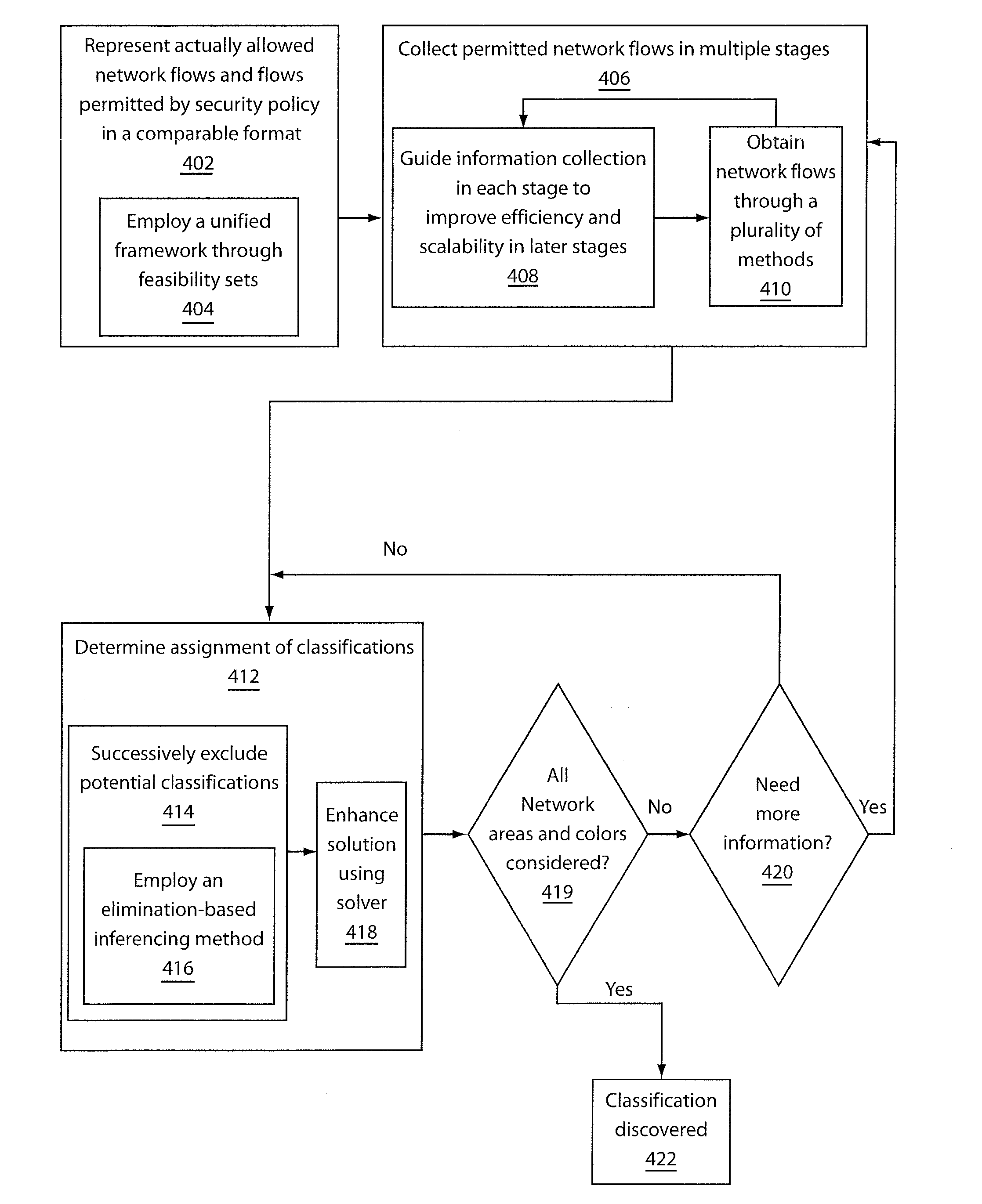
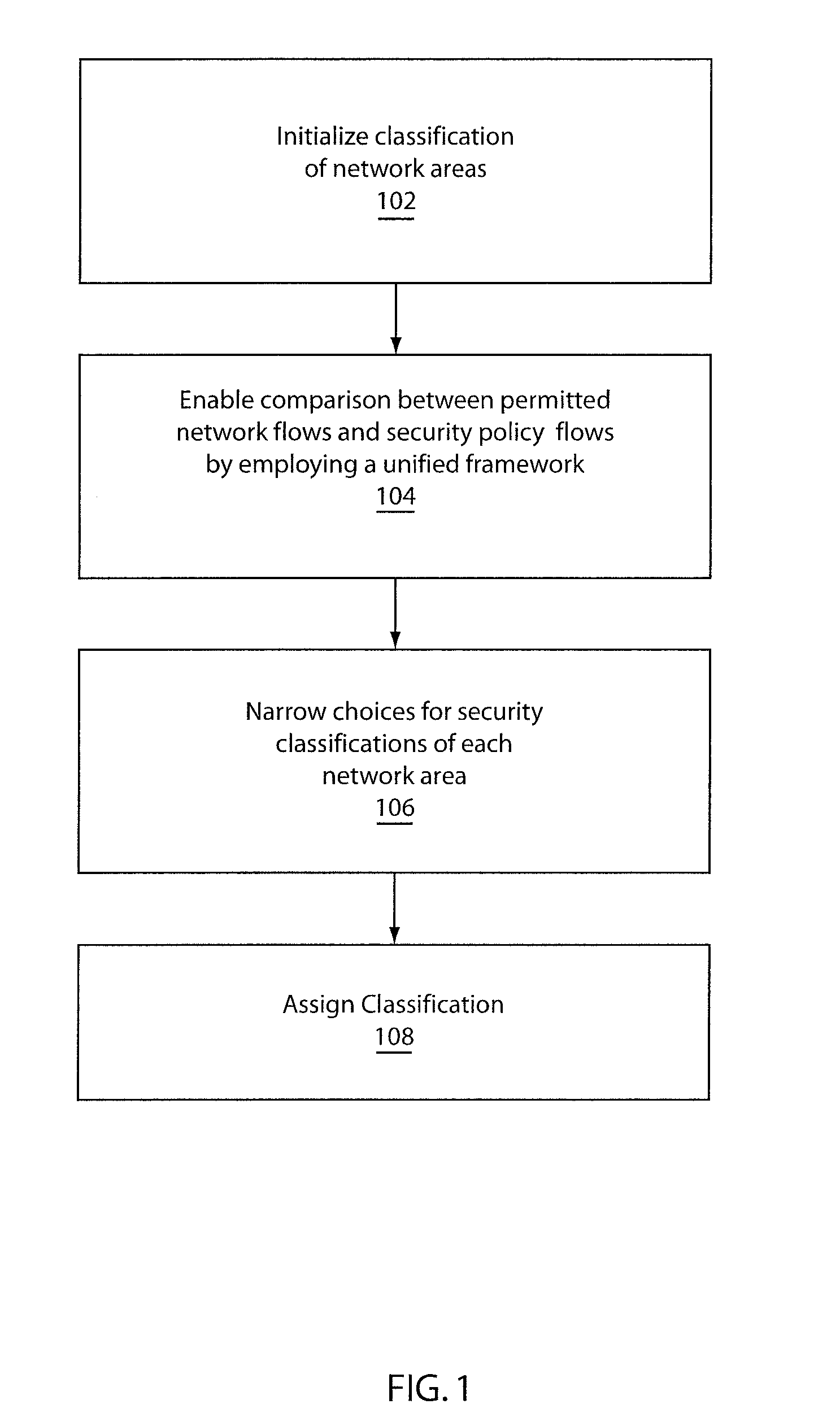
System and method for automatically discovering security classification of hosts
ActiveUS20110131628A1TransmissionSpecial data processing applicationsCorporate securitySecurity policy
A system and method for discovering security classifications of network areas includes representing actually allowed network flows and flows permitted by a security policy in a format that enables comparison. The actually allowed network flows and the security policy are provided in a networked computing environment including network areas, wherein each network area is a collection of one or more computing and network devices, and enterprise security policy defines security requirements for security classifications. An assignment of security classifications to network areas is determined by comparing the actually allowed network flows with the flows permitted by the security policy.
Owner:IBM CORP
Full-process risk management service method
InactiveCN107481153ASimplify work proceduresUnderstand Security RisksFinanceResourcesPrint-throughData shipping
The invention discloses a full-process risk management service method. The method includes the following steps that: 1, enterprise information is entered; 2, enterprise safety status diagnosis experts, carrying mobile terminals, goes to an enterprise; 3, on-site safety data are collected and entered; 4, enterprise property data are entered; 5, insurance data of a next period are entered; 6, a cloud server transmits the data to the corresponding mobile terminal; and 7, a selected insurance contract is printed through an external printer, so that the insurance contract can be used in contract conclusion and signing. With the method adopted, safety evaluation and analysis can be easily and quickly completed, analysis conclusions such as a diagnosis report of the enterprise safety status experts can be obtained; insurance business and full-process risk management service work can be combined together; and insurance services can be completed when the full-process risk management service work is completed.
Owner:河南鑫安利安全科技股份有限公司
Enterprise internal information management system
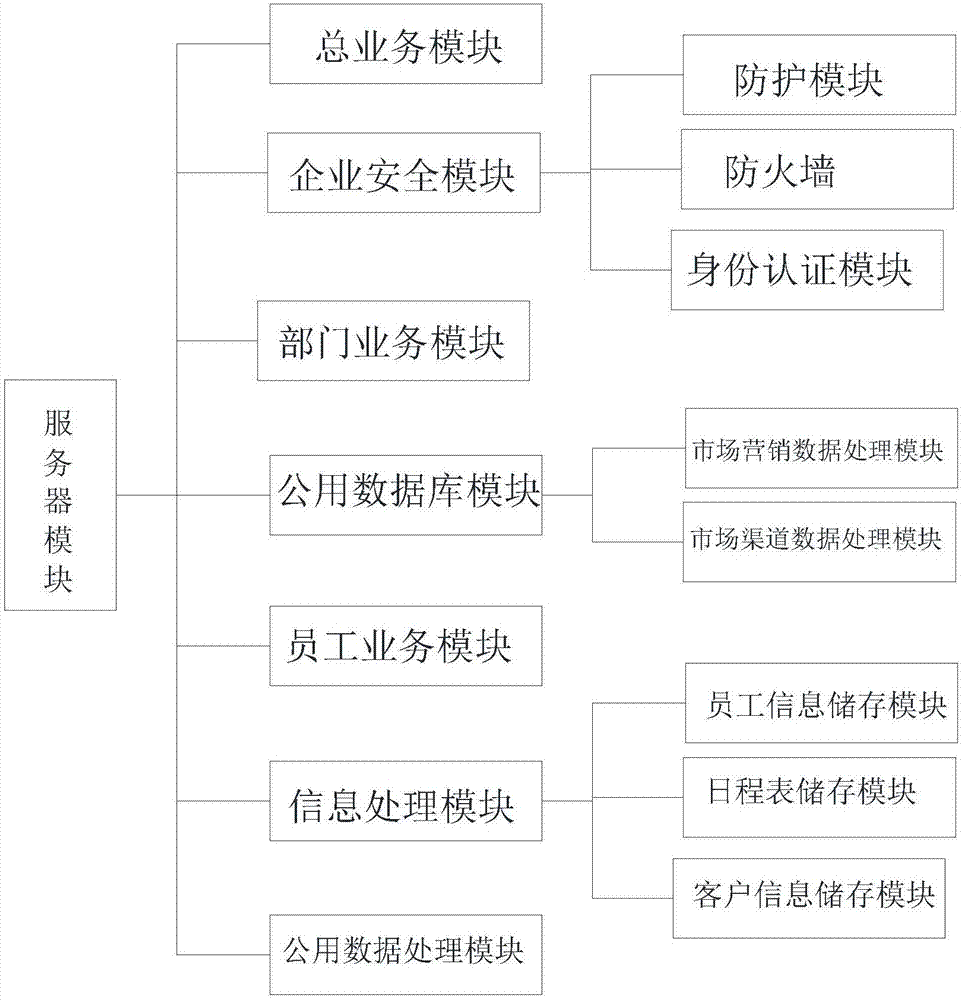
InactiveCN107239884AIncrease flexibilityImprove good performanceDigital data authenticationResourcesExtensibilityInformation processing
The invention discloses an enterprise internal information management system, comprising a server module and a general business module, a departmental business module, an employee business module, an enterprise security module, a public database module, a public data processing module, and an information processing module respectively connected to the server module. The general business module, departmental business module and employee business module have different levels of permissions, which are used to set the reading and downloading permissions of employees of each module. The authority of the general business module is higher than that of the departmental business module. The departmental business module The authority is higher than that of the employee business module. The enterprise security module is used for system security maintenance and the supervision of confidential information. The public database module is open to everyone. The public data processing module is used to monitor and process the public database. The information processing module It is used to manage, control, retrieve, download, track, and supervise the information of the entire system. This system makes it have better flexibility and expansibility.
Owner:苏州市千尺浪信息科技服务有限公司
Information security encryption and number hiding system
ActiveCN108650674AGuaranteed confidentialityEnsure safetyDigital data protectionSubstation equipmentQuality of serviceCustomer engagement
The invention discloses an information security encryption and number hiding system, comprising a primary database and a shared client. The information security encryption and number hiding system provided by the invention assists a process of dialing a mobile phone by an employee by virtue of the shared client, so that the effect that the employee can conveniently and rapidly make or answer customer calls and send and receive messages is guaranteed, the employee also can conveniently identify customers by virtue of identifications for customer names, and service quality is improved; and the effect that phone numbers of the customers are confidential to the employee is also guaranteed, and security of customer information is guaranteed, so that resources of a company are protected, and security risks of the company are greatly reduced.
Owner:我要家网络科技有限公司
Online shopping system and method with cash
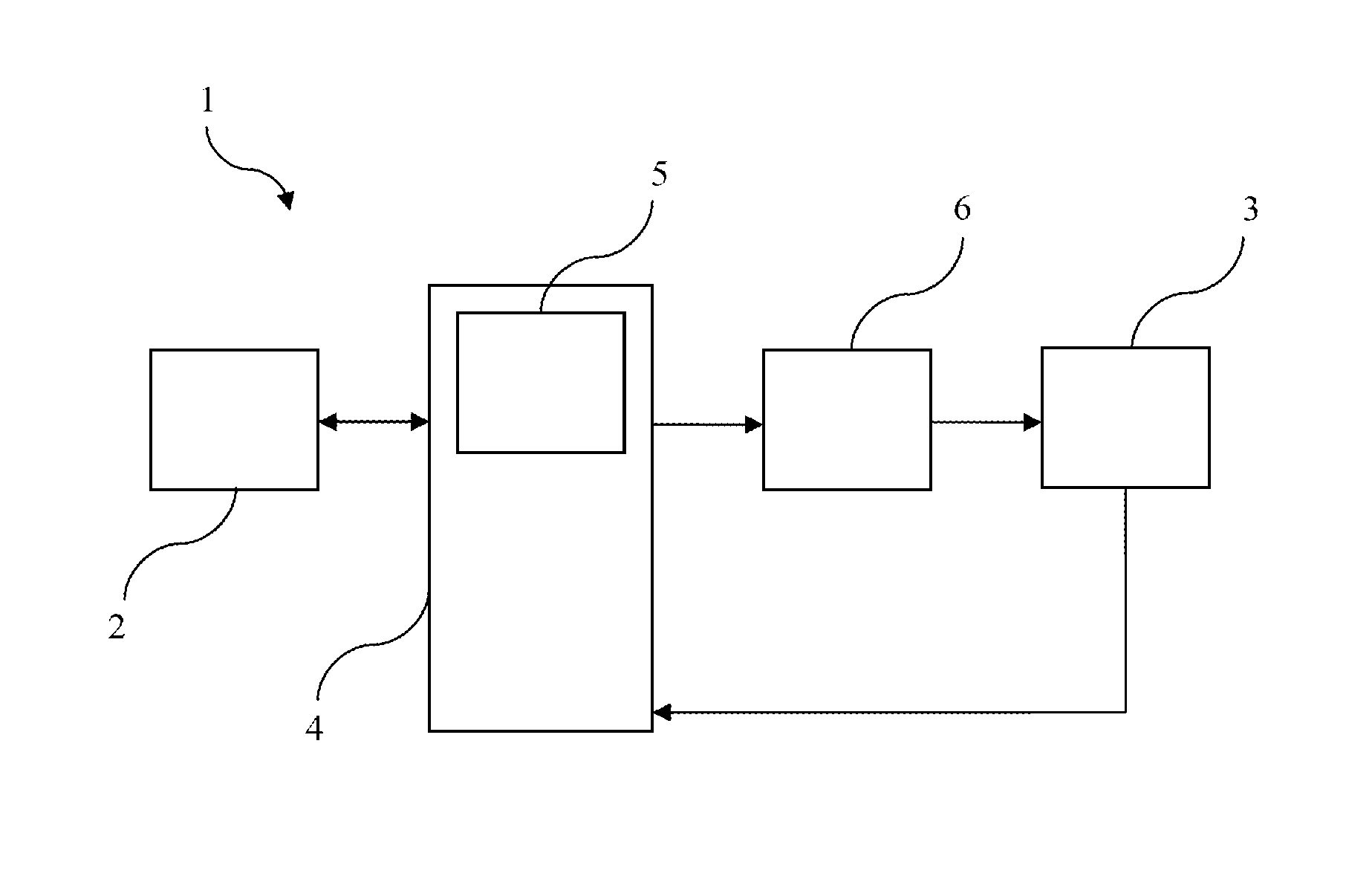
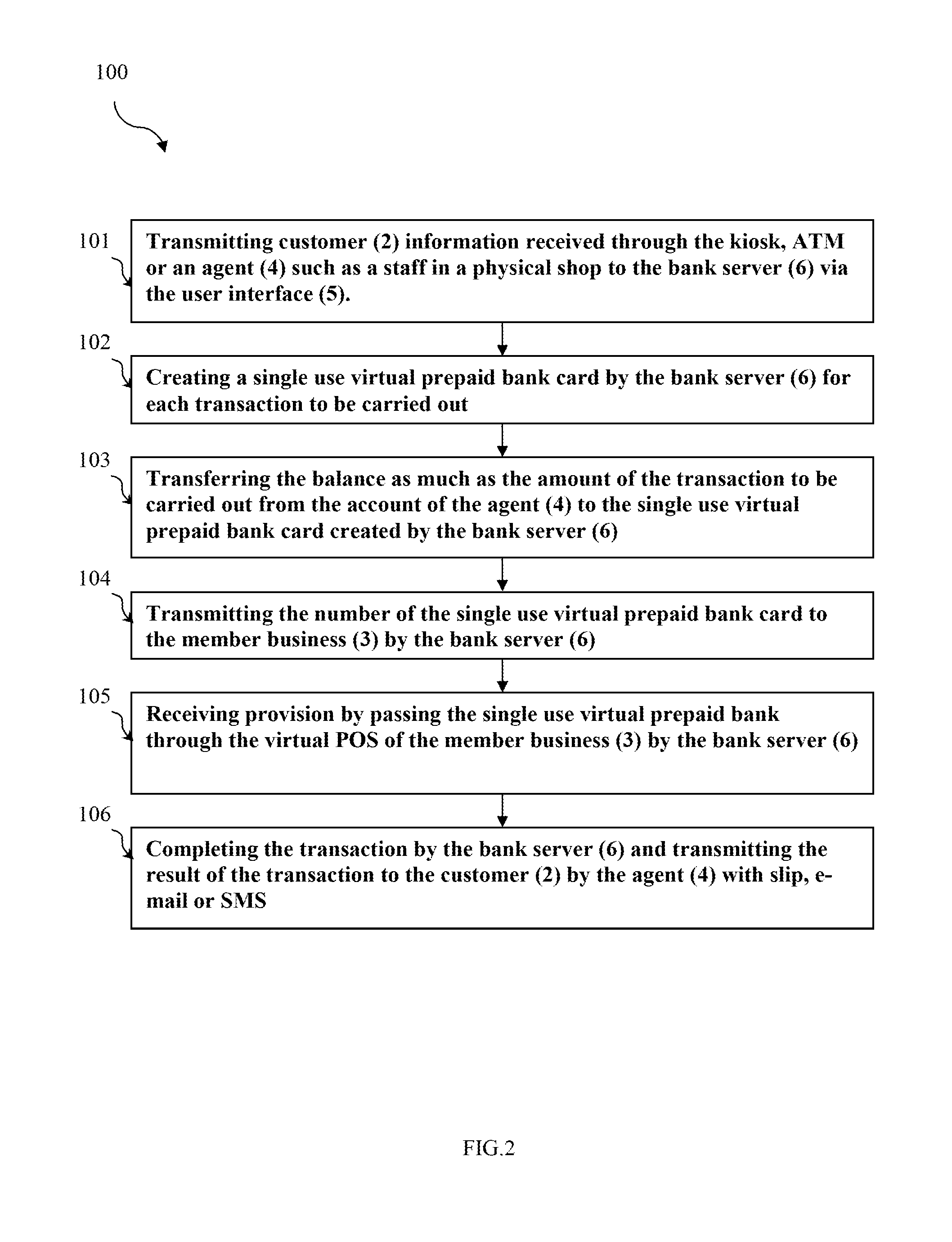
The present invention relates to a system and method which enables to shop online securely by paying with cash without using any credit / bank / pre-paid bank card. The present invention comprises at least one member business selling products or service over the internet, at least one agent adapted to enable the customers to shop securely from member businesses by using, cash and which is registered to the system via a bank or credit card, at least one user interface enabling the customer information to be entered to the system, at least one bank server adapted to create a single use virtual prepaid card, transfer the balance as much as the amount of the transaction which is subtracted from the bank or credit card of the agent to the single use virtual prepaid card, transmit the customer information and the single use prepaid bank card number to the member business.
Owner:GLOBAL ODEME SISTEMLERI ANONIM SIRKETI
Collective enterprise outsourcing service safety credit and on-site construction control platform
InactiveCN109409649ARealize real-time controlSecurity risks are controllableOffice automationResourcesTime managementCorporate security
The invention discloses a collective enterprise outsourcing service safety credit and on-site construction management and control platform, comprising a background server and a mobile terminal, realizing the safety training for the personnel of the outsourcing unit, personnel identification, special work type certificate, the examination and approval of the qualifications of enterprises and personnel, management of operation violation, whole process management and control of credit evaluation, strengthening of the management requirements of the outsourcing unit in planning management, pre-operation management and control, post-arrival, safety inspection and anti-violation inspection, so as to realize the real-time management and control of the whole process of the on-site construction operation, provide technical support for the safety supervision of the Company, and ensure that the safety risks at the construction site are controllable, controllable and under control.
Owner:浙江大有集团有限公司
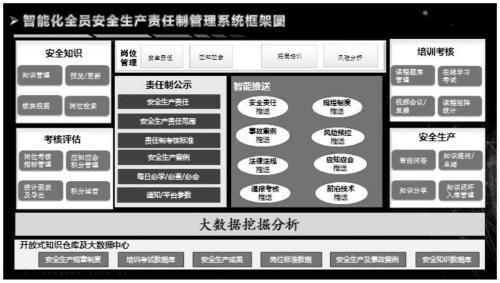
Intelligent personnel responsibility management system for safety production
The invention discloses an intelligent personnel responsibility management system for safety production which is based on a private cloud platform and a big data center and comprises a safety production resource library, a post data warehouse, a safety production training publicity module, a safety quality ability training module, a training course matrix statistics module, a platform operation assessment module and an intelligent pushing module. According to the invention, an enterprise production system intrinsic safety management system is constructed; data such as safety responsibility, production technology, system regulations, laws and regulations, frontier technology, accident cases, report assessment, risk pre-control, informed parties, intelligent training and the like are sorted,integrated, analyzed and published through a comprehensive big data management platform and are intelligently pushed to each level and each employee of each post of an enterprise; all personnel safety production responsibility systems are practically implemented in place, and enterprise safety risks are effectively controlled.
Owner:孟欣
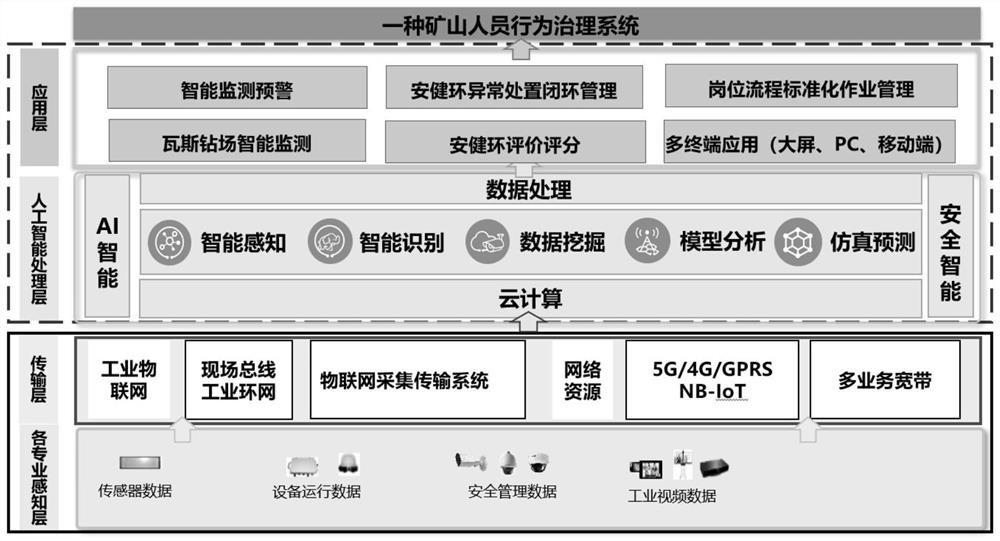
Mine personnel behavior management system and platform
PendingCN113449959AAchieving Intrinsic SafetyGuarantee sustainable developmentResourcesInformatizationHuman behavior
The invention discloses a mine personnel behavior management system and platform, and the system employs advanced technologies such as artificial intelligence, cloud computing, big data, and the Internet of Things, comprehensively masters human behaviors, environment states, key operation steps and operation processes in the mine production operation process, tracks and analyzes in real time, finds problems, prompts in time, gives an alarm to stop, locks safely, records in the background, intelligently identifies dangerous sources and updates a risk source knowledge base. Finally, static personnel behavior management systems, enterprise security governance policies and other rules and regulations files are implemented in place by adopting dynamic and objective informatization, digitization and intelligentization technical means, so that risks can be personally prevented in real time everywhere, piecemeal safety accidents can be avoided, precautions can be taken in the bud, and sustainable development of enterprises is facilitated.
Owner:陕西陕煤黄陵矿业有限公司 +1
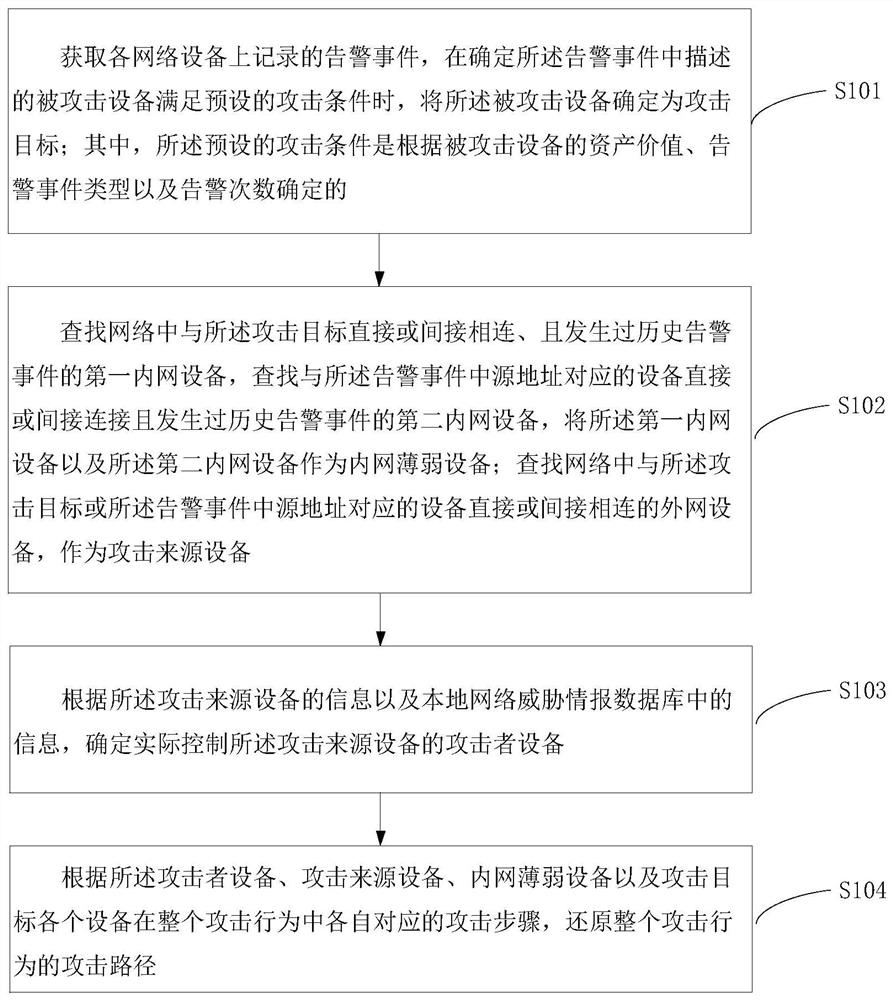
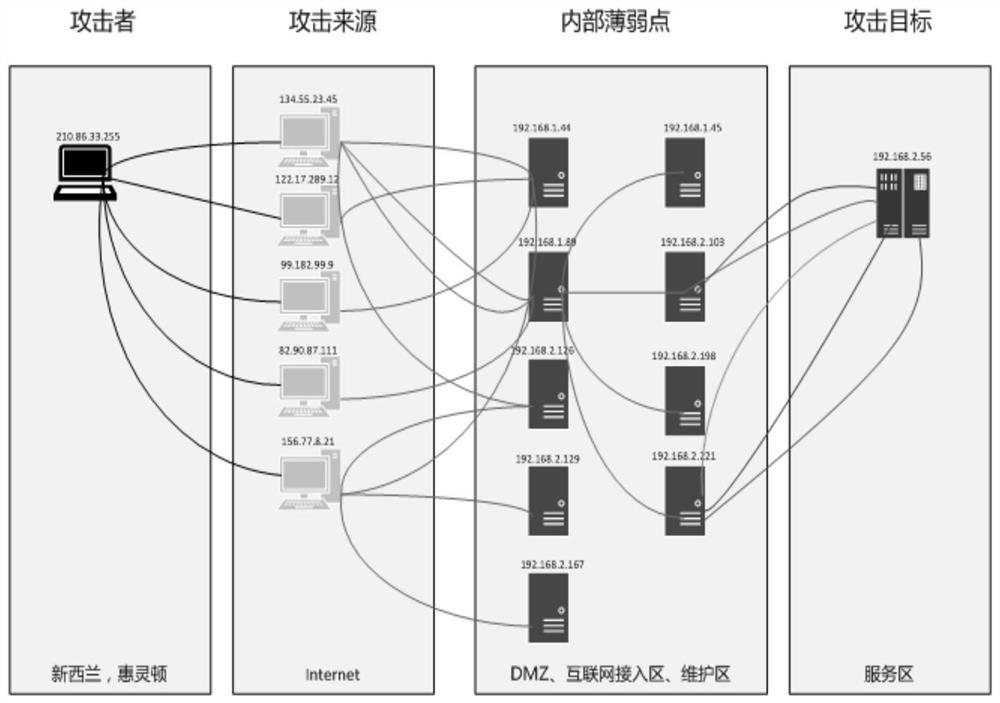
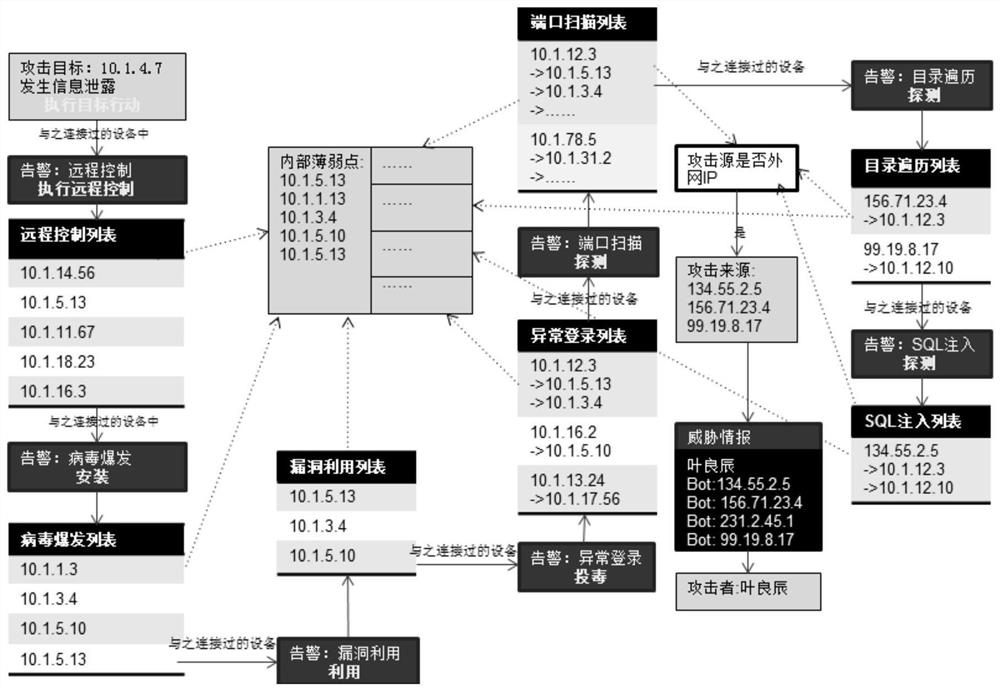
Attack path restoration method and device
The invention relates to an attack path restoration method and apparatus. According to the method, through comprehensive analysis on a security event alarm, and a connection relationship of each device in a network topology, a connection relationship between each of respective lists of an attacker, an internal network weak point, an attack source and the attacker and each set of device is obtained, thereby finishing restoration of an attack process. Compared with the existing path restoration method, the method provided by the embodiment of the invention can go deep into an internal network todiscover a security weak point in internal network protection, so that an attack path is traced to the source and thus the method is more effective to improve the enterprise security and improves theanalysis efficiency; and meanwhile, a noise of an uncritical connection in massive security events can further be shielded and only an attack path coming into effect is traced to the source; moreover, all attacks can be restored, so the restoration capacity is improved; and in addition, according to the method provided by the invention, while the attack path is restored, an operating service is not affect and thus the normal operation of the service can be kept.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
Security qualification certificate management system and management method thereof
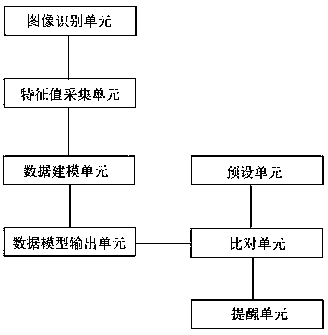
PendingCN110569828AEnsure dynamic monitoringEnsure effectivenessCharacter and pattern recognitionOffice automationData modelingDynamic monitoring
The invention discloses a security qualification certificate management system and a management method thereof. The security qualification certificate management system comprises a preset unit, an image recognition unit, a feature value acquisition unit, a data modeling unit, a data model output unit, a comparison unit and a reminding unit. According to the invention, security posts and related certificates can be bound and managed; the certificate model is deployed into an application system to monitor the certificate state of the security posts in real time; according to certificate expiration configuration time limit, expiration conditions, default conditions and the like, the messages are pushed to company safety supervisor leaders and corresponding safety post personnel in real time through a message pushing mechanism; therefore, dynamic monitoring and effective reminding of the qualification certificates of the safety posts are ensured, the safety, scientificity and reliability of safety production of enterprises are improved, and potential safety hazards or accidents caused by no-certificate on-duty are avoided.
Owner:YUNNAN KUNGANG ELECTRONICS INFORMATION TECH CO LTD
A system for detecting attacks in real time based on artificial intelligence and mapreduce
ActiveCN107623655BImprove construction levelReduce construction costsTransmissionAlgorithmBusiness enterprise
The invention discloses a real-time security attack detection system based on artificial intelligence and MapReduce. The system comprises a preprocessing stage, an MAP stage and a Reduce stage, and each stage comprises a software module. According to the invention, the construction level of an enterprise security operation and maintenance service platform can be improved, and the construction costcan be reduced.
Owner:NANJING LIANCHENG TECH DEV
Enterprise safety condition instant evaluation management system
The invention relates to the technical field of safety management, in particular to an enterprise safety condition instant evaluation management system, which comprises an information setting module, an evaluation module and a management module, the data statistics module is in electric connection or communication connection with the information setting module for information transmission; the data processing module is in electric connection or communication connection with the data statistics module so as to process the safety control parameters; and the safety state evaluation module is in electric connection or communication connection with the data processing module so as to receive the data processed by the data processing module. According to the enterprise security status real-time evaluation management system provided by the invention, the security status of the enterprise can be evaluated according to the check condition of the enterprise on the security risk, and the evaluation result is sent to the corresponding responsible person of the enterprise in time, so that the enterprise responsible person can know the security status of the enterprise in time and take corresponding measures in time.
Owner:TIANDI CHANGZHOU AUTOMATION +1
Automatic credit investigation method and system for enterprise transactions
ActiveCN107368962BProtect transaction data securityPrevent leakageFinanceResourcesCredit systemBusiness enterprise
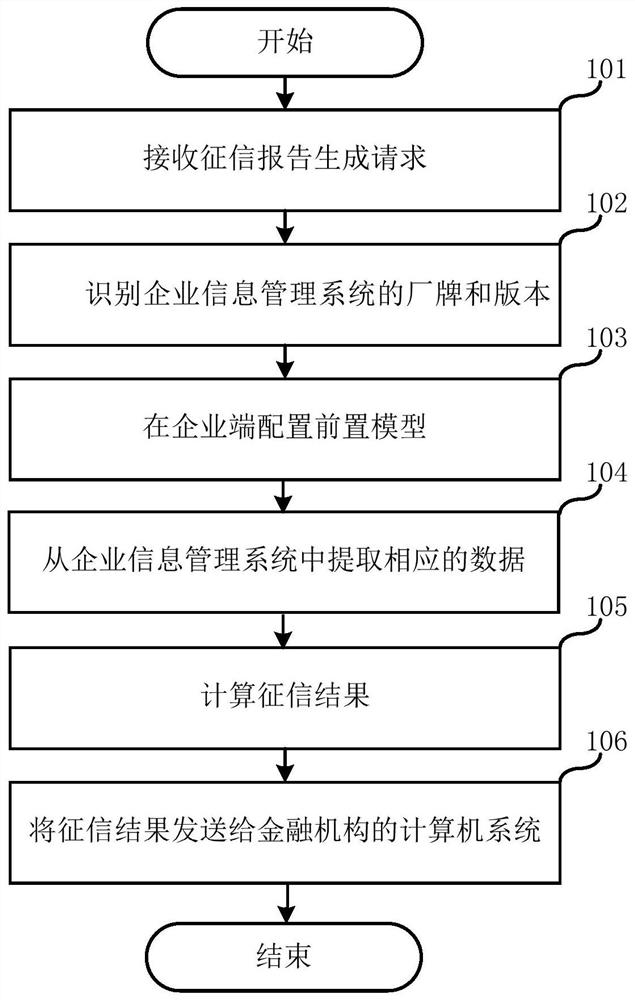
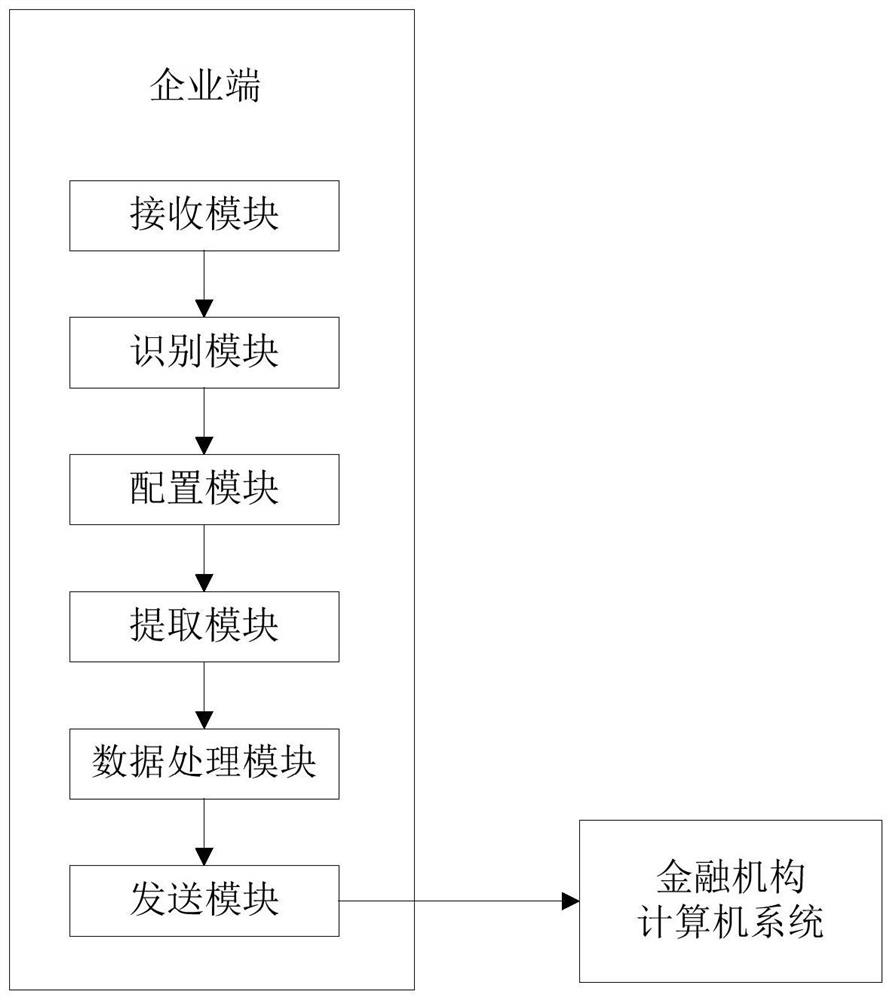
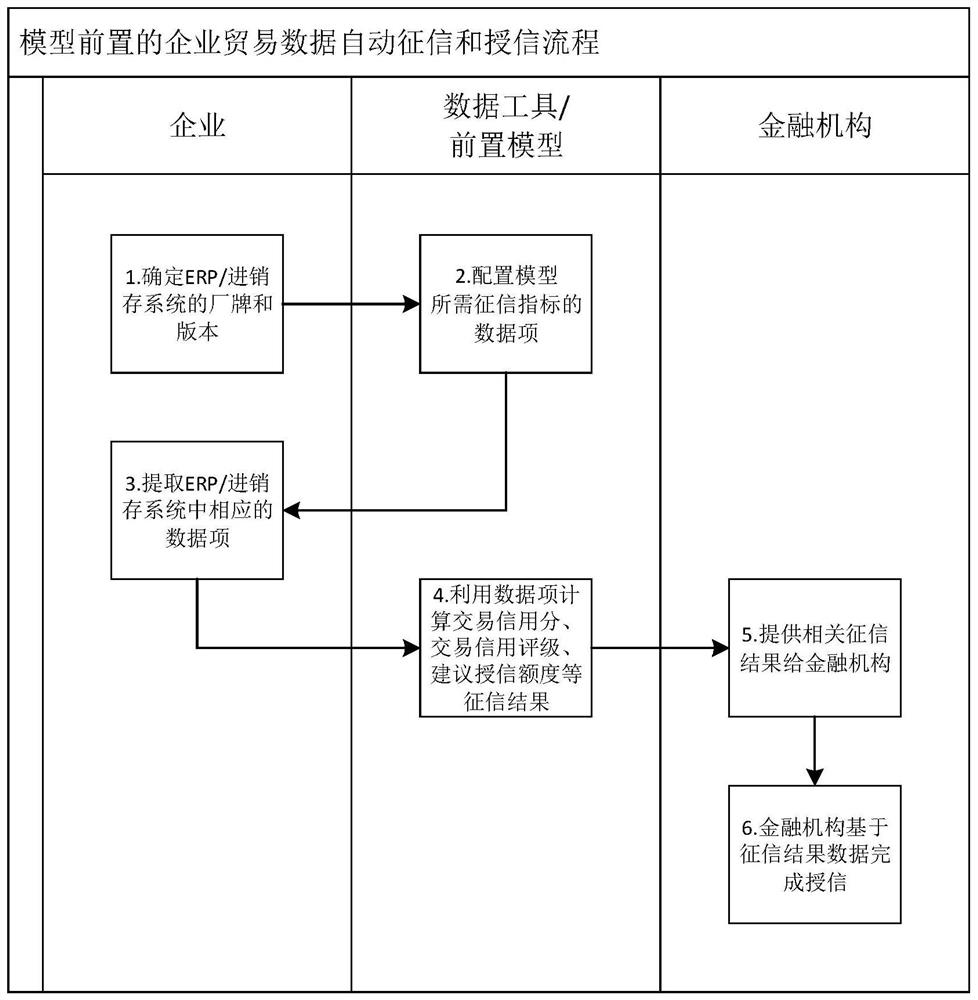
The invention relates to enterprise credit investigation technology, and discloses an automatic credit investigation method and system for enterprise transactions. The credit investigation system on the enterprise side generates requests and credit indicators based on the received credit investigation reports, identifies the brand and version of the enterprise information management system, and configures a pre-model on the enterprise side. Data items and data processing methods. The pre-model extracts the data corresponding to the data items from the enterprise information management system and calculates the credit investigation results, and sends the credit investigation results to the computer system of the financial institution for the financial institution's computer system to complete credit according to the credit investigation results. Through the front-end model set on the enterprise side, the safe and efficient credit investigation and credit granting of financial institutions to enterprises can be realized.
Owner:上海文沥信息技术有限公司
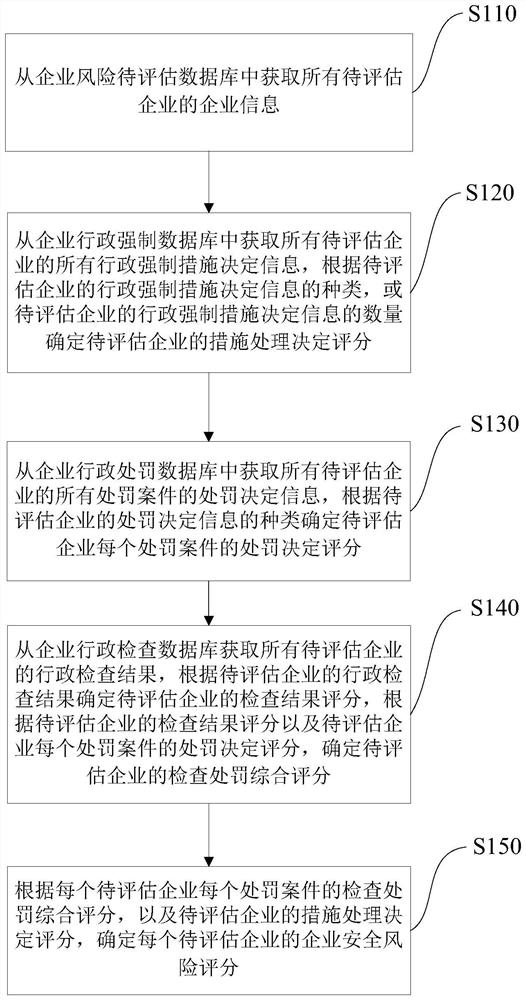
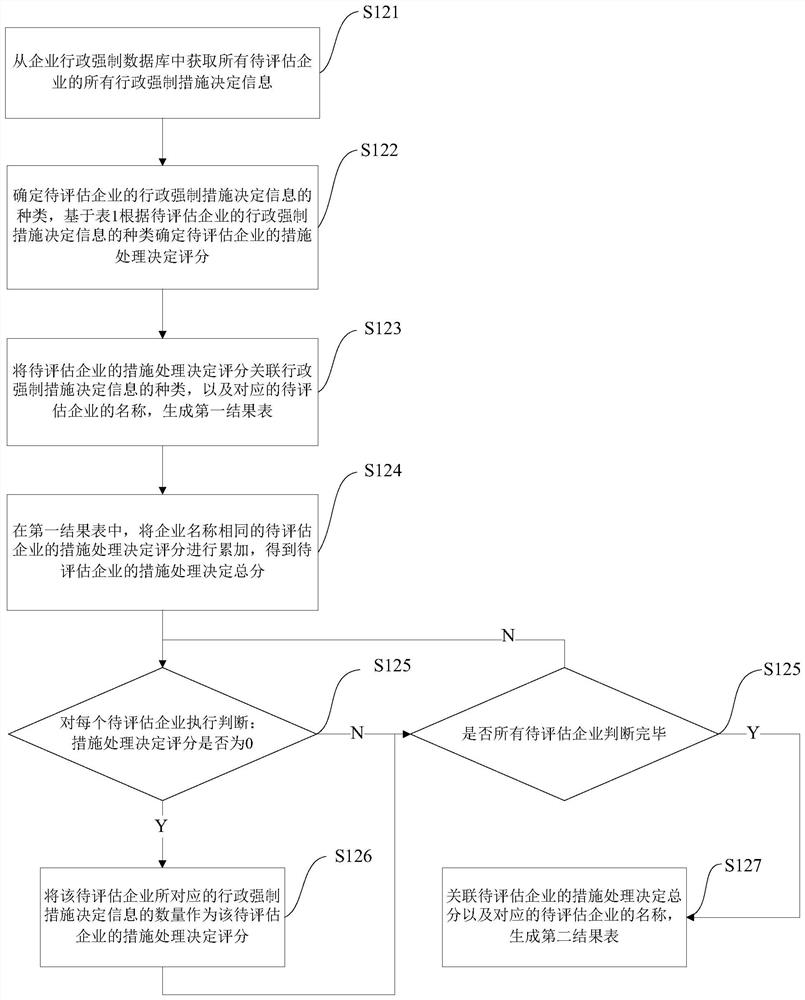
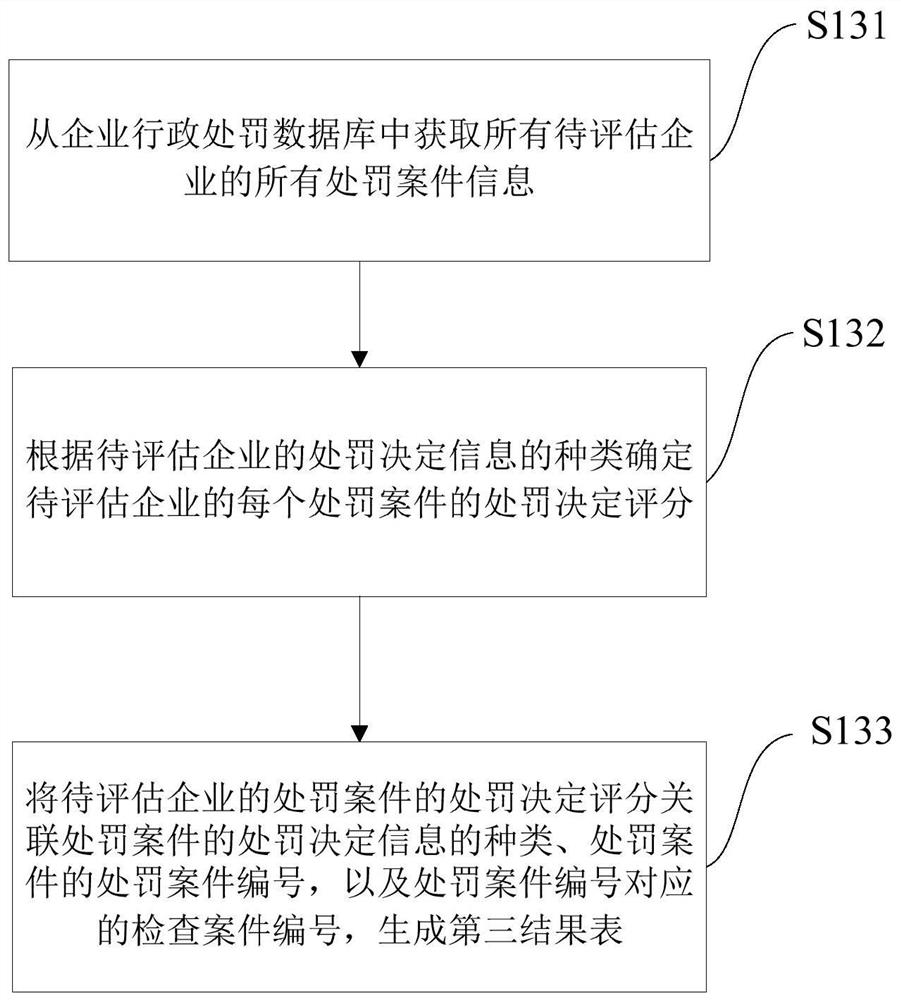
Enterprise operation safety risk assessment method, system, equipment and medium
The invention provides an enterprise operation safety risk assessment method, system and device and a medium. The method comprises the steps of obtaining a to-be-assessed enterprise from an enterprise risk to-be-assessed database; obtaining administrative enforcement measure decision information of the to-be-evaluated enterprise from the enterprise administrative enforcement database, and determining a measure processing decision score according to the type or quantity of the administrative enforcement measure decision information; acquiring punishment decision information of a punishment case of the to-be-evaluated enterprise from an enterprise administrative punishment database, and determining a punishment decision score of the to-be-evaluated enterprise according to the type of the punishment decision information; obtaining an administrative examination result of the to-be-evaluated enterprise from the enterprise administrative examination database, determining an examination result score according to the administrative examination result, and determining an examination and punishment comprehensive score according to the examination result score and the punishment decision score; and determining an enterprise security risk score according to the inspection punishment comprehensive score and the measure processing decision score of the to-be-assessed enterprise. The method is objective and credible, and has huge application value.
Owner:联通(广东)产业互联网有限公司
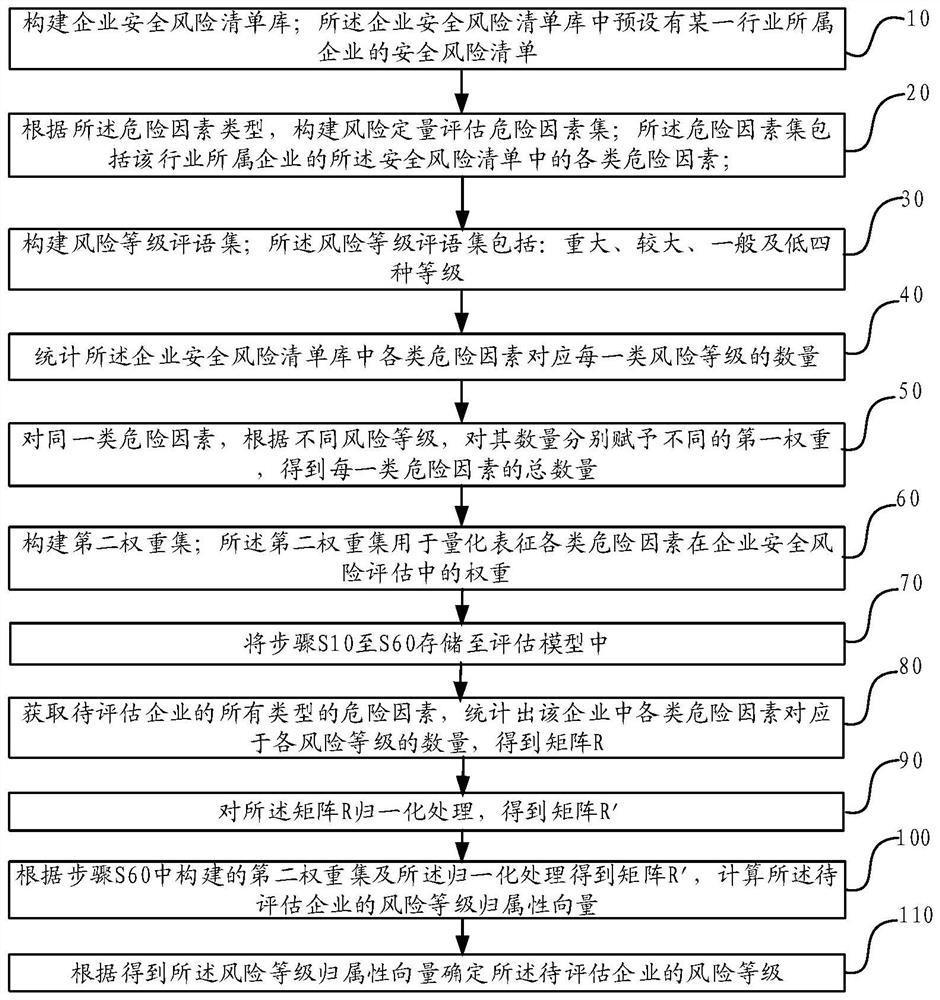
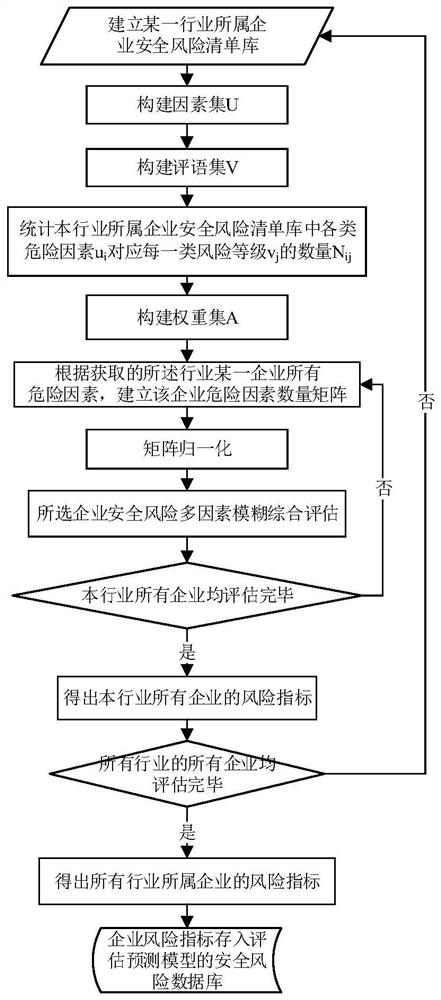
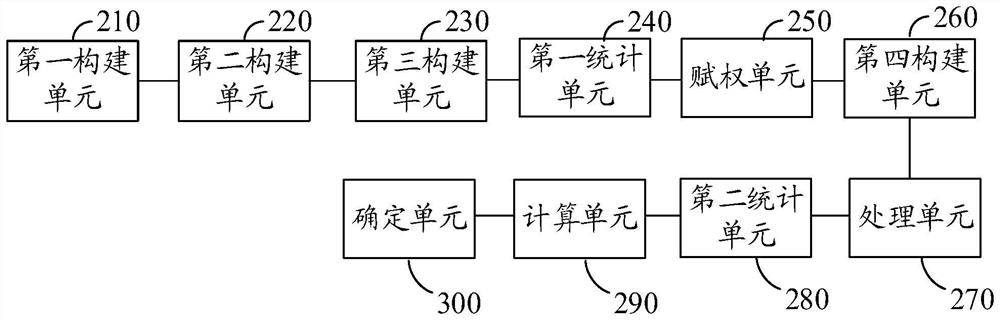
Enterprise security risk assessment method and system, and electronic equipment
The embodiment of the invention discloses an enterprise security risk assessment method and system and electronic equipment, and relates to the technical field of enterprise security risk assessment. The method comprises the following steps: constructing a security risk list library, a risk factor set and a risk level comment set of an enterprise belonging to an industry; counting the number of each risk level corresponding to each risk factor in the enterprise security risk list library; for the same type of risk factors, according to different risk levels, different first weights are given to the number of the same type of risk factors; constructing a second weight set; obtaining all types of risk factors of a to-be-evaluated enterprise, counting the number of risk levels corresponding to various risk factors in the enterprise, obtaining a matrix, and carrying out normalization processing; according to the second weight set and a matrix obtained through normalization processing, calculating a risk level attribution vector of the to-be-evaluated enterprise; and determining the risk level of the to-be-assessed enterprise according to the obtained risk level attribution vector. The risk degree of the enterprise can be quantitatively evaluated.
Owner:NORTH CHINA INST OF SCI & TECH
Enterprise security management system and method based on AI and Internet of Things
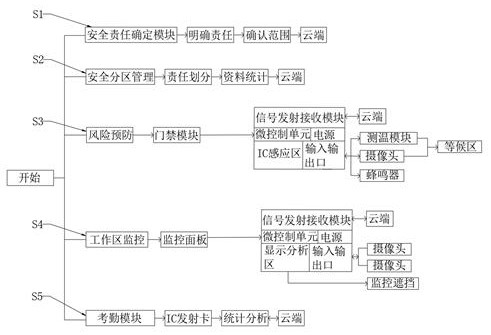
PendingCN113947369AGuarantee the right to life and healthResponsibility breakdownOffice automationIndividual entry/exit registersEnterprise security managementRisk prevention
Owner:南通中安高科电子有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com