Enterprise operation safety risk assessment method, system, equipment and medium
A technology for operating security risks and security risks, applied in data processing applications, resources, calculations, etc., can solve the problems of being unable to objectively and comprehensively reflect the security status of enterprises and strong subjectivity, and achieve effective display forms, comprehensive, The effect of great application value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] This embodiment provides an enterprise operation security risk assessment method, which is used to provide an objective risk assessment method for the enterprise, which does not involve personal experience judgment.
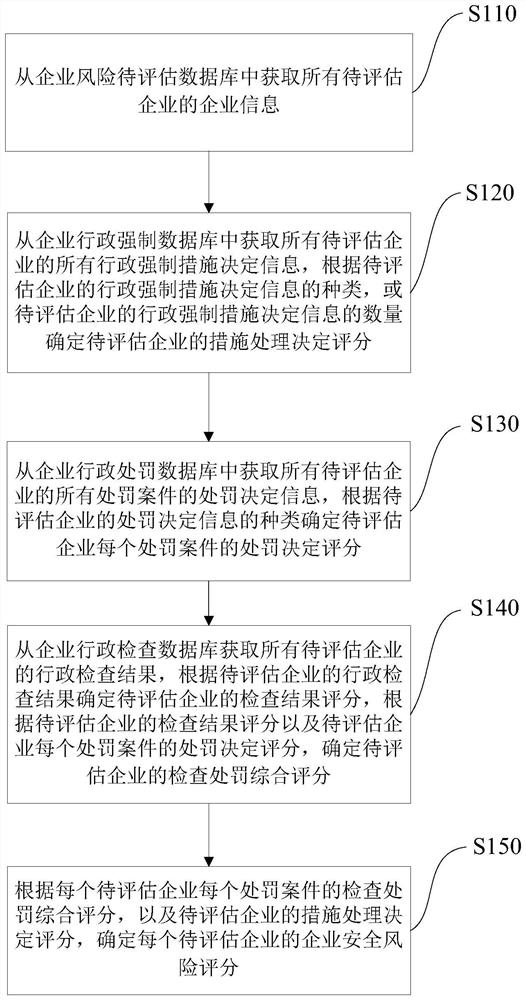
[0033] Such as figure 1 As shown, the method includes:
[0034] S110: Obtain enterprise information of all enterprises to be assessed from the enterprise risk assessment database;
[0035] In this step, the enterprise to be assessed refers to the enterprise that uses this method for risk assessment. The enterprise risk assessment database stores the information of several enterprises, which can be stored according to different types of enterprises. The stored enterprise information is at least Including the enterprise name, enterprise code, etc. of the enterprise. In the enterprise risk assessment database, each enterprise is pre-allocated with a unique identifier to distinguish it from other enterprises. When obtaining the enterprise information of all...
Embodiment 2
[0134] Based on the same idea as in Embodiment 1, such as Figure 6 As shown, this embodiment provides an enterprise operation security risk assessment system, including:
[0135] A data acquisition module 210, configured to acquire all enterprises to be assessed from the enterprise risk assessment database;
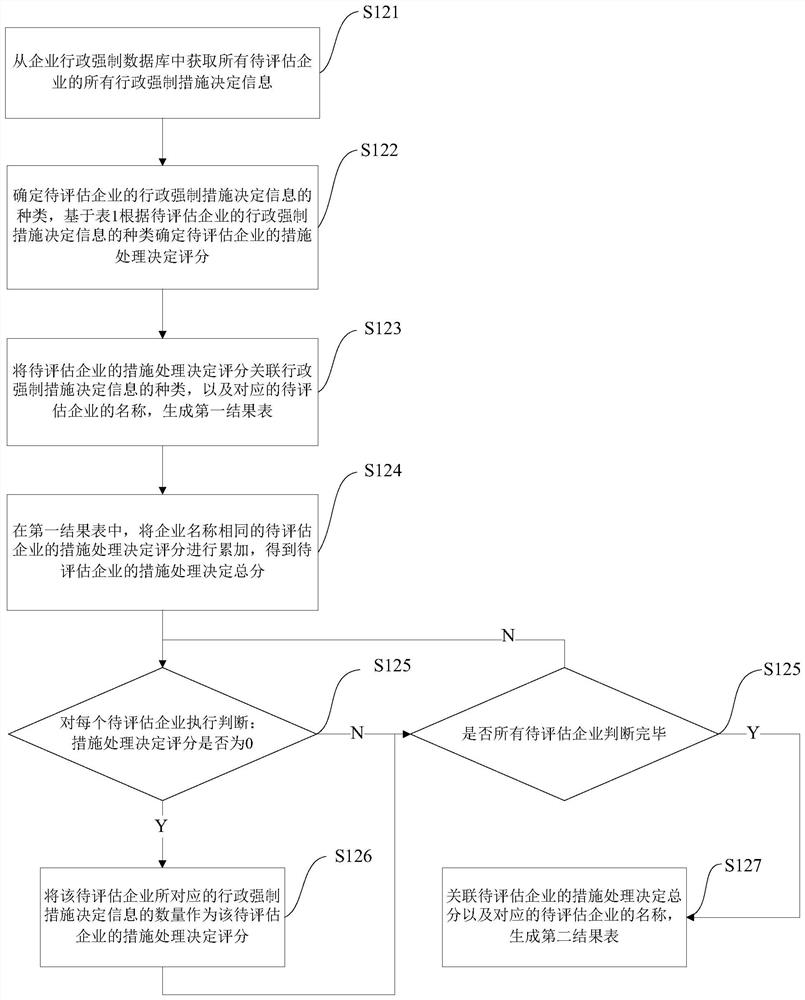
[0136] The first data processing module 220 is used to obtain all administrative compulsory measures decision information of all enterprises to be evaluated from the enterprise administrative compulsory database, and determine information according to the types of administrative compulsory measures of the enterprises to be evaluated, or determine the administrative compulsory measures of the enterprises to be evaluated The amount of information determines the measure-handling decision score for the enterprise to be assessed;
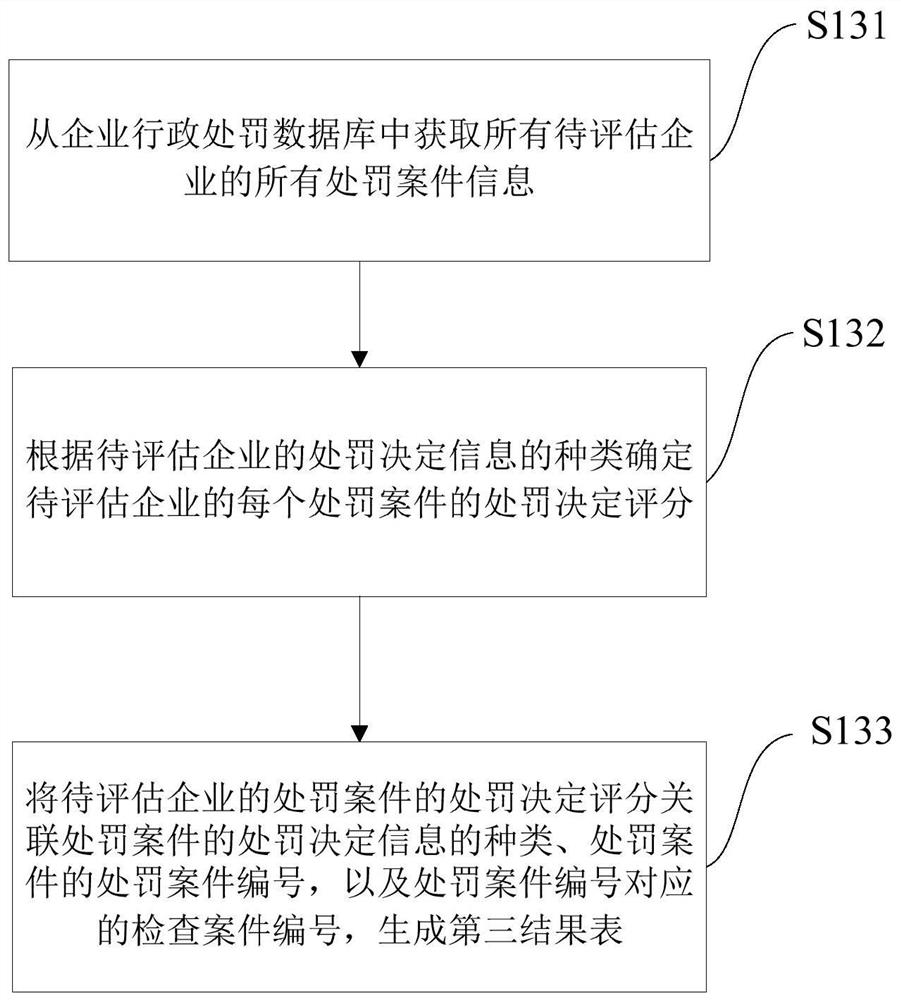
[0137] The second data processing module 230 is used to obtain the punishment decision information of all punishment cases of all enterprises to ...
Embodiment 3
[0152] Based on the same ideas as in Embodiment 1, this embodiment provides a computer device, including a memory and a processor, the memory stores a computer program, and the processor implements the enterprise provided by Embodiment 1 when executing the computer program. Run the security risk assessment methodology.
[0153] This embodiment also provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is executed by a processor, the enterprise operation security risk assessment method provided in Embodiment 1 is implemented.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com