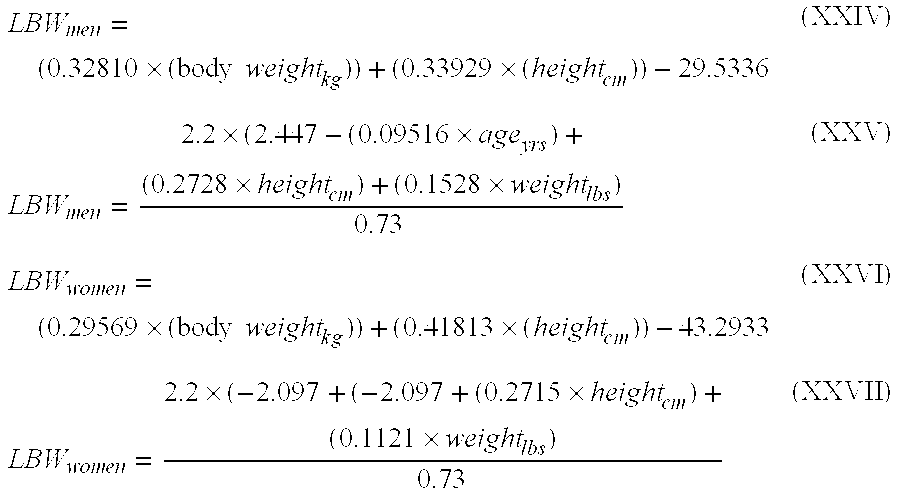Patents
Literature
228 results about "Non compliance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Non-compliance refers to the conduct of research that is inconsistent with the requirements or determinations of the IRB (IRB-approved research protocol, informed consent document or process) or an allegation of such non-compliance.
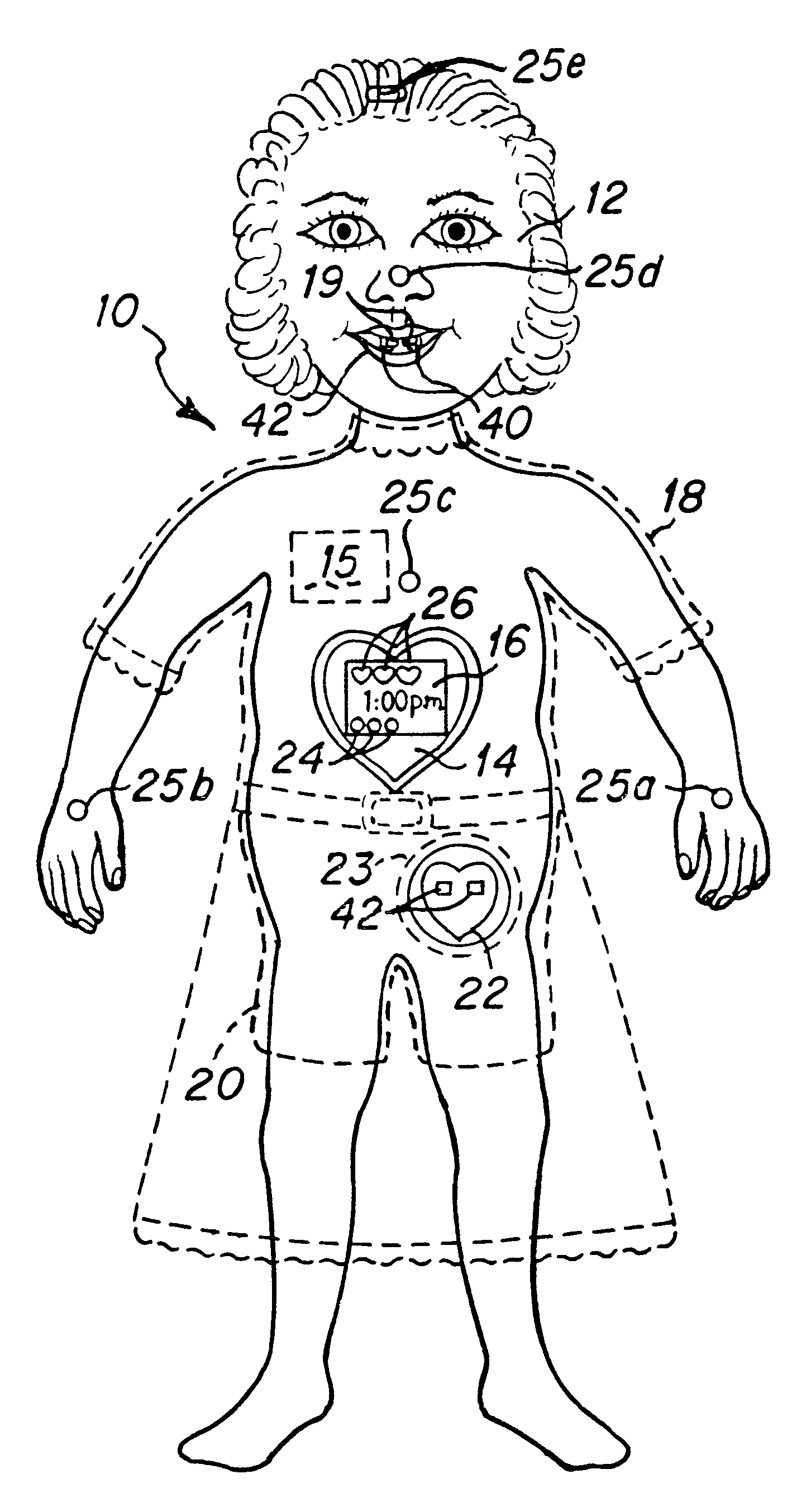
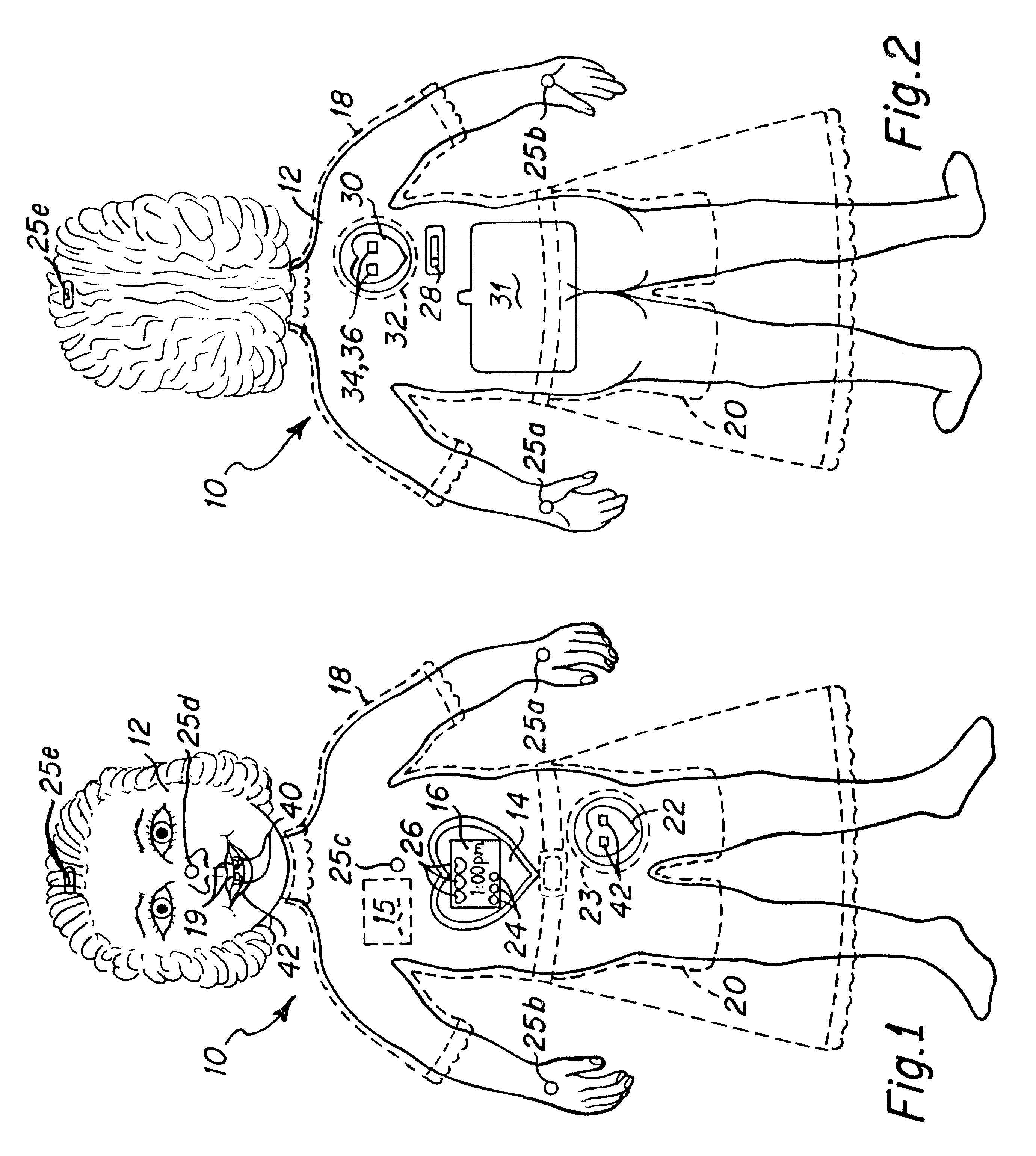
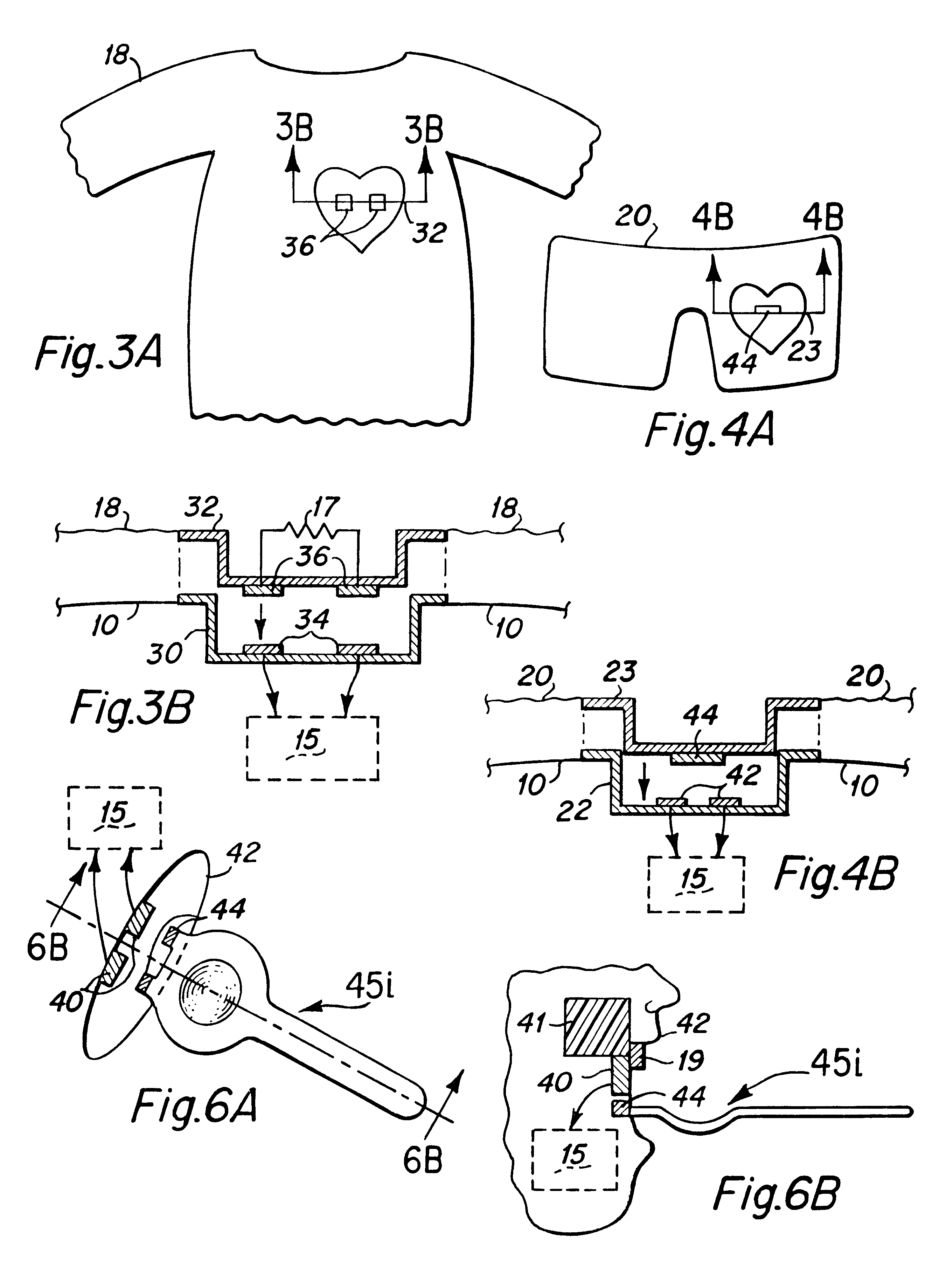
Interactive virtual character doll
The interactive doll simulates the character of a live person or, in other embodiments a fantasy figure or animal, in essence, simulating a living being that possesses respective human or animal qualities: displaying specific needs, tenderness, intelligence and / or understanding. The doll contains a clock or other timekeeping device and thereby knows of the time of day. It automatically enters a sleep mode at a preset sleep time during which the playtoy remains quiet, and wakens at a preset hour of the day, issuing a verbal statement to let the player know it is time to again play. By issuing a sequence of verbal requests from time to time to the player to take action of various kinds on or with the doll, determines the player's compliance or noncompliance with each such request and issues a verbal message appropriate to such compliance or non-compliance. Some of the verbal requests made are of a kind that occur at a particular time of day in the life of the character being synthesized, such as a request for a food or beverage at breakfast time, lunch time or supper time. And, from time to time at its own initiative, the playtoy may issue verbal messages of affection to the player. That doll is accompanied by external objects that simulate a variety of foods, a beverage, medicine and the like, which the doll is to be applied by the player to the doll pursuant to specific verbal requests from the doll and the doll is able to identify those objects for enhanced interactive play with the player.
Owner:PLAYMATES TOYS
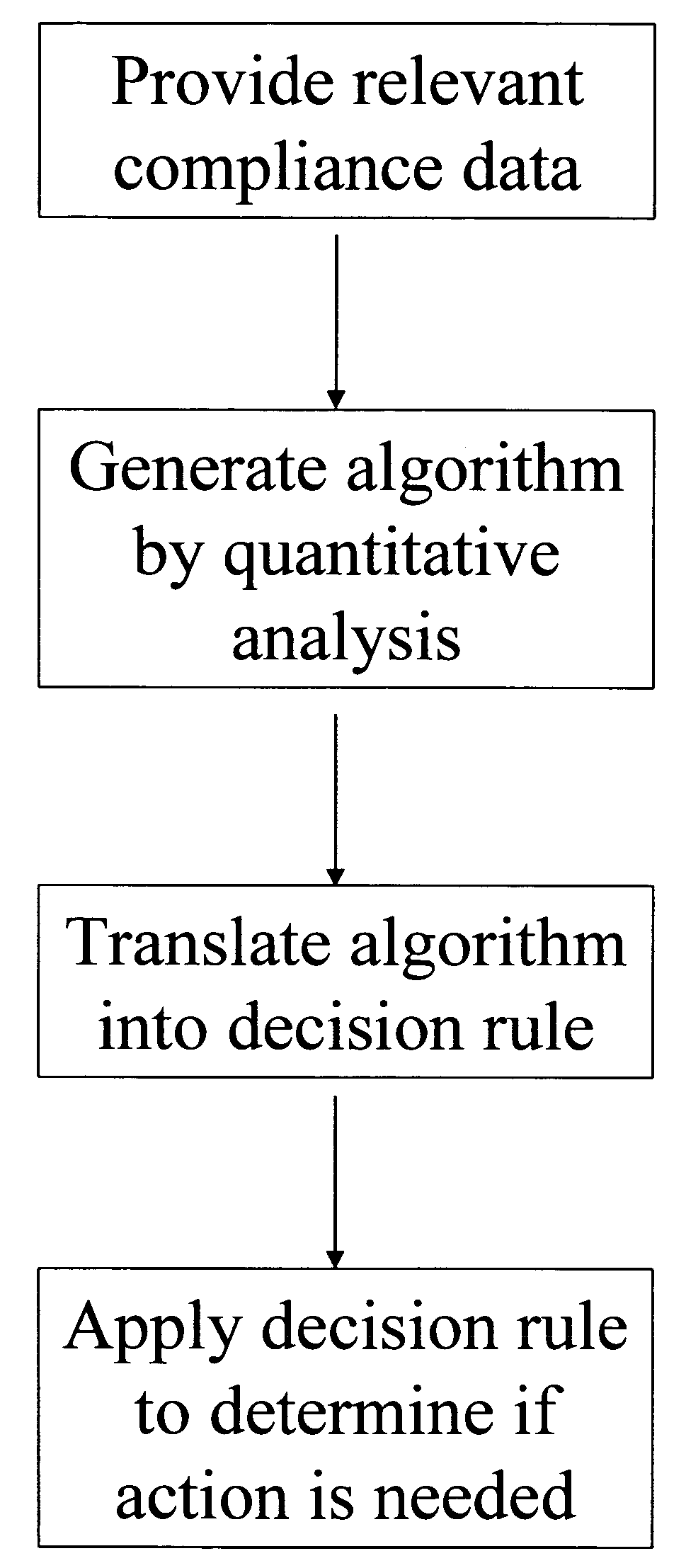
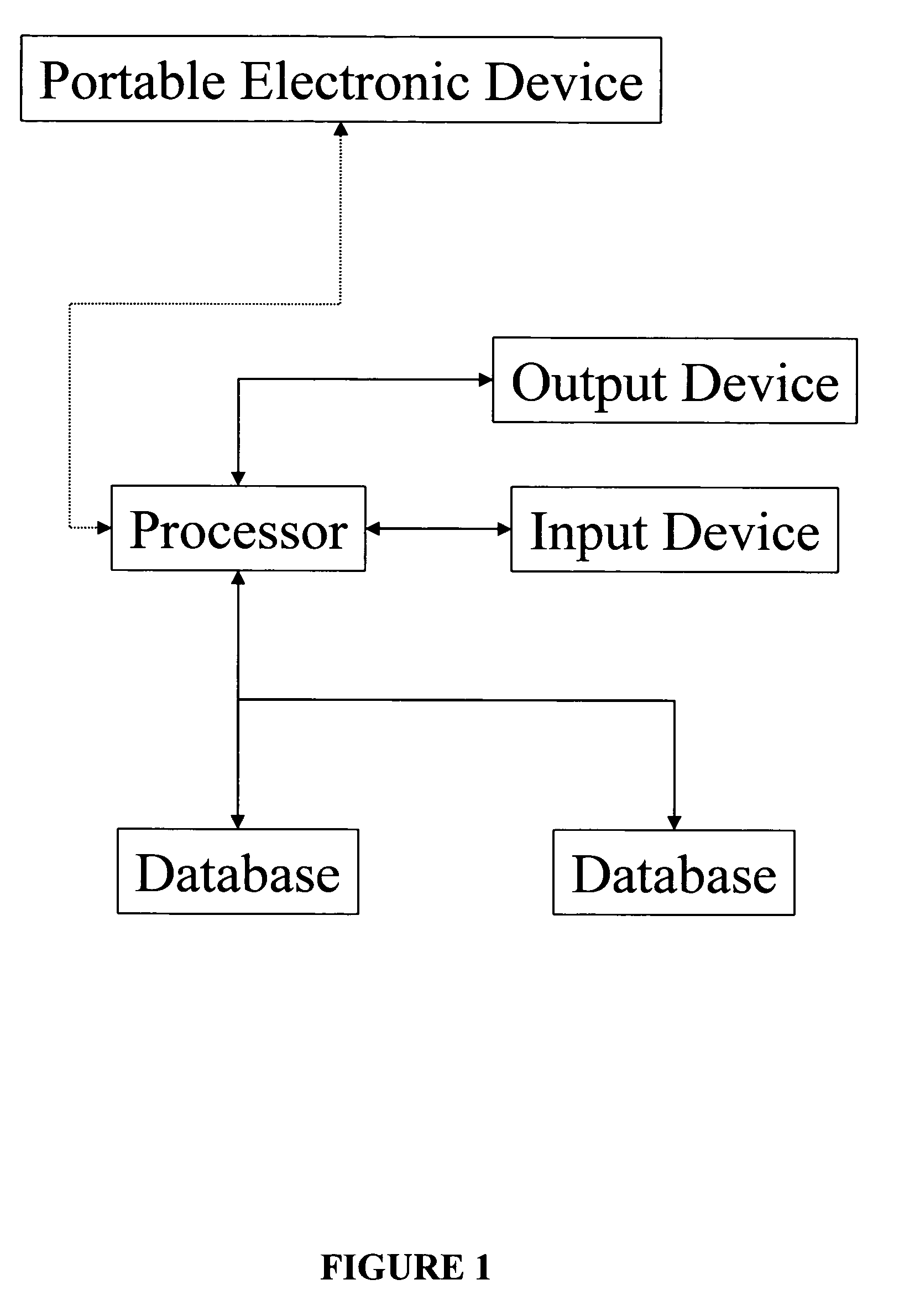
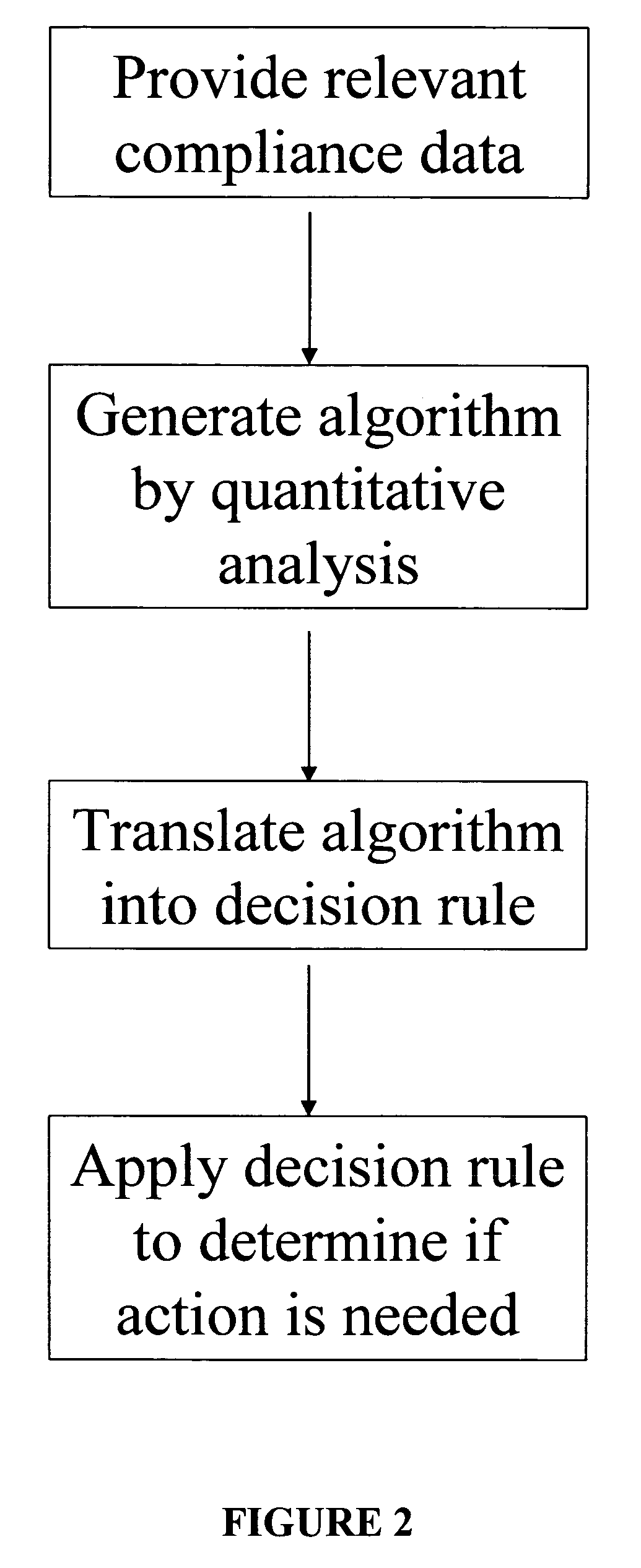
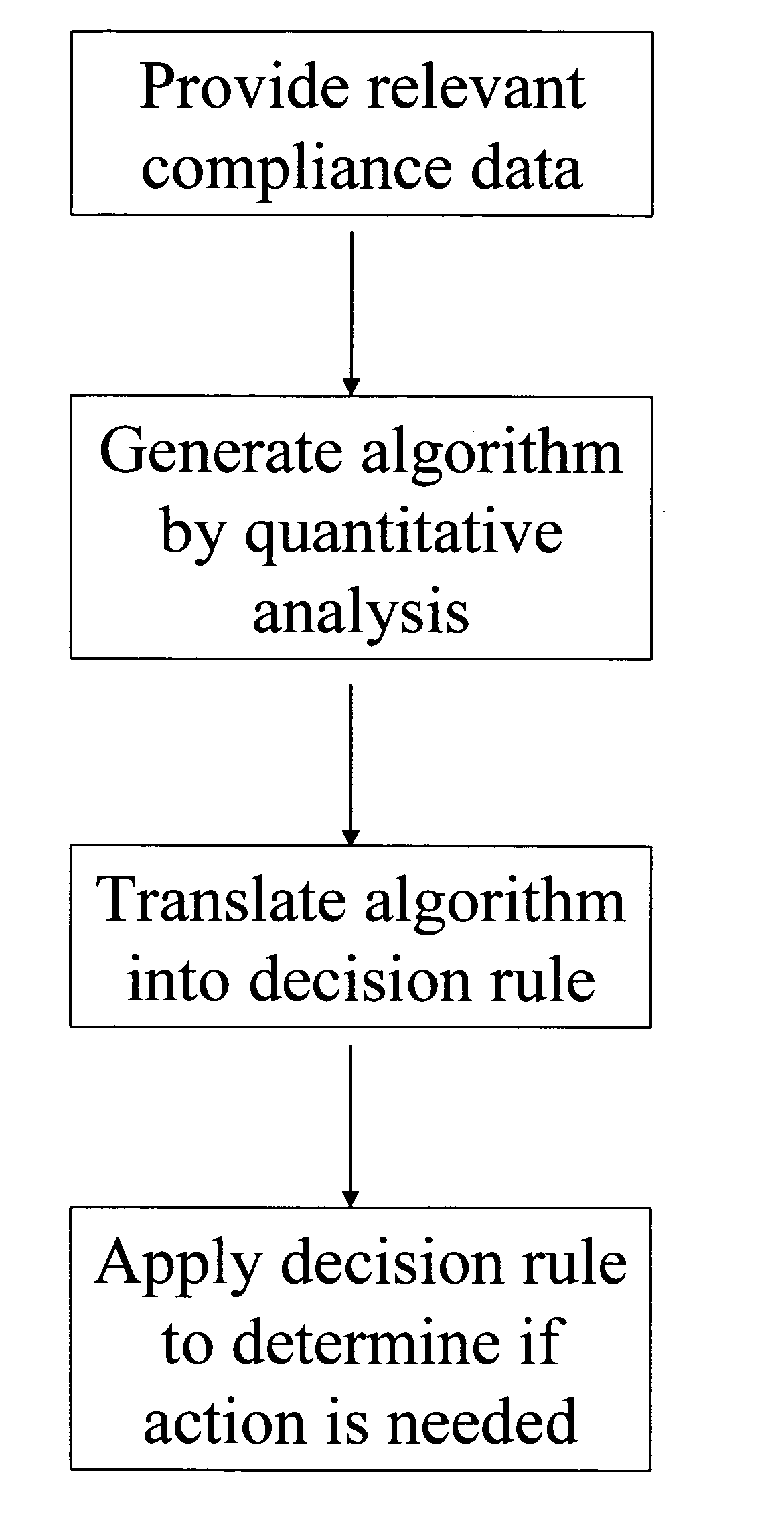
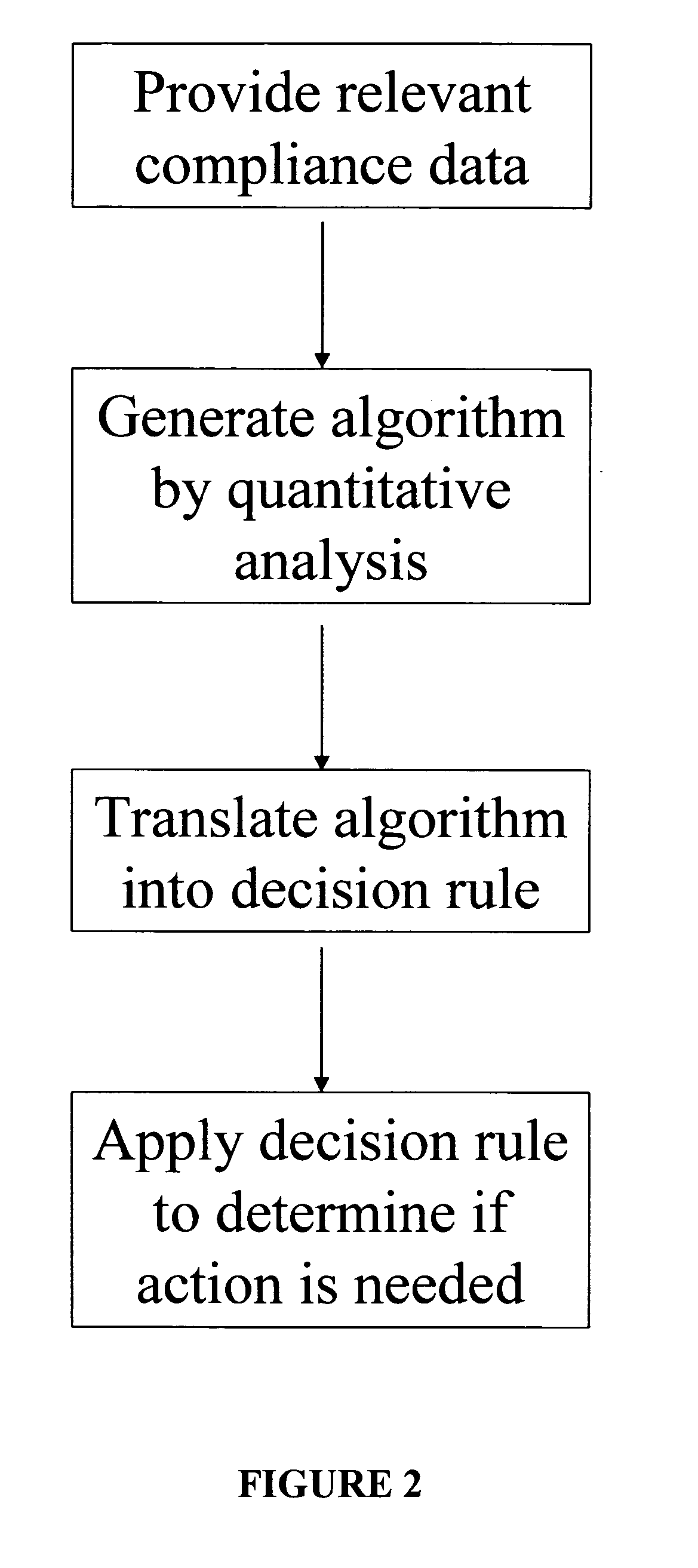
Apparatus and method for prediction and management of participant compliance in clinical research
InactiveUS7415447B2Reduce testing costsImprove statistics performanceDigital computer detailsForecastingNon complianceClinical trial
A system for developing and implementing empirically derived algorithms to generate decision rules to determine participant noncompliance and fraud with research protocols in clinical trials allows for the identification of complex patterns of variables that detect or predict participant noncompliance and fraud with research protocol, including performance and enrollment goals, in the clinical trial. The data may be used to overall predict the performance of any participant in a clinical trial, allowing selection of participants that tend to produce useful, high-quality results. The present invention can also be used to monitor participant compliance with the research protocol and goals to determine preferred actions to be performed. Optionally, the invention may provide a spectrum of noncompliance, from minor noncompliance needing only corrective feedback, to significant noncompliance requiring participant removal from the clinical trial or from future clinical trials. The algorithms and decision rules can also be domain-specific, such as detecting non-compliance or fraud among subjects in a cardiovascular drug trial, or demographically specific, such as taking into account gender, age or location, which provides for algorithms and decision rules to be optimized for the specific sample of participants being studied.
Owner:ERESTECH
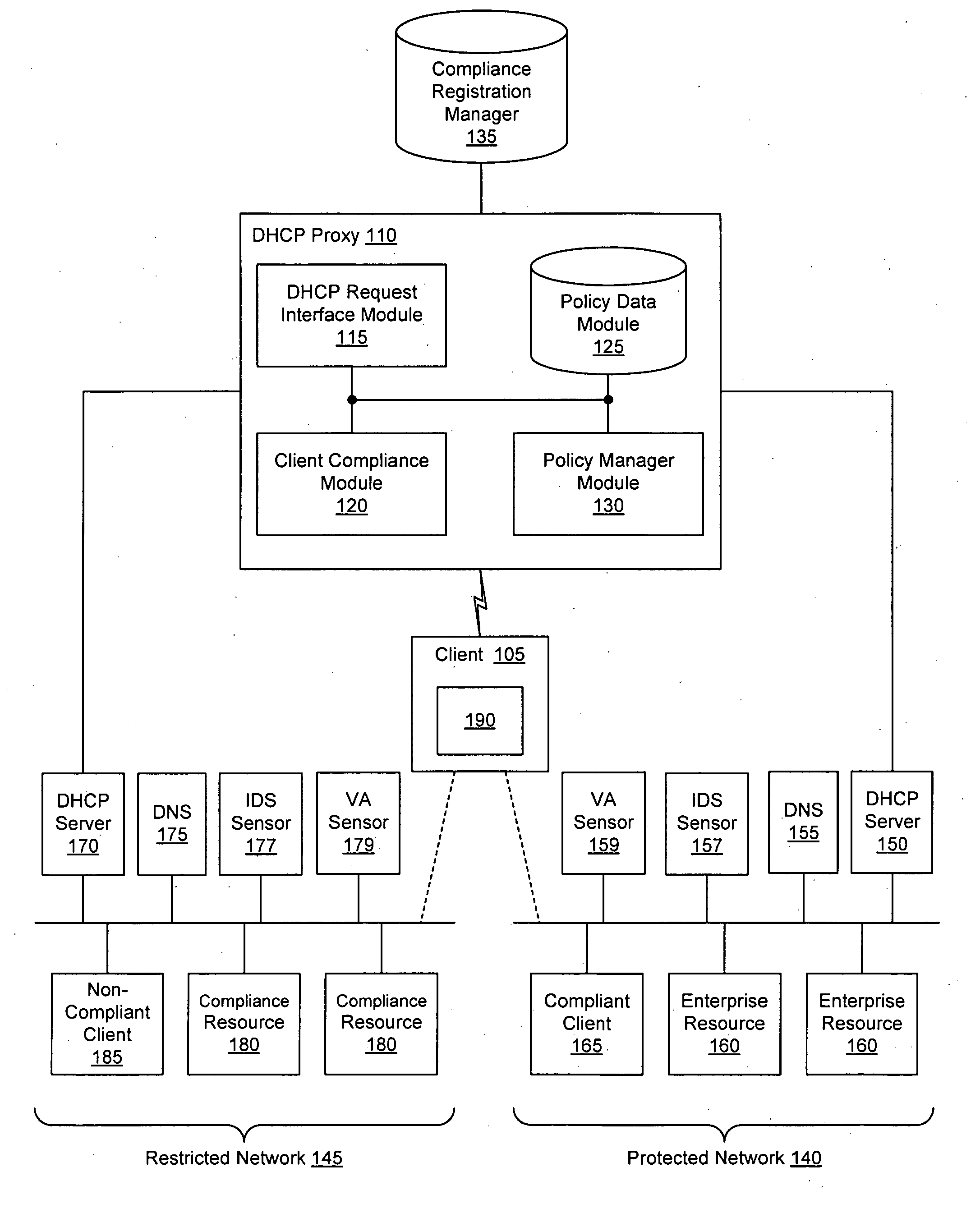
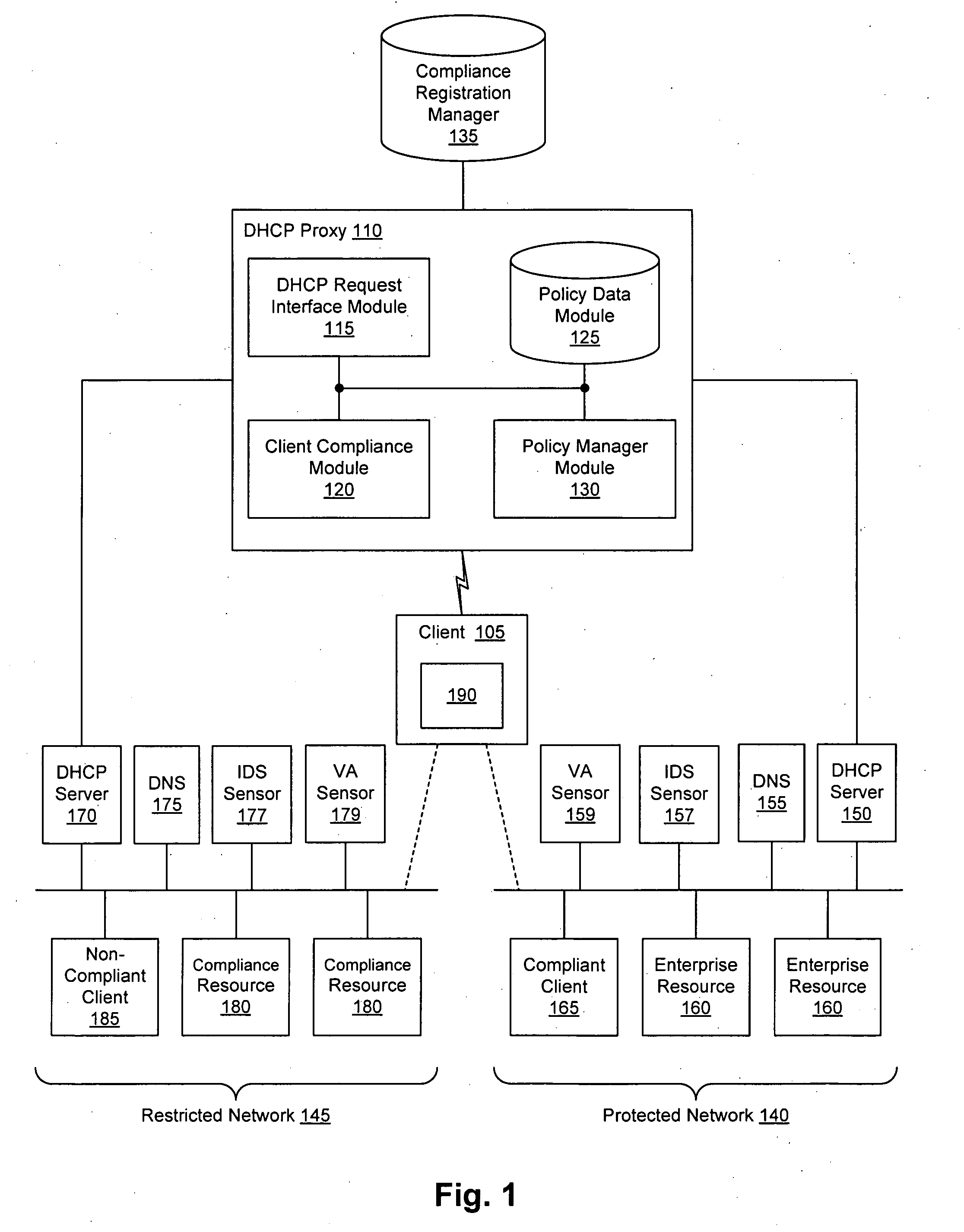
Client compliancy with self-policing clients
InactiveUS20060130139A1Memory loss protectionDigital data processing detailsNon complianceClient compliance
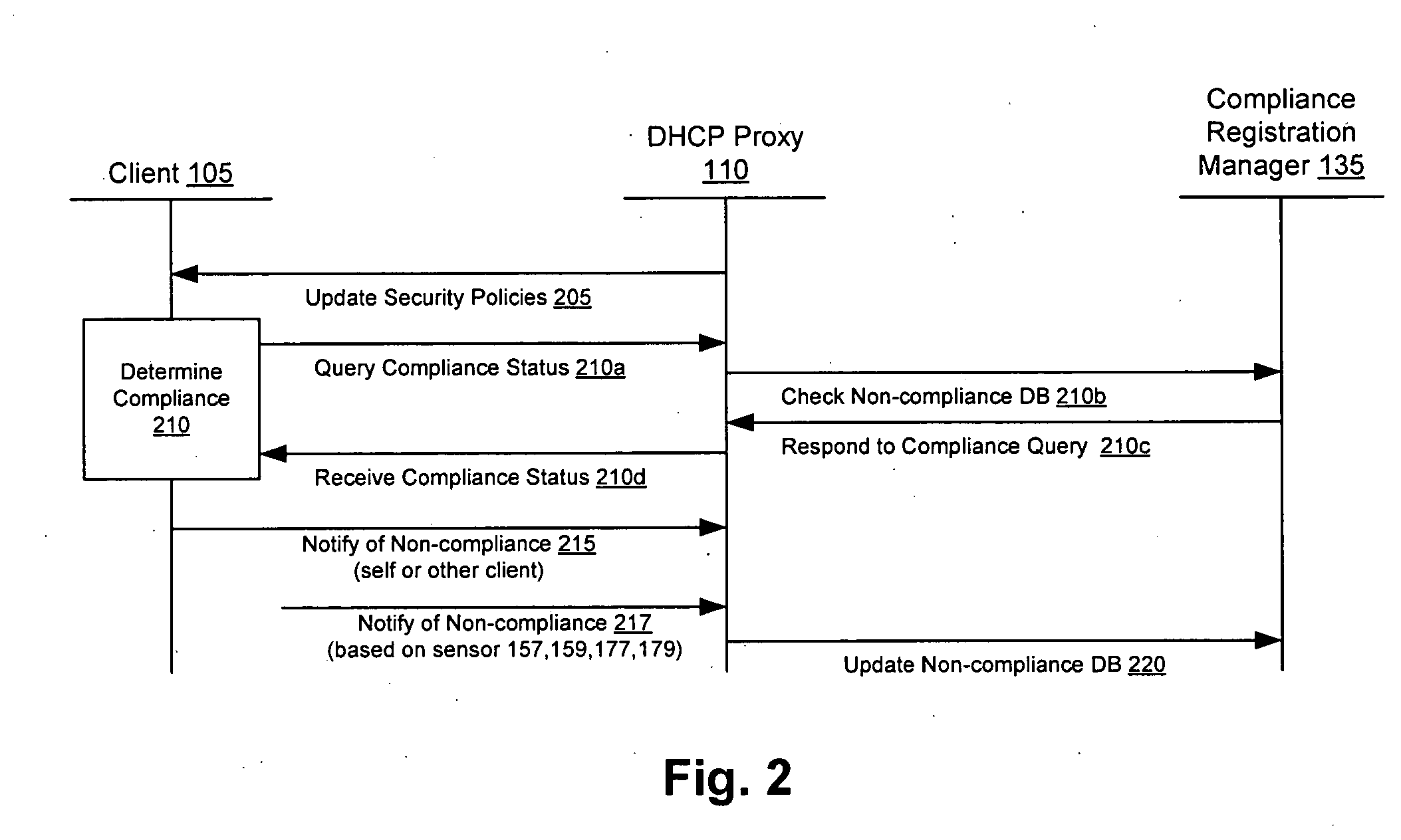
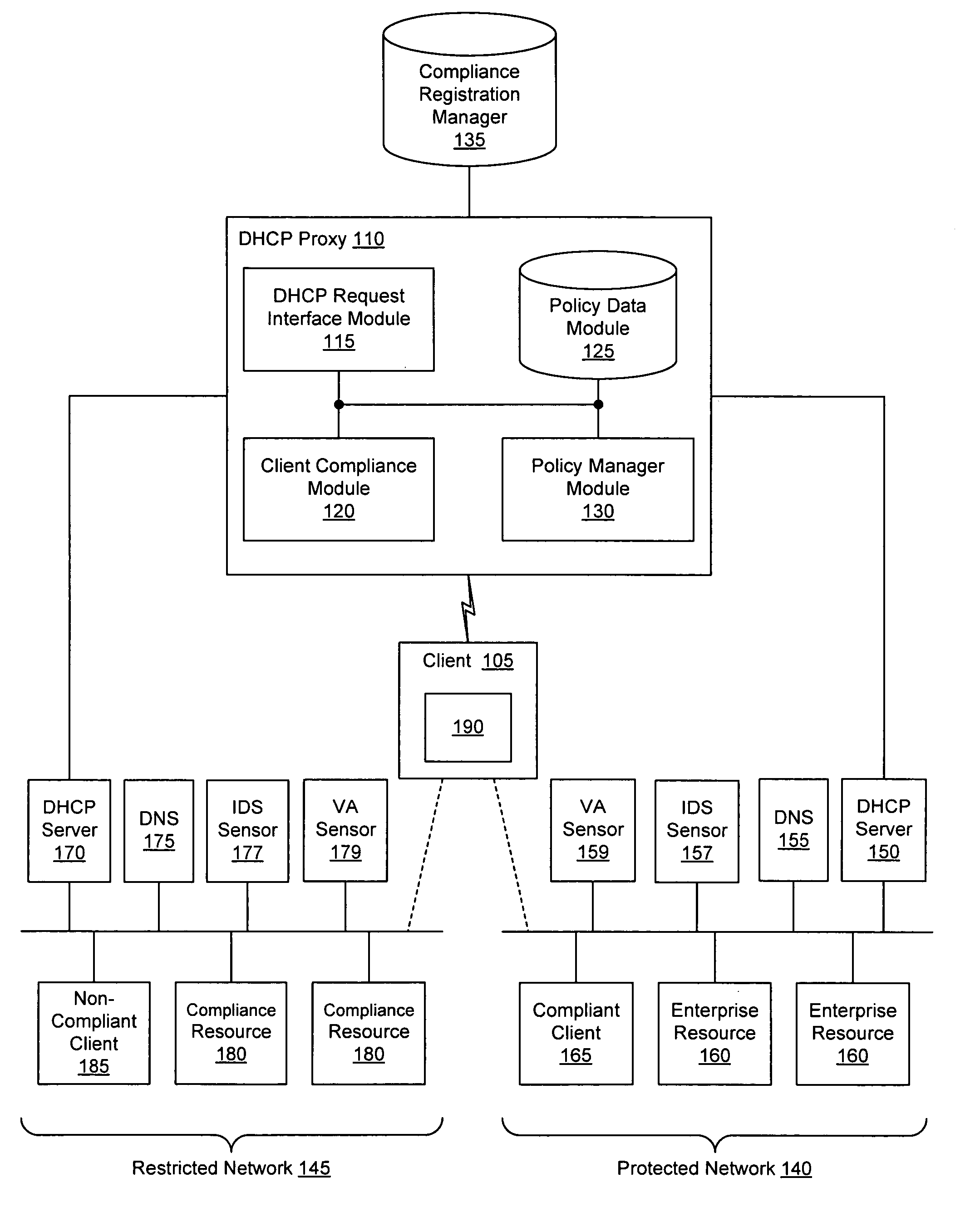
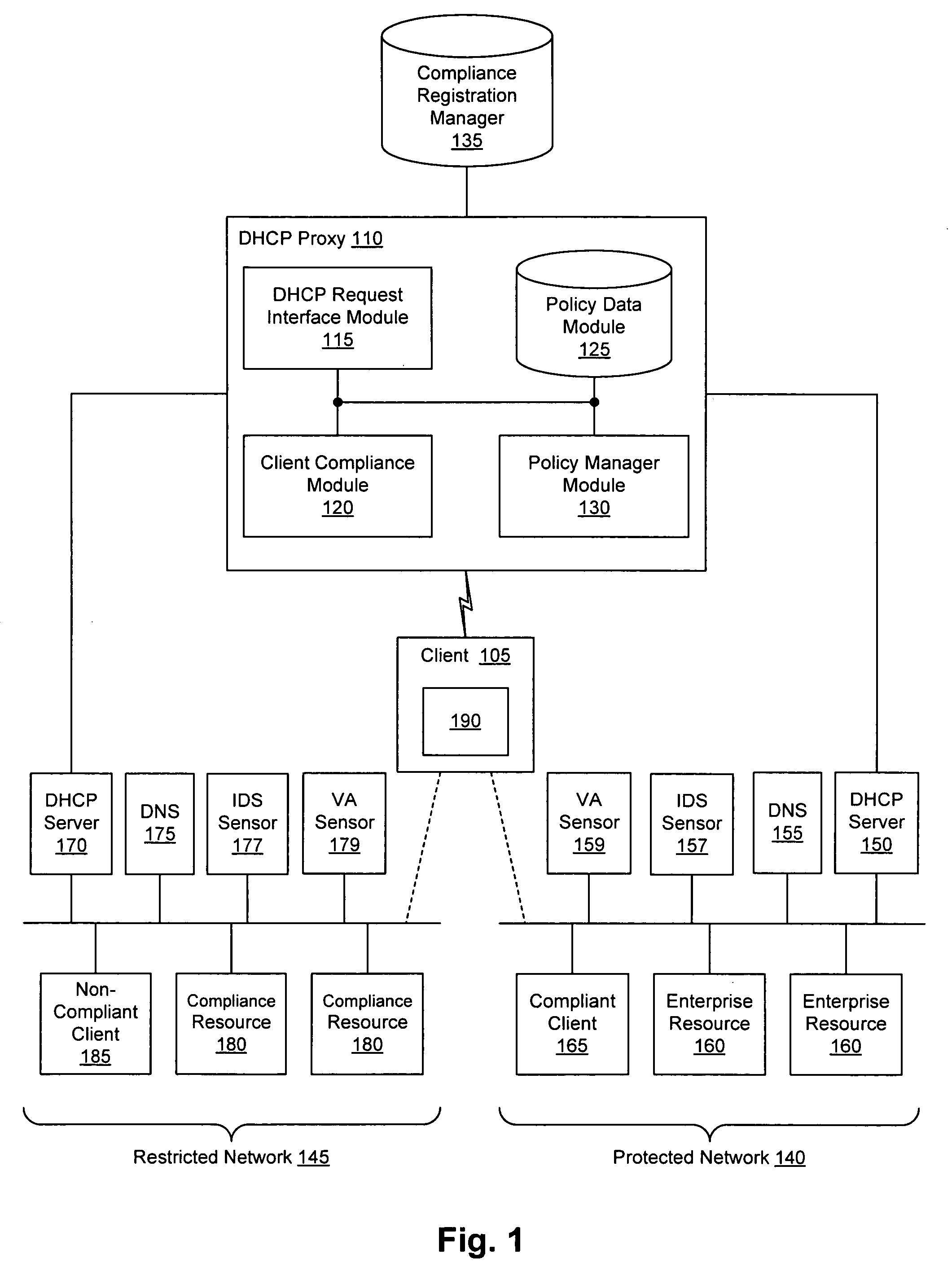
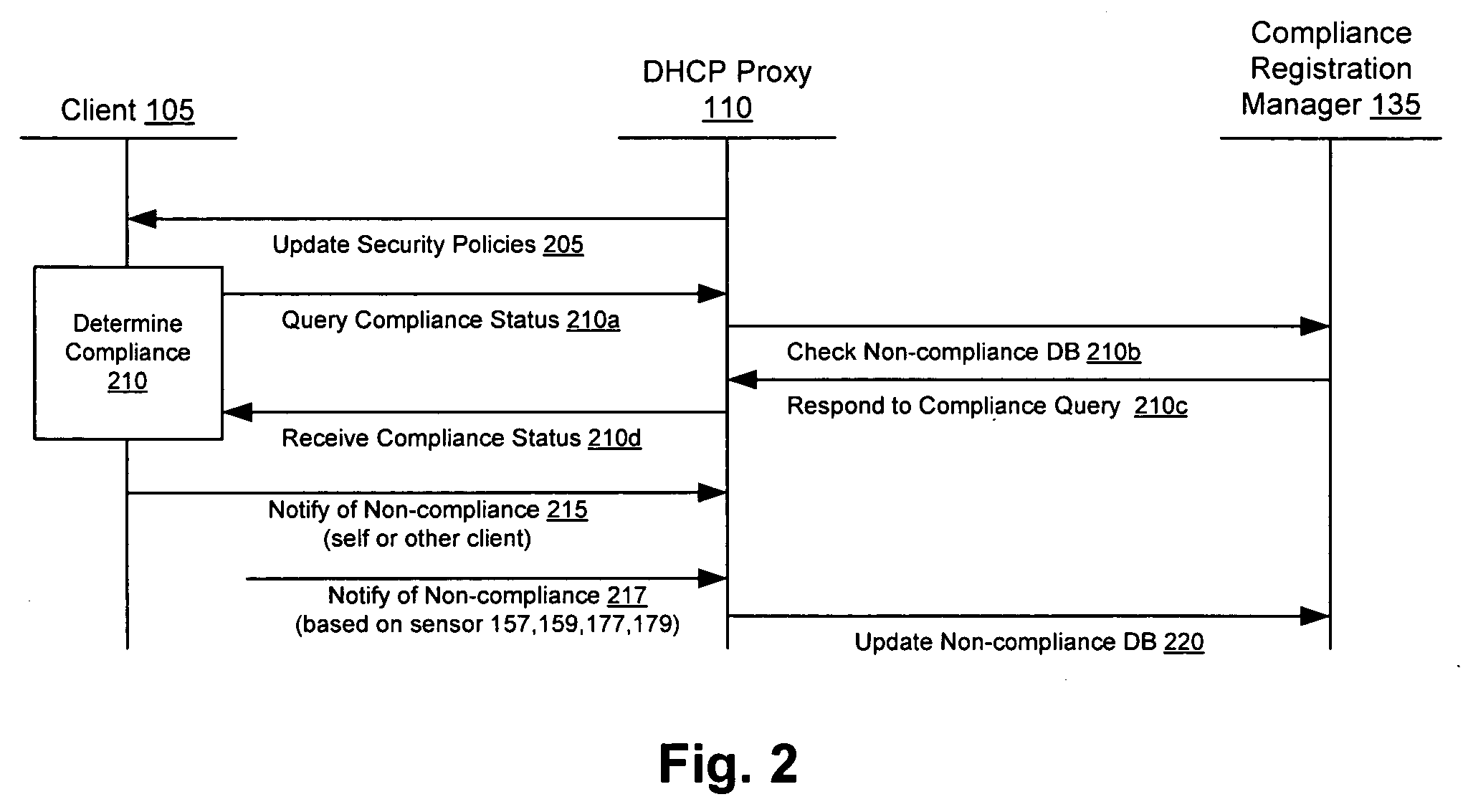
Security sensor data from intrusion detection system (IDS) sensors, vulnerability assessment (VA) sensors, and / or other security sensors is used to enhance the compliancy determination in a client compliancy system. A database is used to store the security sensor data. In one particular embodiment, a list of device compliance statuses indexed by corresponding identifiers (e.g., IP / MAC addresses) combined from IDS, VA, and / or other security sensing technologies is made available as a non-compliance database for query, so that clients and other compliancy authentication elements can tell that a particular client appears to be out of compliance. A client-side self-policing compliance system is enabled, and can be used in conjunction with automated endpoint compliance policy configuration to reduce system administrator burden.
Owner:CA TECH INC
System and method for managing global risk
InactiveUS20020129221A1Level of risk is minimizedLoss of competitive advantageGeneral purpose stored program computerOffice automationRisk statusNon compliance
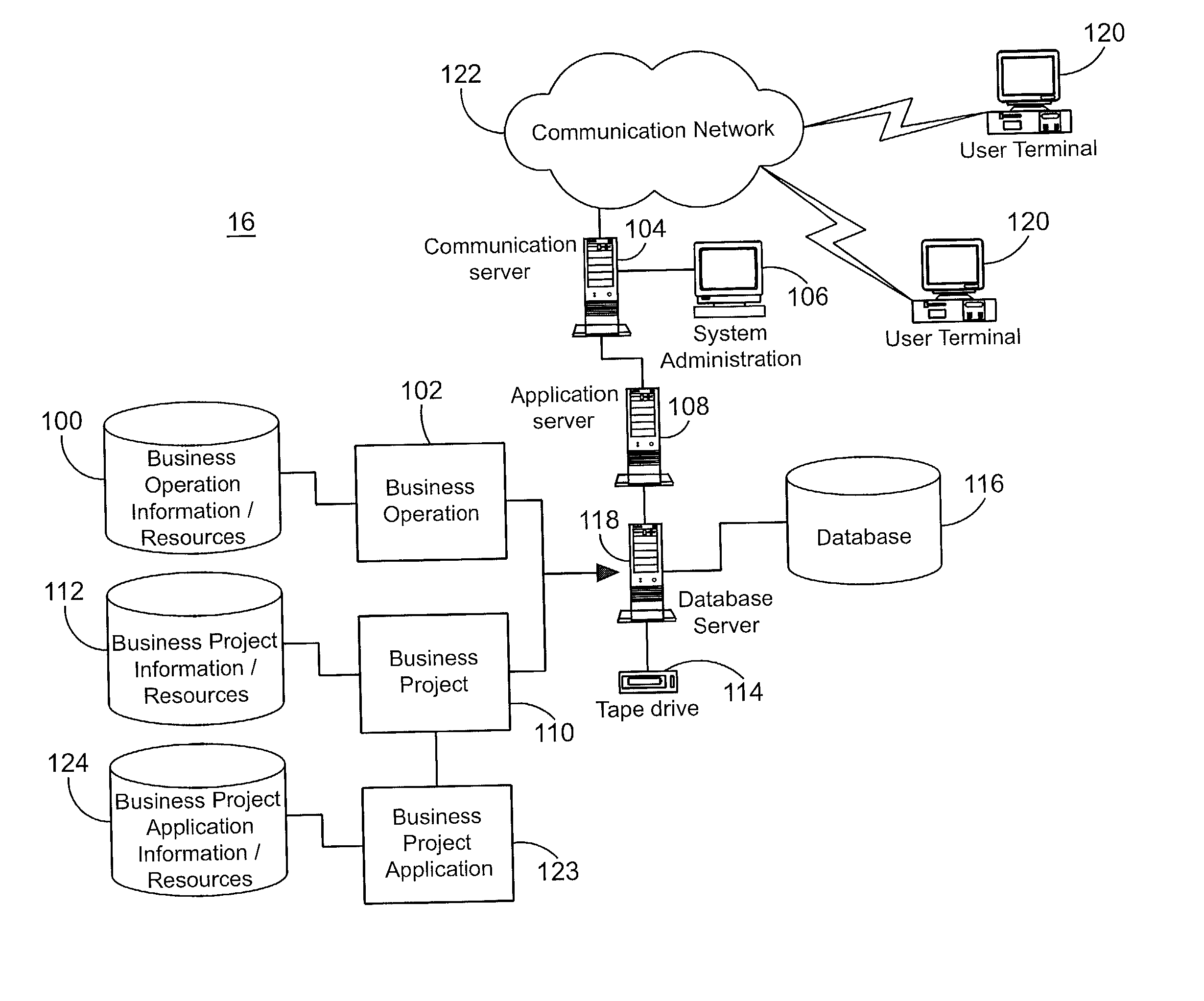
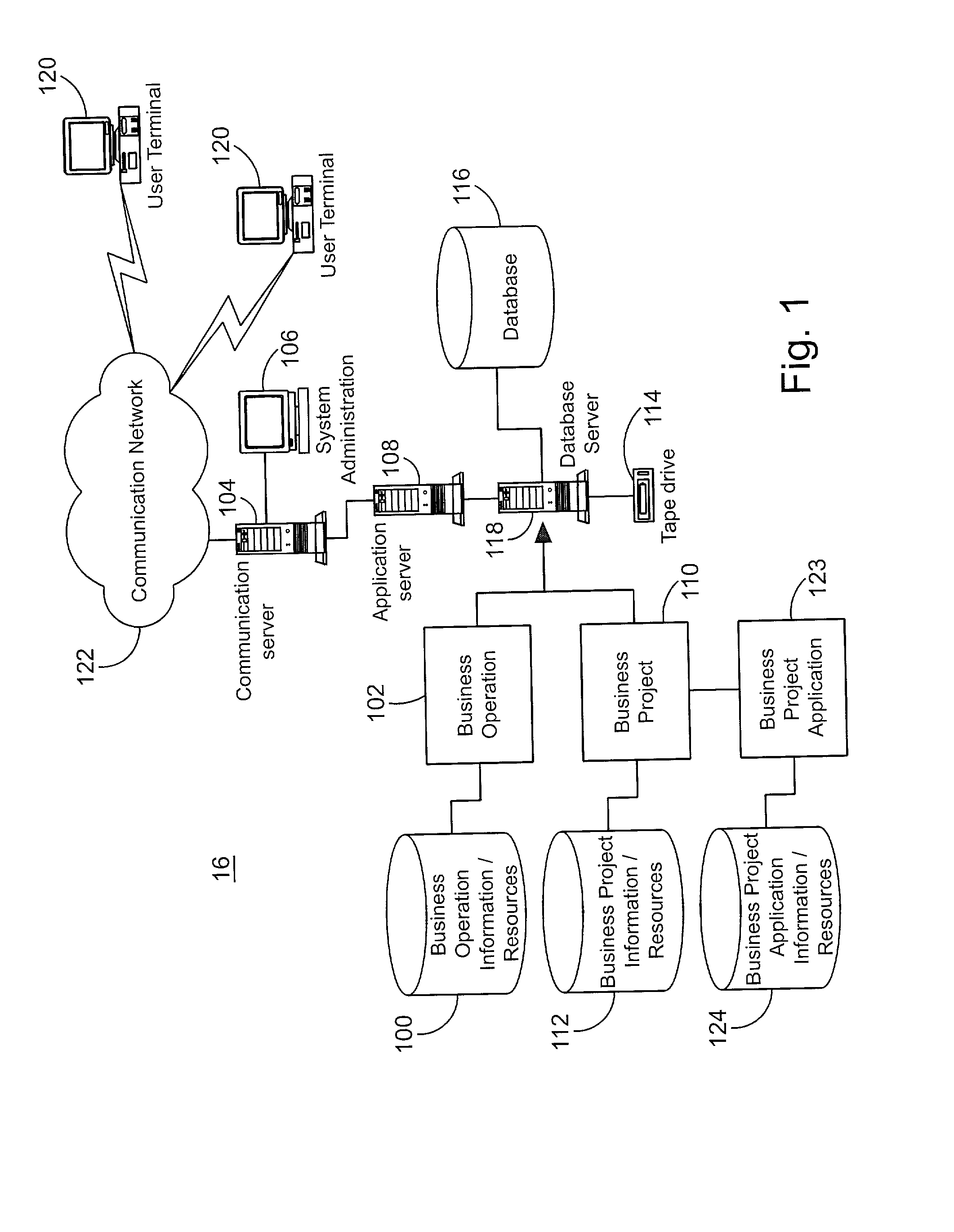
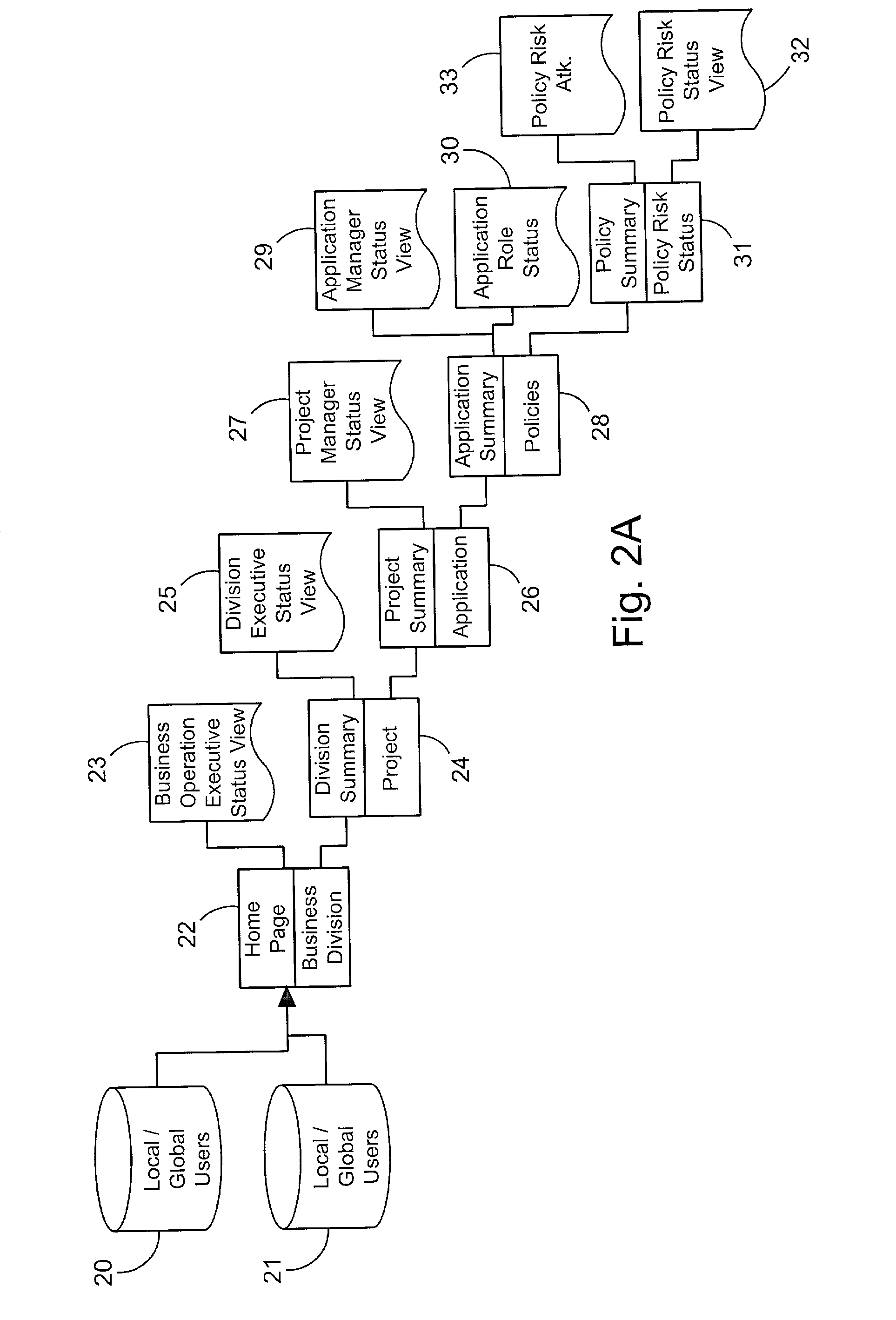
A system for tracking compliance with policies related to management of risk for a given enterprise provides risk status feedback on a number of managerial levels. The system notifies users of potential problems with non-compliance of enterprise policies set on a high level of enterprise management, and prompts the users to take steps to achieve compliance. The enterprise policies are designed to protect the enterprise from various forms of risk associated with enterprise activities. Accordingly, minimizing risk across enterprise operations, subdivisions, projects and applications produces an overall benefit of reduced liability or exposure to liability for the entire enterprise. A compliance status is provided by business groups at all levels of the enterprise, and consolidated for each management level to which the risk status is promoted. Higher level managers can view summaries of risk management status for the business divisions, and select particular statuses to view the condition of compliance among various business groups for which the manager has responsibility.
Owner:JPMORGAN CHASE BANK NA
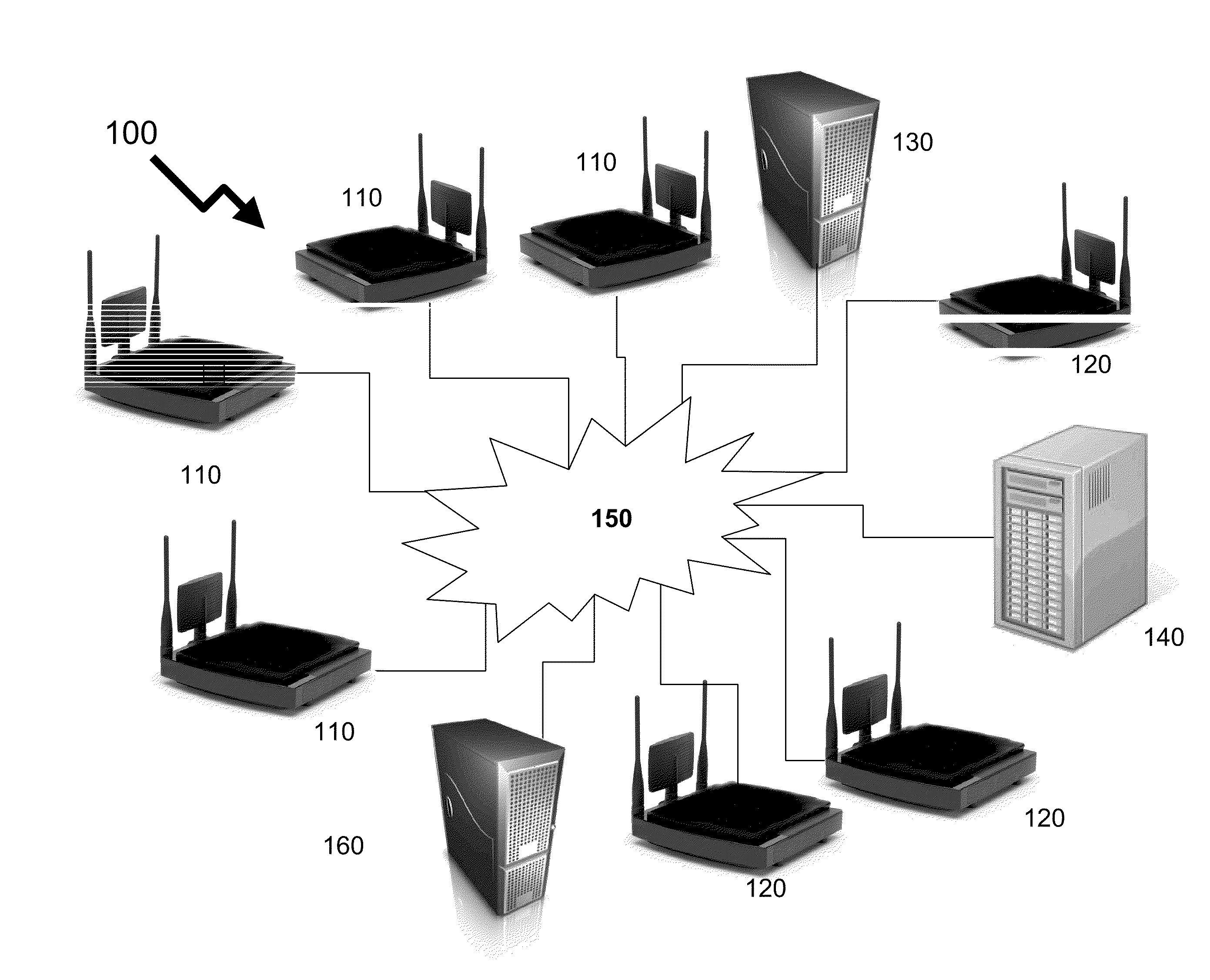
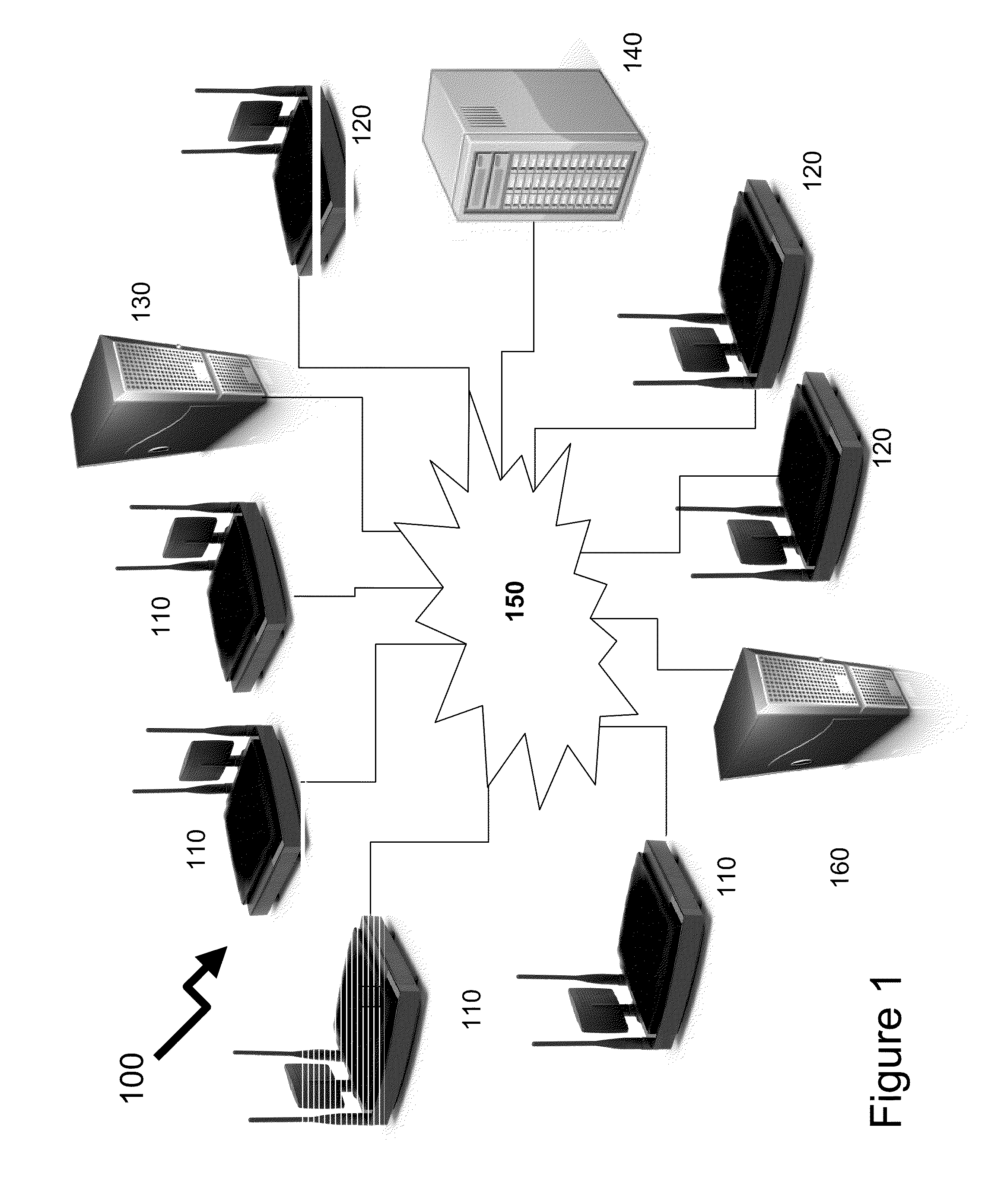
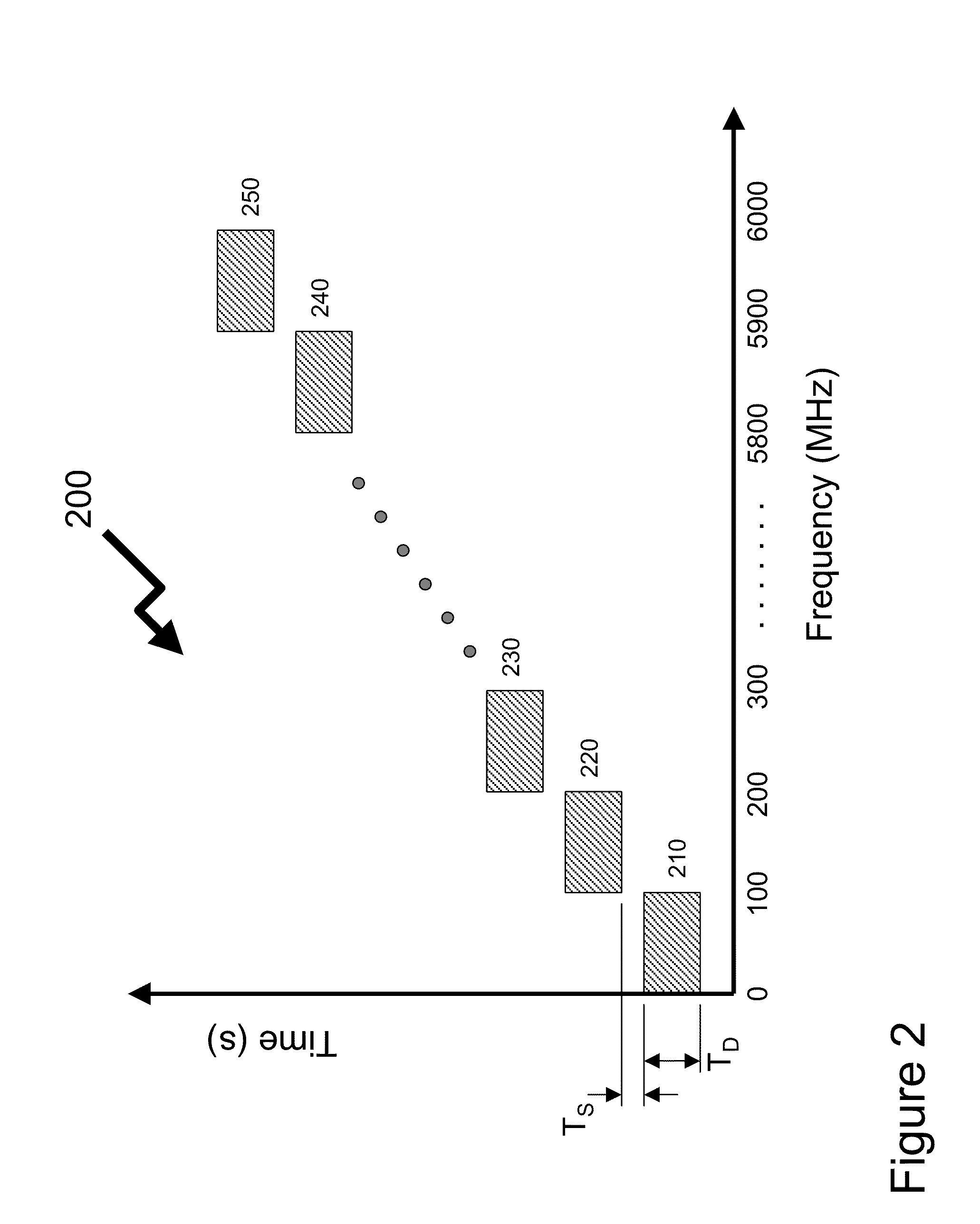
System and method for detecting RF transmissions in frequency bands of interest across a geographic area
ActiveUS20110185059A1Reduce communication overheadLow costNetwork topologiesDigital computer detailsFrequency spectrumNon compliance
Wireless devices form a significant portion of equipment forming the source / destination of content transmitted over telecommunications infrastructure together with applications such as RF identification, smart tags, etc. As such the wireless spectrum supports these devices operating to multiple standards, both licensed and unlicensed. In many environments it would be beneficial for a network administrator to know whether the environment and network they are responsible for is compliant to policies established in dependence of the environment / network. The invention provides distributed wireless signal analyzers within the environment / network to provide signal / spectrum analysis and determine whether received signals by the wireless signal analyzer are compliant to the network administrator policy. Compliance may be based upon time or frequency domain measurements with different rules for different wireless spectrum regions. Non-compliance is communicated to remote servers and / or network administrator and allows local control of network equipment.
Owner:THINKRF CORP
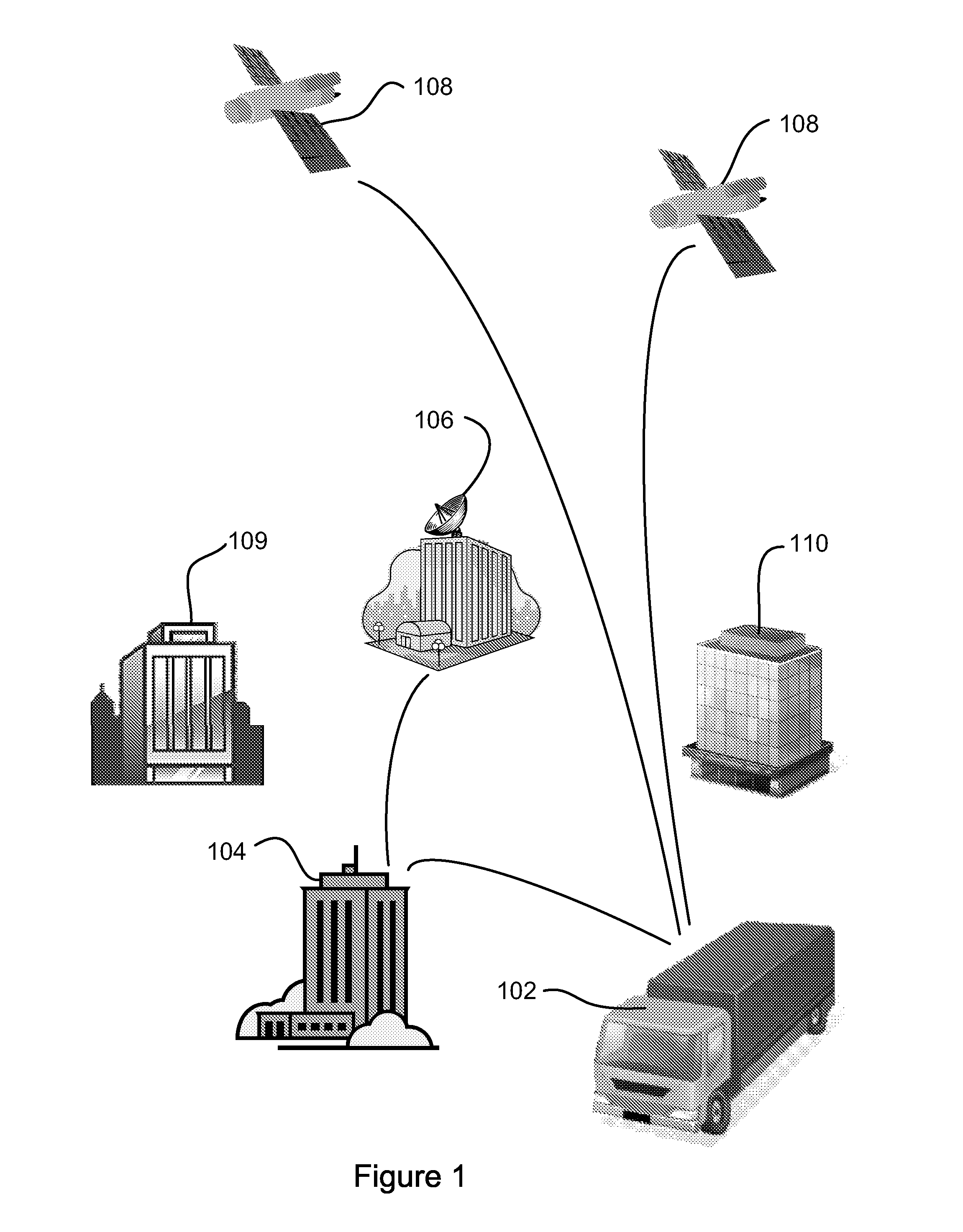
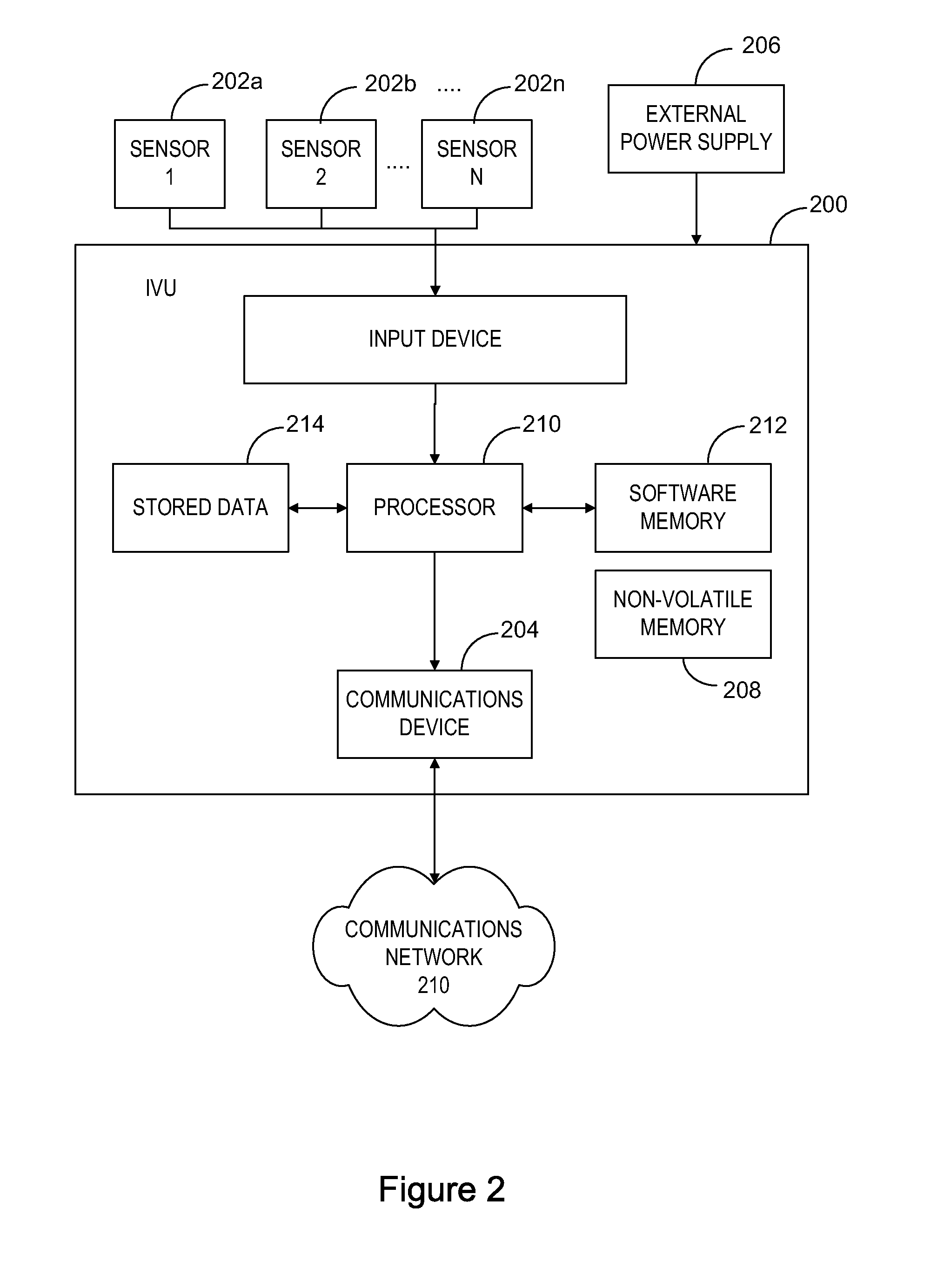
System for Monitoring Vehicle Use
ActiveUS20110035139A1Analogue computers for vehiclesAnalogue computers for trafficTime markNon compliance
A system for monitoring of vehicles and particularly heavy vehicles and their compliance with specific network (e.g. road) access conditions uses vehicle telematics solutions. The system includes an in-vehicle unit (IVU) associated with a vehicle being monitored. The IVU includes a receiver for receiving positioning signals, a processor for processing a time-marked log of vehicle data, a storage element for storing the time-marked log and a first wireless communication element for communicating time marked data to a Service Provider (SP) processing apparatus. One or more Service Providers operate Service Provider (SP) processing apparatus. The SP processing apparatus include a SP wireless communication element for receiving time-marked data from one or more IVUs and a SP processor for processing received data. The SP processor is adapted to compare received data from the time-marked log of a vehicle with one or more vehicle-use conditions applicable to that vehicle, and to generate a non-compliance report where the comparison indicates that non-compliant activity has occurred. A SP storage element stores non-compliance reports and relevant time-marked data.
Owner:TRANSPORT CERTIFICATION AUSTRALIA
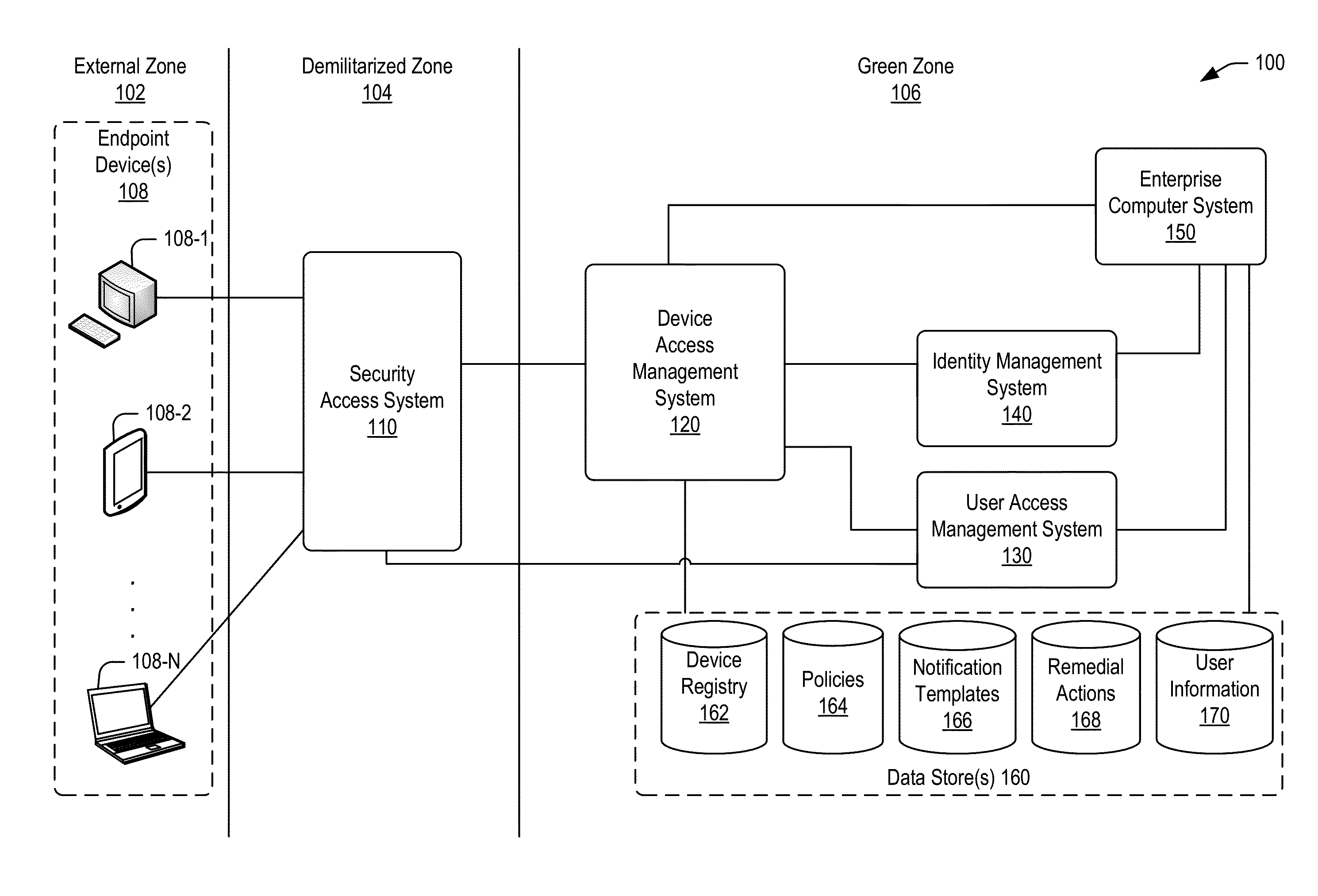
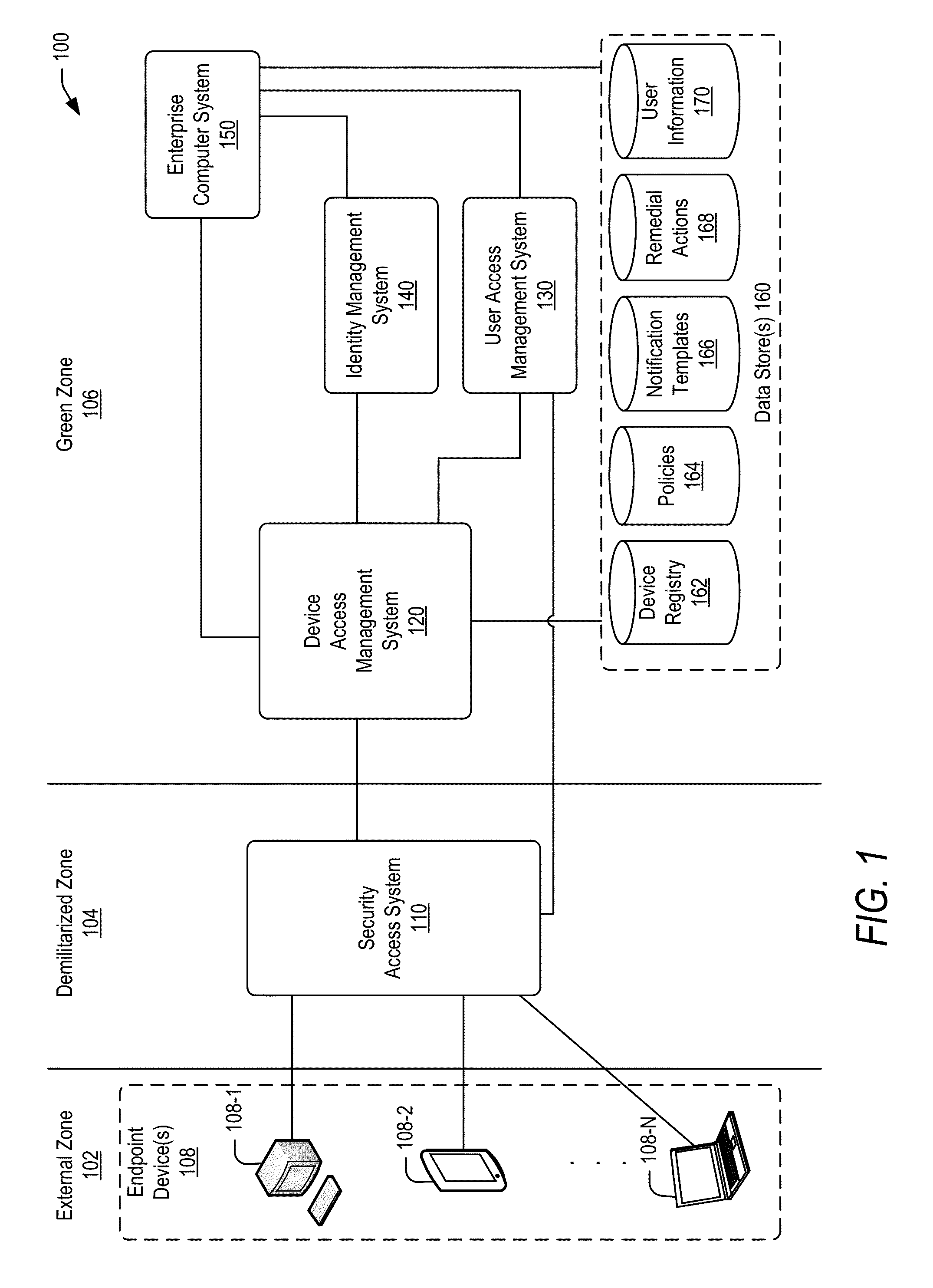
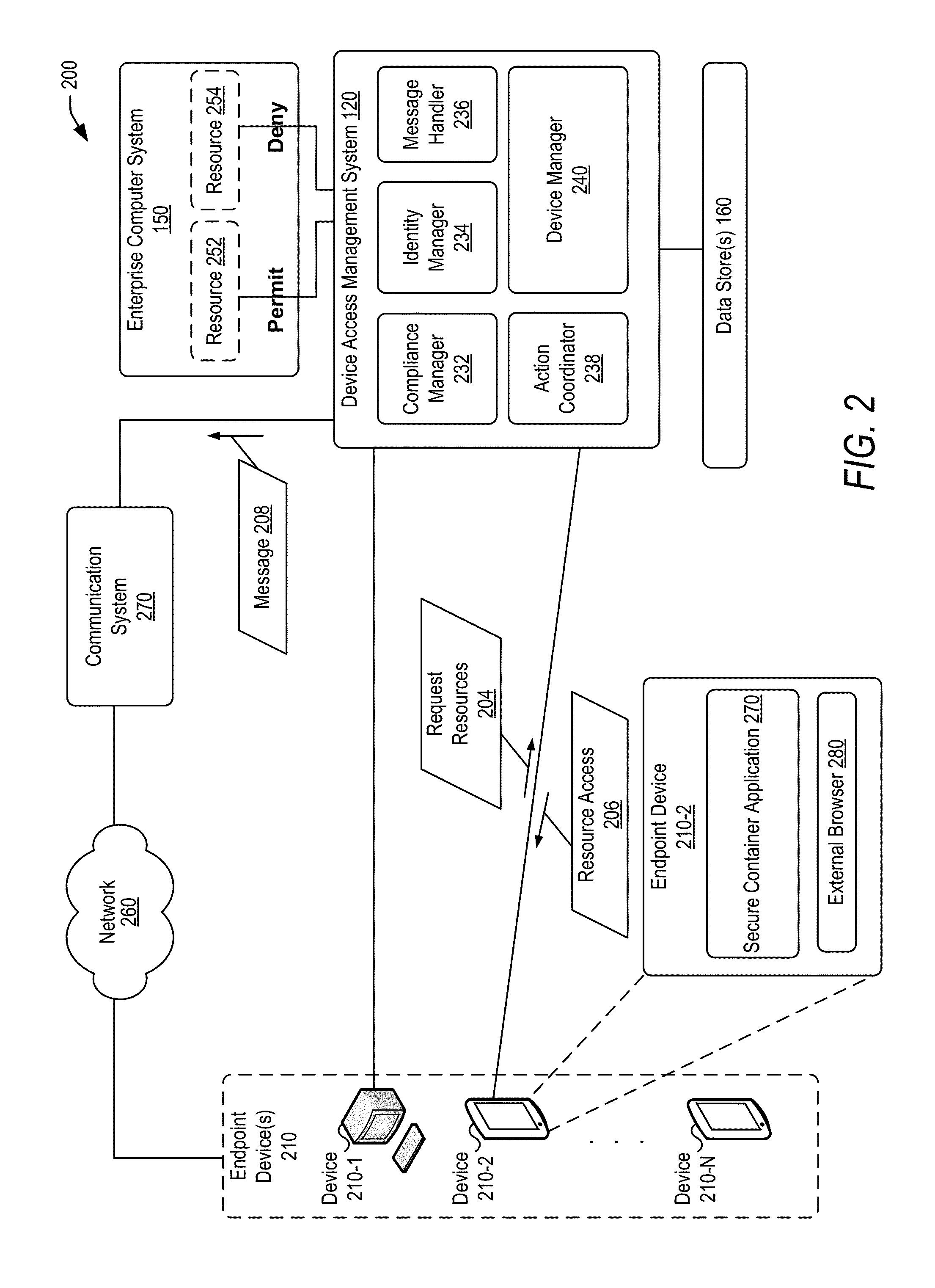
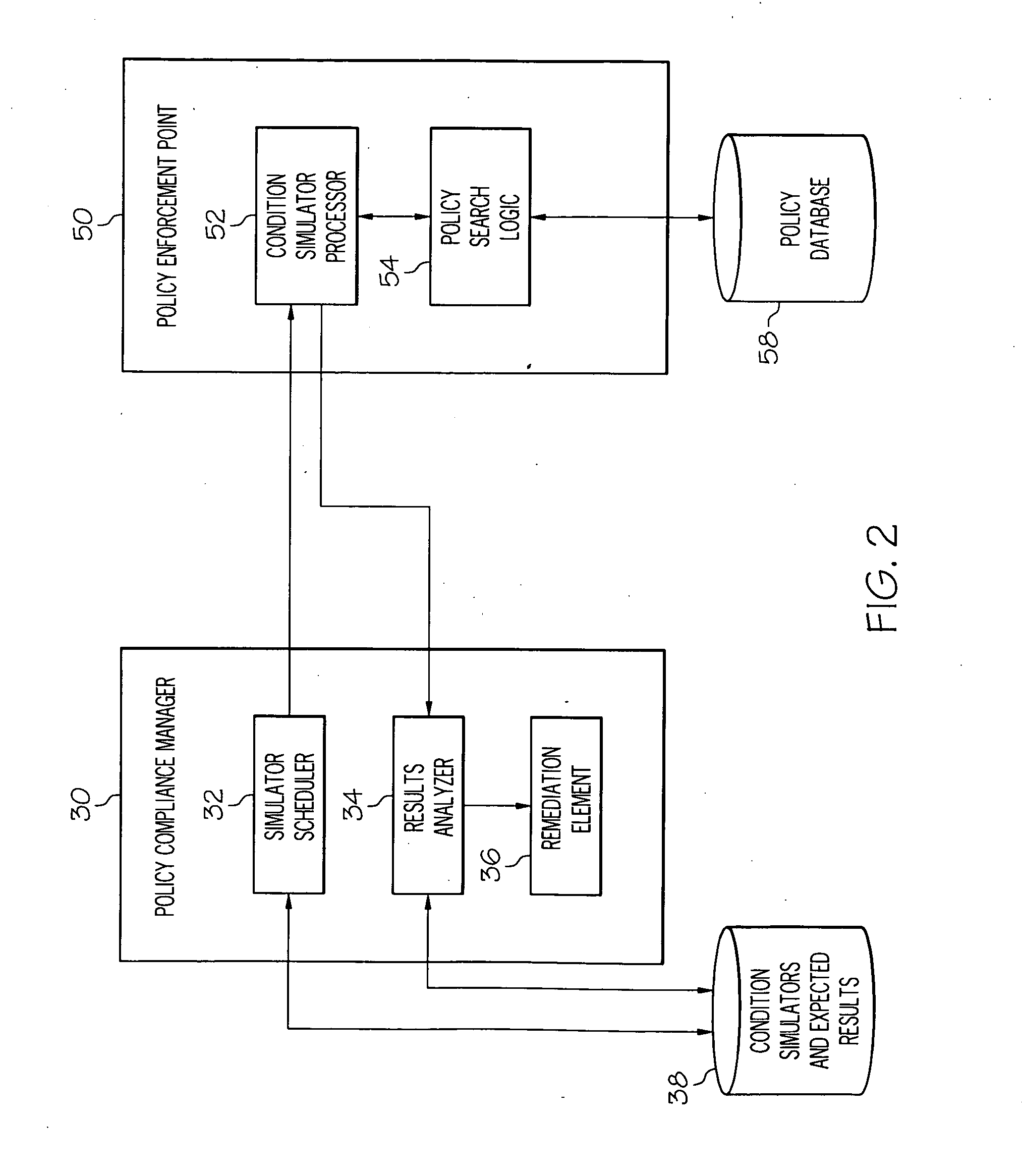
Policy-based compliance management and remediation of devices in an enterprise system
ActiveUS20160088021A1Reduce the burden onAvoid accessService provisioningVersion controlNon complianceEnterprise system
The present disclosure relates generally to managing compliance of remote devices that access an enterprise system. More particularly, techniques are disclosed for using a compliance policy to manage remediation of non-compliances of remote devices that access an enterprise system. A device access management system may be implemented to automate remediation of non-compliances of remote devices accessing an enterprise system. Remediation may be controlled based on different levels of non-compliance, each defined by one or more different non-compliances. In some embodiments, a level of non-compliance may be conditionally defined by one or more user roles for which non-compliance is assessed. Access to computing resources of an enterprise system may be controlled for a remote device based on compliance of the remote device. Access may be inhibited for those resources not permitted during a time period of a non-compliance.
Owner:ORACLE INT CORP
Apparatus and method for prediction and management of participant compliance in clinical research
InactiveUS20060184493A1Improve statistics performanceReduce testing costsDigital computer detailsForecastingCardiovascular drugNon compliance
A system for developing and implementing empirically derived algorithms to generate decision rules to determine participant noncompliance and fraud with research protocols in clinical trials allows for the identification of complex patterns of variables that detect or predict participant noncompliance and fraud with research protocol, including performance and enrollment goals, in the clinical trial. The data may be used to overall predict the performance of any participant in a clinical trial, allowing selection of participants that tend to produce useful, high-quality results. The present invention can also be used to monitor participant compliance with the research protocol and goals to determine preferred actions to be performed. Optionally, the invention may provide a spectrum of noncompliance, from minor noncompliance needing only corrective feedback, to significant noncompliance requiring participant removal from the clinical trial or from future clinical trials. The algorithms and decision rules can also be domain-specific, such as detecting non-compliance or fraud among subjects in a cardiovascular drug trial, or demographically specific, such as taking into account gender, age or location, which provides for algorithms and decision rules to be optimized for the specific sample of participants being studied.
Owner:ERESTECH
Compliance monitoring for anomaly detection
InactiveUS6983266B1Improve accuracyImprove efficiencyFuzzy logic based systemsKnowledge representationCompliance MonitoringTruth value
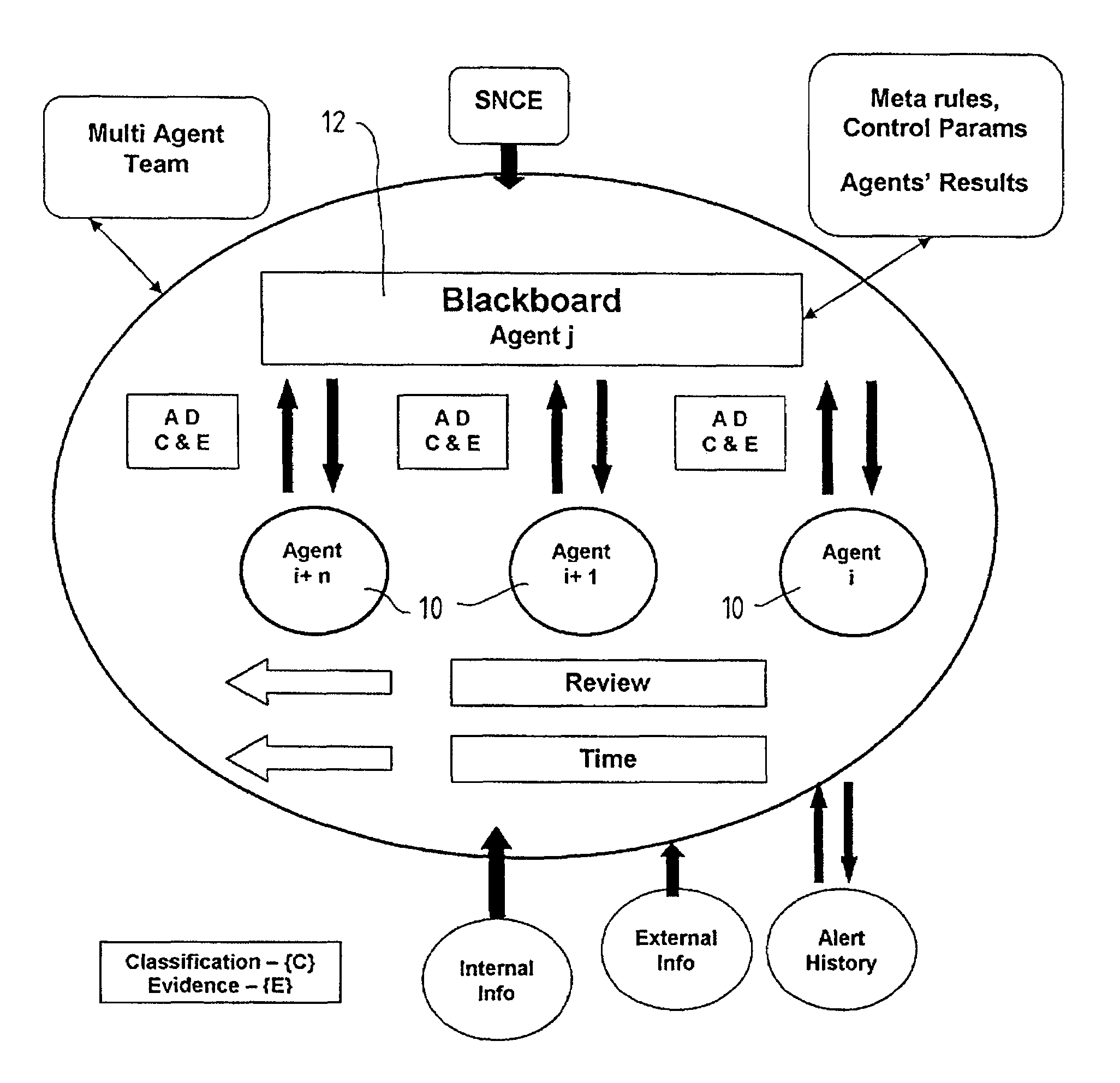
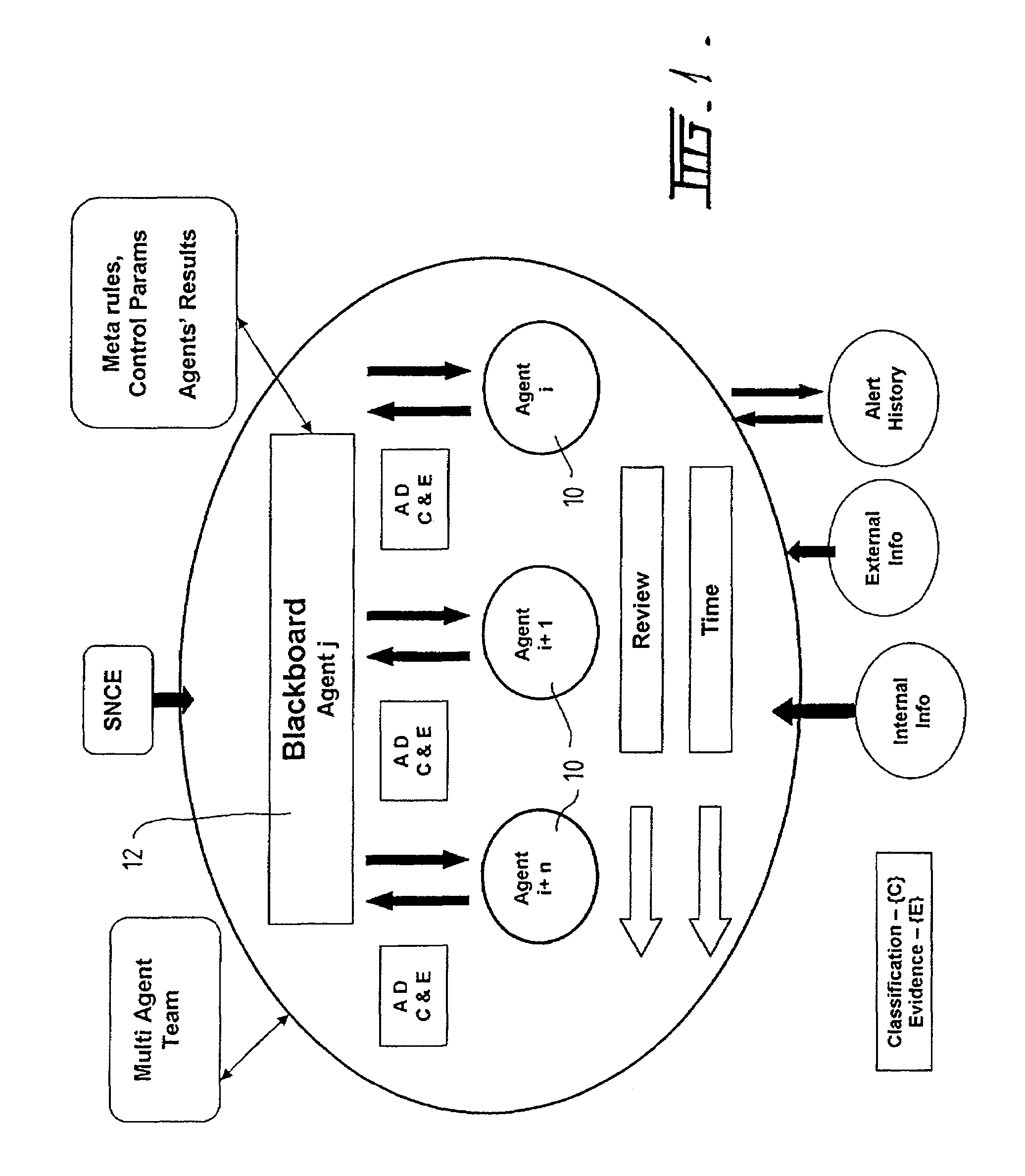
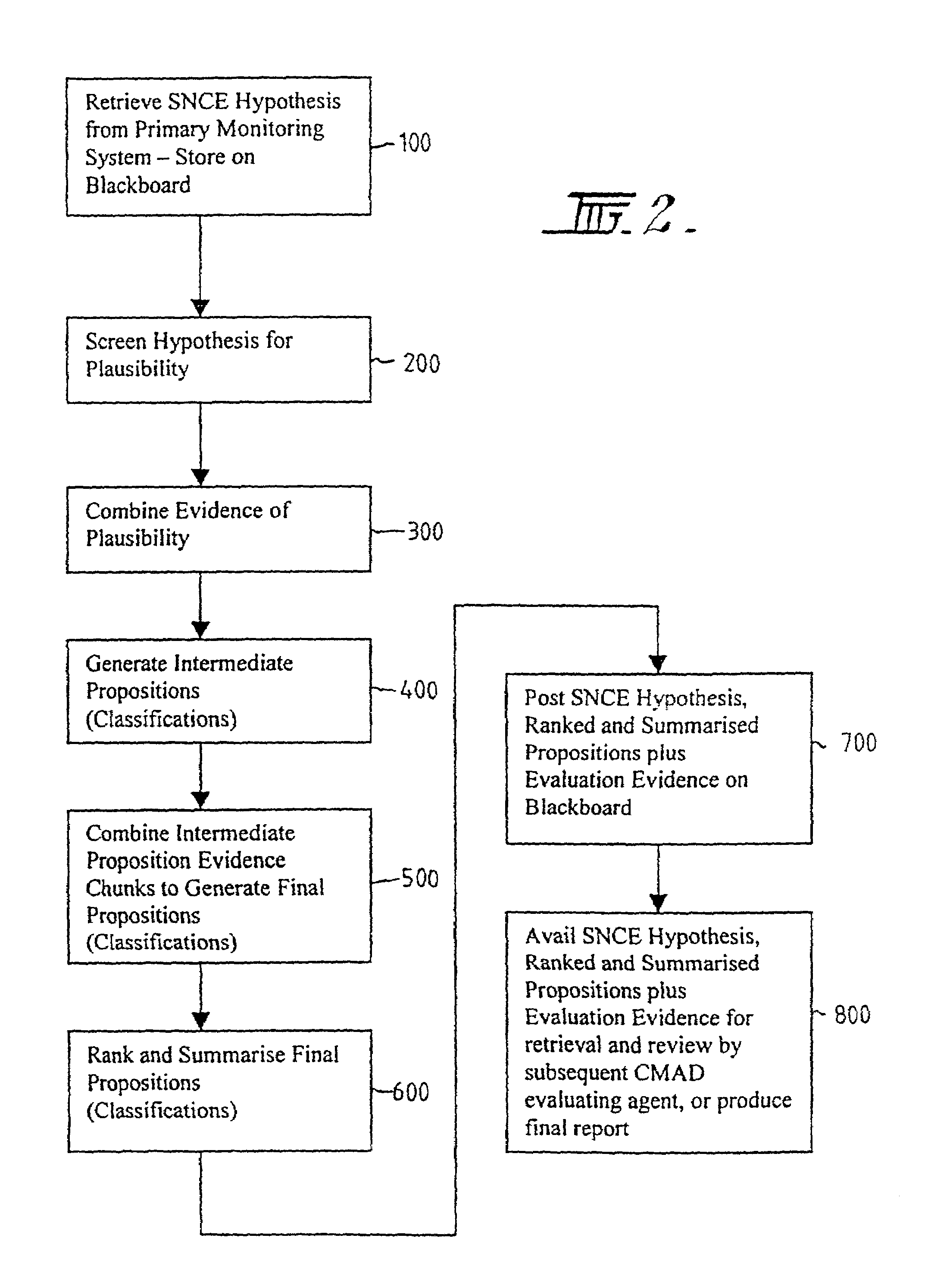
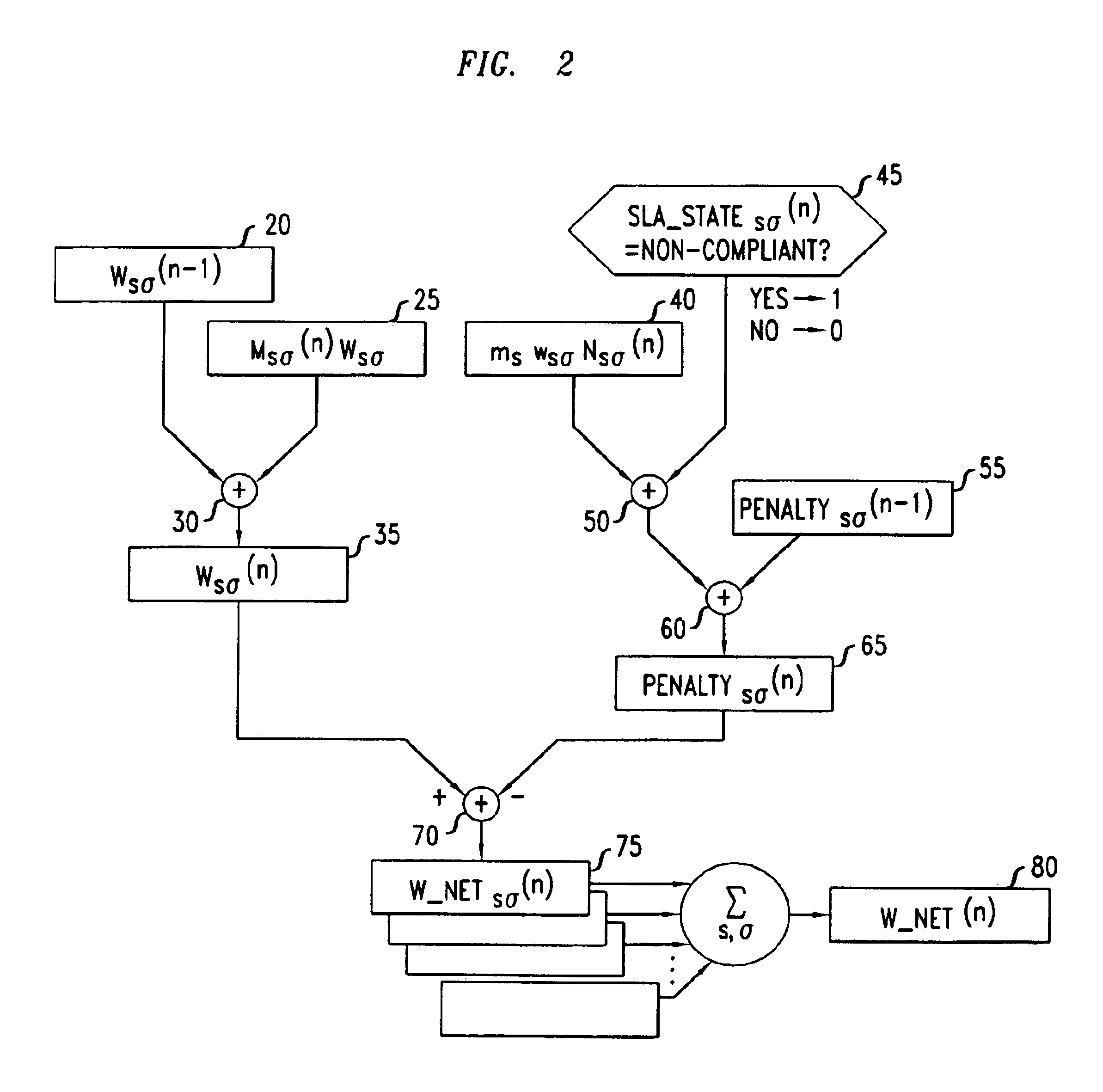
A method and system for supporting a compliance agent in compliance monitoring for anomaly detection (CMAD) involves a primary monitoring system comparing some predetermined conditions of acceptance with the actual data or event. If any variance is detected (an anomaly) by the primary monitoring system, an exception report or alert is produced, identifying the variance. In a simple environment, this identification of the variance fulfils the evidence conditions and determines an instance of non-compliance. However, in a more complex environment, it may only be an indicator of a suspect non-compliant event (SNCE). In the latter case, the compliance agent uses the results of the initial monitoring as well as important information related to the event and requiring judgmental expertise to obtain further evidence of non-compliance. Compliance gents develop propositions or believes, based on their assumption. For each proposition node in the system, the assumption based truth maintenance system maintains a list of minimum sets of assumptions (Boolean cues), which are relevant to the SNCE type. At the macro level, the construct uses the trivalent belief-disbelief-unknown. However, this is refined by applying a measure of importance to individual pieces or empirical evidence.
Owner:ALERT KM
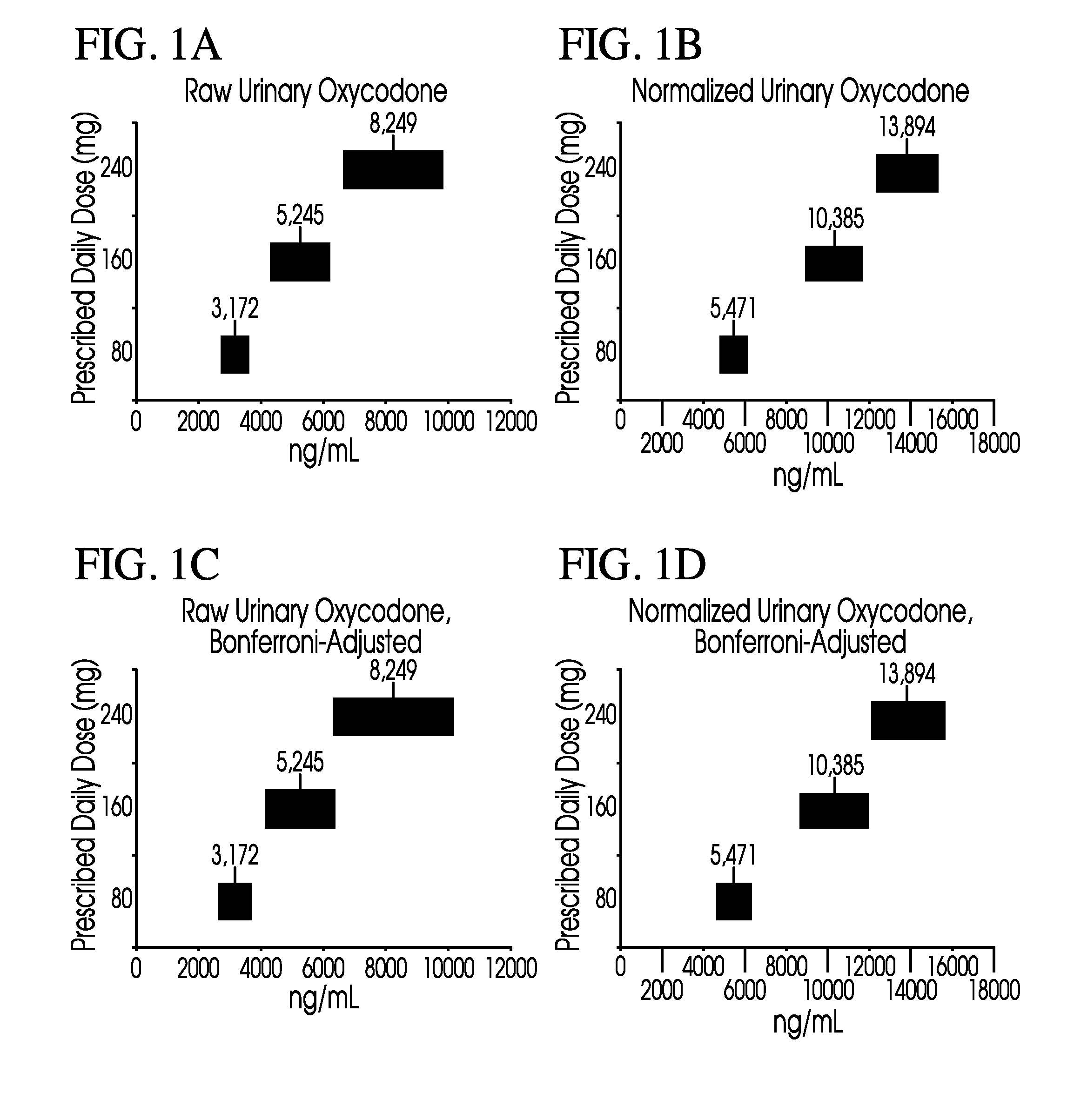
Methods of normalizing measured drug concentrations and testing for non-compliance with a drug treatment regimen
Methods for monitoring subject compliance with a prescribed treatment regimen are disclosed. In one embodiment, the method comprises measuring a drug level in fluid of a subject and normalizing said measured drug level as a function of one or more parameters associated with the subject. The normalized drug level is compared to a reference value and associated confidence intervals or to a concentration range. The reference value and associated confidence intervals and / or the concentration range may be normalized based on one or more parameters associated with subjects in a reference population.
Owner:AMERITOX LLC
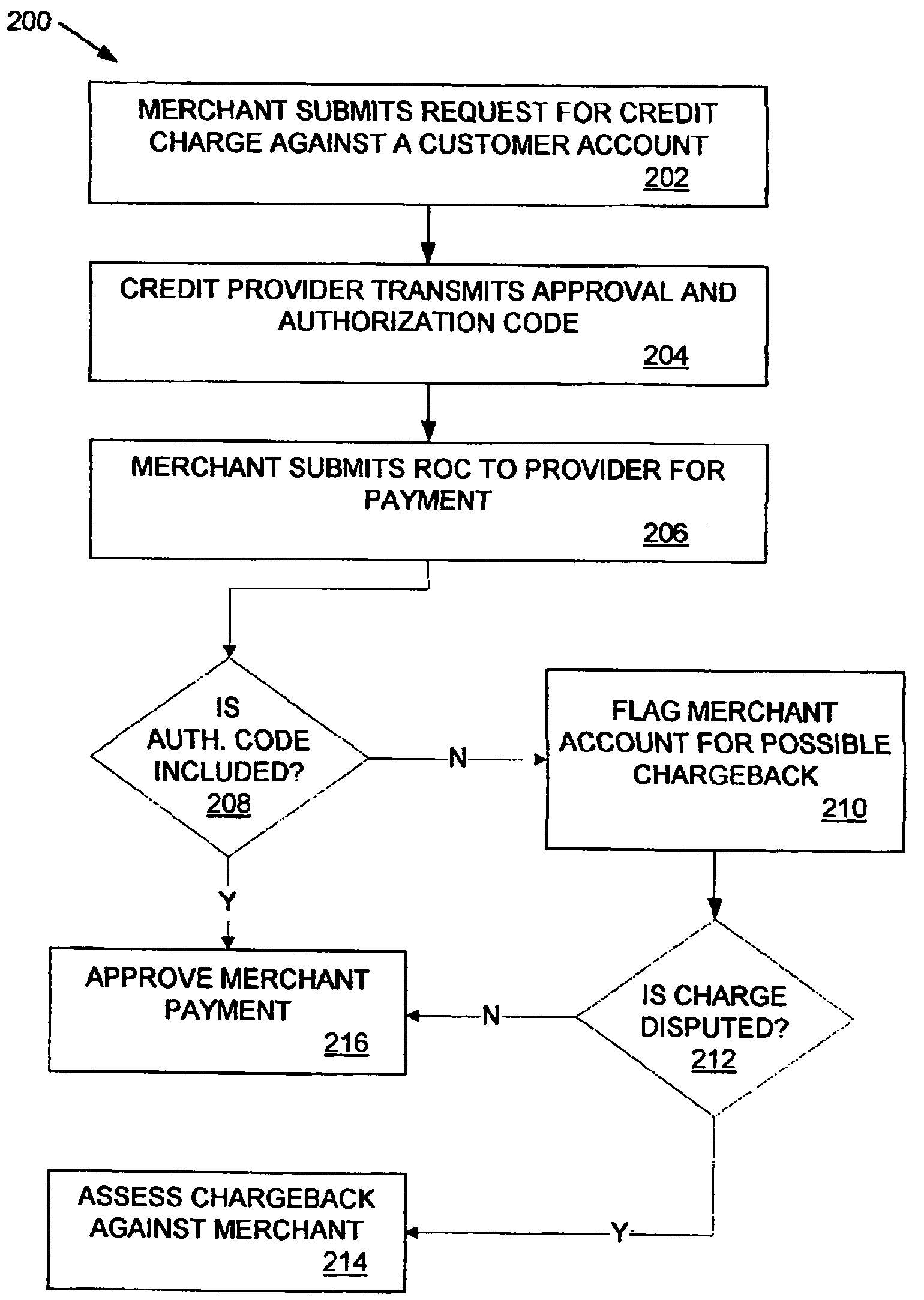
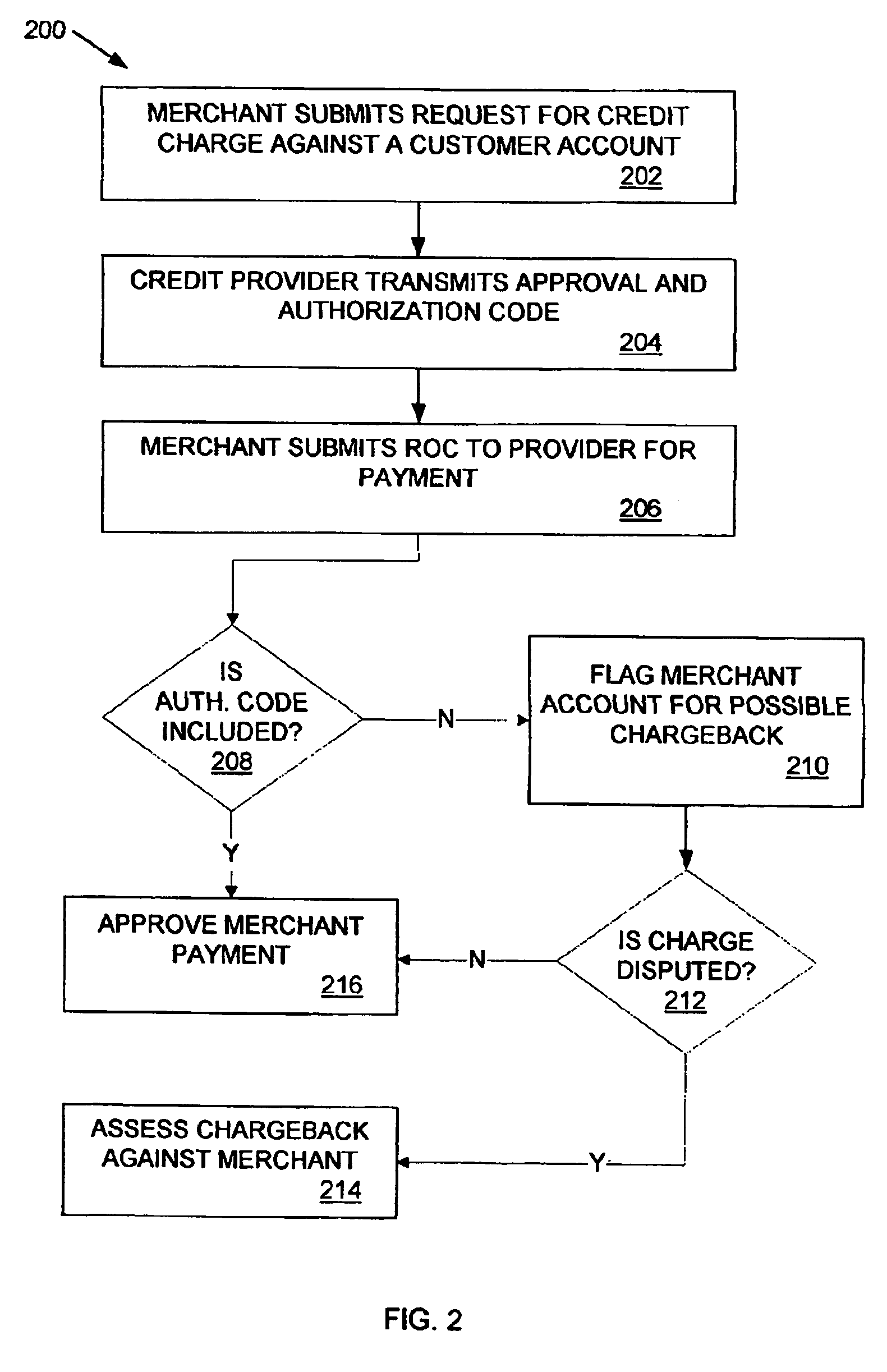
Method and apparatus for reducing fraudulent credit transactions by requiring merchant return of multi-digit authorization codes
Processes for reducing fraudulent credit transactions, including financial (e.g., credit, charge, debit, etc.) card transactions, are introduced, in which merchants receive multi-digit authorization codes from a credit provider (e.g., a customer transaction account card user) with all approved transactions. To guarantee payment, all merchants are required to later resubmit the multi-digit authorization code with every record of charge, regardless of dollar amount, as verification that an authorization was obtained. Merchants that fail to provide any authorization code, or an incorrect authorization code, will be subject to a chargeback for non-compliance.
Owner:LIBERTY PEAK VENTURES LLC
Enhanced client compliancy using database of security sensor data
InactiveUS20060070129A1Eliminate non-compliancyMemory loss protectionDigital data processing detailsNon complianceClient compliance
Security sensor data from intrusion detection system (IDS) sensors, vulnerability assessment (VA) sensors, and / or other security sensors is used to enhance the compliancy determination in a client compliancy system. A database is used to store the security sensor data. In one particular embodiment, a list of device compliance statuses indexed by corresponding identifiers (e.g., IP / MAC addresses) combined from IDS, VA, and / or other security sensing technologies is made available as a non-compliance database for query, so that clients and other compliancy authentication elements can tell that a particular client appears to be out of compliance. A client-side self-policing compliance system is enabled, and can be used in conjunction with automated endpoint compliance policy configuration to reduce system administrator burden.
Owner:CA TECH INC
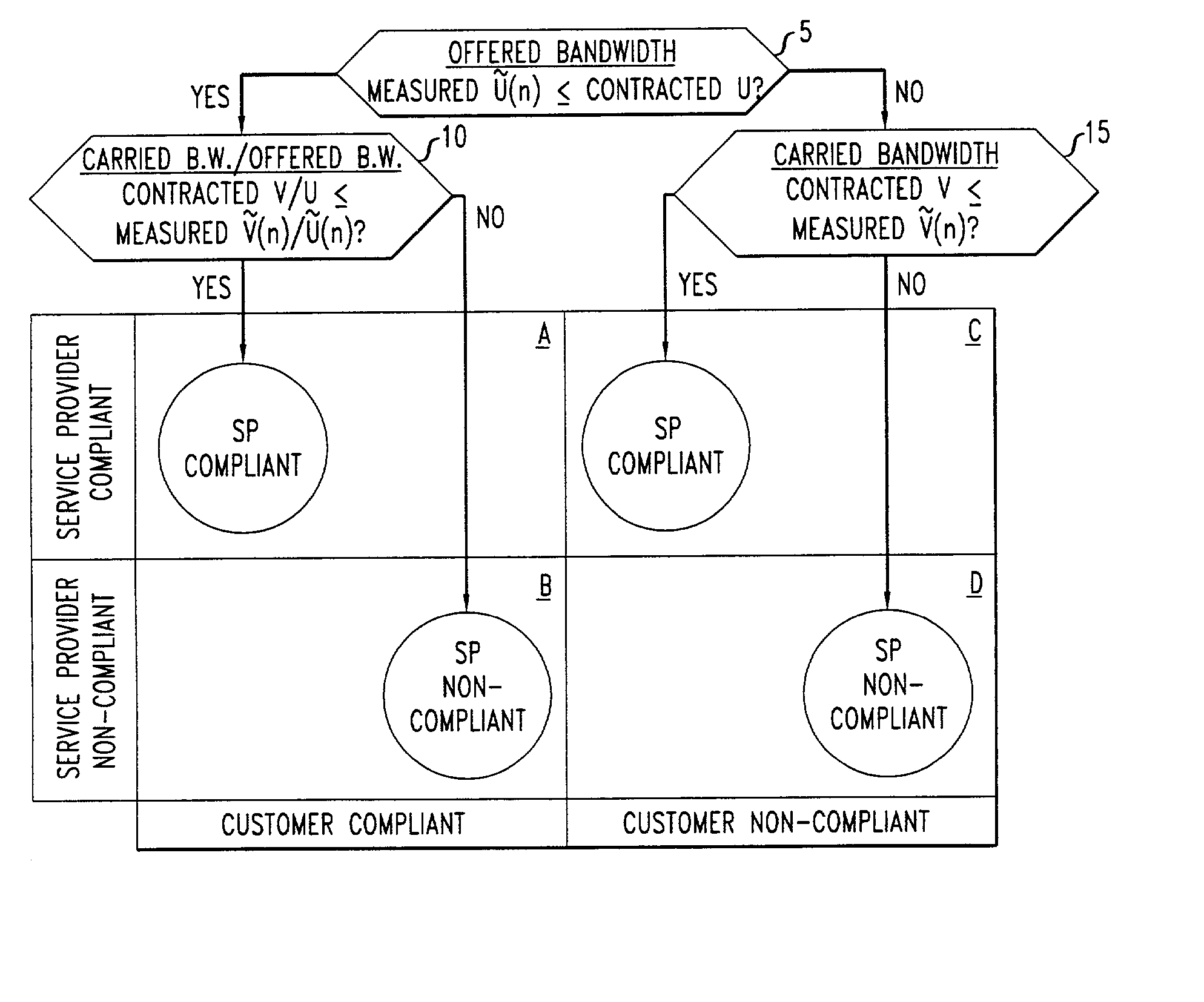
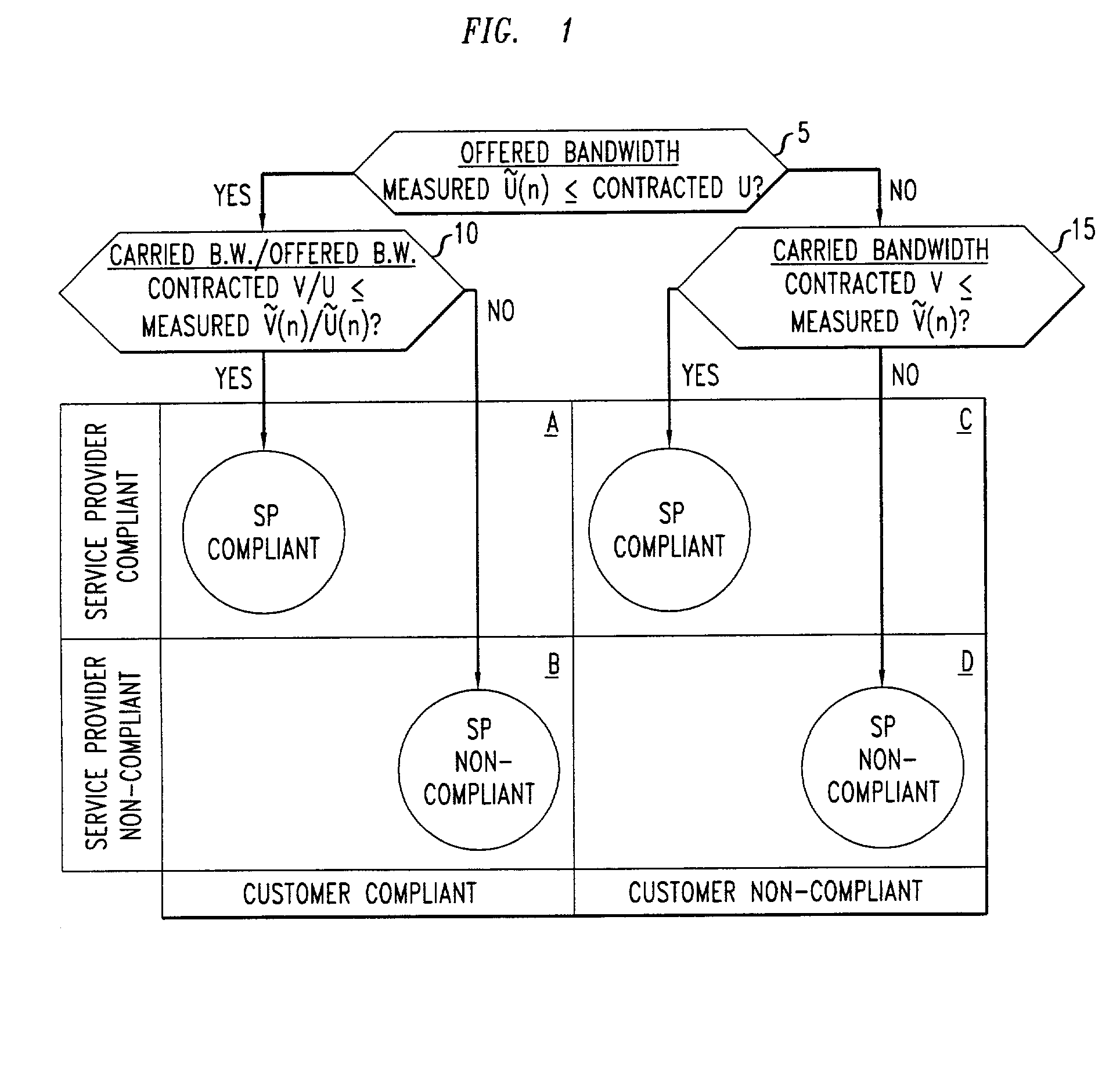
Measurement-based management method for packet communication networks
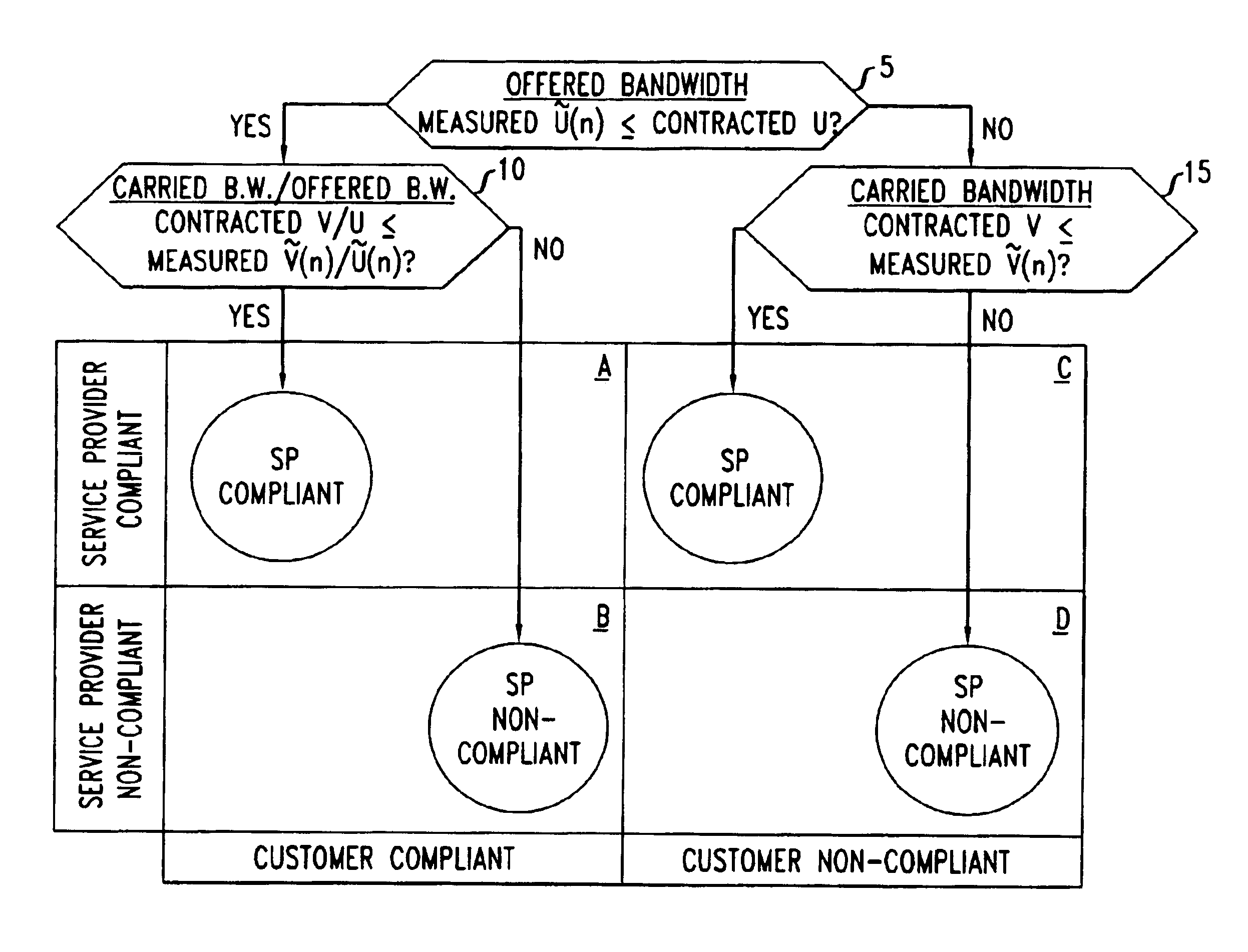
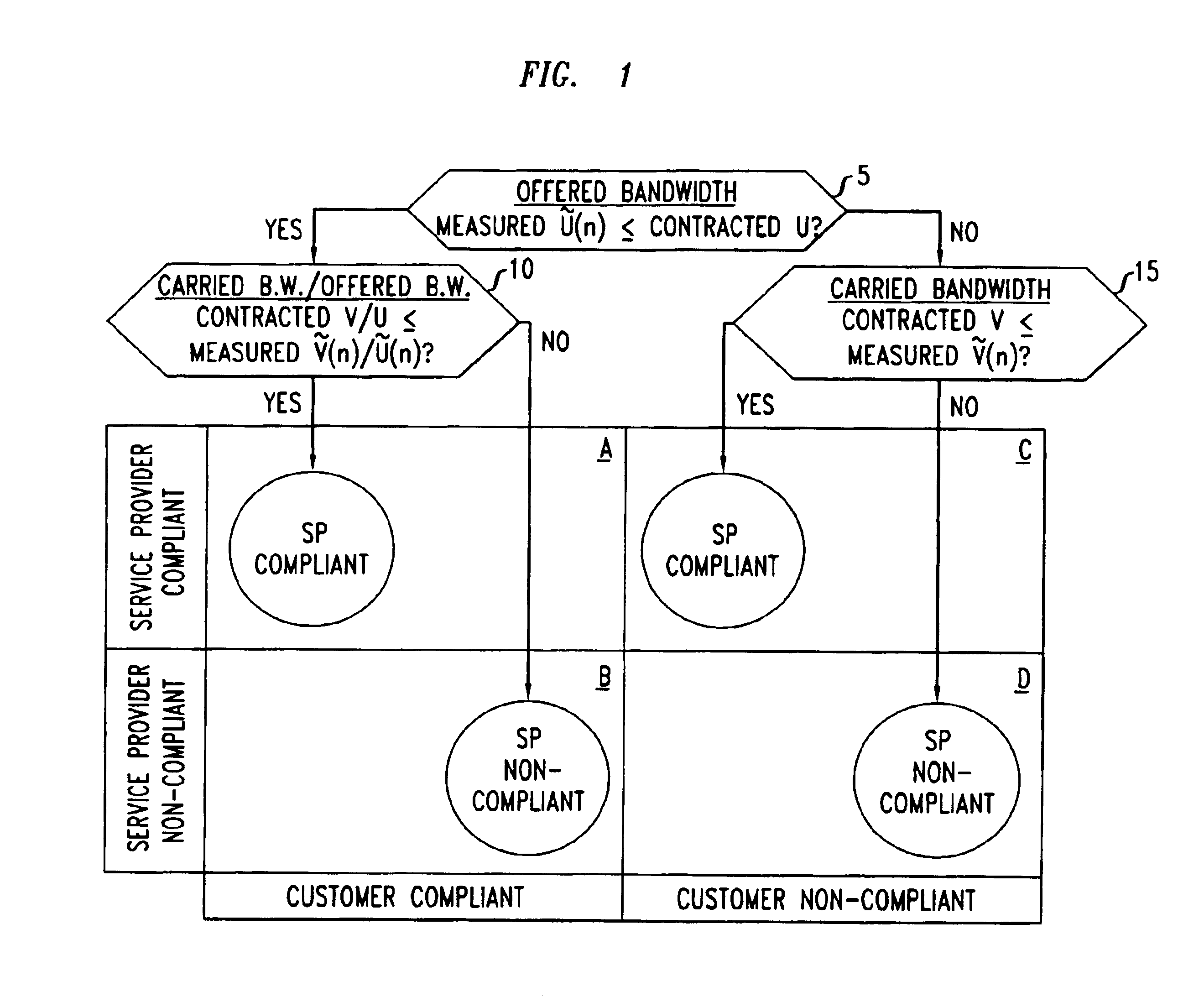
InactiveUS20030101263A1Data processing applicationsMetering/charging/biilling arrangementsPacket communicationNon compliance
Disclosed are network management procedures that apply measurements of traffic load to achieve greater efficiency in the operation of the network. In a method for deciding whether to route an incoming call on a selected potential service route, the potential service route is treated preferentially if each of its links has available capacity that is more than sufficient by a specified margin. In a method for computing billing revenues, the non-compliance of the network service provider with contracted requirements for carried load causes a revenue penalty to be exacted for lost bandwidth.
Owner:WSOU INVESTMENTS LLC
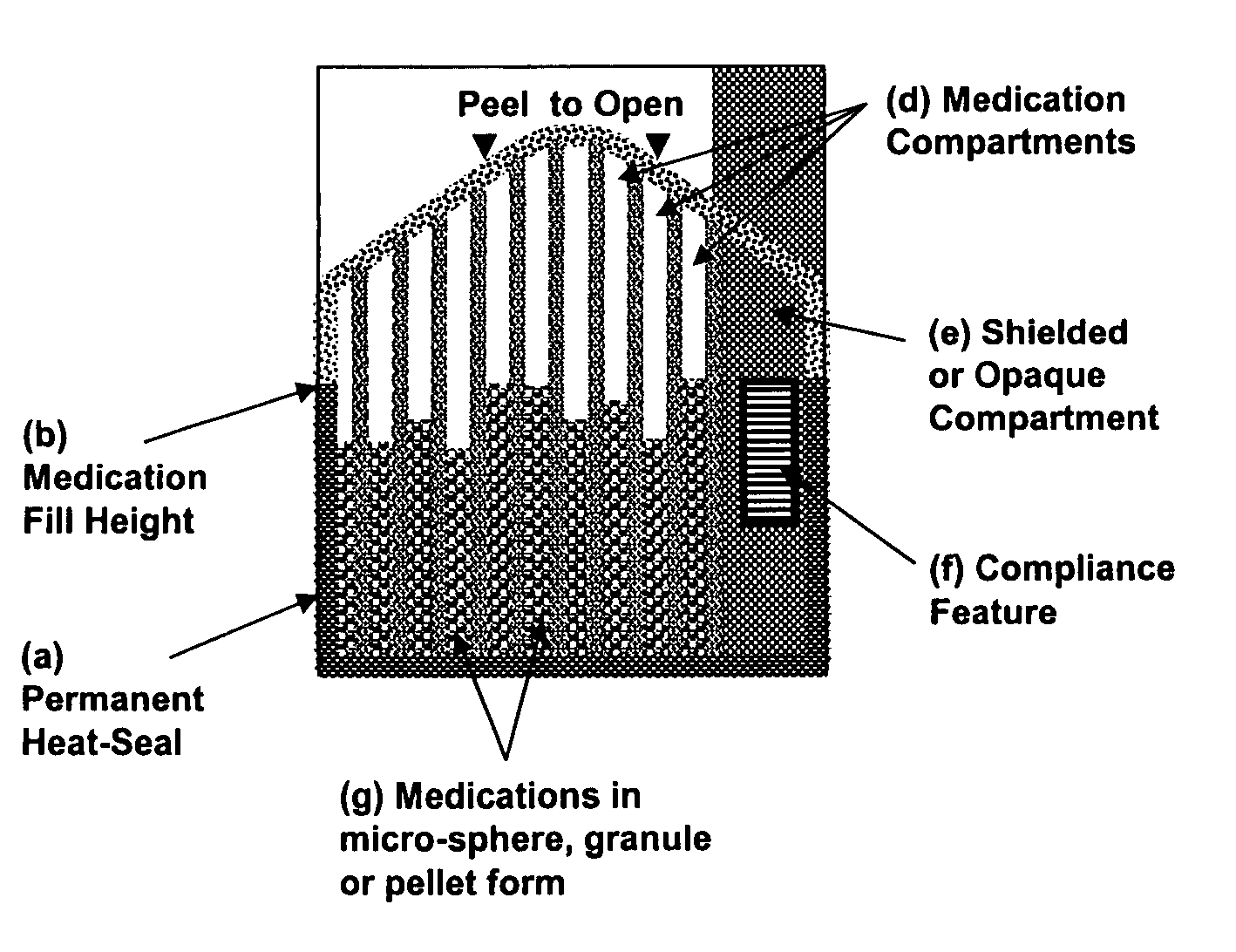
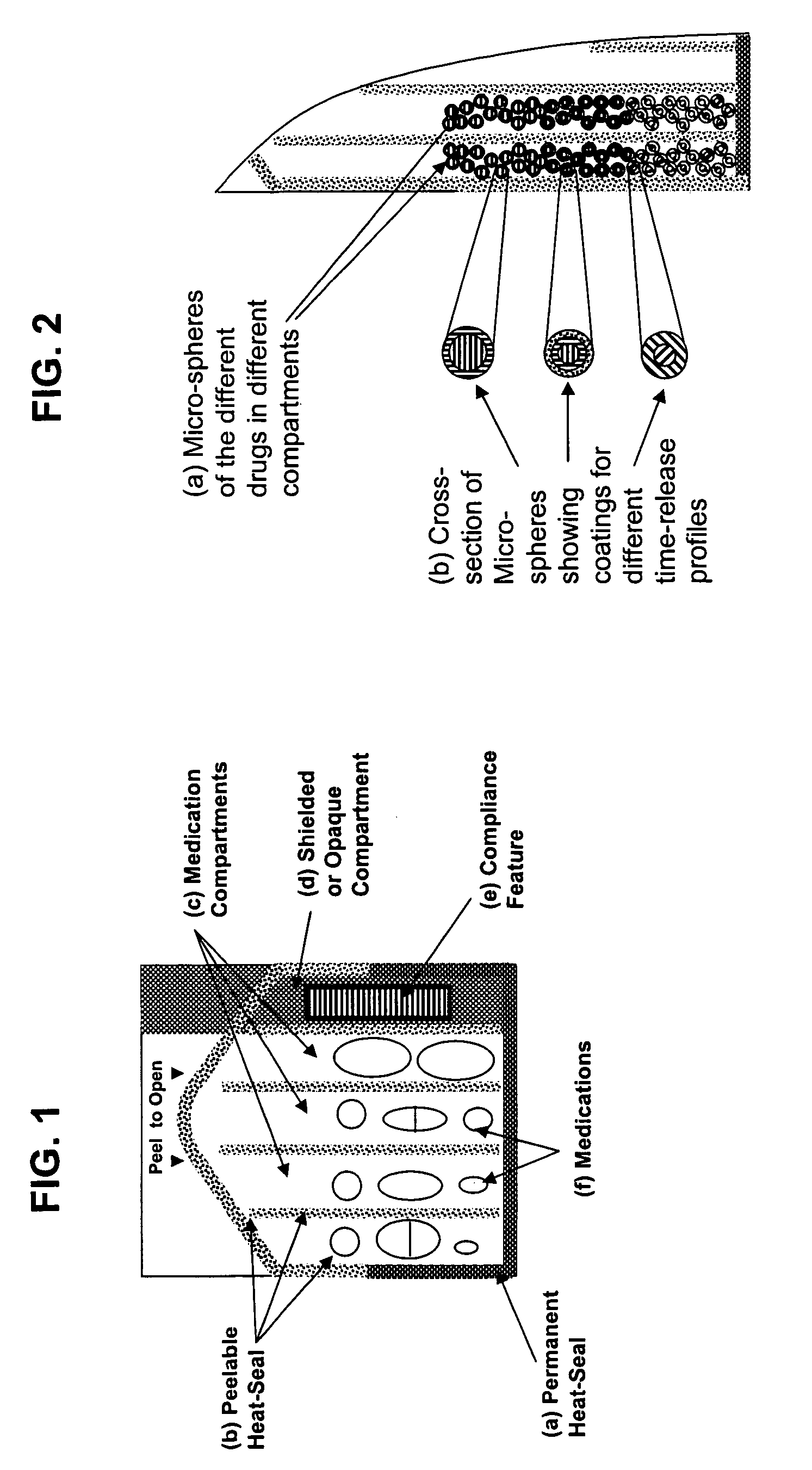
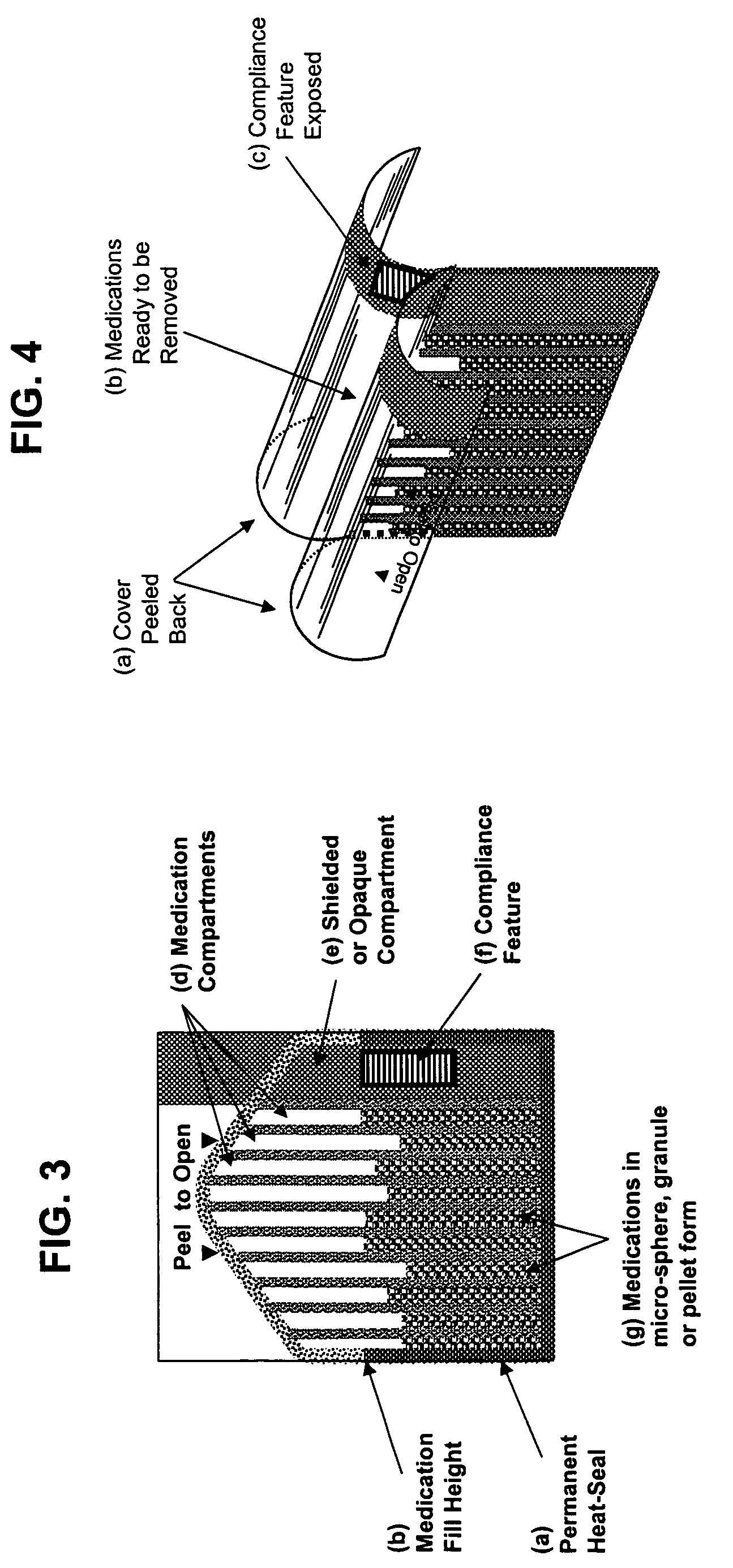
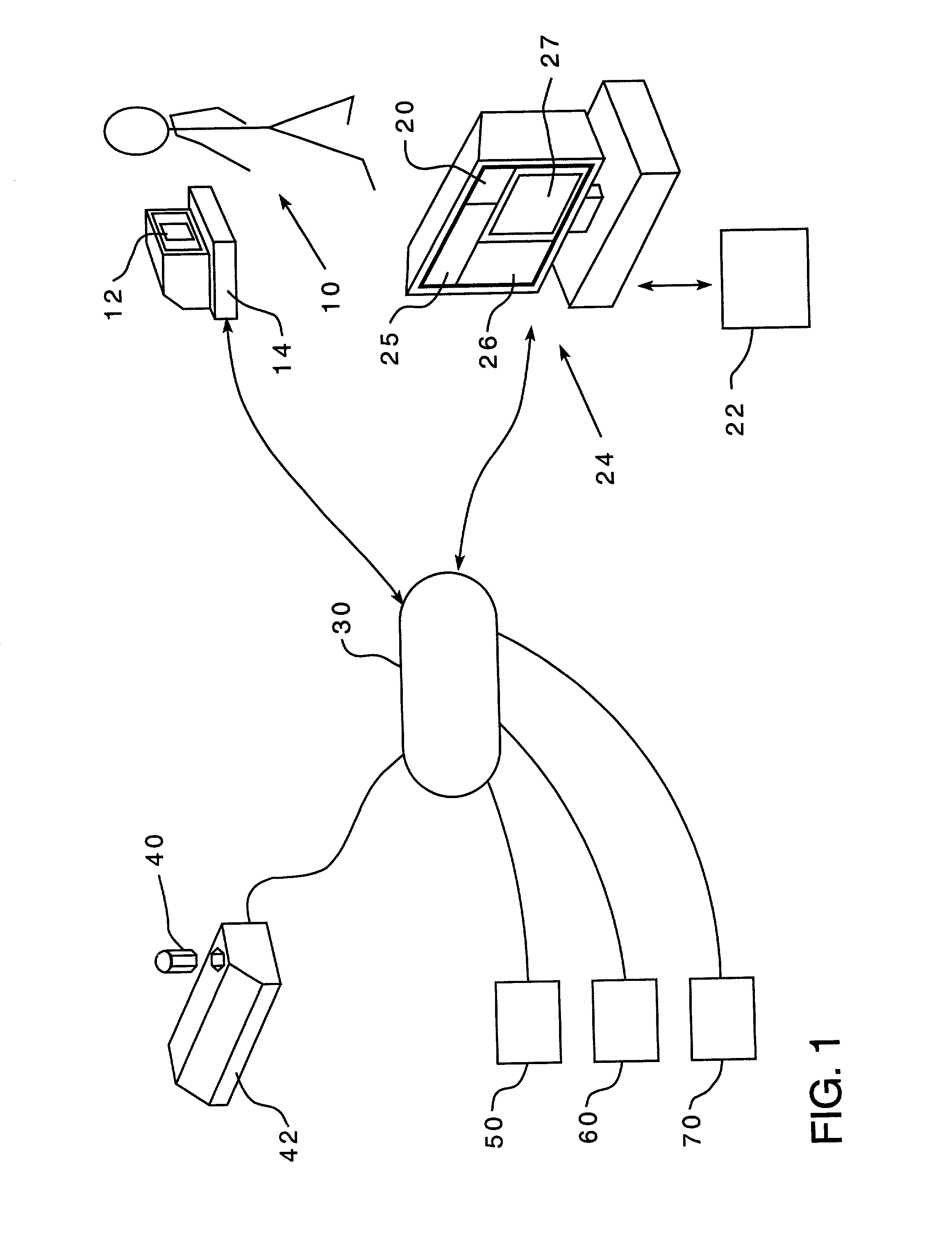
Unified ingestion package and process for patient compliance with prescribed medication regimen
Techniques for reducing non-compliance of medication use are described. The techniques involve generating and storing an identifier for a specific dosage instance of a specific patient, and creating a package that includes a mechanism for conveying the identifier. Once the package is created, a set of one or more medications that are prescribed to be taken by the specific patient at the specific dosage instance are placed in the package. The set of medications within the package in a manner that prevents the identifier from being perceived from the mechanism until the package is opened. Once opened, the identifier is perceived and communicated back to an automated compliance system.
Owner:RAMASUBRAMANIAN NARAYANAN +1
Network Policy Management And Effectiveness System
InactiveUS20070261121A1Digital data processing detailsError detection/correctionNon complianceNetwork security policy
The Present Invention discloses a method and apparatus for maintaining policy compliance on a computer network. A system in accordance with the principles of the Present Invention performs the steps of electronically monitoring network user compliance with a network security policy stored in a database, electronically evaluating network security policy compliance based on network user compliance and electronically undertaking a network policy compliance action in response to network security policy non-compliance. The network policy compliance actions may include automatically implementing a different network security policy selected from network security policies stored in the database, generating policy effectiveness reports and providing a retraining module to network users.
Owner:LONGHORN HD LLC
Network resource configurations
ActiveUS20120290715A1Improve performanceSave capacityDigital computer detailsHybrid transportTime rangeNon compliance
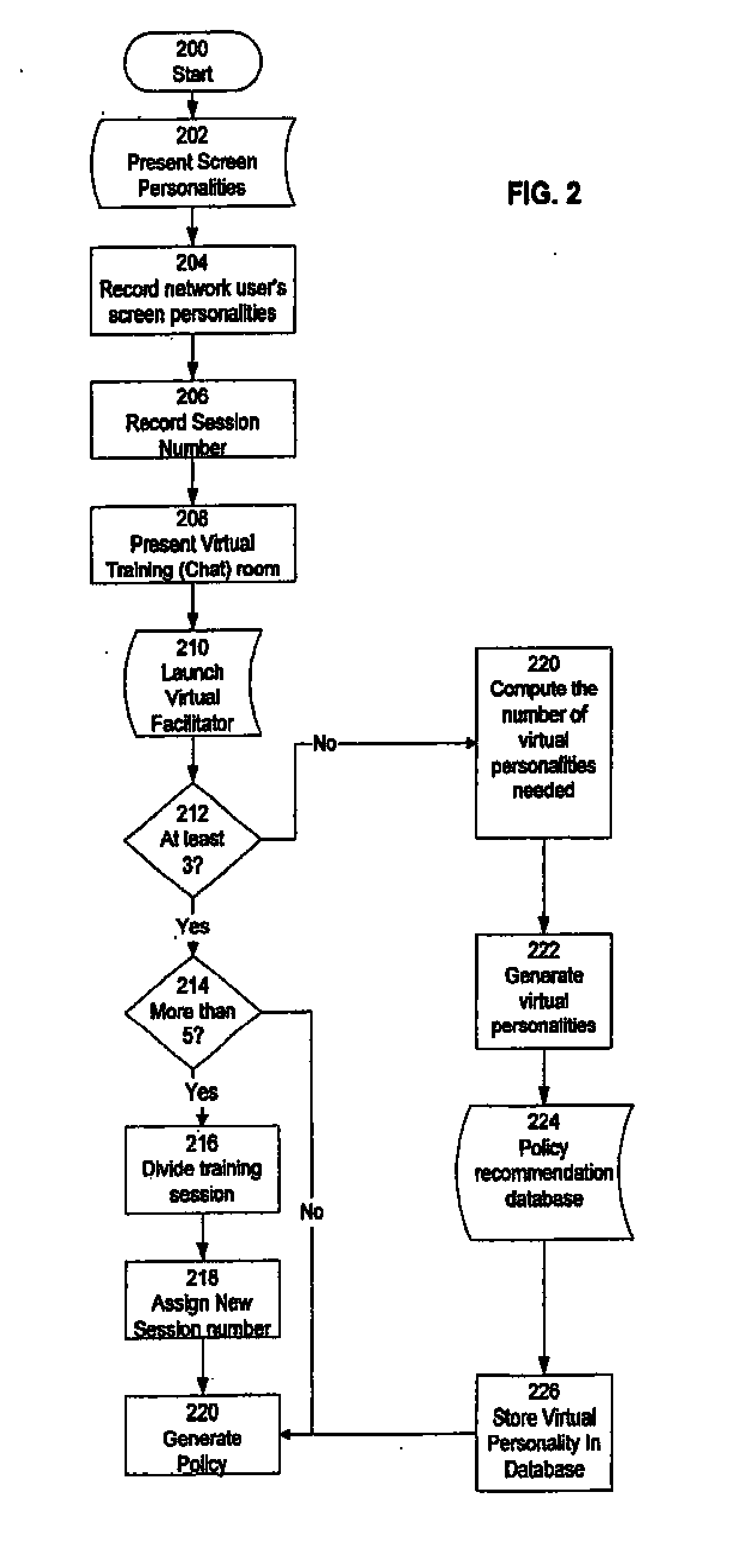
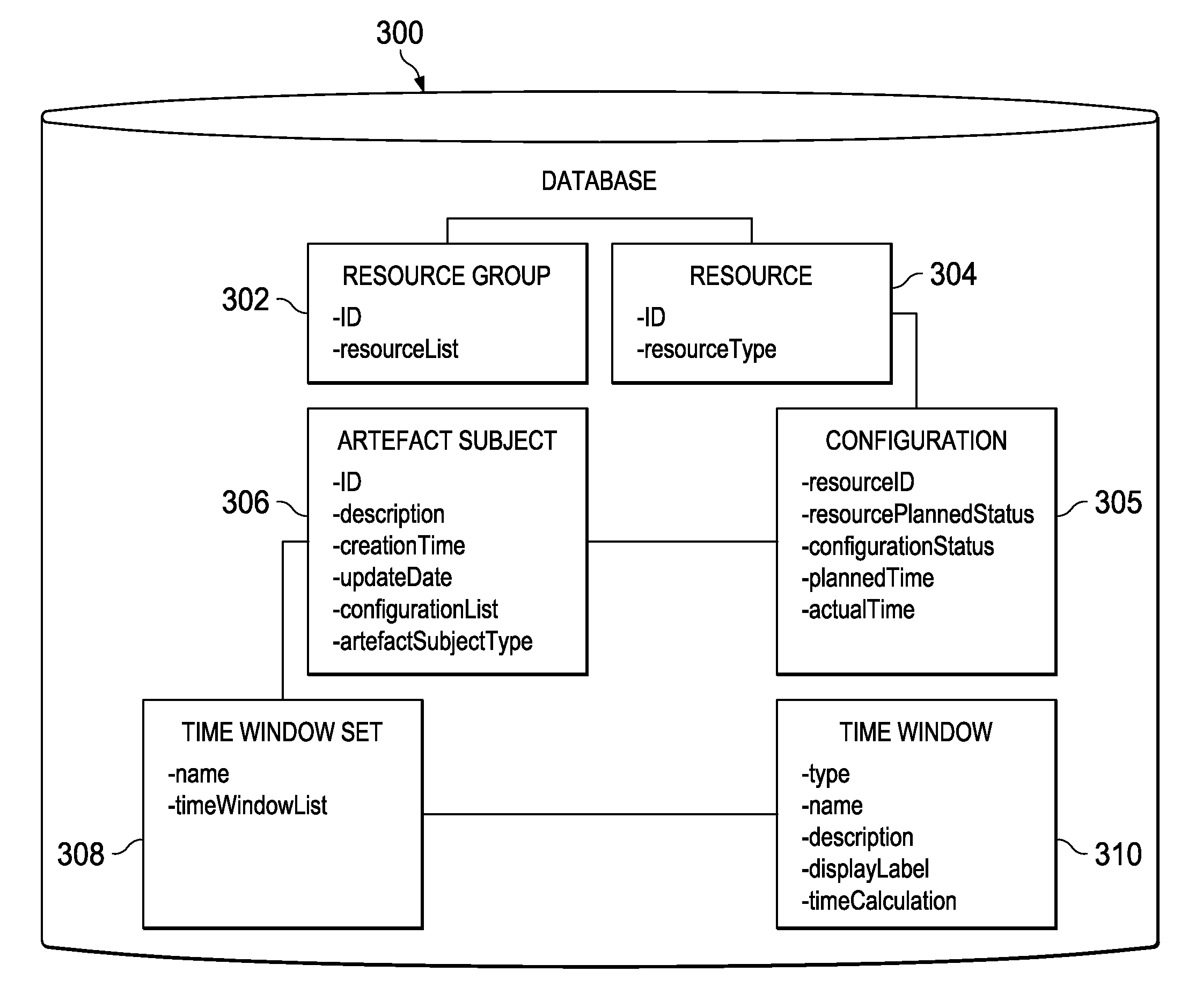
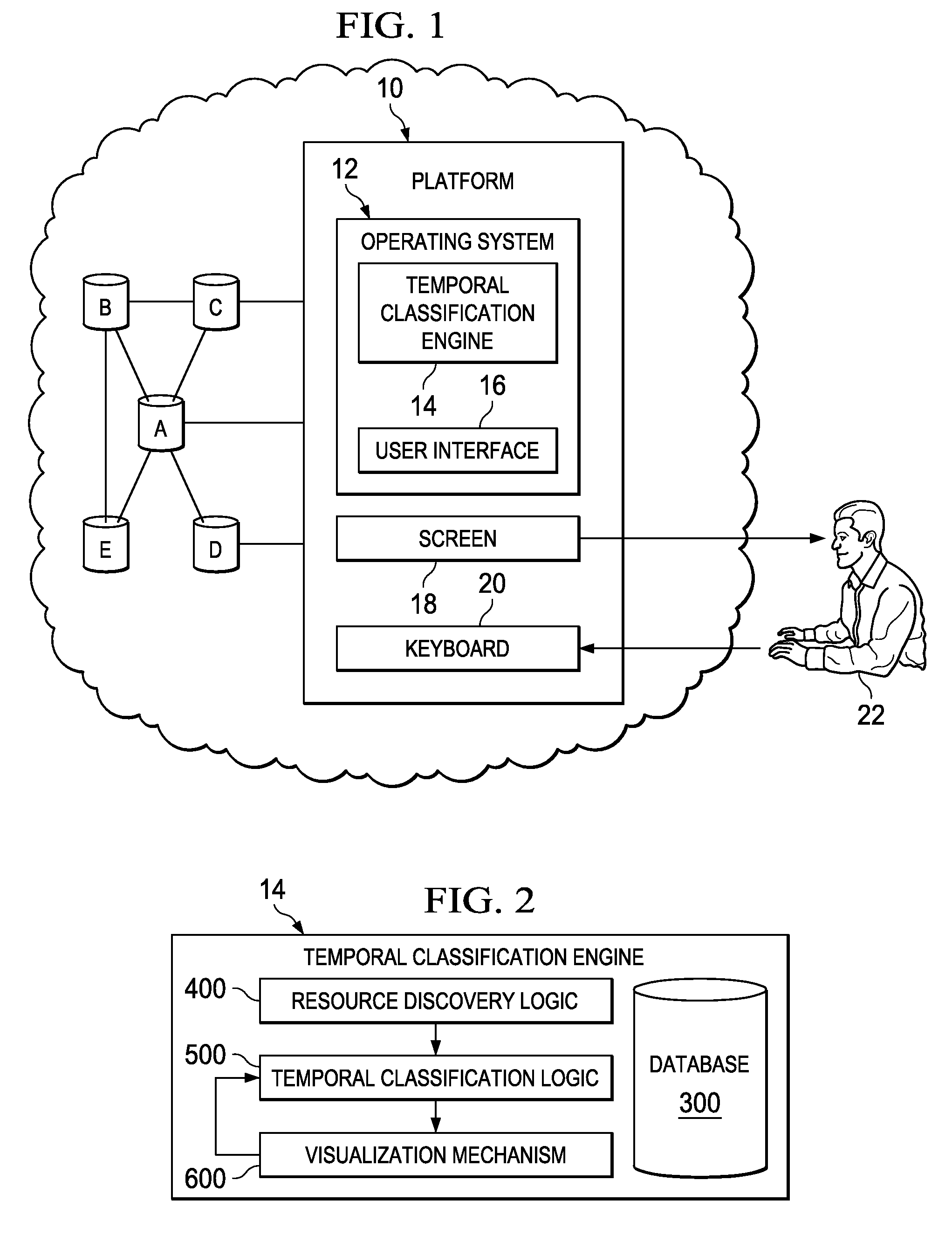
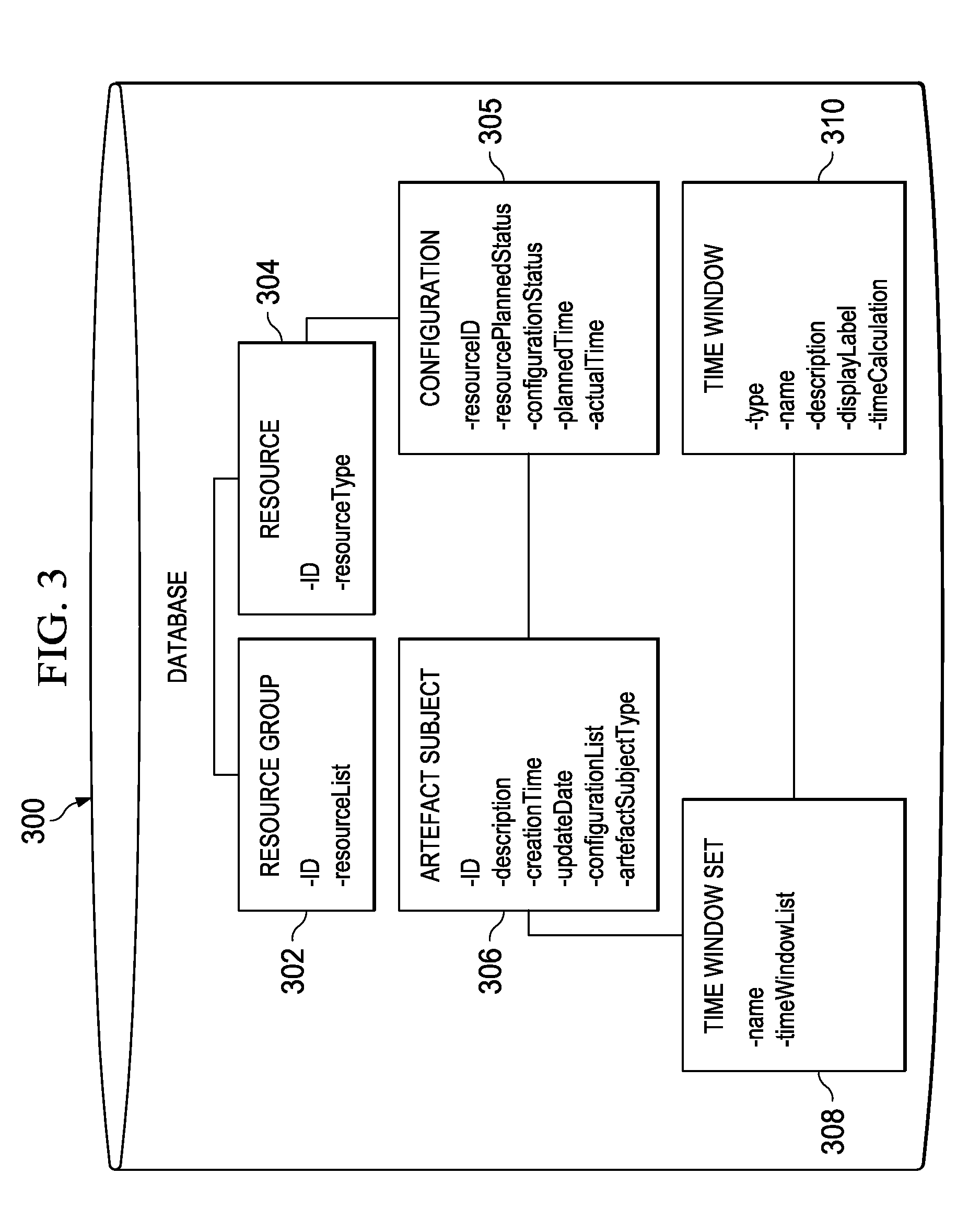
Temporally classifying and visually representing network and IT infrastructure with planned or occurred configuration activities and / or policy compliance or non-compliance of network and IT resources, including a method, apparatus and computer program for gathering and classifying observable configuration aspects of resources and relationships in a network of resources, wherein the method comprises: analyzing the network of resources to collect planned configuration times and actual resource status; monitoring actual resource status to make determinations if planned configurations are executed; and updating a network configuration status with the determinations. Planned and actual configurations are collected and monitored over a defined time range extending before and / or after a time zero. Each planned or actual configuration is categorized with respect to one or more time windows in the defined time range.
Owner:IBM CORP
Measurement-based management method for packet communication networks
InactiveUS6954739B1Metering/charging/biilling arrangementsComputer security arrangementsPacket communicationNon compliance
Owner:WSOU INVESTMENTS LLC +1
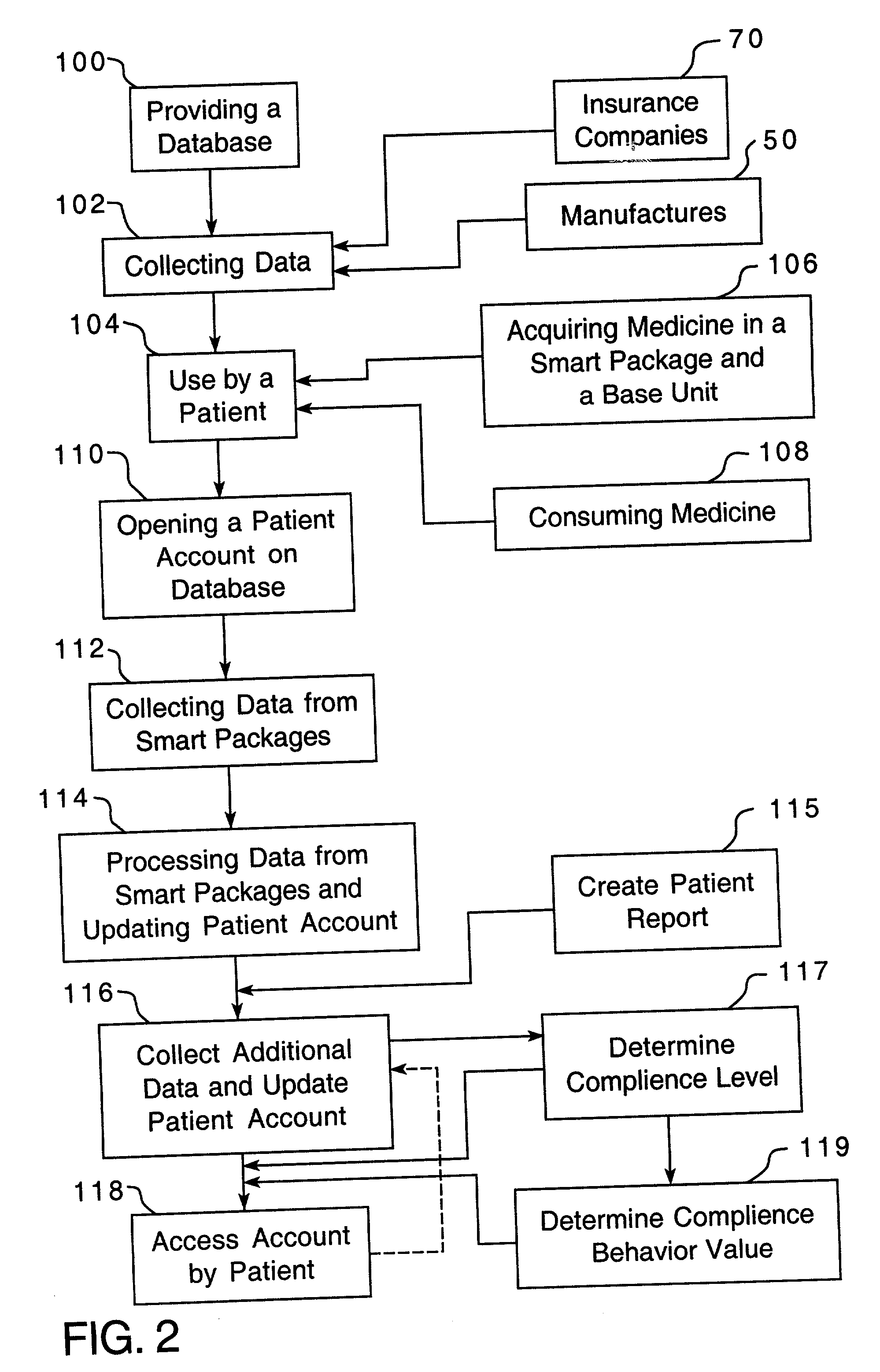
Method of providing comprehensive drug compliance information
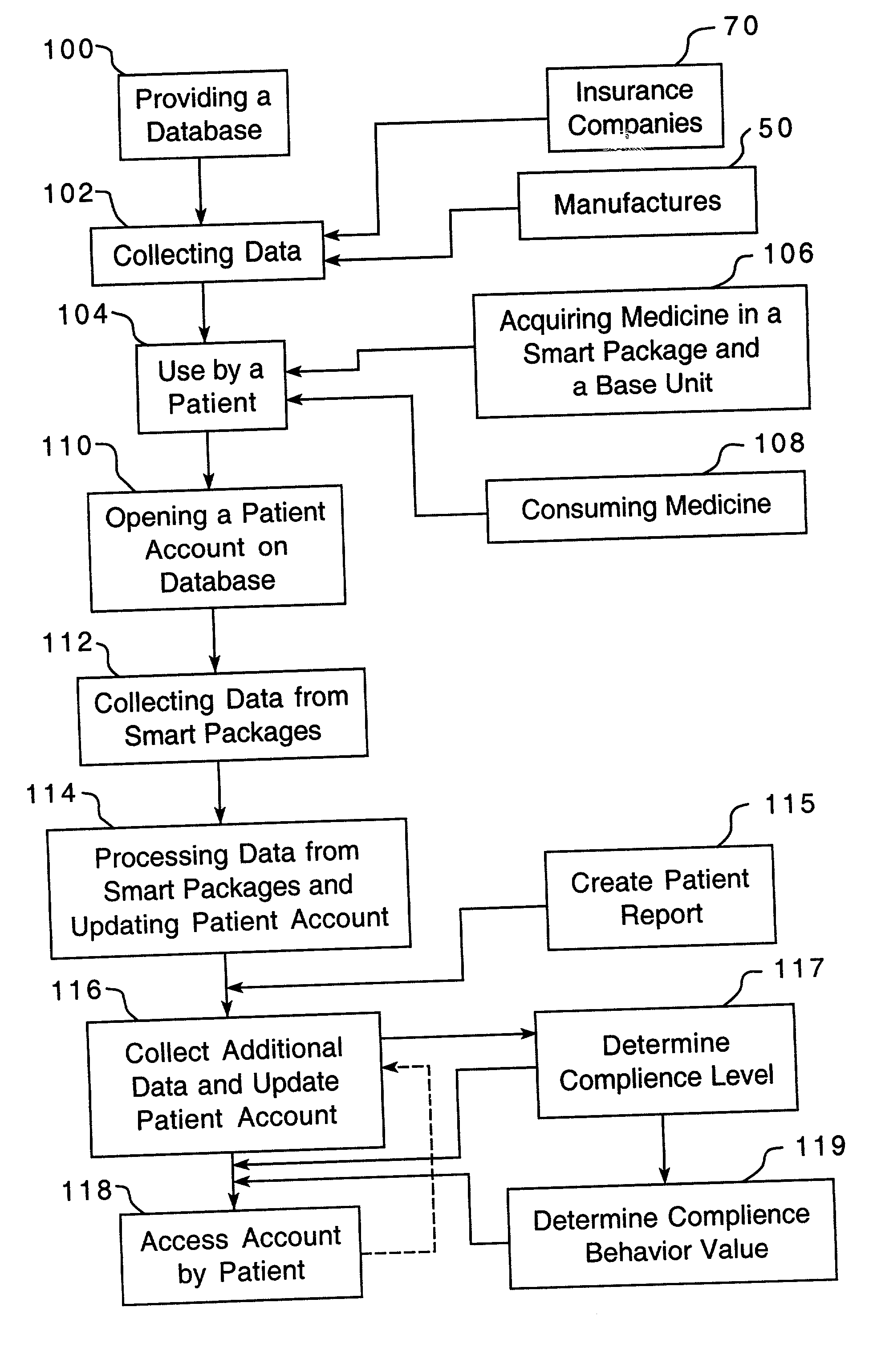
A method is provided for encouraging patient compliance with a medicine regimen that includes interaction with the patient. The method includes the steps of providing a database which includes information regarding each patient. Information is supplied to the database by smart packages and other stakeholders. The information in the database is used to construct a patient report that may be viewed by the patient and others. Information in the patient report includes data on the patient's compliance, side effects of the medicine, expected results, interactions with other medicines, statements complimenting compliance, and warnings discouraging non-compliance. The patient report may be accessed by a common communication means such as the Internet.
Owner:CLEMENTI & ASSOCS
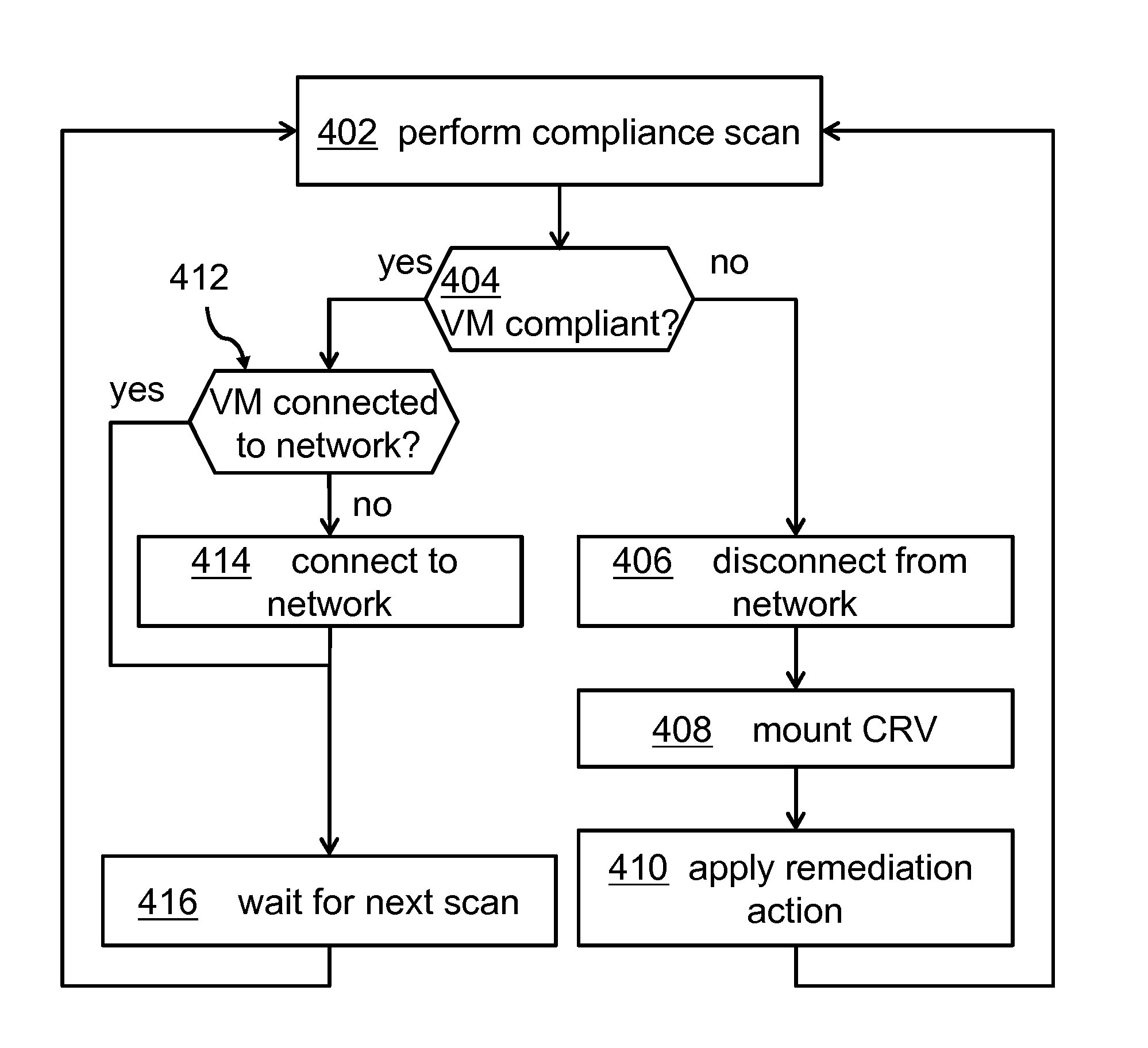
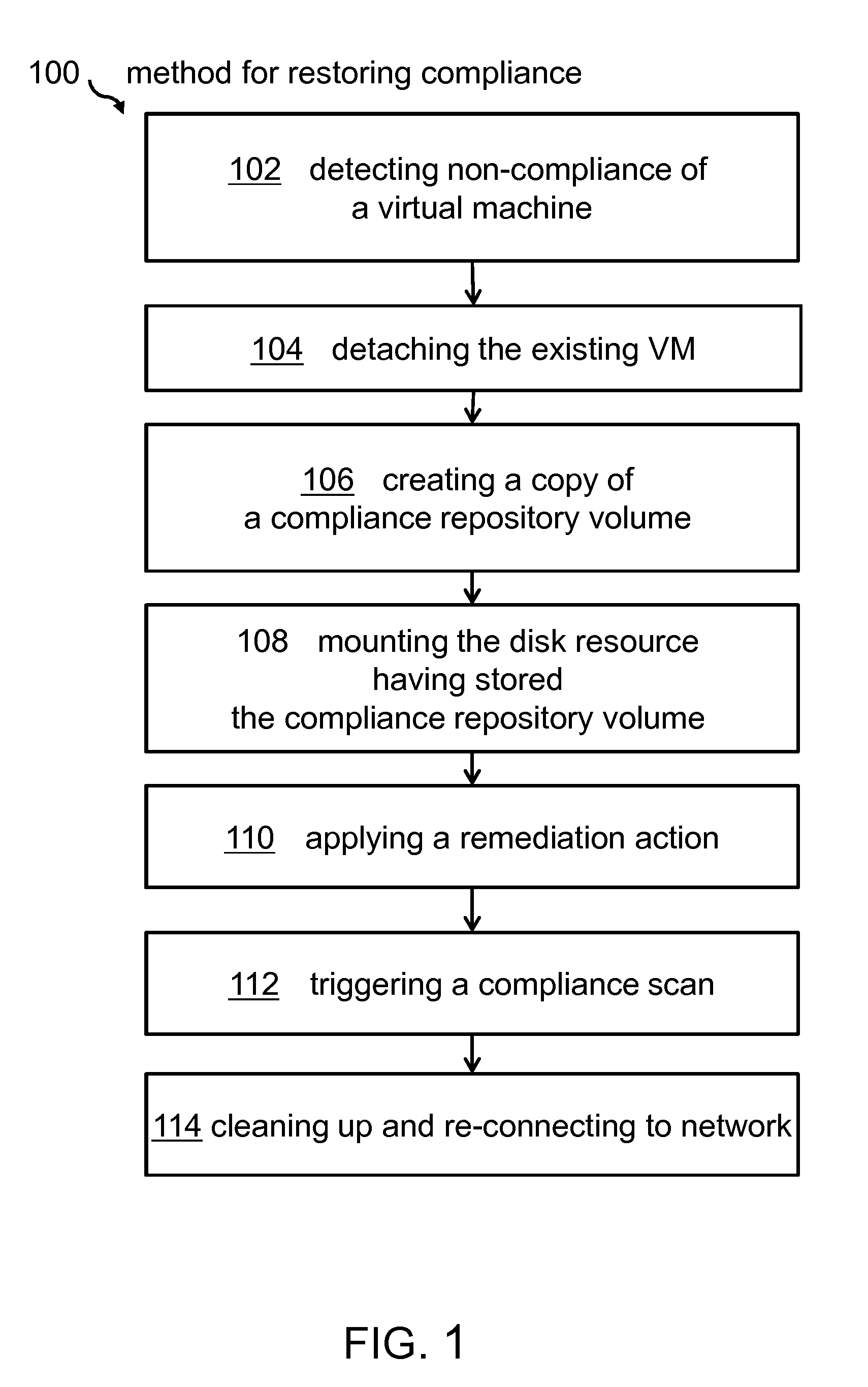
Managing Virtual Machine Policy Compliance
InactiveUS20150012920A1Improve system securityInfluence copying processSoftware simulation/interpretation/emulationMemory systemsNon complianceVirtual machine
A method for managing virtual machine policy compliance. The method for restoring compliance of a virtual machine found to be non-compliant to a compliance rule may comprise detecting non-compliance of a virtual machine using a compliance agent, detaching the virtual machine from a network, creating a copy of a compliance repository volume, mounting the newly requested disk resource having stored the copy of the compliance repository volume, applying a remediation action to the virtual machine, and triggering by the compliance agent a compliance scan for ensuring that the virtual machine complies to the compliance rule.
Owner:IBM CORP
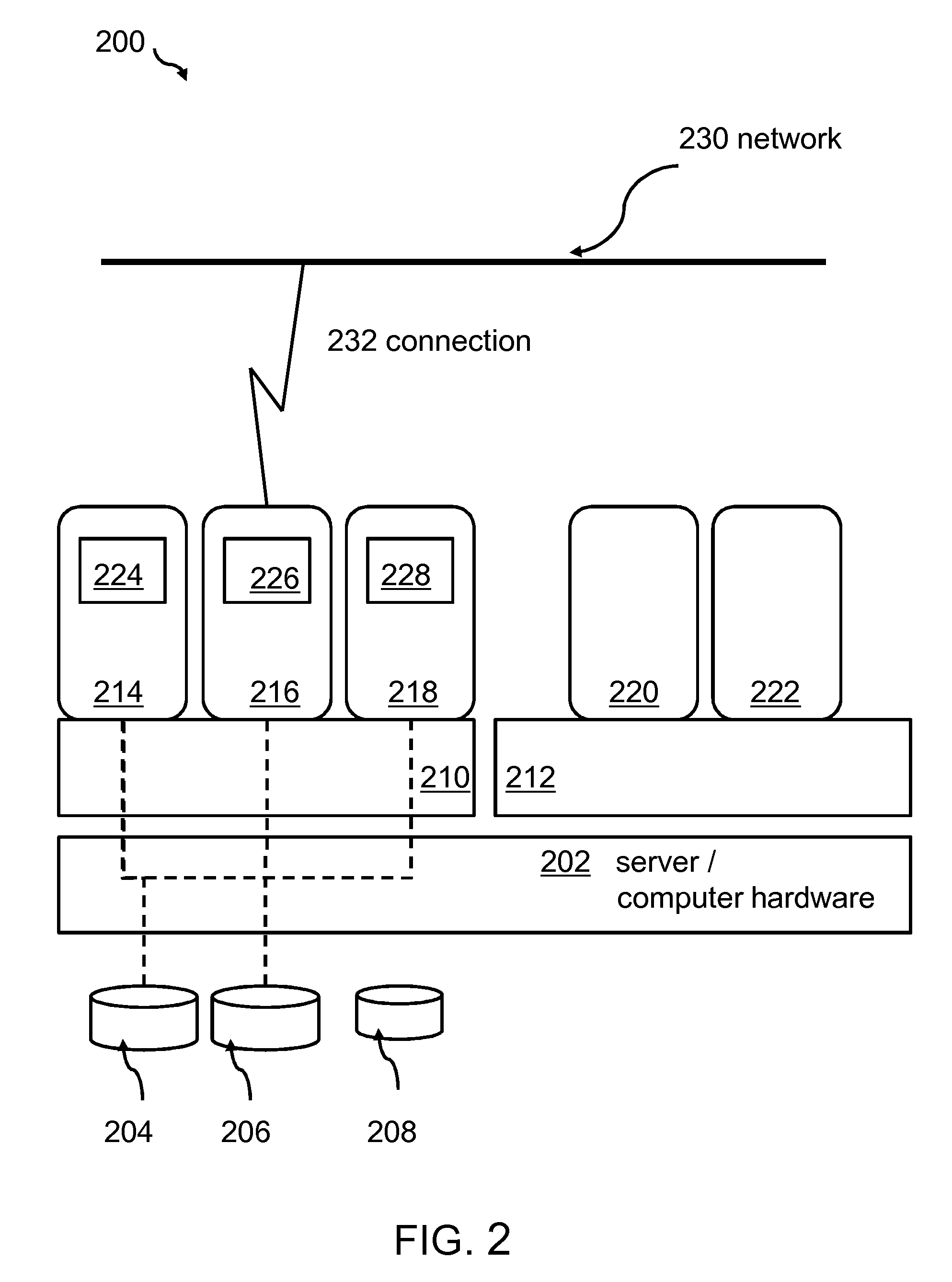
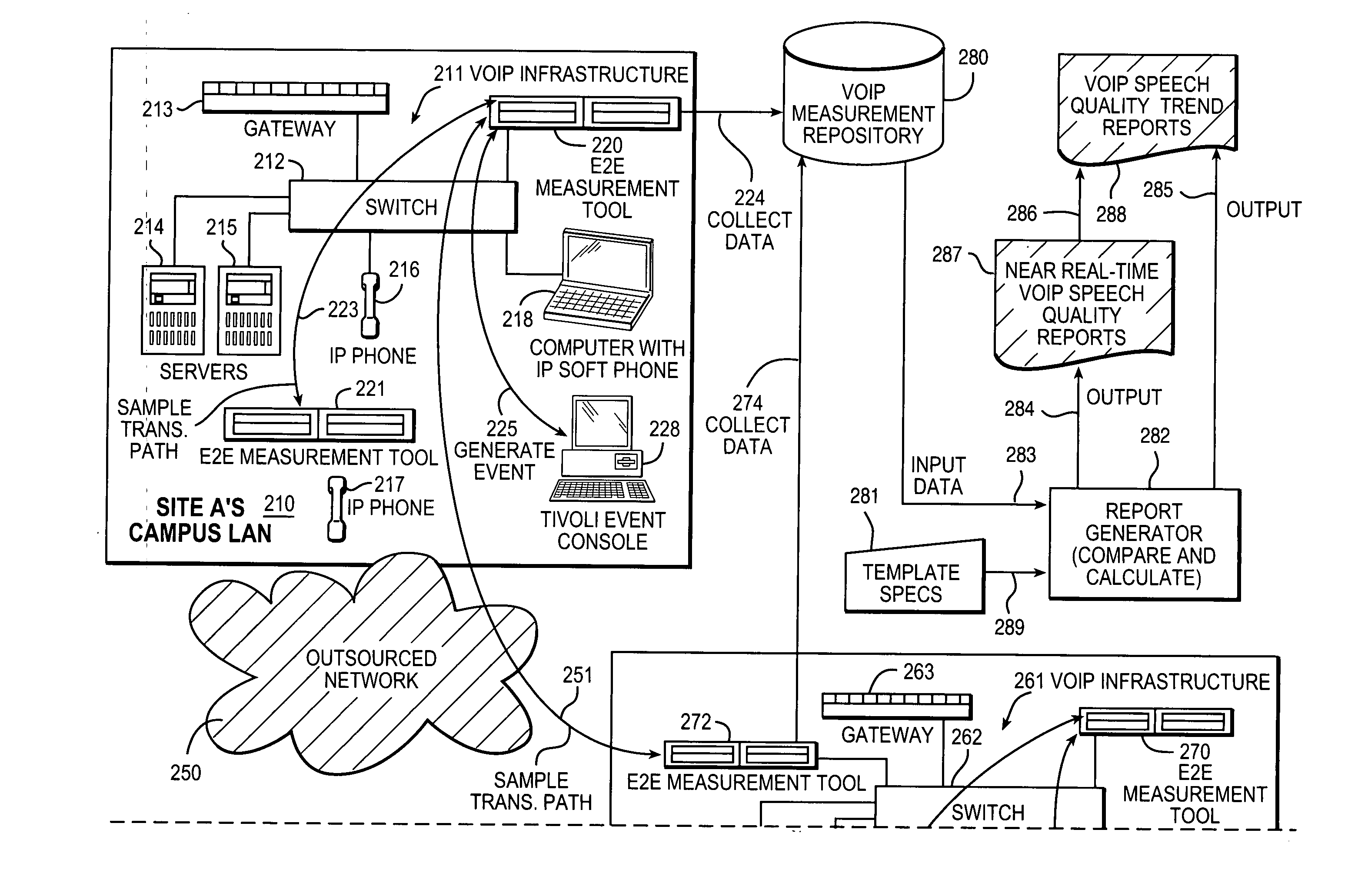
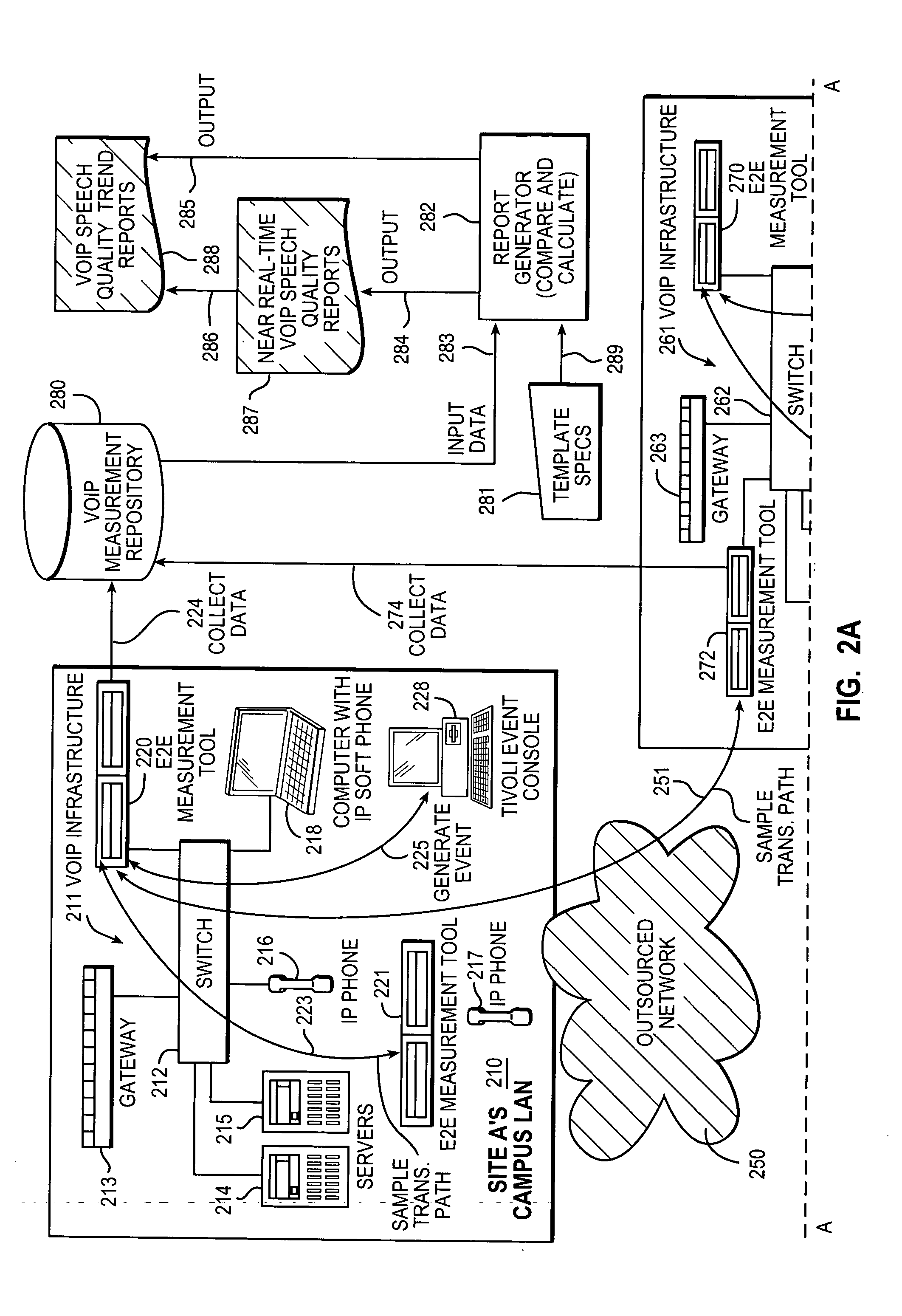
Measurement, reporting, and management of quality of service for a real-time communication application in a network environment
An example of a solution provided here comprises providing a measurement process including: (a) transmitting a test stream over a transmission path; and (b) measuring a quality-of-service indicator for a real-time communication application based on the transmitting; utilizing the measurement process, in continuously sampling a plurality of transmission paths in the real-time communication application's production environment; collecting data from the measurement process; comparing measured values to a threshold value; outputting a representation of compliance or non-compliance with the threshold value; and outputting a trend report based on the data; whereby the real-time communication application may be managed with reference to the threshold value. Such a solution may be selected for a Voice-over-Internet-Protocol application, a video conference application, or a speech-recognition application, to give some non-exclusive examples. One such example comprises measuring a speech-quality indicator for a Voice-over-Internet-Protocol application.
Owner:IBM CORP
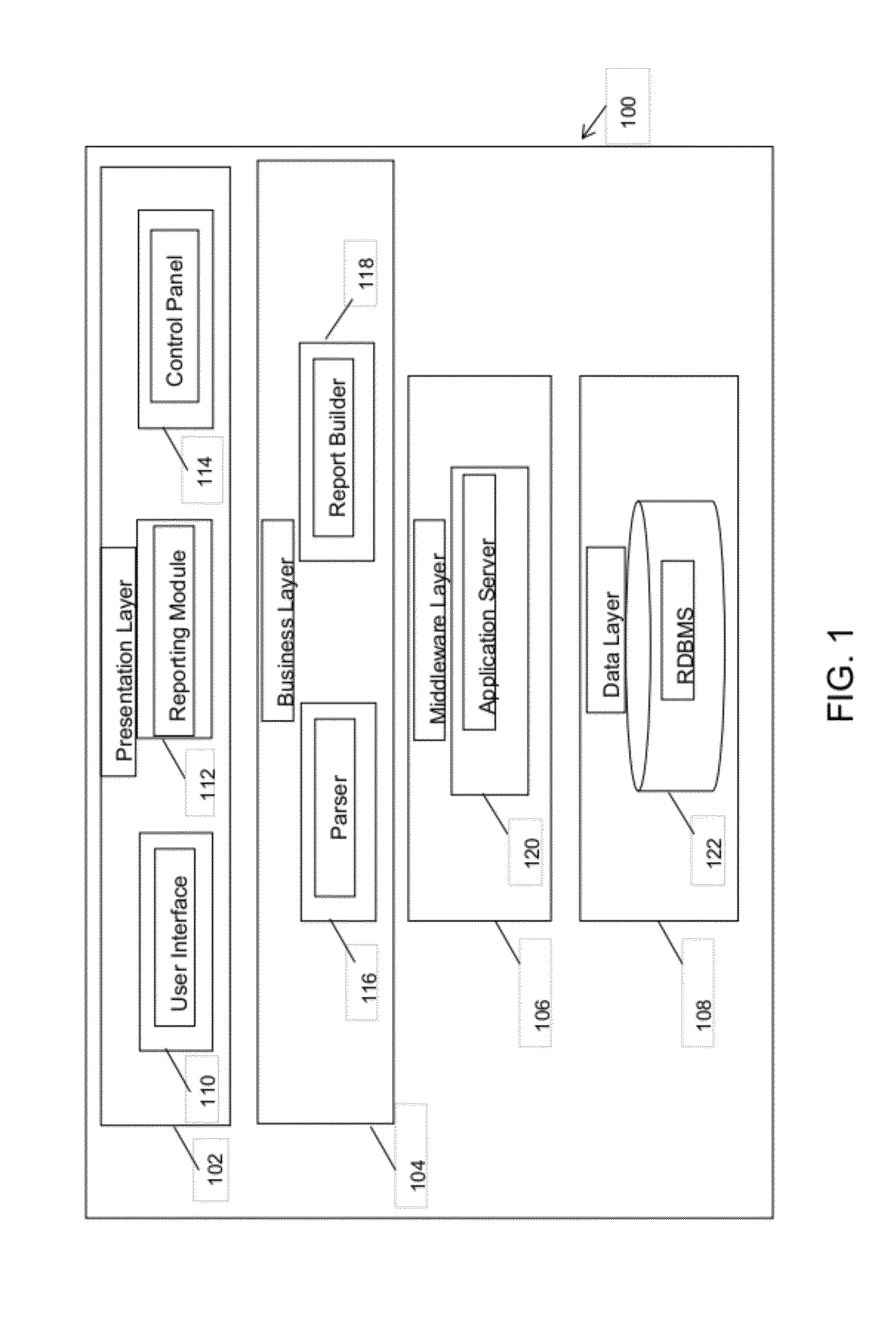
Method and system for reporting web standard non-compliance of web pages
ActiveUS20120254723A1Natural language data processingSpecial data processing applicationsNon complianceGuideline
A method and system for reporting web standard non-compliance of web pages is provided. The method includes receiving a local copy of the web page to be tested for web standard non-compliance. The method further includes determining a set of errors on the web page corresponding to a user specified accessibility guideline. Thereafter an HTML overlay report is generated based on the determined set of errors. Further, a set of controls is generated based on the user specified accessibility guideline, the local copy and the set of errors. Finally, one or more controls are selected from the set of controls and based on the one or more selected controls and the determined set of errors one or more images are associated with each HTML element non-conformant to the accessibility guideline on the web page.
Owner:INFOSYS LTD
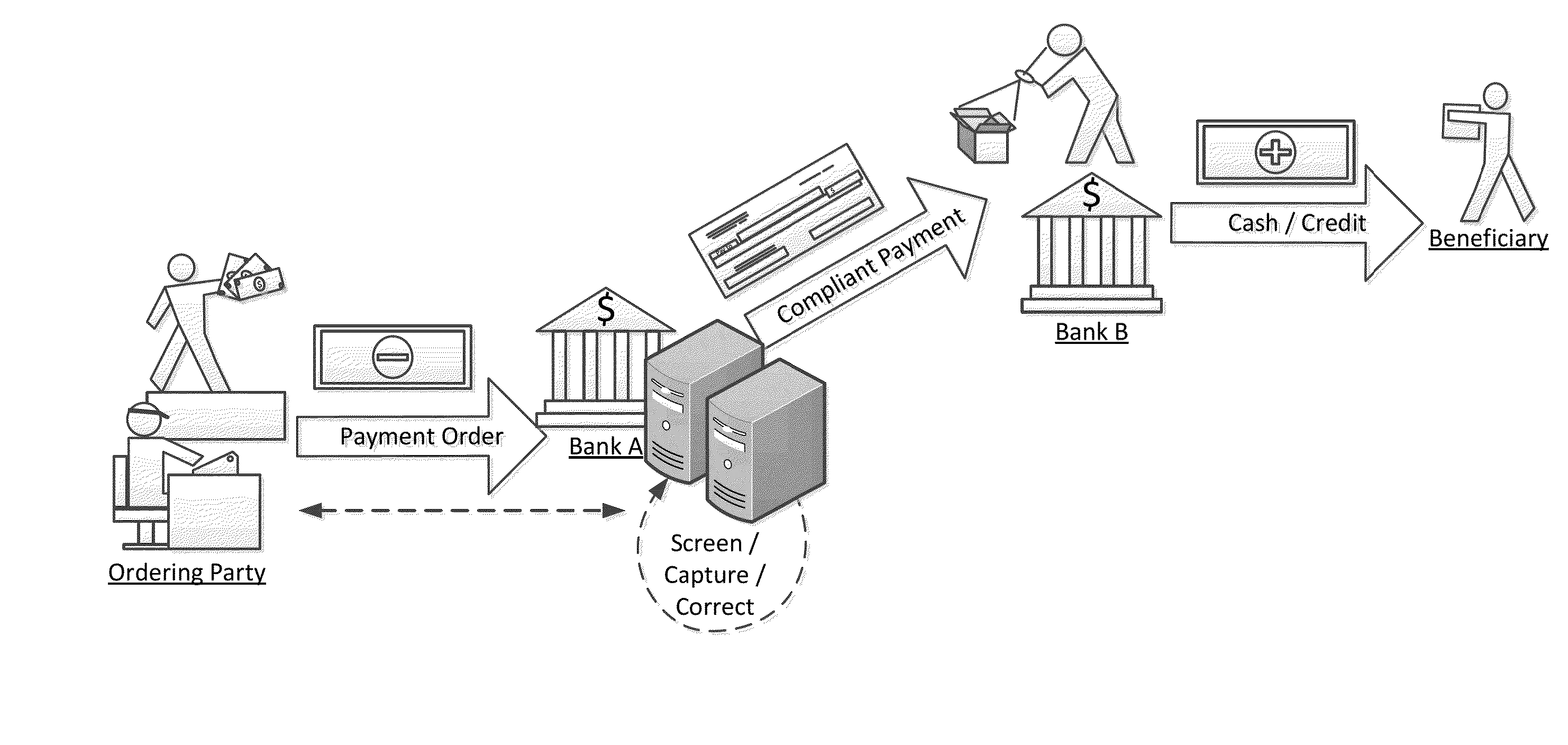
Non-compliant payment capture systems and methods
InactiveUS20150120545A1Overcome limitationsEfficiently detect and correctFinanceProtocol authorisationNon compliancePayment order
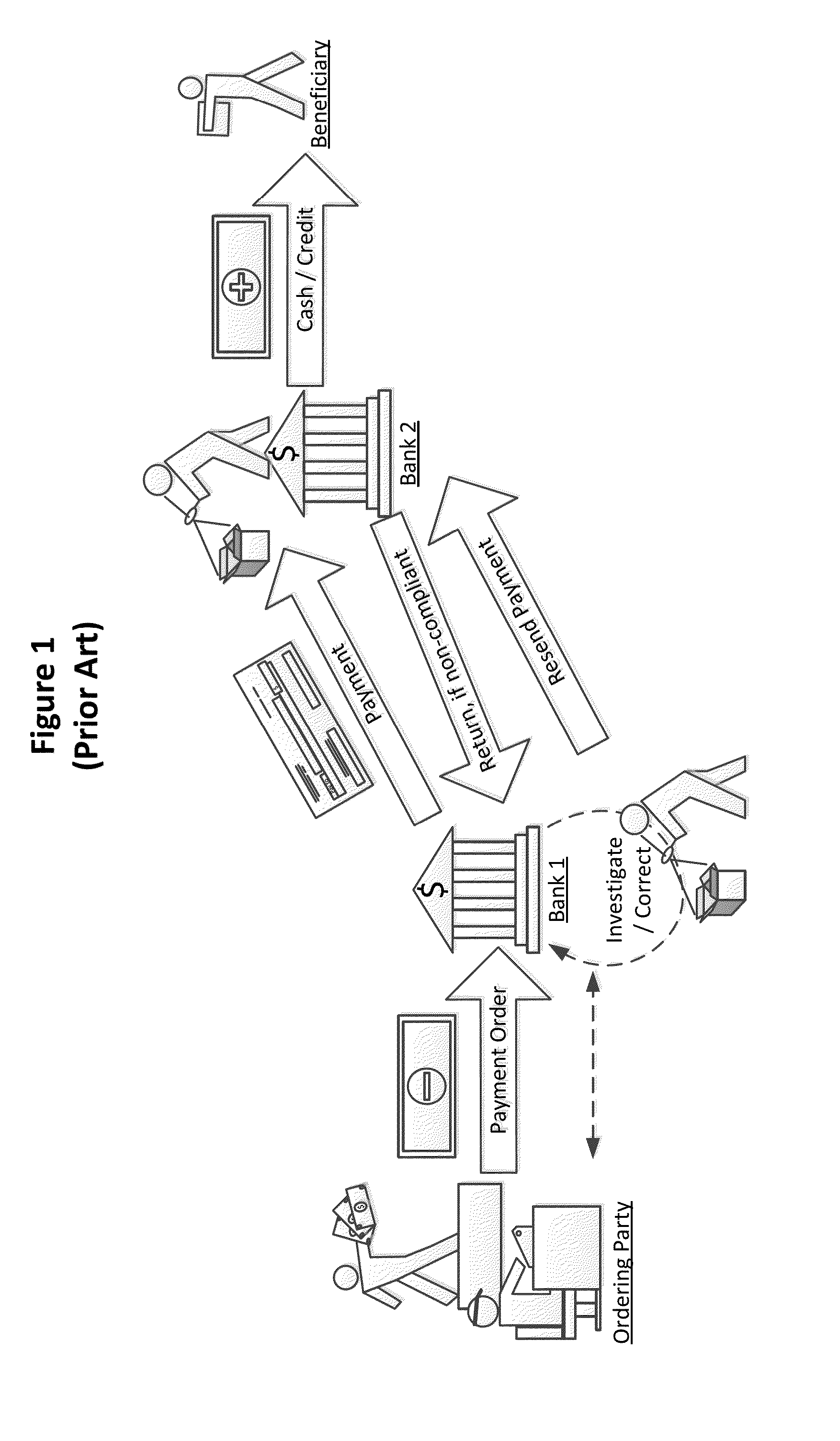
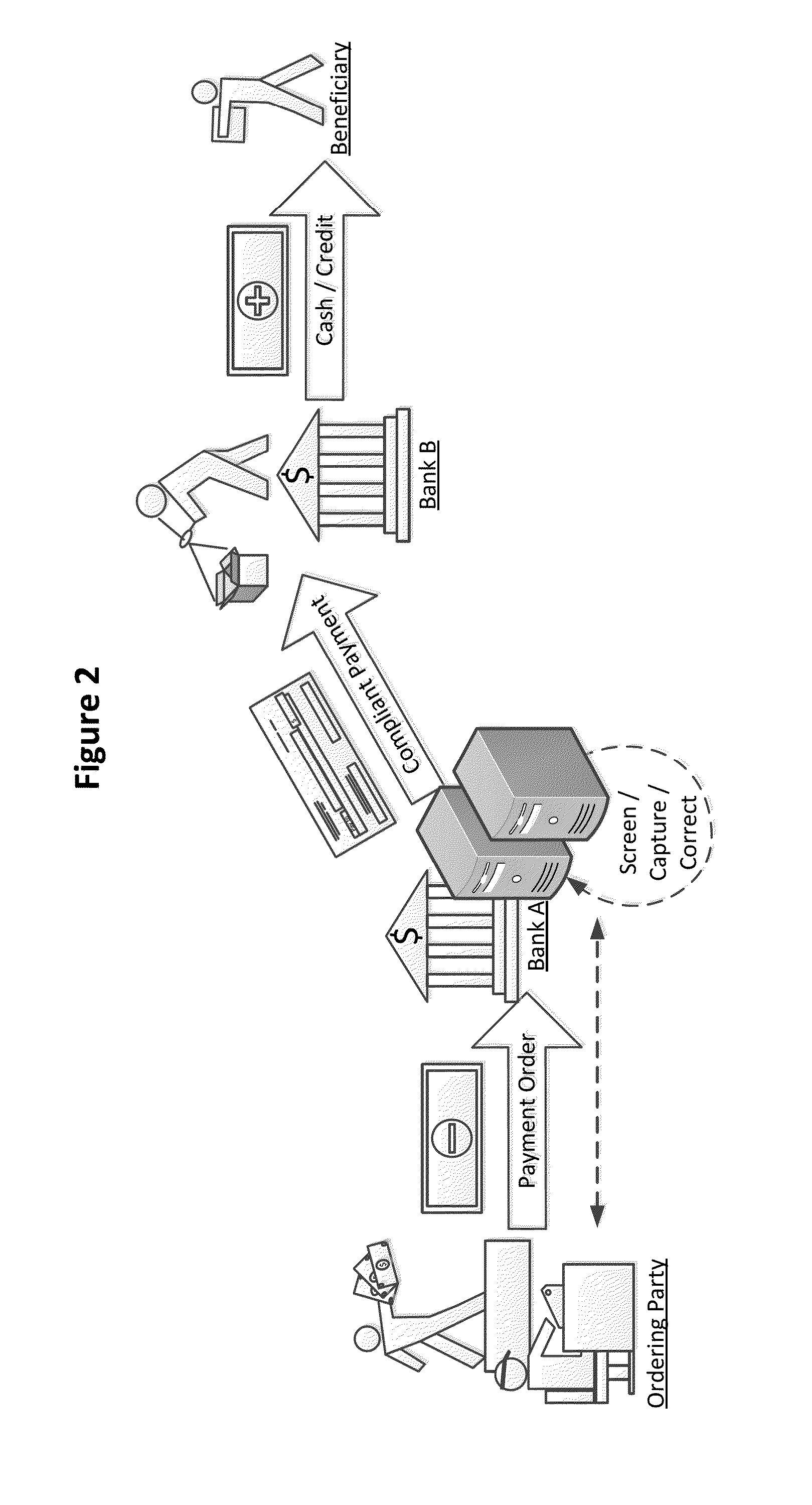
Embodiments of the present invention are generally directed to detection of non-compliant payment requests or payment orders. In particular, the invention detects non-compliance with travel rules put in place by multiple countries throughout the world. The systems and methods for capturing non-compliant payments may be adapted for various funds transfer channels or systems, including but not limited to Society for Worldwide Interbank Financial Telecommunication (SWIFT), Federal Reserve Wire Network or FedWire, Clearing House Interbank Payments System (CHIPS), or other public or proprietary funds transfer or payment systems.
Owner:JPMORGAN CHASE BANK NA
Fall-sensing systems, hip protector systems, and other protective systems
InactiveUS20060049950A1Small sizeInertial sensorsDiagnostic recording/measuringNon complianceHip protector
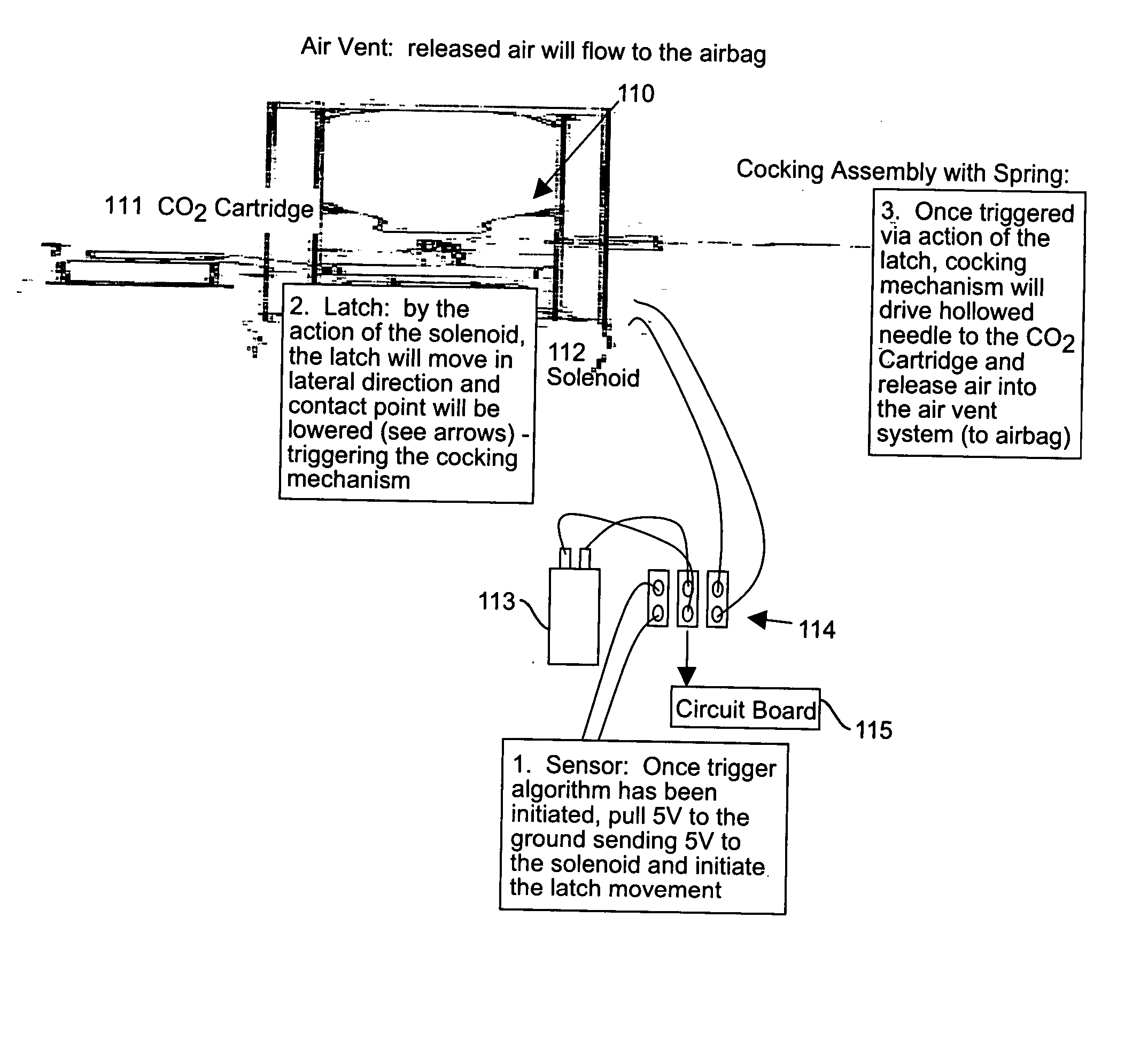
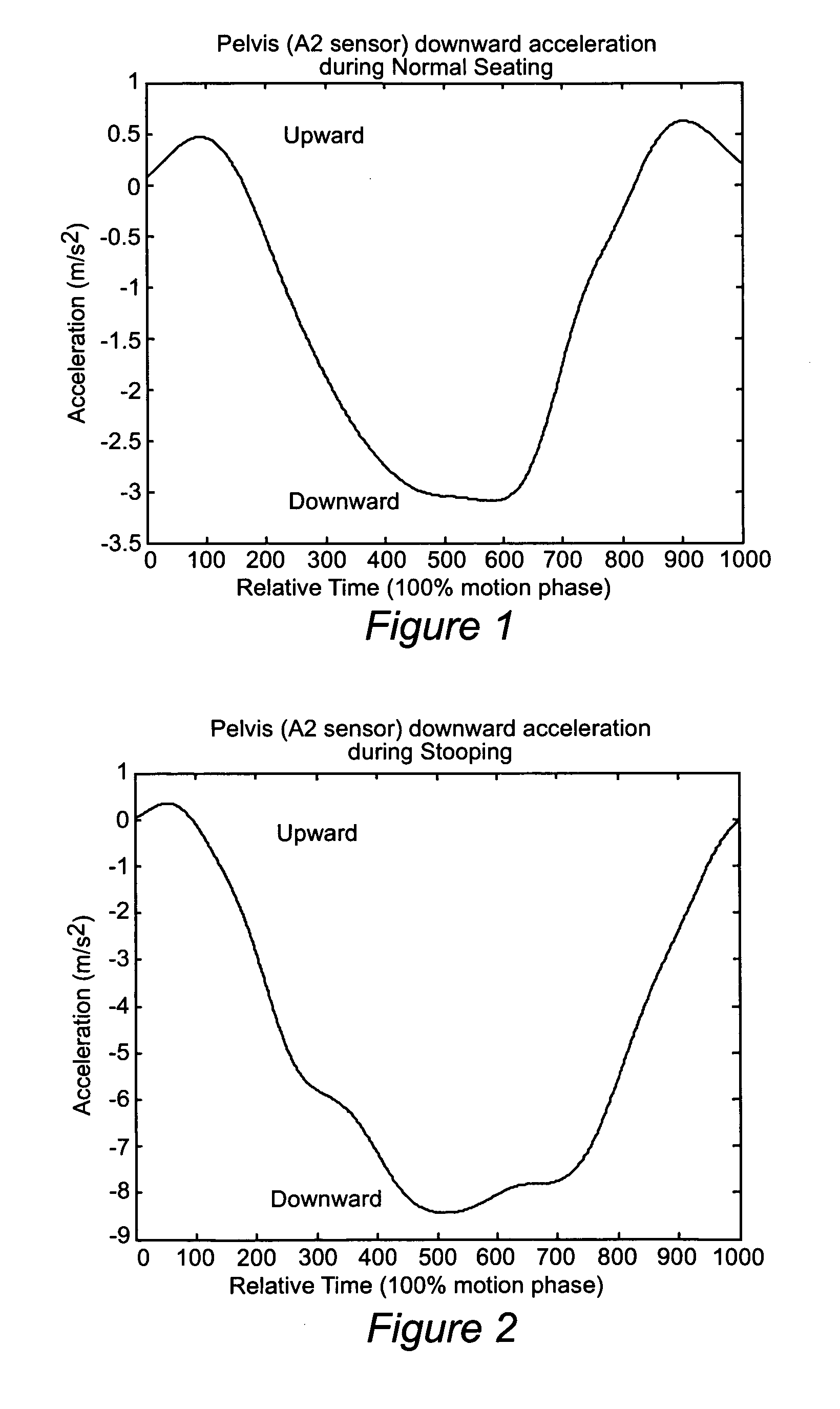
Fall-sensing systems are provided which do not generate false alarms for a non-falling event. Inventive fall-sensing systems may be magnetometer-free. Thin-profile (less than ½ inch, pre-inflation) wearable systems are provided. By removing the problem of false alarms and by slimming the pre-inflation profile, a practically useable wearable protection solution may be provided for an individual prone to falling. The number and severity of hip fractures in the elderly may be reduction. The inventive product actively assesses fall accidents and triggers an inflatable airbag protection device. The problem of non-compliance in wearing hip protectors that has previously limited the effectiveness of other hip protectors also has been solved.
Owner:VIRGINIA TECH INTPROP INC
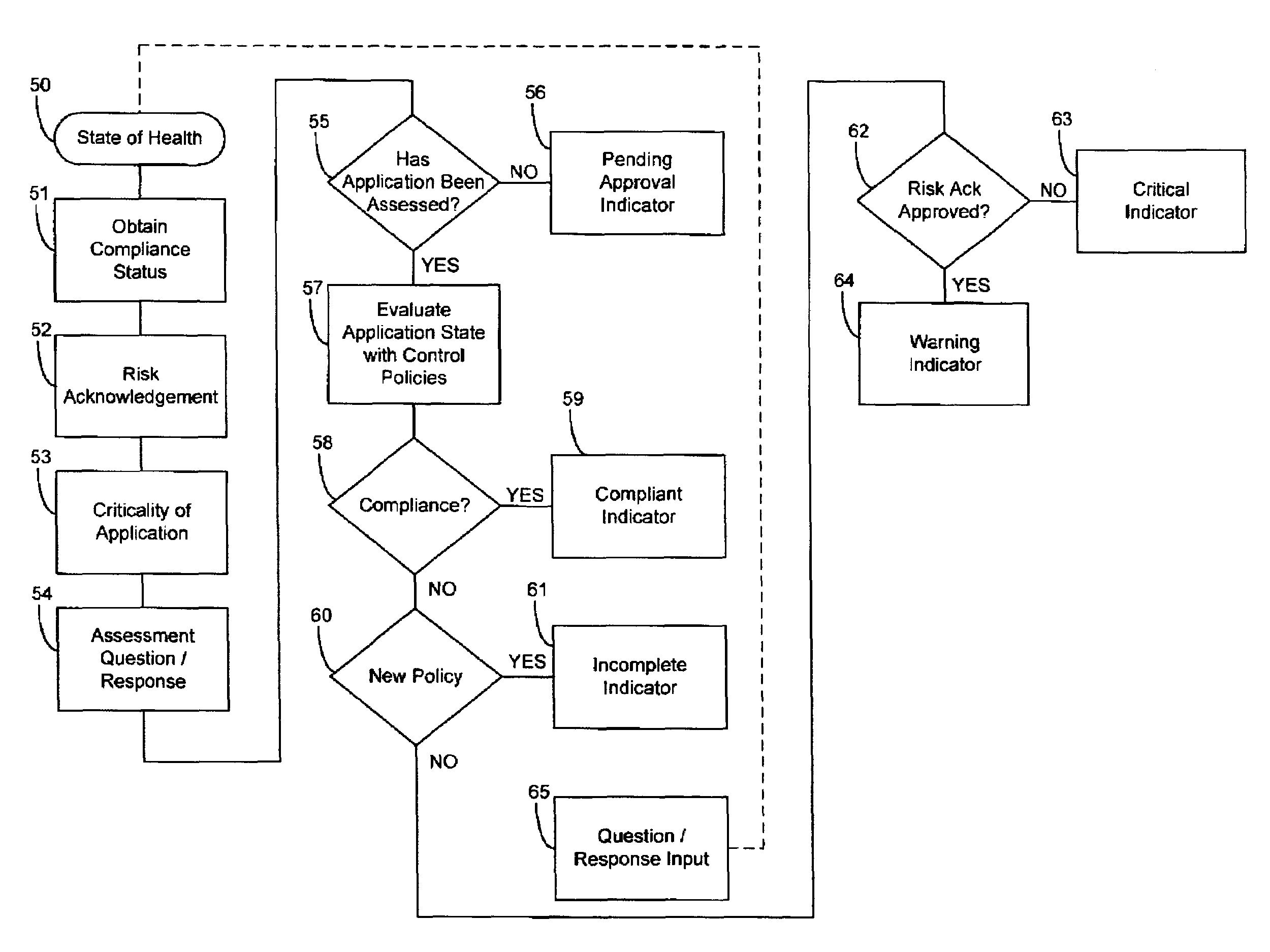
System and method for managing global risk
InactiveUS7433829B2General purpose stored program computerOffice automationNon complianceRisk status
A system for tracking compliance to risk management policies for a given enterprise that provides risk status feedback on hierarchical managerial levels. The system notifies users of potential problems with non-compliance of enterprise policies set on a high level of enterprise management, and prompts the users to take steps to achieve compliance. The enterprise policies are designed to protect the enterprise from various forms of risk associated with enterprise activities. Accordingly, minimizing risk across enterprise operations, subdivisions, projects and applications produces an overall benefit of reduced liability or exposure to liability for the entire enterprise. A compliance status is provided by business groups at all levels of the enterprise, and consolidated for each management level to which the risk status is promoted. Higher level managers can view summaries of risk management status for the business divisions, and select particular statuses to view compliance among various business groups under the manager's responsibility.
Owner:JPMORGAN CHASE BANK NA
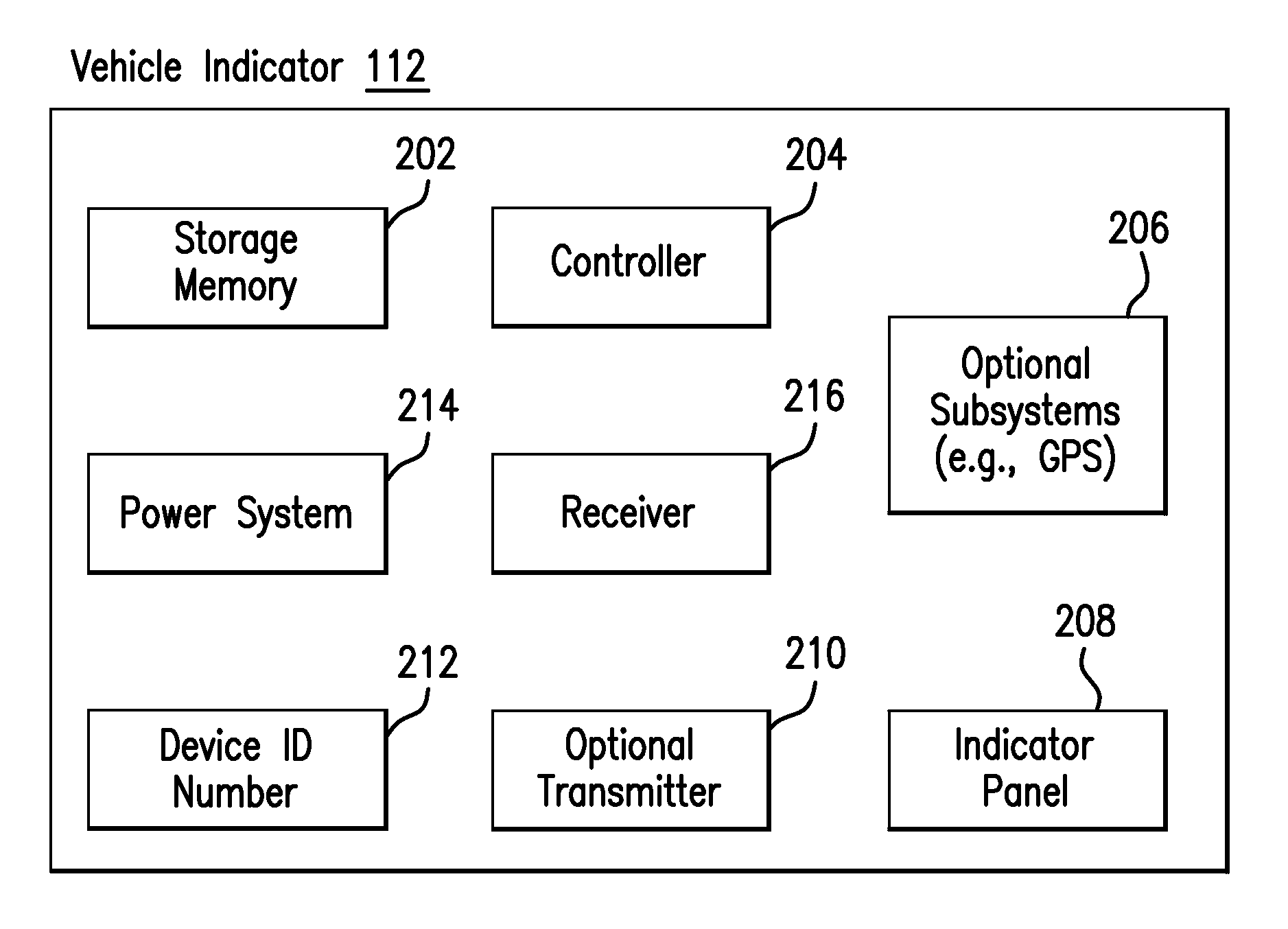
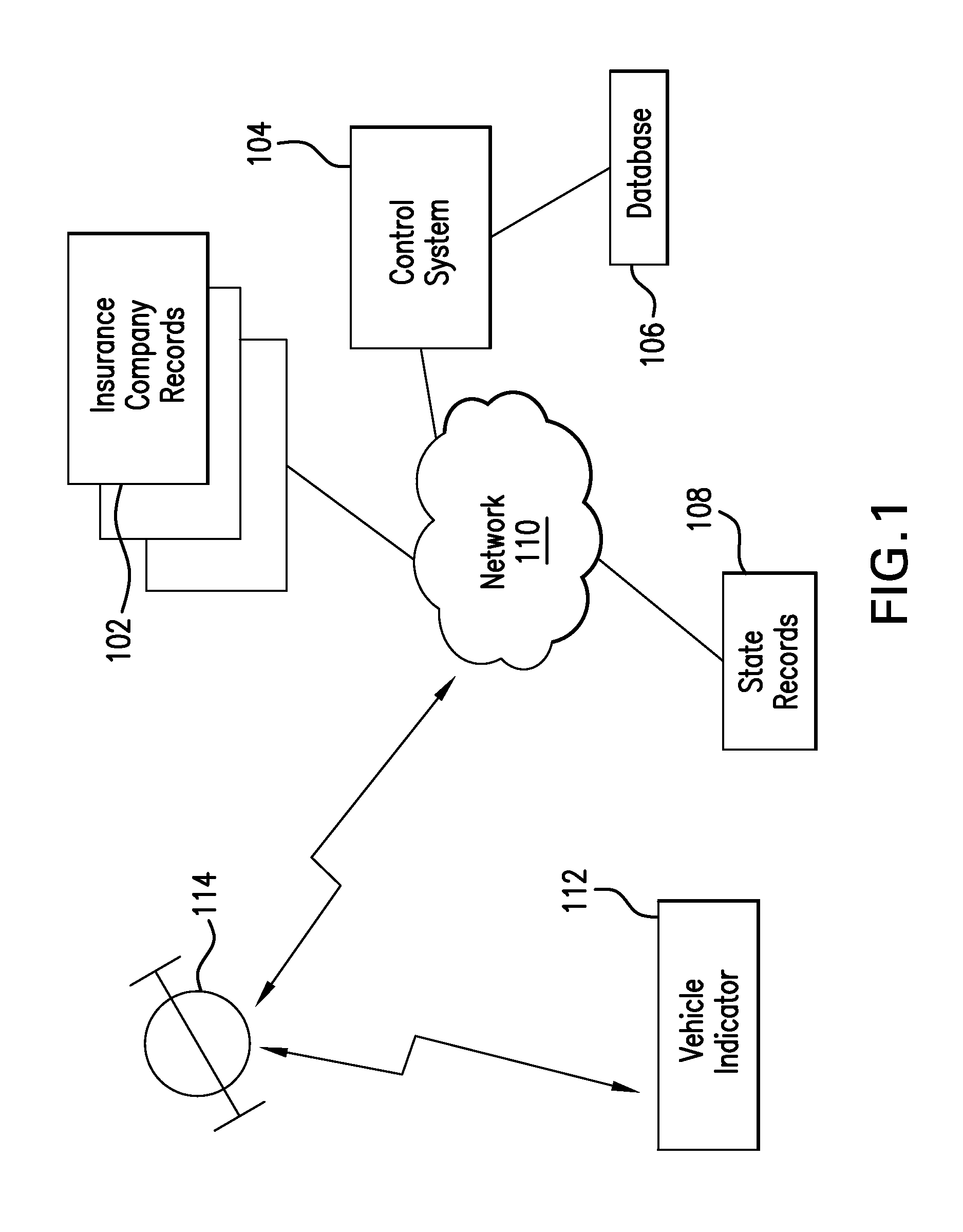
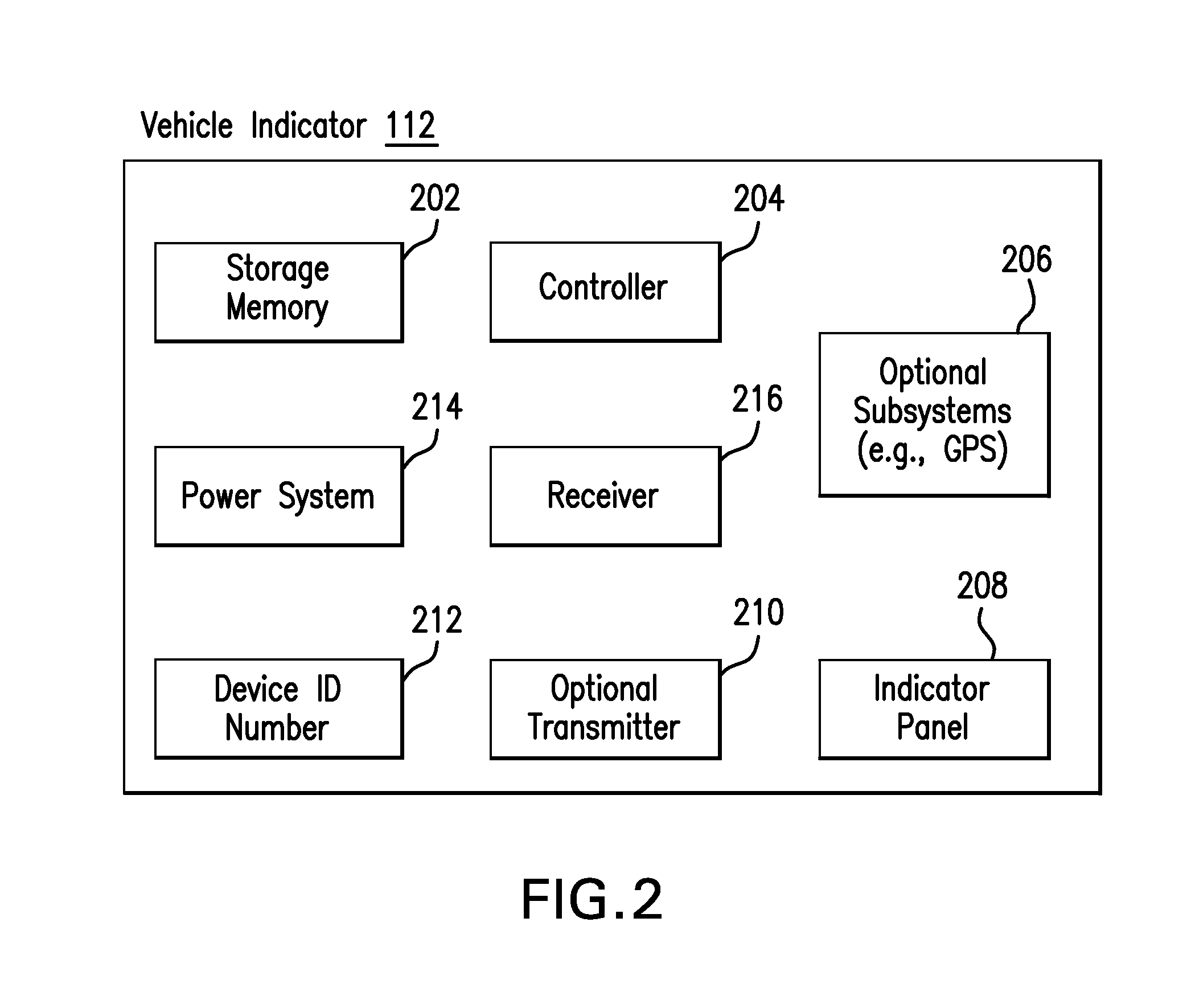
Method and apparatus for providing probable cause relating to vehicle non-compliance
InactiveUS20130138267A1Digital data processing detailsRoad vehicles traffic controlNon complianceControl signal
The present invention provides systems, methods and devices to generate an indication or signal by an indicator device of a vehicle that is detectable near the vehicle regarding one or more statuses of the vehicle, such as insurance policy, registration, crimes, wanted persons, etc. The indicator device may produce the indication or signal based on a control signal sent from a remote control system to the indicator device via a network and / or broadcast transmitter. The control system may determine the control signal and vehicle status based on information from external database(s). The indicator device may also receive local status information regarding the vehicle or any person associated with the vehicle. Such local status information may be sent back to the control system as a report signal, which may be stored in a remote database. The indicator signal or report signal may be detected by law enforcement near the vehicle.
Owner:HIGNITE GERALD +3
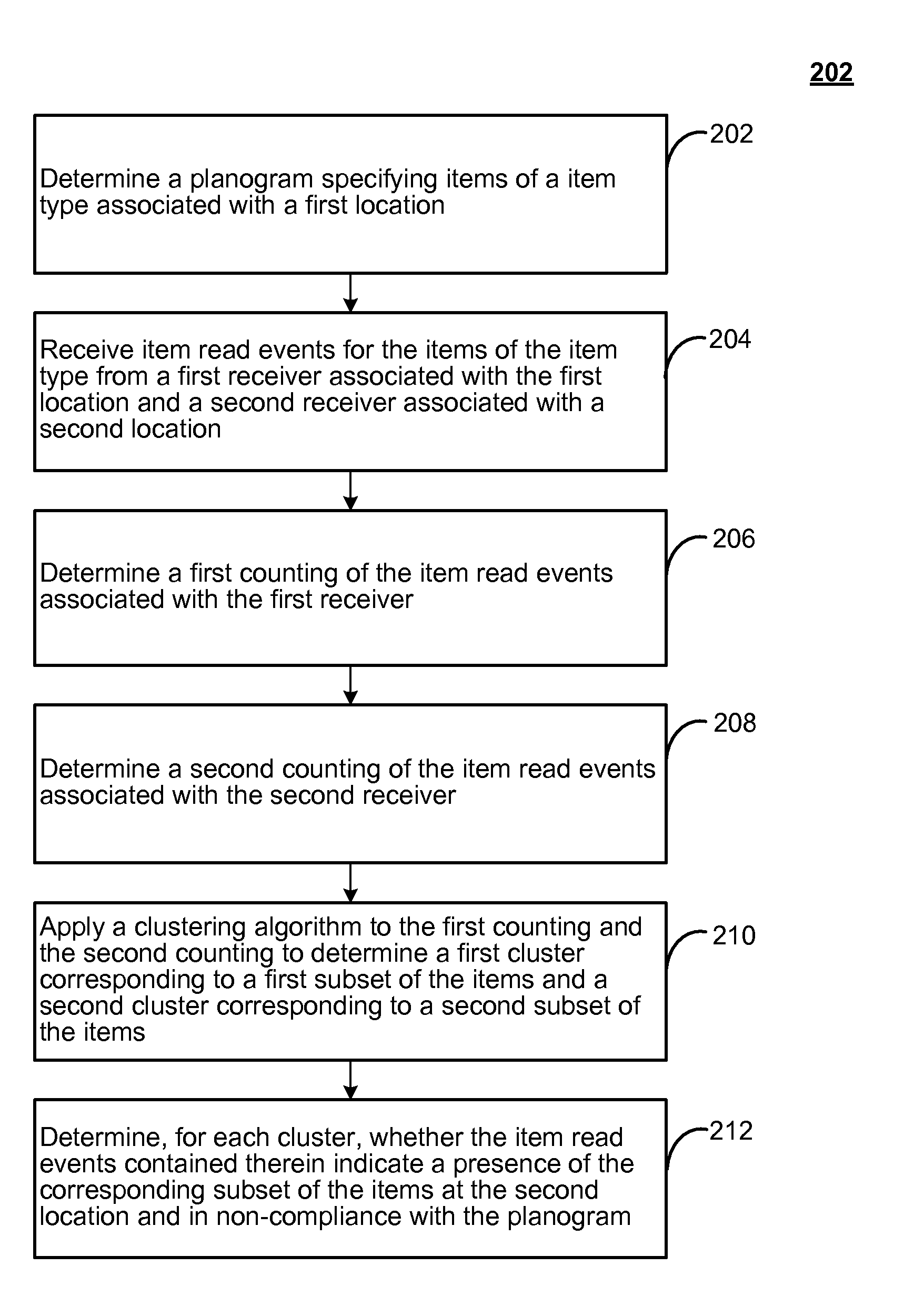
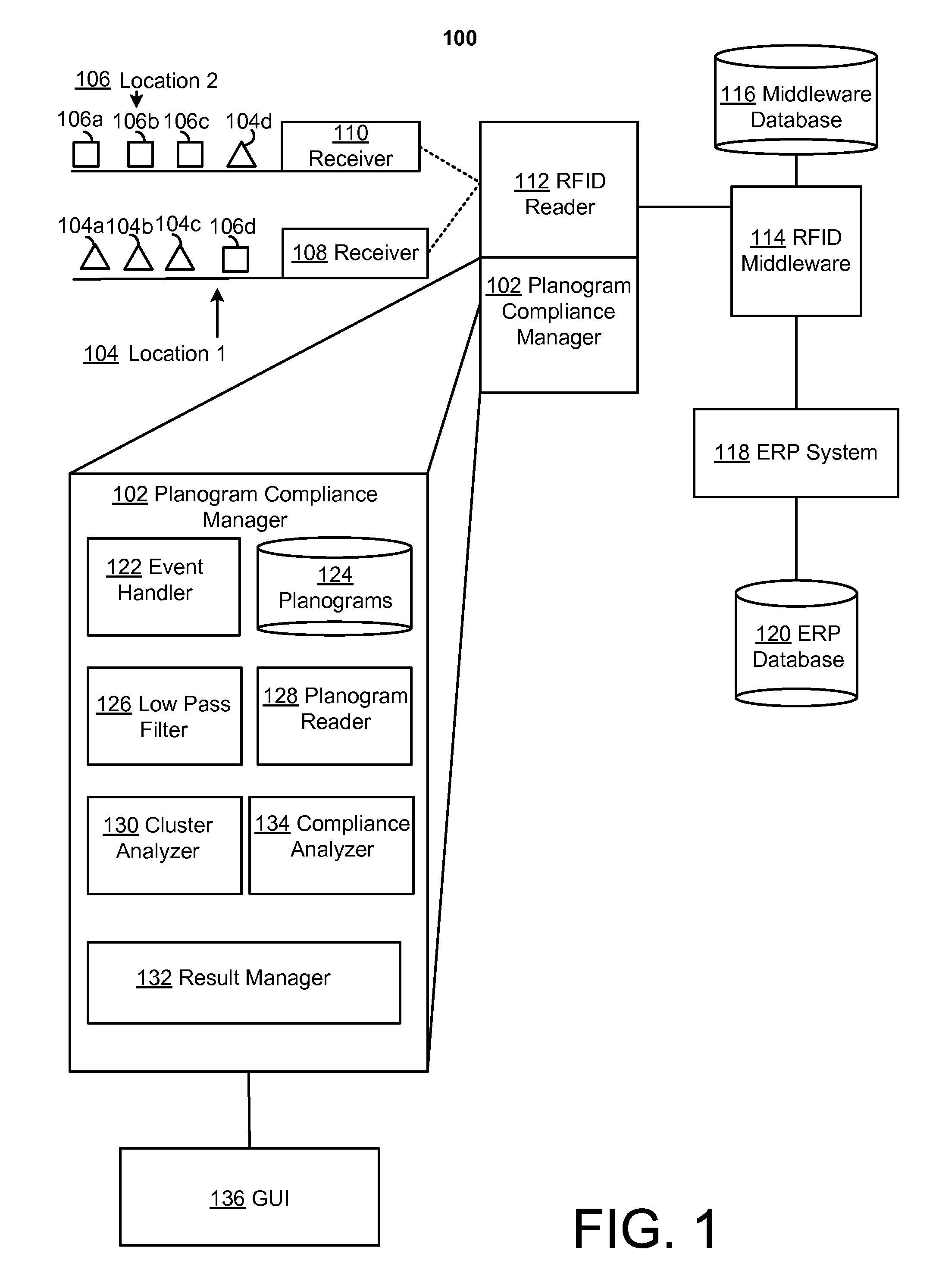
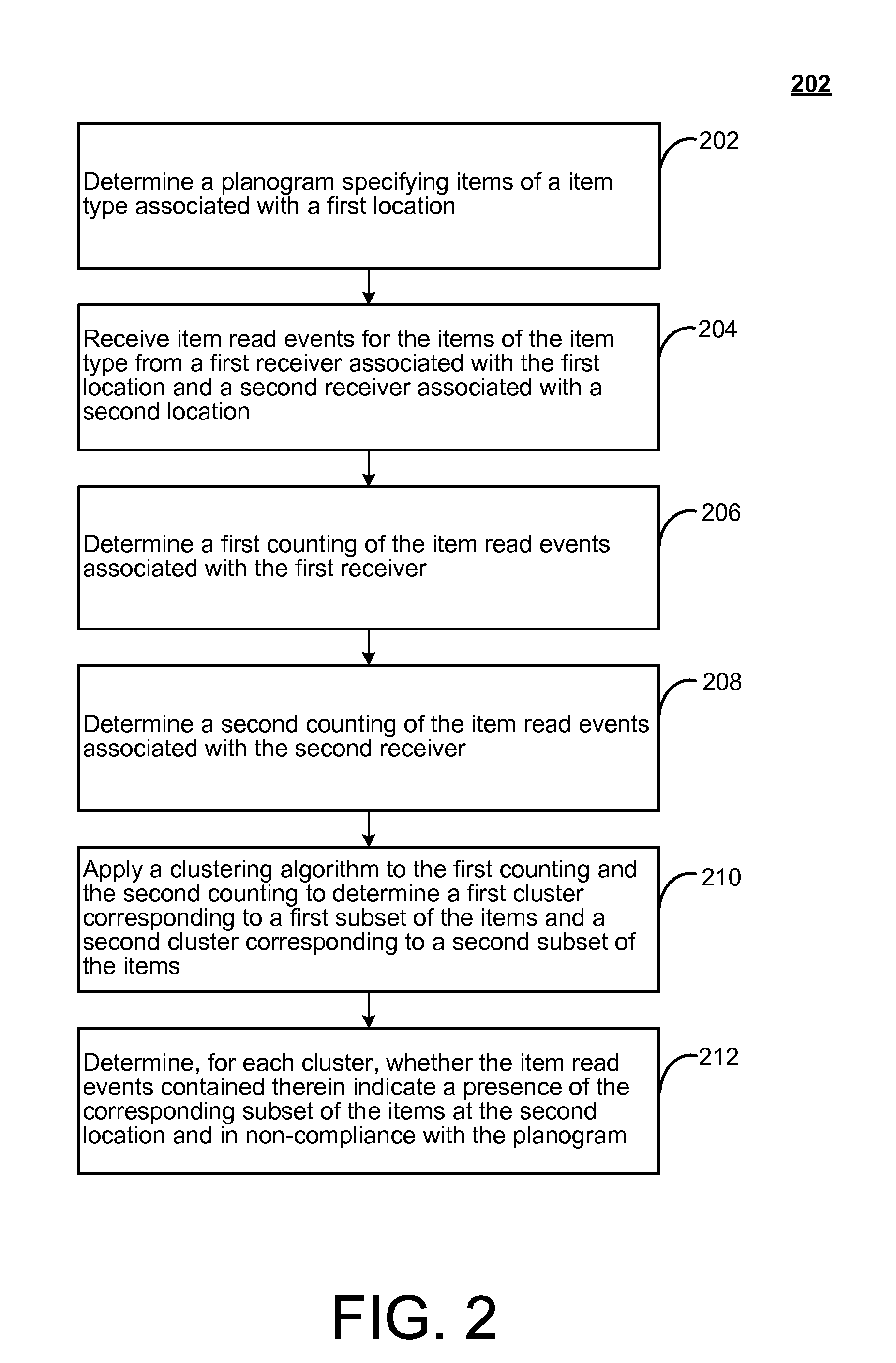
Planogram compliance using automated item-tracking
ActiveUS20110050396A1Sensing by pneumatic/hydraulic meansSubscribers indirect connectionCluster algorithmPlanogram
A planogram specifying items of a item type associated with a first location may be determined, and item read events for the items of the item type may be received from a first receiver associated with the first location and from a second receiver associated with a second location. A first counting of the item read events associated with the first receiver may be determined, and a second counting of the item read events associated with the second receiver may be determined. A clustering algorithm may be applied to the first counting and the second counting to determine a first cluster corresponding to a first subset of the items and a second cluster corresponding to a second subset of the items. Then, for each cluster, it may be determined whether the item read events contained therein indicate a presence of the corresponding subset of the items at the second location and in non-compliance with the planogram.
Owner:SAP AG
Validating network security policy compliance
InactiveUS20100050229A1Avoid security breachesSpecial data processing applicationsSecuring communicationNon complianceNetwork security policy
The present invention may provide the ability to determine the actions triggered by a network security policy given a set of conditions. Embodiments of the invention involve testing the security policy at specified times, documenting and analyzing the test results for compliance, recording the results for auditing purposes, writing events to warn of non-compliance findings, and dynamically taking defensive action to prevent security breaches as the result of non-compliance findings.
Owner:IBM CORP
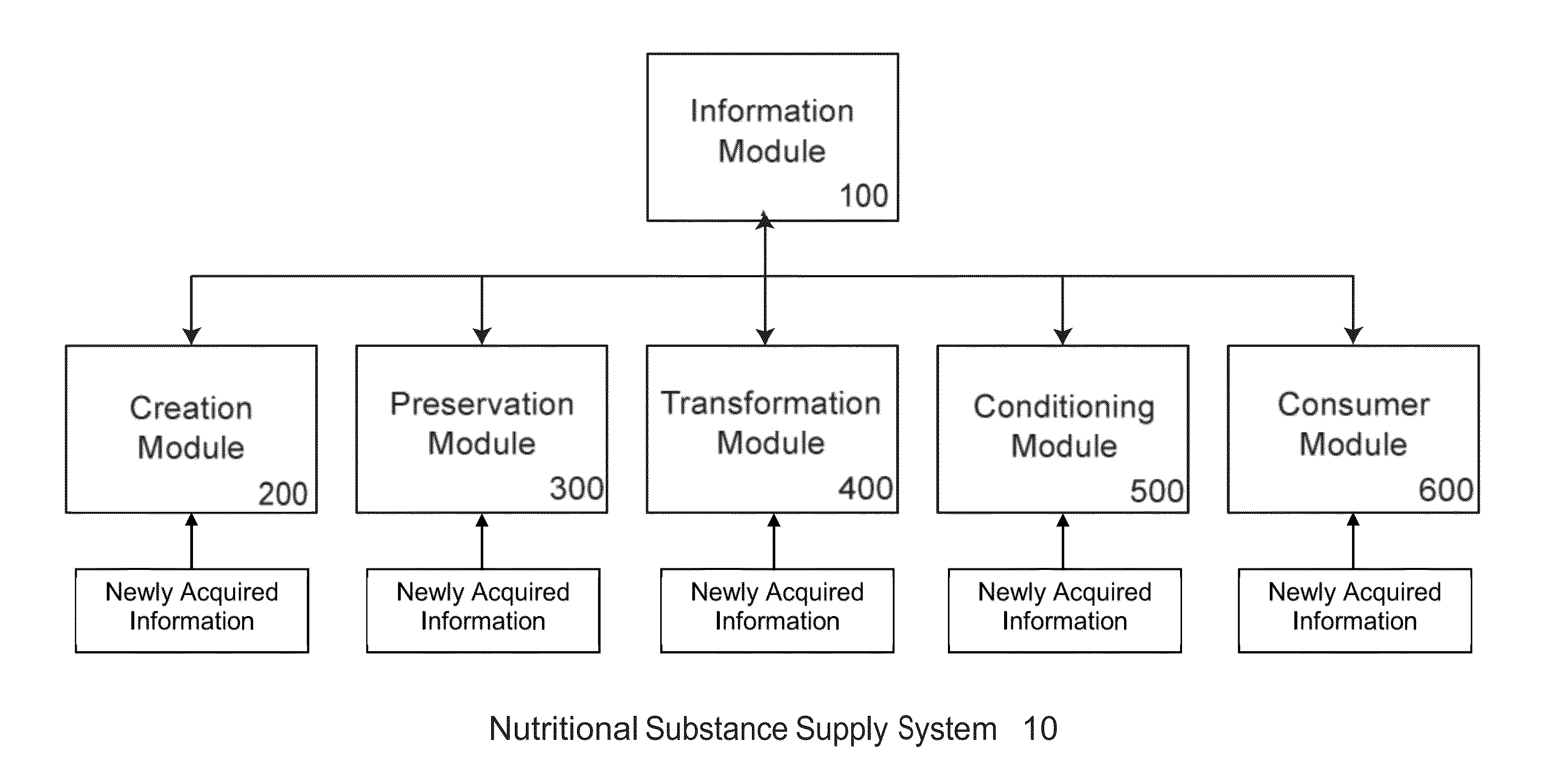
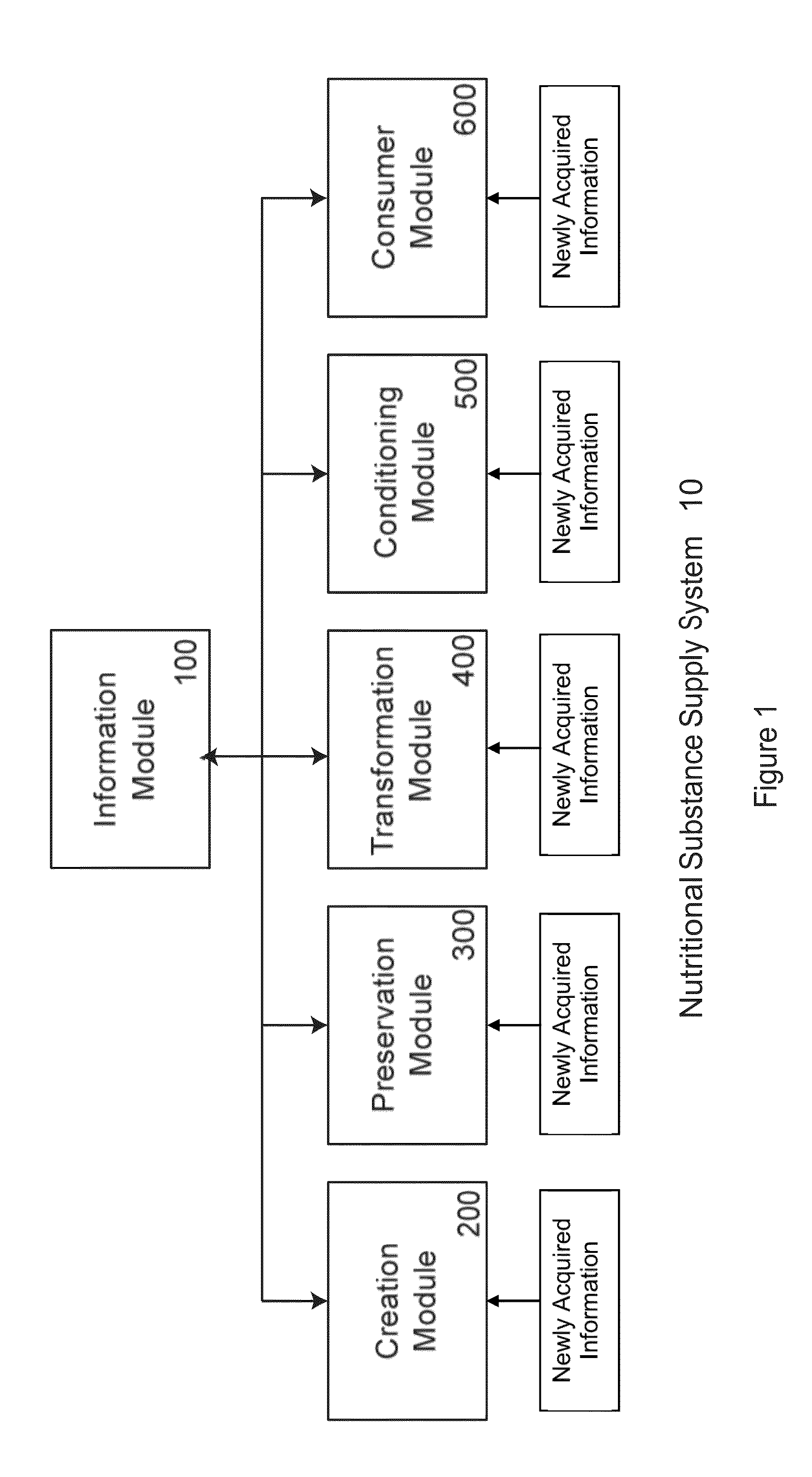
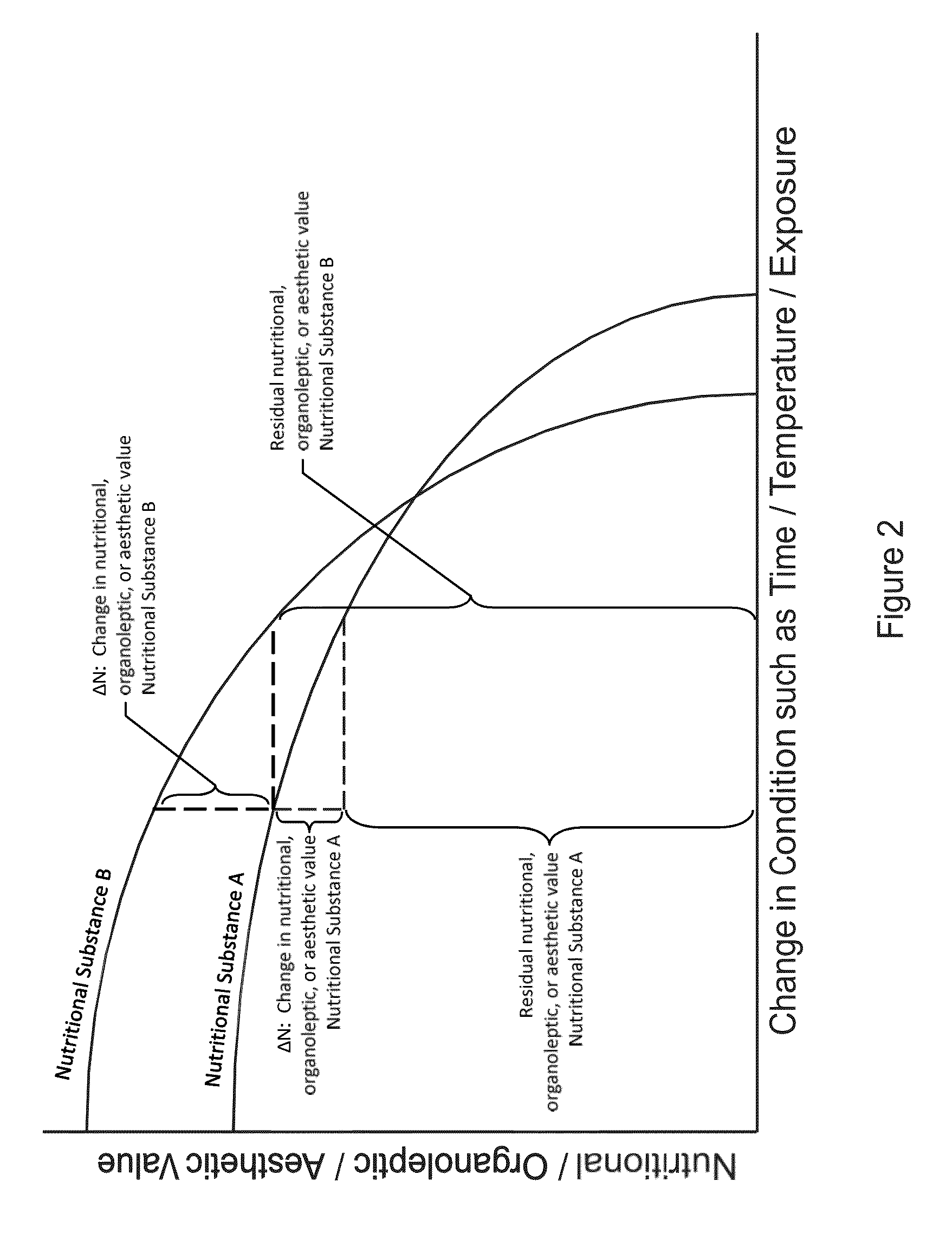
Transformation and Dynamic Identification System for Nutritional Substances
ActiveUS20130275318A1Improve abilitiesMagnitude is minimisedAutomatic control devicesData processing applicationsNon complianceNutritional content
Disclosed herein is a transformation system for at least one component of a single or multi-component nutritional substance. The transformation system obtains information regarding the nutritional substance to be transformed, the desired transformation, and the desired properties, including nutritional content, of the transformed nutritional substance, and dynamically modifies the transformation in response to this information. Also disclosed herein is an information system that enables the rapid determination of a nutritional substance's compliance, or non-compliance, with a consumer's nutritional substance requirements.
Owner:ICEBERG LUXEMBOURG S A R L
System and method for ensuring accurate reimbursement for travel expenses
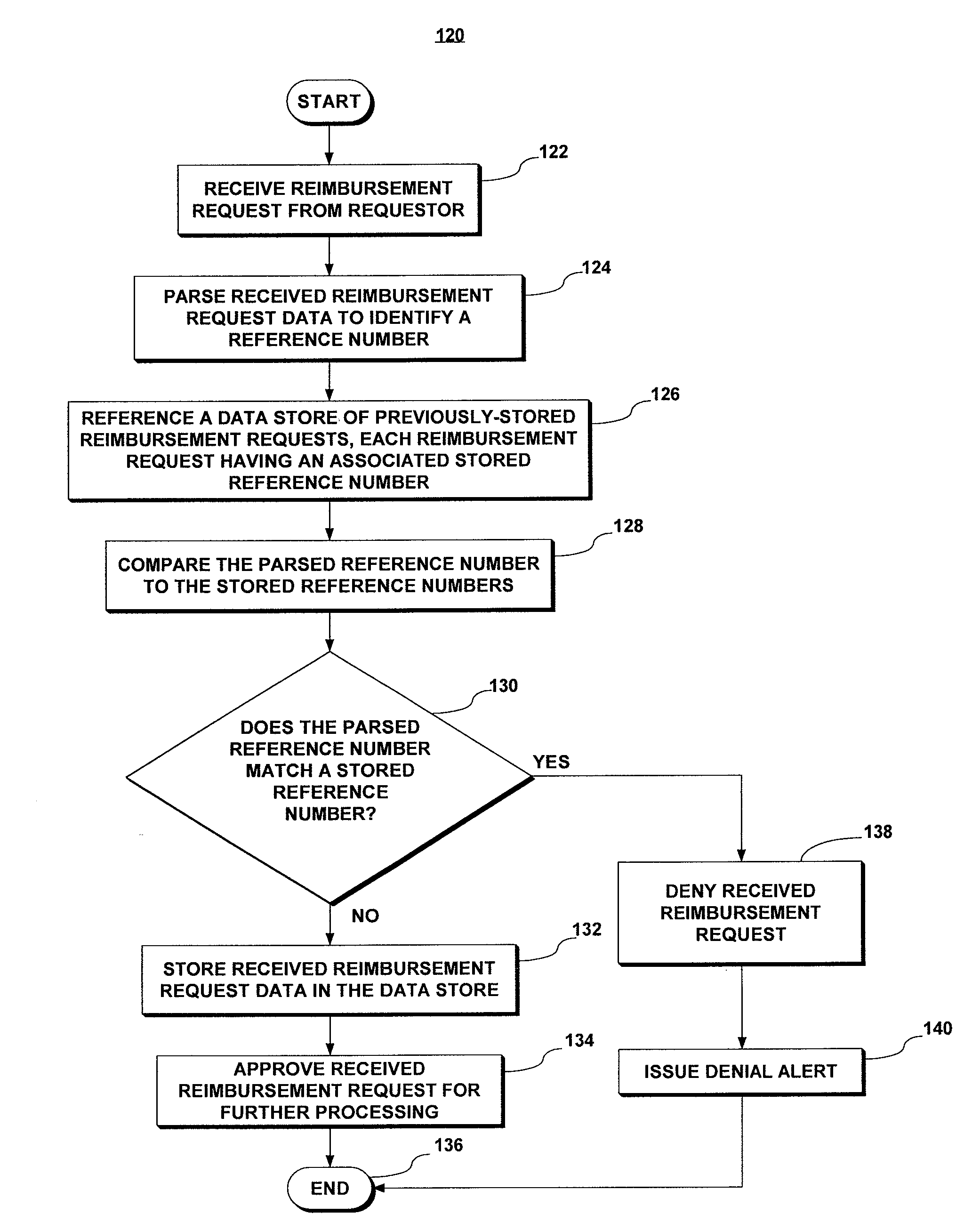
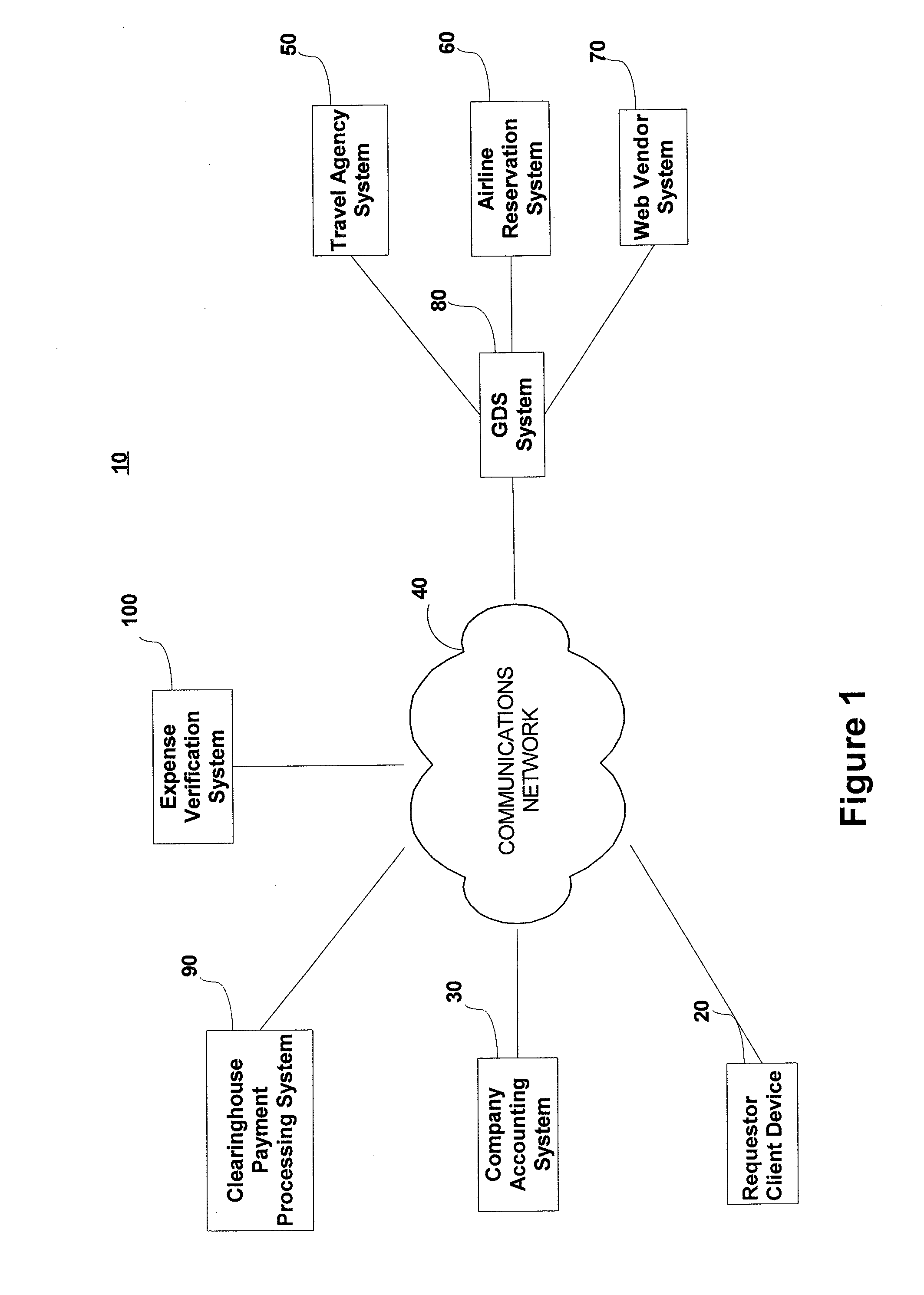
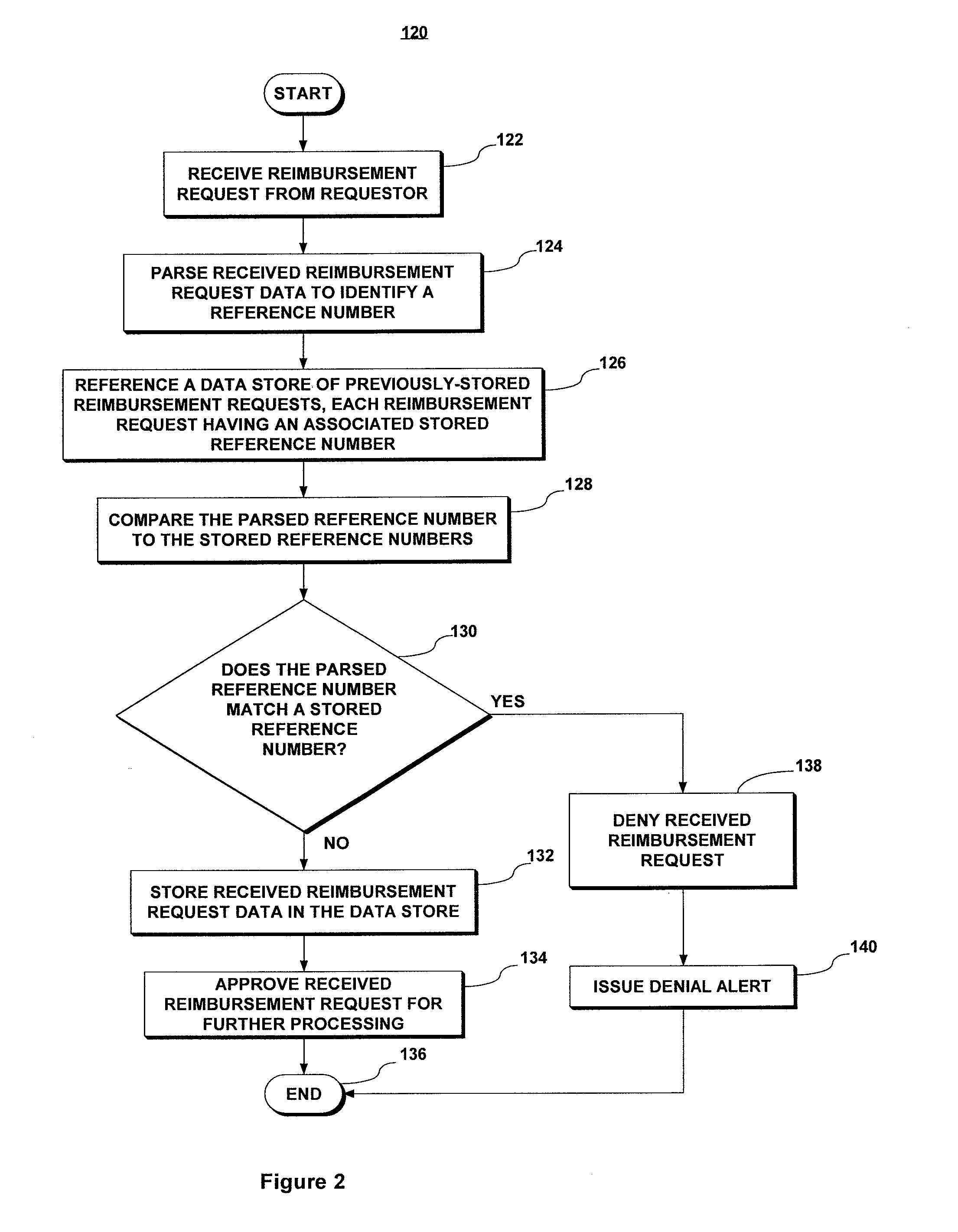
InactiveUS20120209640A1Accurate reimbursementAccurate travelComplete banking machinesFinanceNon complianceData source
An Expense Verification System (EVS) checks for fraud / errors in reimbursement requests. The EVS stores rules for reimbursement in accordance with company policies. The EVS receives travel reservation records for auditing, parses the records to identify a reference number, and then obtains from a trusted source travel record data for a corresponding reference number. Trusted data is compared to company policy-specific rules to determine compliance. In one embodiment, an extracted fare basis identifier is compared to lists of permitted and / or prohibited fare basis codes in the rules to determine compliance. In another embodiment, data is extracted from acknowledgment receipt records from a trusted data source and extracted booking and travel dates are compared to the rules to determine compliance. The EVS issues an alert in the event of non-compliance.
Owner:BIZ TRAVEL SOLUTIONS
Method of managing a wellness programme and a system therefor
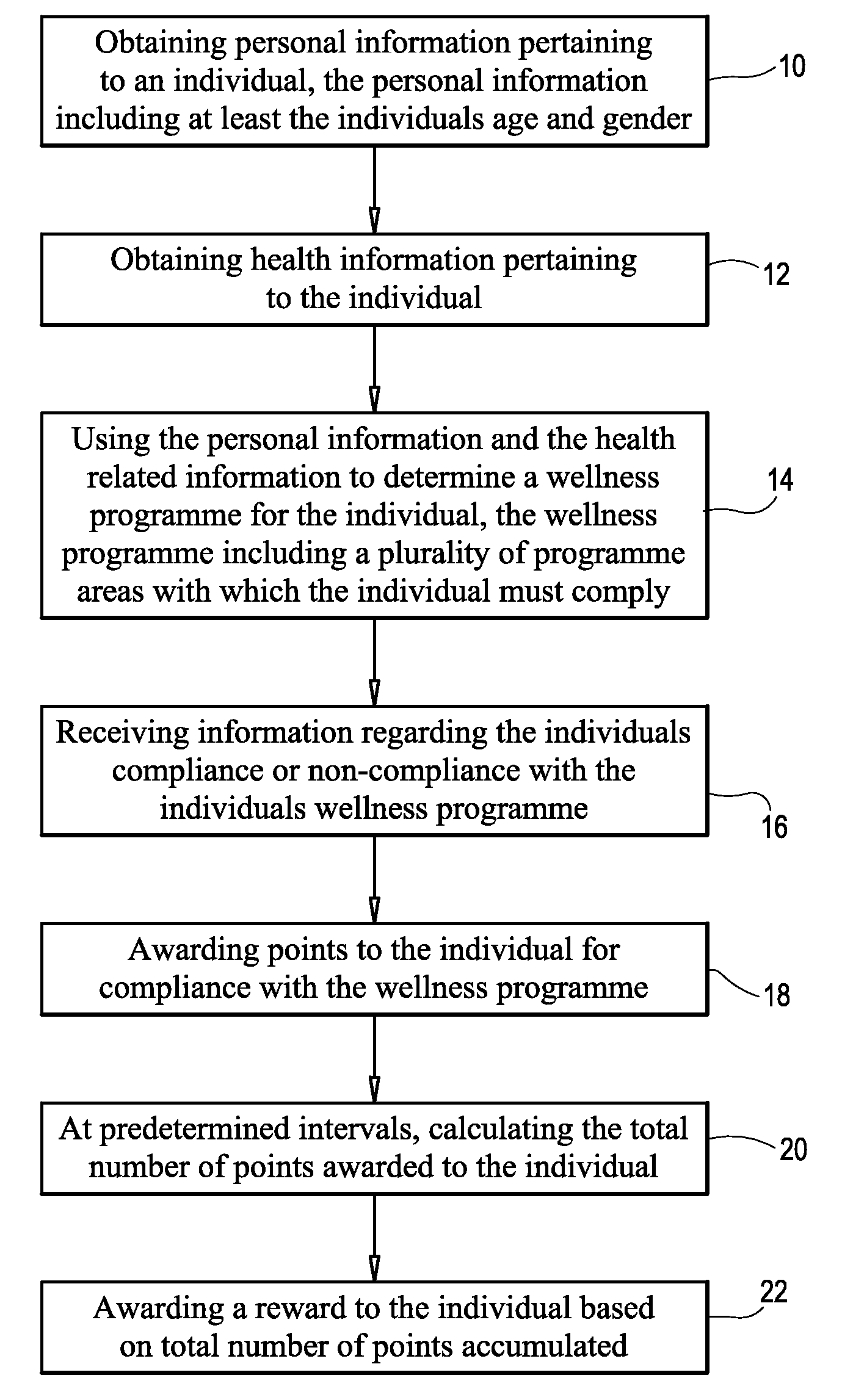
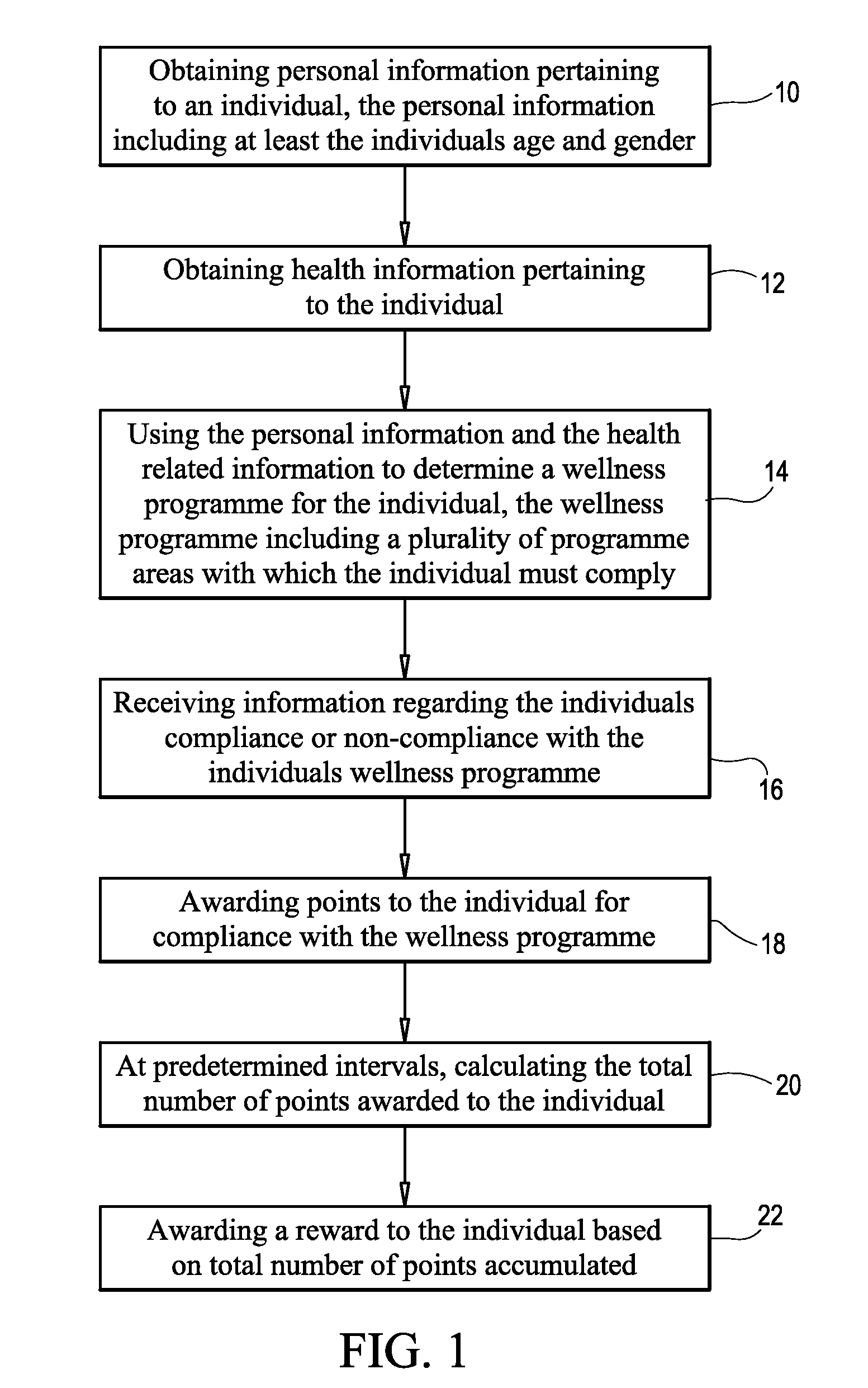
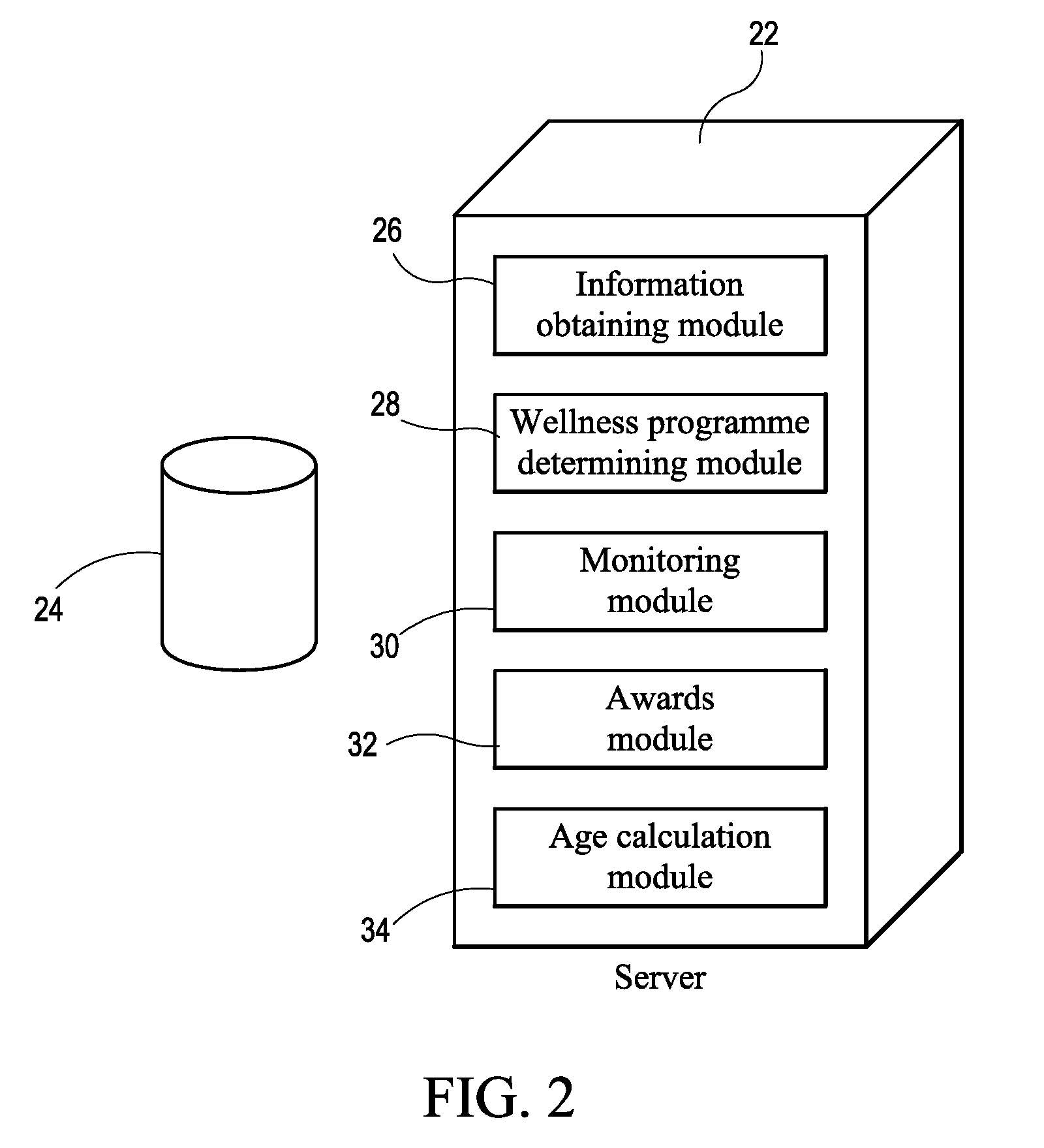
InactiveUS20090265183A1Lower cholesterol levelsStop smokingFinanceHealth-index calculationAge and genderNon compliance
A method and system for managing a wellness programme includes obtaining personal information pertaining to an individual, the personal information including at least the individual's age and gender. In addition, health information pertaining to the individual is obtained. The health information typically includes at least one of exercise, diet, smoking, blood pressure, cholesterol and weight. The personal information and the health information are then used to determine a wellness programme for the individual, the wellness programme including a plurality of programme areas with which the individual must comply. Information is then received regarding the individual's compliance or non-compliance with the individual's wellness programme and points are awarded to the individual for compliance with the wellness programme. At predetermined intervals the total number of points awarded to the individual are calculated and a reward is awarded to the individual based on the total number of points accumulated.
Owner:DISCOVERY HOLDING COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com