Patents
Literature
894 results about "Sleep time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
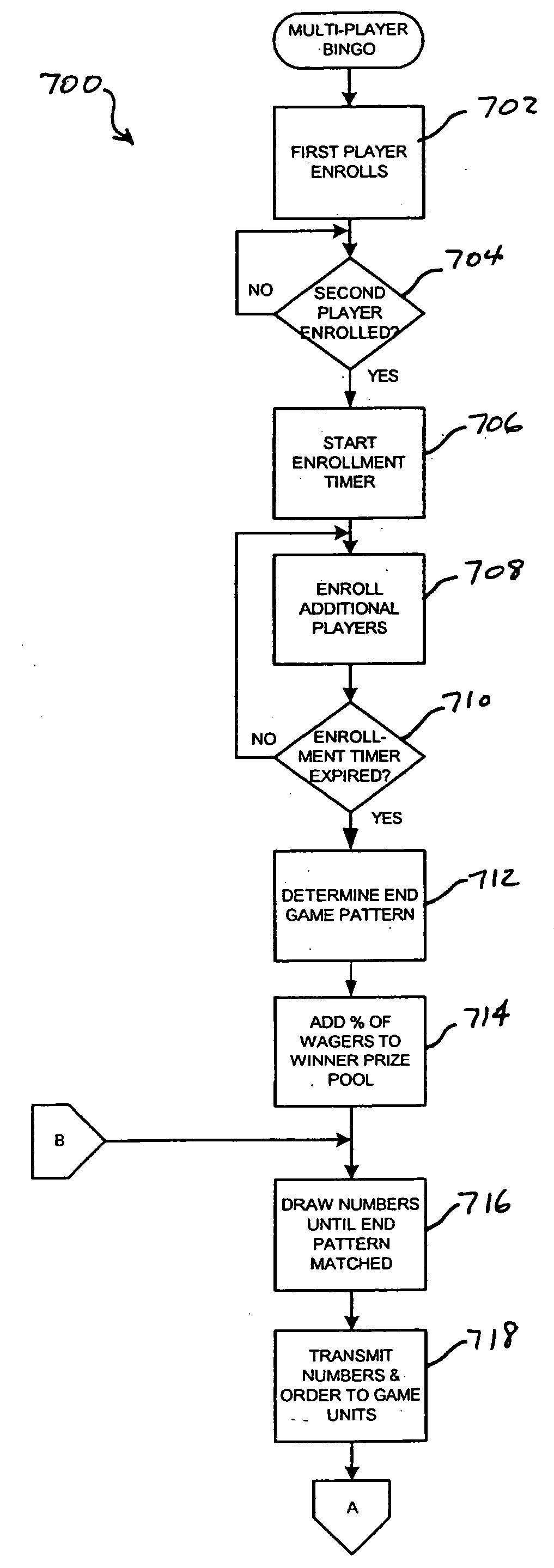
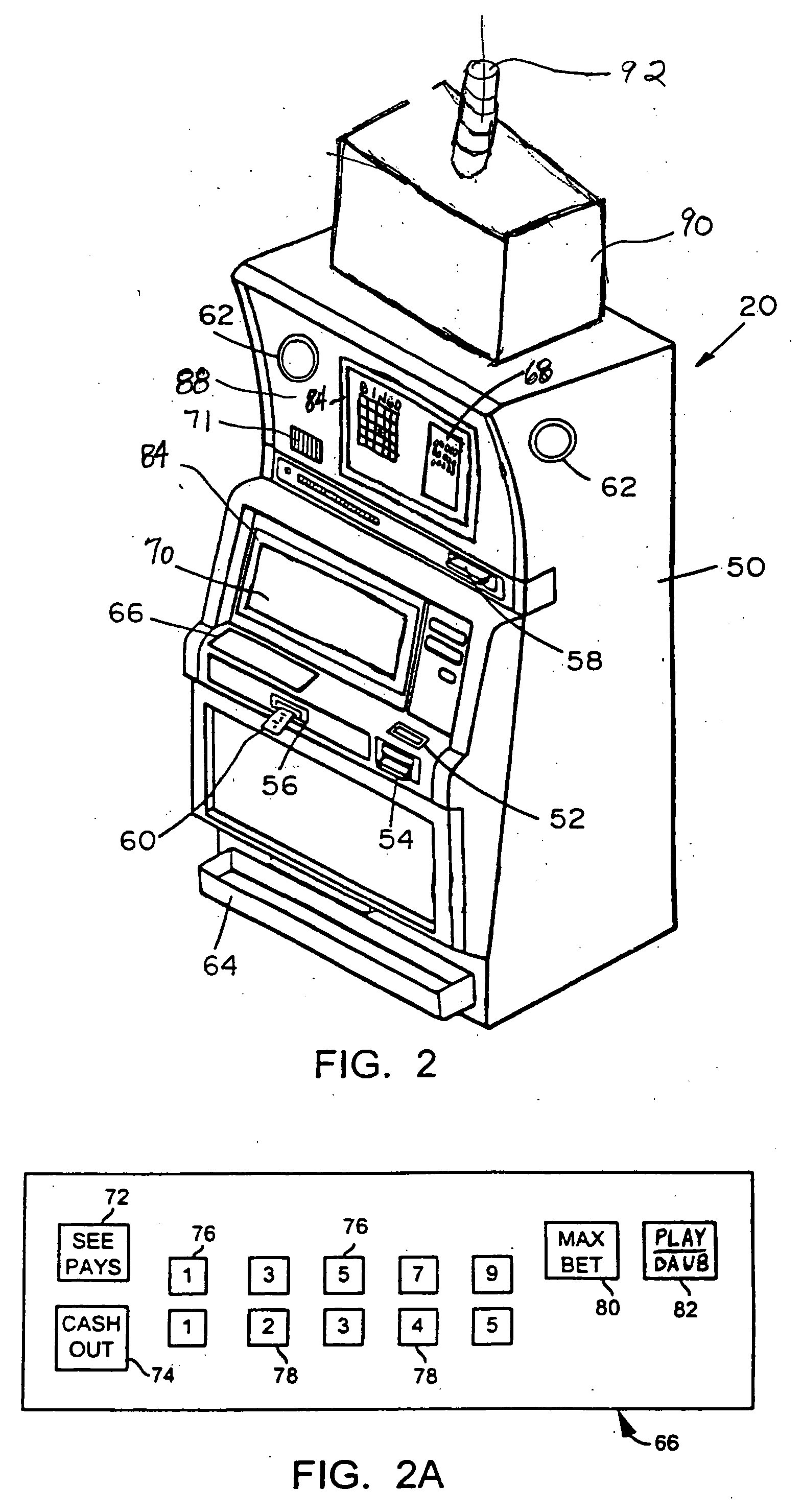
Multi-player bingo with slept awards reverting to progressive jackpot pool
The invention is directed to methods and gaming units for conducting a wagering game and an associated progressive jackpot, wherein each player has a unique game array of game indicia for the occurrence of the wagering game and individual game indicia are sequentially selected from a range of available game indicia. Players may win the wagering game, interim pattern awards and / or progressive jackpot awards by matching predetermined patterns with patterns formed on their unique game array with indicia matching selected indicia. The players may sleep interim pattern awards and progressive jackpot awards by failing to claim the awards by acknowledging the awards at the gaming unit within a finite sleep time period. The slept interim pattern awards and slept progressive jackpot awards may be added to a progressive jackpot pool.
Owner:IGT
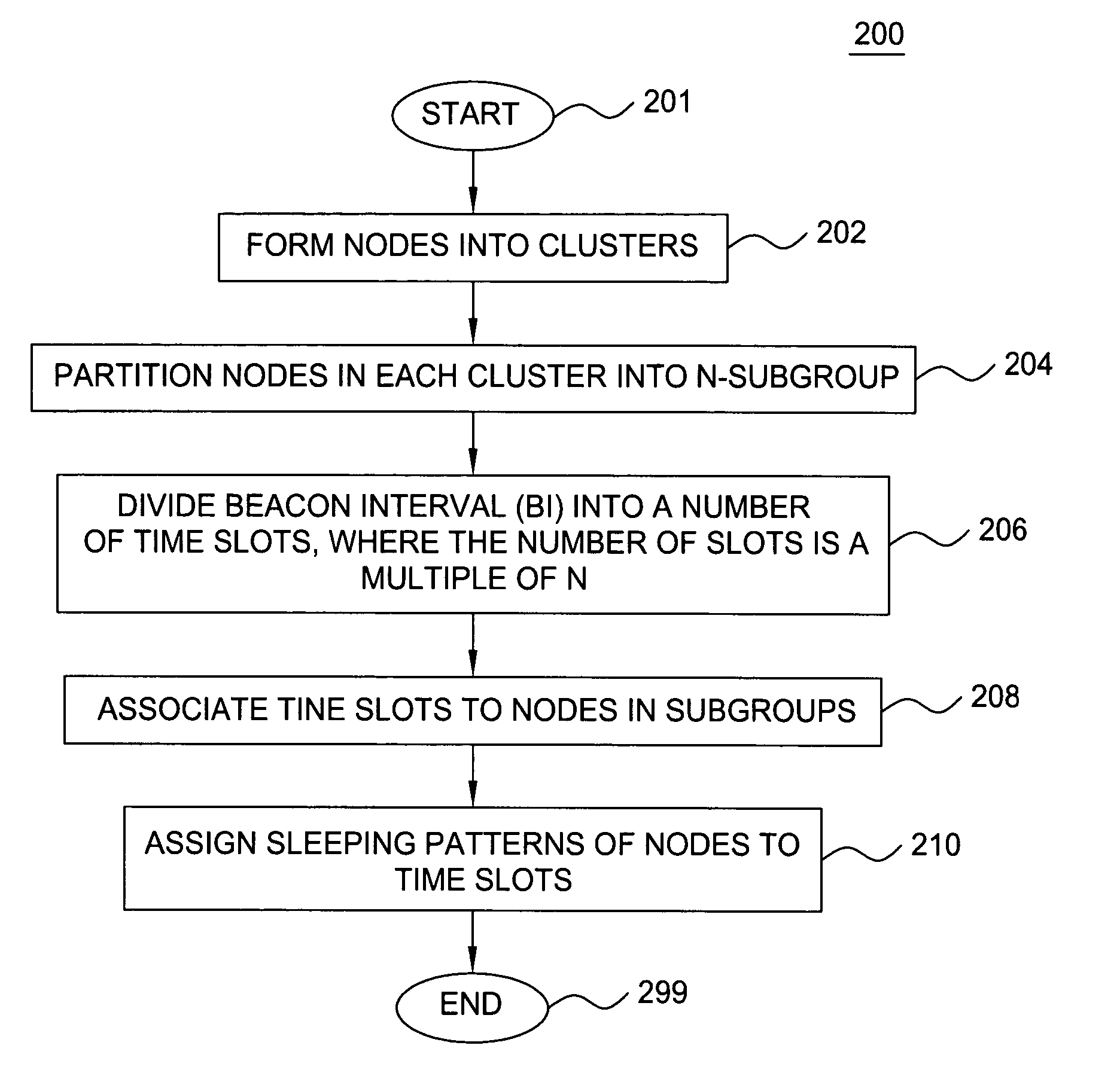
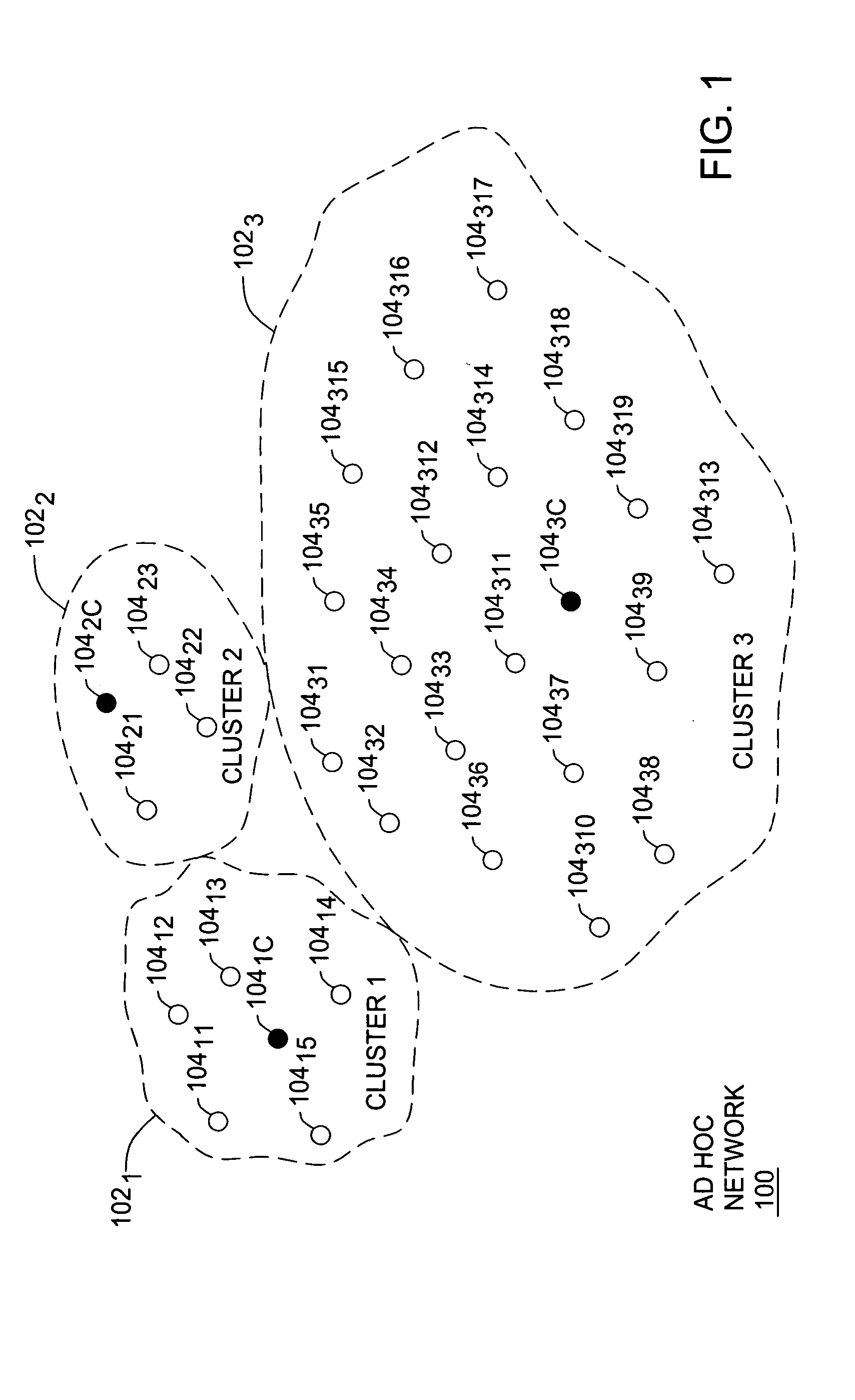
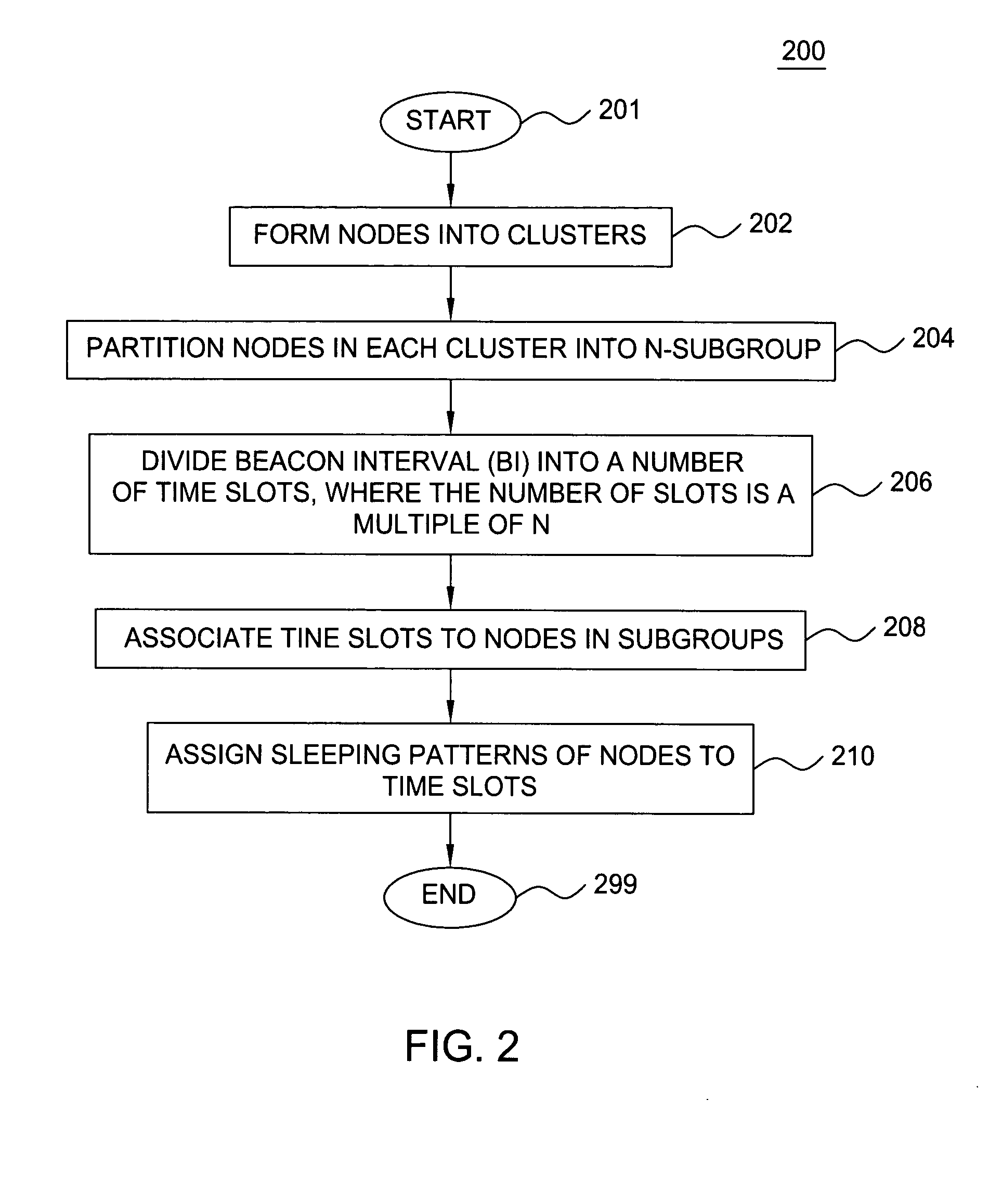
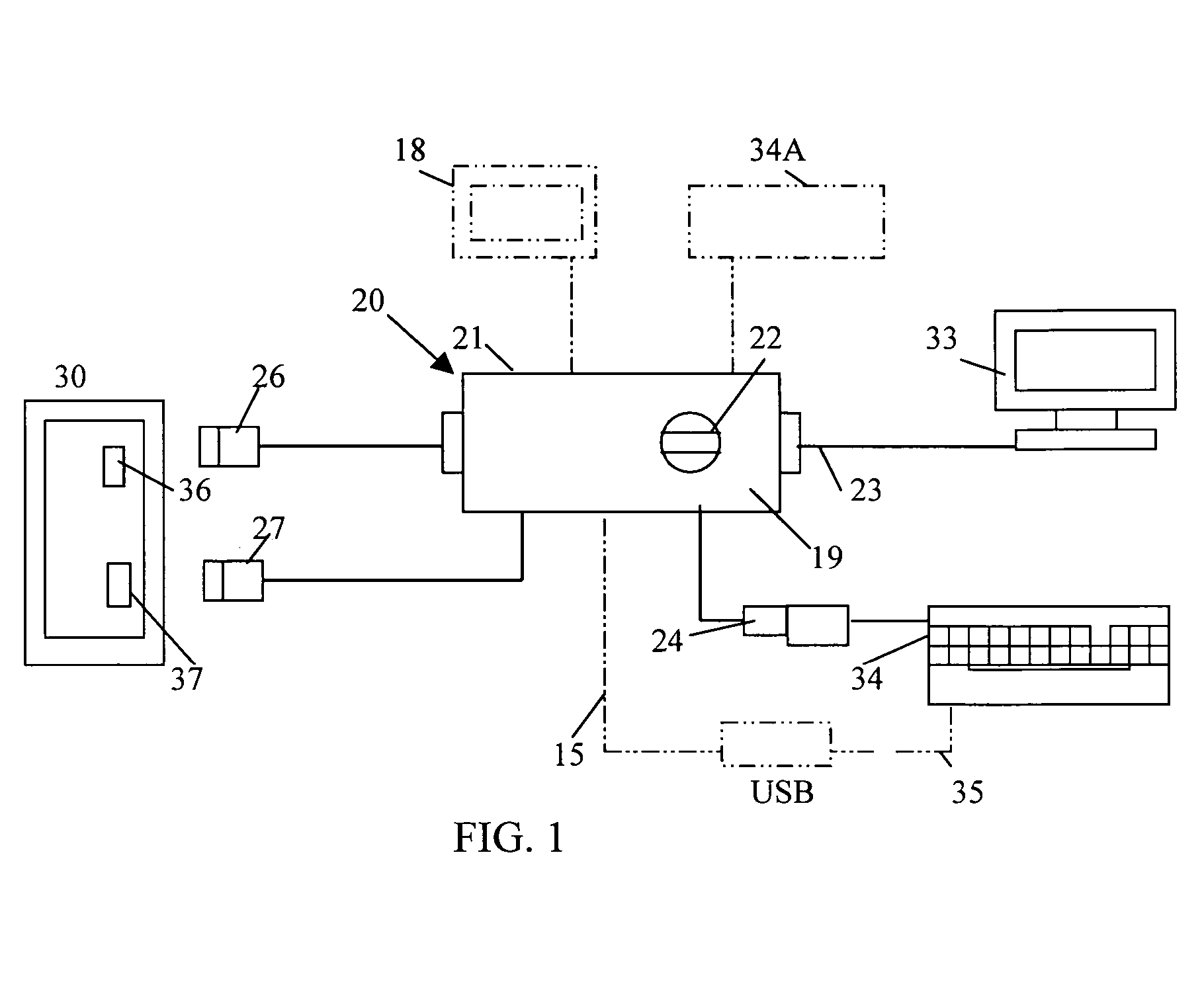
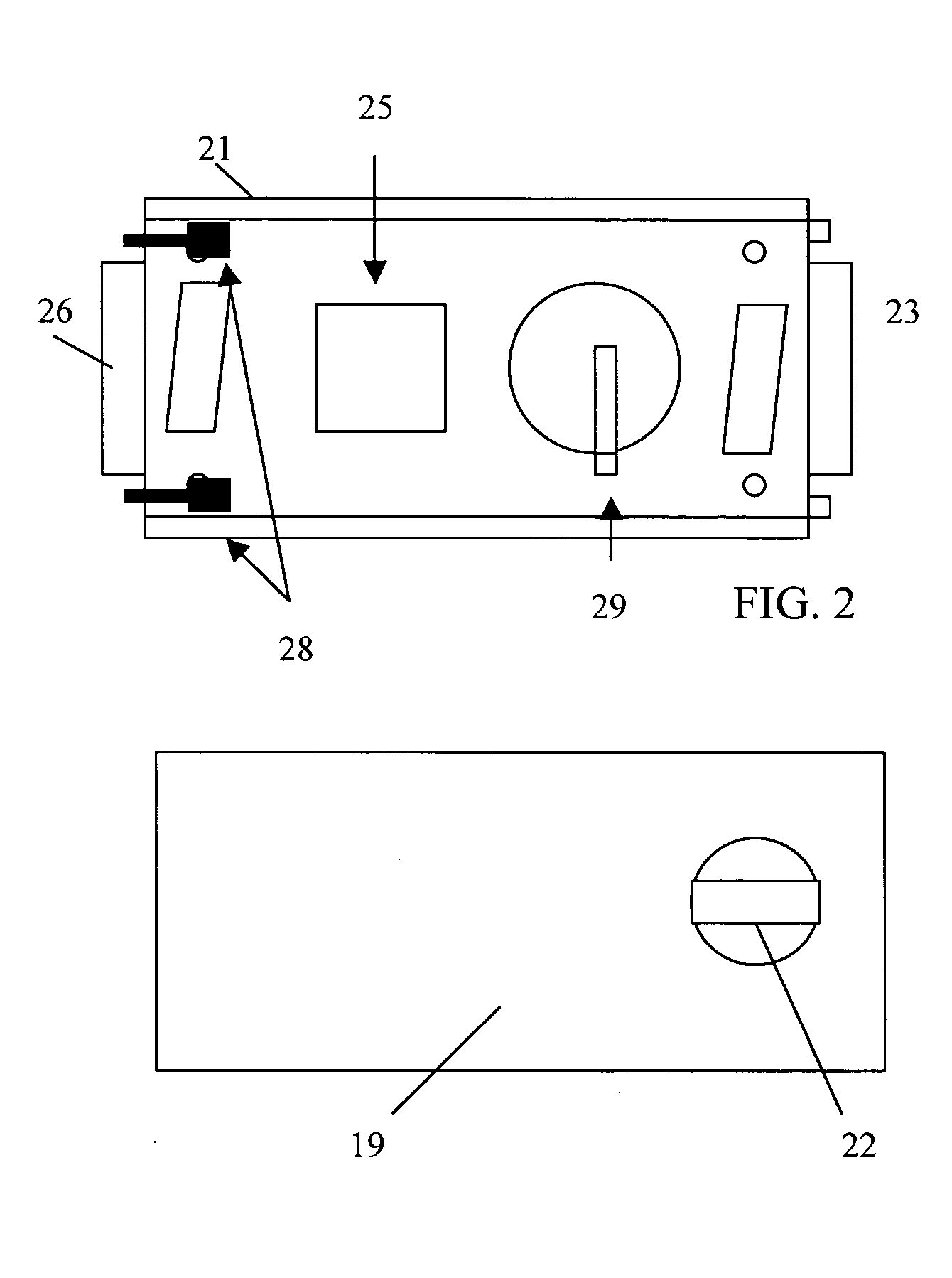
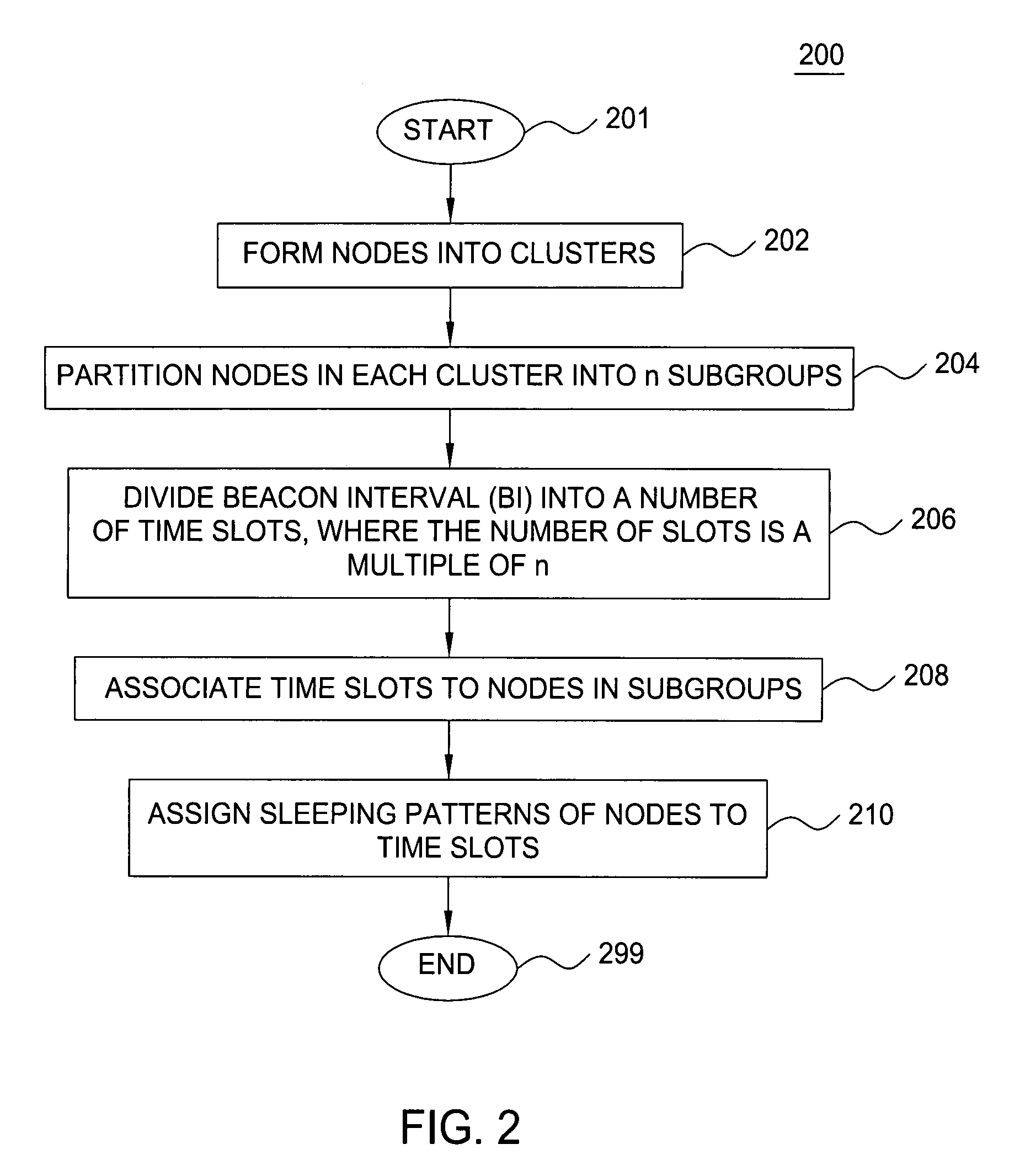
Clustering based load adaptive sleeping protocol for ad hoc networks
InactiveUS20050117530A1Sleep longerNeed to synchronizePower managementSynchronisation arrangementSleep patternsBiological activation
A clustering based load adaptive sleeping protocol for ad hoc networks includes a plurality of nodes forming a cluster, where the nodes in the cluster are partitioned into n groups. This partitioning is performed based on the node ID (e.g. node_id modulo n). The cluster head transmits a beacon at fixed intervals. The beacon interval is divided into N slots, where N is a multiple of n. Node sleep / activation times are synchronized to the beacon interval slots. The node's group number is used to determine the slots within a beacon interval that a node begins it s sleep cycle. Therefore, no additional signaling is required between nodes to indicate sleep patterns. The sleeping time of each node may be increased when extended periods of inactivity are detected according to an adaptive procedure.
Owner:ALCATEL-LUCENT USA INC +1
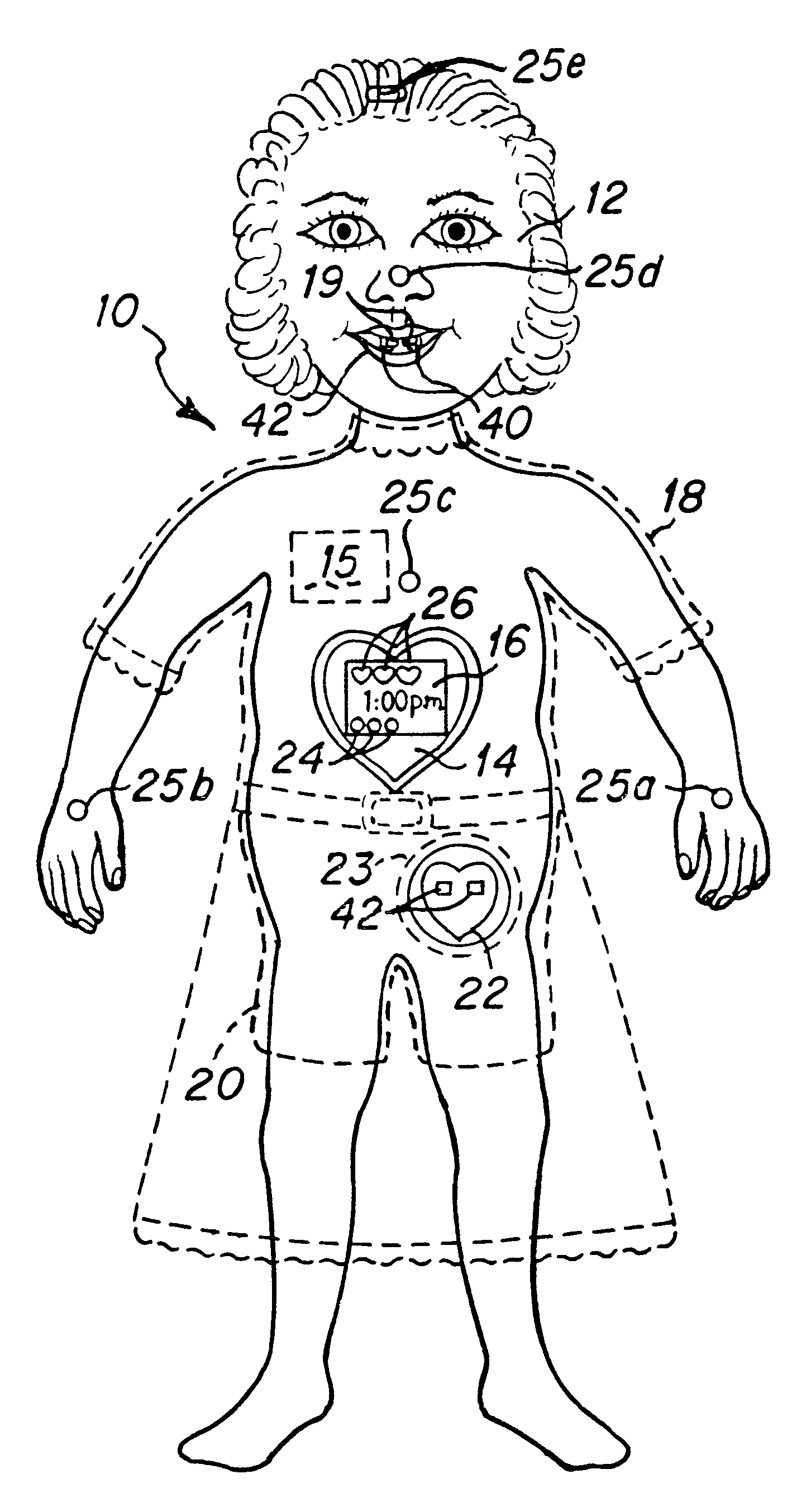
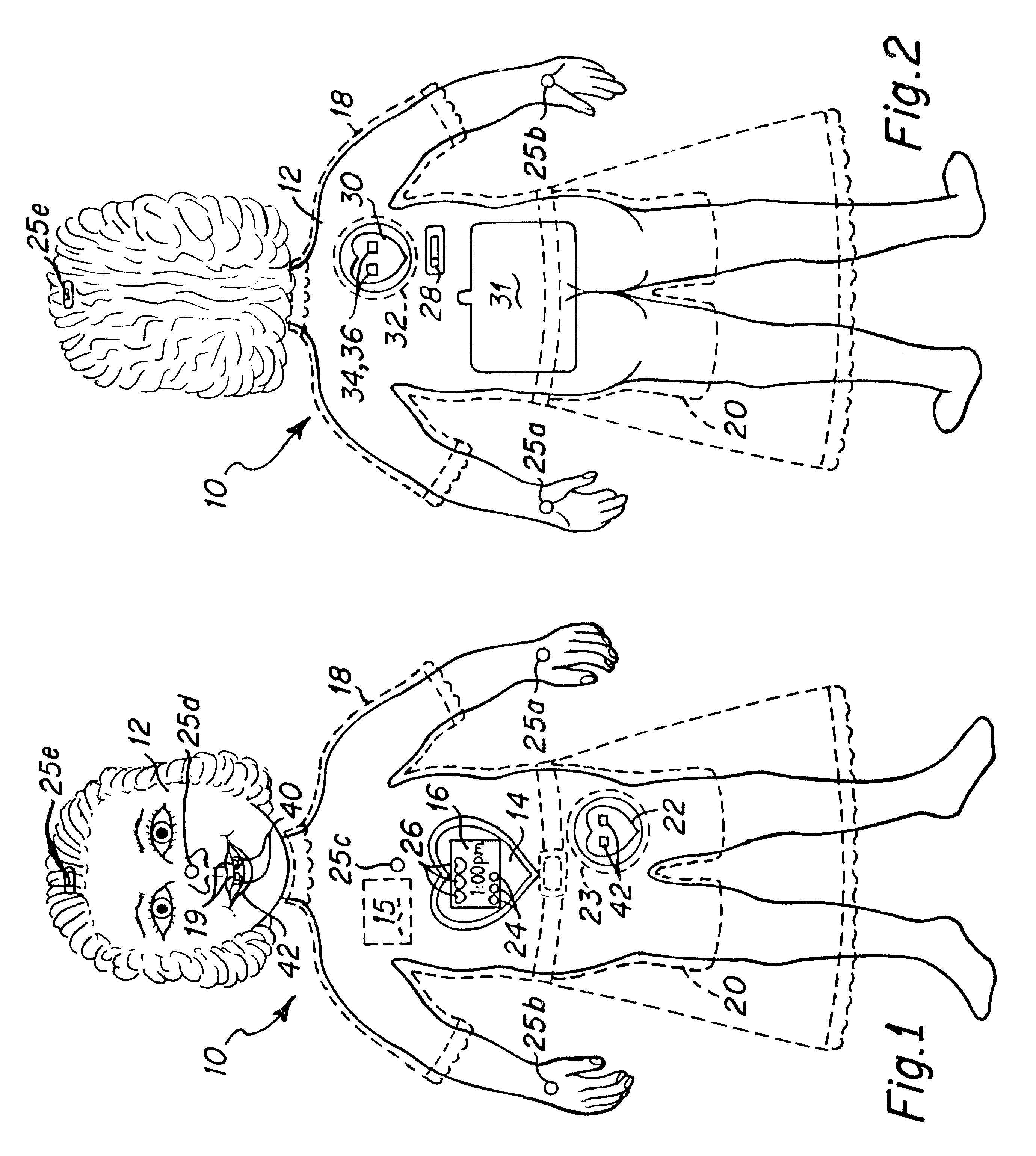
Interactive virtual character doll
The interactive doll simulates the character of a live person or, in other embodiments a fantasy figure or animal, in essence, simulating a living being that possesses respective human or animal qualities: displaying specific needs, tenderness, intelligence and / or understanding. The doll contains a clock or other timekeeping device and thereby knows of the time of day. It automatically enters a sleep mode at a preset sleep time during which the playtoy remains quiet, and wakens at a preset hour of the day, issuing a verbal statement to let the player know it is time to again play. By issuing a sequence of verbal requests from time to time to the player to take action of various kinds on or with the doll, determines the player's compliance or noncompliance with each such request and issues a verbal message appropriate to such compliance or non-compliance. Some of the verbal requests made are of a kind that occur at a particular time of day in the life of the character being synthesized, such as a request for a food or beverage at breakfast time, lunch time or supper time. And, from time to time at its own initiative, the playtoy may issue verbal messages of affection to the player. That doll is accompanied by external objects that simulate a variety of foods, a beverage, medicine and the like, which the doll is to be applied by the player to the doll pursuant to specific verbal requests from the doll and the doll is able to identify those objects for enhanced interactive play with the player.
Owner:PLAYMATES TOYS
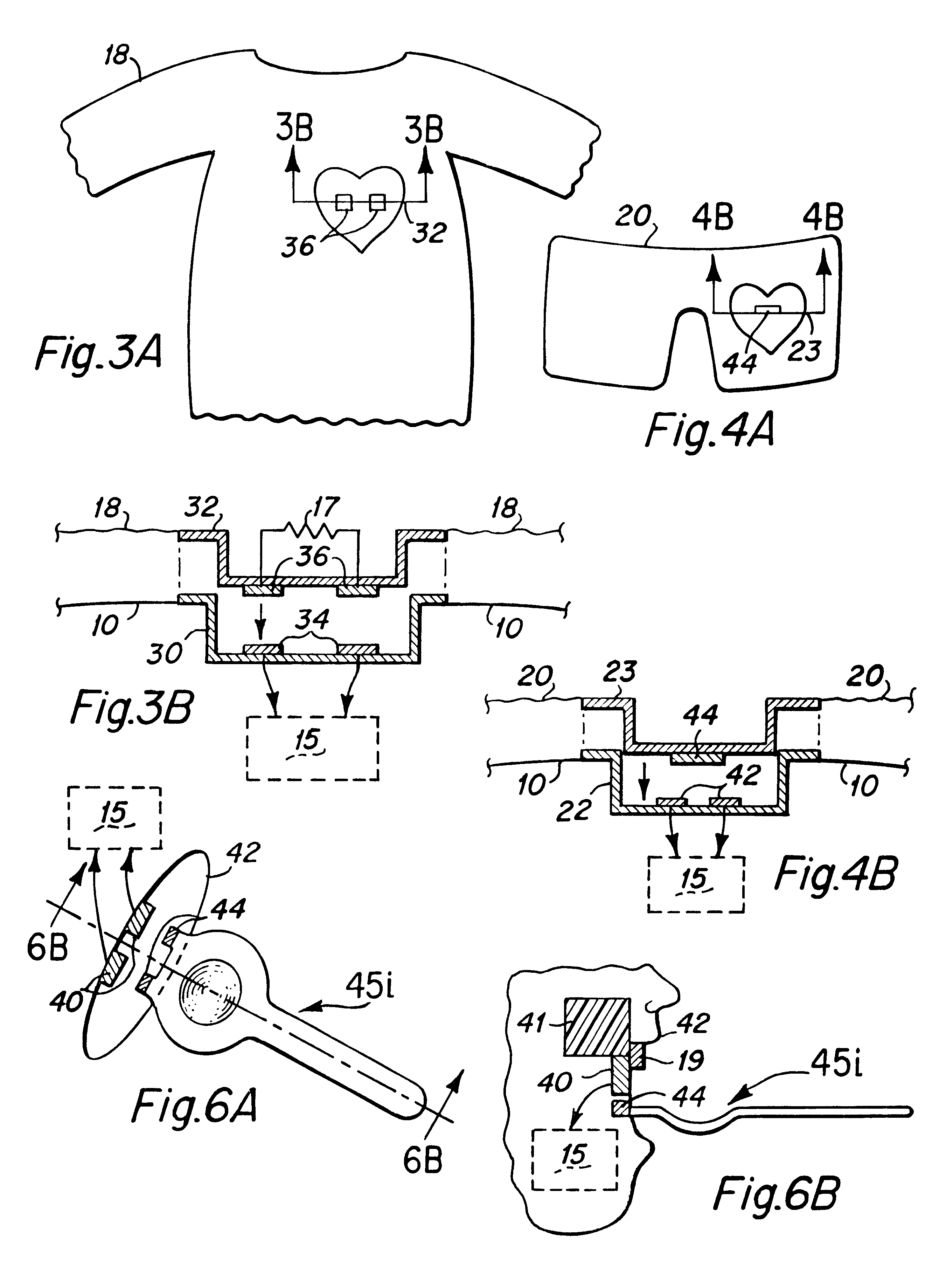
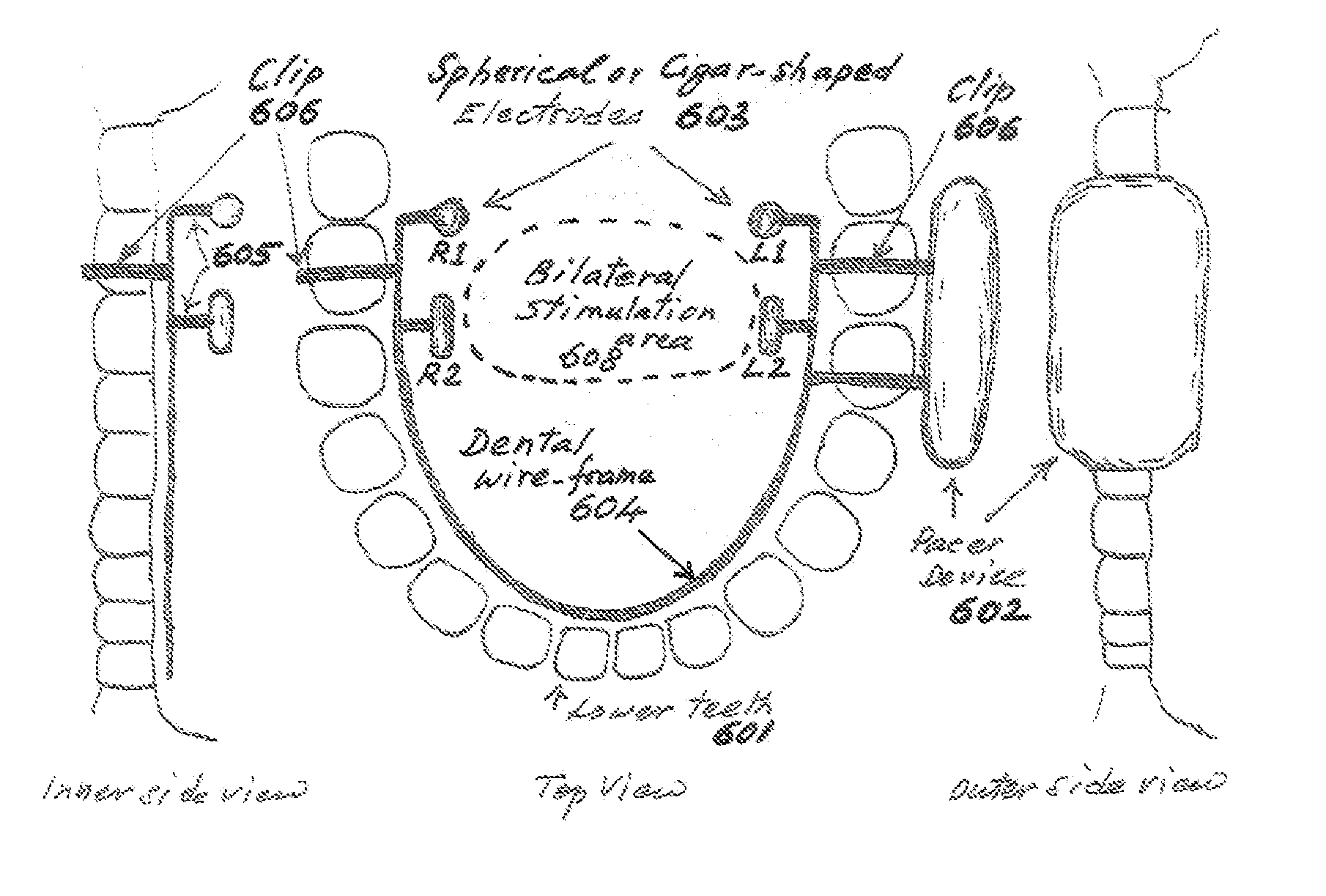
Non-invasive intraoral electrical stimulator system and method for treatment of obstructive sleep apnea (OSA)
InactiveUS20140135868A1Easy to installEasily removable retainerHead electrodesSnoring preventionDilatorClosed loop
A non-invasive, removable intraoral electrical Stimulator or Pacemaker system and method is described, for electrically-stimulating and re-establishing the tone in the upper pharyngeal dilator muscle, the genioglossus and base-of-tongue muscles, for the treatment of Obstructive Sleep Apnea (OSA) in human adults and young adults. The Stimulator system consists of an intraoral Stimulator device assembly with a rechargeable battery, an external (inductive) Recharger appliance and an external hand-held (inductive) Programmer appliance. The Stimulator device assembly is inserted into the mouth by the OSA patient before sleep time and is removed when awake or during normal activity and placed in the charging cradle of the Recharger appliance for recharging the device battery. The physician uses the hand-held Programmer appliance to determine and set the patient-specific stimulation therapy parameters in the device, at the patient's initial evaluation. The stimulation therapy is delivered either in an open loop configuration without regard to patient's respiration activity, or in a closed loop configuration synchronized to the patient's respiration detected by one or more sensors in the system.
Owner:BASHYAM JACOB BASHYAM
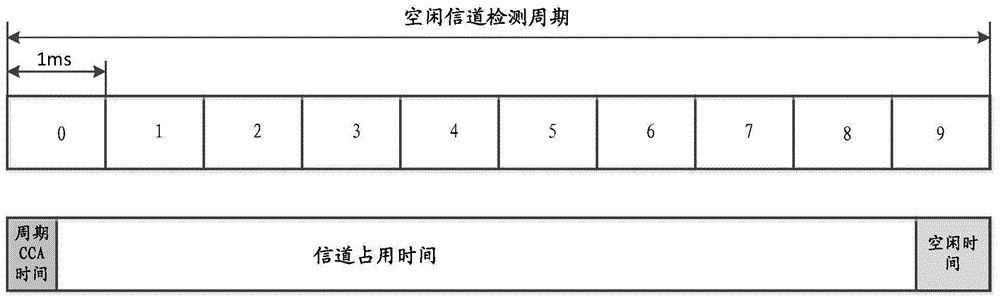
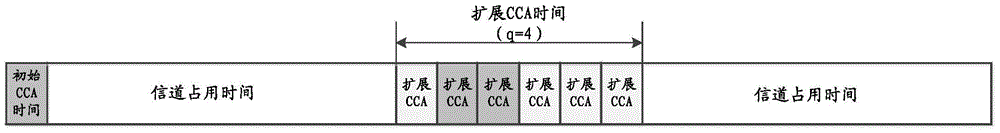
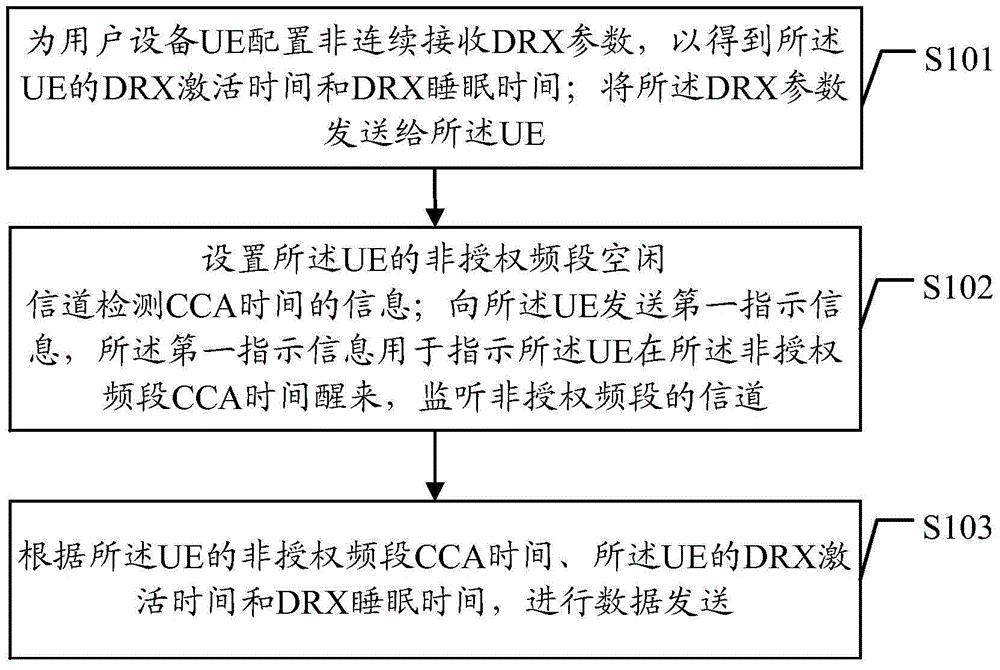
Method and device for using DRX in non-authorized frequency band
ActiveCN104812032AFair shareReduce power consumptionPower managementConnection managementSleep timeIdle channel
The embodiment of the invention discloses a method for using DRX in a non-authorized frequency band. The method comprises the steps of configuring non-continuous received DRX parameters for UE to obtain the DRX activating time and the DRX sleeping time of the UE; sending the DRX parameters to the UE; setting information of CCA detection time of an idle channel of the UE at the non-authorized frequency band; sending the first indication information to the UE to indicate the UE to wake up at the CCA time in the non-authorized frequency band so as to monitor the channel of the non-authorized frequency band; sending the data according to the CCA time of the UE at the non-authorized frequency band, and the DRX activating time and the DRX sleep time of the UE. According to the technical scheme, the method has the advantages that the UE can effectively monitor the channel of the non-authorized frequency band while the power consumption of the UE at the non-authorized frequency band is reduced; the LTE device and the WiFi device can fairly share the resources in the non-authorized frequency band.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
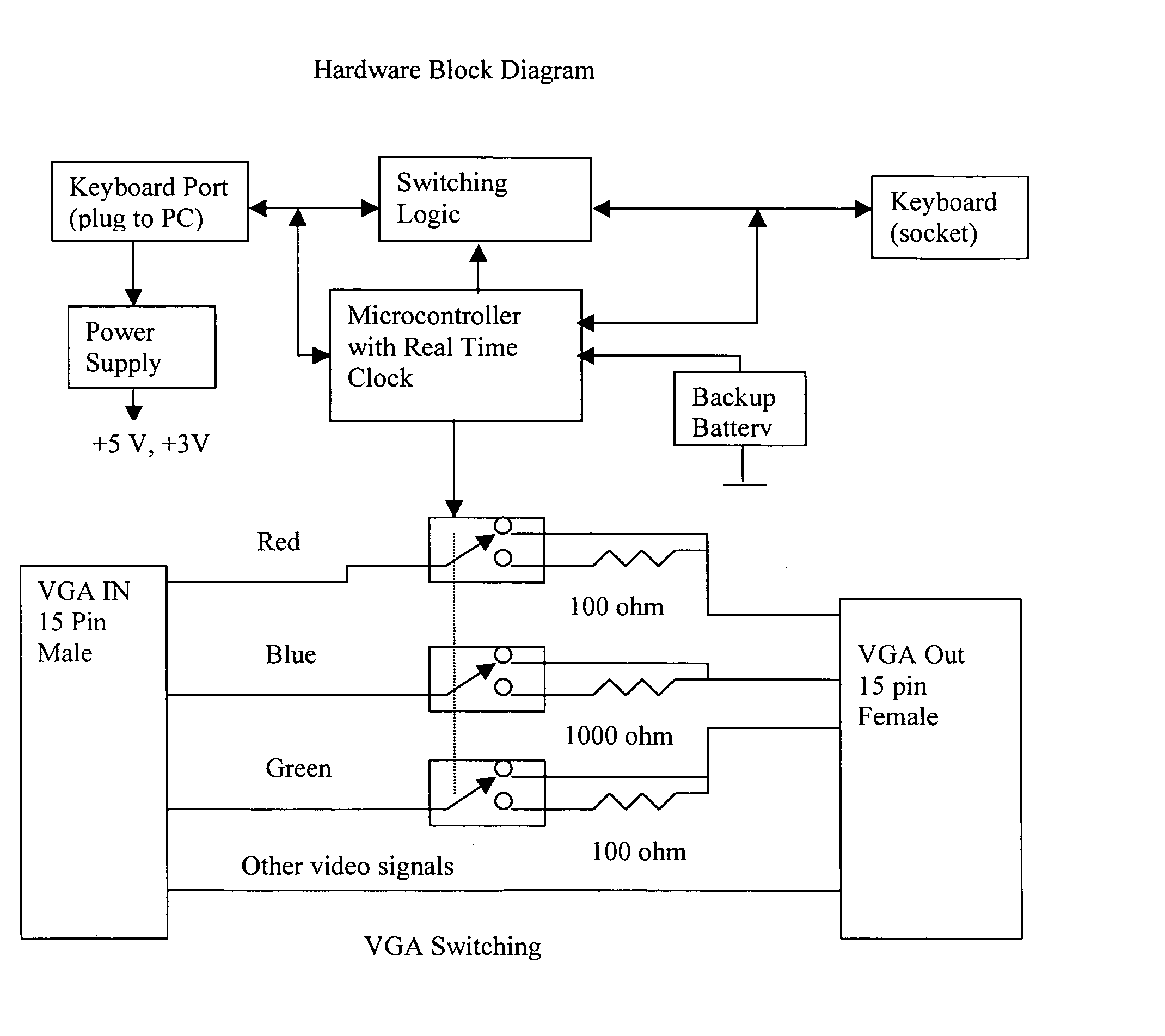
Viewing screen color limiting device and method
InactiveUS20060152525A1Not be hacked, deleted, or overriddenCathode-ray tube indicatorsSleep timeSpecific time
A timed programmable control alters signals between an electronic device and a viewing screen to lower or eliminate a signal for a specific color on the screen at specific times. Eliminating or lowering blue color on the screen allows normal production of melatonin prior to normal sleep times to permit normal sleep cycles. The control may be a microcontroller or simple switch inside a locked box, a video card, or software to control light pixel values in memory, VGA signals, and digital to analog conversions.
Owner:WOOG KENNETH M
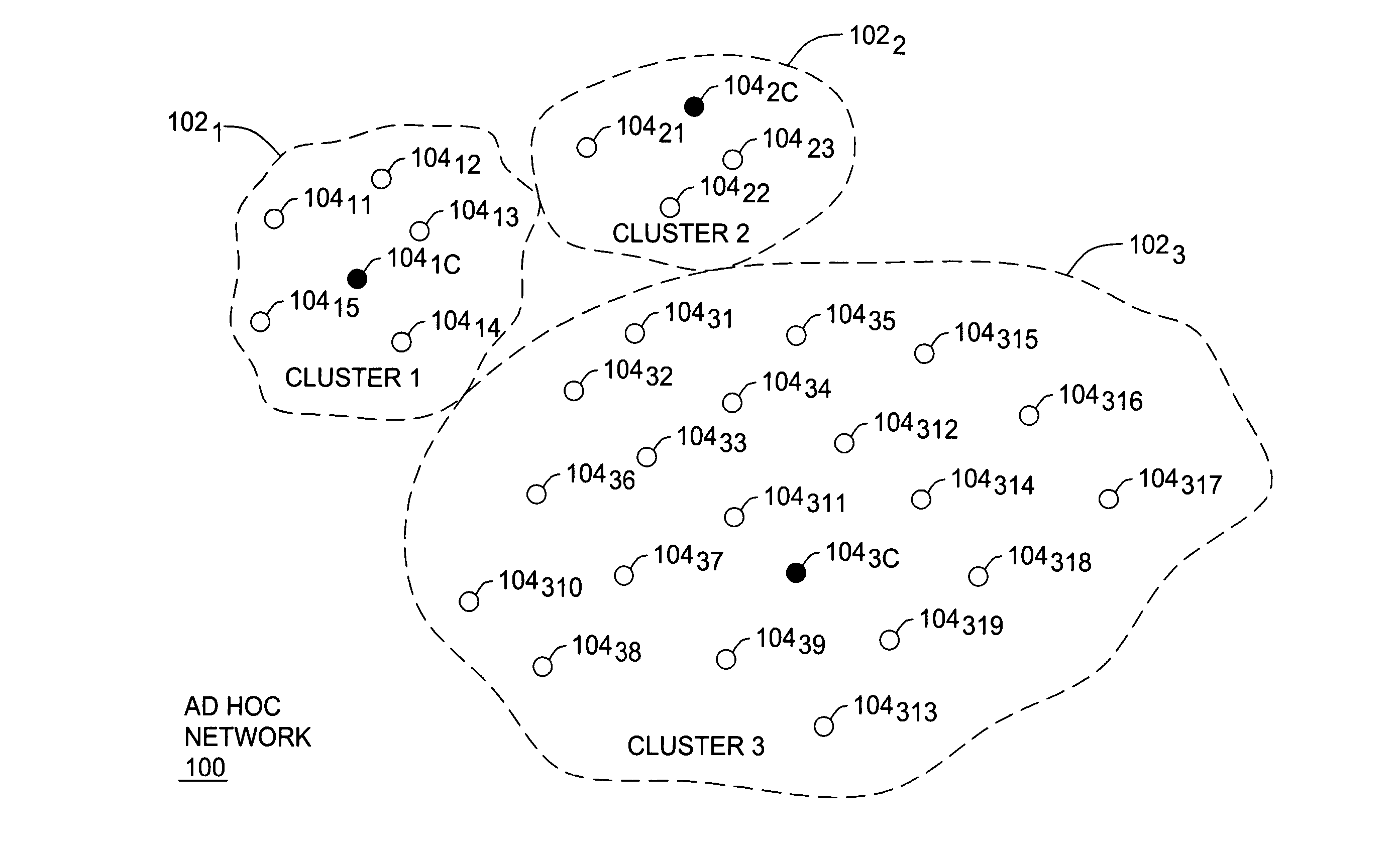
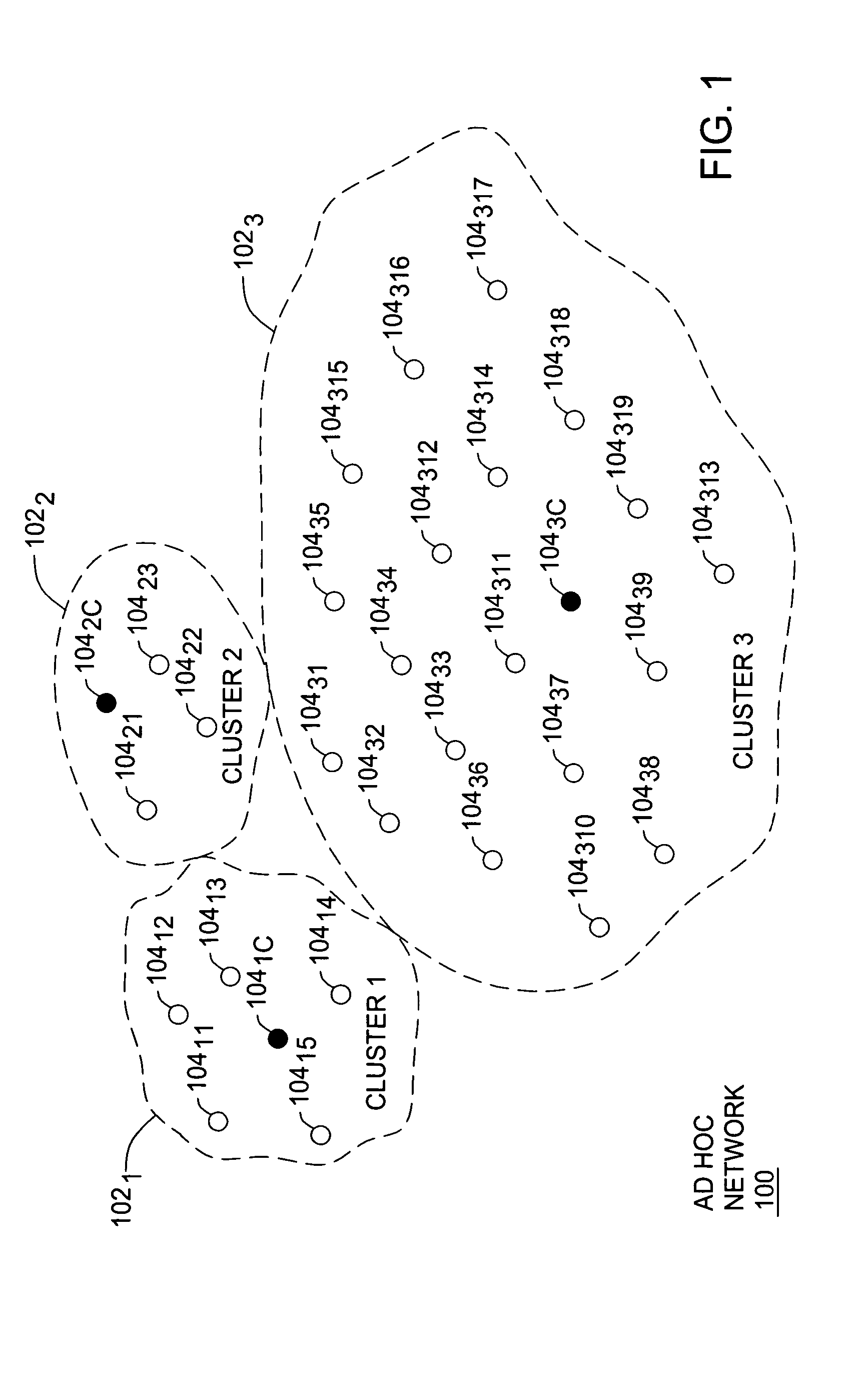
Clustering based load adaptive sleeping protocol for ad hoc networks
InactiveUS7298716B2Sleep longerNeed to synchronizePower managementSynchronisation arrangementSleep timeSleep patterns
A clustering based load adaptive sleeping protocol for ad hoc networks includes a plurality of nodes forming a cluster, where the nodes in the cluster are partitioned into n groups. This partitioning is performed based on the node ID (e.g. node_id modulo n). The cluster head transmits a beacon at fixed intervals. The beacon interval is divided into N slots, where N is a multiple of n. Node sleep / activation times are synchronized to the beacon interval slots. The node's group number is used to determine the slots within a beacon interval that a node begins it s sleep cycle. Therefore, no additional signaling is required between nodes to indicate sleep patterns. The sleeping time of each node may be increased when extended periods of inactivity are detected according to an adaptive procedure.
Owner:ALCATEL-LUCENT USA INC +1
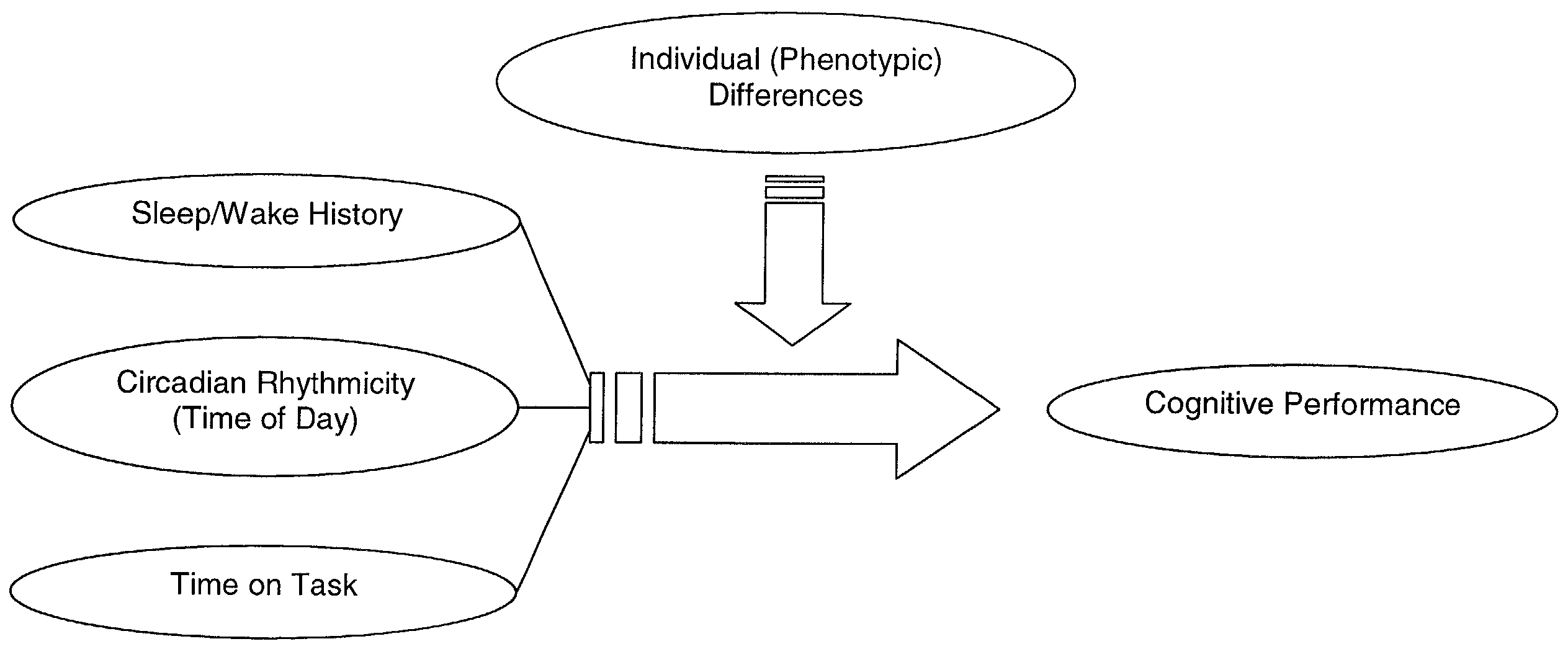
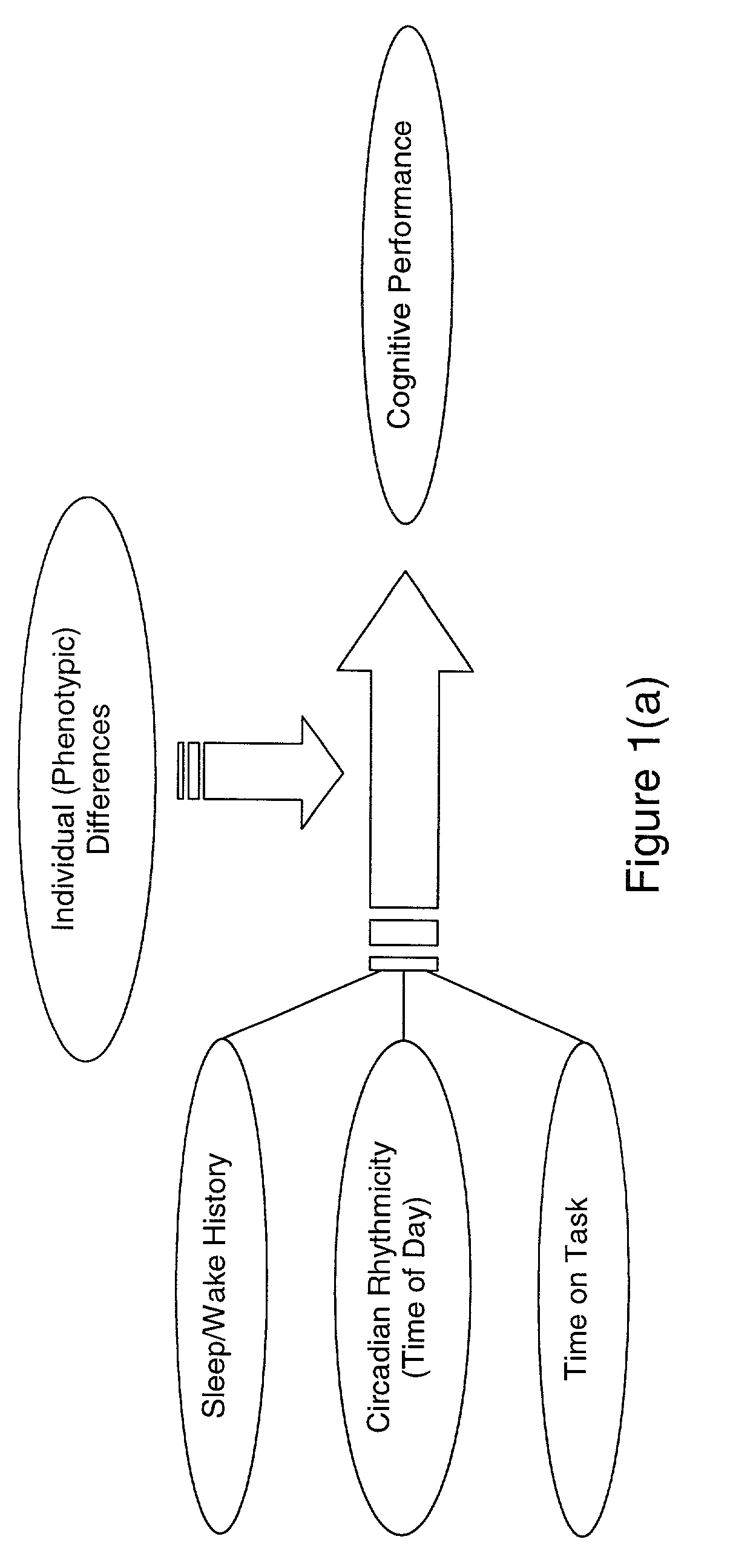
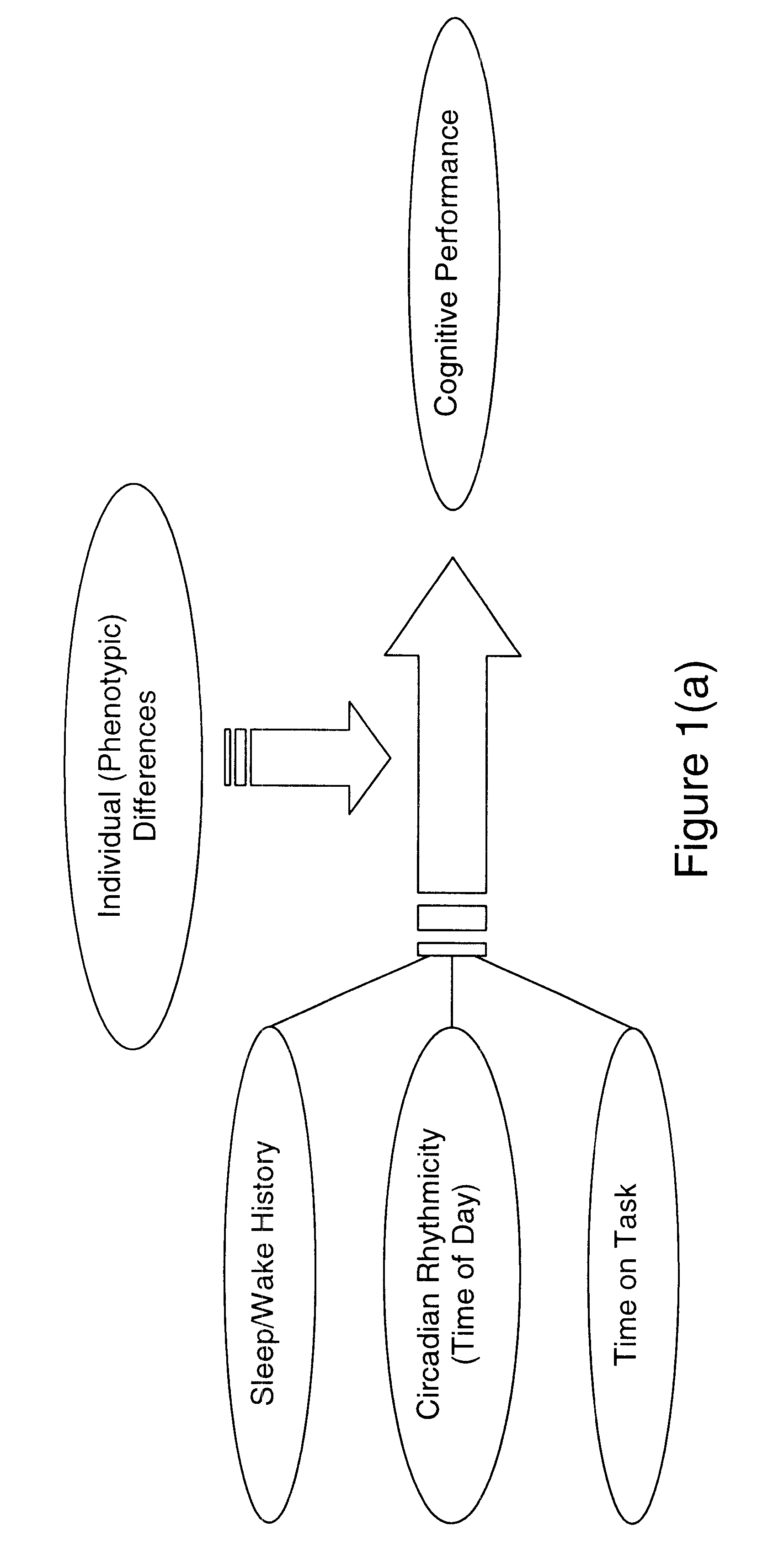
Method for predicting human cognitive performance
Owner:ARMY US SEC THE
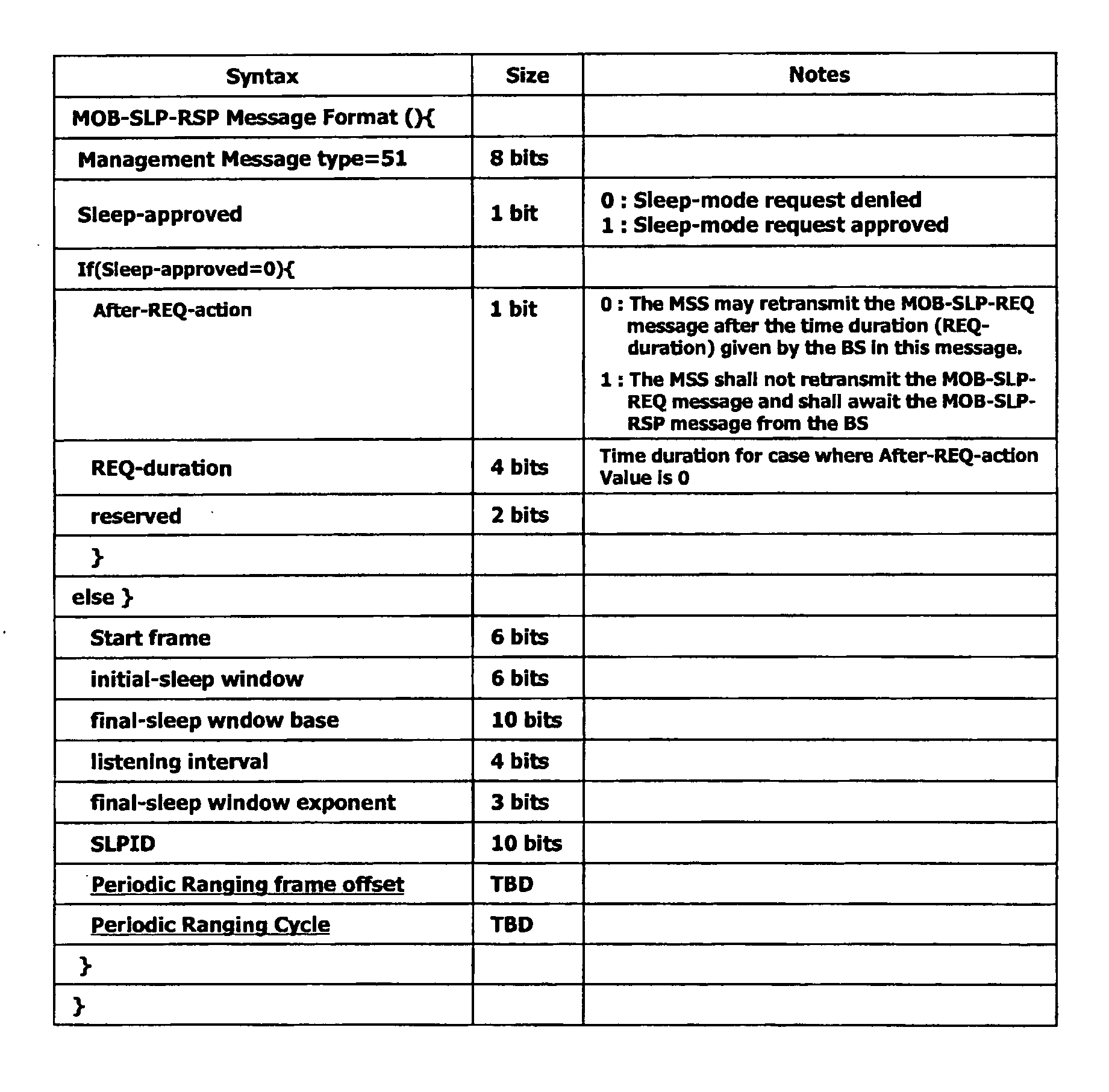
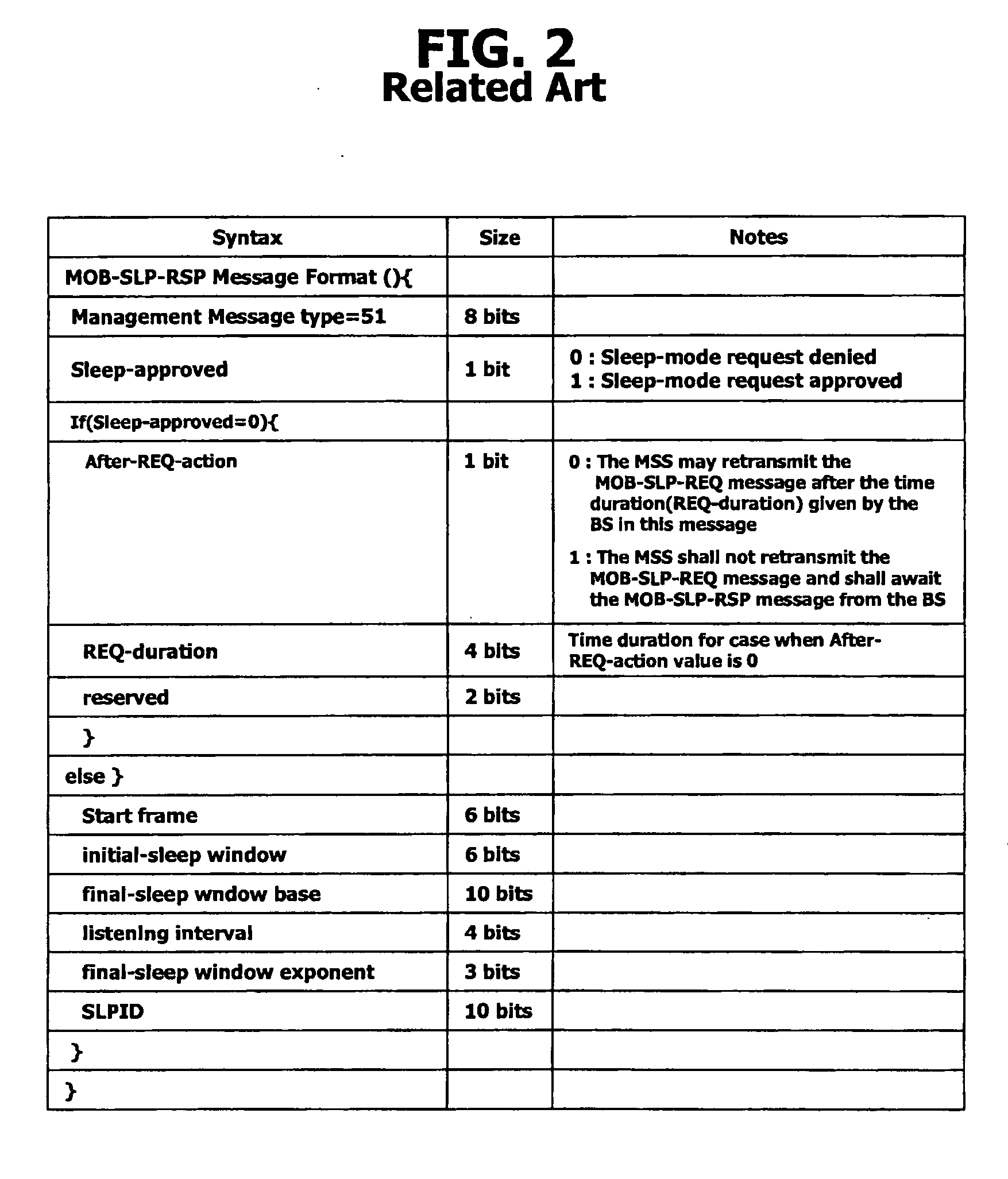
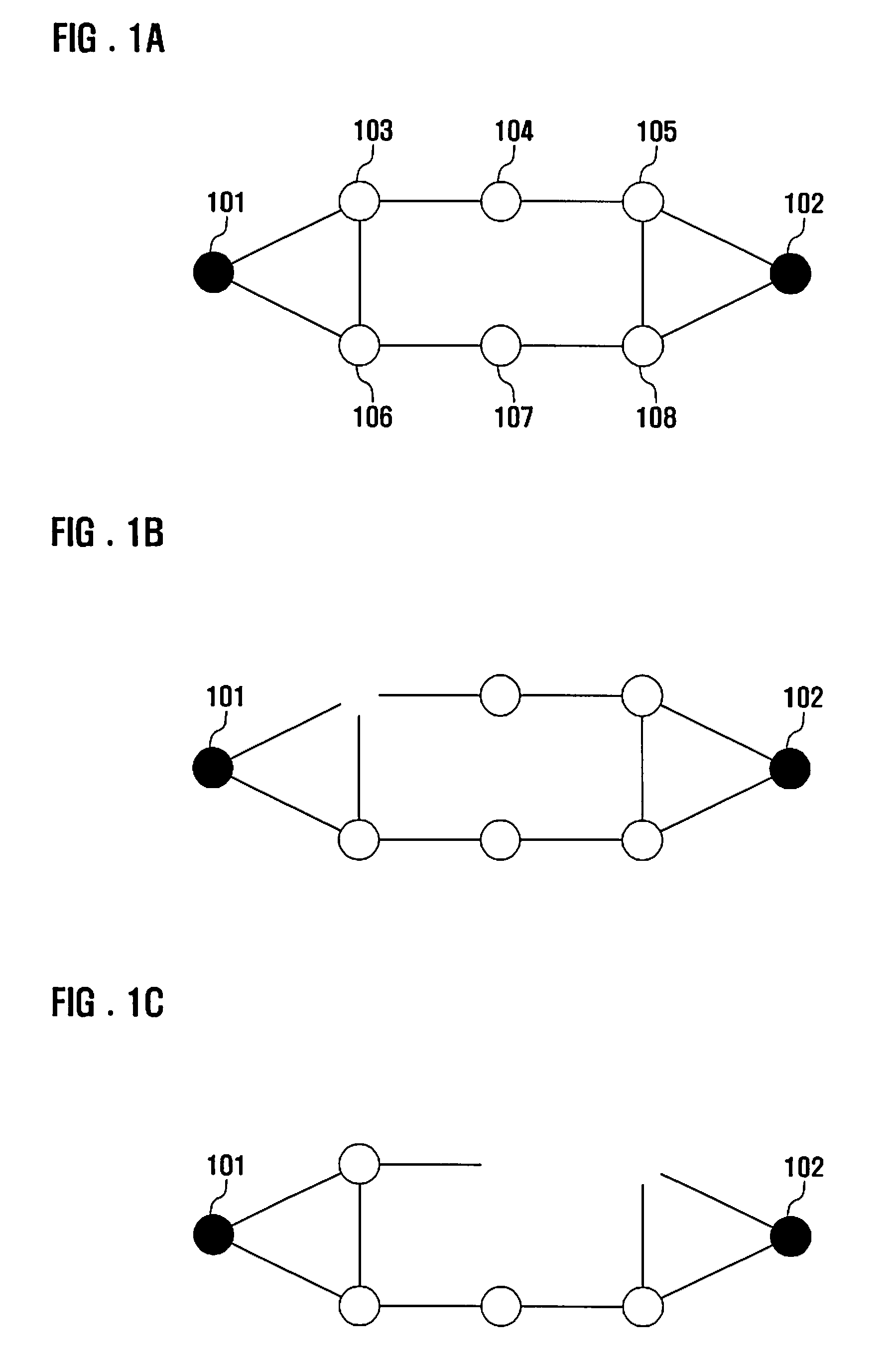
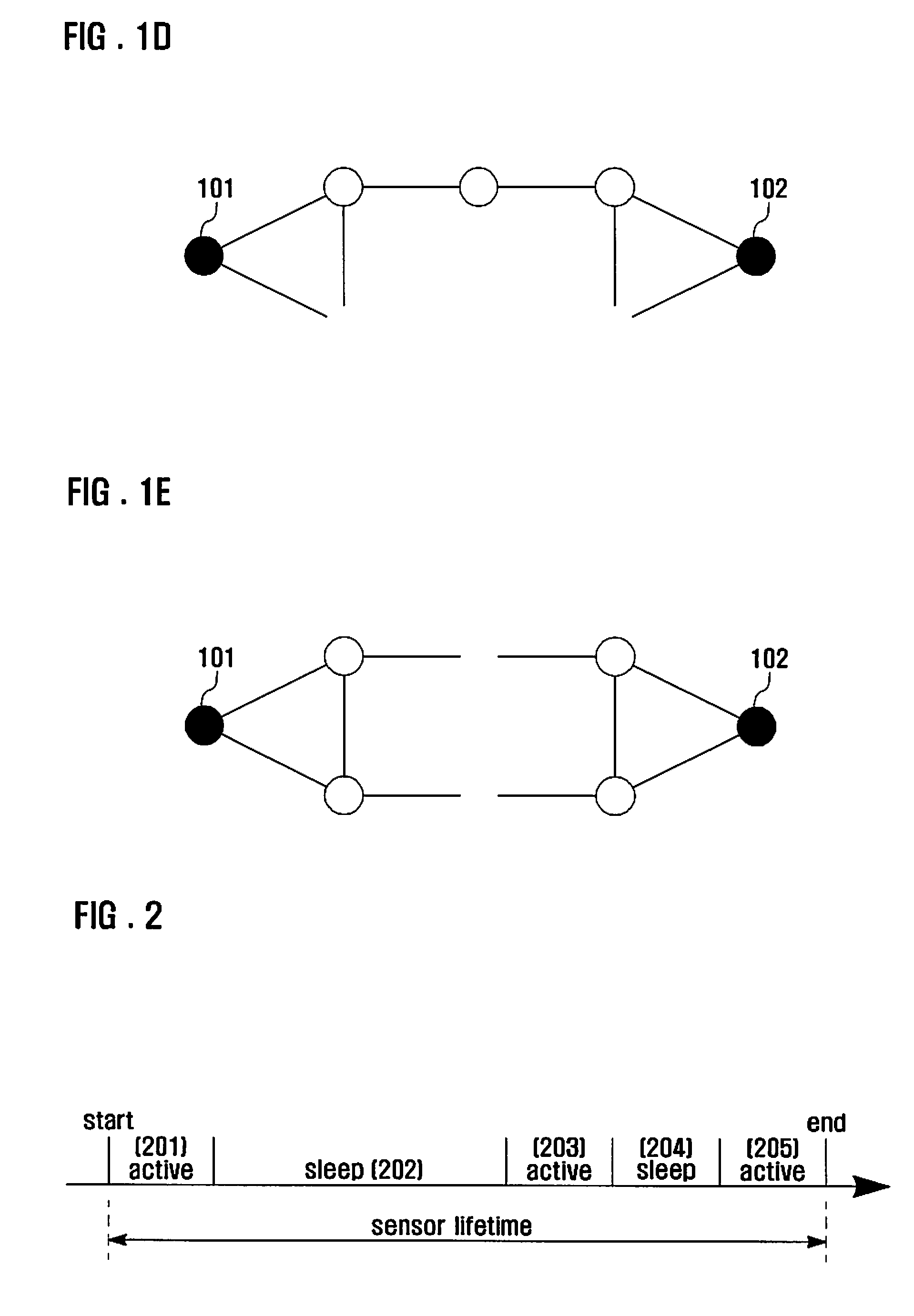
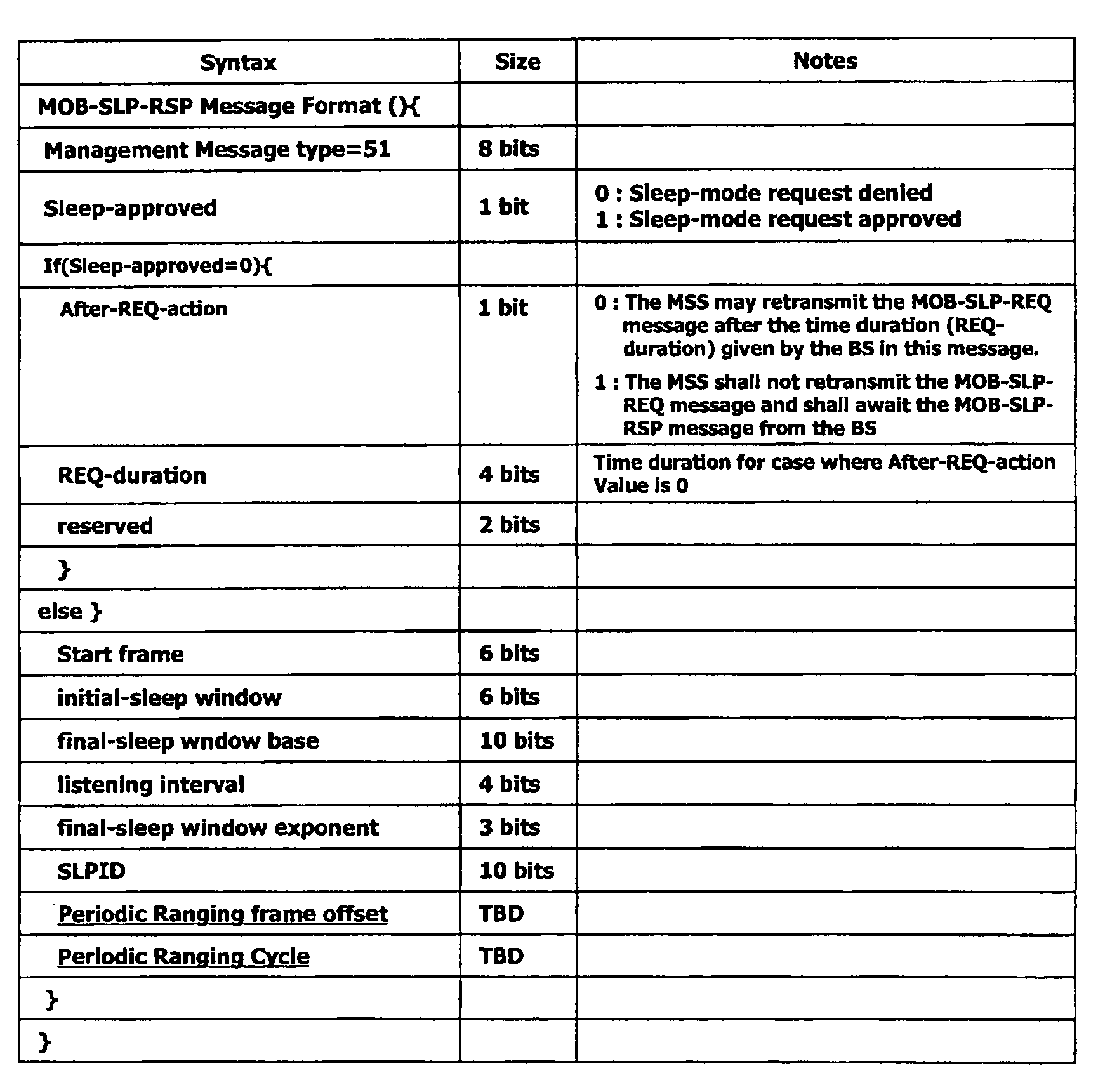
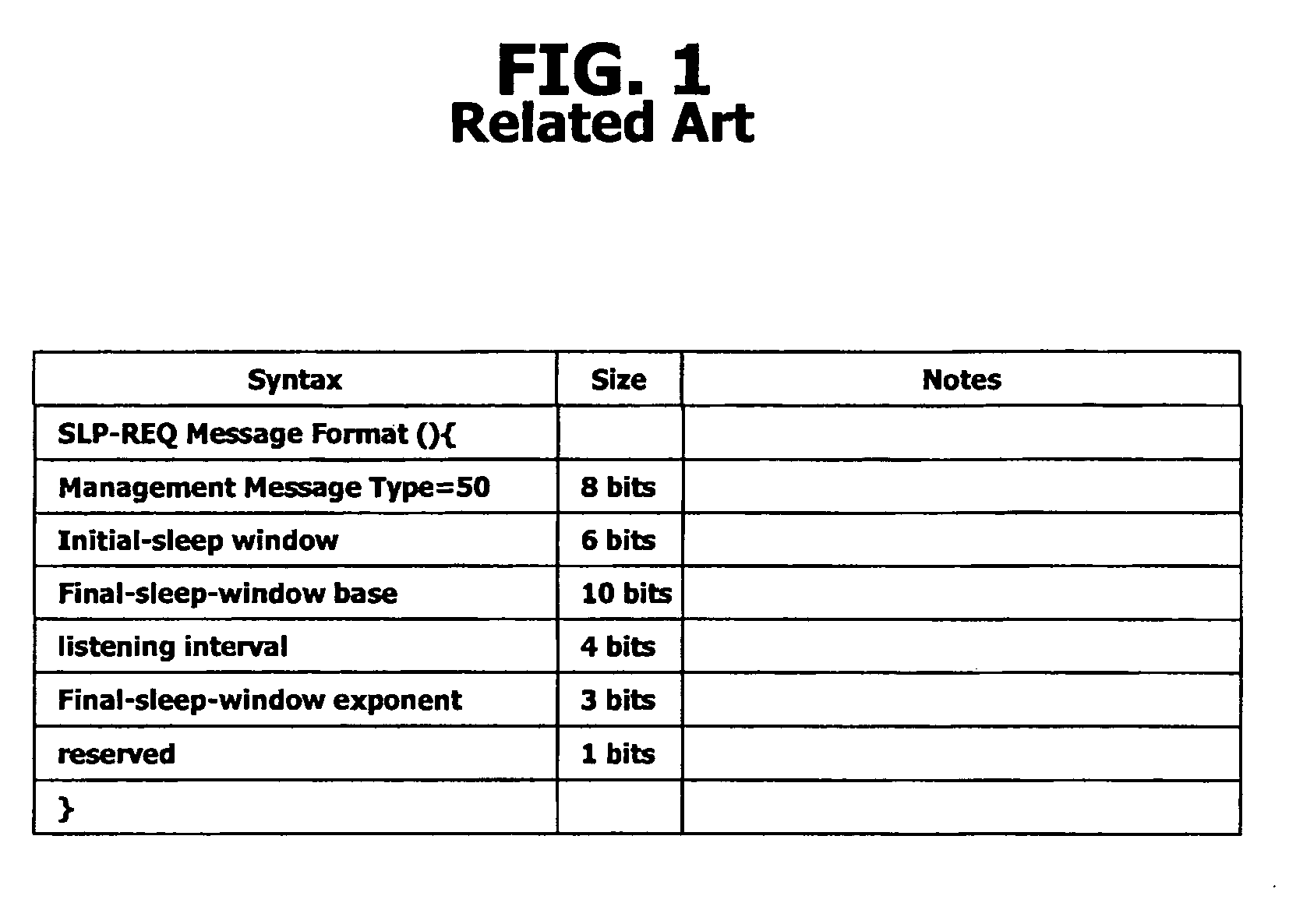
Periodic ranging in a wireless access system for mobile station in sleep mode
InactiveUS20060030305A1Eliminate the problemPower managementSubstation equipmentSleep timeMobile station
A method of performing a ranging process between a base station and a mobile station in sleep mode in a wireless access system, wherein the base station provides the mobile station with an initial notification of a periodic ranging time that occurs during a sleep time interval and during which the mobile station is to perform the ranging process, the initial notification included in a first message indicating whether the mobile station should terminate sleep mode to receive downlink data, and wherein the base station provides the mobile station with subsequent notifications of periodic ranging times that occur during the sleep time interval, the subsequent notifications indicated in a second message, the second message transmitted to the mobile station as part of the ranging process such that the mobile station performs a plurality of ranging processes within the sleep time interval.
Owner:LG ELECTRONICS INC
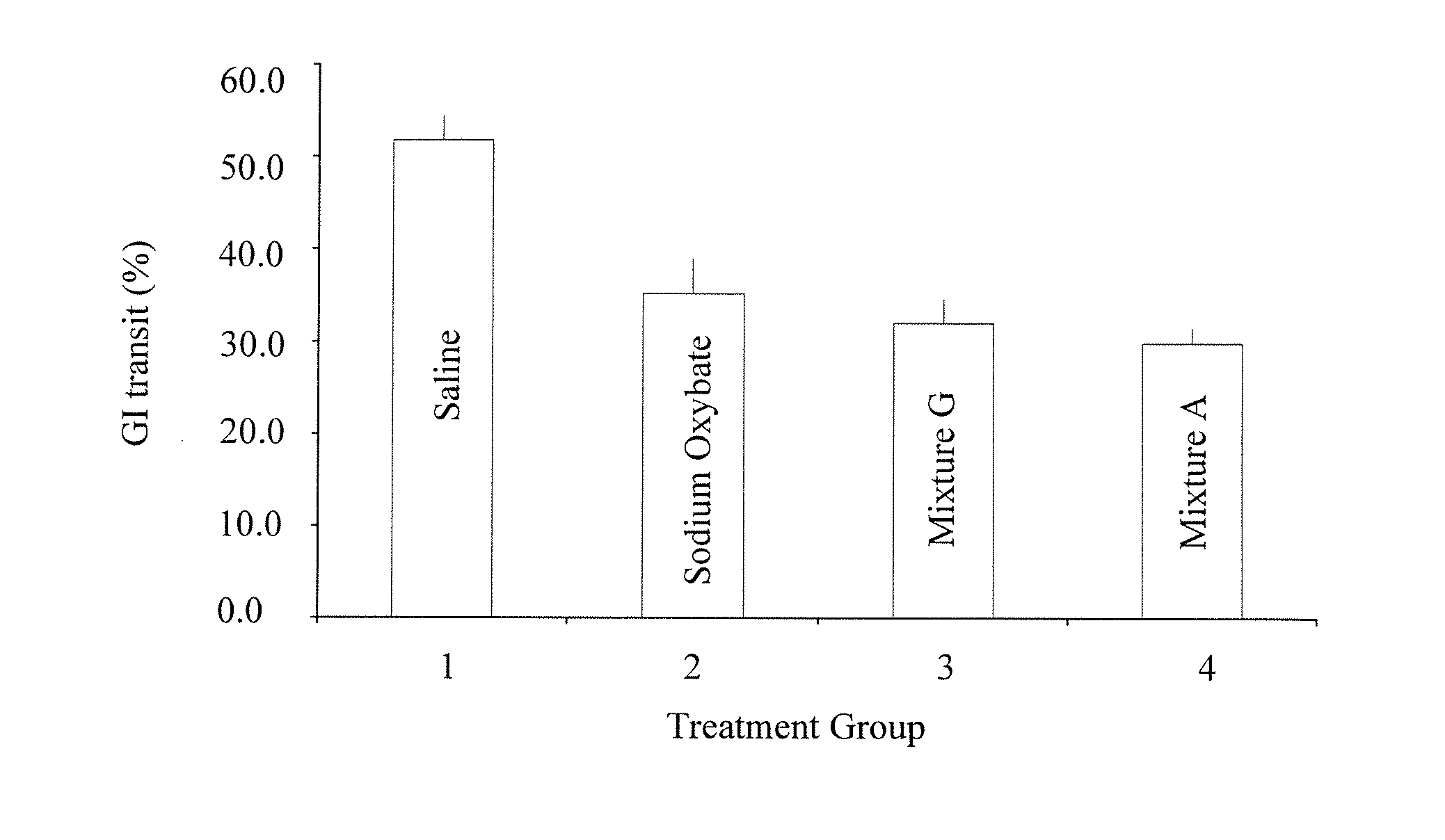
Gamma-hydroxybutyrate compositions and their use for the treatment of disorders
Provided herein are pharmaceutical compositions and formulations comprising mixed salts of gamma-hydroxybutyrate (GHB). Also provided herein are methods of making the pharmaceutical compositions and formulations, and methods of their use for the treatment of sleep disorders such as apnea, sleep time disturbances, narcolepsy, cataplexy, sleep paralysis, hypnagogic hallucination, sleep arousal, insomnia, and nocturnal myoclonus.
Owner:JAZZ PHARMA IRELAND LTD
Communication method
InactiveUS20060092907A1Preventing deterioration of performance of systemPower managementError preventionSleep timeStable state
A radio communication system suitable for a sensor net system is provided. In a TDMA method, one slot is divided into four periods. Even when a majority of sensor nodes simultaneously perform access, they can settle in a steady state in high speed corresponding to the transition response of the system. Even when sleep time intervals of the sensor nodes are changed according to the priority thereof and the transmission intervals of the sensor nodes are not constant, the TDMA method control can be performed. Moreover, even when the transmission intervals of the sensor nodes are not constant, the original system performance is not deteriorated.
Owner:HITACHI LTD
Method and apparatus for low cost, long range, power efficient, wireless system with enhanced functionality
ActiveUS20110176464A1Save battery powerLong power save statePower managementTransmission systemsSleep timePower efficient
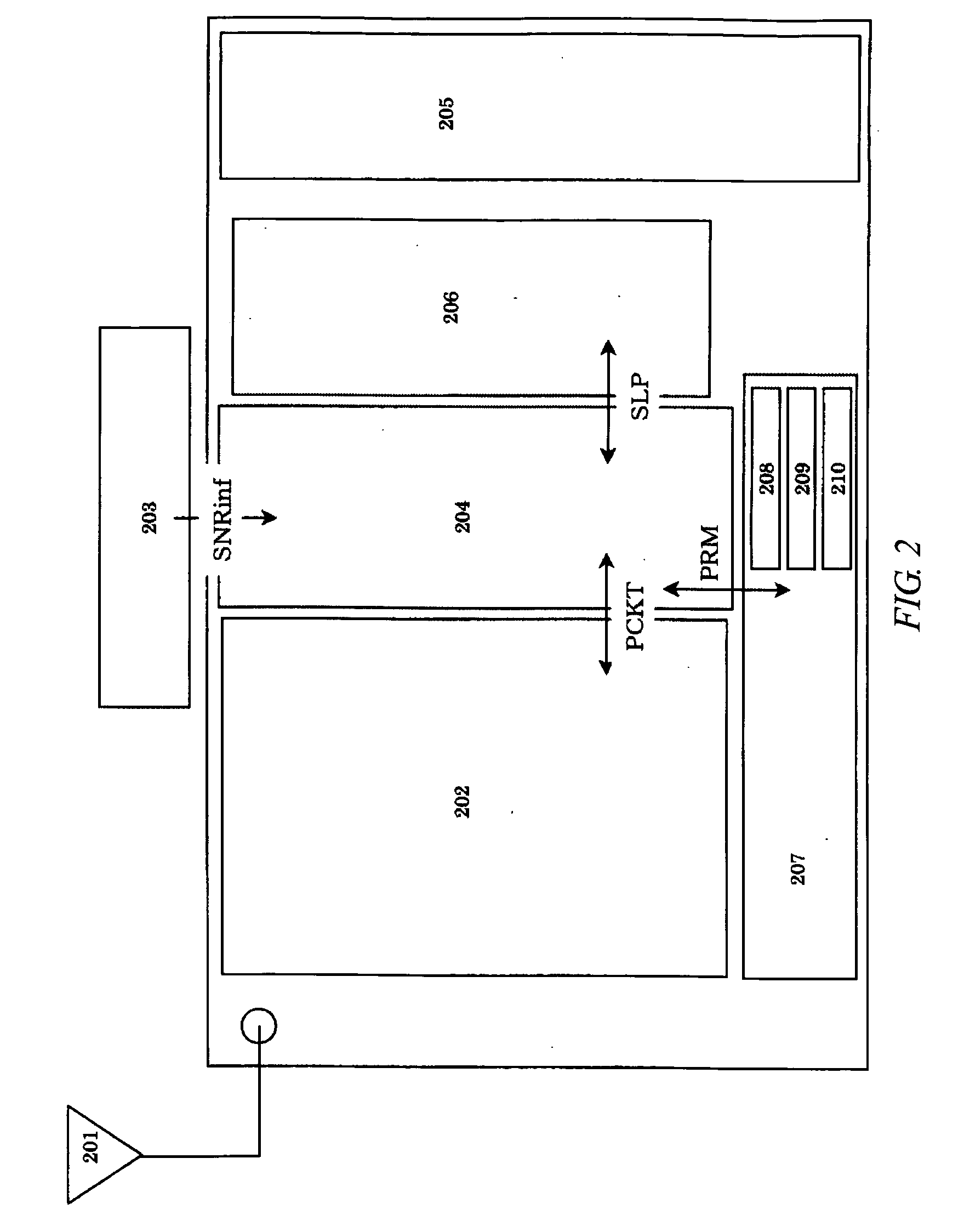
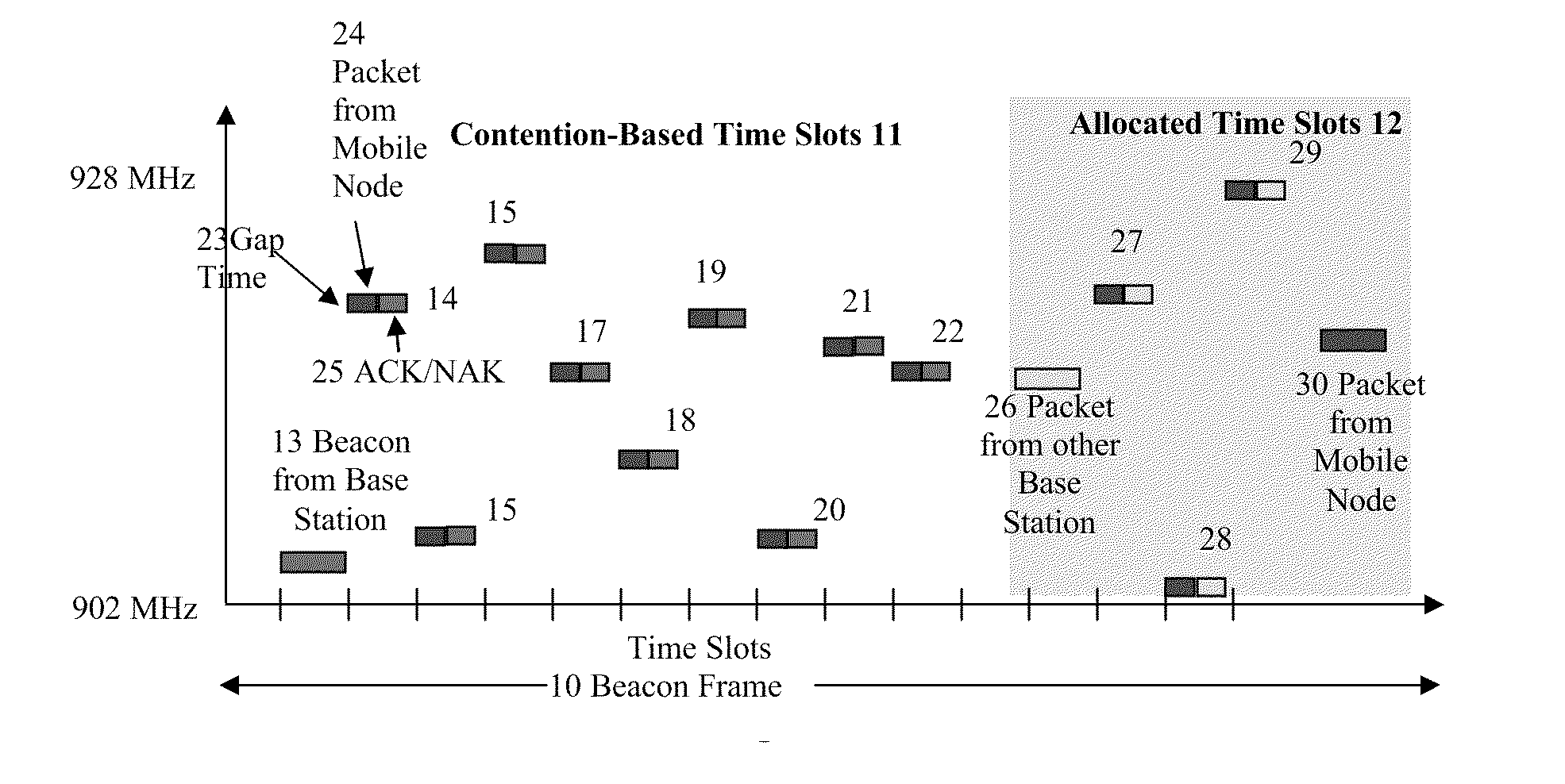
The present invention provides a method and system for establishing a highly mobile, long range secure wireless network with dynamic topologies and near full connectivity with acceptable latency using low cost, low power, compact and lightweight devices. One aspect of the system deals with a highly mobile network with dynamic network topologies and a time varying wireless medium that has neither absolute nor readily observable boundaries outside of which radio nodes are known to be unable to receive network frames, although the desirable open field boundary is 1 mile in radius from a base station node. A synchronous frequency hopping technique is used with mobile nodes that can become slave base station nodes to a master base station node to increase the effective range of the master base station without increasing the transmit power. Furthermore, the use of adjustable sleep times for the mobile nodes, as well as a novel clock calibration method, provides a substantial range increase with acceptable battery size and system latency.
Owner:III HLDG 1
Positioning signal receiving apparatus
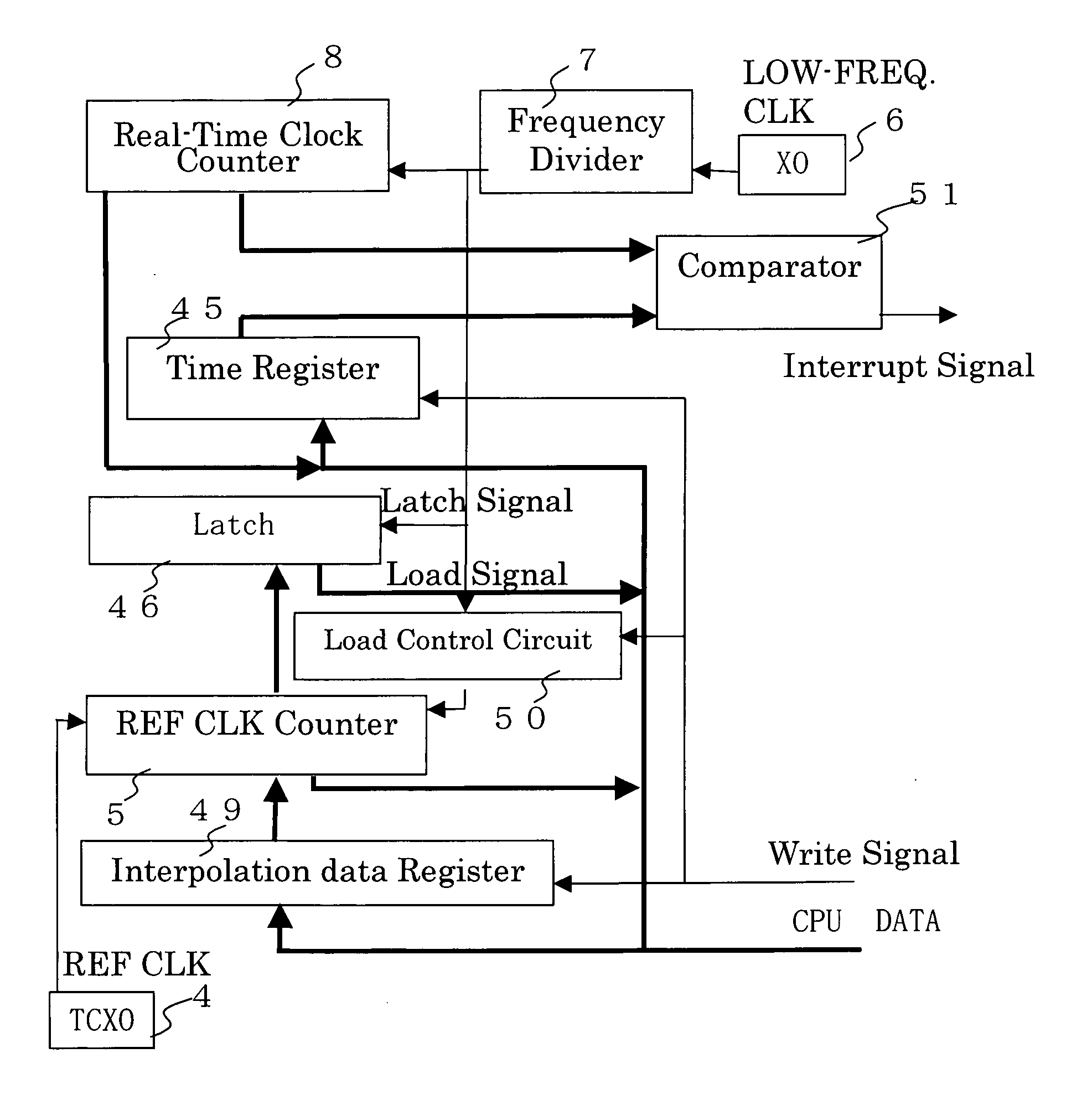
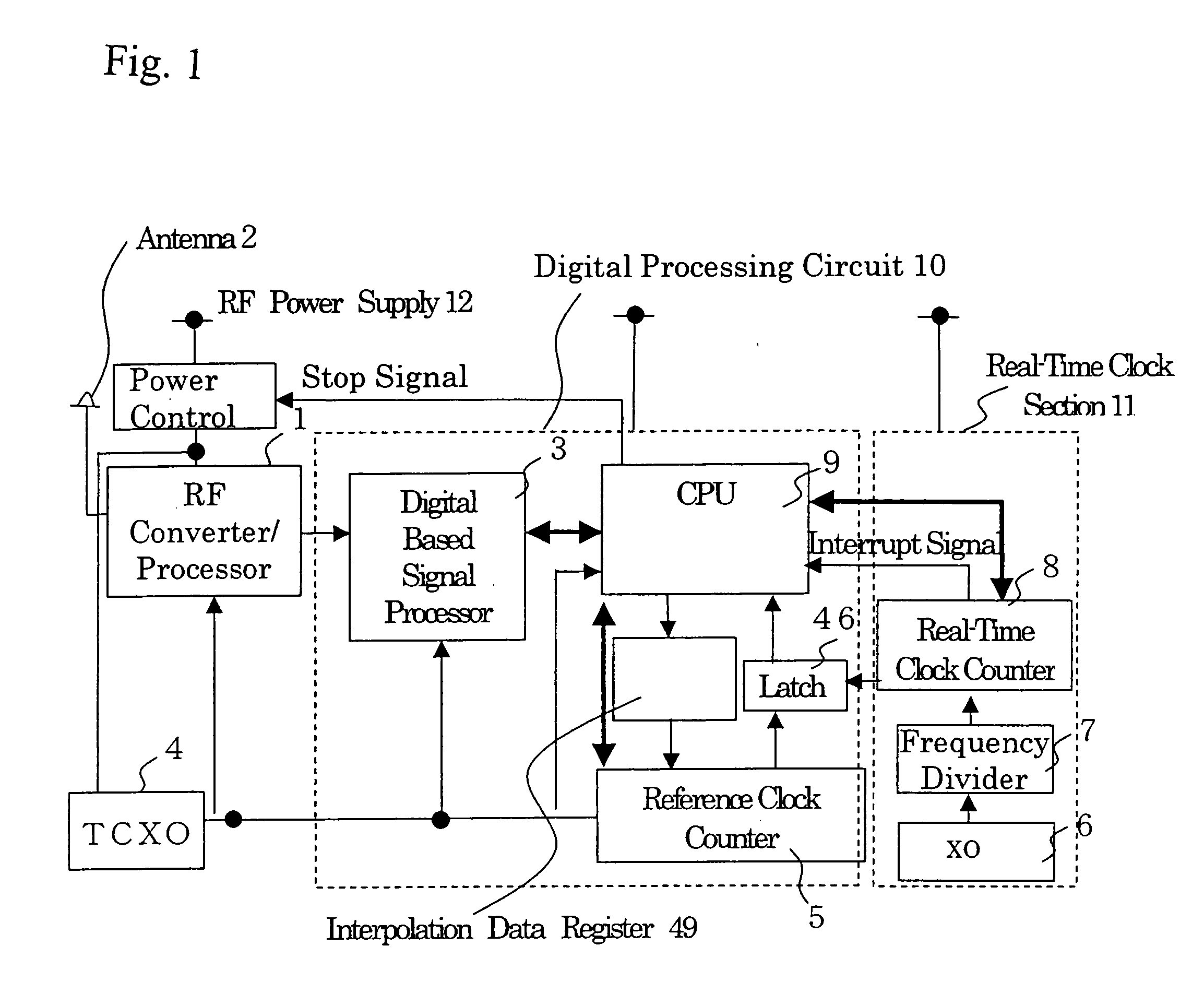
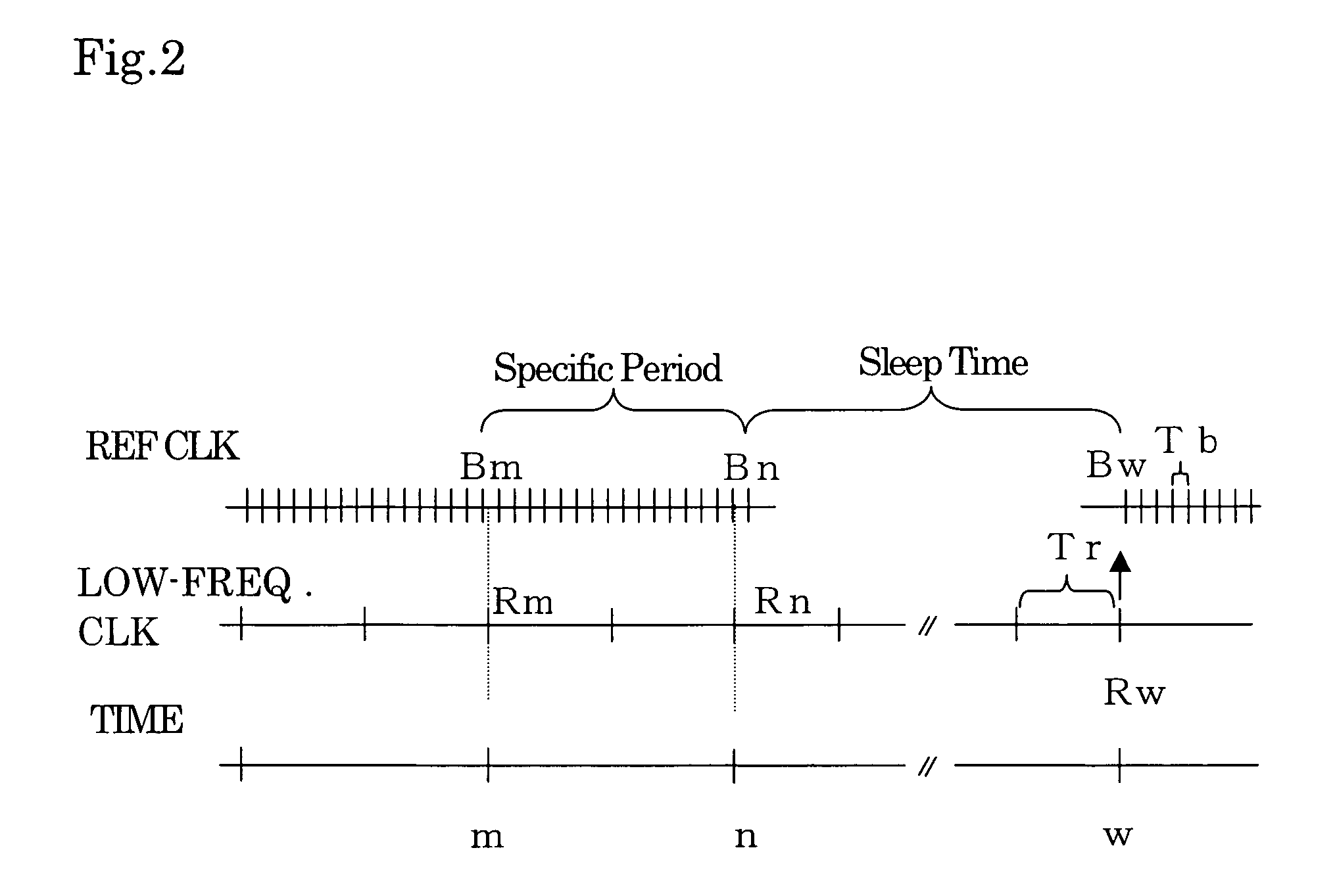
InactiveUS20060149984A1Reduce power consumptionRapid positioningEnergy efficient ICTVolume/mass flow measurementSleep timeReal-time clock
A GPS receiver is alternately switched between sleep conditions under which between sleep conditions under which a temperature-compensated crystal oscillator is shut off for a specific sleep time while a real-time clock section is kept operational and normal operating conditions under which both the temperature-compensated crystal oscillator and the real-time clock section are kept operational. The GPS receiver determines the ratio of the number of pulses of a reference clock signal to the number of pulses of a low-frequency clock signal counted during a specific period of time preceding the sleep time. The GPS receiver estimates a count value which should have been reached by a reference clock counter at the end of the sleep time if the temperature-compensated crystal oscillator continuously generated the reference clock signal based on the number of pulses of the low-frequency clock signal counted during the sleep time.
Owner:FURUNO ELECTRIC CO LTD
Method and system for extending lifetime of sensor nodes in wireless sensor network
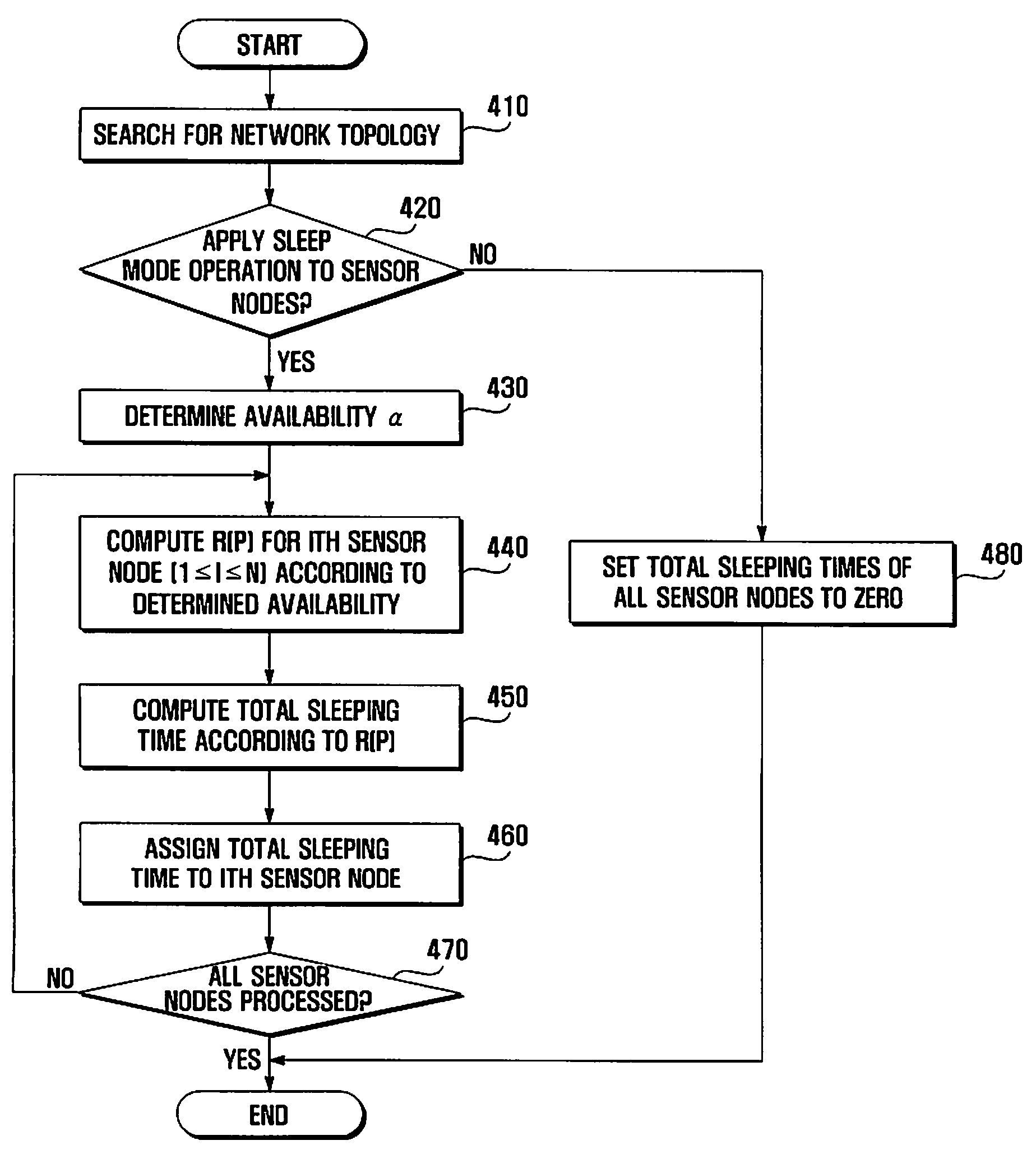
InactiveUS20090216349A1Extended service lifeMinimizes operation probabilityProgramme controlEnergy efficient ICTLine sensorSleep time
A method and system are provided that extend the lifetime of sensor nodes in a wireless sensor network while ensuring network availability. An availability level is set for ensuring network connectivity corresponding to importance of network connectedness. An operation probability that a sensor node is in operation is calculated. A total sleeping time of the sensor node is calculated that minimizes the operation probability while maintaining the availability level.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Periodic ranging in a wireless access system for mobile station in sleep mode
InactiveUS7194288B2Eliminate the problemPower managementSubstation equipmentSleep timeMobile station
A method of performing a ranging process between a base station and a mobile station in sleep mode in a wireless access system, wherein the base station provides the mobile station with an initial notification of a periodic ranging time that occurs during a sleep time interval and during which the mobile station is to perform the ranging process, the initial notification included in a first message indicating whether the mobile station should terminate sleep mode to receive downlink data, and wherein the base station provides the mobile station with subsequent notifications of periodic ranging times that occur during the sleep time interval, the subsequent notifications indicated in a second message, the second message transmitted to the mobile station as part of the ranging process such that the mobile station performs a plurality of ranging processes within the sleep time interval.
Owner:LG ELECTRONICS INC
Energy consumption control method under delay constraint in wireless sensor network
InactiveCN103052131AReduce energy consumptionExtend effective lifePower managementHigh level techniquesWireless mesh networkWork cycle
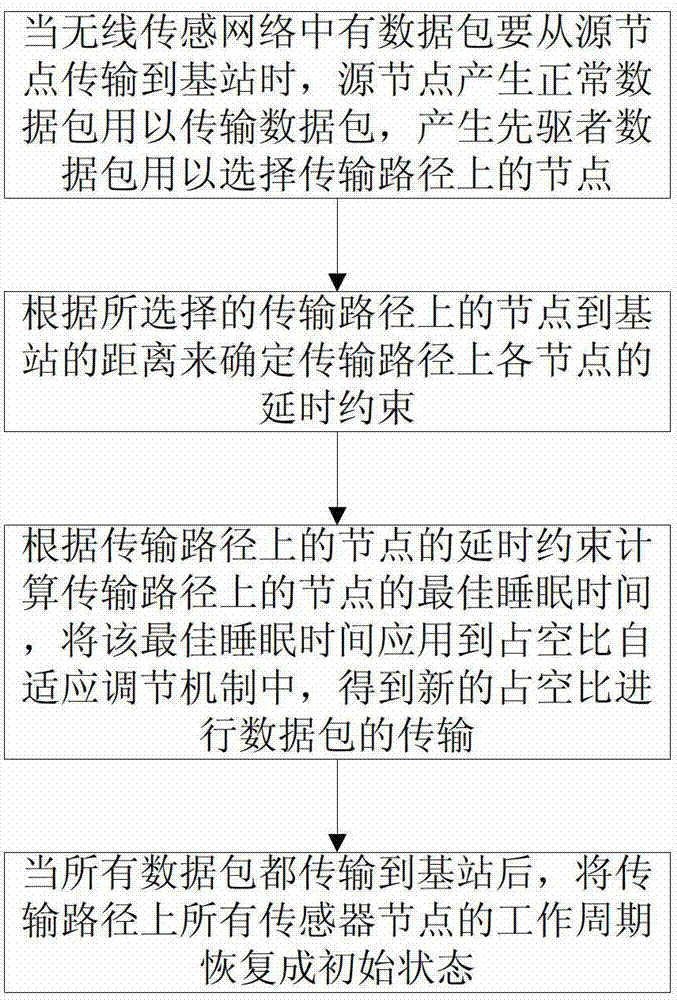
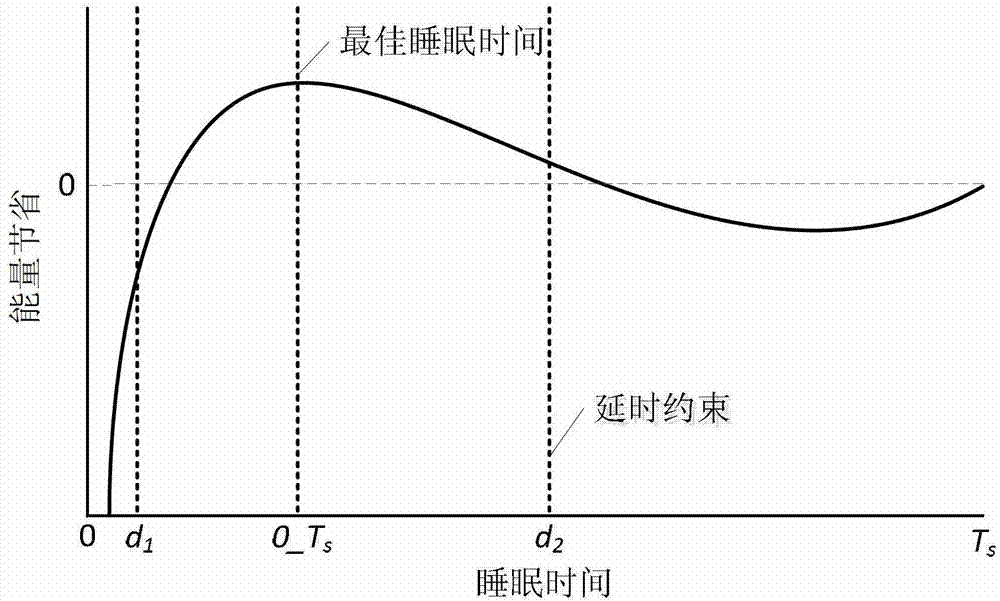
The invention relates to the field of wireless self-organizing networks and sensor networks, in particular to an energy consumption control method under delay constraint in a wireless sensor network. The energy consumption control method comprises the following steps of: generating a normal data packet and a pioneer data packet by a source node when data packets in the wireless sensor network need to be transmitted to a base station from the source node, wherein the normal data packet is used for transmitting the data packets, and the pioneer data packet is used for selecting nodes on a transmission path; determining the delay constraint of the nodes on the transmission path; computing the best sleep time of the nodes on the transmission path; applying the best sleep time to a duty ratio self-adaptive adjustment mechanism to obtain new duty ratio to transmit the data packets; and respectively recovering work cycles of all the nodes on the transmission path into an original state after all the data packets are transmitted to the base station. According to the energy consumption control method under the delay constraint in the wireless sensor network, on the premise that the constraint condition of the wireless sensor network on transmission delay is met, the energy consumption of the wireless sensor network is reduced to the maximum limit, and the service life of the wireless sensor network is prolonged.
Owner:RUN TECH CO LTD
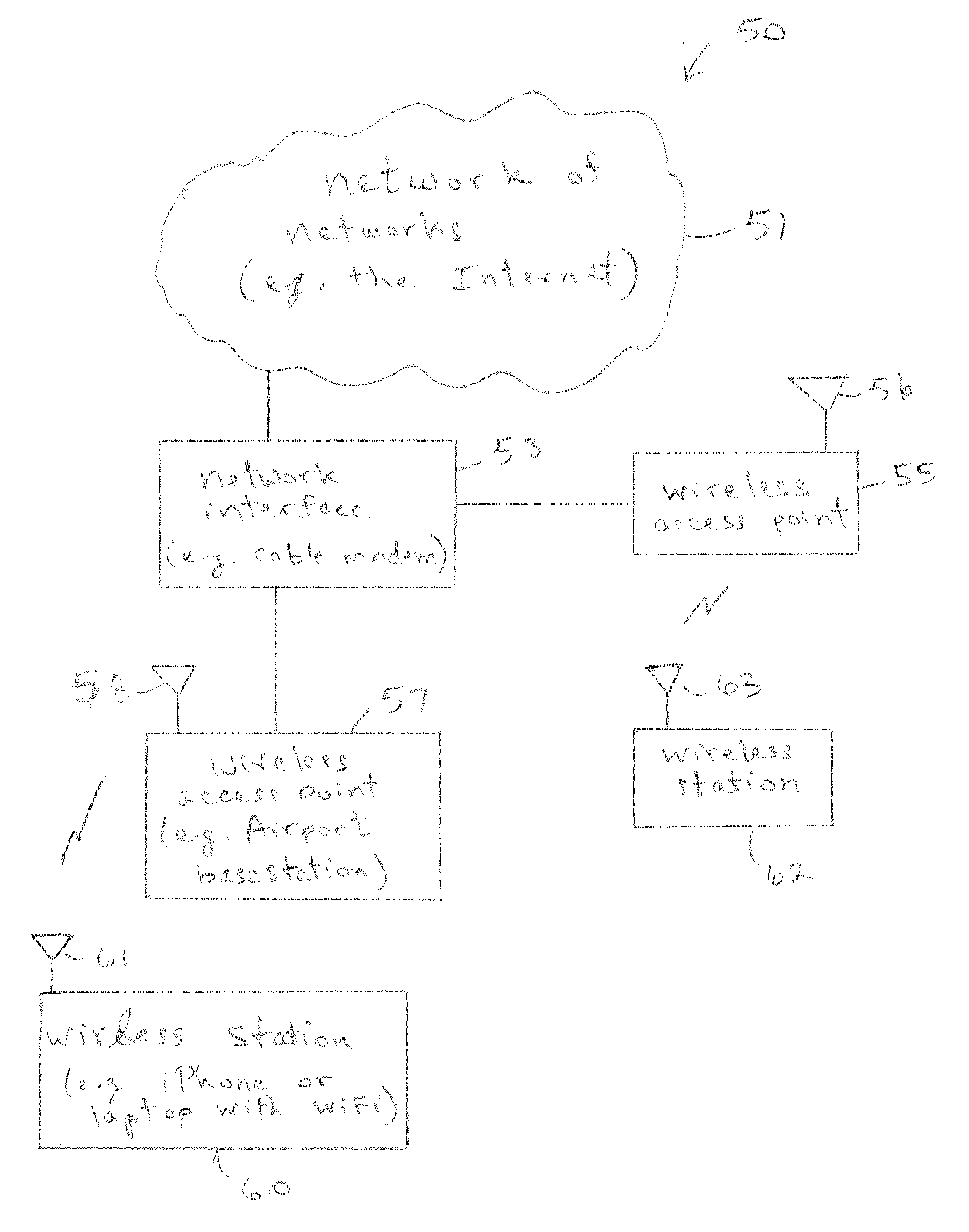
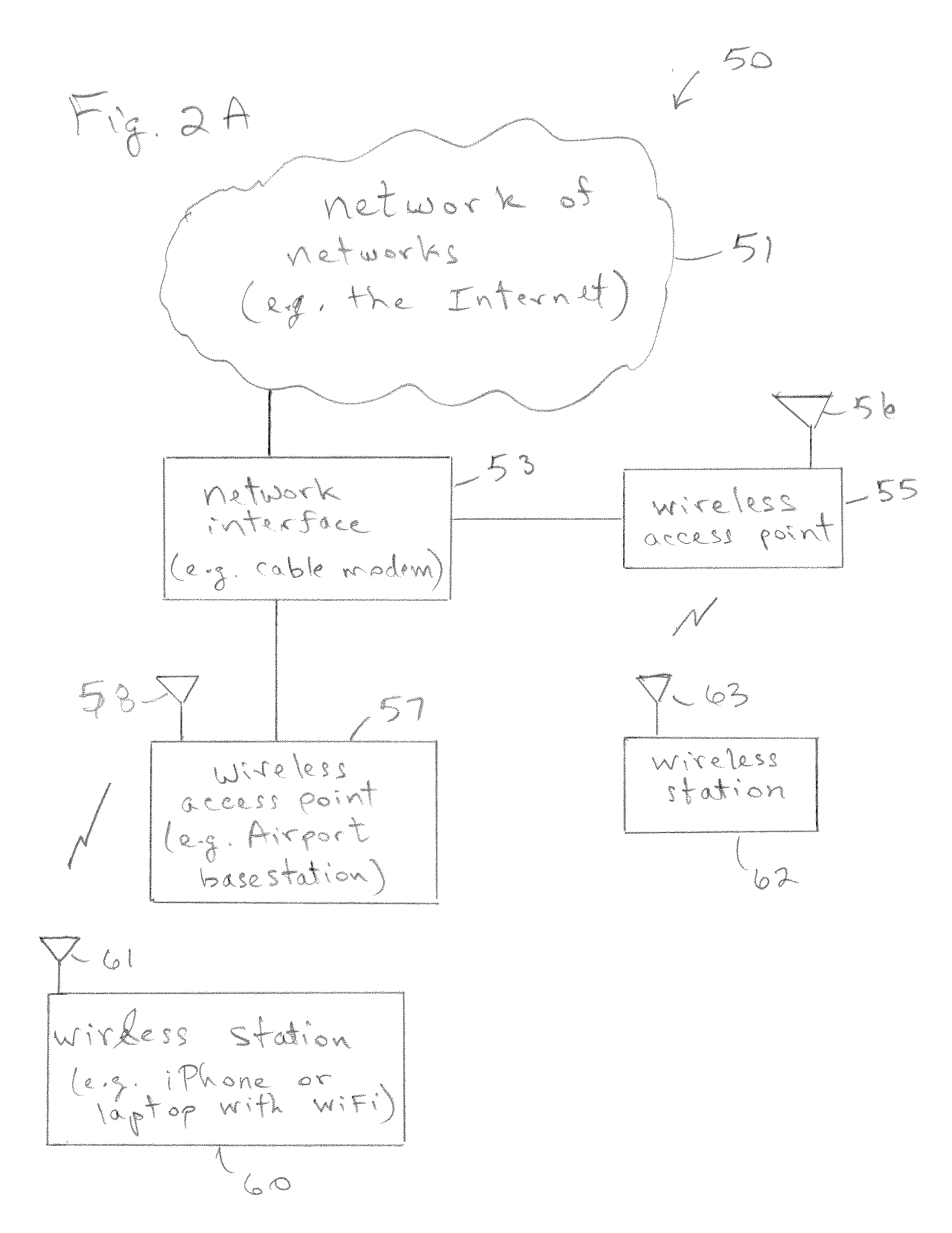
Power Management Of A Radio Data Transceiver
Methods and apparatuses for operating a wireless mobile station configured to communicate with a wireless access point are described. A sleep state may be maintained in which a radio frequency (RF) radio in the wireless mobile station is in a low power state. The wireless station may use a plurality of sleep states, each with a different sleep timer period based upon recent network activity. In one embodiment, a device may have two sleep states with two sleep timers, and in another embodiment a device may have three sleep timers for three sleep states. The first sleep time may be started for a first sleep state and to determine when to awake the device to determine whether there is any network activity. The device then determines whether a first period of network inactivity has occurred and, if so, it starts a second sleep timer for a second sleep state in response to determining that the first period of network inactivity has occurred. The method can further include determining whether a second period of network inactivity has occurred and, in response to determining that a second period of network inactivity has occurred, the device starts a third sleep timer for a third sleep state
Owner:APPLE INC
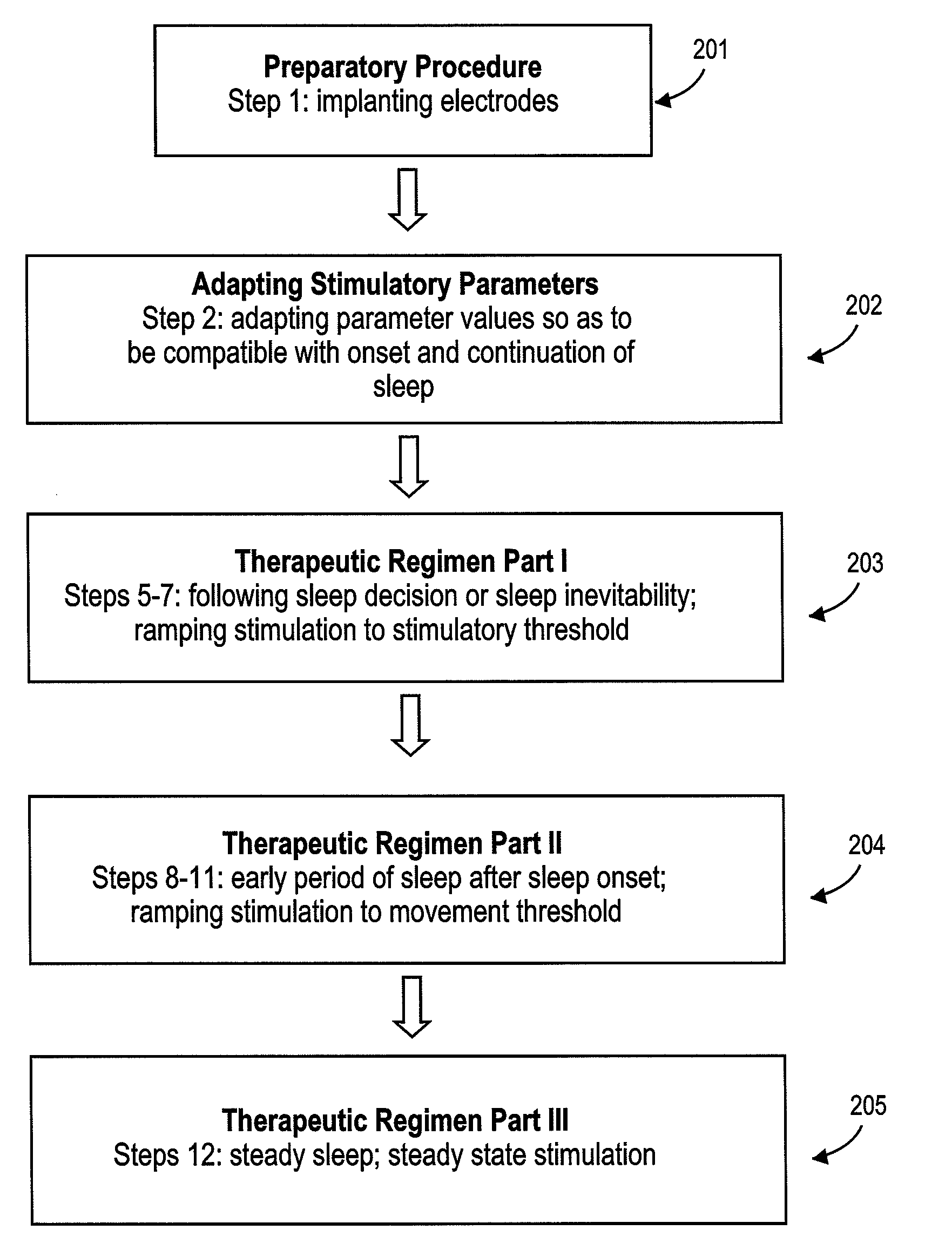
Method of improving sleep disordered breathing
ActiveUS8478412B2ElectrotherapyDiagnostic recording/measuringSleep disordered breathingSommeil paradoxal
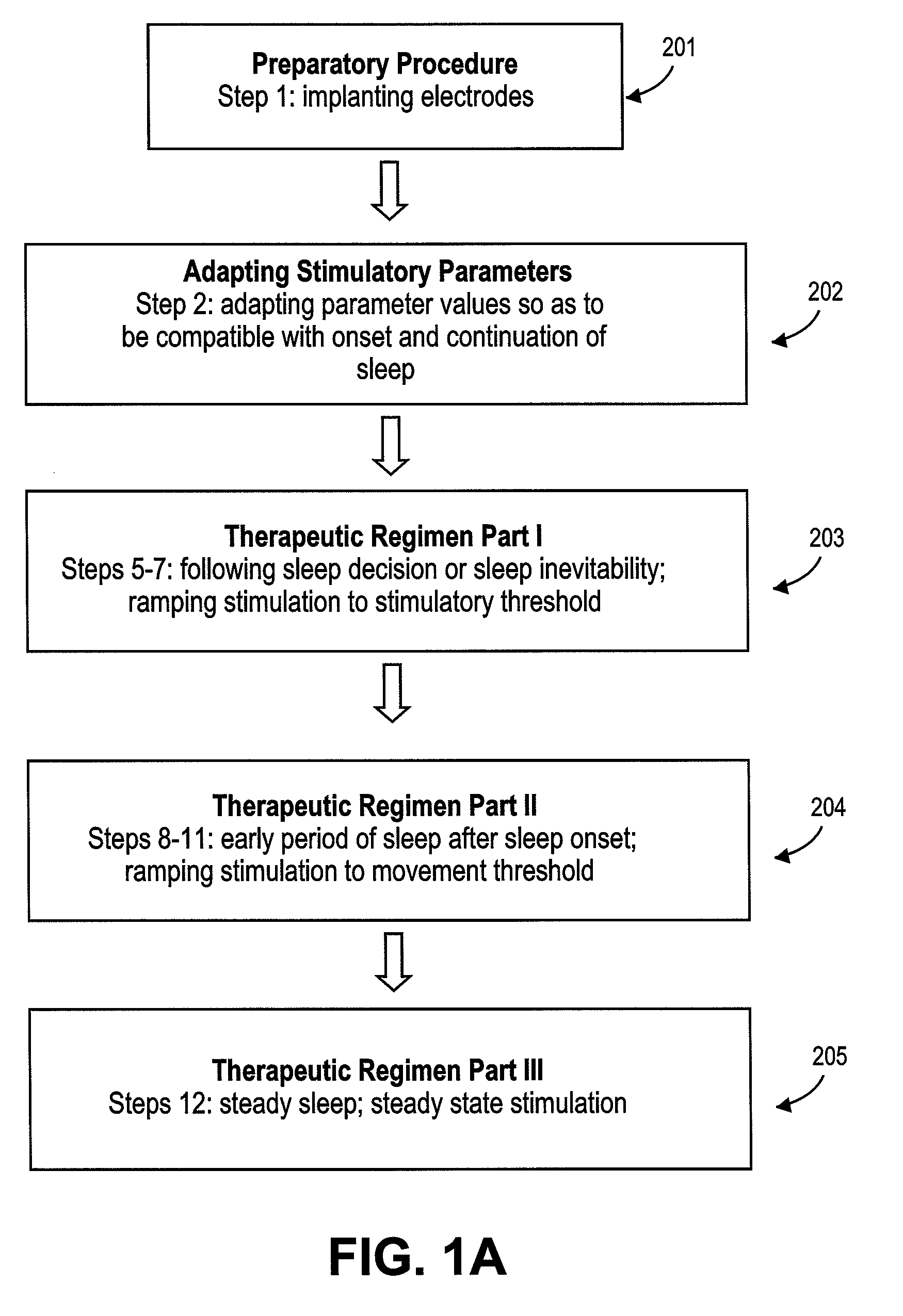
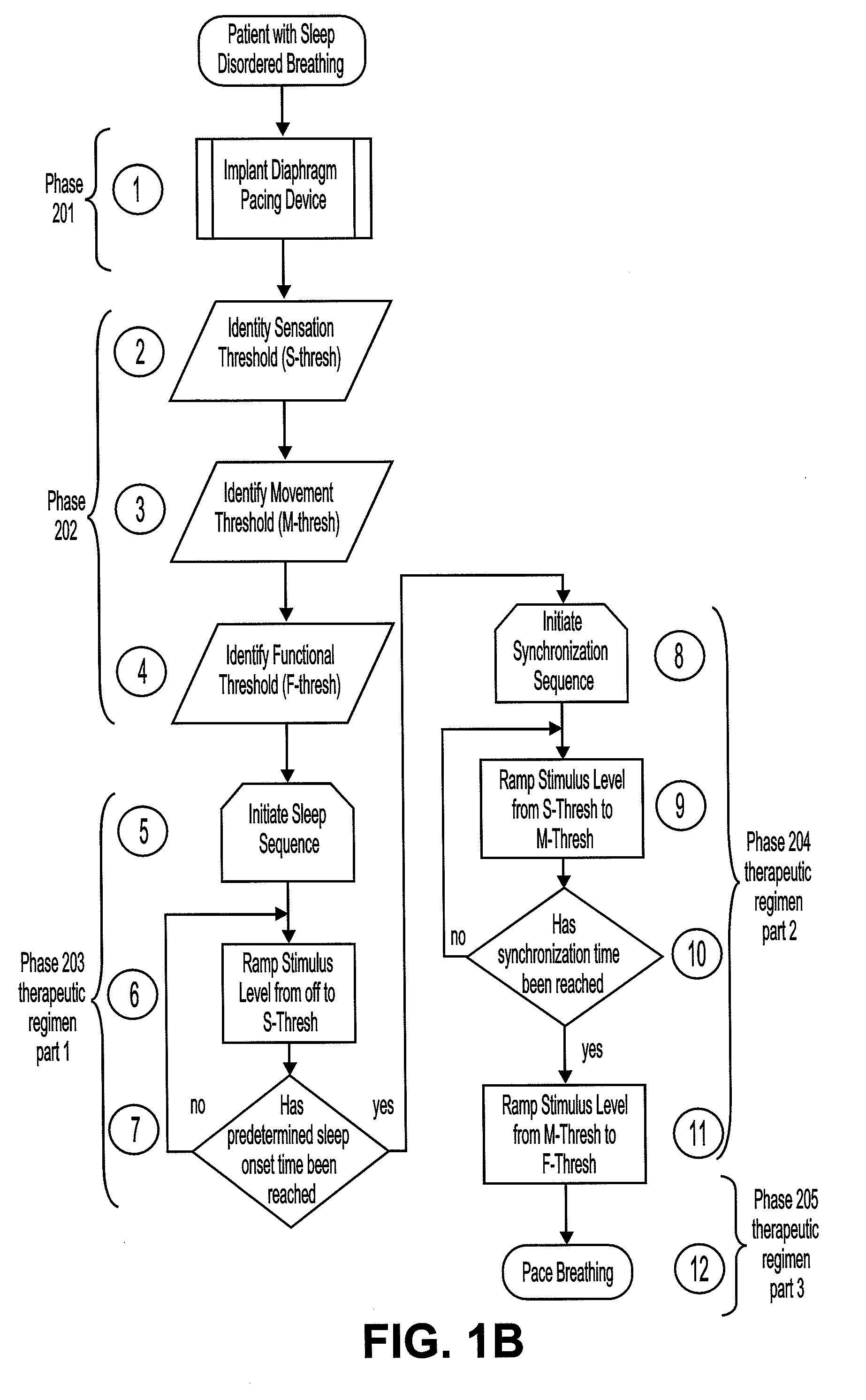
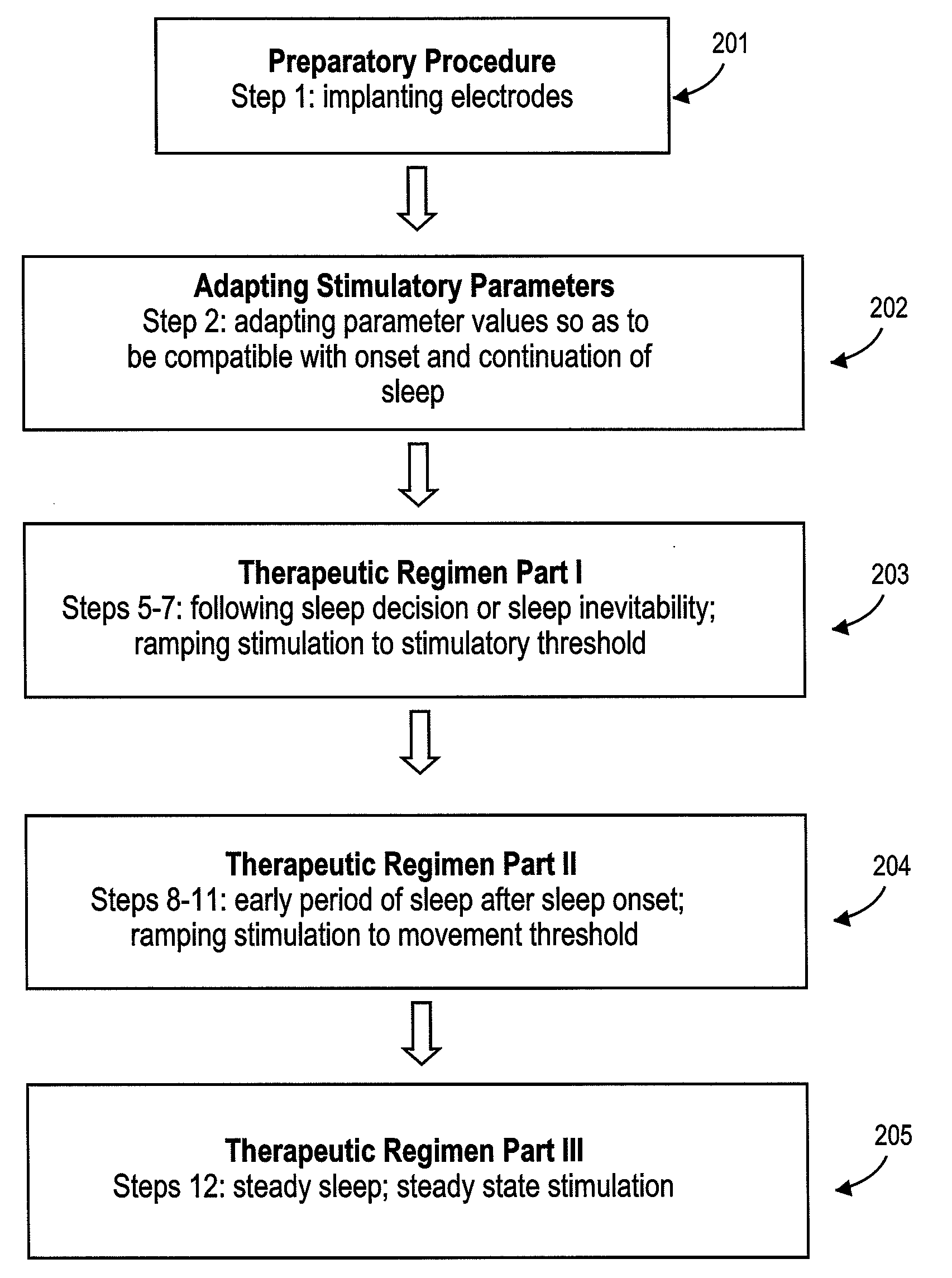
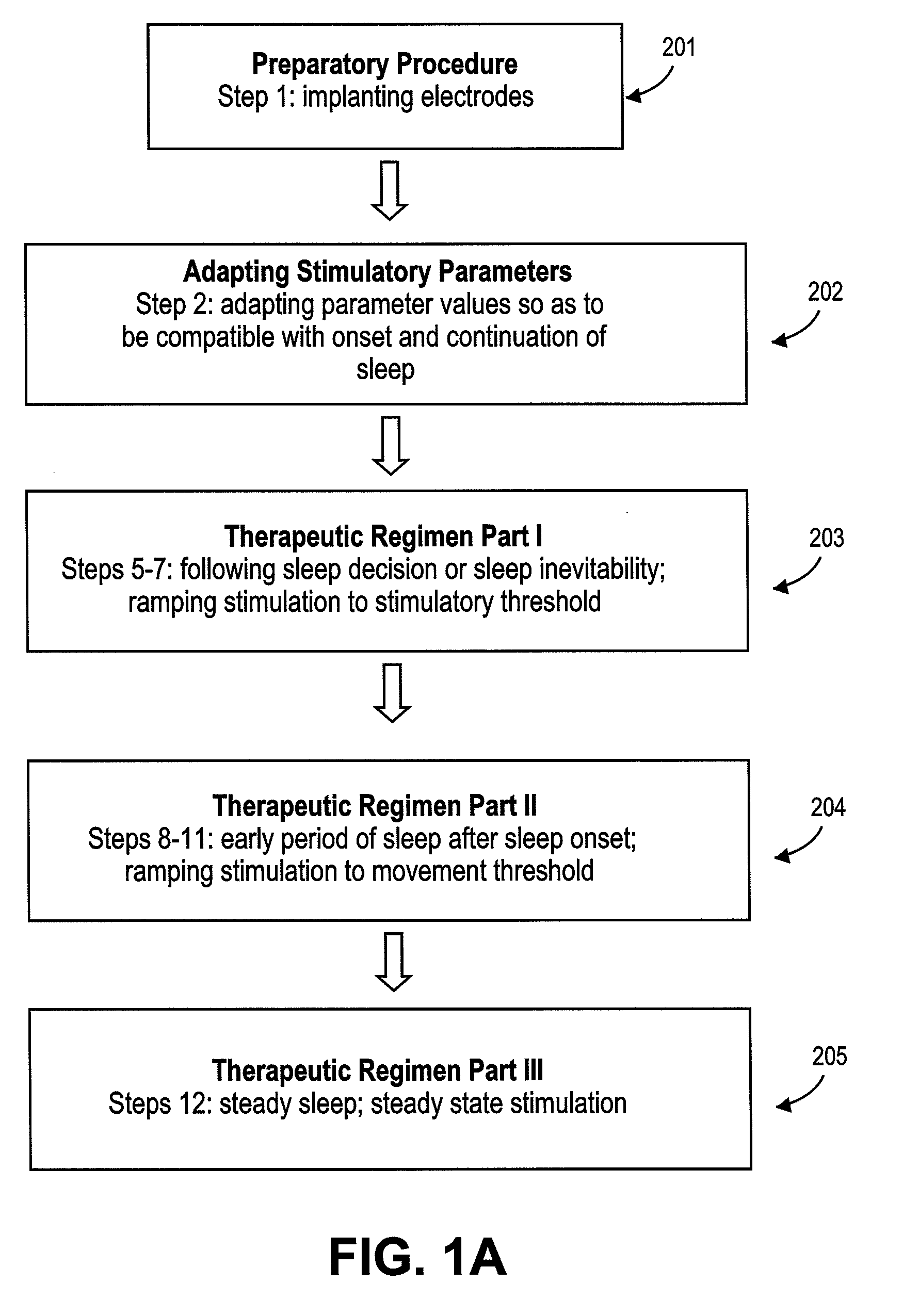
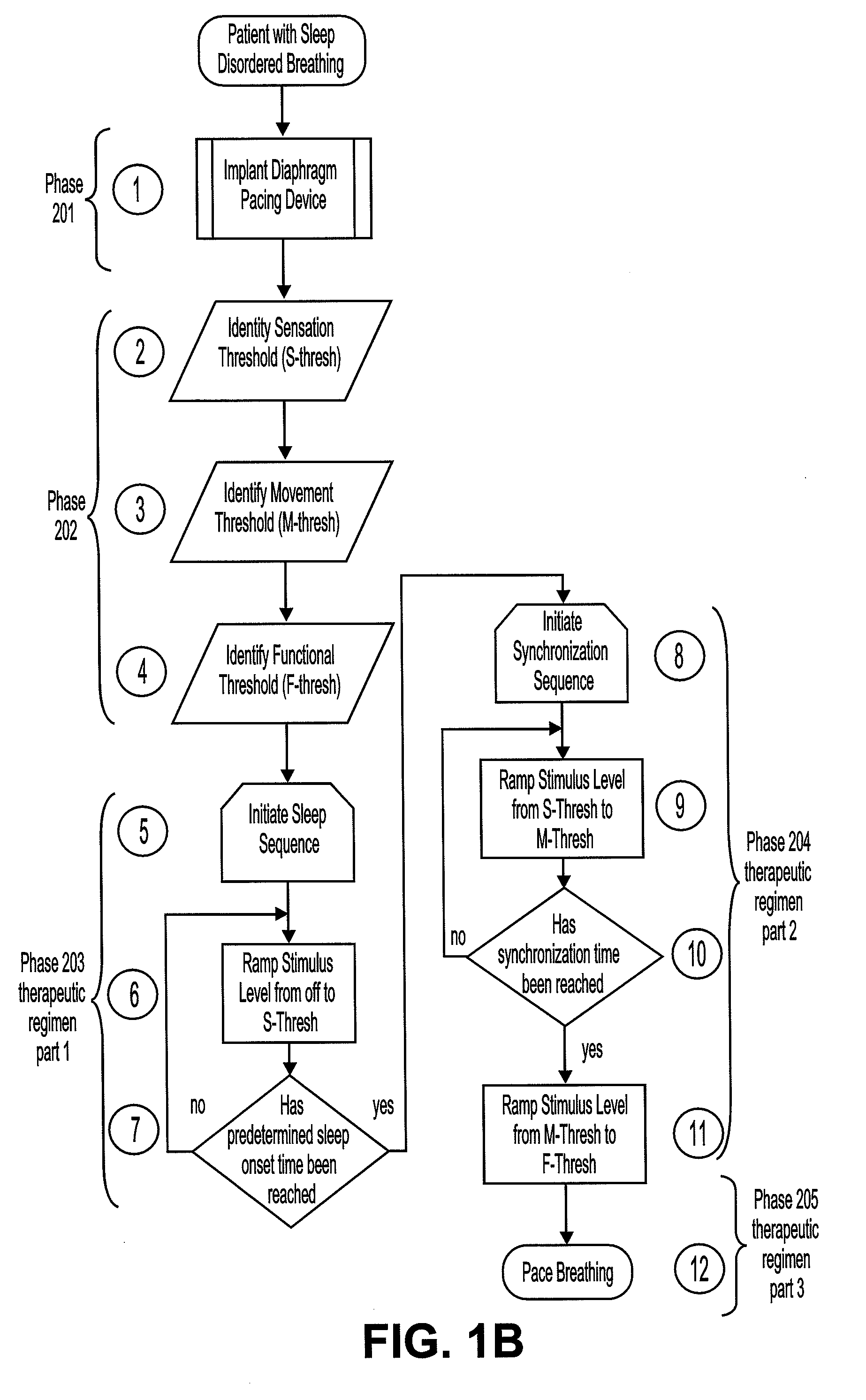
A diaphragm pacing stimulatory method and a system to implement the method are provided to improve respiratory function and the quality of sleep in patients whose sleep is compromised by poor respiration. The diaphragm pacing method includes adaptations that make it particularly compatible with the onset of sleep and sustaining sleep. Embodiments of the method are operated independently of breathing effort the patient may make during sleep. Patients for whom the invention is appropriate include those with a neuromuscular disease, such as amyotrophic lateral sclerosis (ALS). System elements include an external electrical stimulator coupled to one or more implanted electrodes that stimulate diaphragm contraction. The system and method provide for a pacing of the diaphragm, improved breathing, and improved sleep. Features of improved sleep include longer sleep time, an increased amount of REM sleep, and fewer episodes of wakefulness and restlessness.
Owner:SYNAPSE BIOMEDICAL INC
Disabling execution of malware having a self-defense mechanism
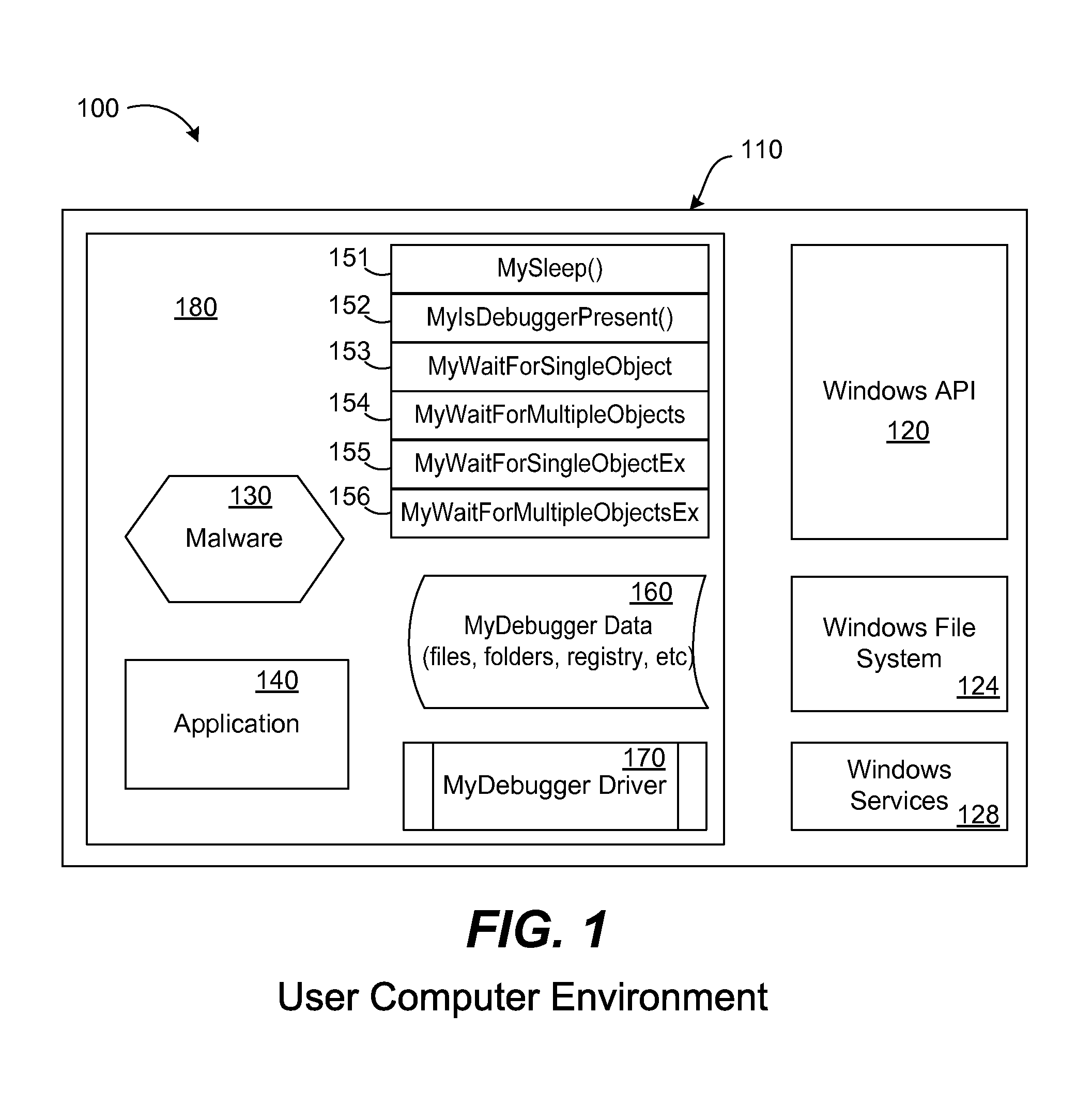
ActiveUS8763125B1Preventing executionThe process is simple and fastDigital data information retrievalMemory loss protectionSleep timeOperational system
A dummy debugger program is installed within the user computer system. The dummy program is registered with the operating system as a debugger and may also be registered as a system service as if it is a kernel mode debugger. The dummy debugger program may have the name of a popular debugging program. Dummy registry keys are created that are typically used by a debugger to make it appear as if a debugger is present within the operating system of the user computer. Dummy program folders or dummy program names are created to make it appear as if a debugger is present within the operating system of the user computer. API calls are intercepted by using API hooks and modified to always return a meaningful value indicating that a debugger is present. Malware performing any checks to see if a debugger is present will be informed that a debugger is present and will then shutdown, sleep, terminate, etc. Or, in order to trick malware into thinking that an emulator is present, any API call is intercepted and the sleep time passed in is raised by a couple of milliseconds. Malware will determine that the time parameter passed in is not equivalent to the elapsed time from before the API call to after the call and the malware will determine that an emulator is present and will terminate.
Owner:TREND MICRO INC
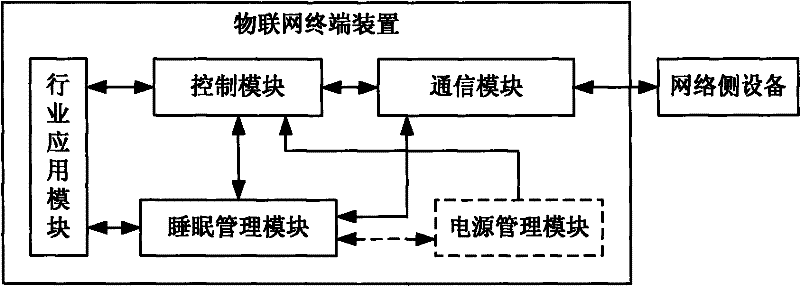
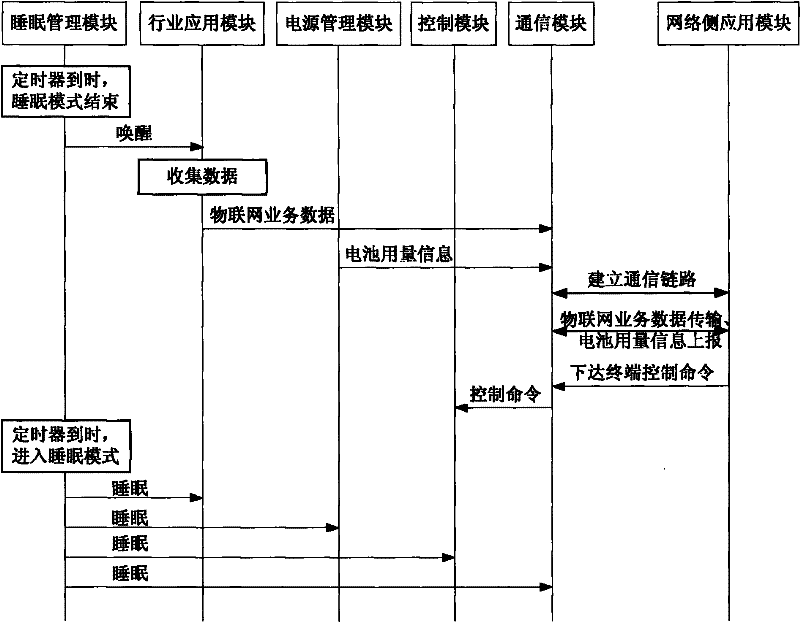
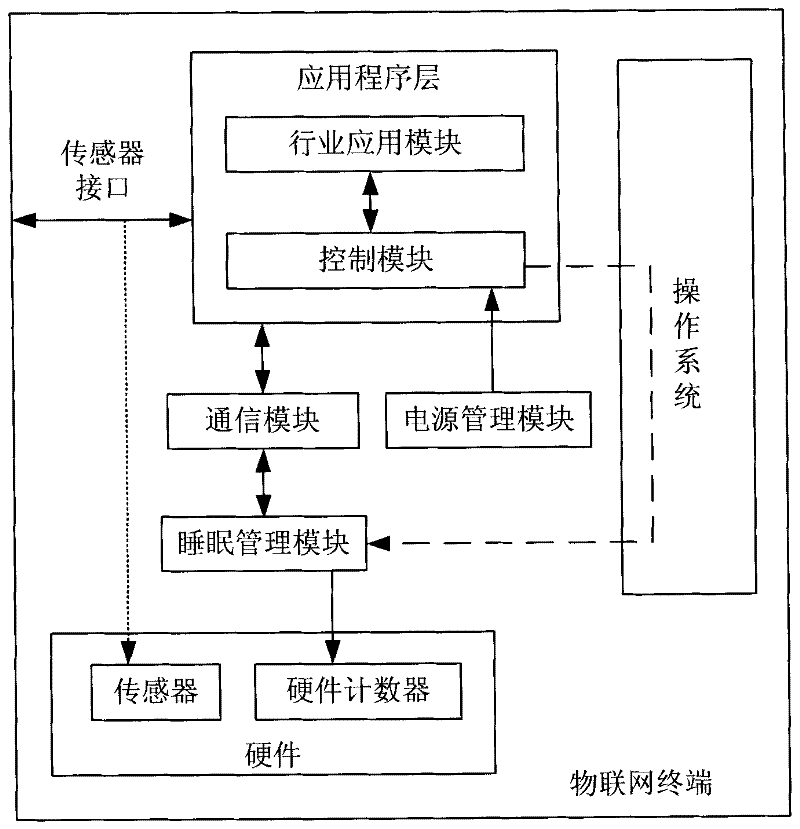
Internet of things terminal, network side equipment and system
InactiveCN102196539AReduce management and maintenance costsReduce power consumptionPower managementNetwork topologiesSleep timeSleep management
The invention discloses an Internet of things terminal, network side equipment and an Internet of things system, which have low power consumption and meet the service requirements of the Internet of things. The Internet of things terminal comprises an industry application module, a communication module, a control module and a sleep management module, wherein the industry application module is used for collecting or collecting and processing the service data of the Internet of things; the communication module is used for establishing a transmission link with a network side, transmitting the collected data or the collected and processed data to the network side, receiving a control command from the network side and transmitting the control command to the control module; the control module is used for controlling each module according to the control command transmitted by the network side; and the sleep management module is used for controlling the sleep time and awakening time of the Internet of things terminal, and at least disabling the industry application module and the communication module in the sleep time of the Internet of things terminal.
Owner:ZTE CORP
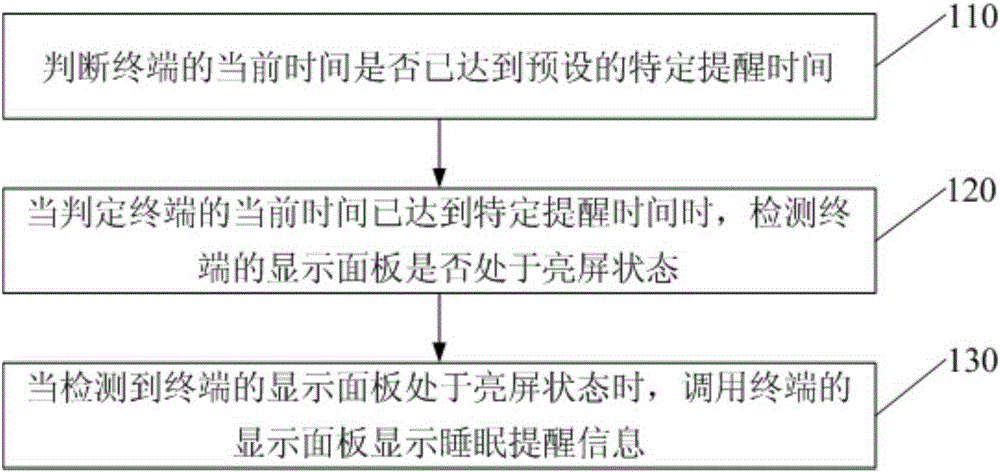
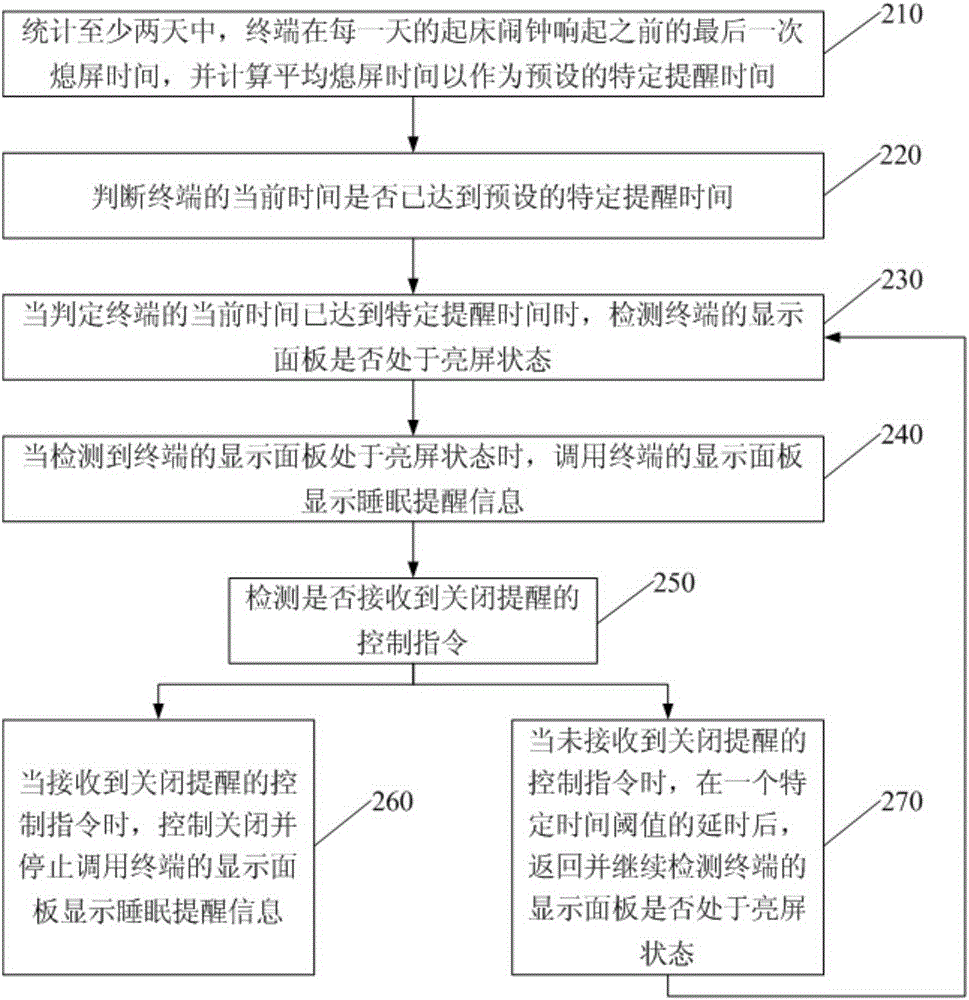
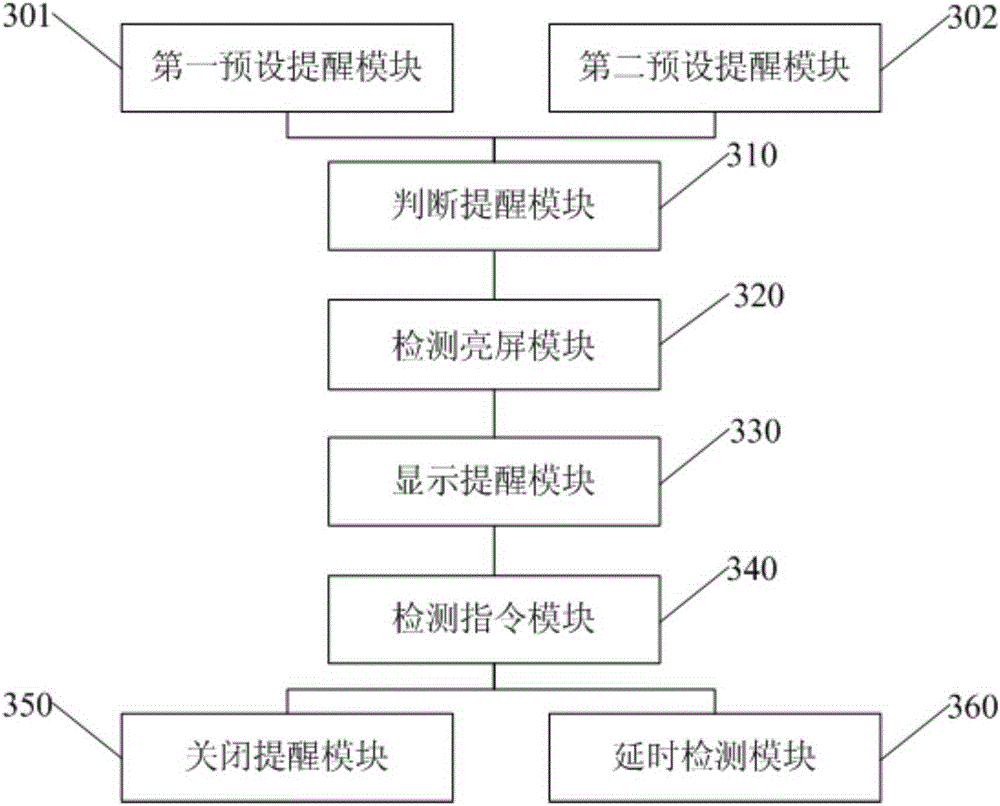
Smart sleep reminding method and smart sleep reminding device
ActiveCN105282343AImprove the problem of staying up late and playing with mobile phonesAdequate sleep timeSubstation equipmentSleep timeMental health
Embodiments of the invention disclose a smart sleep reminding method and a smart sleep reminding device. The method comprises the steps as follows: judging whether the current time of a terminal reaches a preset specific reminding time; detecting whether the display panel of the terminal is bright when judging that the current time of a terminal reaches the preset specific reminding time; and calling the display panel of the terminal to display sleep reminding information when detecting that the display panel of the terminal is bright. According to the invention, users are intelligently reminded of the time for sleep, the problem that users stay up late playing with the mobile phone can be improved, users can have adequate sleep time, and the physical and mental health of users can be improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
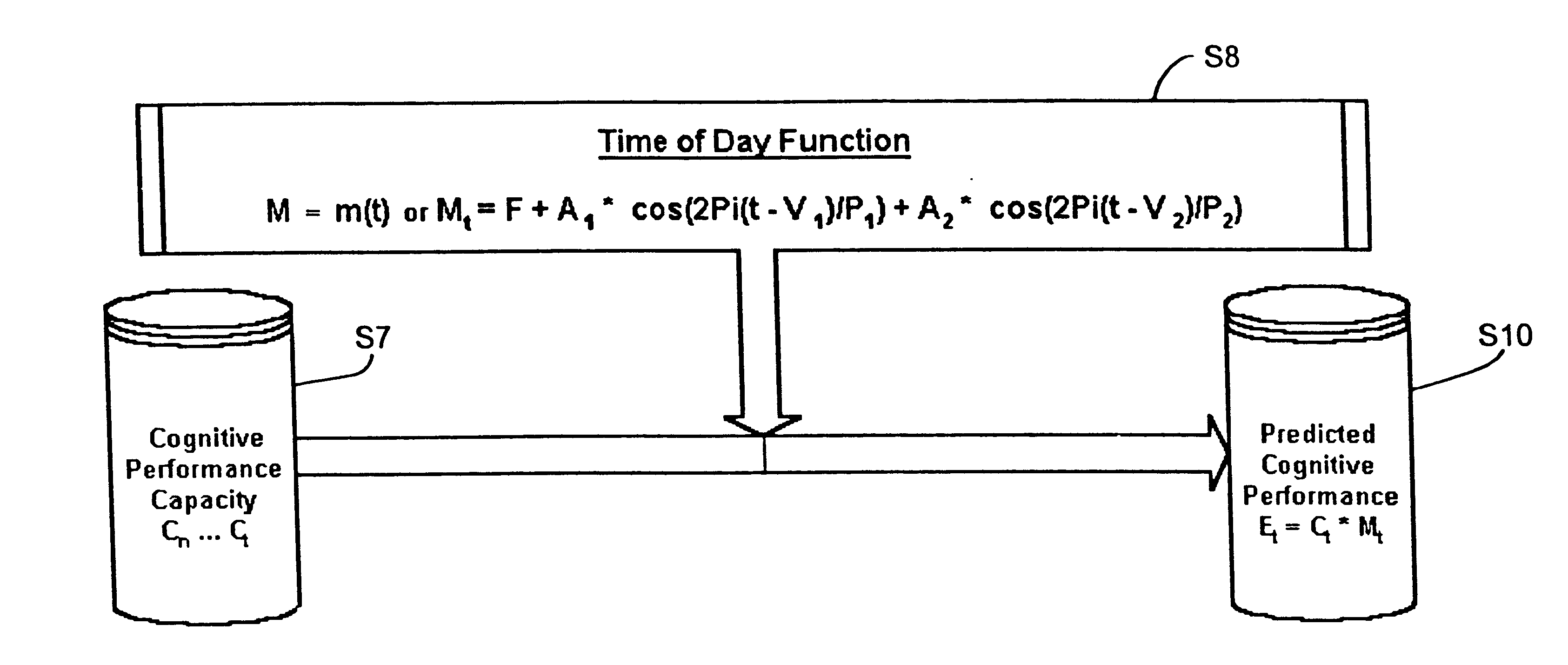
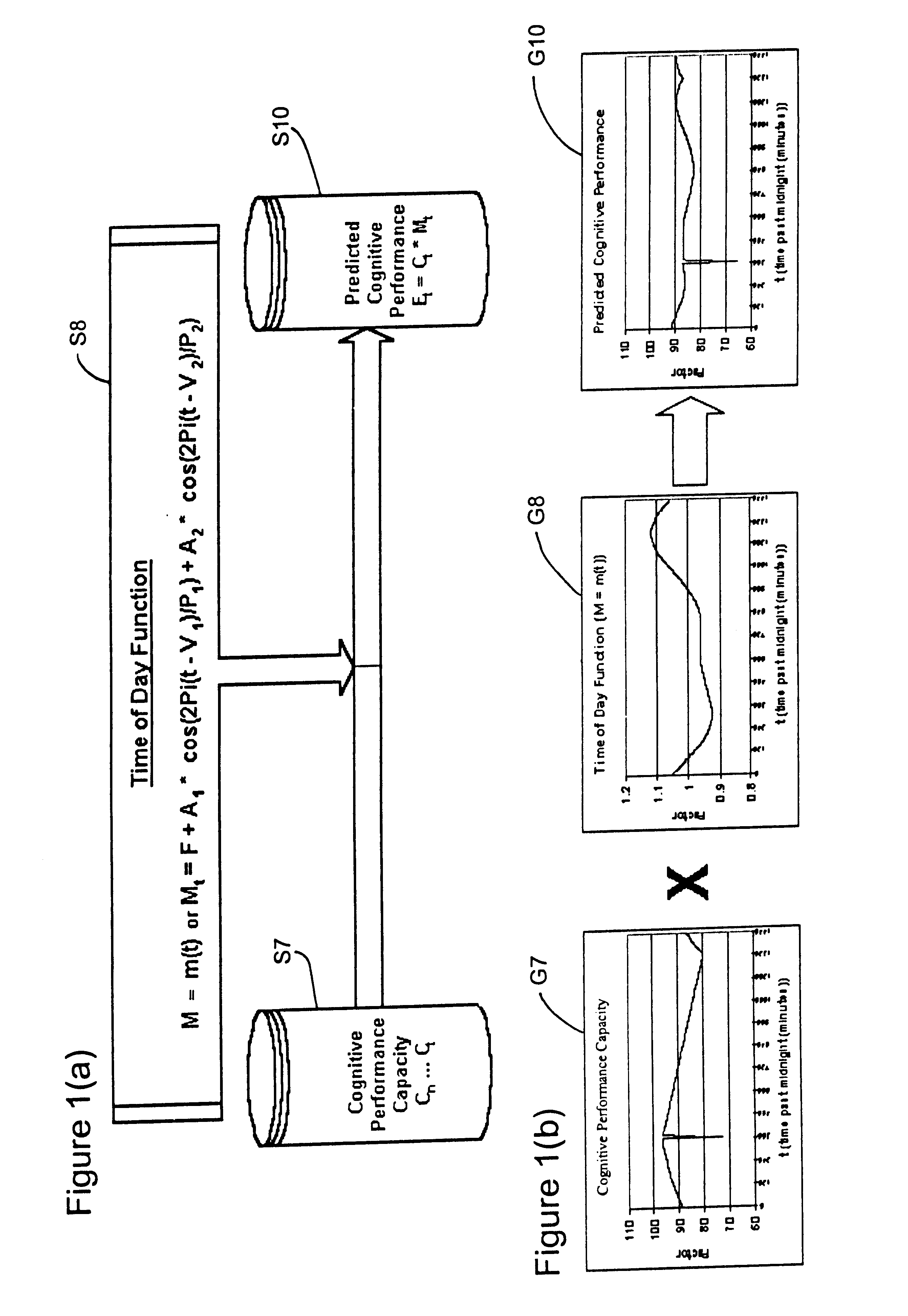
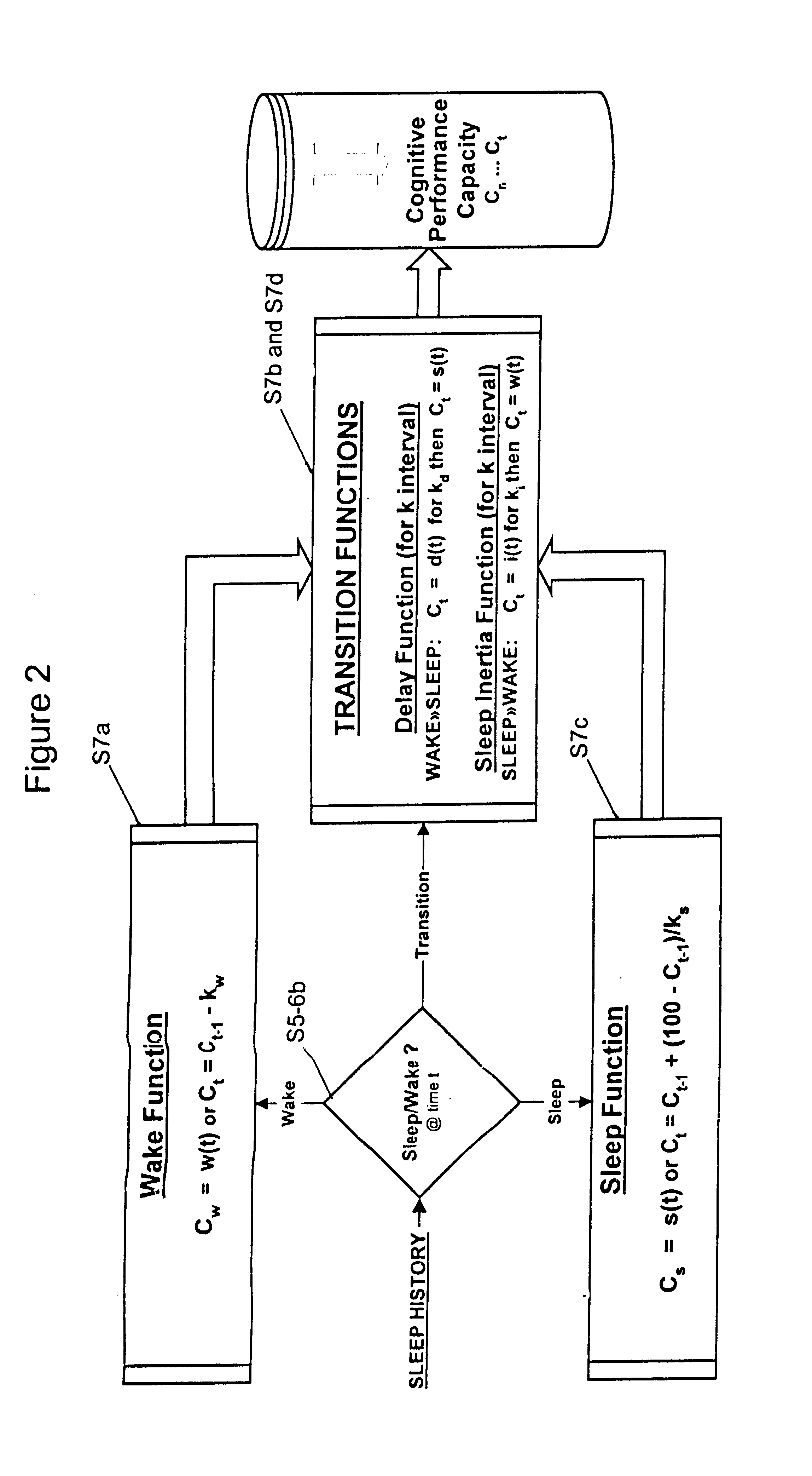
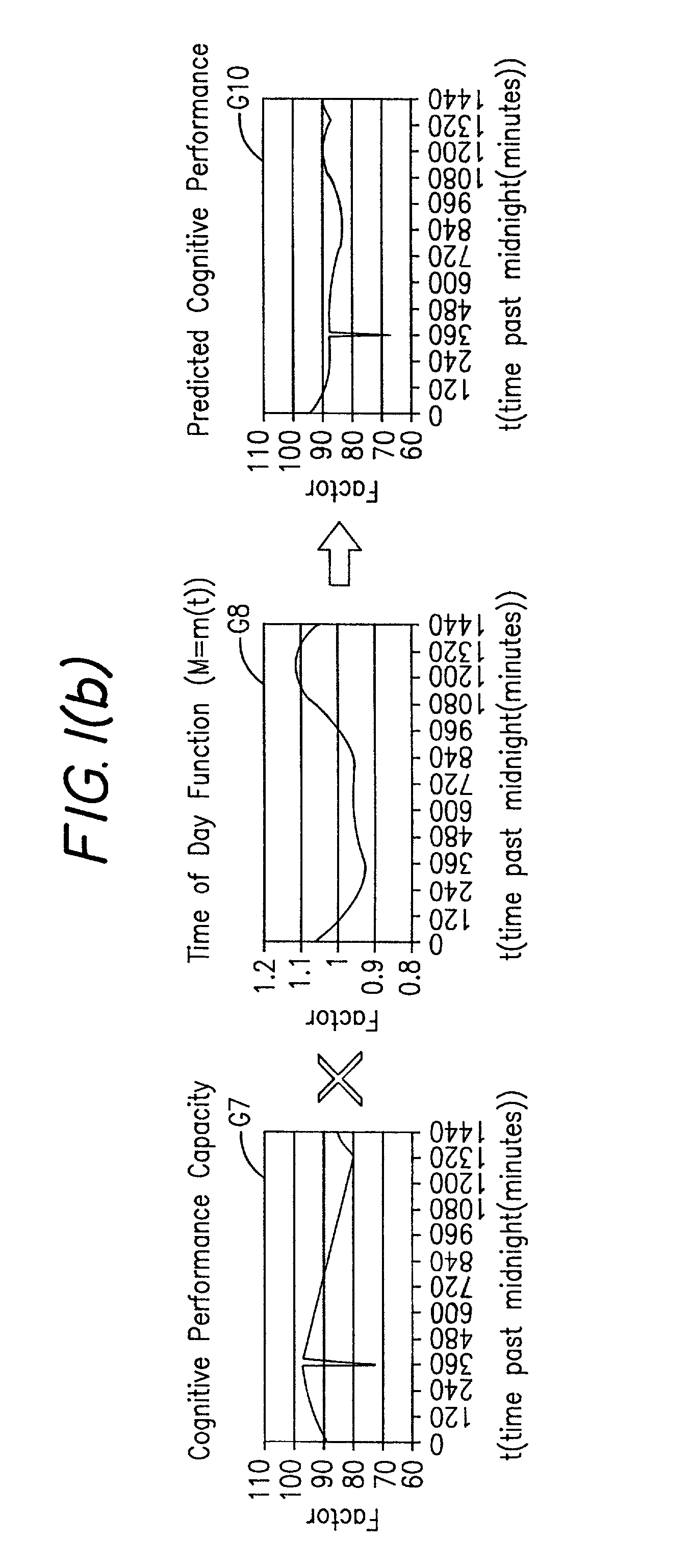
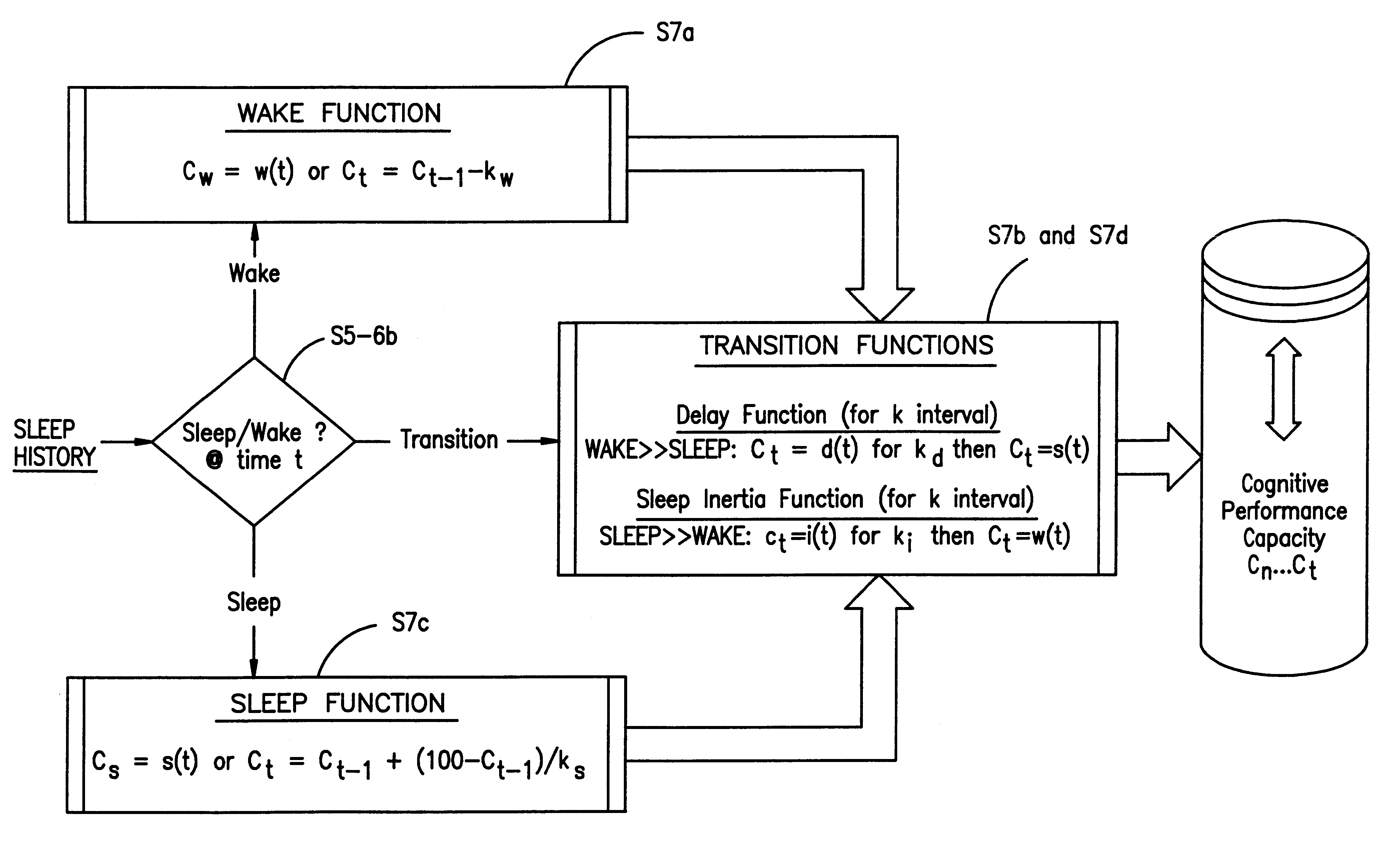
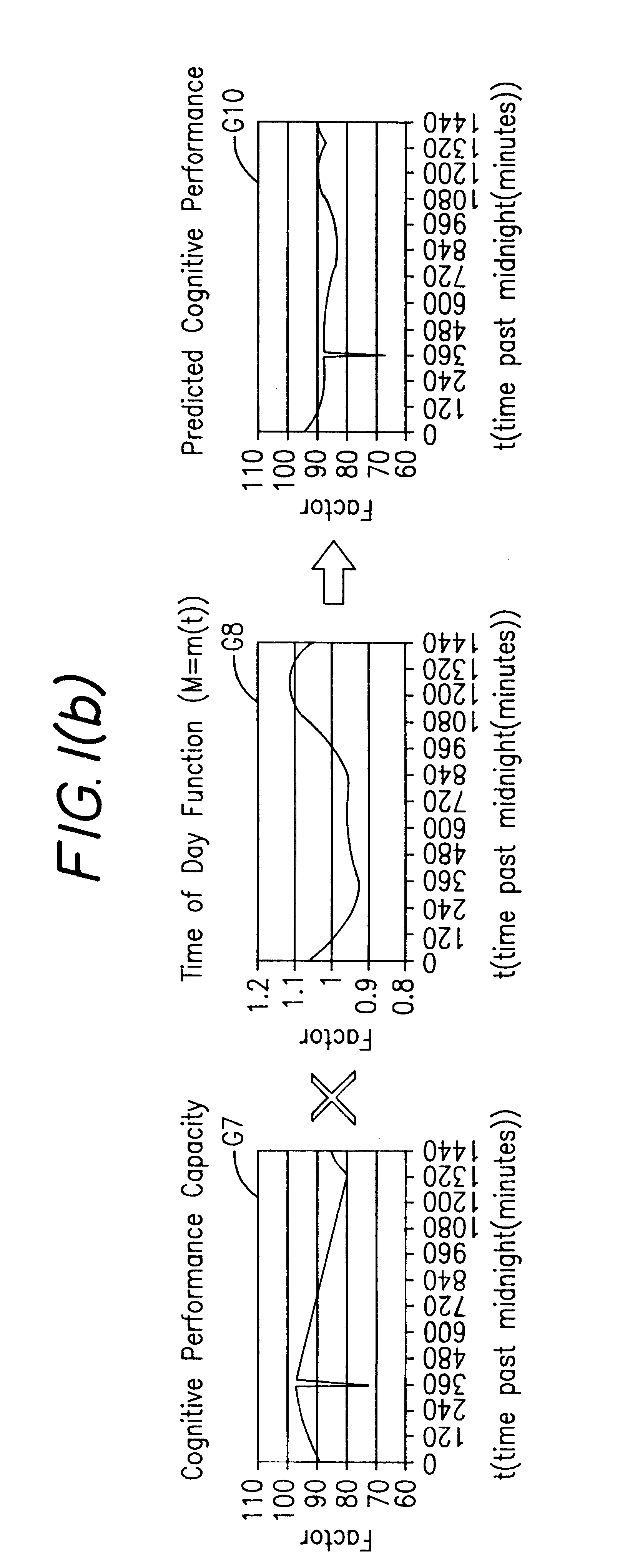
Method and system for predicting human cognitive performance
InactiveUS20020017994A1Easy to adaptMedical simulationData processing applicationsSleep timeSleep duration
An apparatus and method for predicting cognitive performance of an individual based on factors including preferably sleep history, the time of day, and the individual's activities. The method facilitates the creation of predicted cognitive performance curves that allow an individual to set his / her sleep times to produce higher levels of cognitive performance. The method also facilitates the reconstruction of past cognitive performance levels based on sleep history.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
Method and system for predicting human cognitive performance
InactiveUS6530884B2Easy to adaptMedical simulationData processing applicationsSleep timeSleep duration
An apparatus and method for predicting cognitive performance of an individual based on factors including preferably sleep history, the time of day, and the individual's activities. The method facilitates the creation of predicted cognitive performance curves that allow an individual to set his / her sleep times to produce higher levels of cognitive performance. The method also facilitates the reconstruction of past cognitive performance levels based on sleep history.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
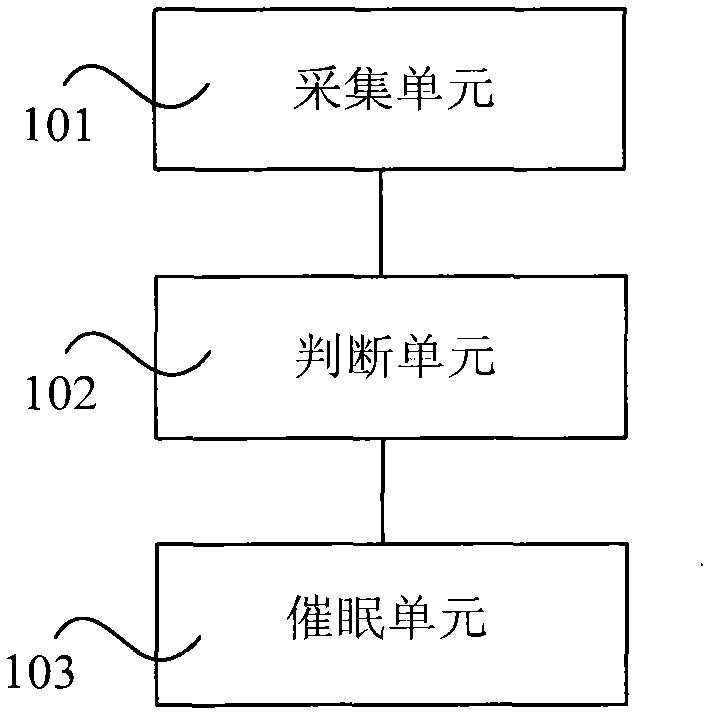
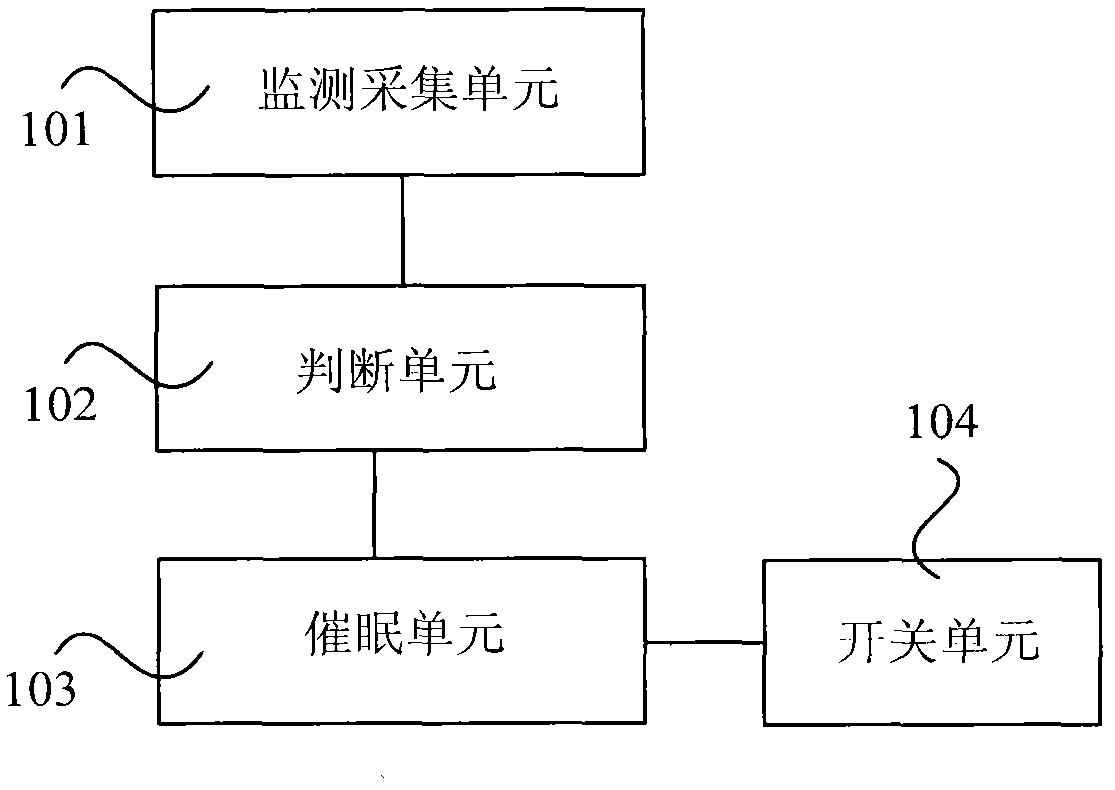
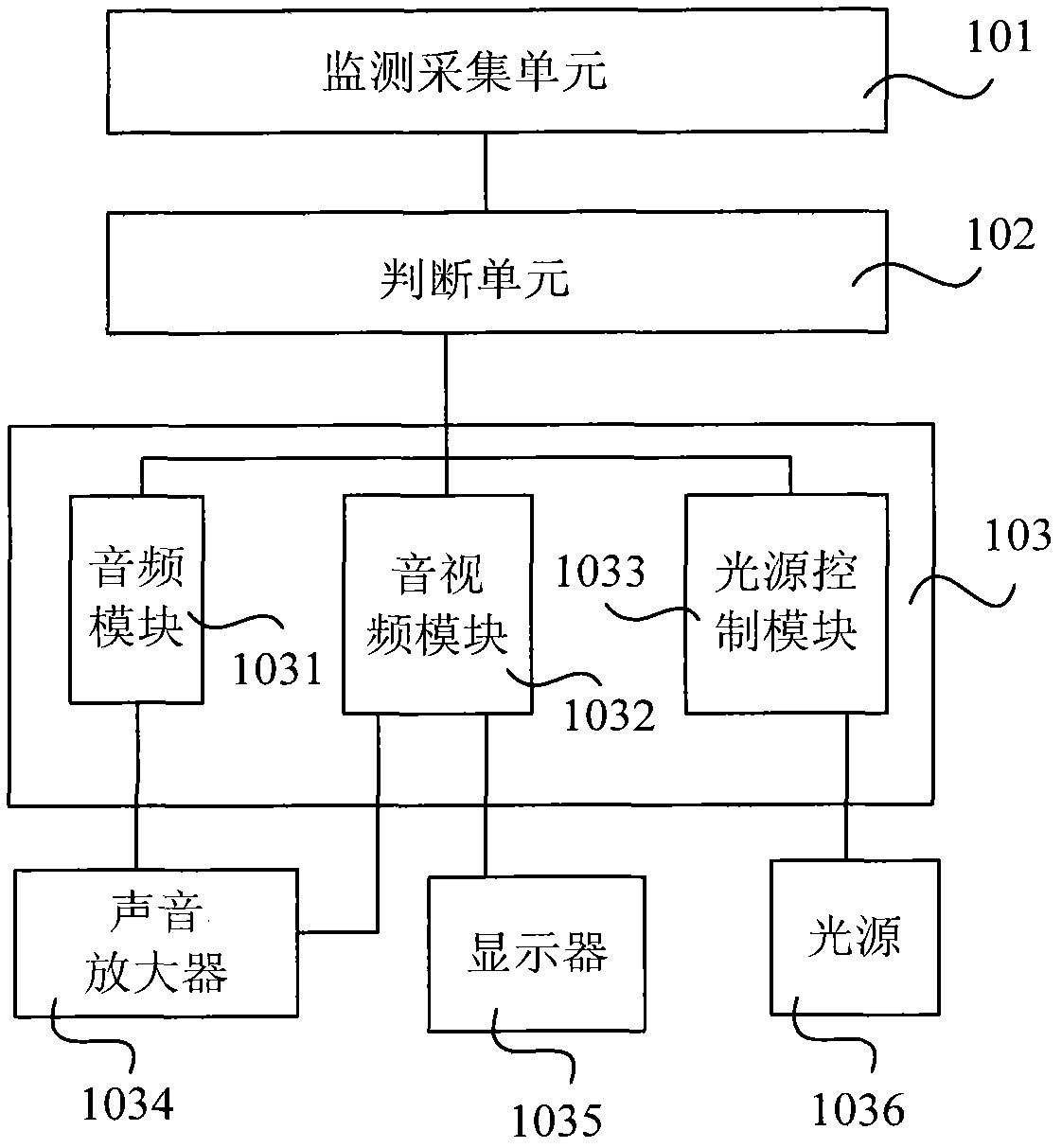
Feedback hypnosis therapeutic instrument
InactiveCN102430182AEnough sleep timeAdequate restSleep/relaxation inducing devicesSleep timeSleep state
The invention provides a feedback hypnosis therapeutic instrument, which comprises a monitoring and acquiring unit, a judging unit and a hypnosis unit, wherein the monitoring and acquiring unit is used for monitoring and acquiring human body physiological parameters; the judging unit is used for judging whether the monitored and acquired human body physiological parameters are within the normal sleeping parameter range of a person; and the hypnosis unit is used for immediately starting hypnosis for a hypnosis object automatically when the monitored and acquired human body physiological parameters are not in the normal sleeping parameter range of the person. The feedback hypnosis therapeutic instrument provided by the invention can be used for performing hypnosis on the hypnosis object in the sleeping process and can be used for performing hypnosis on the hypnosis object who is going to be awake from the sleeping state, so that the hypnosis object reenters the sleeping state, an expected medically-allowed sleeping time range is realized for the hypnosis object, the hypnosis object rest completely, the hypnosis object is in stable sleeping state during sleeping simultaneously, and the sleeping quality of the hypnosis object is improved effectively.
Owner:汪卫东
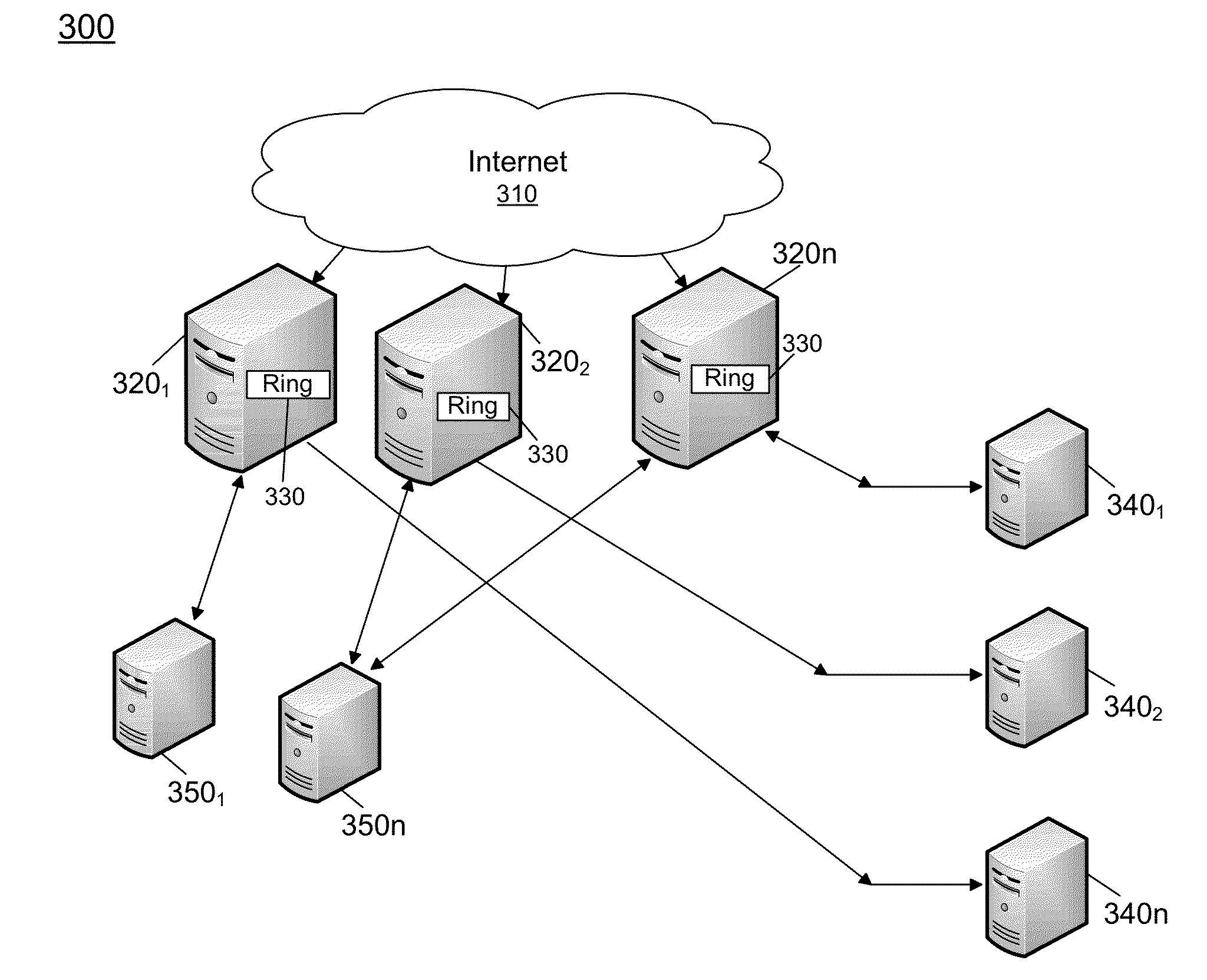
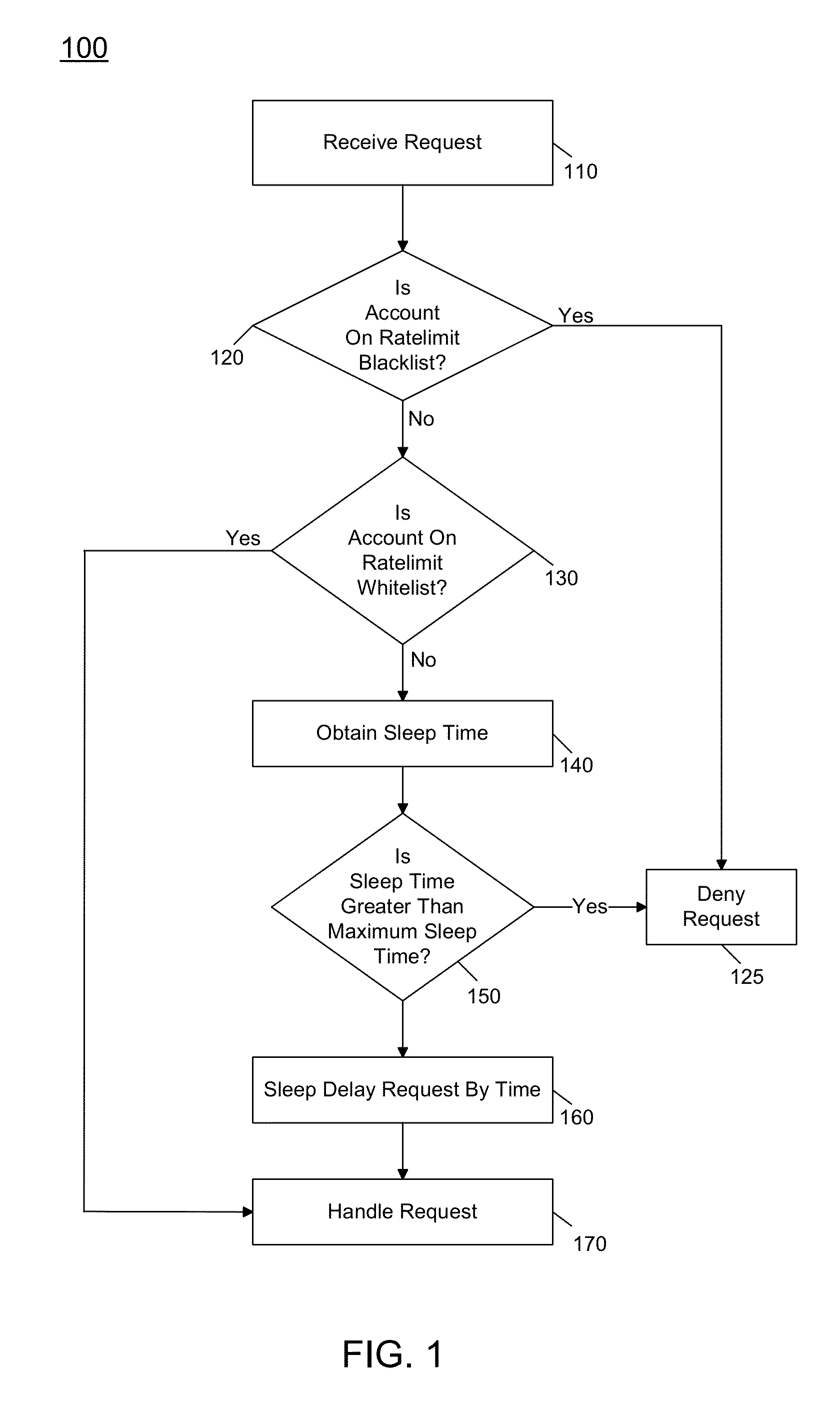
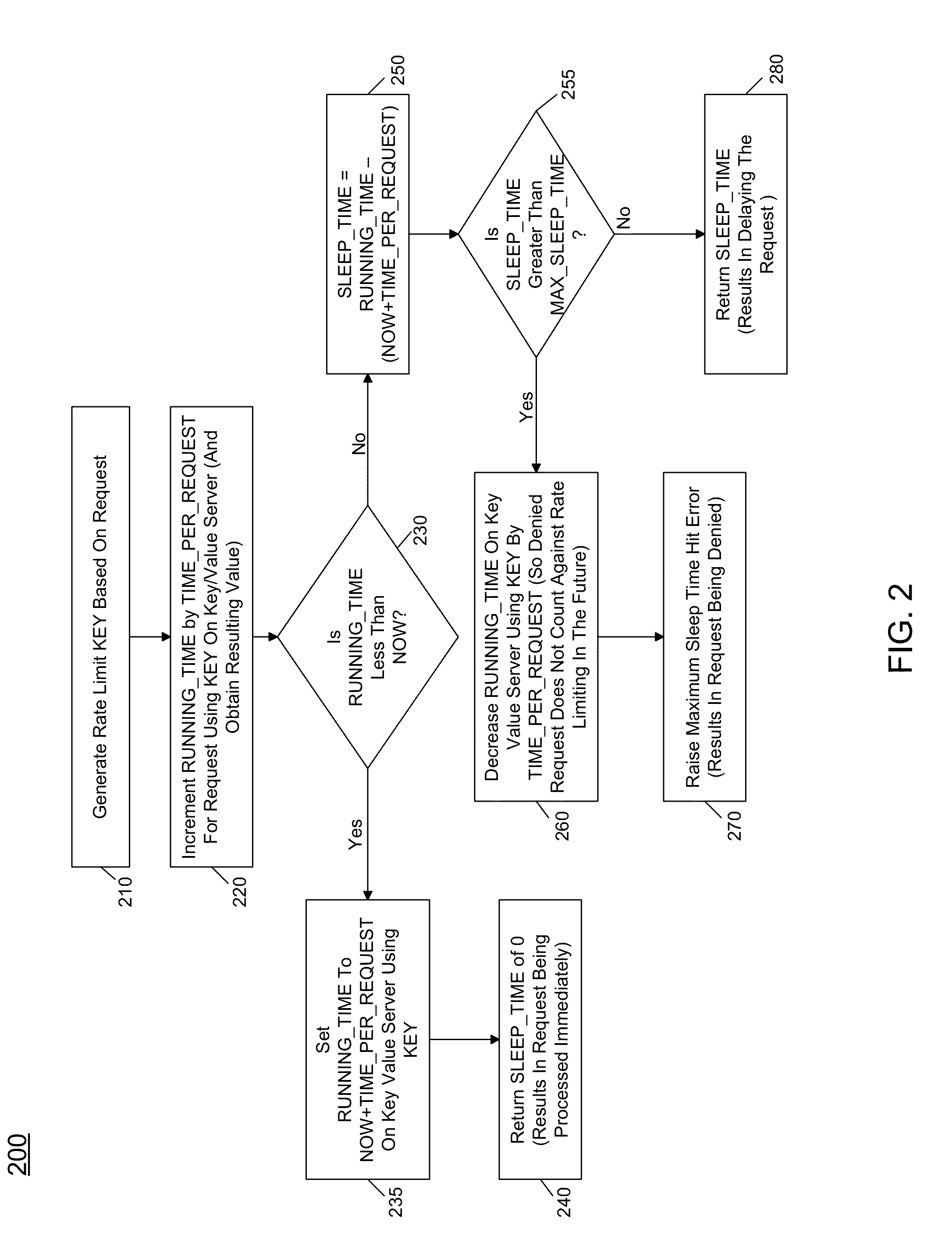
Distributed Rate Limiting Of Handling Requests
In one embodiment, the present invention includes a method for performing rate limiting in a horizontally distributed and scalable manner. The method includes receiving a request in a rate limiter. In turn, a sleep time can be obtained for the request based at least in part on a time value and an allotted time per request, and the request can be delayed according to the sleep time. The time value can be obtained from a distributed key value store using a key generated from the request. After this sleep time, the request can be forwarded from the rate limiter to the handling server.
Owner:RACKSPACE US
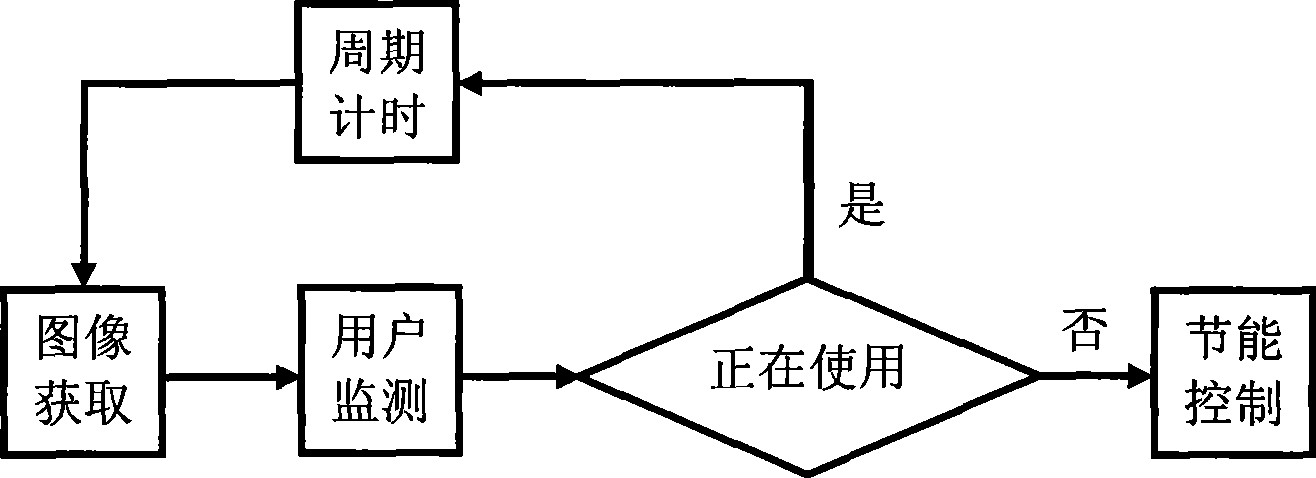
Computer intelligent energy-conserving method
ActiveCN101458560AMonitor usage statusRealize smart energy savingEnergy efficient ICTCharacter and pattern recognitionSleep timePower management system
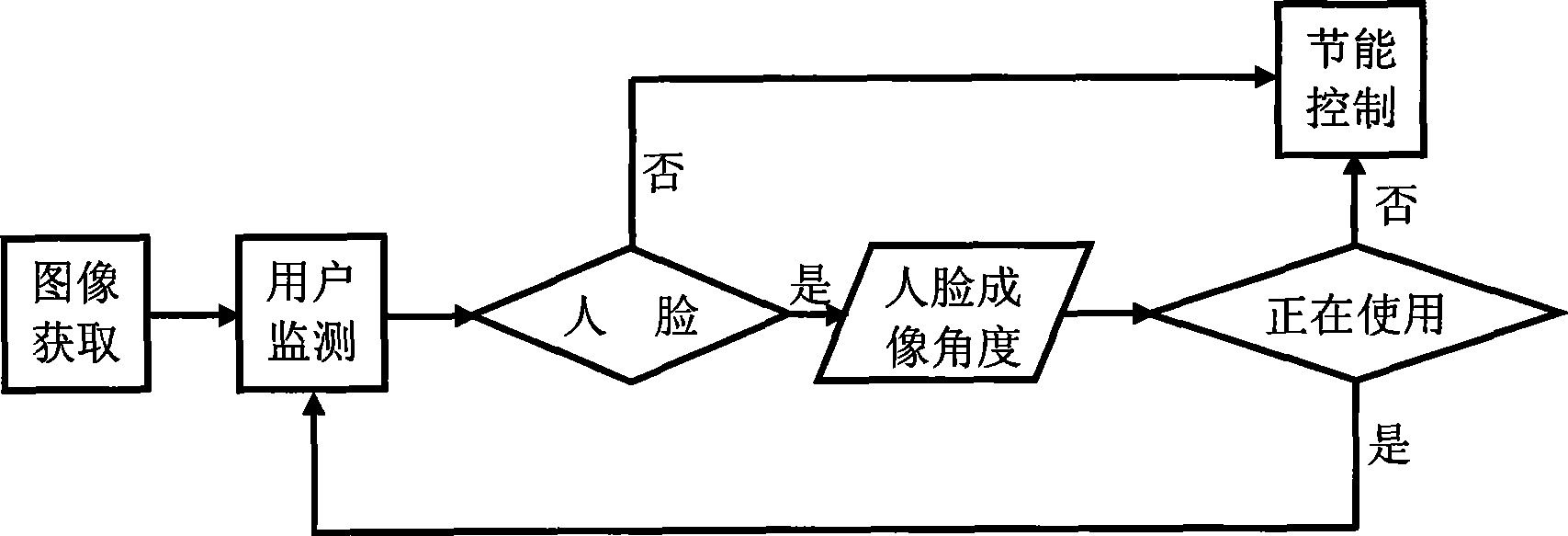
The invention relates to a computer save energy method. The method includes steps as follows: an image information collected by an image obtaining module is sent to a user monitor module, the user monitor module scans the image information and sends result to an energy saving control module, if no facial image, the energy saving control module processes energy saving control to computer, if facial image being, the energy saving control module keeps normal working state of computer. The method solves problem that computer consumes energy still when a user is disturbed by something and the computer is not turned off or is adjusted to waiting, sleeping modes in computer power management system with existing technique, and waiting or sleeping time interval is overlong, and inconvenient using caused by user using manual switching energy saving mode. The method has energy saving function with human-computer communication mode, the computer is controlled to enter energy saving mode when no people is ahead on the computer or people does not operate computer, and can realize energy saving control when user leaves and using computer when user comes, the method is convenient and can save energy efficiently.
Owner:NANJING UNARY INFORMATION TECH
Low-power dissipation media access control method of node dynamic state resting
InactiveCN101232518AReduce transmissionImprove Clock Synchronization AccuracyTime-division multiplexTransmissionWork cycleCarrier signal
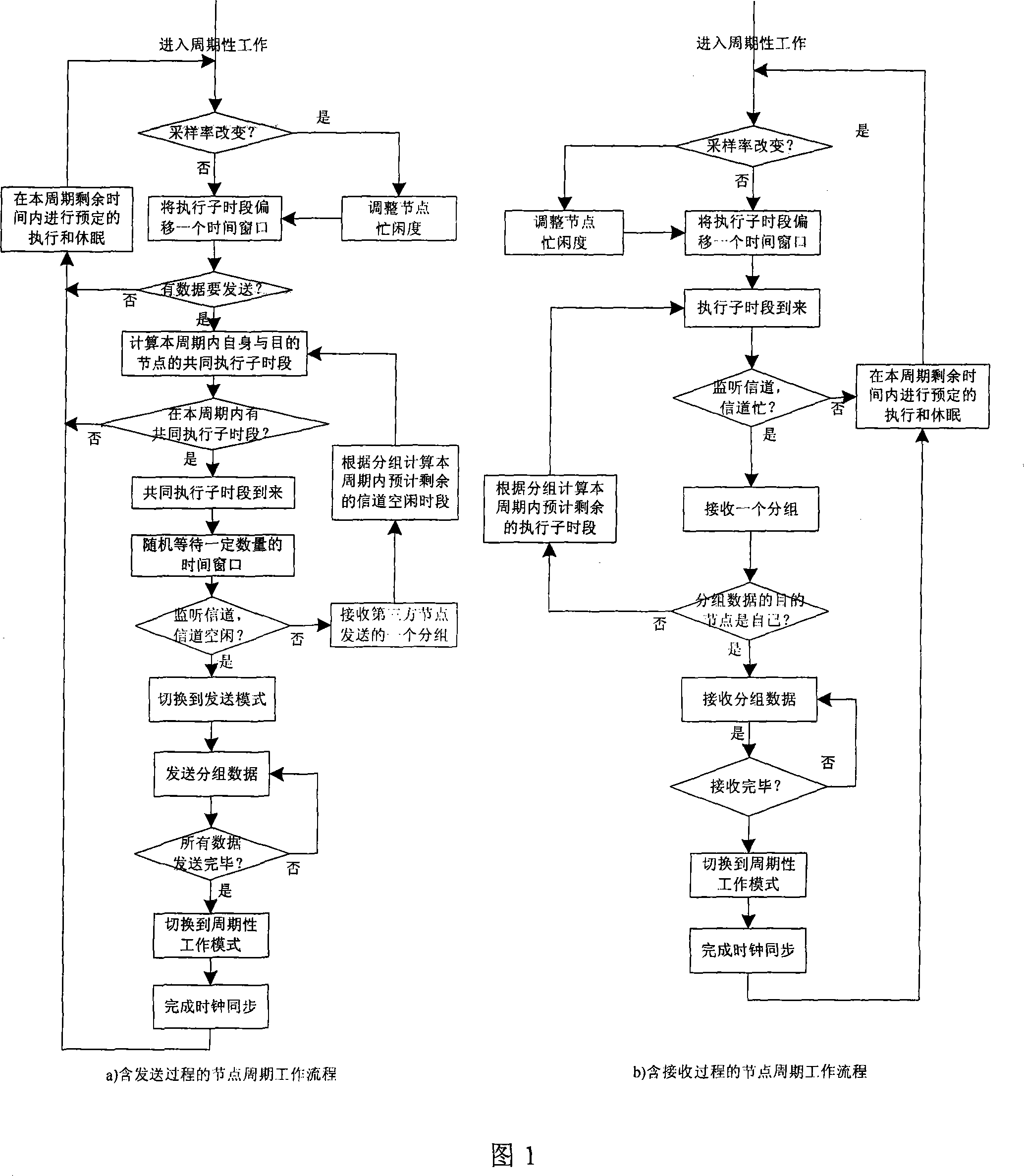
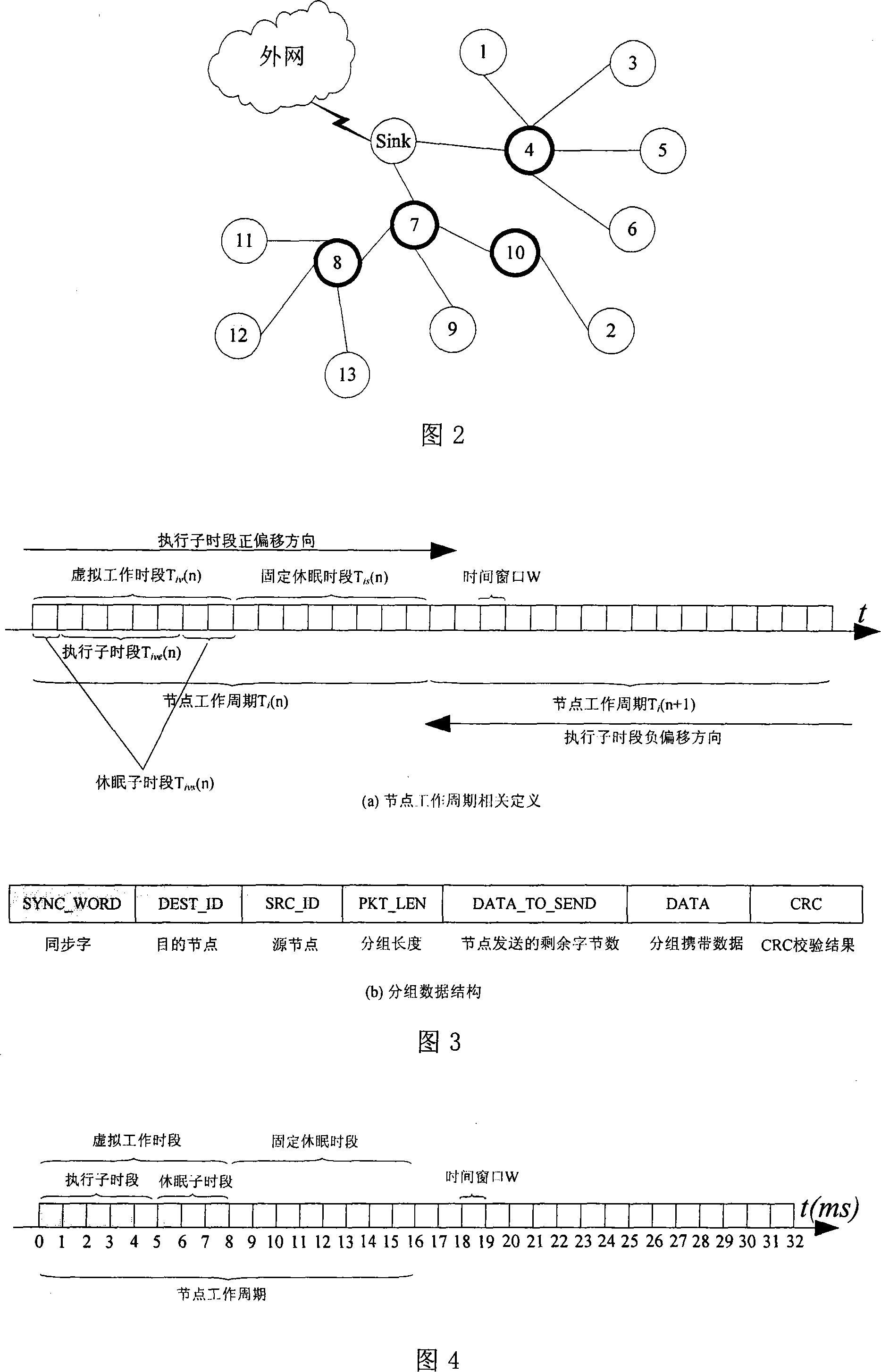
A low-power media access control method of node dynamic sleeping includes the following steps: (1) organizing the network topology to clustering topology and realize a coarse-grained clock synchronization between the node inside the cluster and the cluster head and make the node work and sleep periodically; (2) the nodes have three operating modes: a sending mode, a receiving mode and a cycle work mode, wherein the node of the cycle work mode is characterized in that the nodes work or sleep periodically and the actual work and sleep time period of the nodes changes dynamically and the operation sub-time-period of the neighboring node can be calculated; (3) in one work cycle, the operation sub-time-period of any two adjacent nodes can be overlapped to guarantee the communication; (4) the node can intercept the packet sent by the adjacent node and adjust the sleep time period according to the information carried by the packet to reduce the carrier interception times; (5) dynamically adjusting the busy and idle degree of the node according to different data sampling rates so as to reduce the power consumption while guaranteeing the throughput. The method, which is simple and reliable, has advantages of low power consumption, short delay, strong adaptive capacity and effectively prolonged life cycle of the network.
Owner:BEIHANG UNIV
Method for realizing communication by controlling multiple communication systems, and user equipment
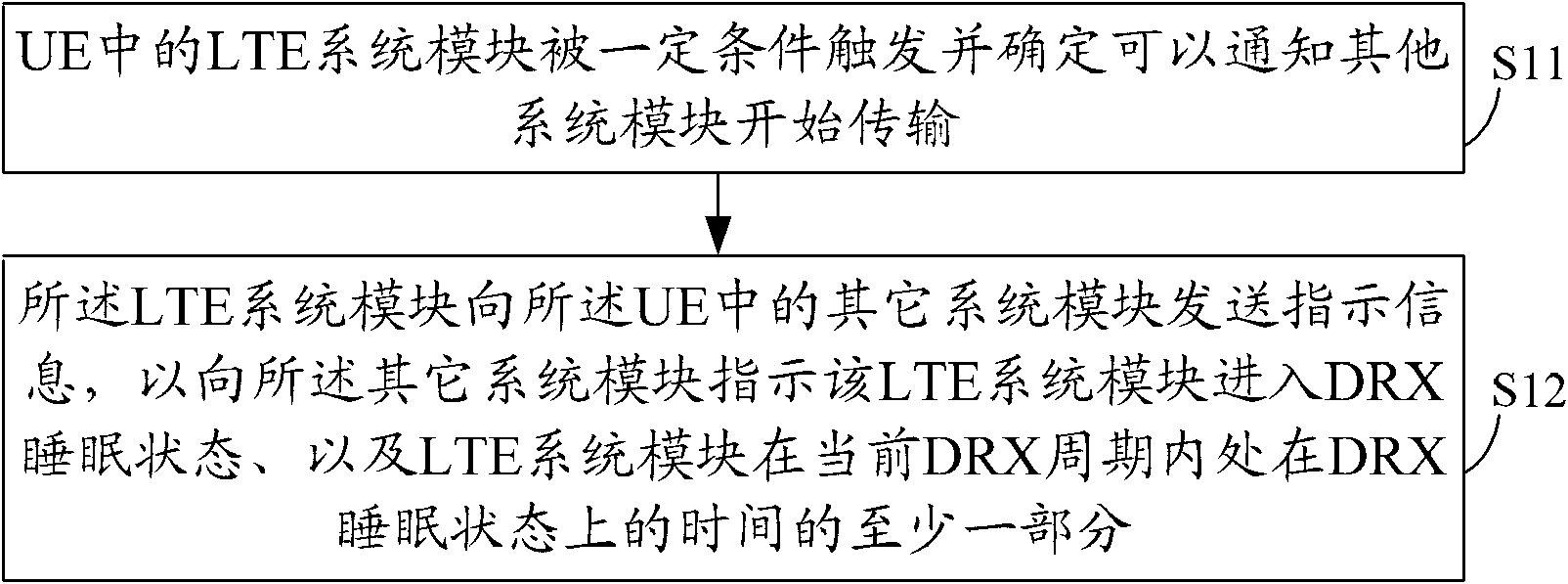
ActiveCN102421148AReduce mutual interferenceImprove resource utilization efficiencyPower managementNetwork traffic/resource managementSleep timeCommunications system
The embodiment of the invention discloses a method for realizing communication by controlling multiple communication systems, and user equipment. The method comprises the step: when a long term evolution (LTE) system module in the UE is about to enter a discontinuous reception (DRX) sleep state or transiently stops data transmission, the LTE system modules sends first indication information to other system modules in the UE, wherein the first indication information is used for indicating the conditions that the LTE system module enters the DRX sleep state and the LTE system module is in at least one part of time of the time on the DRX sleep state for other system modules, or the first indication information is used for indicating that the other system modules can carry out data transmission and indicating the time of carrying out data transmission by the other system modules. By adopting the method, the other system modules can fully utilize sleep time of the LTE system modules for carrying out communication, thus mutual interference between the two kinds of systems is reduced, and resource utilization efficiency is increased.
Owner:HONOR DEVICE CO LTD
Method of improving sleep disordered breathing
ActiveUS20090118785A1Improve sleepingElectrotherapySurgerySleep disordered breathingSommeil paradoxal
A diaphragm pacing stimulatory method and a system to implement the method are provided to improve respiratory function and the quality of sleep in patients whose sleep is compromised by poor respiration. The diaphragm pacing method includes adaptations that make it particularly compatible with the onset of sleep and sustaining sleep. Embodiments of the method are operated independently of breathing effort the patient may make during sleep. Patients for whom the invention is appropriate include those with a neuromuscular disease, such as amyotrophic lateral sclerosis (ALS). System elements include an external electrical stimulator coupled to one or more implanted electrodes that stimulate diaphragm contraction. The system and method provide for a pacing of the diaphragm, improved breathing, and improved sleep. Features of improved sleep include longer sleep time, an increased amount of REM sleep, and fewer episodes of wakefulness and restlessness.
Owner:SYNAPSE BIOMEDICAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com