System and method for protecting against dictionary attacks on password-protected TPM keys
a dictionary attack and password-protected technology, applied in the field of system and method for protecting against dictionary attacks on password-protected tpm keys, can solve the problems of unable to keep backup copies of keys, keys are rendered useless, and keys must be regenerated
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
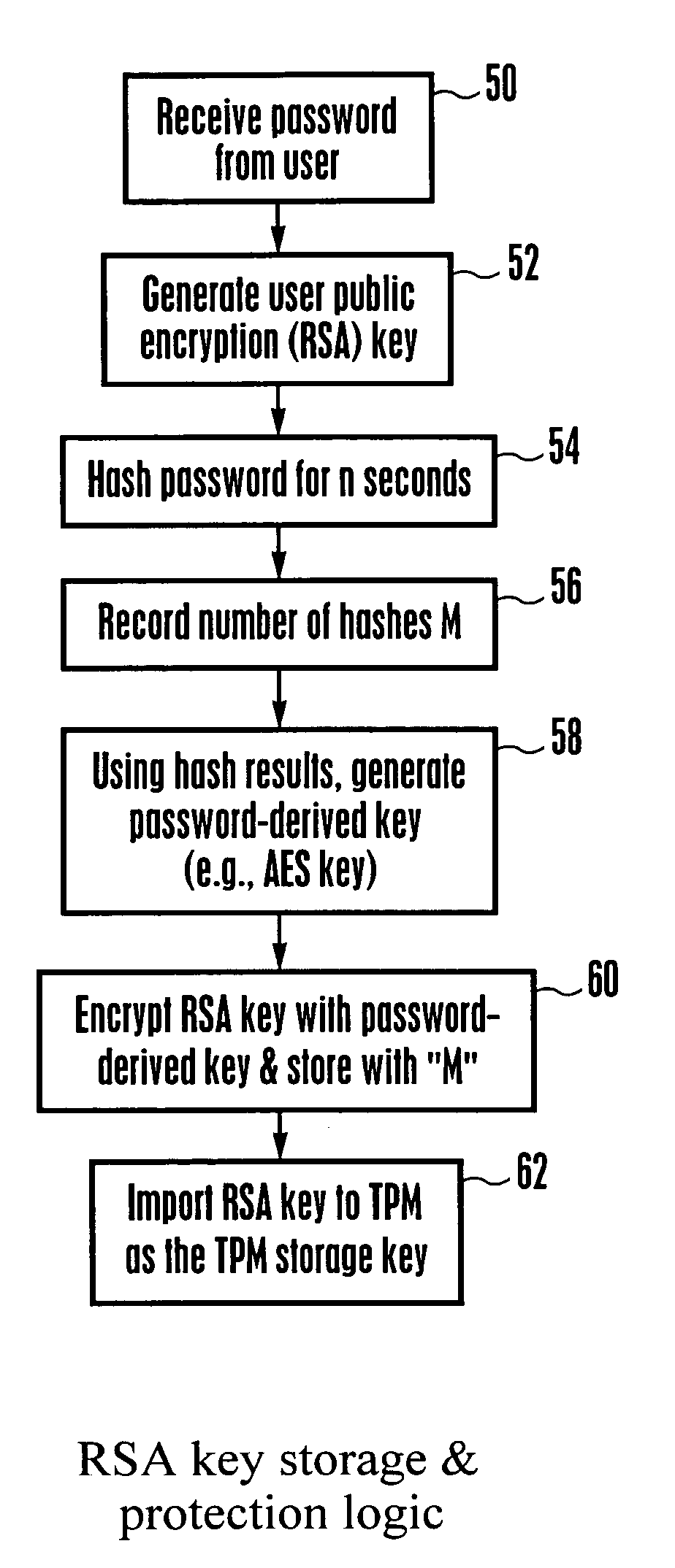
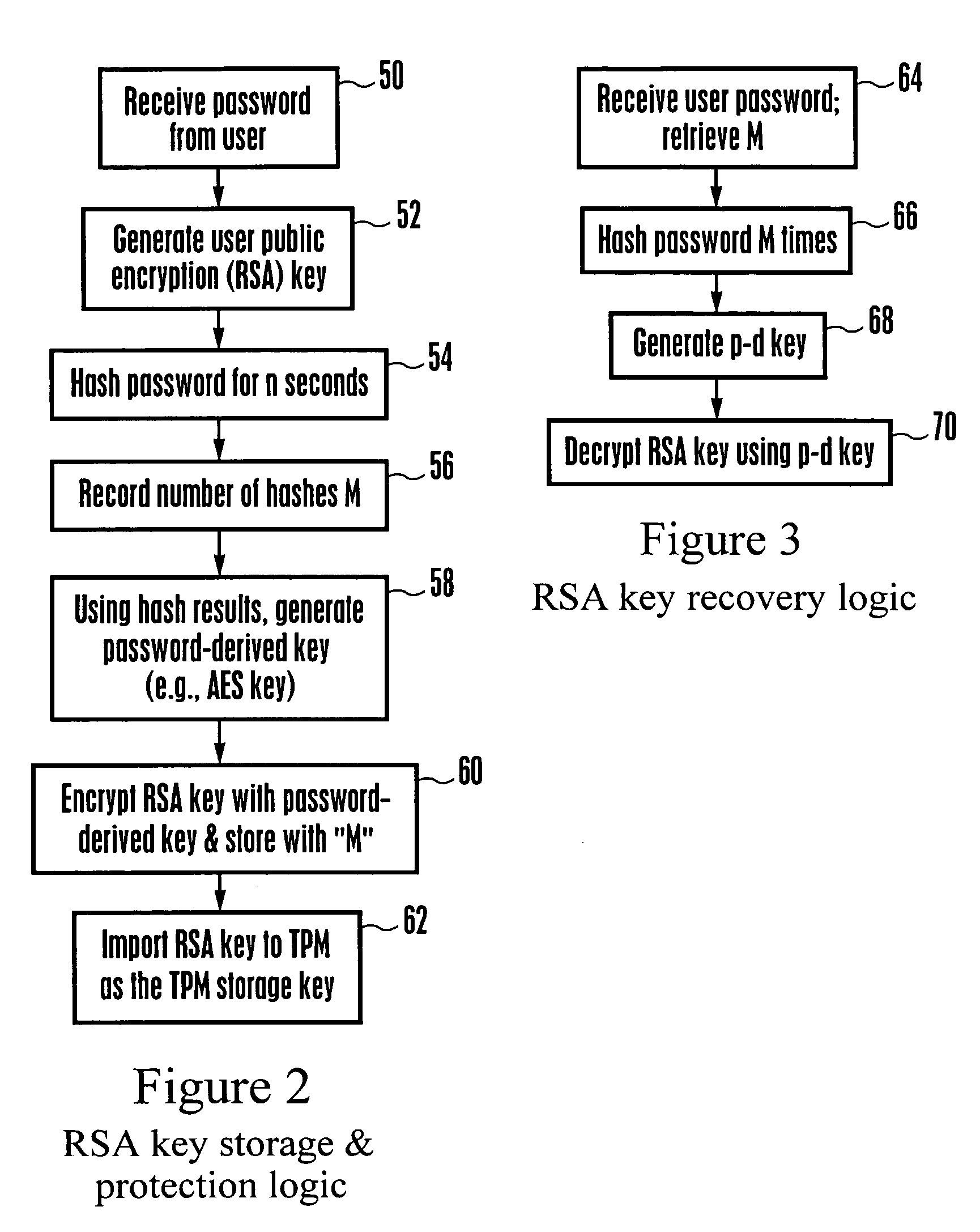
Embodiment Construction
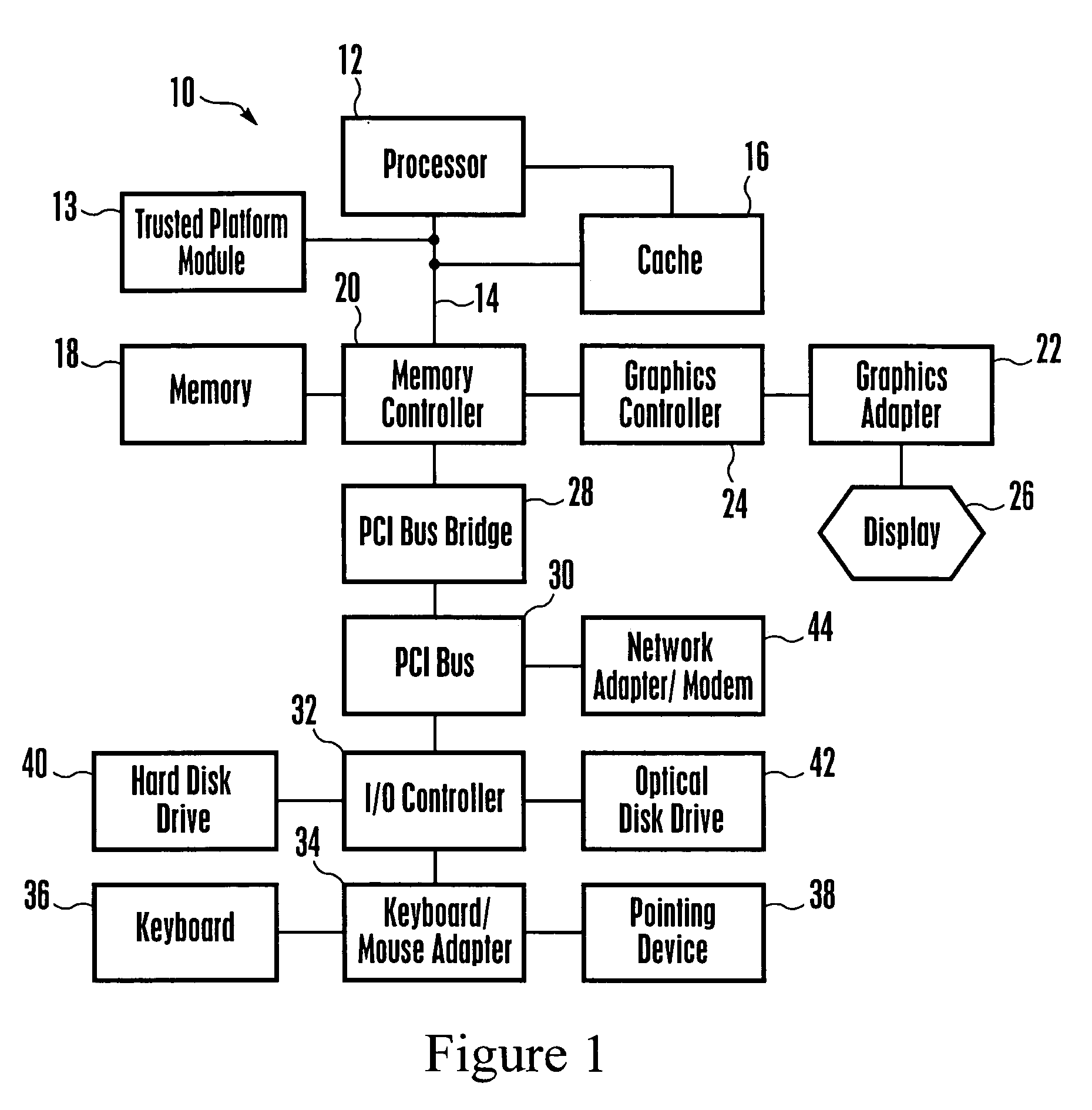
[0014] Referring initially to FIG. 1, a high-level block diagram of a data processing system, generally designated 10, is shown in which the present invention may be implemented. The system 10 in one non-limiting embodiment is a personal computer or laptop computer, and can function as the below-described recording computer and / or reading computer. The system 10 includes a processor 12, which may be, without limitation, a PowerPC processor available from International Business Machines Corporation of Armonk, N.Y. (or other processors made by, e.g., Intel or AMD and common to the industry). The system 10 may also include a trusted platform module (TPM) 13 that may be implemented by a chip, for providing security functions in accordance with TPM principles known in the art, including the encryption, using a security key, data to be stored in the system 10.
[0015] The processor 12 and TPM 13 may be connected to a processor bus 14, and a cache 16, which is used to stage data to and from...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com