Verification method and system for second-level cache interface protocol
A technology of secondary cache and interface protocol, applied in the field of multi-core verification, can solve the problems of low debugging efficiency, consuming a lot of time and energy, affecting the progress of the project, etc., to achieve the effect of improving debugging efficiency and effective and rapid positioning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] This embodiment provides a verification method of a secondary cache interface protocol. When the method checks the read data, it records the key information of each read request, and compares the data of the memory model with the DUT data when the read data is returned, and performs When the wake-up request is checked, it is checked through the protocol agreement; when the method checks the data of the D or C channel, the data of the memory model is compared with the DUT data, and when the rationality of the B / C channel is checked, it is judged according to the content of the secondary cache .
[0048] This embodiment checks the read data, records key information such as the address of each read request, flag bits, etc., when the read data returns, query the recorded read request information through the flag bits, and read the data of the memory model according to the queried address , and compared with the DUT data.
[0049] The check of the wake-up request in this em...
Embodiment 2
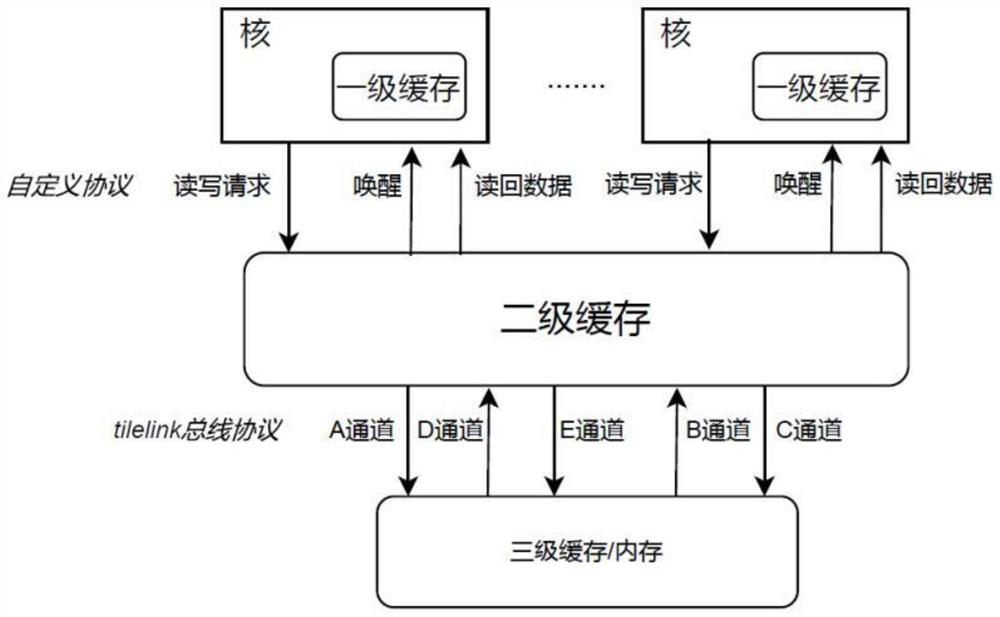
[0055] At the specific implementation level, this embodiment provides a secondary cache interface structure, such as figure 1 Shown:
[0056] In this embodiment, the interface between the secondary cache and the core is a custom protocol, including a read request signal sent from the core, a write request signal, a wake-up signal returned by the secondary cache, and a read-back data signal. The secondary cache can be connected to multiple cores, and the number of cores can be configured.
[0057] In this embodiment, the interface between the second-level cache and the third-level cache or memory is a tilelink bus protocol interface. This protocol is mainly used in the RISCV architecture and includes five channels of A / B / C / D / E.
[0058] In this embodiment, channel A is a read-write request channel, which includes information such as read-write addresses, write data, and request types.
[0059] In this embodiment, channel B is a snoop request channel, and includes information ...
Embodiment 3
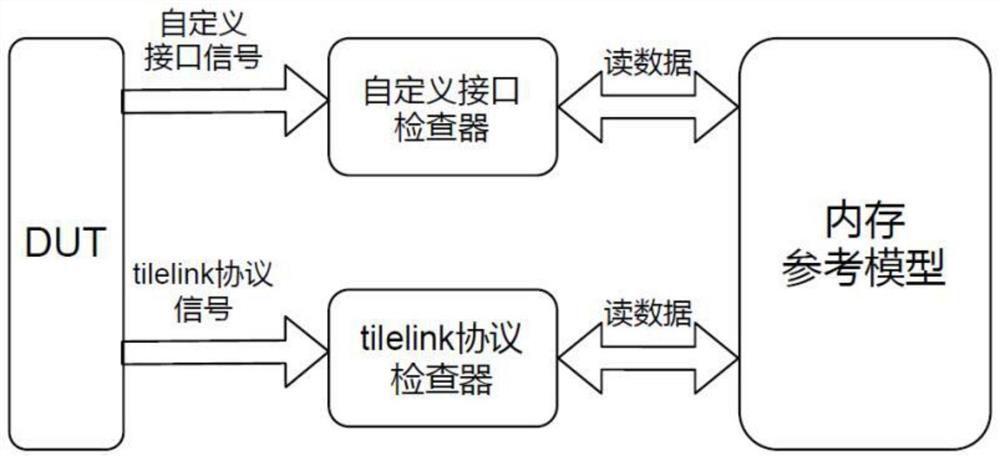
[0065] At the specific implementation level, this embodiment provides a checker structure, such as figure 2 Shown:
[0066] In this embodiment, a custom interface checker is used to monitor the correctness of the custom interface signal.
[0067] The inspection process of the read data in this embodiment:
[0068] a. When the core sends a read request signal to the L2 cache, the checker stores the read address, read flag, and read request type into the read request queue;
[0069] b. When the second-level cache returns the read data, monitor the flag bit of the returned information and traverse the read request queue at the same time. If there is a valid request flag bit in the read request queue that is the same as the flag bit of the returned information, it means that the returned data corresponds to the read request;
[0070] c. Obtain the address and read request type information from the read request with the same flag bit. If the read request type is a write upgrade...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com