System encrypted method using multifunctional assistant SCM
An encryption method and single-chip technology, applied in computer security devices, protection of internal/peripheral computer components, instruments, etc., can solve the problems of easy COPY, less time required, etc., and achieve simple functions, improved security, and high safety factor. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
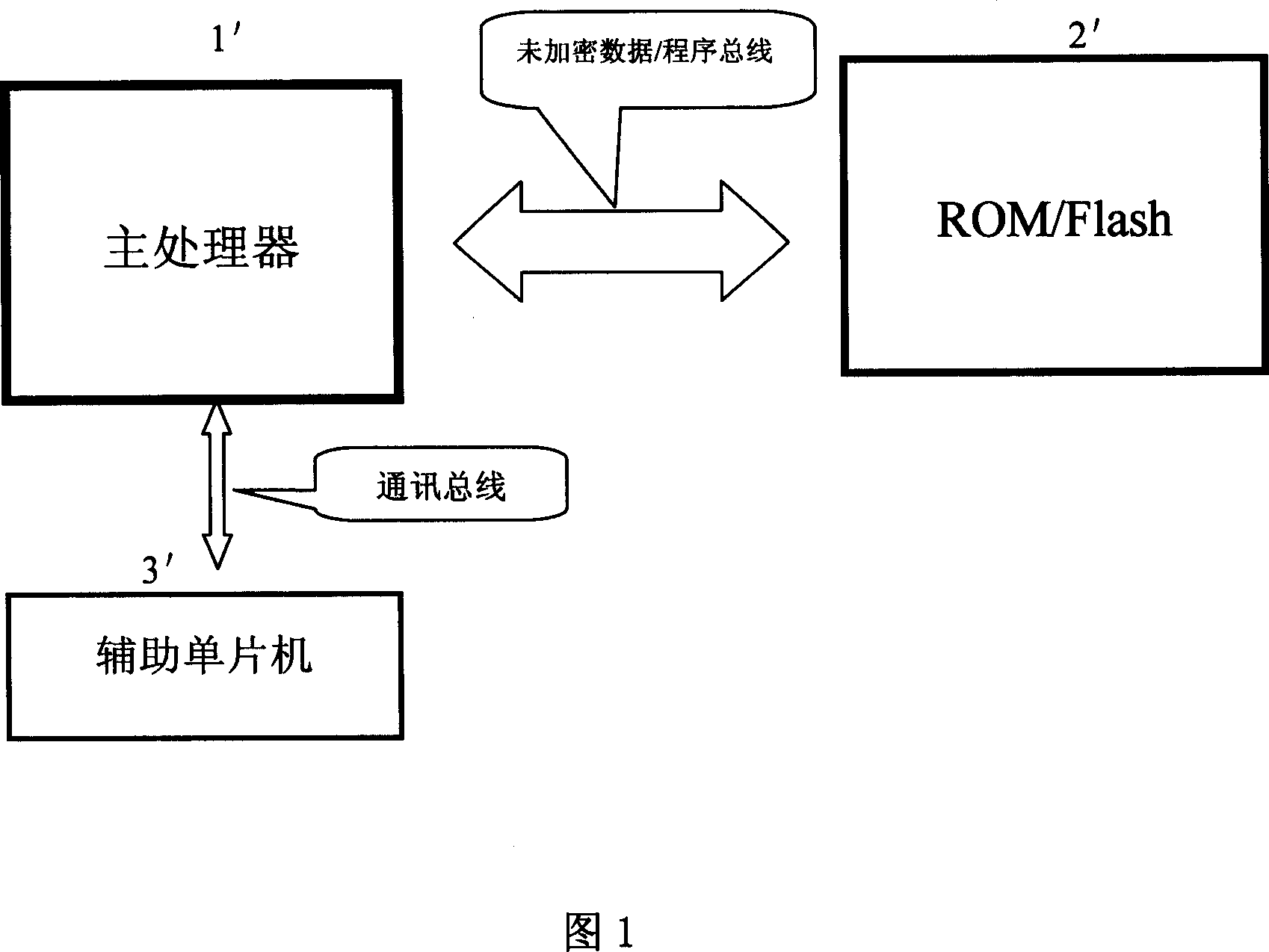
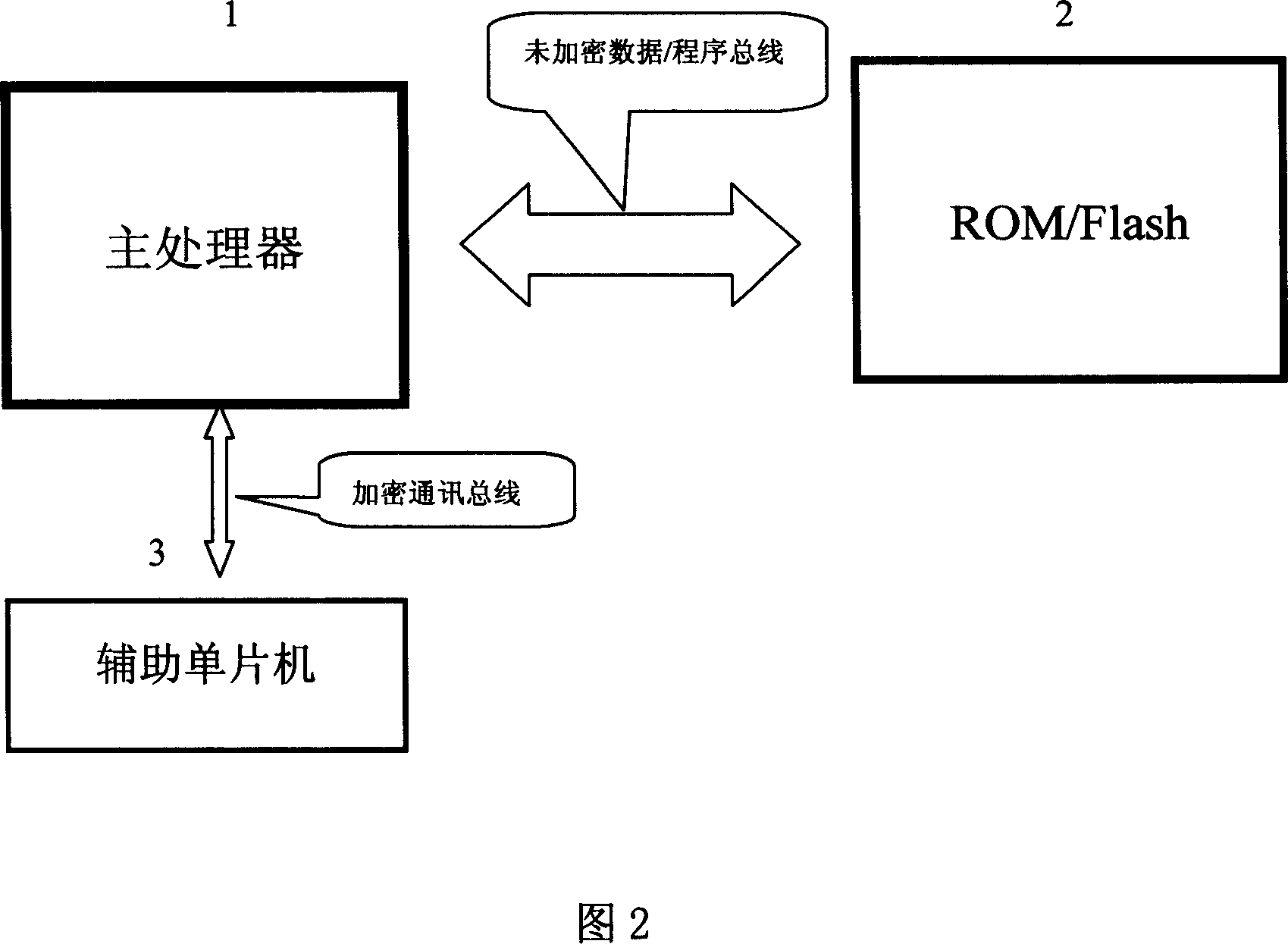
[0033] Embodiment one, referring to Fig. 2 to shown in Fig. 4, a kind of system encryption method that adopts multi-purpose auxiliary single-chip microcomputer of the present invention, is on the basis of using the single-chip microcomputer with built-in burning (anti-reading) program memory, by The main processor program and the auxiliary single-chip microcomputer program add the password verification method of the agreed encryption protocol algorithm, so that the system program cannot be read or copied, and the purpose of system encryption is achieved. The system hardware usually includes the main processor 1, ROM The / Flash program memory 2 and the auxiliary single-chip microcomputer 3 adopt unencrypted mode communication and storage between the main processor 1 and the external program memory 2, so that maintenance work such as modification and upgrading of the software can be facilitated. All key points in the software running of the main processor 1 are cryptographically ...
Embodiment 2
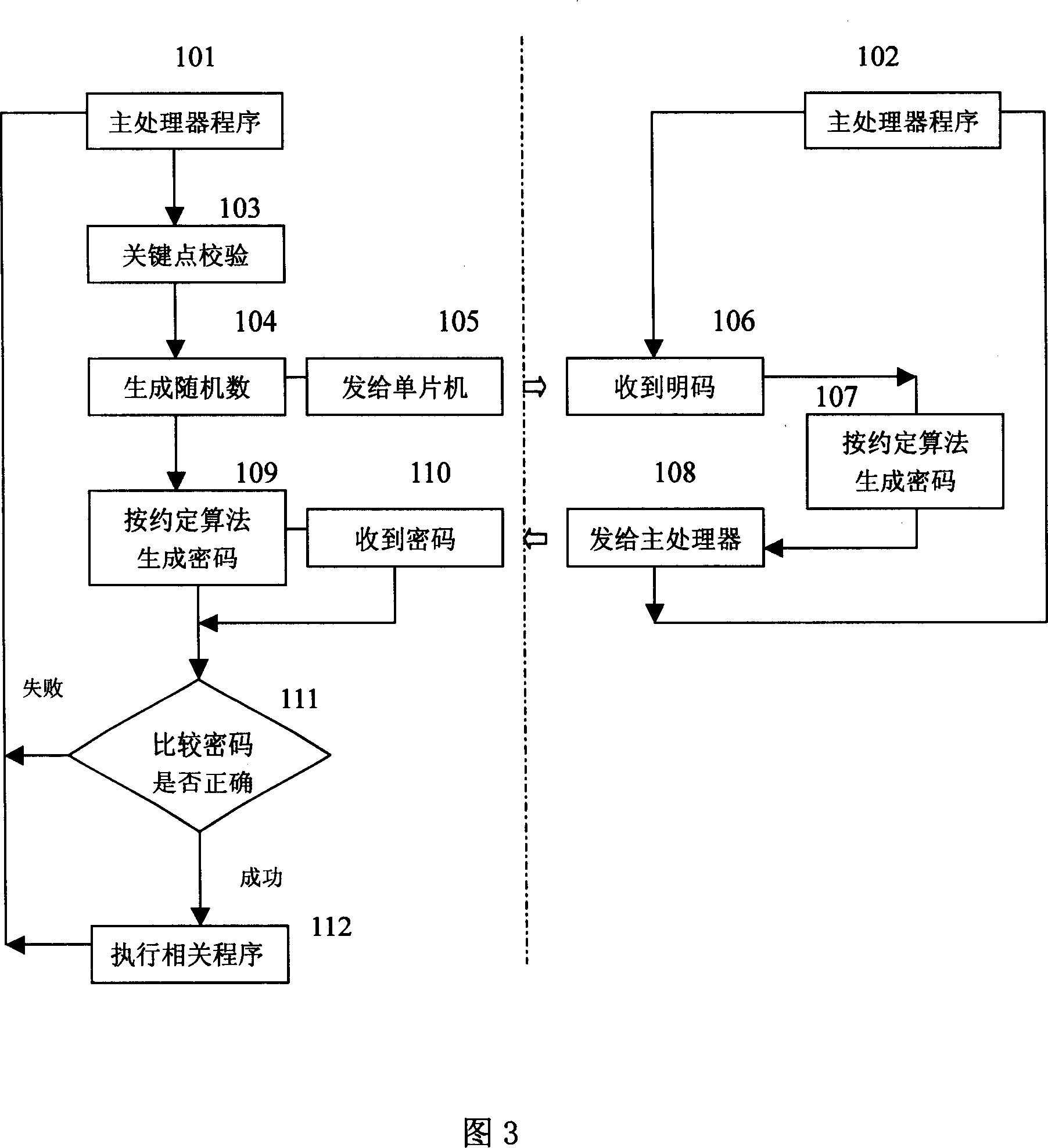
[0054] Embodiment two, referring to Fig. 6, a kind of system encryption method that adopts multi-purpose auxiliary single-chip microcomputer of the present invention, differs from embodiment one in that the encryption protocol algorithm adopted is a reversible algorithm; therefore,
[0055] In step e: the main processor 1 decrypts and restores the password sent by the auxiliary single-chip microcomputer 3 into a plain code according to the encryption protocol algorithm of the reversible algorithm, and compares the decrypted and restored plain code with the original plain code;
[0056] In step f: when the corresponding two plain codes are consistent, the main processor 1 continues to run the follow-up program or includes repeating step c;
[0057] When the two corresponding plain codes are inconsistent, the main processor 1 refuses to run the follow-up program, and the system stops running.
[0058] Fig. 6 is a schematic flowchart of the encryption of the reversible algorithm;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com