Private file encryption method and private file encryption device
A file encryption and file technology, applied in the Internet field, can solve the problems of private file information leakage, cumbersome encryption process, and inability to apply for file encryption, etc., and achieve the effect of simple encryption process and avoiding the leakage of private files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
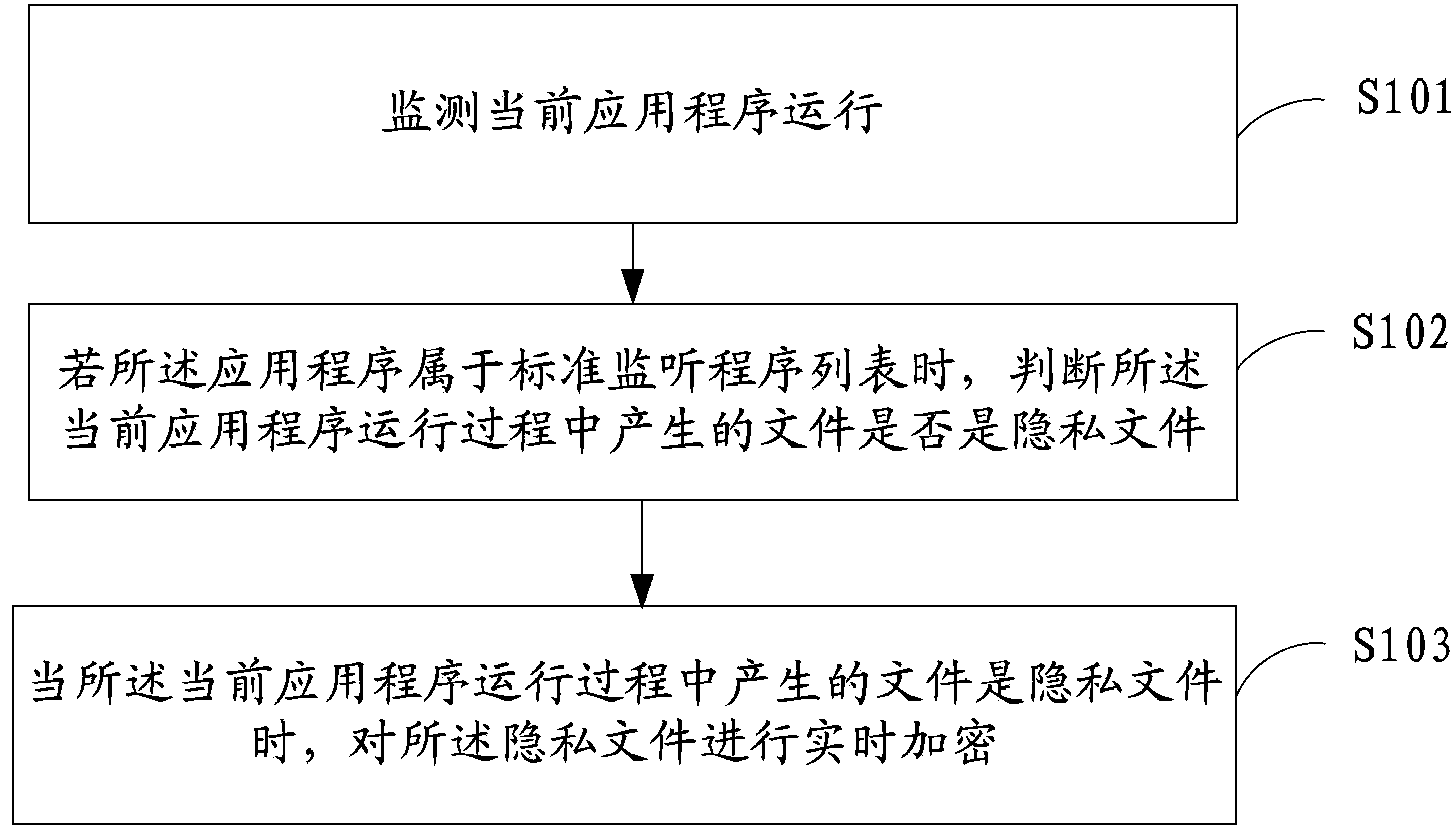
[0025] figure 1 It shows the flow chart of the implementation of the private file encryption method provided by Embodiment 1 of the present invention, and the details are as follows:
[0026] In S101, monitor the running of the current application program;
[0027] In this embodiment, the application program is an application program installed locally on the terminal device, for example, a game program, an instant messaging program, a call program, and the like.
[0028] In S102, if the application program belongs to the standard listening program list, determine whether the file generated during the running of the current application program is a private file;
[0029] Wherein, the standard listening program list stores the application program information to be monitored, and the application program information may include information such as the name and size of the application program. When the application program belongs to the standard listening program list, it indicate...
Embodiment 2
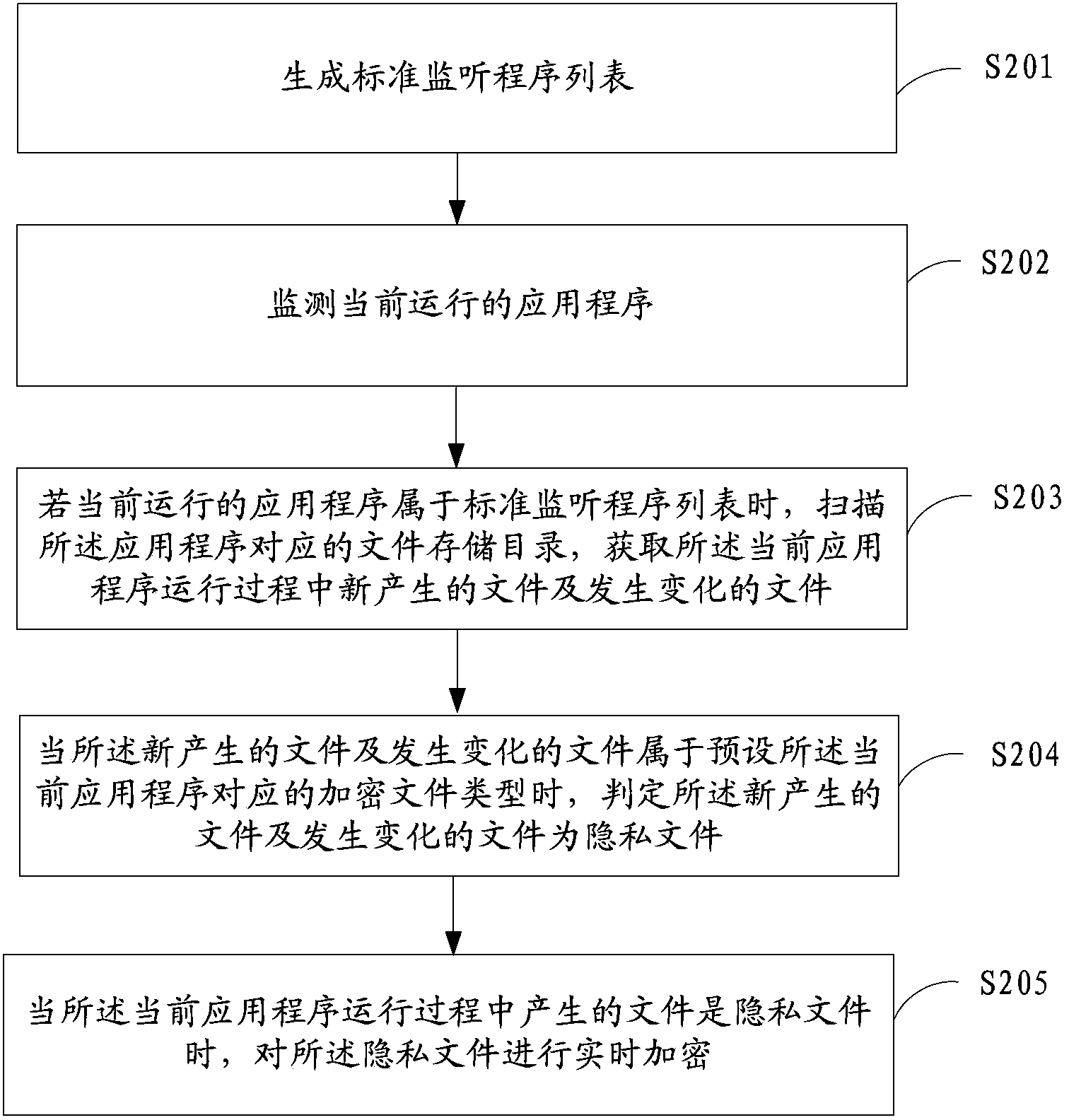
[0034] figure 2 It shows the flow chart of the implementation of the private file encryption method provided by Embodiment 2 of the present invention, and is described in detail as follows:
[0035] In this embodiment, after the terminal device is powered on, it may output prompt information to the user whether to encrypt the private file, and if yes, execute S201.
[0036] In S201, generate a list of standard listening programs;
[0037] Optionally, S201 is implemented in the following way 1: generate a standard listening program list according to the application information to be encrypted selected by the user and the encrypted file type corresponding to each application set, specifically, a shortcut entry can be set on the terminal, when When the shortcut entry is clicked, a list of encryption program selection and setting encrypted files will pop up. The list shows the applications that need to be encrypted locally on the terminal device and the corresponding encrypted f...
Embodiment 3
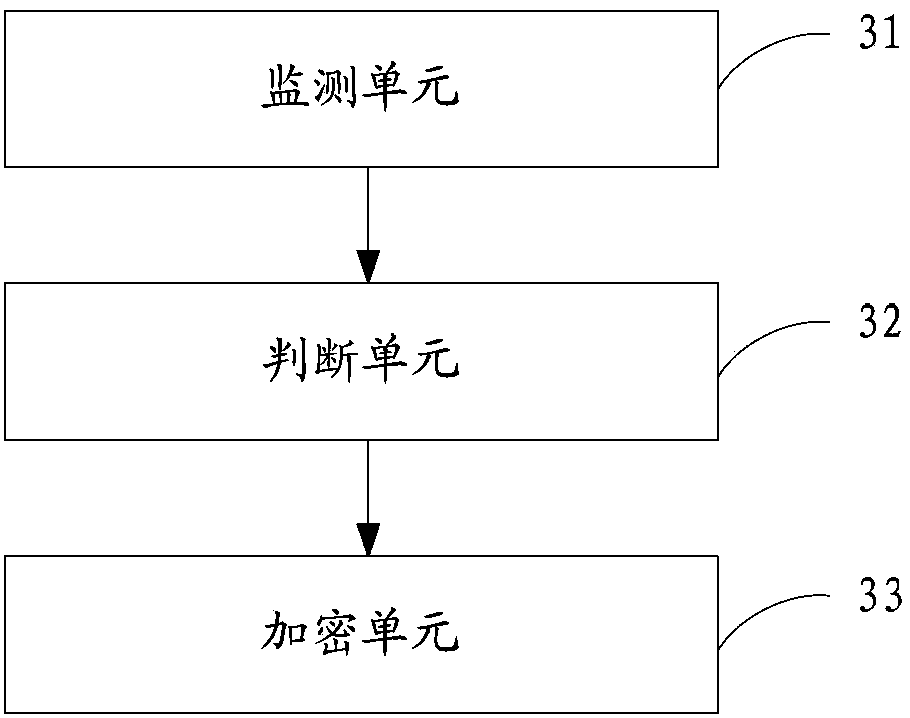
[0057] image 3 The structure diagram of the private file encryption device provided by the third embodiment of the present invention, for the convenience of description, only shows the part related to the embodiment of the present invention, the device can be a software unit, a hardware unit or a software unit built in the terminal device. Hard binding unit.
[0058] The device includes: a monitoring unit 31 , a judging unit 32 and an encryption unit 33 .
[0059] A monitoring unit 31, configured to monitor currently running application programs;
[0060] A judging unit 32, configured to judge whether the file generated during the running of the current application is a private file if the application belongs to a standard listening program list, and the standard listening program list stores application information to be monitored;
[0061] The encryption unit 33 is configured to encrypt the private file in real time when the file generated during the running of the curren...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com