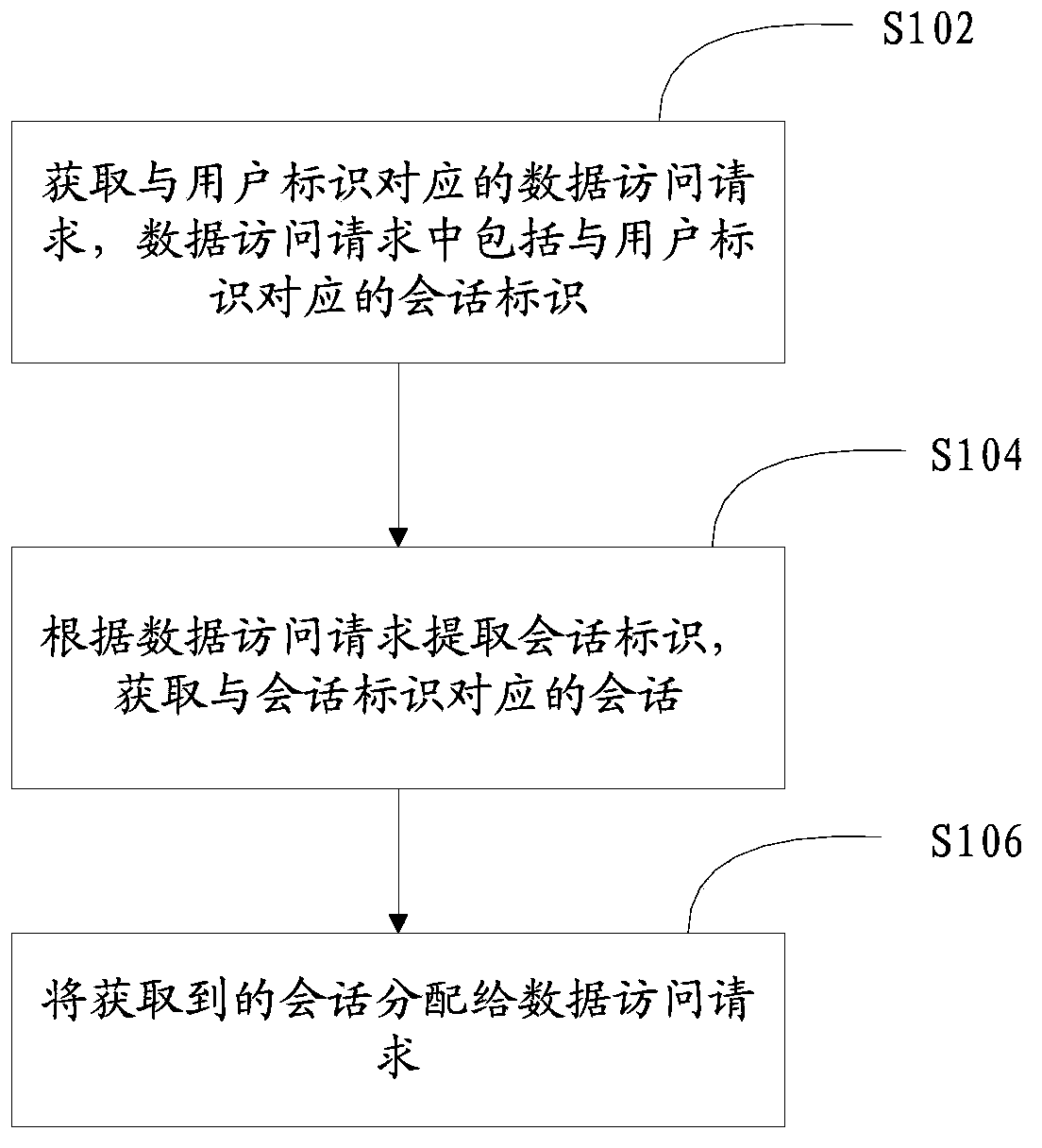
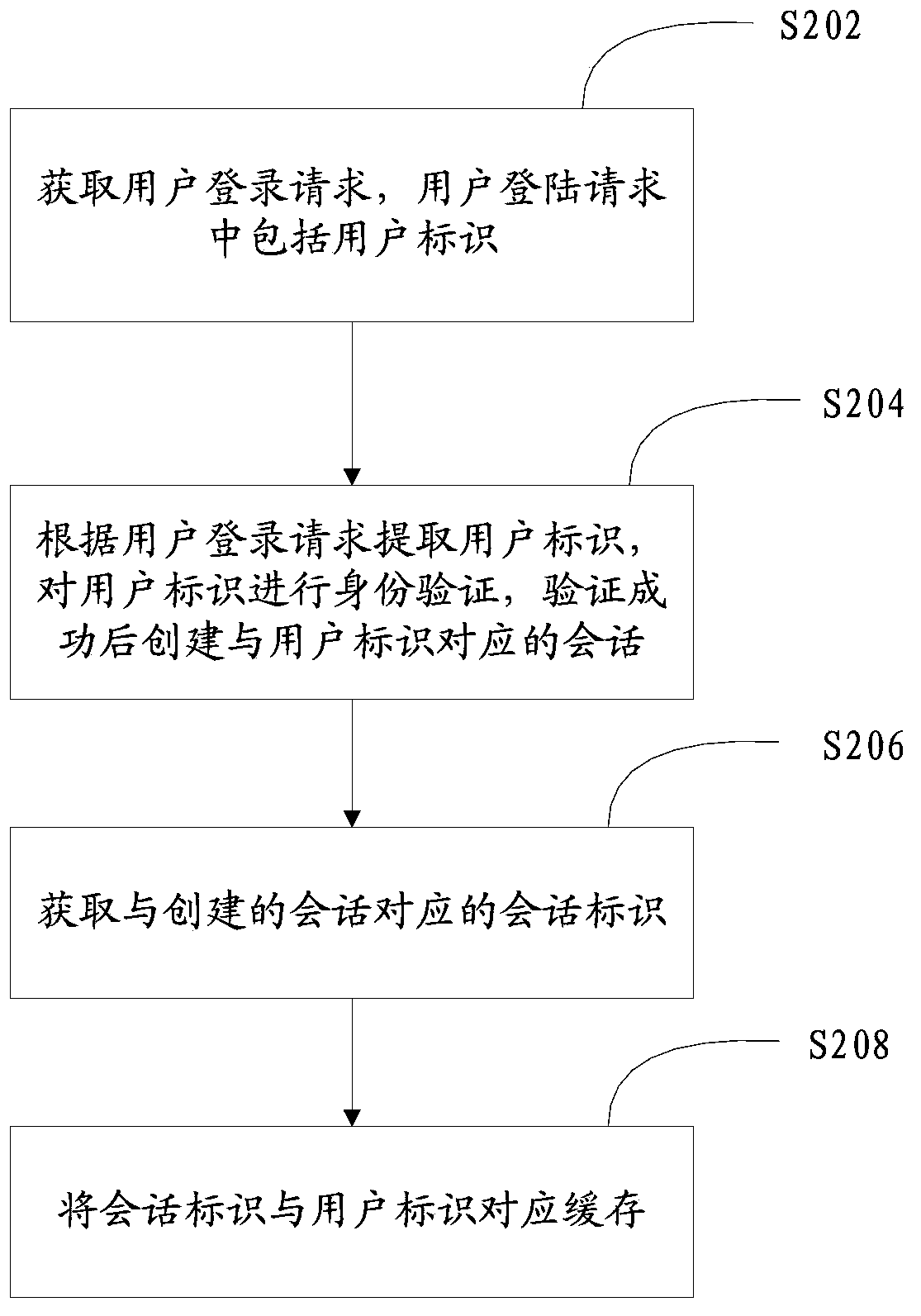
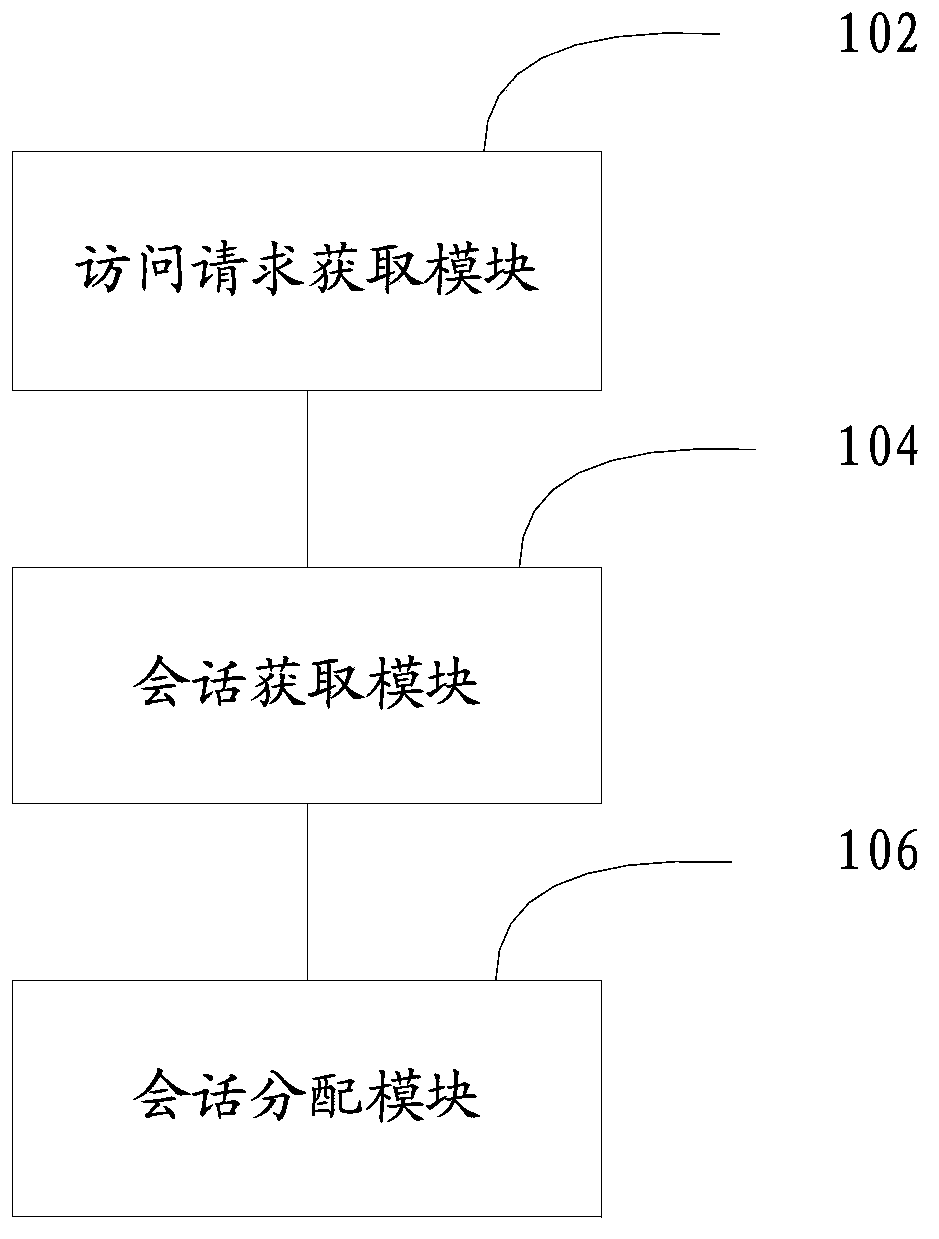
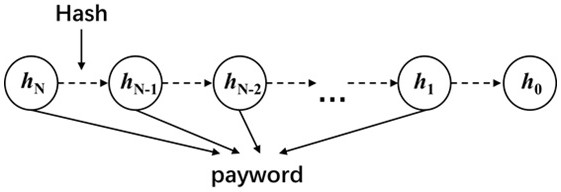
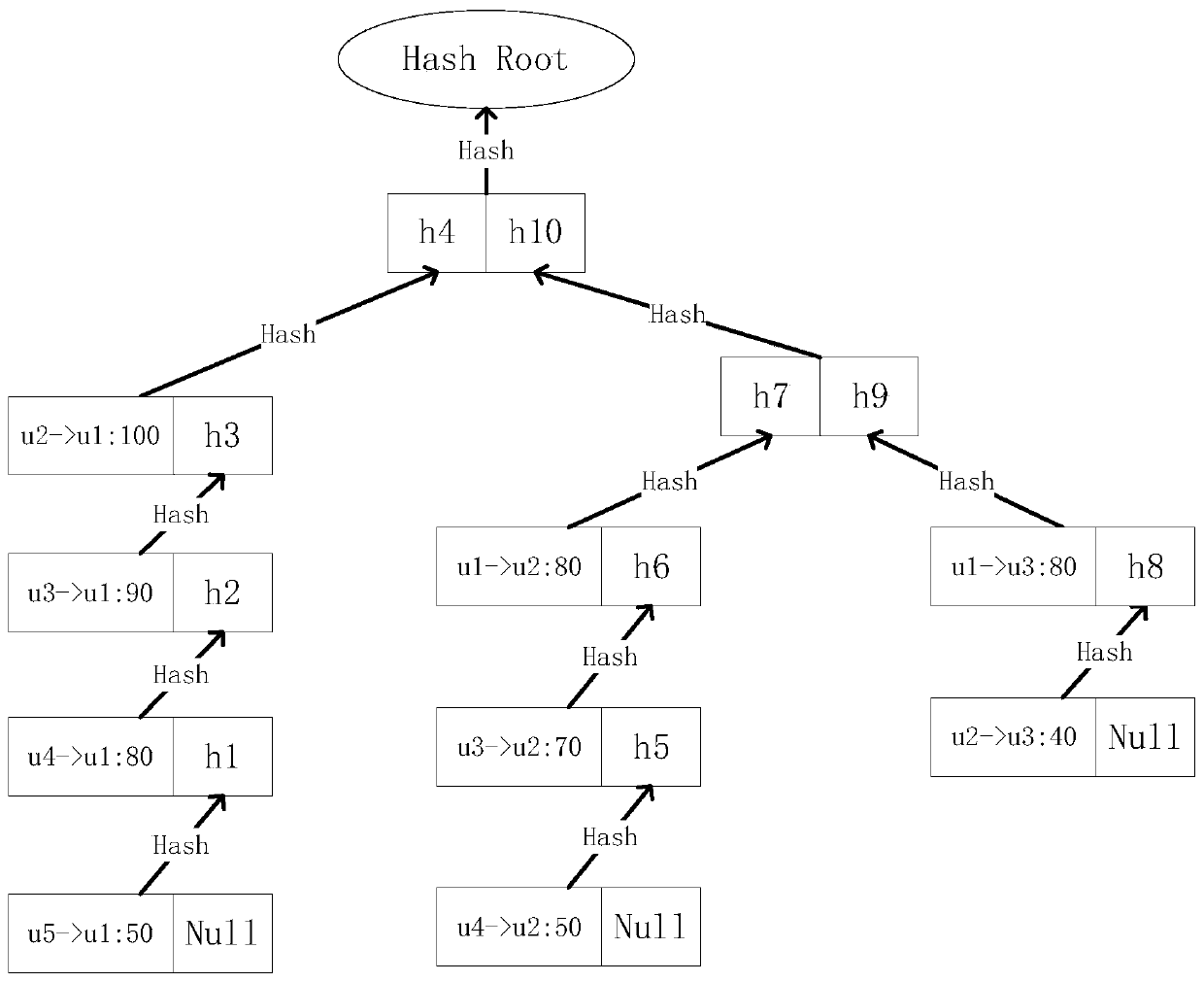
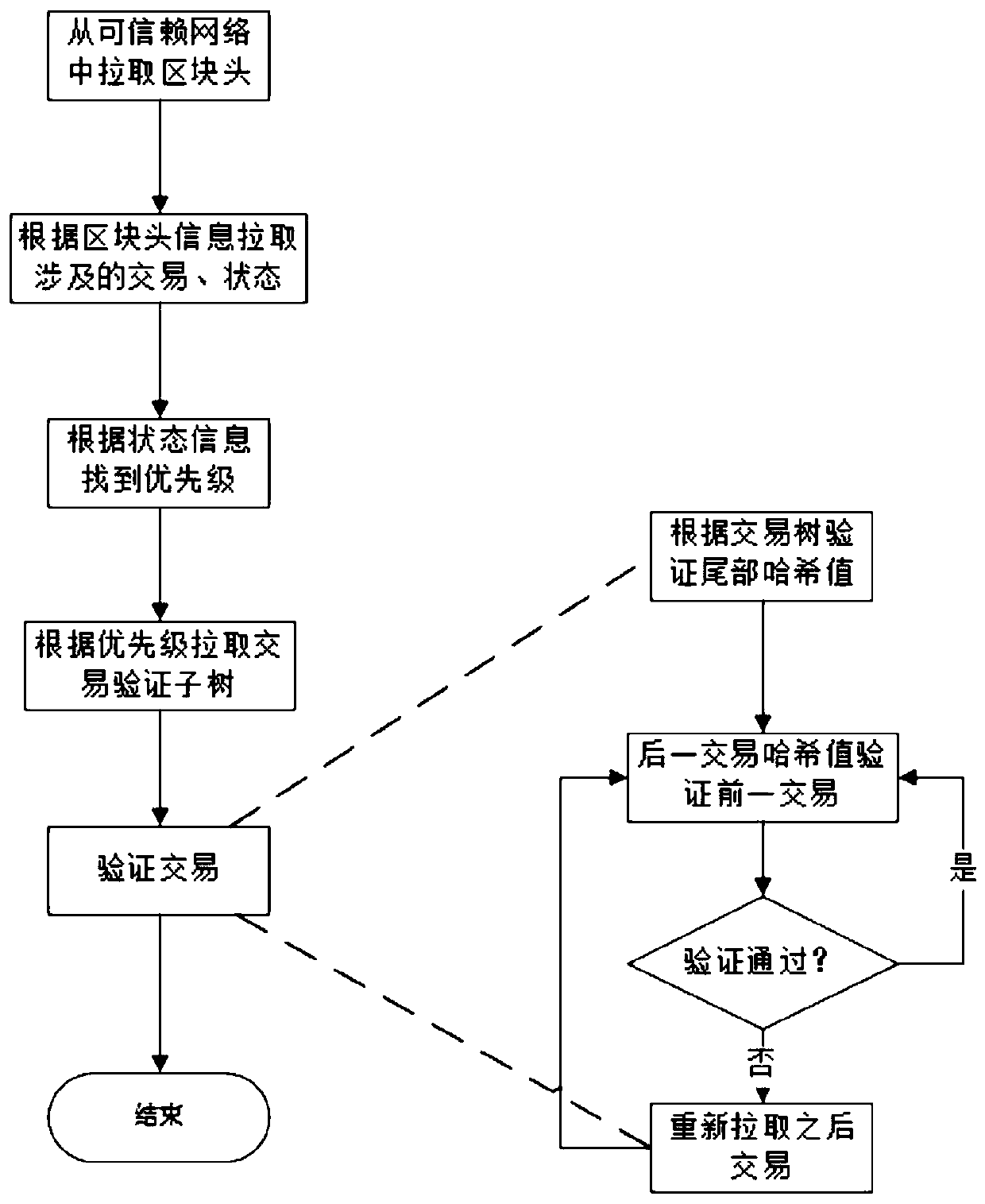
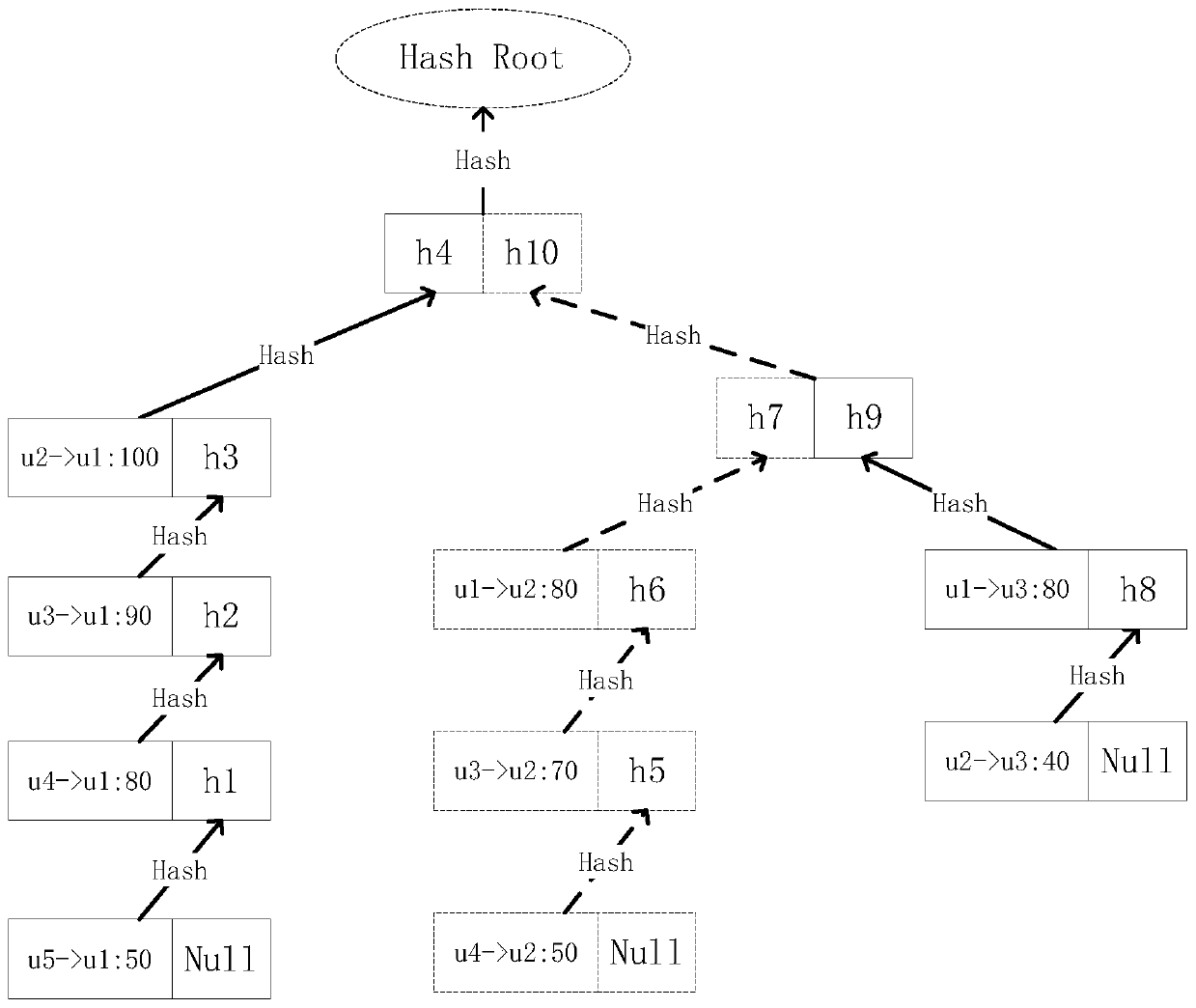
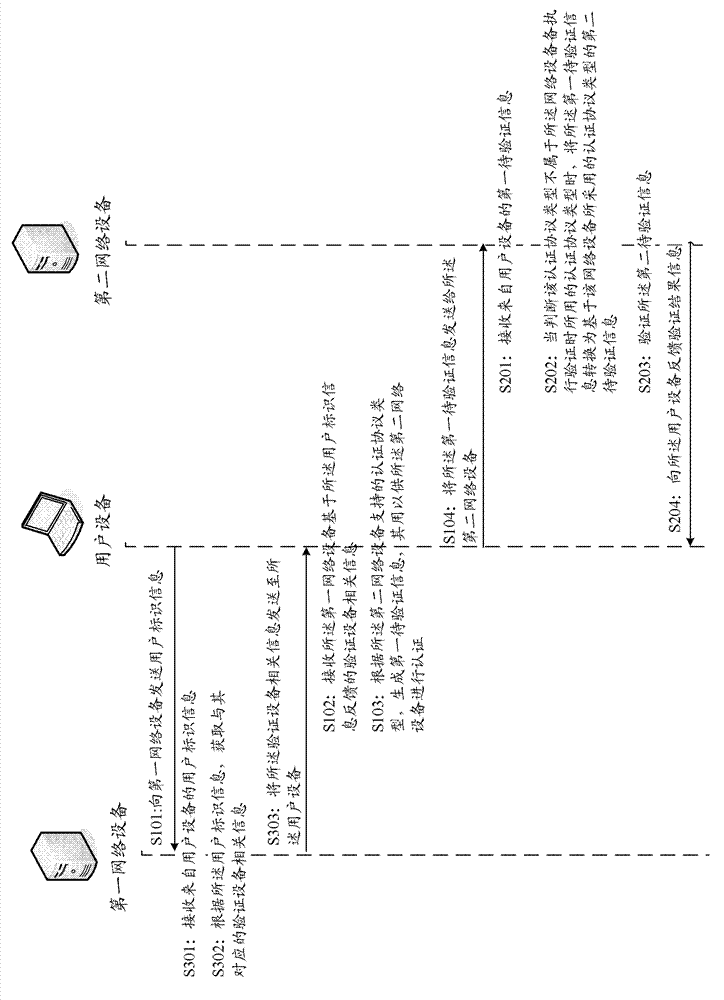
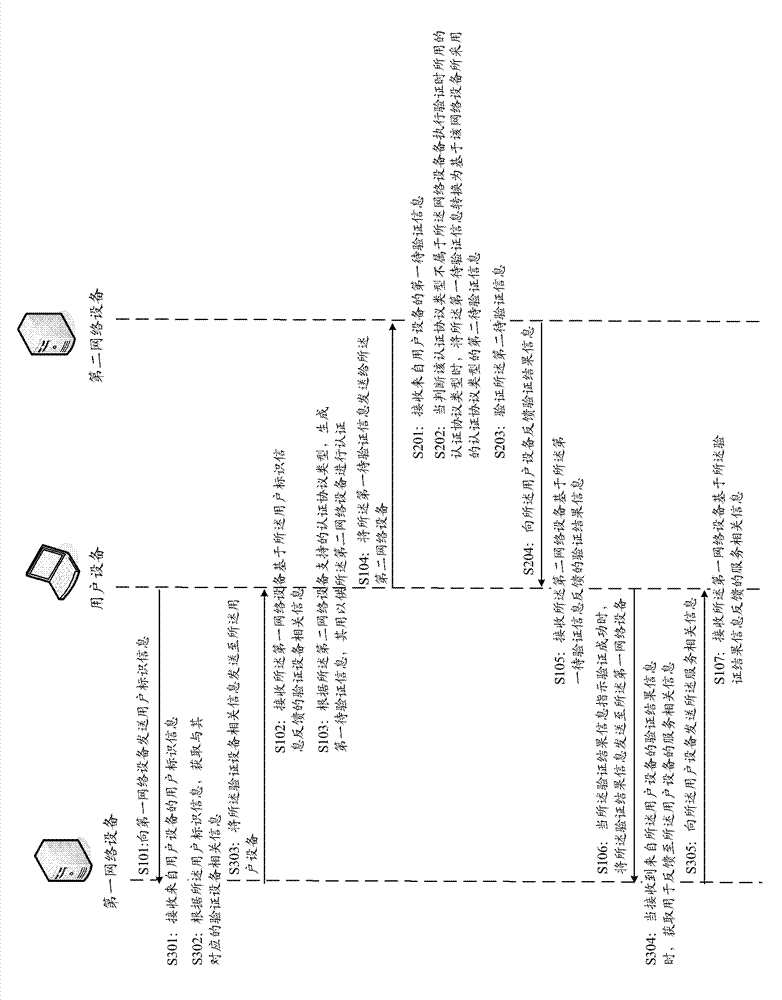
Patents
Literature
56results about How to "Reduce verification times" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
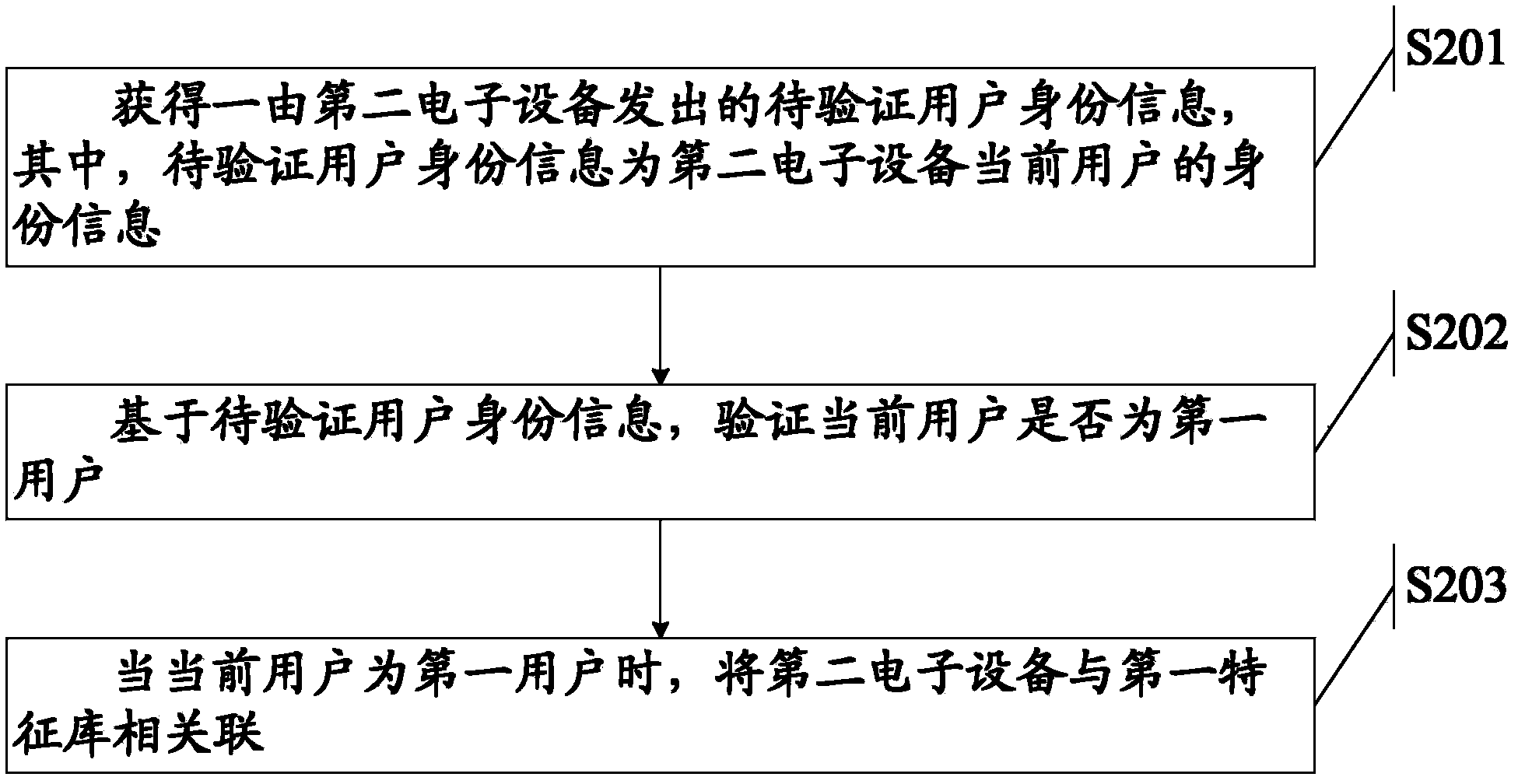
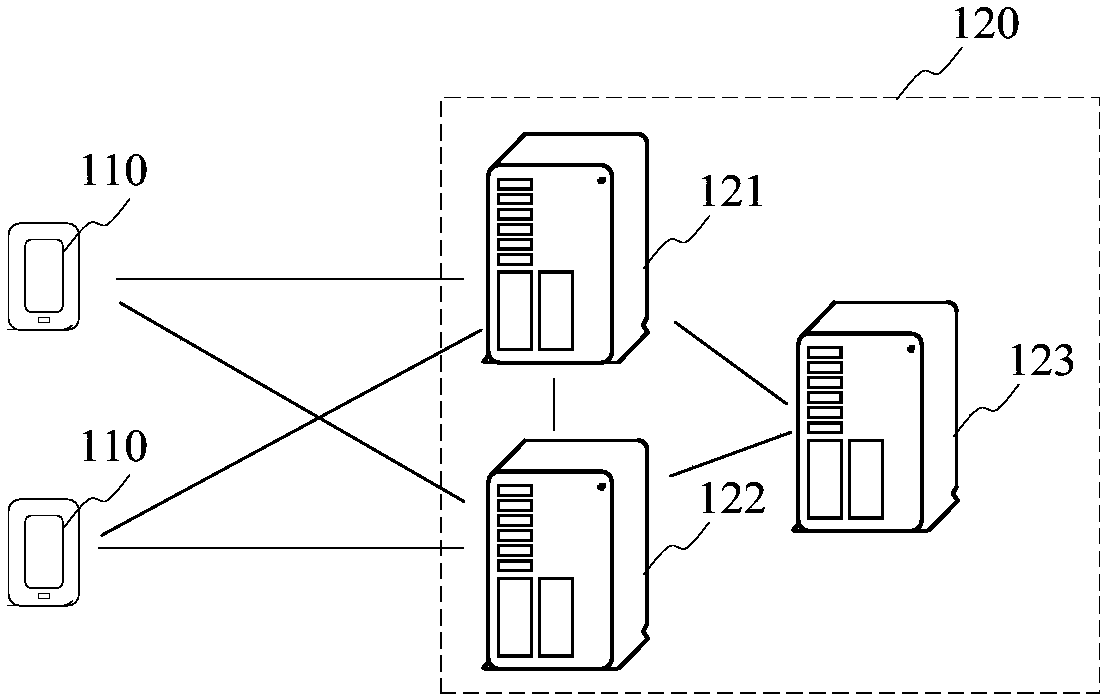
Method and system for maintaining login state of user account
ActiveCN103532919AReduce verification timesRelieve pressureUser identity/authority verificationDigital data authenticationData accessWorld Wide Web
Owner:TENCENT TECH (SHENZHEN) CO LTD
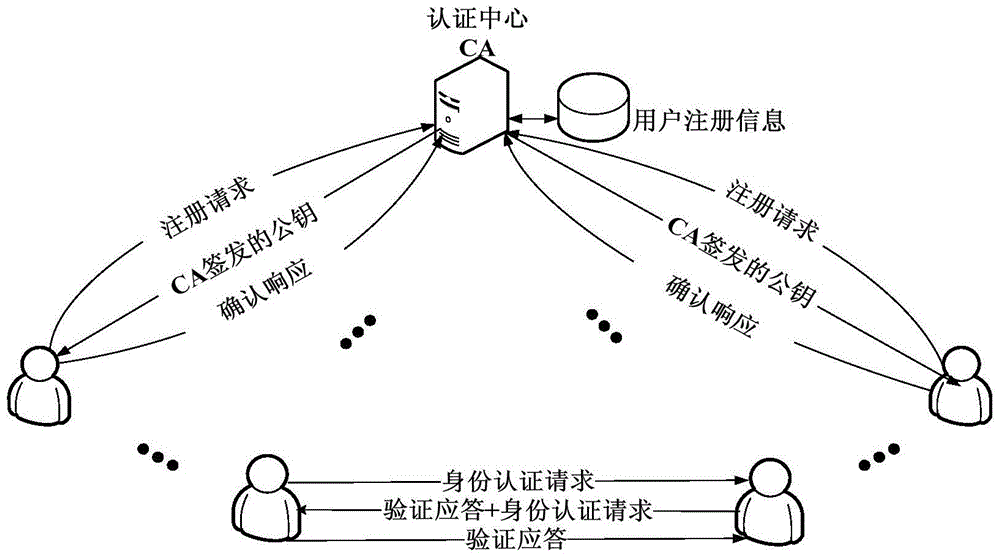
Method for mutual authentication of user identities based on elliptic curve passwords
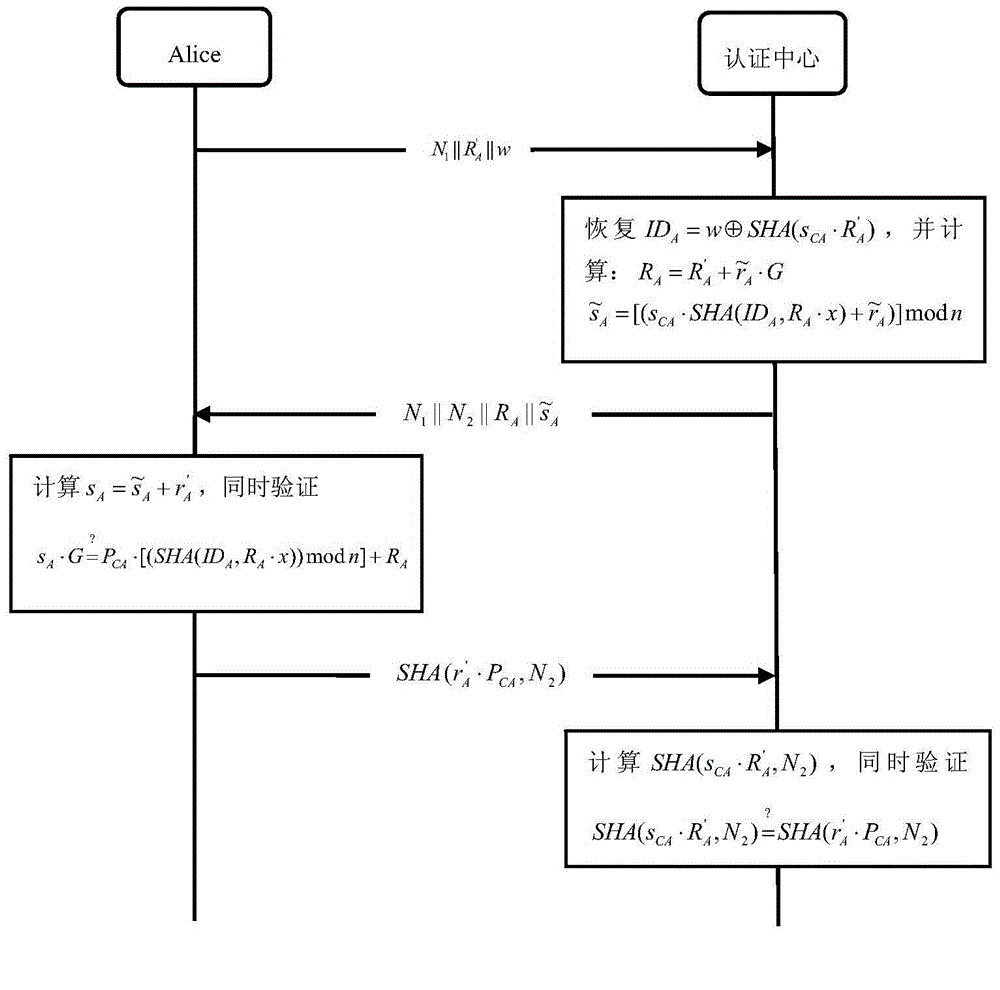
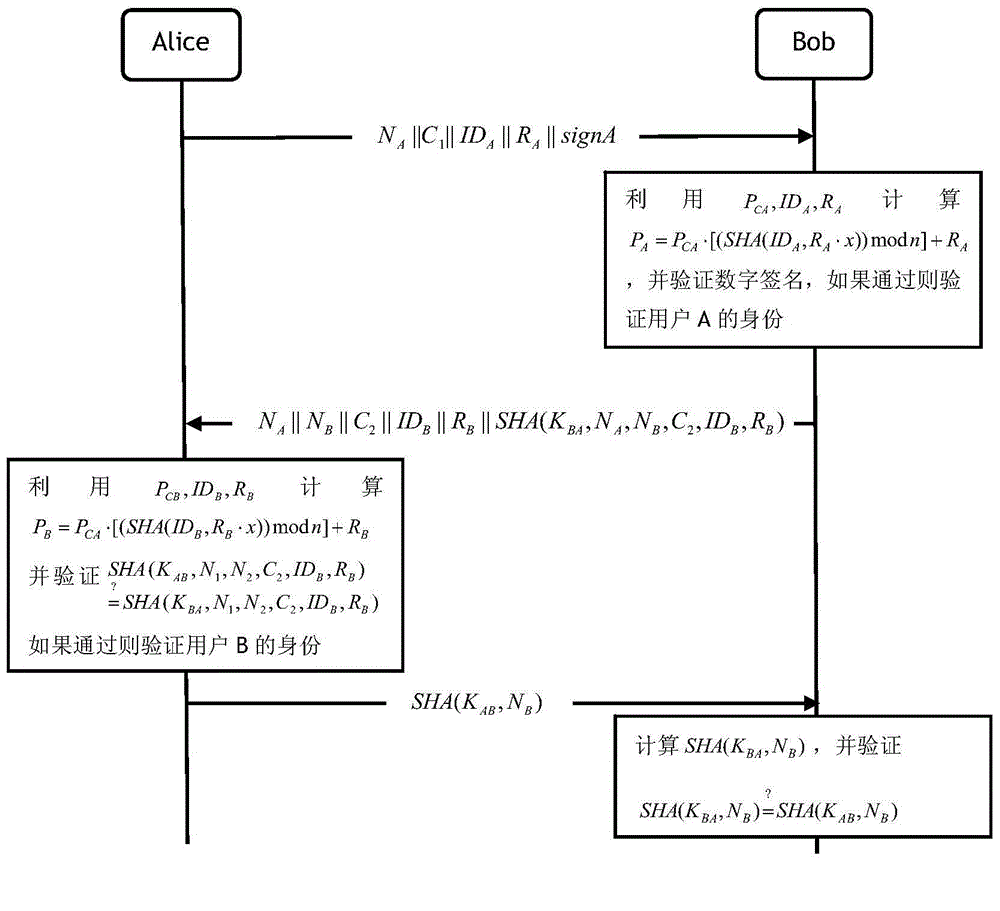
ActiveCN104639329AReduce verification timesReduce storage overheadPublic key for secure communicationUser identity/authority verificationInteraction timeMan-in-the-middle attack
The invention relates to a method for mutual authentication of user identities based on elliptic curve passwords. The characteristics of storage capability, calculation capability and limited bandwidth of an Ad Hoc network are considered, and a self-authentication public key system and the intractability of an elliptic curve discrete logarithm problem are utilized, so as to reduce the interaction times of the user identity authentication process, and accelerate the authentication speed. The method comprises the following steps of system initializing, user registering, and mutual authentication of the user identities. The method has the advantages that while the mutual authentication of the user identities is guaranteed, the function of session key negotiation is realized, the storage expense, communication expense and calculation expense are all less, the replay attack, man-in-the-middle attack, counterfeiting and tampering attack, and key disclosure counterfeiting attack can be resisted, a generated one-time session key has the advancing security and backward security, and the security is higher.
Owner:ZHEJIANG UNIV
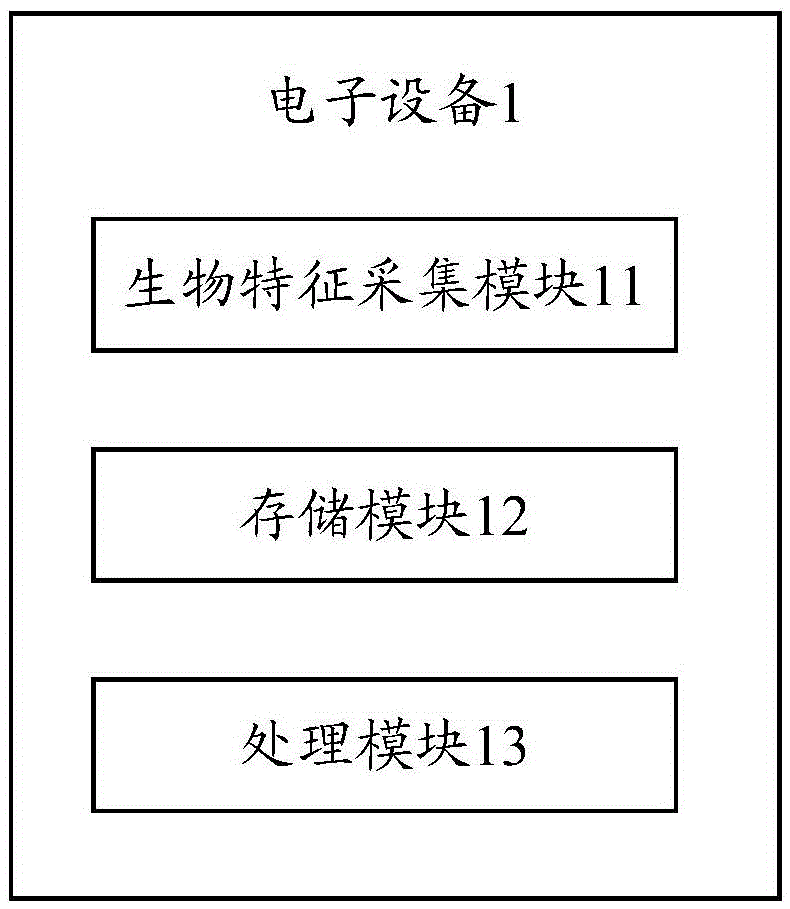
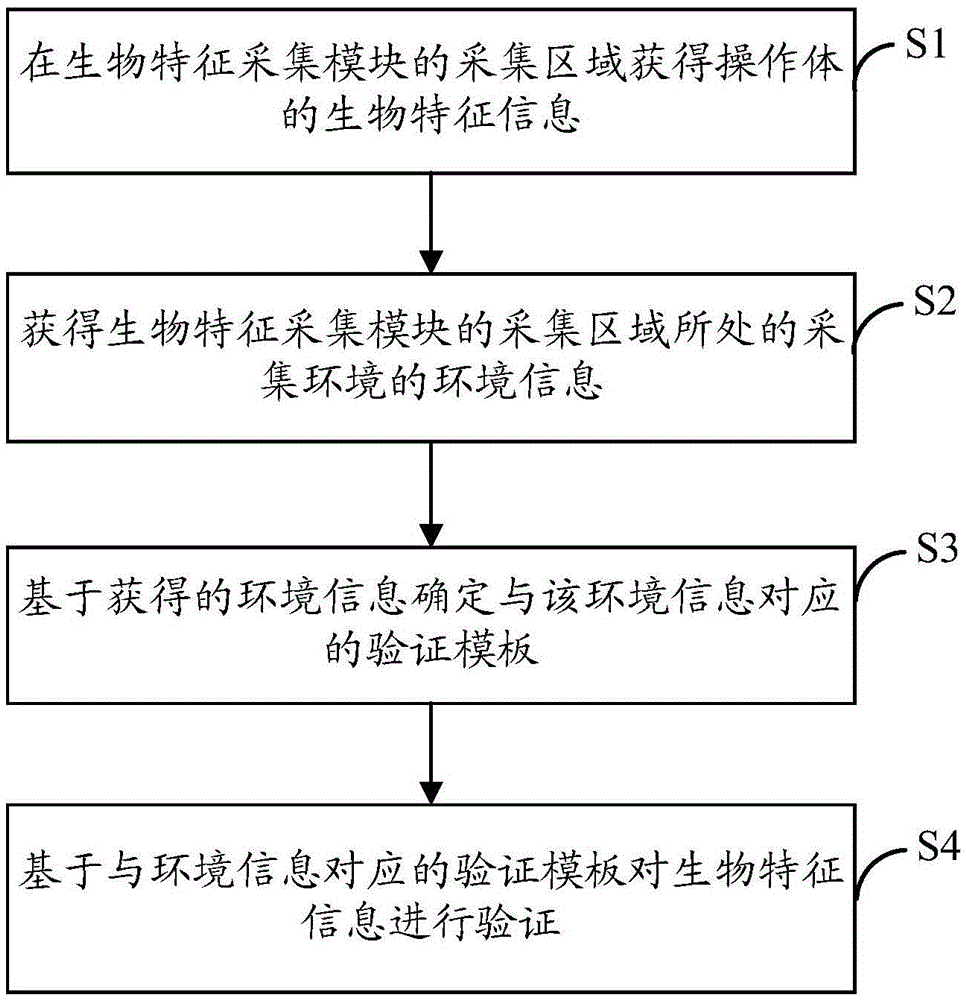
Bio-feature verification method and electronic device
ActiveCN105653922AImprove user experienceImprove effectivenessDigital data authenticationInformation acquisitionComputer engineering
The invention provides a bio-feature verification method and an electronic device. By utilizing environment information of an acquisition environment during bio-feature information acquisition, a proper verification template is selected for verifying the acquired bio-feature information so as to improve the effectiveness of verification processing. The bio-feature verification method comprises the steps of obtaining the bio-feature information of an operation body in an acquisition region of a bio-feature acquisition module; obtaining the environment information of the acquisition environment in which the acquisition region of the bio-feature acquisition module is located; based on the environment information, determining a verification template corresponding to the environment information; and based on the verification template corresponding to the environment information, verifying the bio-feature information.
Owner:LENOVO (BEIJING) CO LTD
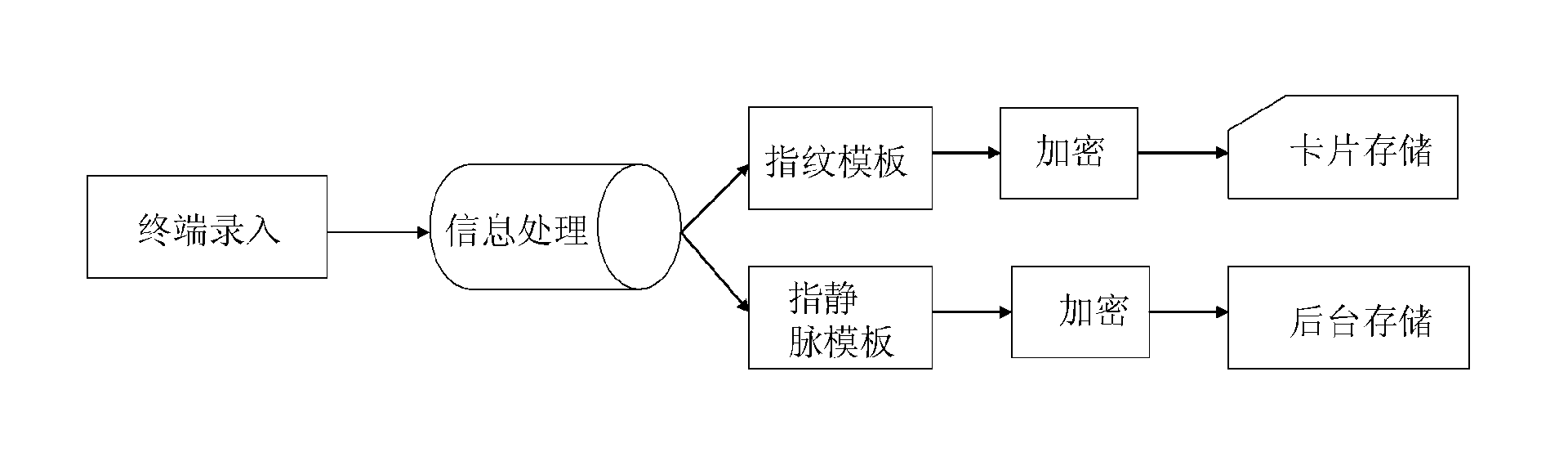
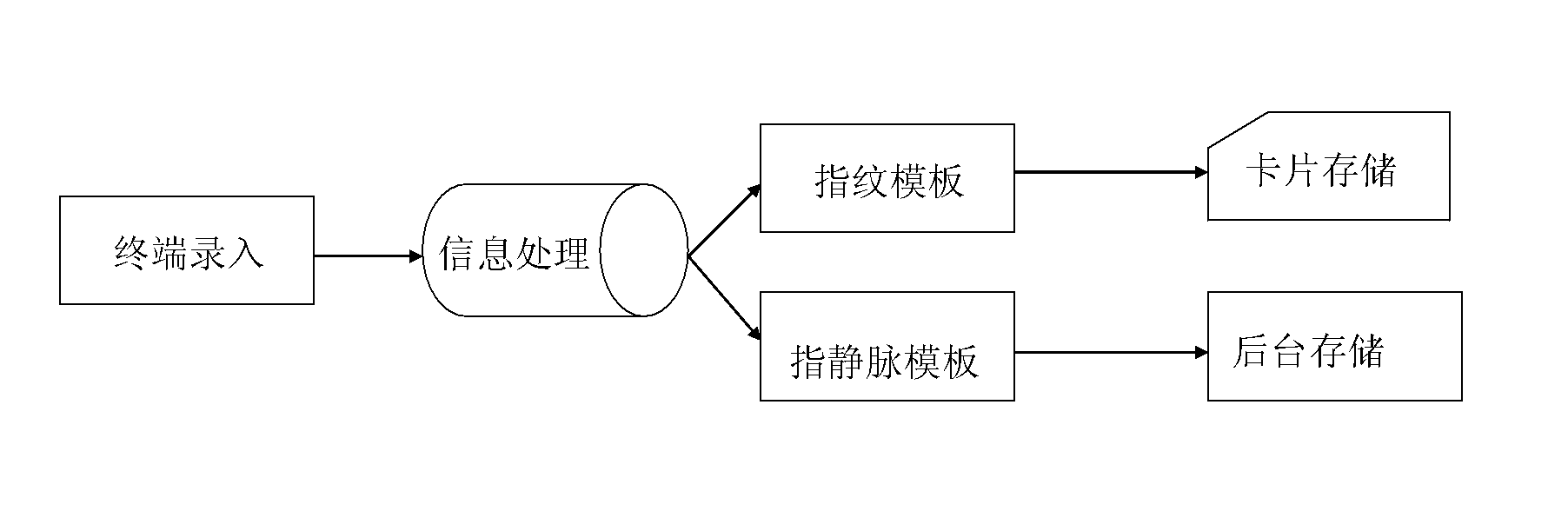
Payment authentication method based on fingerprints and finger veins
InactiveCN103699995AReduce verification timesImprove verification efficiencyMatching and classificationSpoof detectionFingerprintIntegrated circuit
The invention relates to an integrated circuit (IC) card payment authentication method based on fingerprints and finger veins. The method comprises the following steps: registration: a registered terminal acquires registration finger vein information and registration fingerprint information of a cardholder to generate a finger vein template and a fingerprint template, stores the fingerprint template in an IC card and the finger vein template in a background system; trading: a payment terminal obtains site payment fingerprint information and site payment finger vein information acquired when the cardholder pays at site, compares the site payment fingerprint information with the fingerprint template stored in the IC card, if the comparison fails, trading is refused, if the comparison succeeds, the background system compares the site payment finger vein information with the finger vein template stored in the background system, if the comparison fails, the trading is refused, if the comparison succeeds, the trading is authenticated. By adopting the method, the identity authentication security level can be effectively improved.
Owner:CHINA UNIONPAY
Identifying method and electronic device
ActiveCN104078045ASolve the problem of not being able to input information based on the same voice of different usersSolve operational problemsSpeech recognitionSpecial data processing applicationsSpeech soundFeature based
Owner:LENOVO (BEIJING) CO LTD
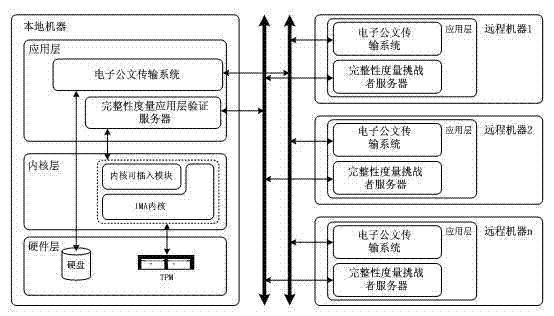
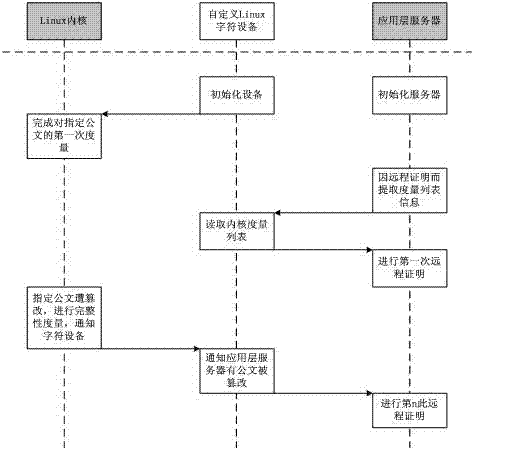
Dynamic integrity measurement method for security of electronic government cloud platform
InactiveCN102880826AReduce verification timesImprove verification capabilitiesPlatform integrity maintainanceTransmissionMultiplexerComputerized system
The invention provides a high-dynamic degree and high-security dynamic integrity measurement method for the security of an electronic government cloud platform. An integrity measurement architecture (IMA) is involved. The method comprises the following steps of: setting a double linked list in a kernel for a specified process and a specified file respectively, storing measurement results of the process and the file, and expanding the measurement results into corresponding program control registers (PCR) by using a terminal-to-computer multiplexer (TCM) chip. The specification refers to that a file to be measured is determined by an authority department, for example, a government department is required to strictly protect certain official documents; and the measurement of the specified process mainly aims to improve the security of a computer system and assist in protecting the integrity of a confidential official document.
Owner:SOUTH CHINA UNIV OF TECH
Prediction and optimization method for efficient working condition area range of centrifugal pump impeller
ActiveCN110909422APrediction is accurateGuaranteed reasonablenessGeometric CADDesign optimisation/simulationStructure extractionEngineering
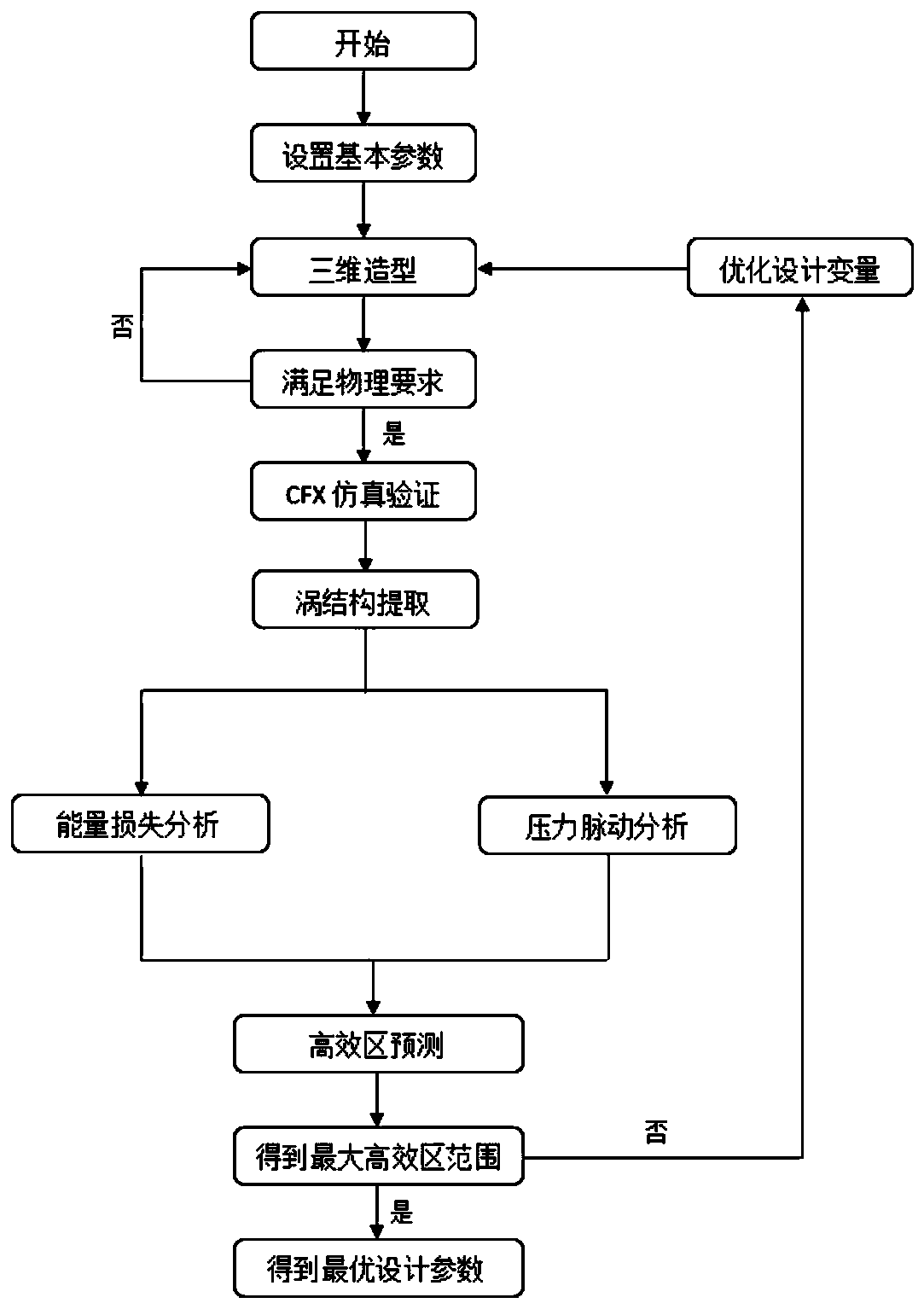
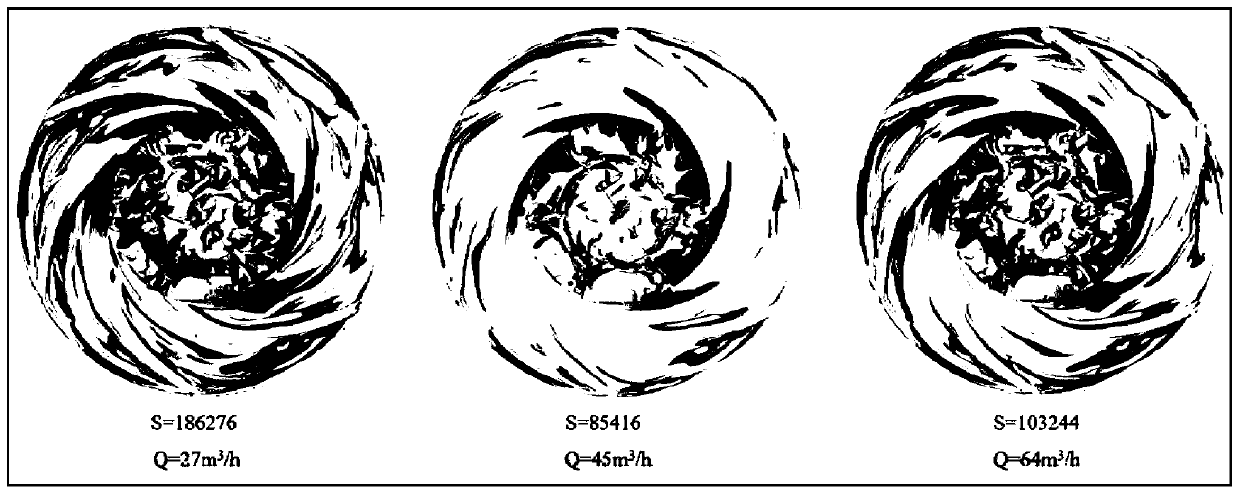
The invention relates to the field of centrifugal pump hydraulic optimization. The invention aims to provide a prediction and optimization method for an efficient working condition area range of a centrifugal pump impeller. According to the method, on the premise that the maximum efficiency point of the centrifugal pump is not changed, factors of energy loss and pressure pulsation of the centrifugal pump impeller are fully considered, an efficient working condition area of the centrifugal pump impeller is accurately predicted, and design parameters of the centrifugal pump impeller are optimized according to the efficient working condition area, so that the application range of the centrifugal pump is expanded, the operation stability of the centrifugal pump is improved, resources are saved, and the centrifugal pump is more economical. According to the technical scheme, the method for predicting and optimizing the efficient working condition area range of the centrifugal pump impeller comprises the following steps of (1) modeling and meshing, (2) CFX simulation verification, (3) vortex structure extraction, (4) energy loss analysis, (5) pressure pulsation analysis, (6) efficient working condition area prediction and (7) centrifugal pump impeller design parameter optimization.
Owner:ZHEJIANG SCI-TECH UNIV
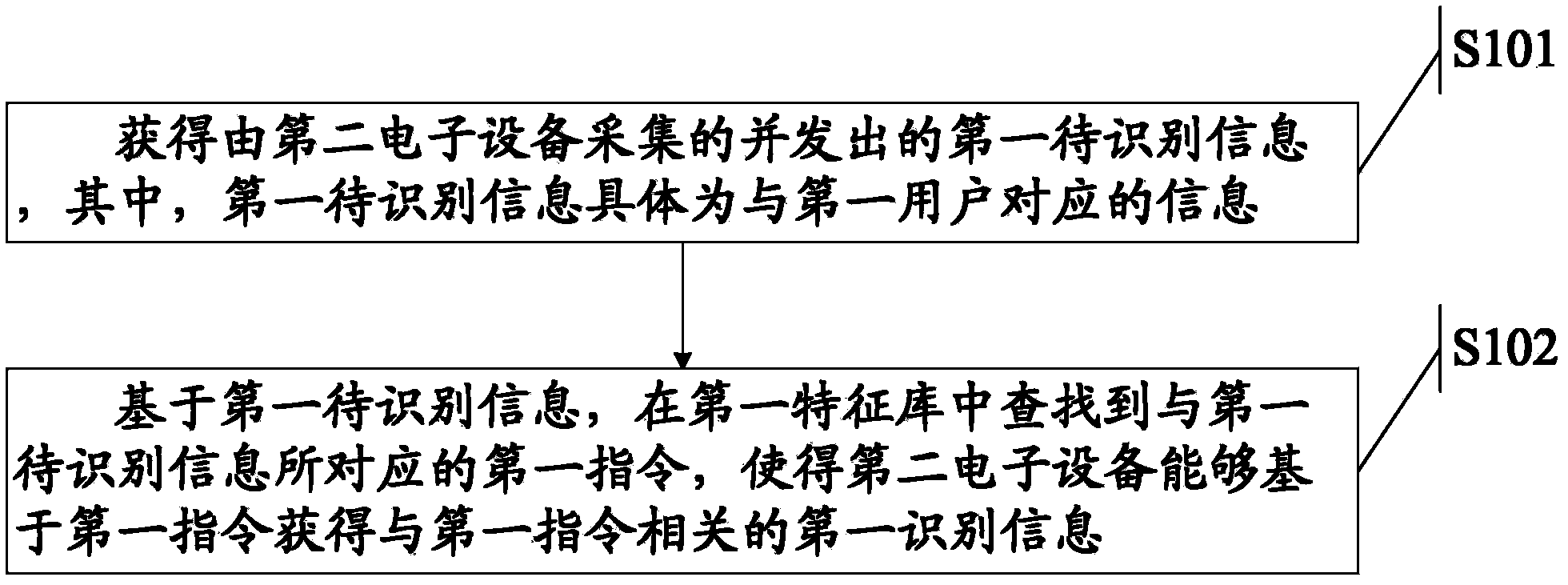
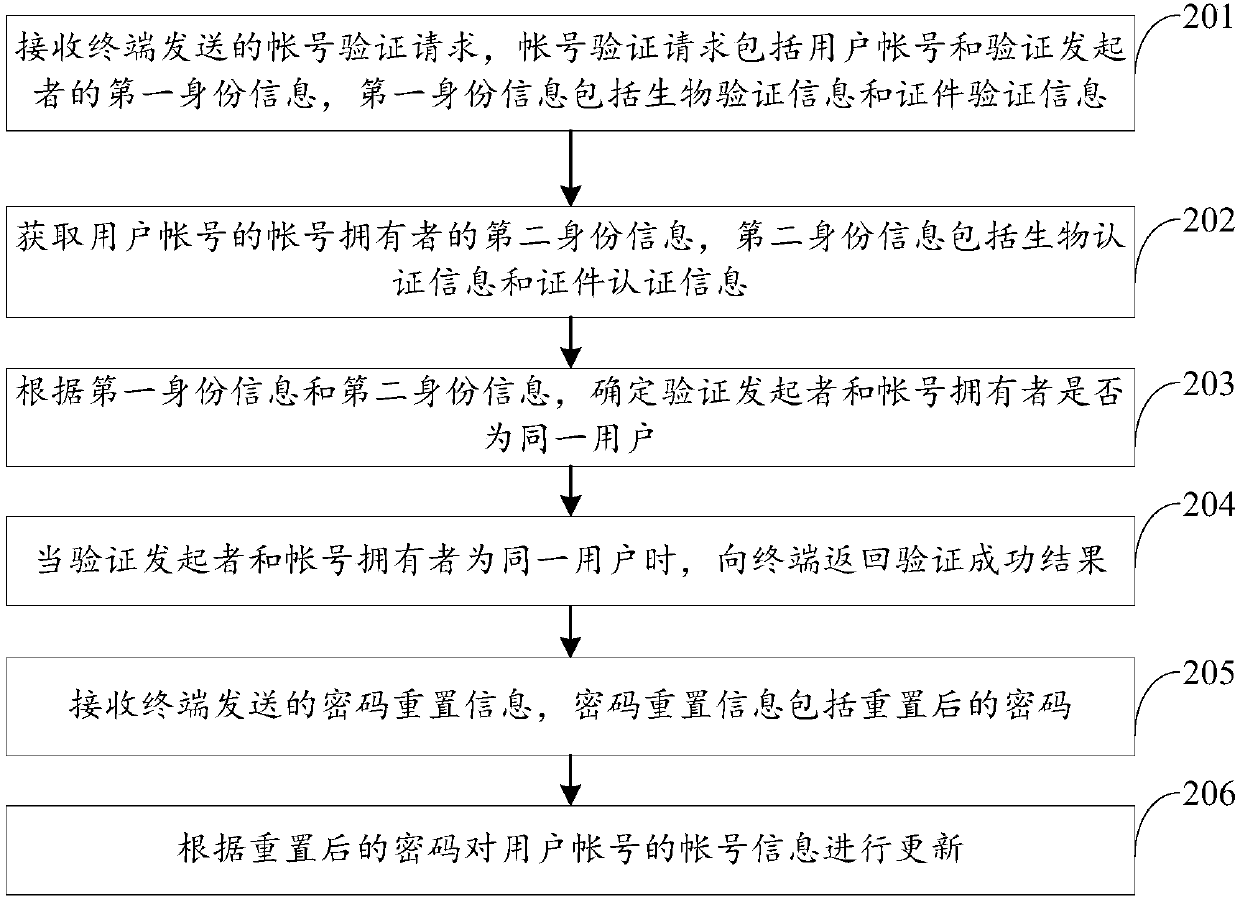
Account verification method and device
InactiveCN107786491AImprove efficiency and successReduce verification timeTransmissionFilling-inValidation methods
The invention discloses an account verification method and device and belongs to the field of network security. The account verification method comprises the following steps of receiving an account verification request sent by a terminal, wherein the account verification request comprises a user account and first identity information of a verification initiator, and the first identity informationcomprises biological verification information and certificate verification information; obtaining second identity information of an account owner of the user account, wherein the second identity information comprises biological authentication information and certificate authentication information; determining whether the verification initiator and the account owner are the same user according to the first identity information and the second identity information; and when the verification initiator and the account owner are the same user, returning a verification success result to the terminal.In the embodiments of the invention, the user only needs to upload the biological verification information and the certificate verification information which do not need to be memorized so as to complete the account verification, and thus the user can be prevented from filling in the verification data according to the memory, and the efficiency and success rate of account verification are improved on the premise of ensuring the security of the account.
Owner:TENCENT TECH (SHENZHEN) CO LTD
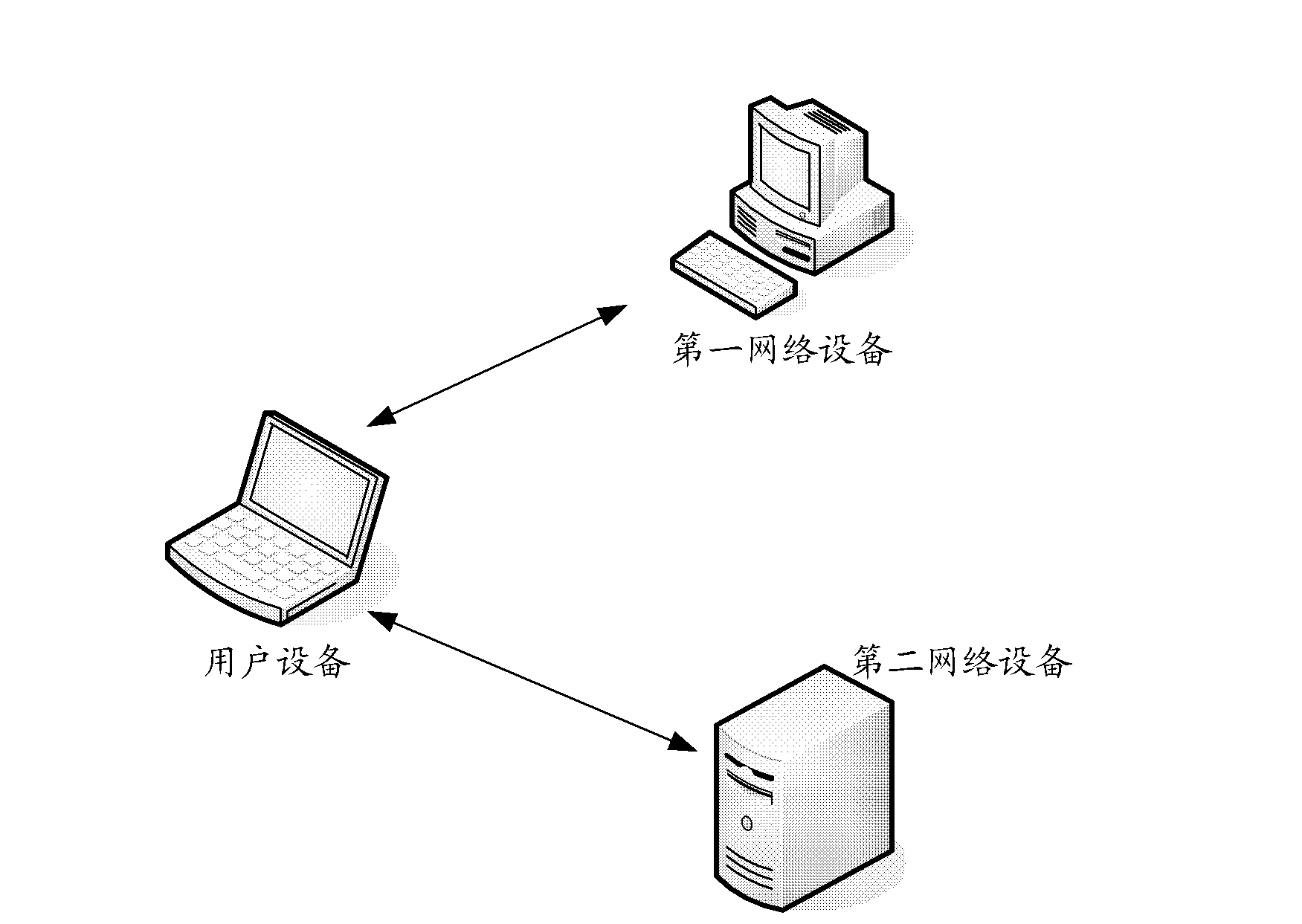
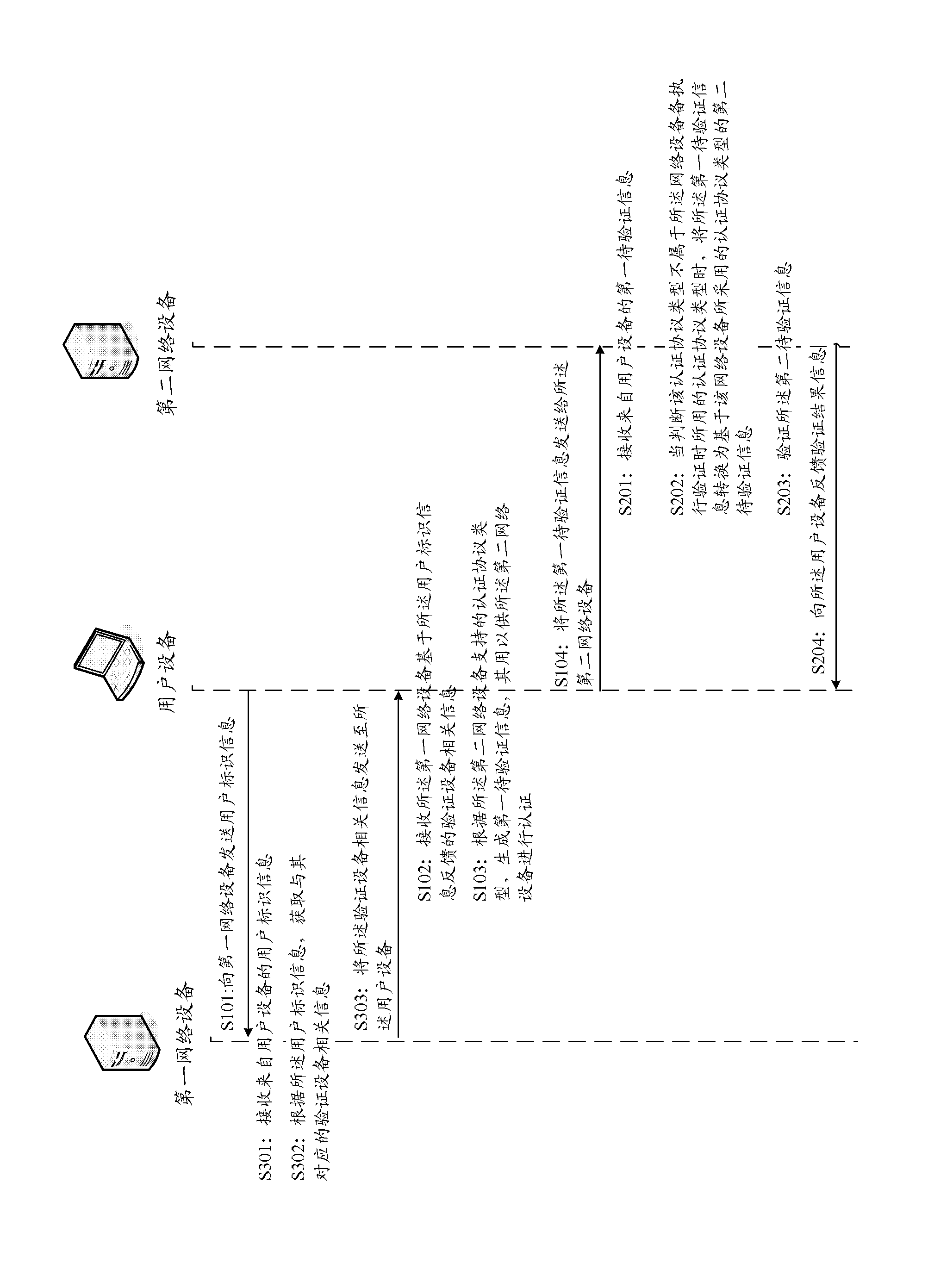
Method, device, equipment and system for executing third-party authentication
InactiveCN102611683AReduce conversionReduce the burden onTransmissionThird partyProtocol for Carrying Authentication for Network Access
The invention aims at providing a method, a device, equipment and a system for executing third-party authentication. The method comprises the following steps of: receiving first information to be authenticated from user equipment; when an authentication protocol type does not belong to the authentication protocol type used when network equipment executes authentication, and converting the first information to be authenticated into second information to be authenticated used when the network equipment executes the authentication; authenticating the second information to be authenticated; and feeding authentication result information back to the user equipment. The method, the device, the equipment and the system have the advantages that the application under the network environment with multiple authentication protocol types can be realized, so that the efficiency for executing the third-party authentication is increased; the times for carrying out third-party authentication are reduced, so that the use experience of a user is improved; first network equipment does not need to keep connection with the user equipment all the time and can acquire information related to the authentication process directly according to authentication identifying information, so that the load of the first network equipment is reduced.
Owner:SHANGHAI SYNACAST MEDIA TECH
Blockchain network sniffer, network sniffing method and optimization method
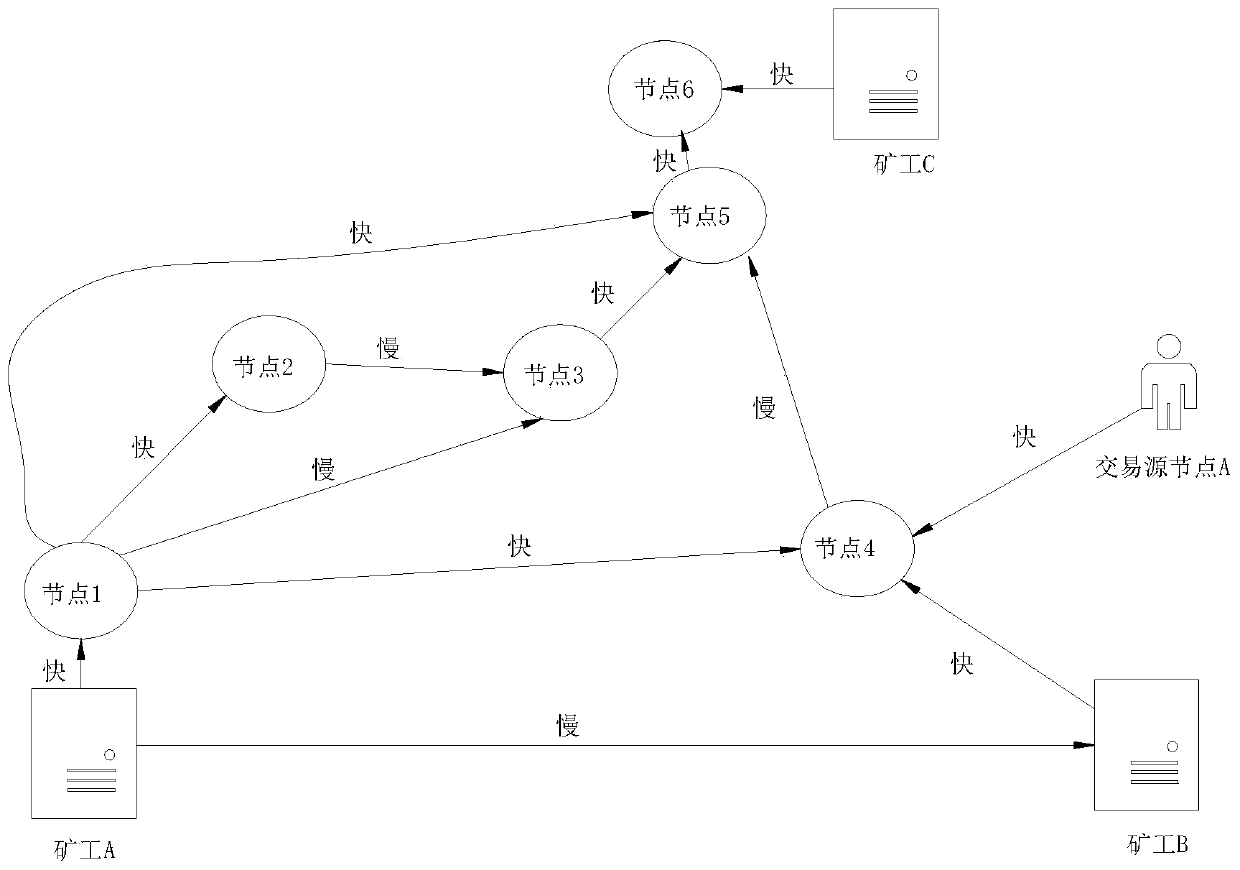
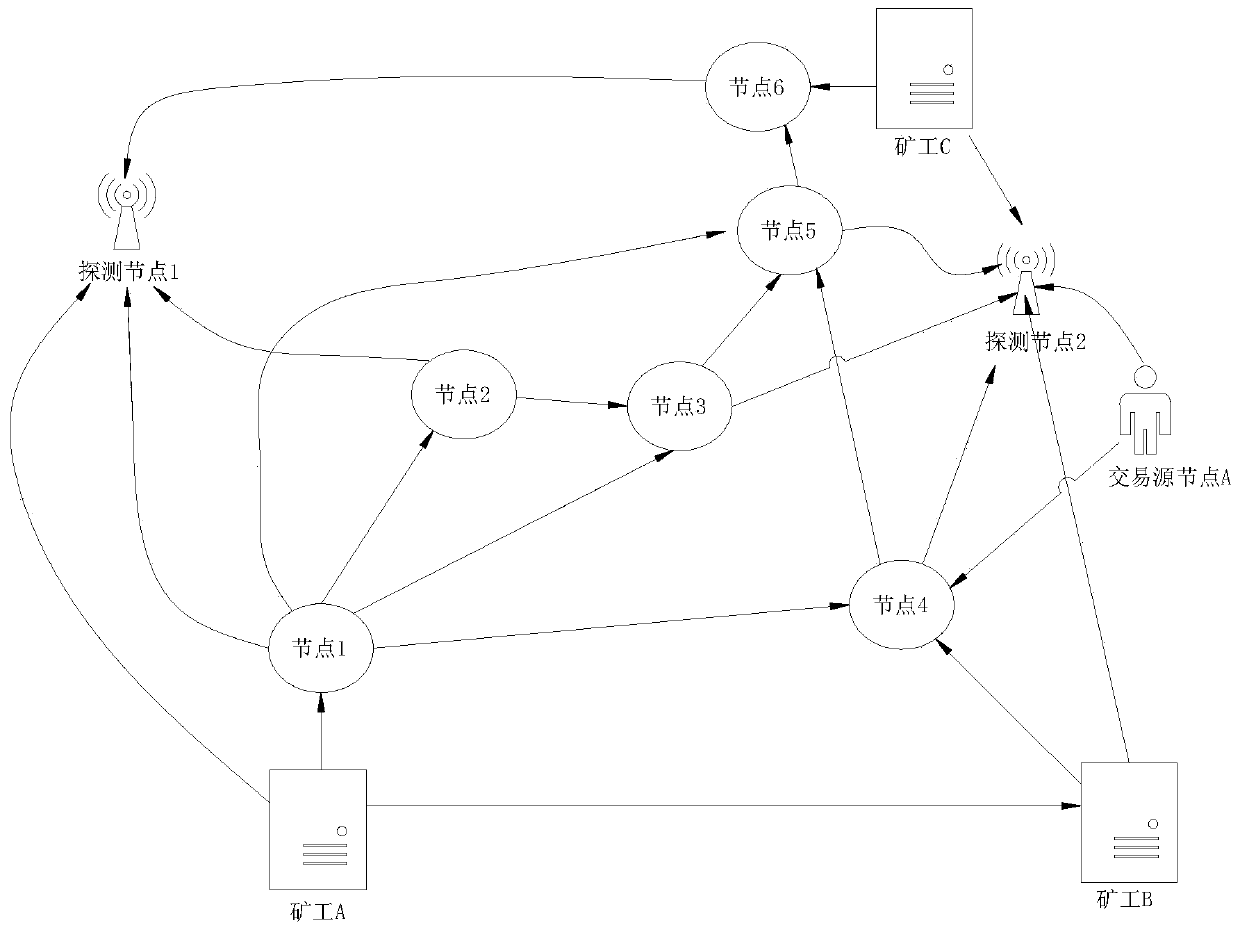
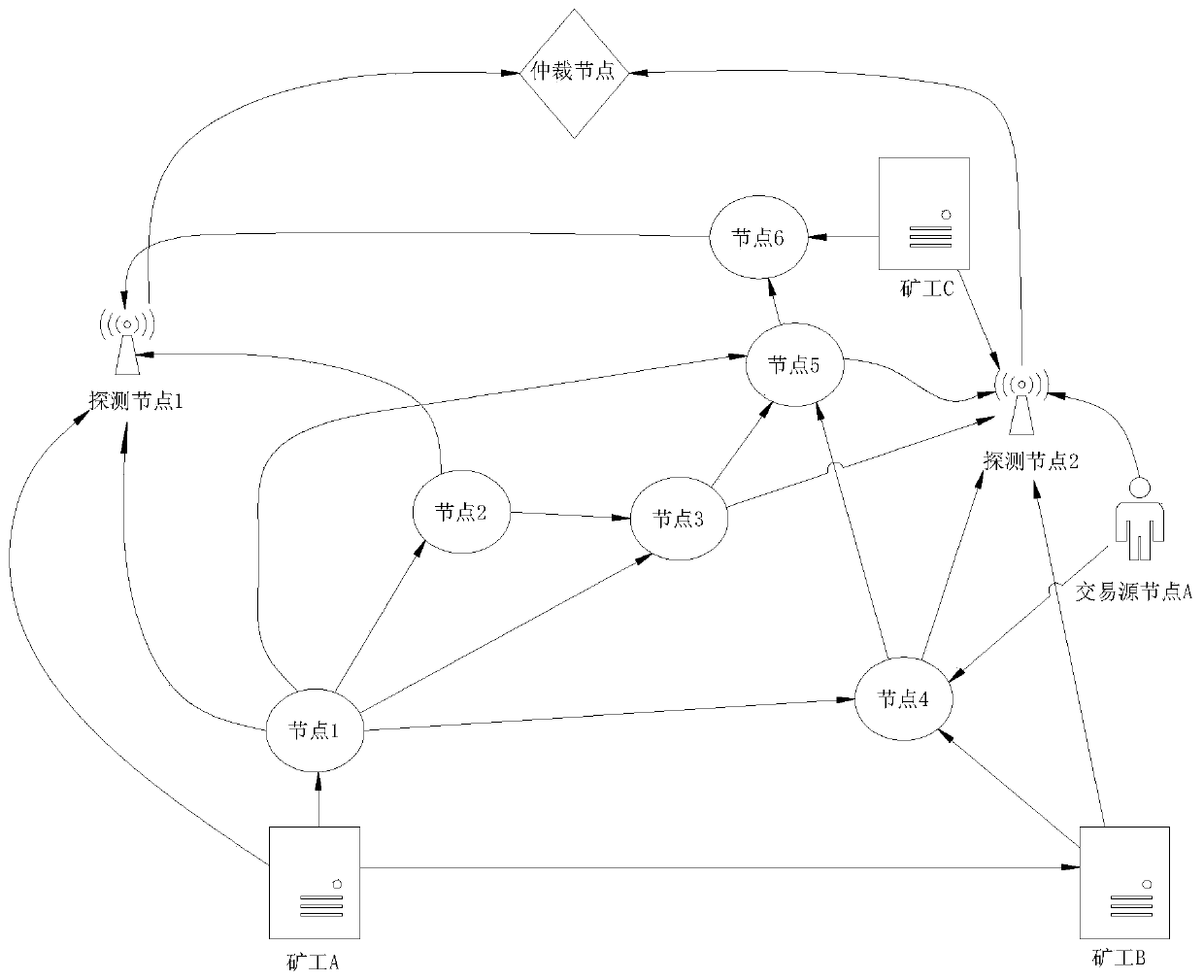
ActiveCN110474818AReduce the number of verificationsIncrease the speed of transmissionFinanceData switching networksData transmissionBlockchain
The embodiment of the invention relates to a blockchain network sniffer, a network sniffing method and an optimization method, the blockchain network sniffer comprises a detection module and a decision arbitration module, the detection module comprises at least one detection node, and the detection node is connected with all nodes in a blockchain network; wherein each detection node is connected with subsets of all the nodes, the subsets connected with the detection nodes are not overlapped, and a combined set of all the subsets is a complete set of all the nodes of the blockchain; the decision arbitration module is composed of an arbitration node and further comprises an arbitration node, and the arbitration node is placed in the blockchain network and connected with all the detection nodes. According to the invention, a quantitative measurement index can be provided for the service data transmission efficiency in the blockchain network. Meanwhile, by means of the network channel of the sniffer, the hop count of data transmission can be reduced, the verification frequency can be correspondingly reduced, and the propagation speed can be increased from a network layer by means of the network channel of the sniffer.
Owner:福州博泉网络科技有限公司
Debugging method of overdrive brightness value lookup table, use method and display panel
ActiveCN109410850AReduce verification timesShorten the timeStatic indicating devicesLookup tableComputer science
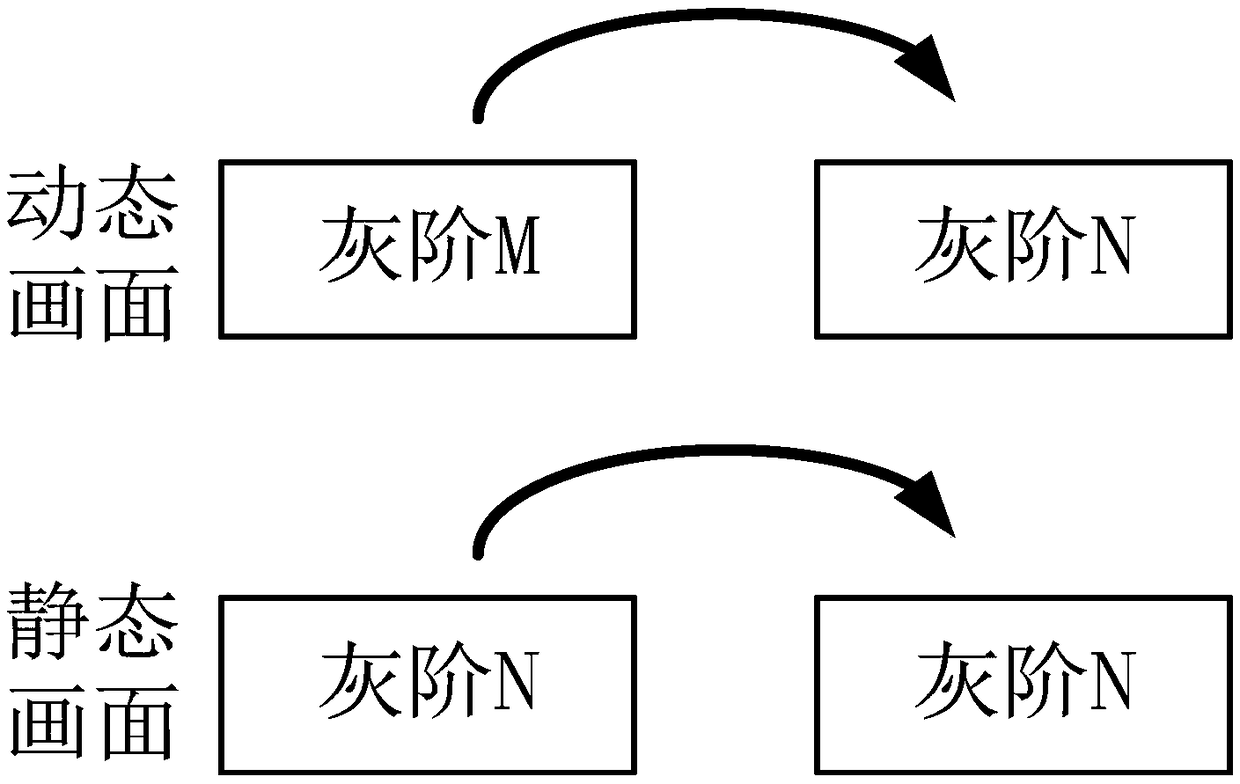
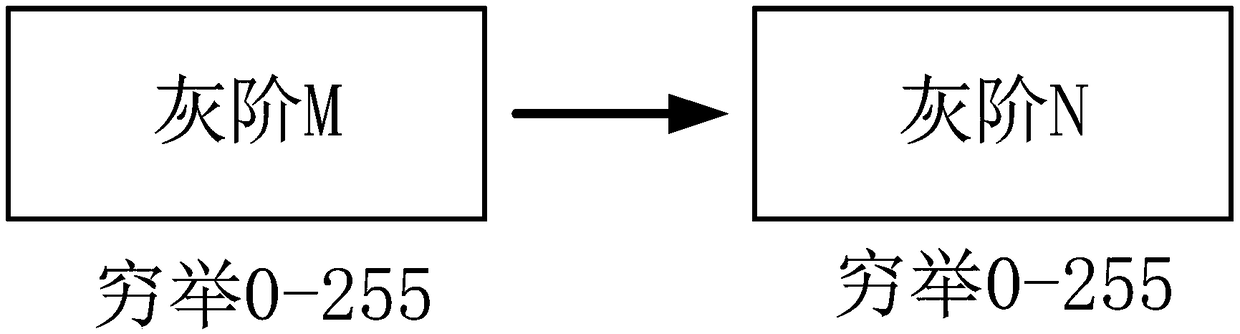
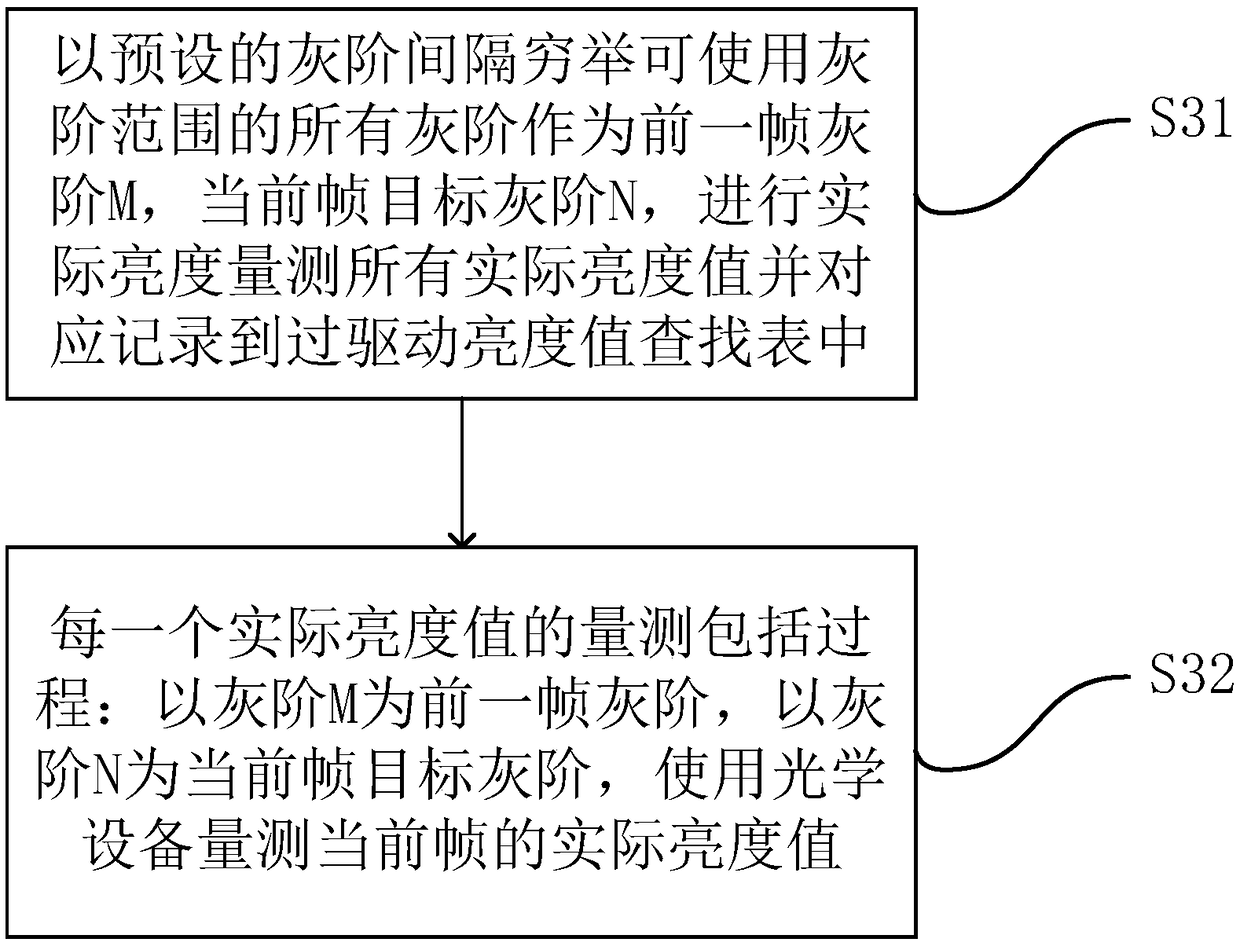
The invention discloses a debugging method of an overdrive brightness value lookup table, a use method and a display panel. The debugging method includes the steps of: using a preset gray scale interval to exhaust all gray scales of a usable gray scale range as a previous frame gray scale M, using a preset gray scale interval to exhaust all gray scales of a usable gray scale range as a current frame target gray scale N, measuring the actual brightness, and recording all the actual brightness values into the overdrive brightness value lookup table correspondingly, wherein the measurement process of each actual brightness value includes: taking the gray scale M as the previous frame gray scale, adopting the gray scale N as the current frame target gray scale, and using optical equipment to measure the actual brightness value of the current frame. The debugging method provided by the invention can reduce the debugging time.
Owner:HKC CORP LTD
An optimization method of block chain tamper-proof technology
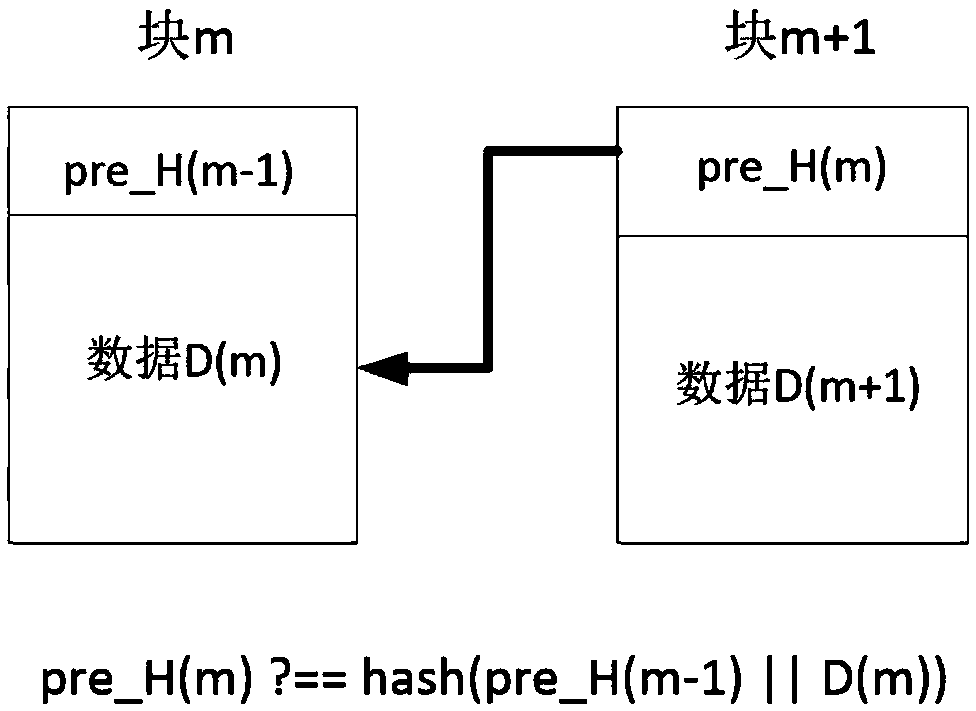
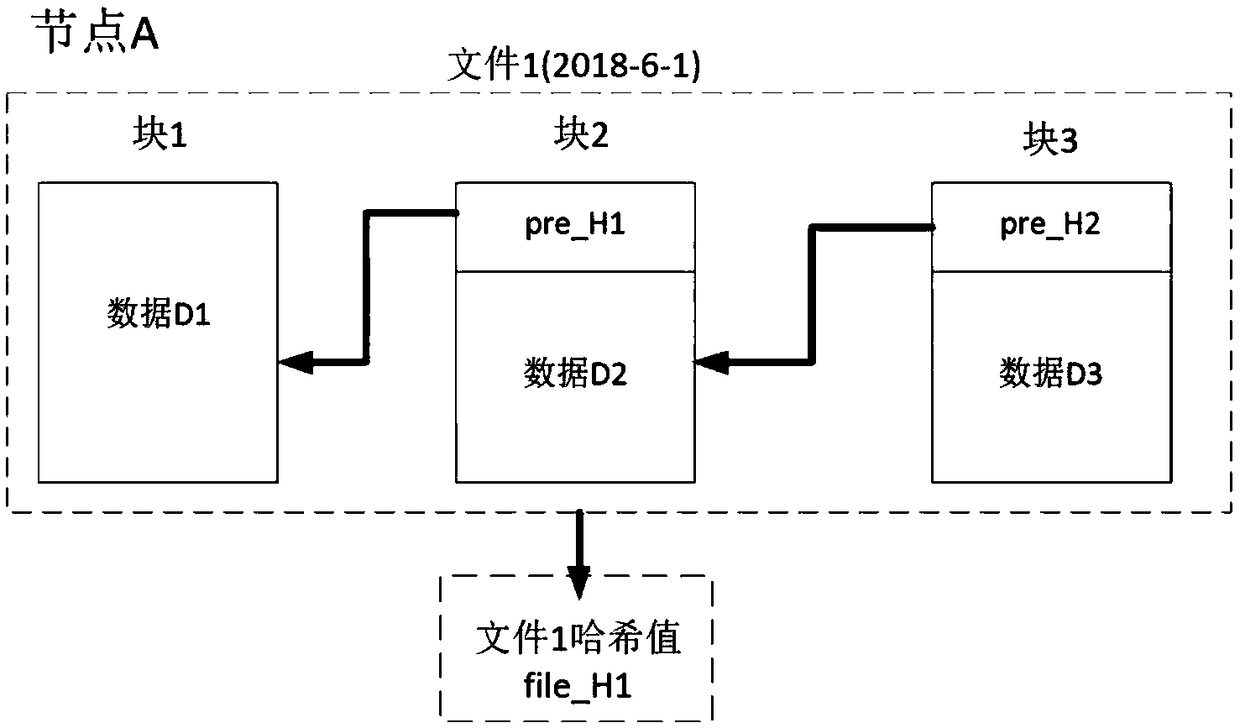
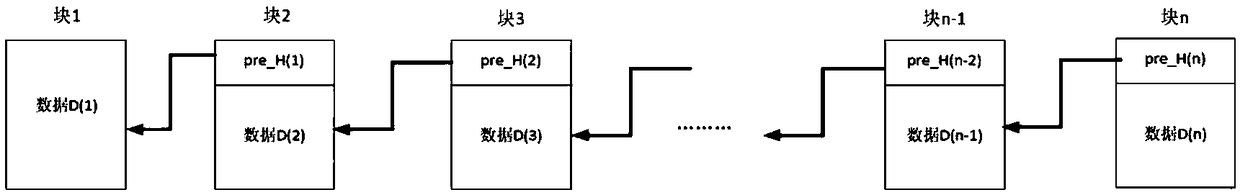
ActiveCN109102284ARepair dataReduce verification timesFinancePayment protocolsTamper resistanceData storing
The invention provides a method for discovering tampering with the account book data stored in a node on a block chain. The method firstly traverses and verifies whether all blocks except the last block in the block chain stored in the node are tampered with. If there are tampered blocks in the verification node, the pre_H is recorded for recovering the data. When a new block is added to the nodeblock chain, the pre_H stored in the new block and the data stored in the new block are signed with the private key of the node and stored separately. The pre_H and data stored in the latest block arecompared with the pre_H and data stored in the signature to verify whether the data in the new block has been tampered with and to locate and recover the data in the previously tampered block.
Owner:黄芸芸
V2G network cross-domain transaction security method based on block chain
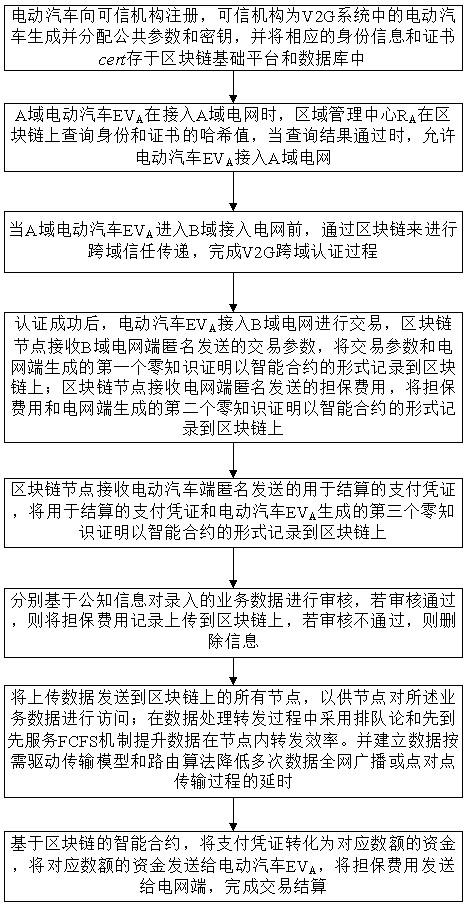
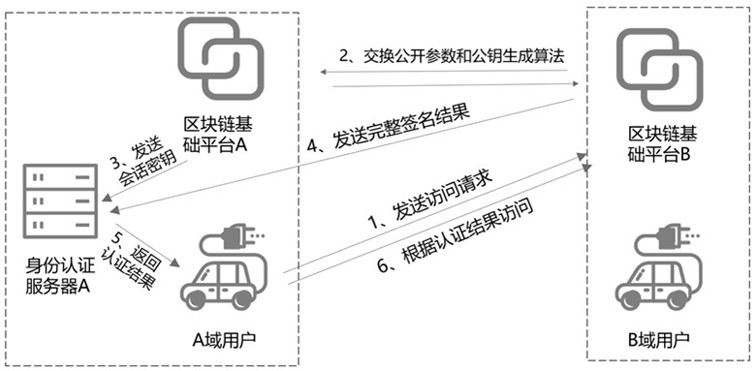
InactiveCN114154993AReduce verification timesImprove efficiencyInformation technology support systemProtocol authorisationPower gridElectric vehicle
The invention discloses a V2G network cross-domain transaction security method based on a block chain. The method comprises the following steps: step 1, an electric vehicle registers in a trusted mechanism; step 2, when the A-domain electric vehicle EVA accesses the A-domain power grid, a region management center RA inquires the Hash values of the identity and the certificate on the block chain, and when the inquiry result passes, the electric vehicle EVA is allowed to access the A-domain power grid; and step 3, before the A-domain electric vehicle EVA enters the B-domain access power grid, cross-domain trust transfer is carried out through the block chain, and a V2G cross-domain authentication process is completed. According to the method, the characteristic that the block chain technology is not easy to tamper is utilized, the Hash algorithm is used for verifying the certificate, the signature and verification times of the public key algorithm are reduced, and the method is high in efficiency and high in expandability. The introduction of the block chain technology provides a new thought and method for solving the security problem of the smart power grid.
Owner:国网天津市电力公司营销服务中心 +3
Block generation and transaction verification method suitable for energy blockchain
PendingCN111080298AFast verificationReduce verification timesFinanceDatabase distribution/replicationEngineeringFinancial transaction
The invention relates to the field of energy block chains, in particular to a block generation and transaction verification method suitable for an energy blockchain. An obvious hotspot account is provided for electric energy transaction; an original block generation mode enables a blockchain to verify whether a transaction is legal, and needs the same calculation and storage cost for each account.According to the invention, targeted optimization is carried out on an electric energy transaction scene; according to the method, by modifying the merkle tree organization form, the account with thehigh priority is closest to the root node of the query when forming the block and can be found more quickly, and compared with the prior art, the method can achieve the purpose of reducing the calculation cost and has the characteristics of flexibility, simplicity and high practicability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
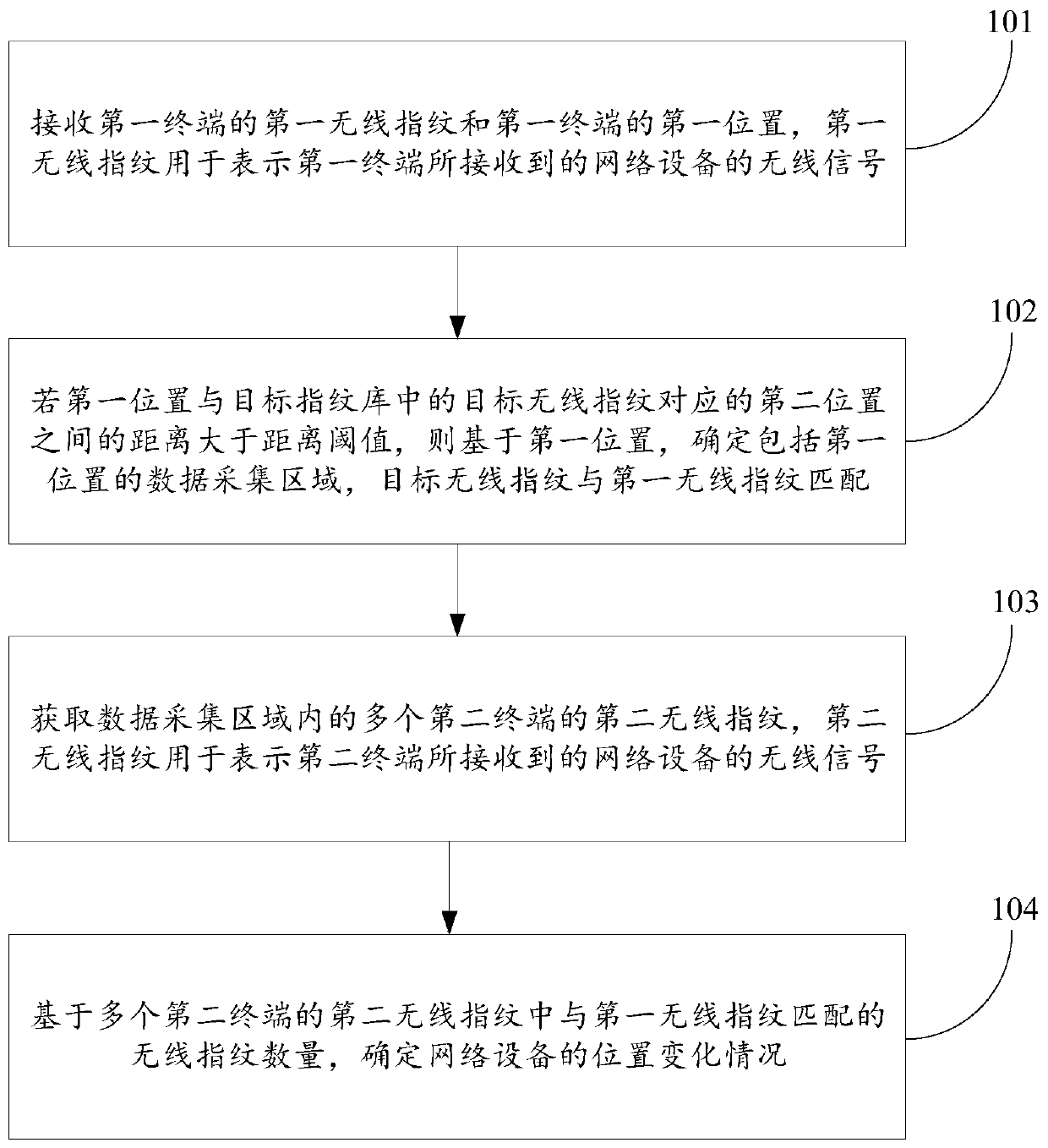
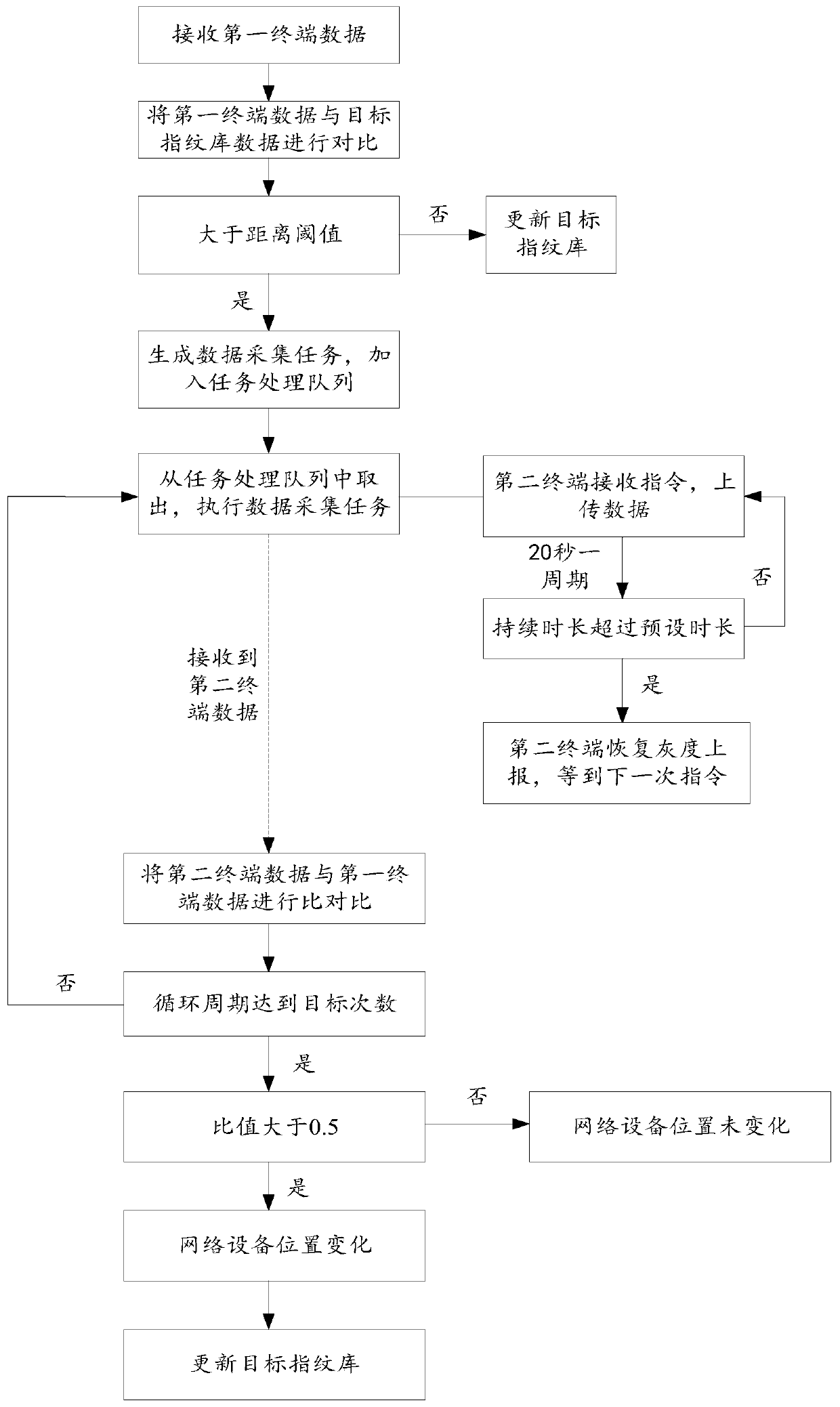
Method and device for determining position change of network equipment, computer equipment and medium
ActiveCN110099442AImprove referenceThe verification result is accurateWireless communicationData acquisitionComputer terminal
The invention relates to a method and device for determining position change of network equipment, computer equipment and a medium, and belongs to the field of positioning. The method comprises the following steps: receiving a first wireless fingerprint of a first terminal and a first position of the first terminal; if the distance between the first position and a second position corresponding toa target wireless fingerprint in the target fingerprint database is greater than a distance threshold, determining a data acquisition area comprising the first position based on the first position, the target wireless fingerprint being matched with the first wireless fingerprint; acquiring second wireless fingerprints of a plurality of second terminals in the data acquisition area; and determiningthe position change condition of the network equipment based on the number of the wireless fingerprints matched with the first wireless fingerprint in the second wireless fingerprints of the plurality of second terminals. By acquiring the wireless fingerprint of the terminal in the data acquisition area, the verification process is accelerated, the acquisition of useless information is reduced, and the verification efficiency is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
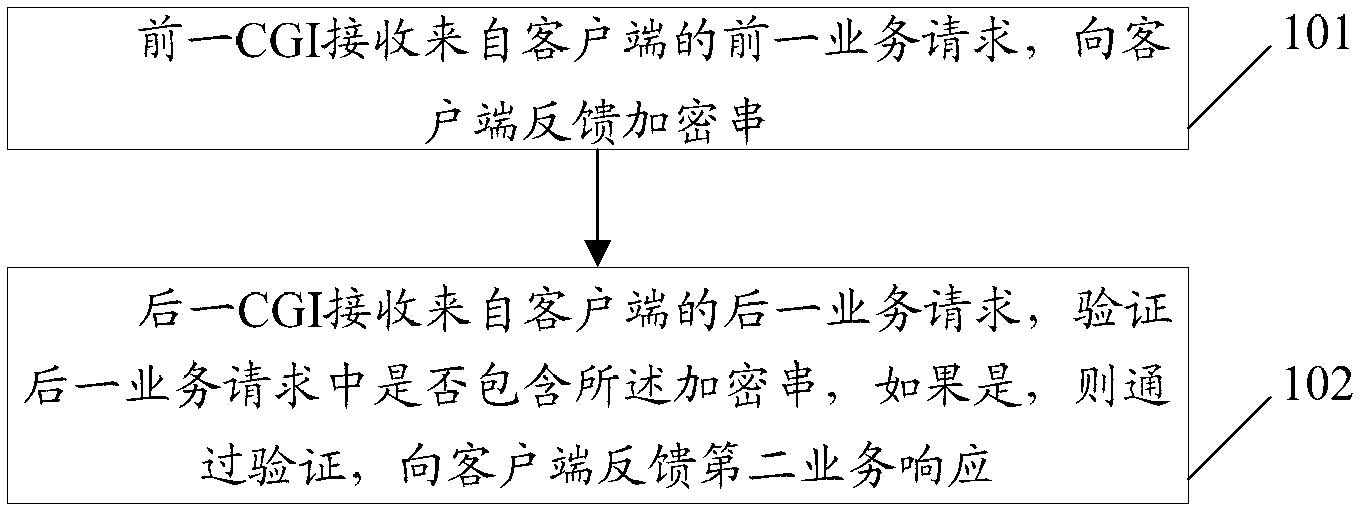
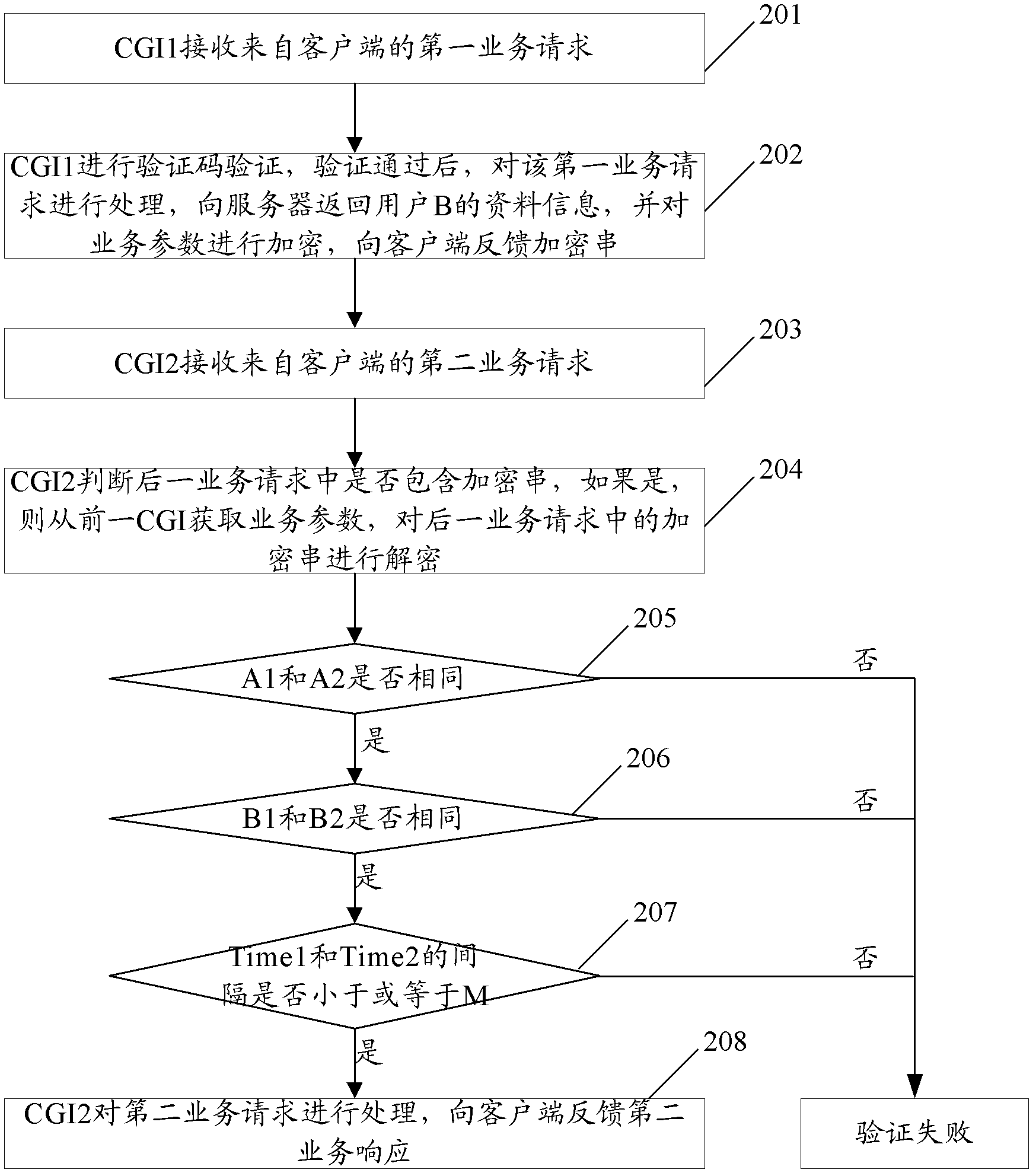
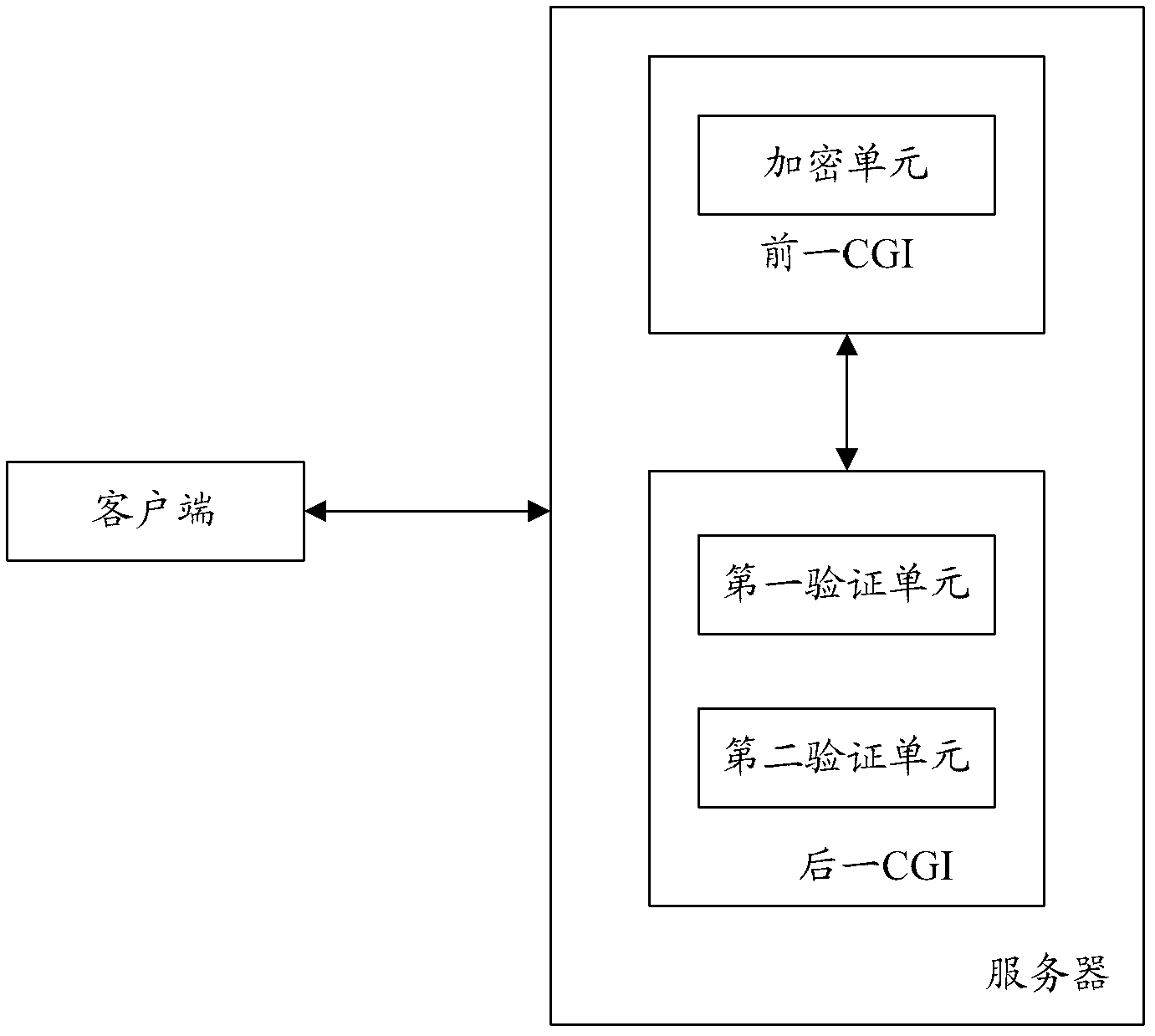
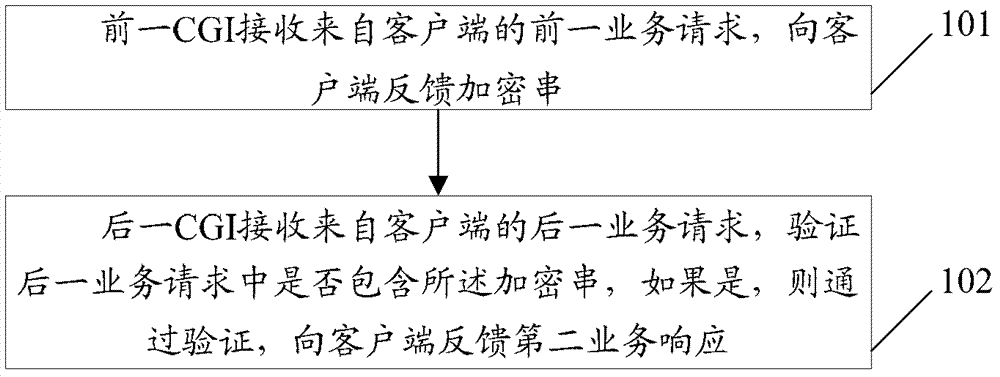
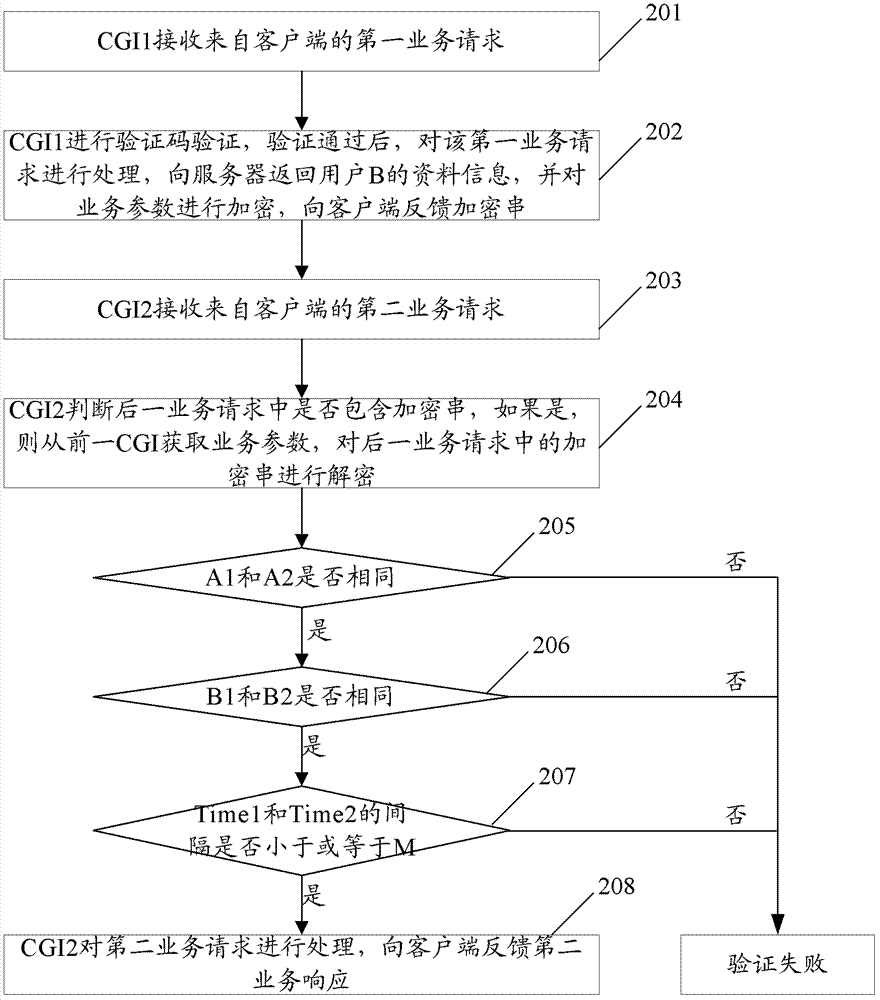
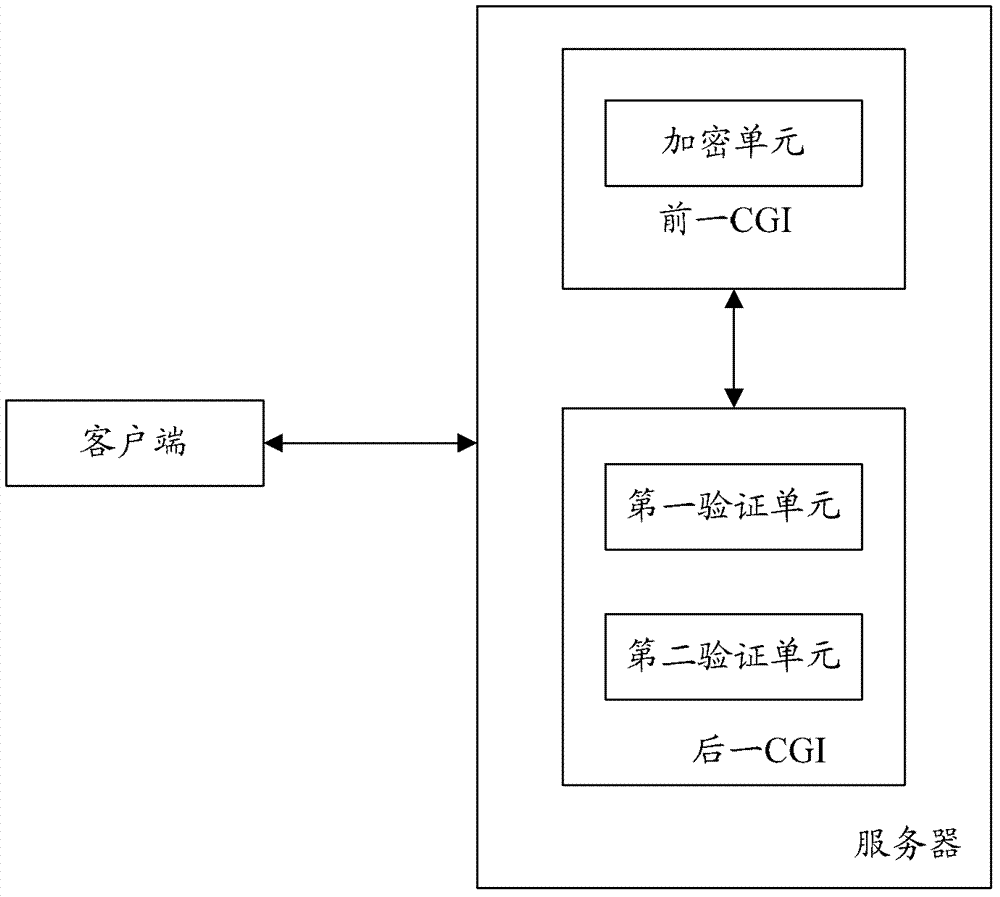
Protection method and protection system of common gateway interface business
The invention provides a protection method and a protection system of a common gateway interface (CGI) business. The method comprises that a first CGI receives a first business request from a client side and sends encrypted strings to the client side, a second CGI receives a second business request from the client side and verifies whether the second business request includes the encrypted strings, if so, the verification is passed through, and a second business response is sent to the client side. The protection method and the protection system of the common gateway interface business can guarantee the safety of the common gateway interface business under the premise of reducing the number of the verification of verification codes.
Owner:TENCENT TECH (SHENZHEN) CO LTD
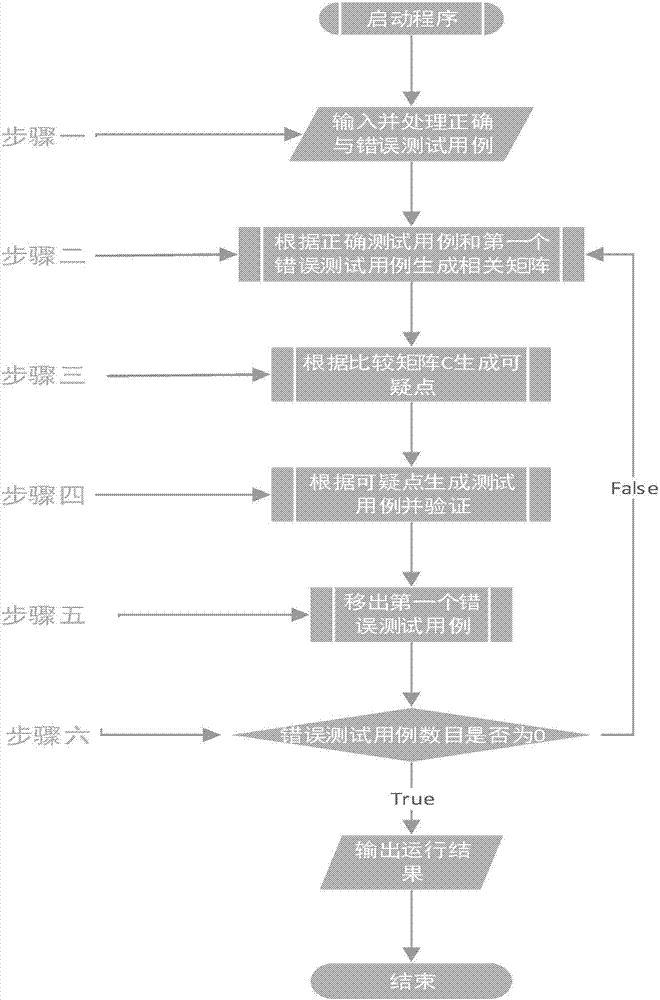
Method for obtaining dependencies between process modules based on test cases
ActiveCN107992414AAvoid analysisEasy to analyzeSoftware testing/debuggingProcess moduleComputer module
The invention relates to a method for obtaining dependencies between process modules based on test cases. The method aims at solving the problems that verification efficiency is extremely low and there are a large number of redundant verification problems when a module m is larger due to the fact that orders of magnitude of the generated test cases generated by means of an exhaustion method are power series. The method includes the steps of 1, inputting and processing correct and erroneous test cases, wherein the test cases include all process modules; 2, generating a correlation matrix basedon the correct test cases and a first erroneous test case; 3, generating suspicious points according to a comparison matrix C; 4, generating the test cases based on the suspicious points and verifyingthe test cases; 5, removing the first erroneous test case; 6, determining whether or not the number of the erroneous test cases is 0; outputting operation results if the number is 0; executing the step 2 if the number is not 0. The method is used in the task block dependency determination field.
Owner:黑龙江易通智能教育科技有限公司
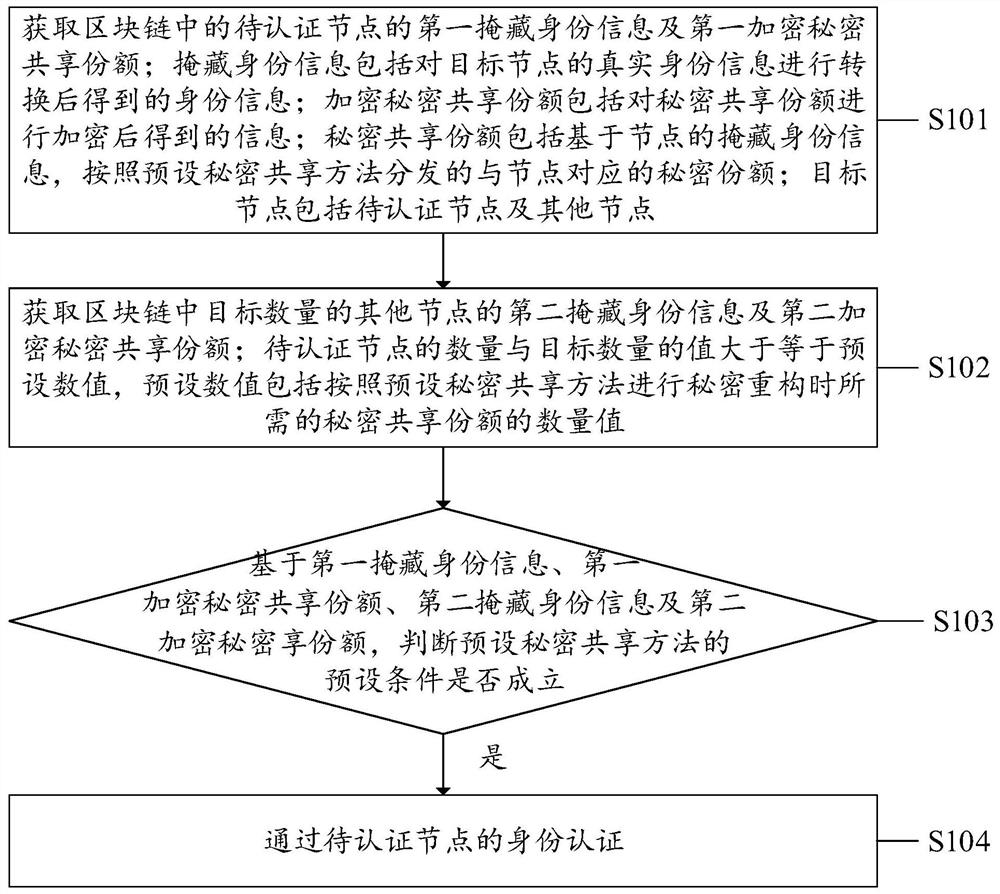
Identity authentication method, system and device and computer readable storage medium
ActiveCN112468293AEnsure safetySimplify the verification processKey distribution for secure communicationDatabase distribution/replicationEngineeringMaster key
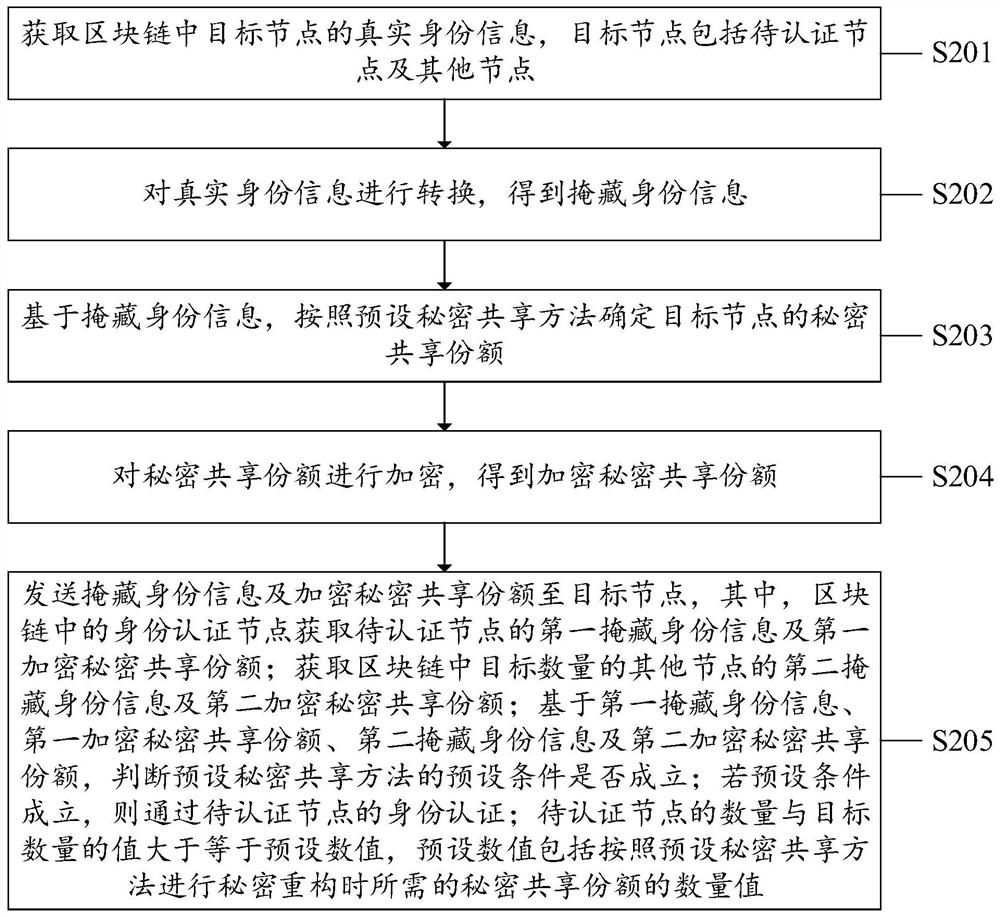
The invention discloses an identity authentication method, system and device, and a computer readable storage medium, which are applied to an identity authentication node in a block chain. The methodcomprises the steps of: obtaining first hidden identity information and a first encrypted secret sharing share of a to-be-authenticated node in the block chain; obtaining second hidden identity information and a second encrypted secret sharing share of a target number of other nodes in the block chain; based on the first hidden identity information, the first encrypted secret sharing share, the second hidden identity information and the second encrypted secret sharing share, judging whether a preset condition of a preset secret sharing method is satisfied or not; and if the preset condition issatisfied, passing the identity authentication of the to-be-authenticated node. The identity information is hidden, the real identity information of the target node cannot be leaked, anonymous identity authentication can be realized, only the encrypted master key can be obtained after secret recovery is performed on the encrypted secret sharing share according to the preset secret sharing method,and the method security can be ensured; and only one-time verification is needed, so that the efficiency is high.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
A whole vehicle electric balance simulation test method
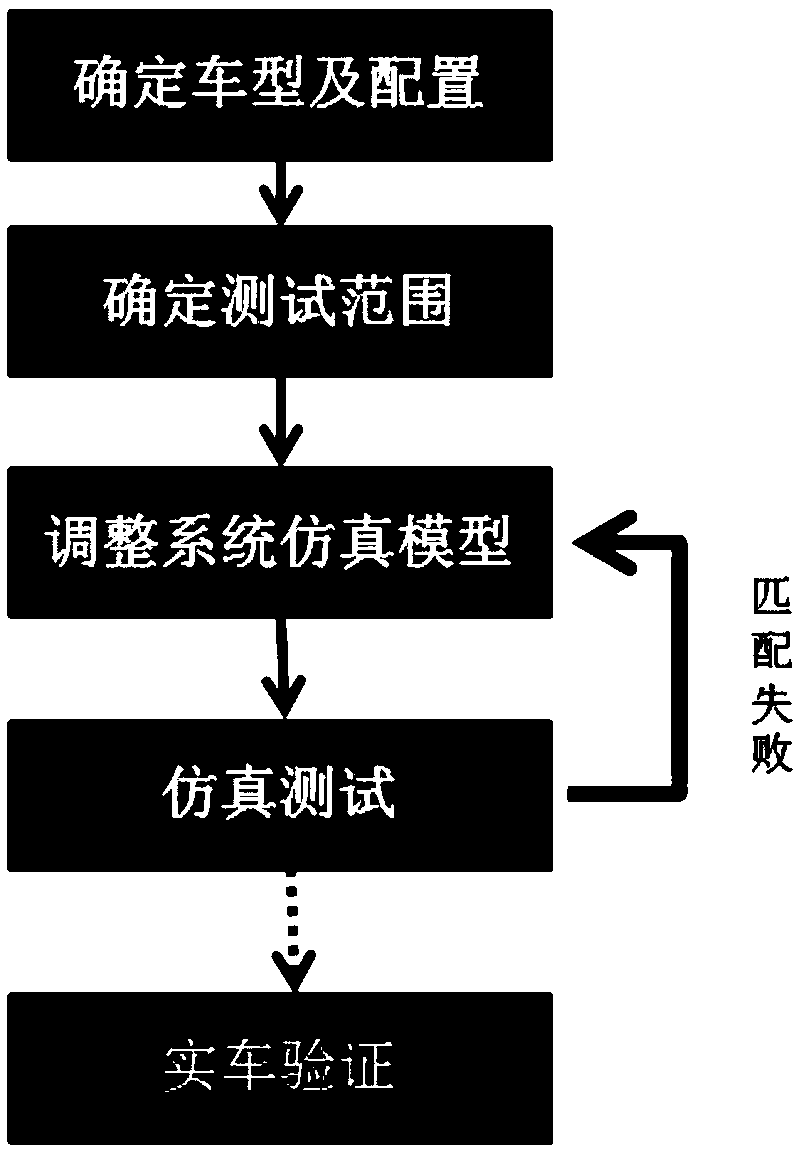
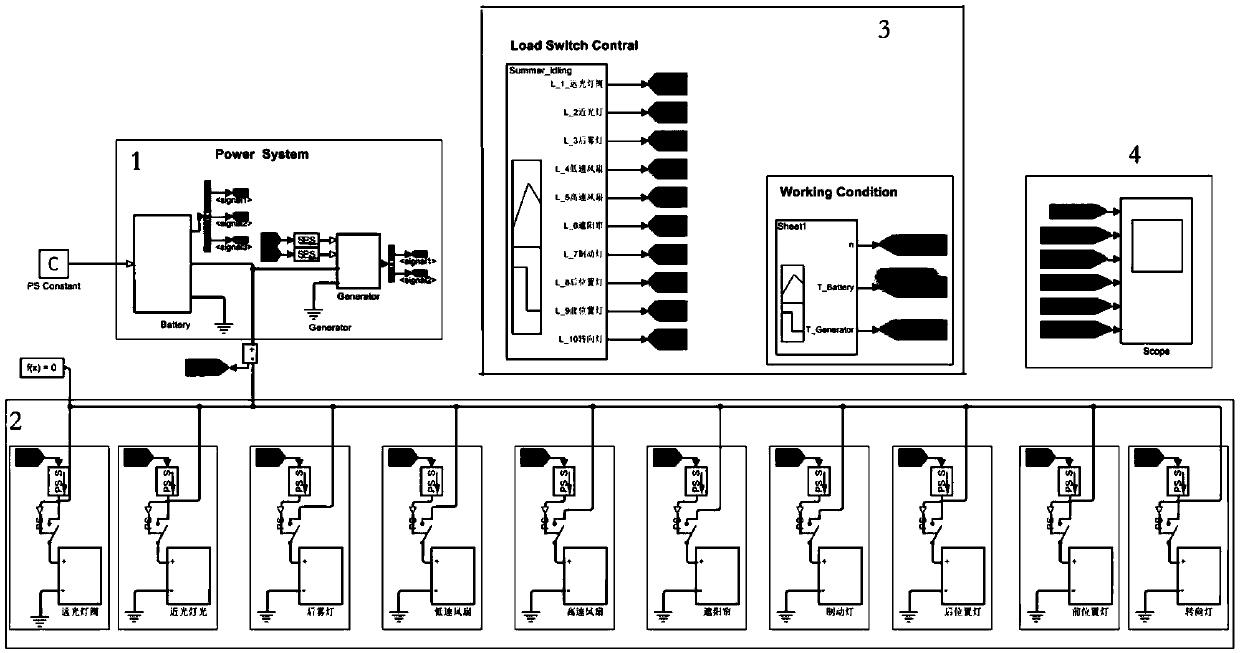
PendingCN109583127AReduce verification timesAdaptableGeometric CADDesign optimisation/simulationModel selectionSimulation
The invention discloses a whole vehicle electric balance simulation test method. An electric balance simulation model is established through software; And simulating each working condition according to the electric balance experiment standard of each main engine plant, displaying parameters corresponding to the electric balance judgment standard, and comparing the display parameters with the electric balance standard to obtain a simulation test result. The method has the advantages that the cost of manpower and material resources is low, the period is short, and the verification frequency andresource consumption of a special vehicle person are reduced; Model selection configuration adjustment is flexible, problems are easy to find in time, and adjustment is convenient; Virtual developmentis achieved, adaptability is high, and precision is high.
Owner:CHERY AUTOMOBILE CO LTD
Chip verification auxiliary environment and chip verification system
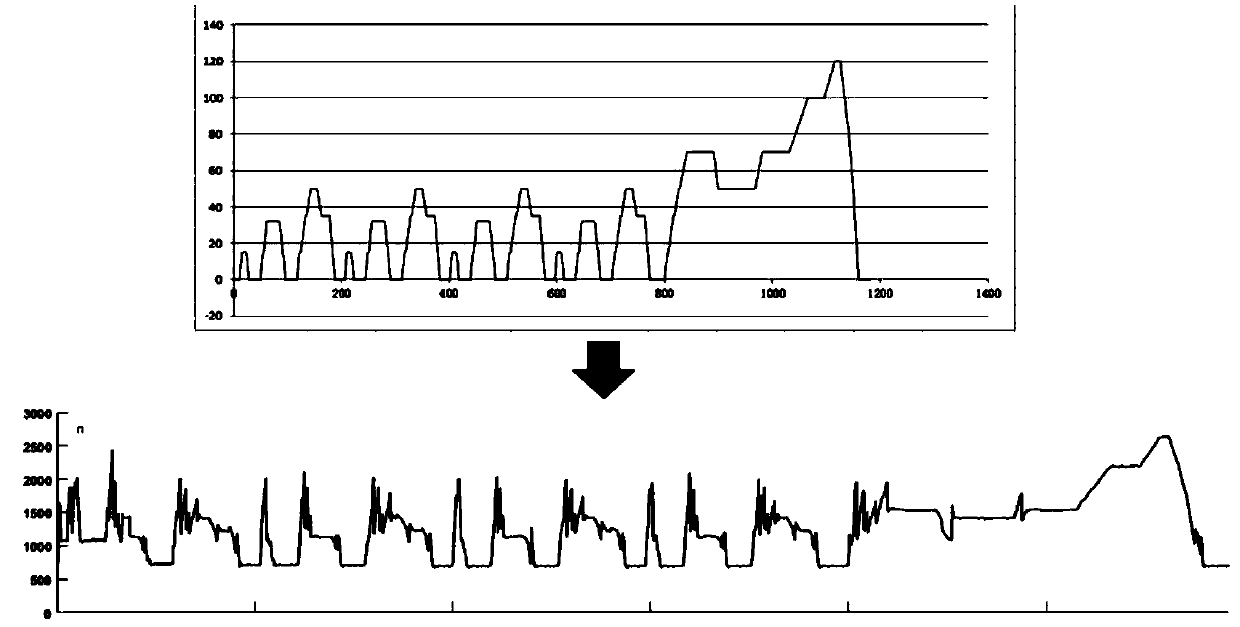
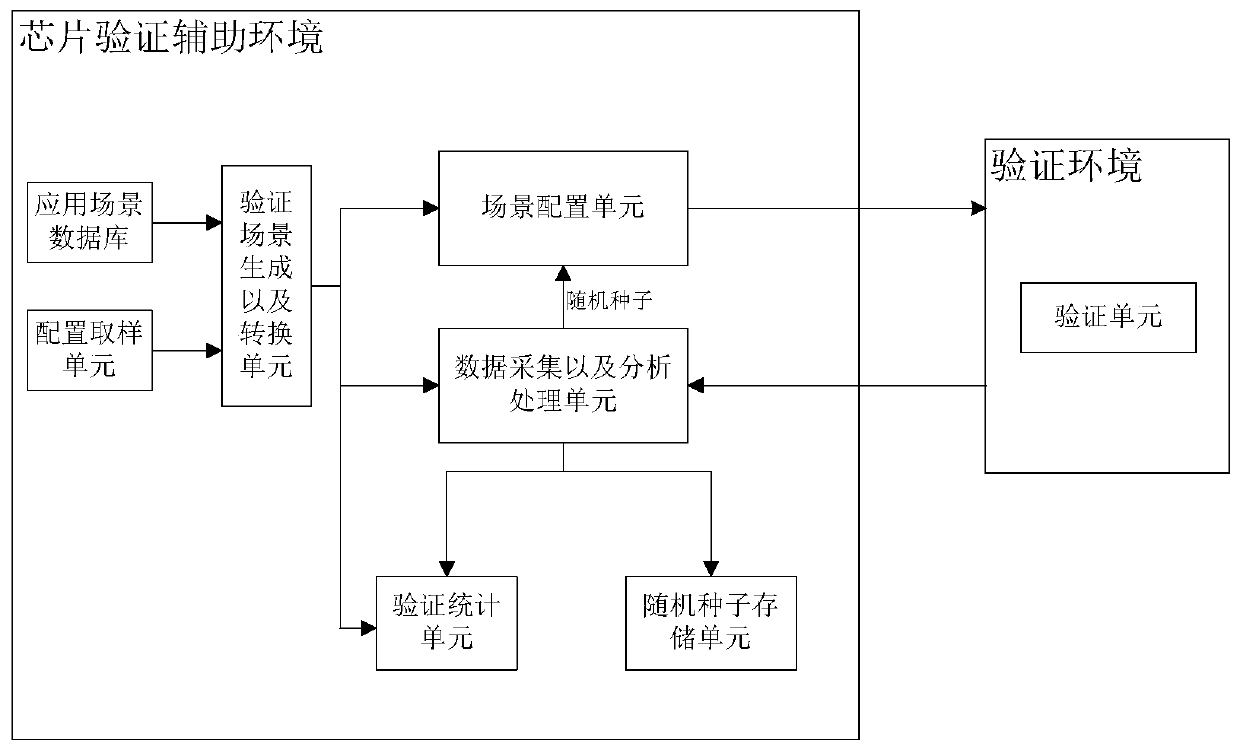
ActiveCN110781637ASpeed upReduce verification timesComputer aided designSpecial data processing applicationsComputer hardwareData acquisition
The invention discloses a chip verification auxiliary environment and a chip verification system. The chip verification auxiliary environment comprises an application scene database used for recordingall application scenes of a chip; a verification scene generation and conversion unit used for automatically generating various to-be-verified verification scenes according to the application scenesand converting formats of all configurations of the verification scenes into languages which can be recognized by the verification environment; a data acquisition and analysis processing unit used for generating a random seed and acquiring a verification result of a verification scene in the verification environment; a scene configuration unit which selects a verification scene according to the random seed, and sends each configuration of the verification scene to the verification environment for verification of the verification scene. According to an auxiliary environment, all verificationscenes can be automatically generated according to settings and converted into languages which can be recognized by the verification environment; the verification environment setting accuracy and thechip verification speed are greatly improved, and the chip development progress is accelerated.
Owner:ZHUHAI HUGE IC CO LTD
Message timeout determining method and device based on multi-processor system simulation
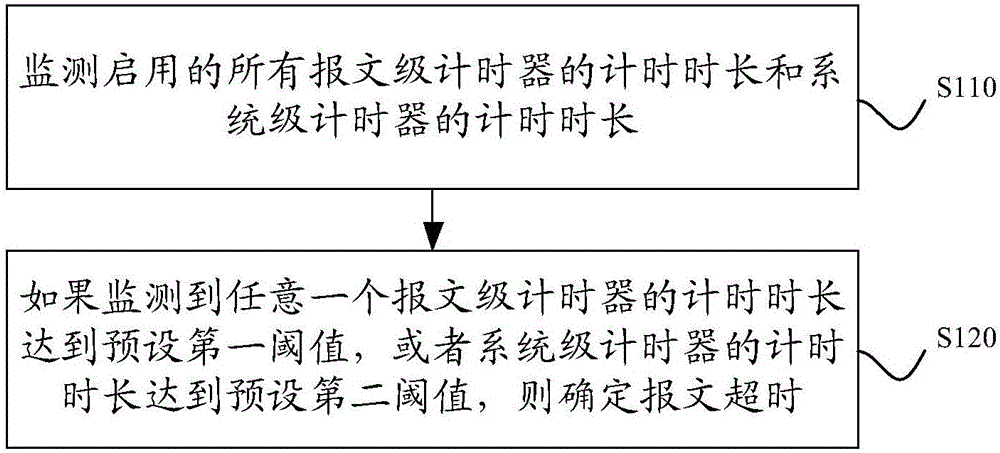
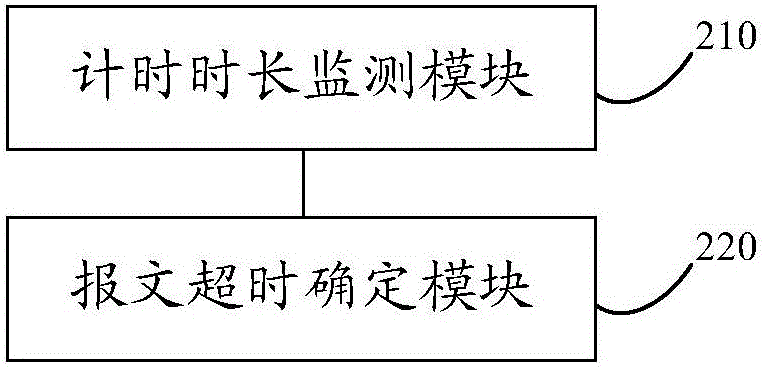
ActiveCN106452960AShorten the judgment timeReduce verification timeData switching networksSystems simulationReal-time computing
The invention discloses a message timeout determining method and device based on multi-processor system simulation. A multi-processor system comprises a plurality of message-level timers and a system-level timer; different message-level timers correspond to different messages; each message-level timer is used for recording the time interval of a corresponding message from sending to processing completion; and the system-level timer is used for recording the processing completion time interval of two sequentially processed messages. The method comprises the following steps of: monitoring the timing duration of all the started message-level timers and the timing duration of the started system-level timer; and determining message timeout if the fact that the timing duration of any message-level timer reaches a pre-set first threshold value or the timing duration of the system-level timer reaches a pre-set second threshold value is monitored. By means of the technical scheme provided in the embodiment of the invention, the timeout message judgement duration when the system is not in the worst condition can be effectively shortened; and thus, the verification duration is shortened.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Protection method and system for general gateway interface service
ActiveCN103179088BReduce verification timesEnsure safetyTransmissionClient-sideCommon Gateway Interface
The present invention provides a method and system for protecting CGI services of a general gateway interface, wherein the method includes: a previous CGI receives a previous service request from a client, and feeds back an encrypted string to the client; a latter CGI receives a subsequent service from the client request, verifying whether the encrypted string is included in the next service request, if yes, passing the verification and feeding back the second service response to the client. The solution of the invention can ensure the security of the general gateway interface service on the premise of reducing the verification times of the verification code.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Automobile safety analog simulation automatic control processing method and system
InactiveCN103413009AShorten the development cycleAutomate analysisSpecial data processing applicationsAutomatic Generation ControlAutomatic control
The invention provides an automobile safety analog simulation automatic control processing method and system. The method includes: building corresponding automatic generation computer aided engineering (CAE) modules according to specific classification, obtaining CAD data according to the specific classification, guiding the obtained CAD data of each class into corresponding automatic generation CAE module, and associating the specific classes to achieve CAE whole vehicle assembly. By means of the technical scheme, the automobile safety analog simulation automatic control processing method and system achieves automatic analyzing and processing of automobile simulation safety verification, is high in efficiency, greatly shortens verification duration and accordingly effectively shortens development period of new model cars.
Owner:罗斯德尔汽车工程技术(北京)有限公司
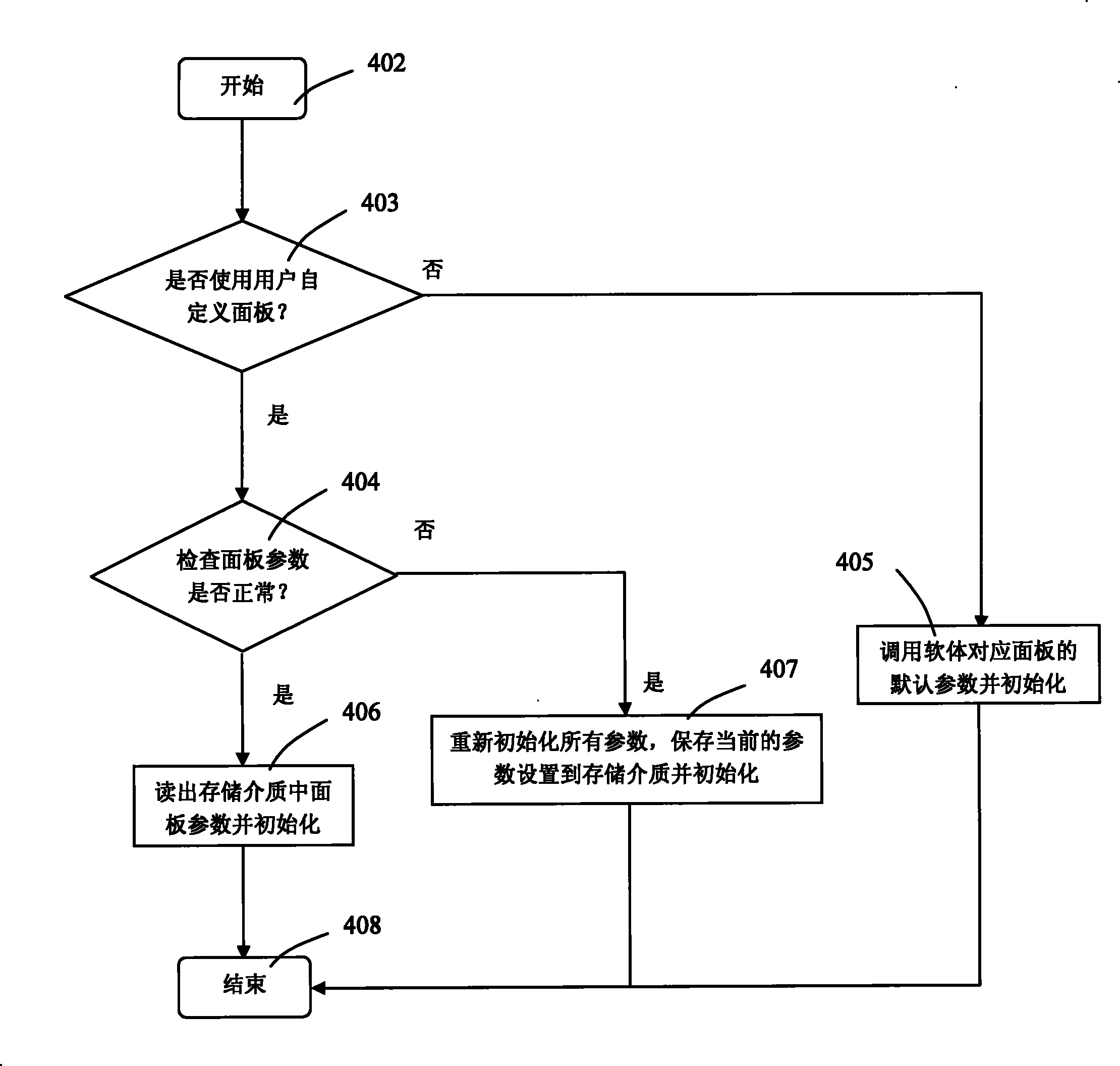
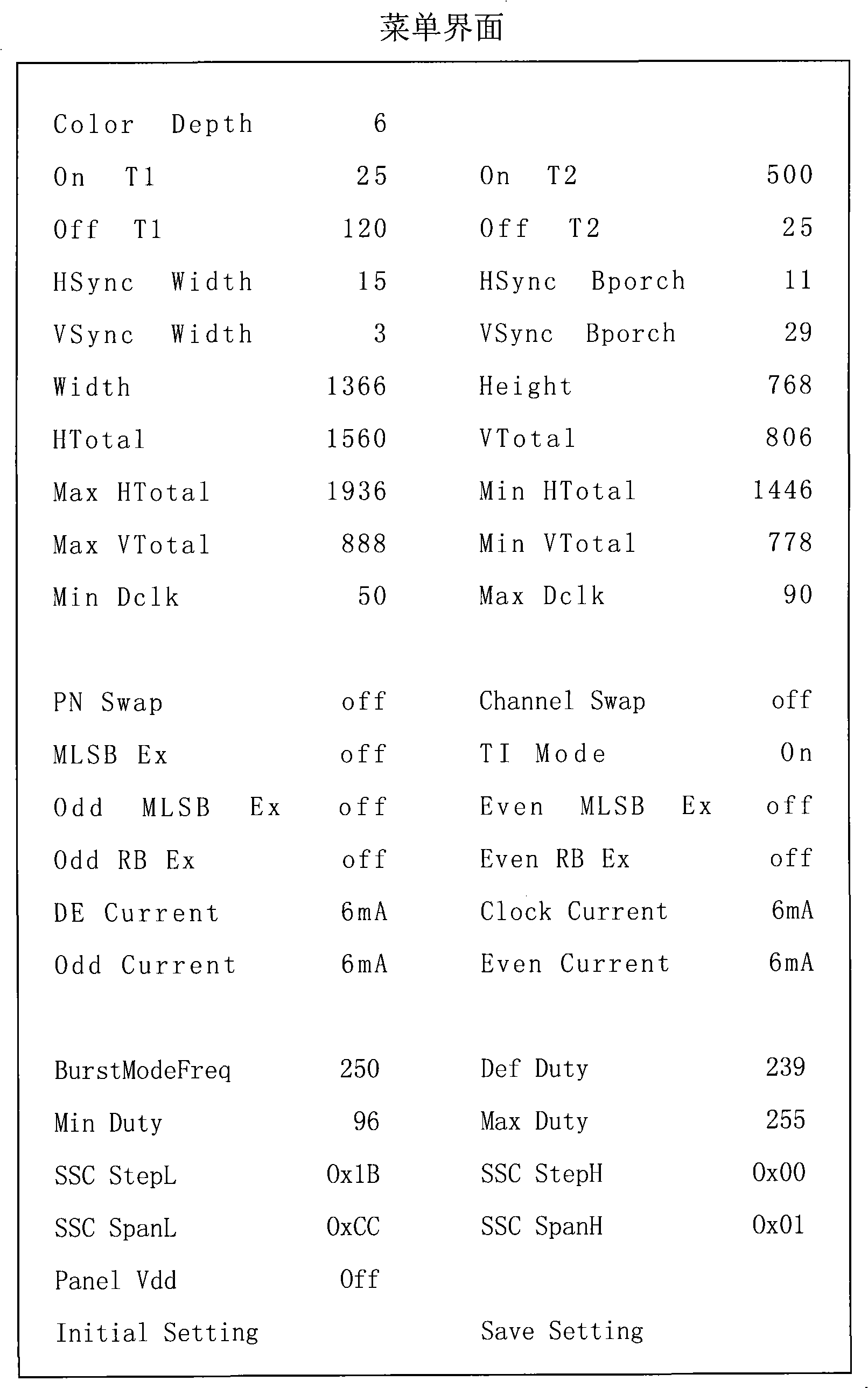
Method for reducing LCD device development cycle
InactiveCN101435931BShorten the development cycleReduce the number of versionsSpecific program execution arrangementsNon-linear opticsLiquid-crystal displayMaintainability
The invention relates to a method for shortening the development period of LCD panels. The method comprises the following steps: adding a panel parameter offshoring module into a LCD software program, storing the prior unchangeable panel parameters in a storage medium, and modifying a plant menu into an adjustable item to open to users for adjusting. In addition, the method adds a data loss protection mechanism for the added panel parameter offshoring module. The method has the advantages of reducing the released version number of the software program and the verification numbers of relational tests by verifiers, shortening the development period of importing the LCD to a new panel, improving the development flexibility of types of the LCD, and improving the development efficiency. In addition, the method improves the maintainability of the panel, improves the after-sales service efficiency, and reduces after-sales service costs.
Owner:TPV ELECTRONICS (FUJIAN) CO LTD
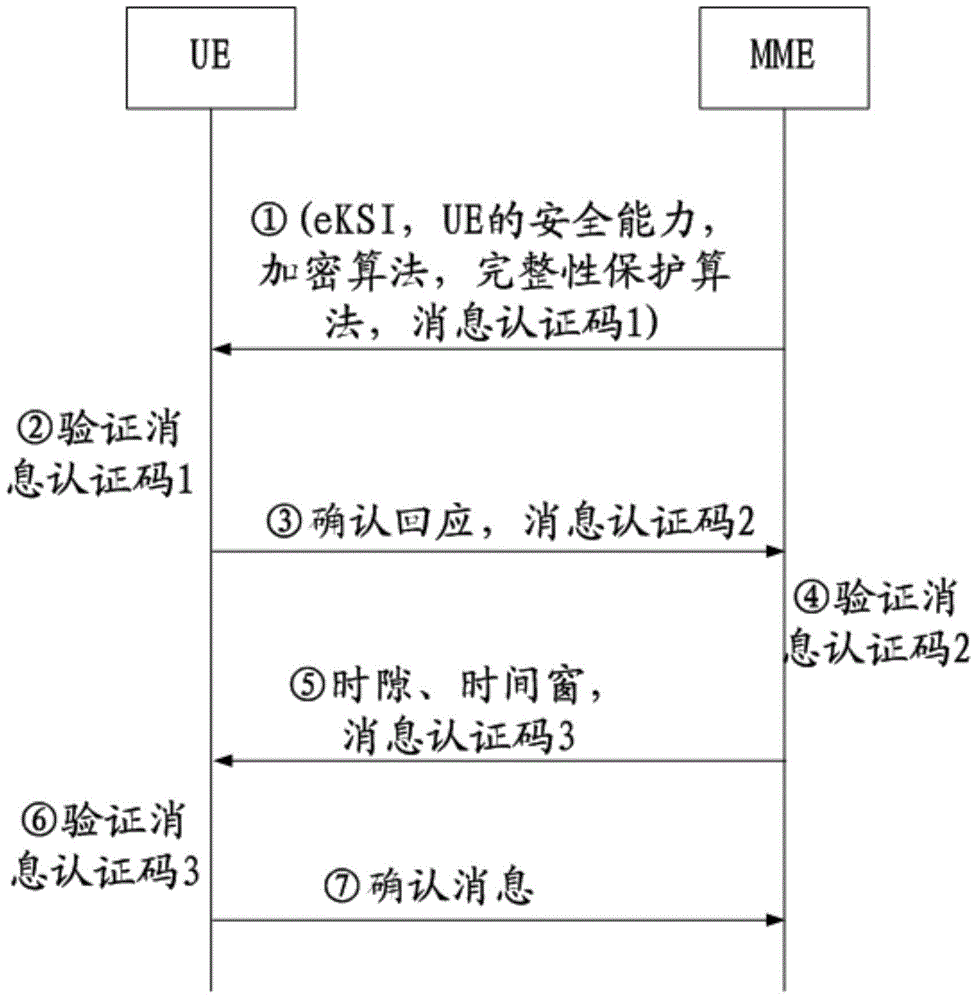
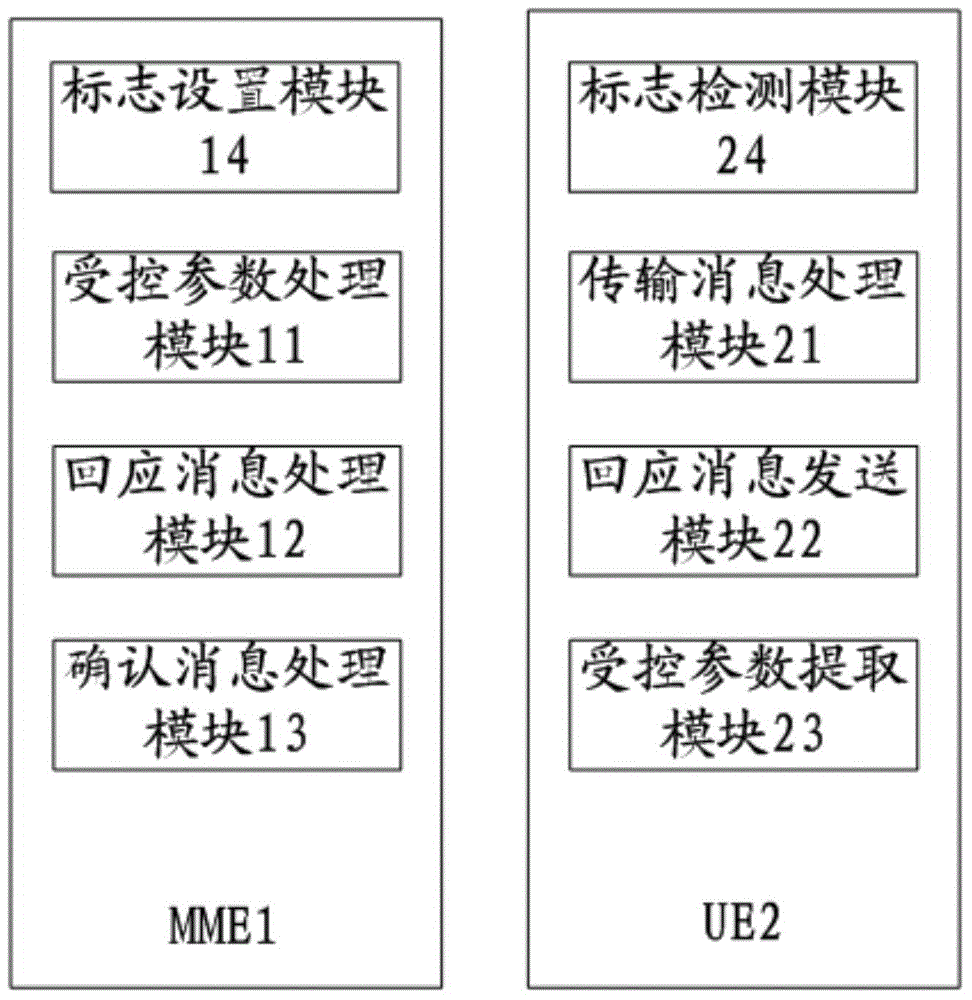
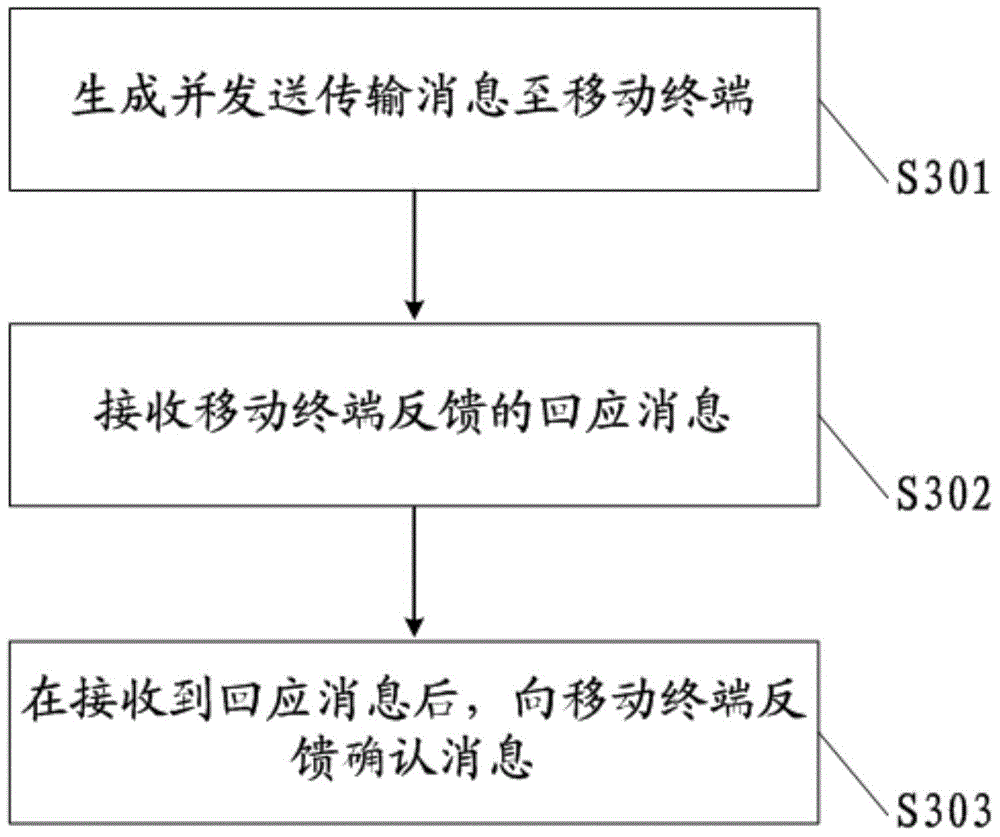
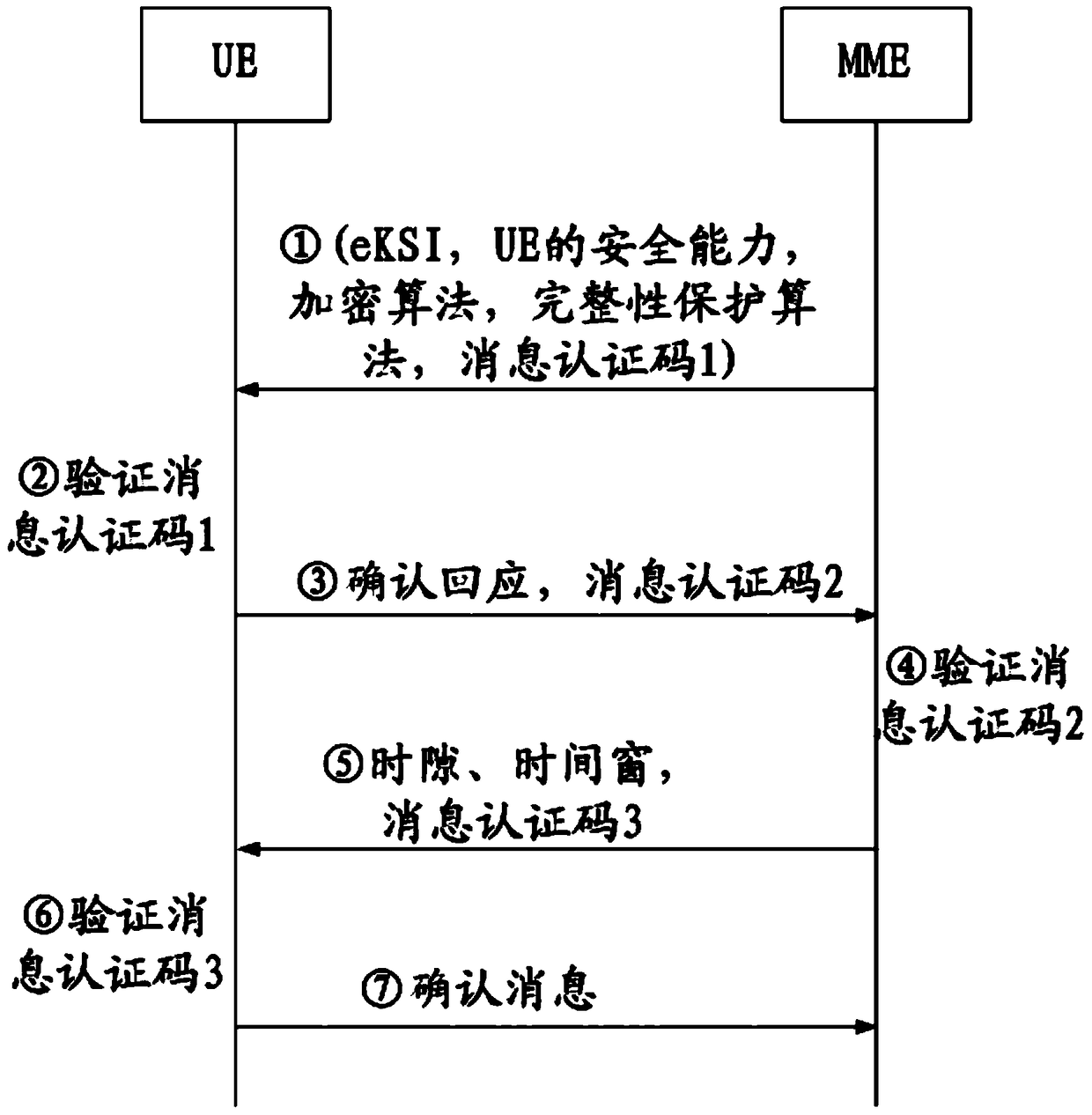
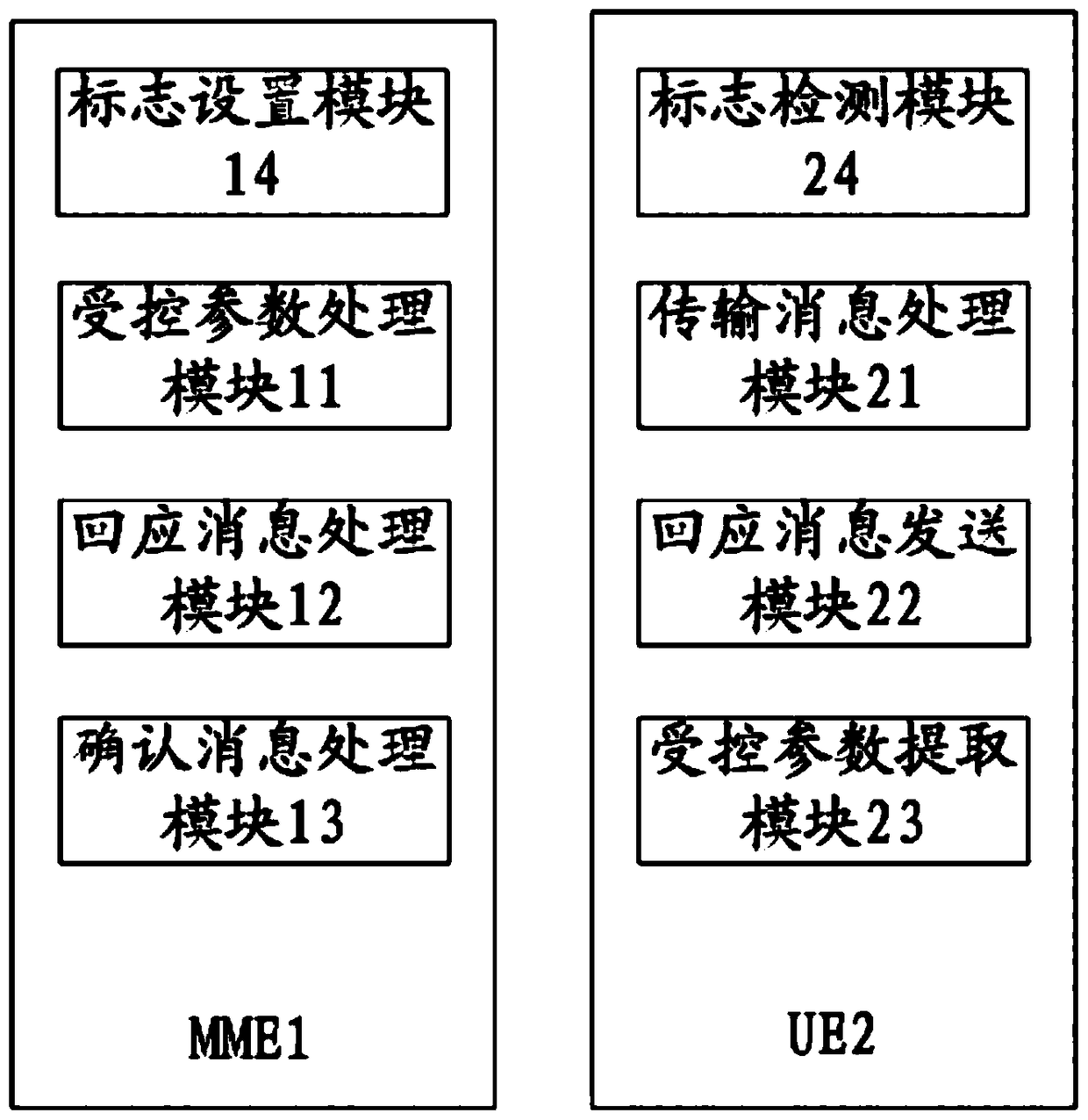
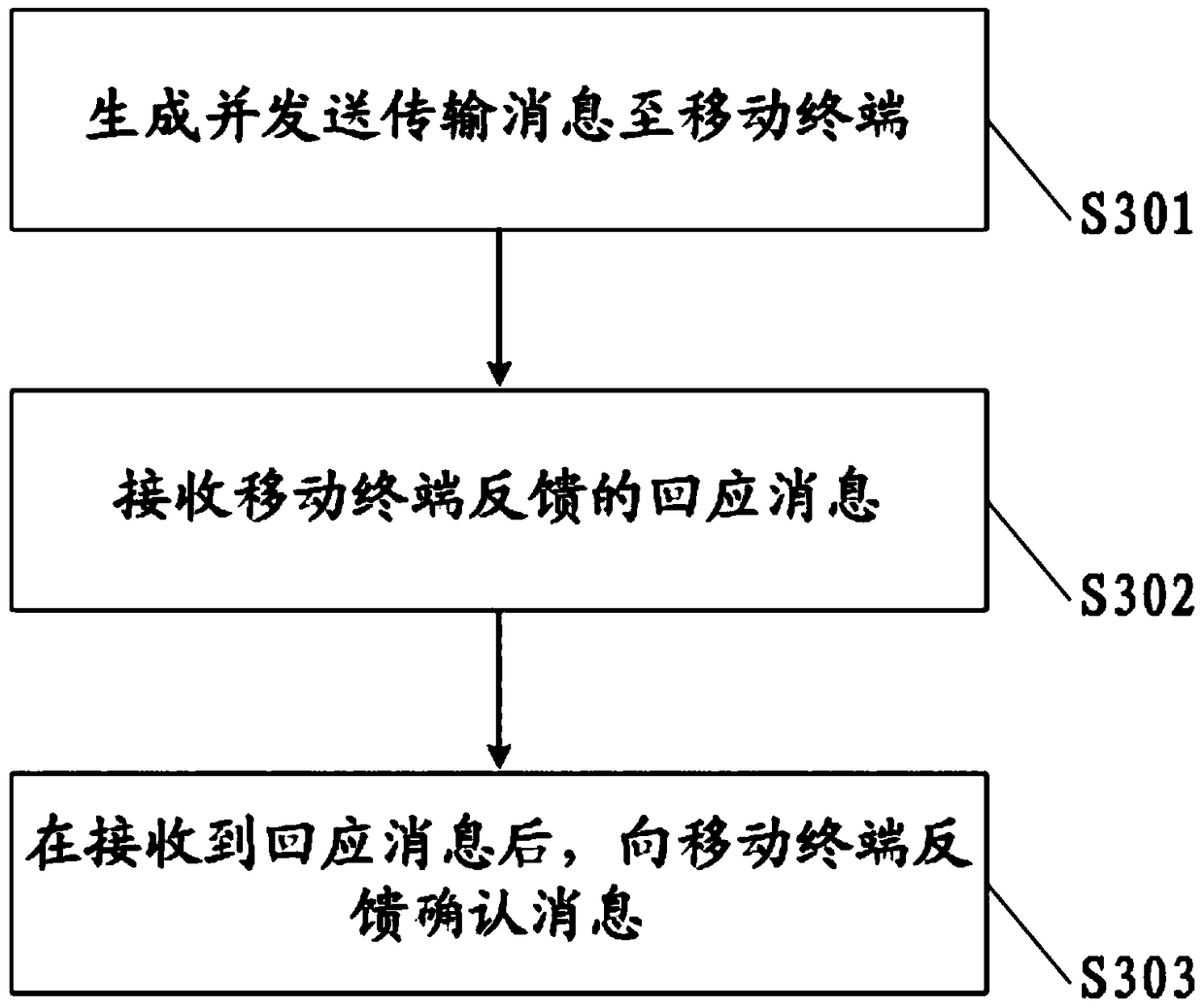
Mobility management entity, mobile terminal, controlled parameter transmission system and controlled parameter transmission method
ActiveCN104486717AGuaranteed safe transmissionReduce verification timesWireless commuication servicesSecurity arrangementComputer terminalMobility management
The invention provides a mobility management entity, a mobile terminal, a controlled parameter transmission system and a controlled parameter transmission method. The method includes the following steps: a transmission message is generated and transmitted to the mobile terminal, and a controlled parameter, a verification parameter and a first authentication parameter are carried by the transmission message; a response message fed back by the mobile terminal is received; after the response message is received, an acknowledgement message is fed back to the mobile terminal. By implementing the invention, the MME (mobility management entity) adds the controlled parameter, the verification parameter and the first authentication parameter into the same transmission message, and transmits the transmission message to the UE (user equipment), the UE feeds back the response message to the MME after verifying the transmission message, the MME transmits the acknowledgement message to the UE after receiving the response message, and thereby the transmission of the controlled parameter is complete by means of three times of information interaction; compared with the conventional controlled parameter transmission method, the flow is simplified.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Mobile management device, mobile terminal, transmission system and method for controlled parameters
ActiveCN104486717BGuaranteed safe transmissionReduce verification timesSecurity arrangementMachine-to-machine/machine-type communication serviceComputer hardwareTransport system
The invention provides a mobility management entity, a mobile terminal, a controlled parameter transmission system and a controlled parameter transmission method. The method includes the following steps: a transmission message is generated and transmitted to the mobile terminal, and a controlled parameter, a verification parameter and a first authentication parameter are carried by the transmission message; a response message fed back by the mobile terminal is received; after the response message is received, an acknowledgement message is fed back to the mobile terminal. By implementing the invention, the MME (mobility management entity) adds the controlled parameter, the verification parameter and the first authentication parameter into the same transmission message, and transmits the transmission message to the UE (user equipment), the UE feeds back the response message to the MME after verifying the transmission message, the MME transmits the acknowledgement message to the UE after receiving the response message, and thereby the transmission of the controlled parameter is complete by means of three times of information interaction; compared with the conventional controlled parameter transmission method, the flow is simplified.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Segmentation and verification method, device, electronic device, storage medium
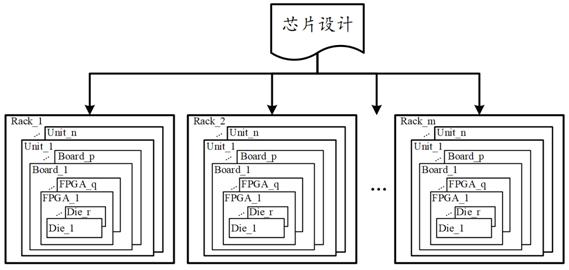
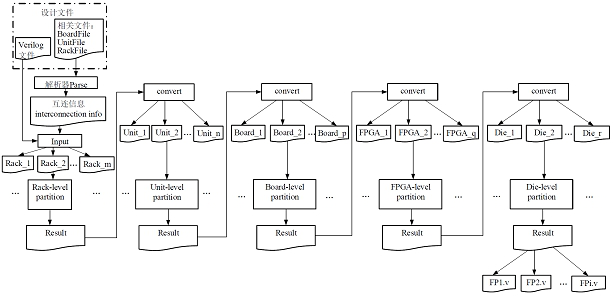
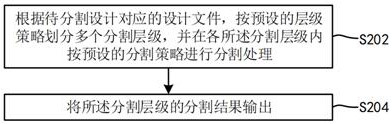
ActiveCN113255265BReduce segmentationReduce verification timesComputer aided designSpecial data processing applicationsComputer hardwarePersonalization
The embodiment of this specification provides a segmentation and verification method, device, electronic equipment, and storage medium, which are applied in the field of electronic design automation technology, wherein the segmentation method includes: dividing multiple segmentation levels according to the design level according to the design file corresponding to the design to be divided , and perform segmentation processing in each of the segmentation levels, and output the segmentation results. Through multi-level segmentation processing based on the design level, users can design custom groups to meet the user's personalized segmentation verification needs and improve the efficiency of segmentation verification.
Owner:S2C
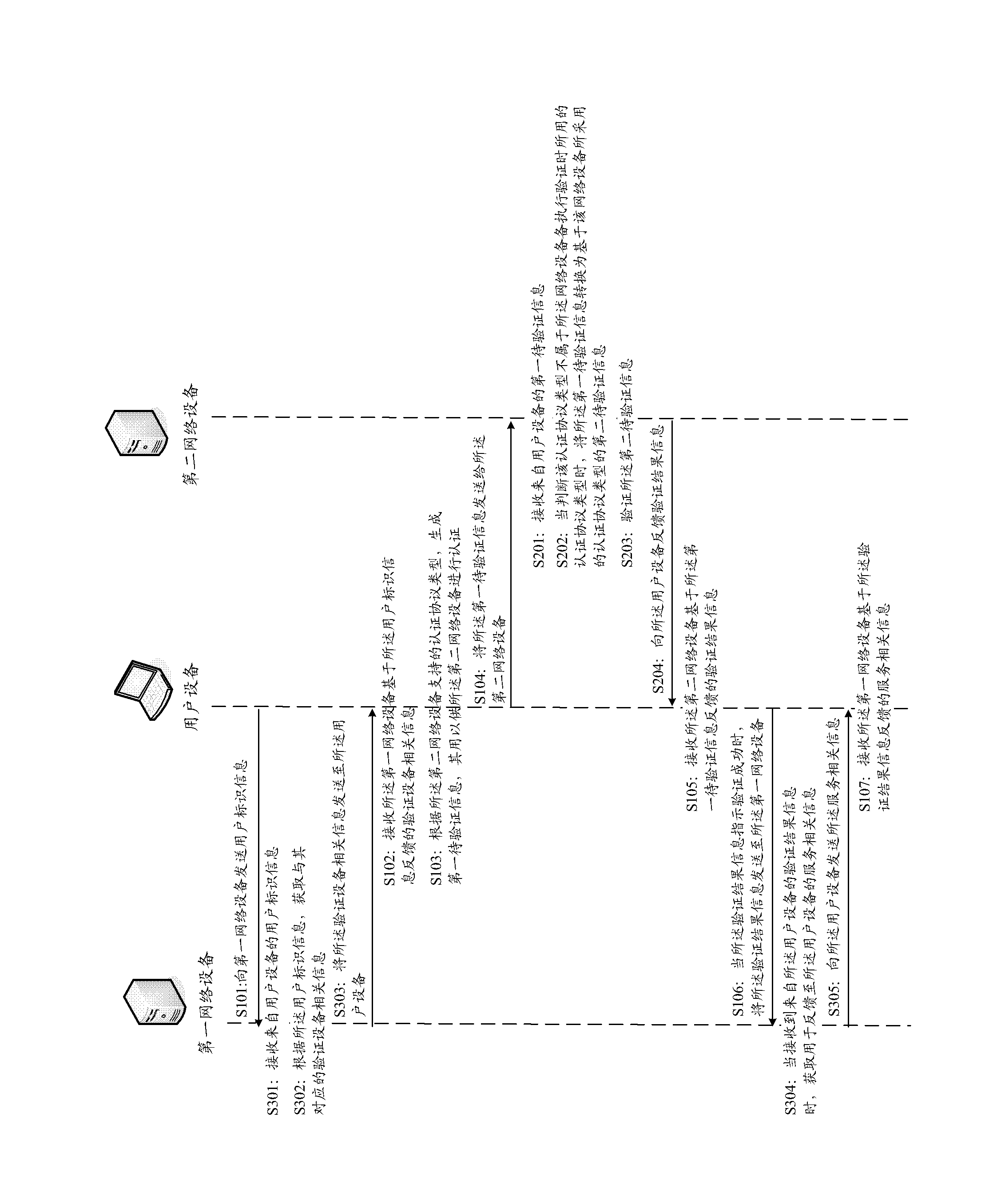
A method, device, device and system for performing third-party authentication
The invention aims at providing a method, a device, equipment and a system for executing third-party authentication. The method comprises the following steps of: receiving first information to be authenticated from user equipment; when an authentication protocol type does not belong to the authentication protocol type used when network equipment executes authentication, and converting the first information to be authenticated into second information to be authenticated used when the network equipment executes the authentication; authenticating the second information to be authenticated; and feeding authentication result information back to the user equipment. The method, the device, the equipment and the system have the advantages that the application under the network environment with multiple authentication protocol types can be realized, so that the efficiency for executing the third-party authentication is increased; the times for carrying out third-party authentication are reduced, so that the use experience of a user is improved; first network equipment does not need to keep connection with the user equipment all the time and can acquire information related to the authentication process directly according to authentication identifying information, so that the load of the first network equipment is reduced.
Owner:SHANGHAI SYNACAST MEDIA TECH
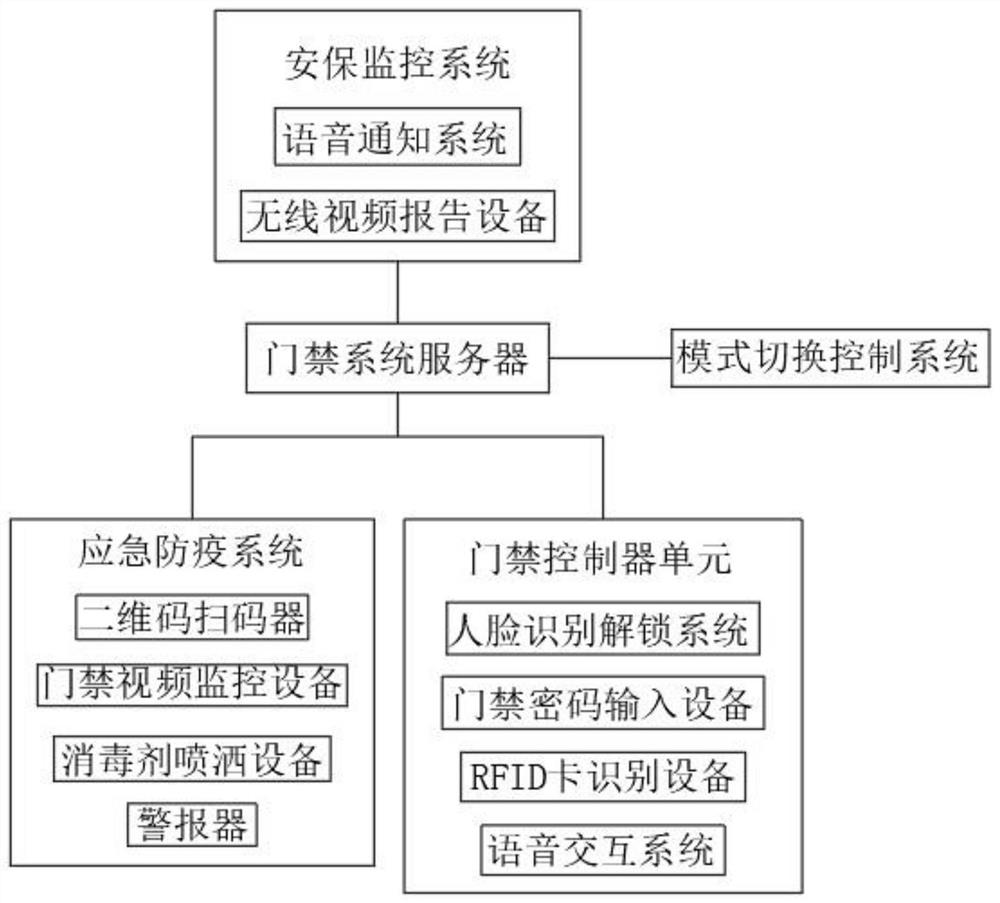
Emergency epidemic prevention system capable of switching modes
PendingCN114530007AReduce verification timeReduce the pressure of epidemic prevention workLavatory sanitoryClosed circuit television systemsData storage systemSpeech sound
The invention discloses an emergency epidemic prevention system capable of switching modes, and particularly relates to the field of building construction, which comprises an access control system server, an access control unit, an emergency epidemic prevention system, a security monitoring system and a mode switching control system, the access control system server is internally provided with a two-dimensional code recognition system for scanning health codes, a color recognition system for distinguishing image color data, a voice interaction system for voice interaction and an access control data storage system for storing user data; the entrance guard master control system is used for controlling entrance guard recognition and opening and closing; and the emergency anti-epidemic equipment control system is used for controlling emergency anti-epidemic equipment. According to the invention, by designing the emergency epidemic prevention system and the mode switching control system, the security and protection system of the community has a function of cooperating with epidemic prevention work, and by designing the security and protection monitoring system, the field condition at the entrance guard is fed back to the entrance guard system server in real time, and an instruction signal from the entrance guard system server is received.
Owner:豪越科技有限公司
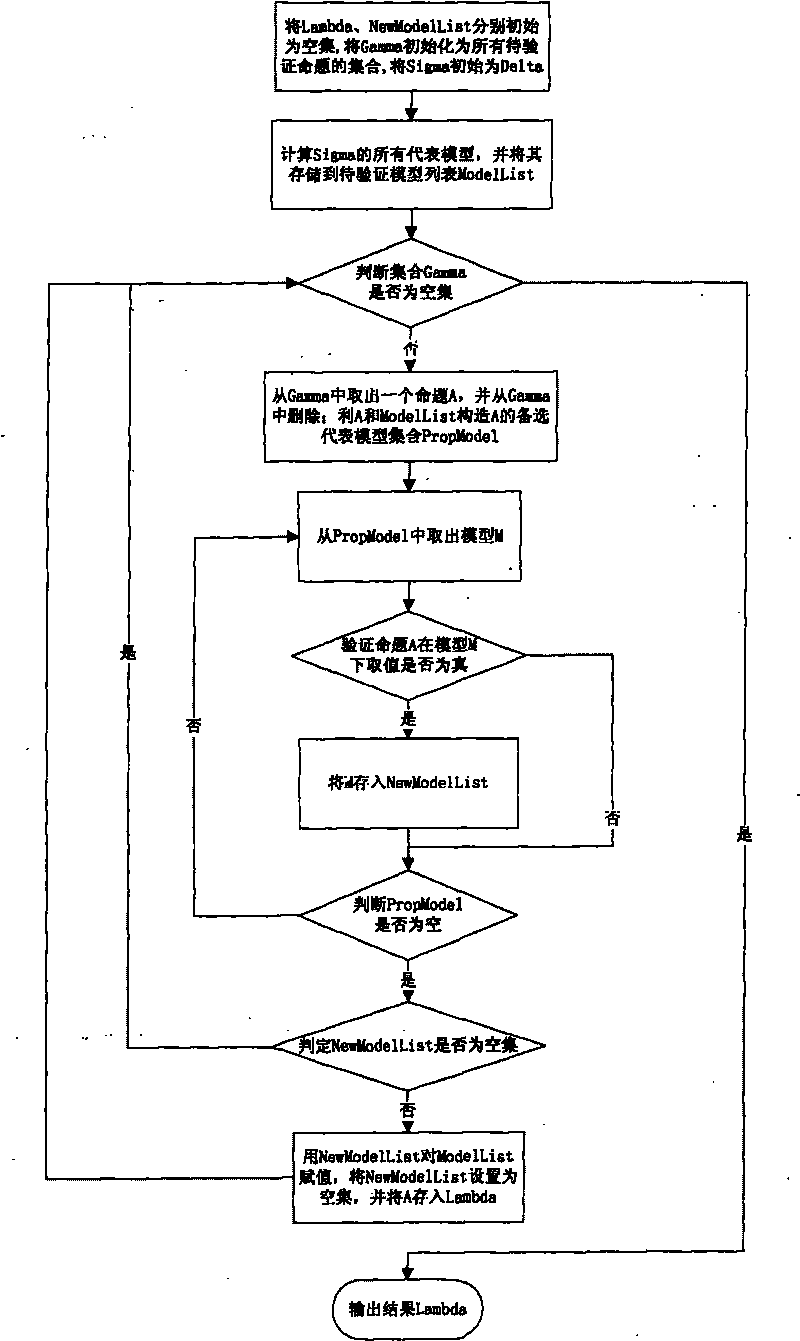
Propositional logic correcting method based on representative model
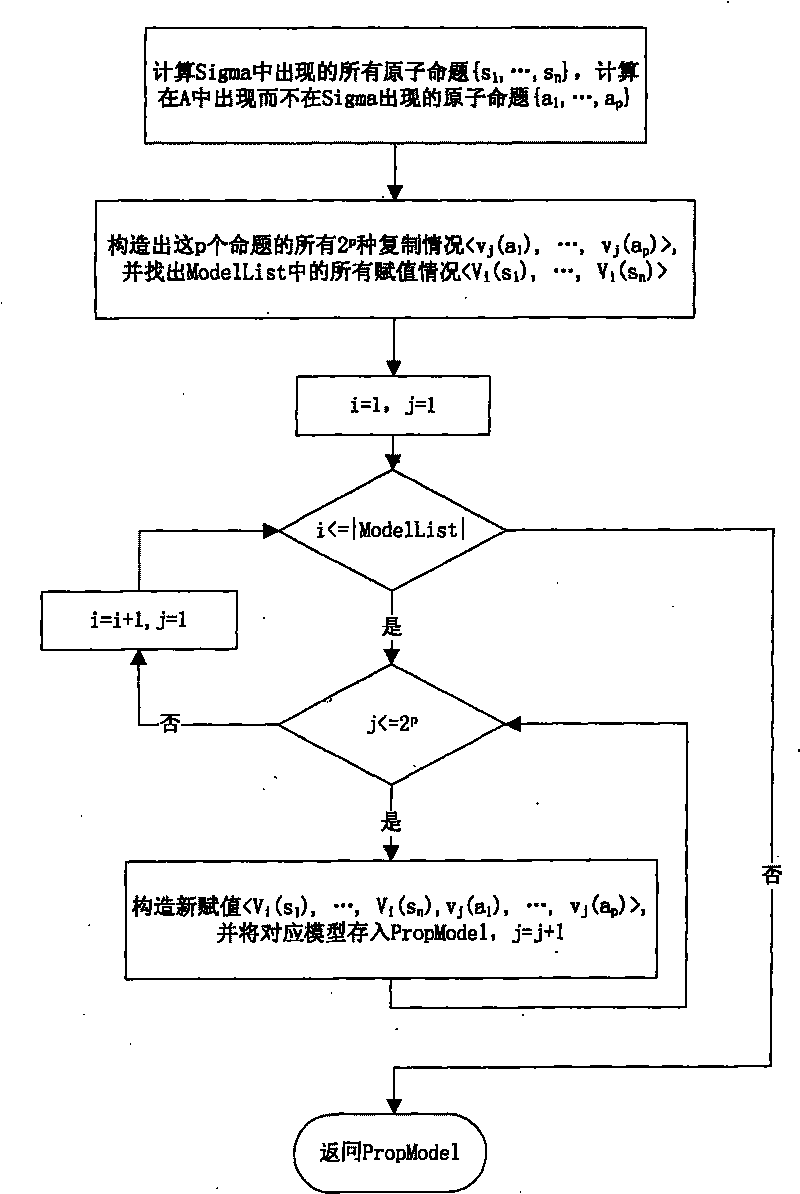
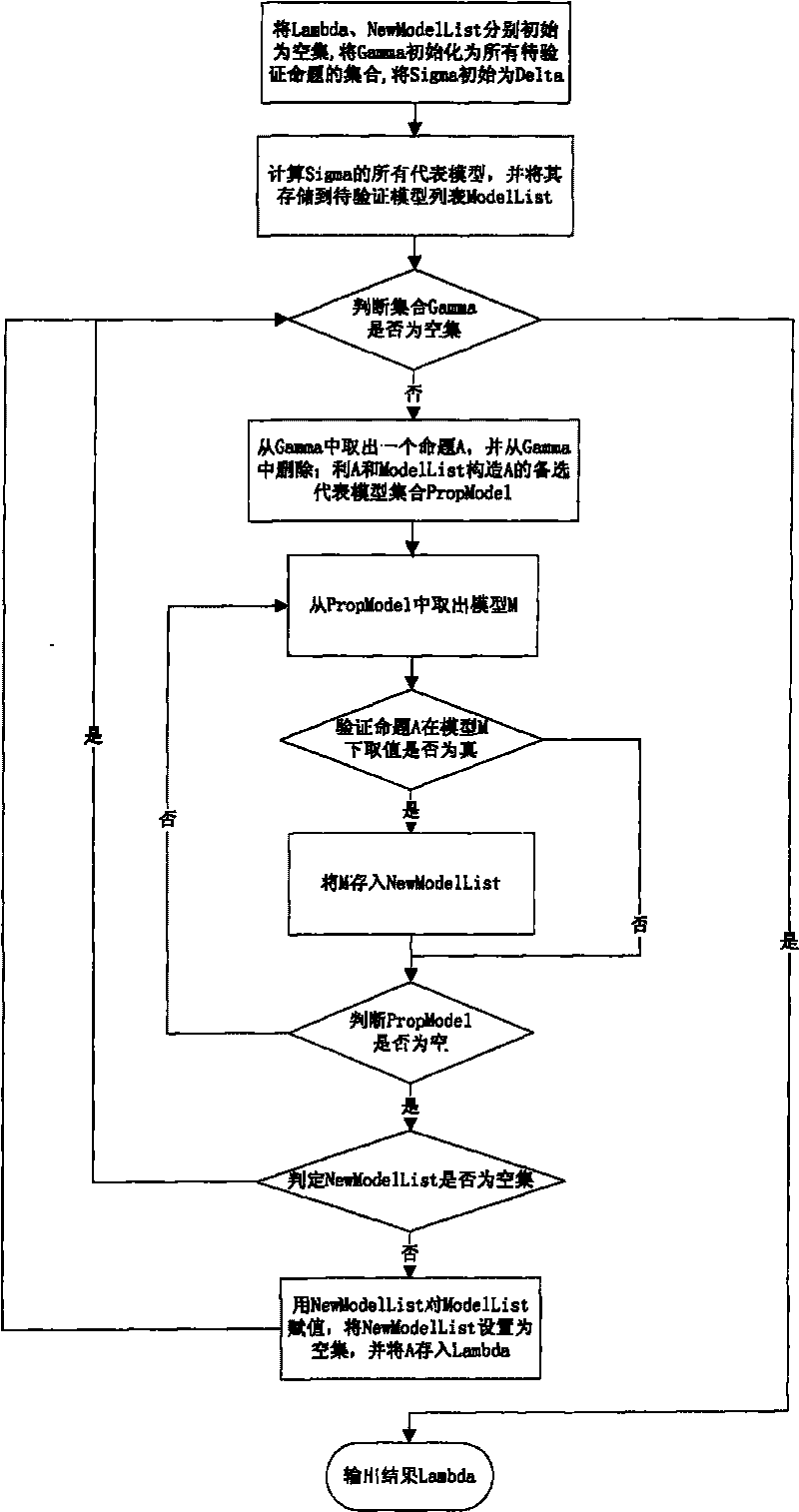
The invention relates to a propositional logic correcting and calculating method based on a representative model, comprising the following steps: (1) initiating a result set Lambda, accepting a set Sigma, a system set Gamma and a new representative model list (New Model List); (2) initiating a representative model list (Model List) by using all representative models of Sigma; (3) if the system set Gamma is an empty set, turning to step (8); (4) taking out and deleting a proposition A from Gamma; (5) constructing an alternative representative model set Prop Model of A by using A, Sigma and Model List; (6) carrying out verification to A by all alternative representative models in Prop Model one by one: if an alternative representative model M leads A to be true, storing M into New Model List; (7) if New Model List is not an empty set, assigning a value to Model List by using New Model List, resetting New Model List to be the empty set, storing A into Lambda and Sigma respectively, and turning to step (3); and if New Model List is an empty set, directly turning to step (3); and (8) outputting the result Lambda. In the method, the representative model is constructed according to every proposition condition in the system set, and a method for only verifying related models is used so as to reduce the checking times of models, thus improving the efficiency of correction and calculation.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com