Identity authentication method, system and device and computer readable storage medium
A technology for identity authentication and pending authentication, applied in the field of user identity authentication in the blockchain, which can solve the problems of low efficiency and cumbersome verification process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] Next, the technical scheme in the present application embodiment will be described in the present application, and it is understood that the described embodiments are intended to be described herein, not all of the embodiments of the present application. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without making creative labor premises, all of the present application protected.
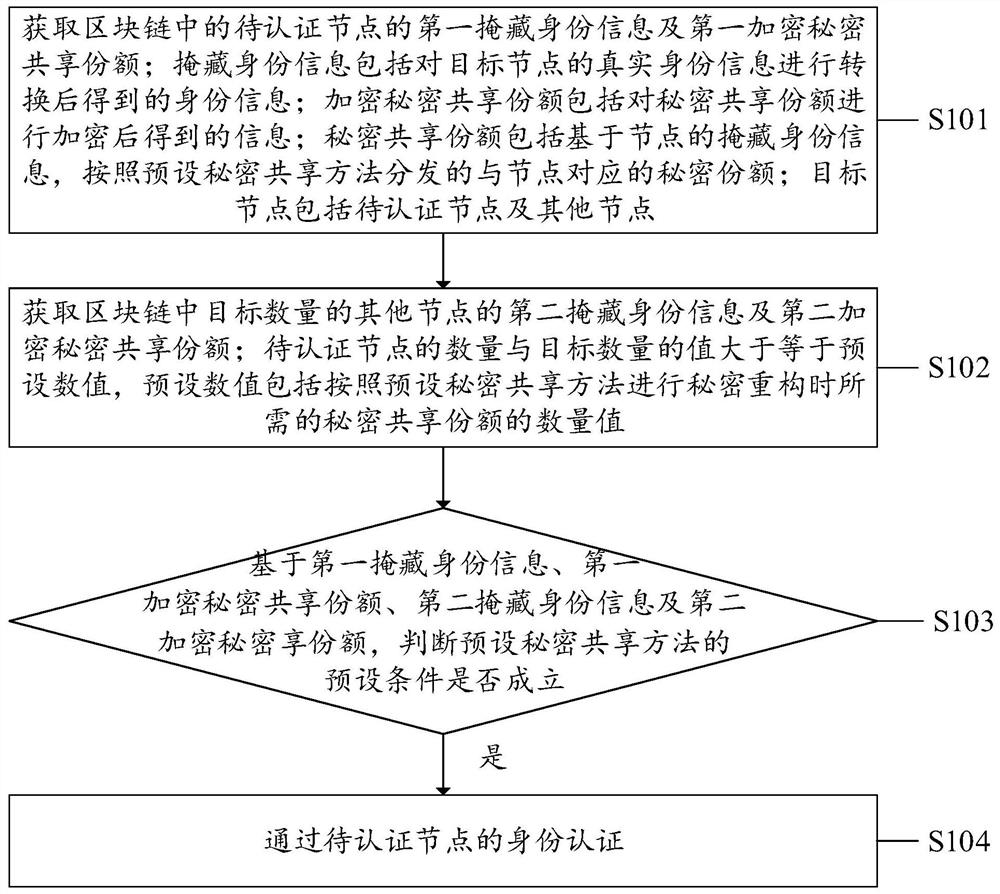
[0057] See figure 1 , figure 1 A first flow diagram of an identity authentication method provided by the embodiment of the present application.
[0058] An identity authentication method provided by the embodiment of the present application, applied to the identity authentication node in the block chain, which may include the following steps:
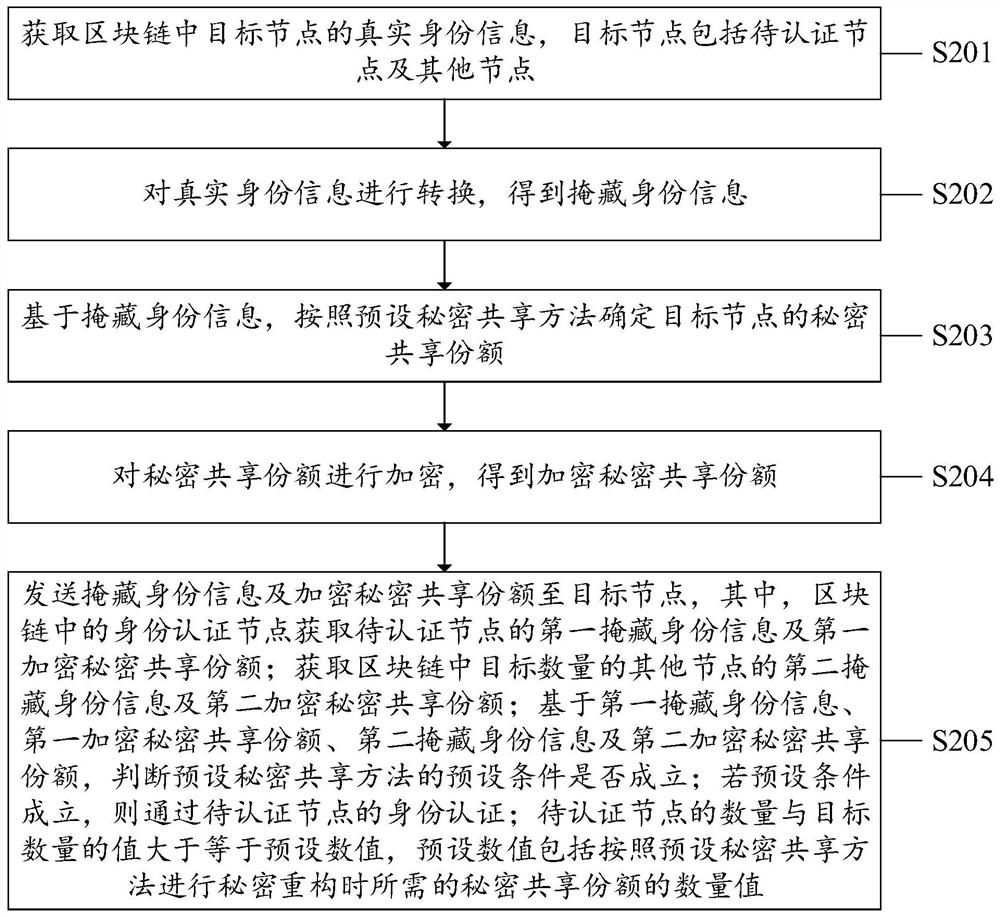
[0059] Step S101: Get the first hidden identity information of the zipper chain to be authenticated to the node and the first encrypted secret shared share; hidden identity infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com