An optimization method of block chain tamper-proof technology
An optimization method and technology of blockchain, applied in the field of blockchain, can solve problems such as application impact, destruction of original data of the ledger, and acquisition of historical transaction data by smart contracts, achieving the effect of high verification efficiency and few verification times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical scheme of the present invention will be further described in detail below in conjunction with the accompanying drawings:
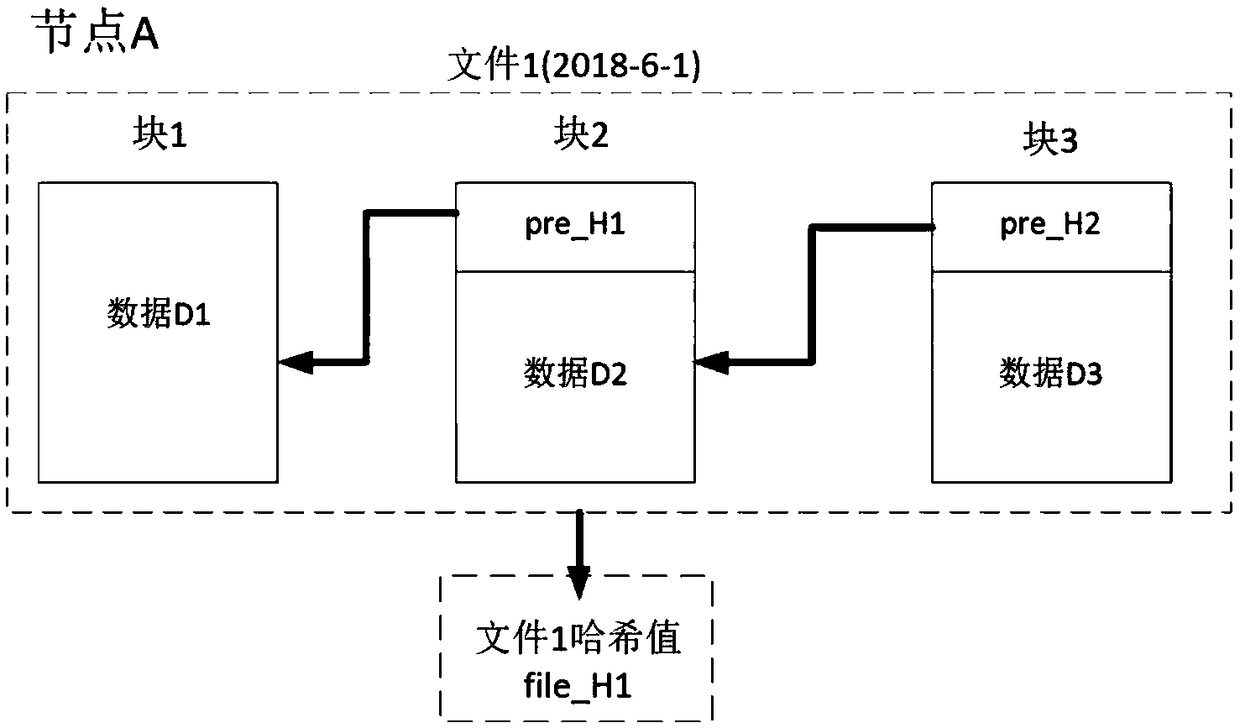
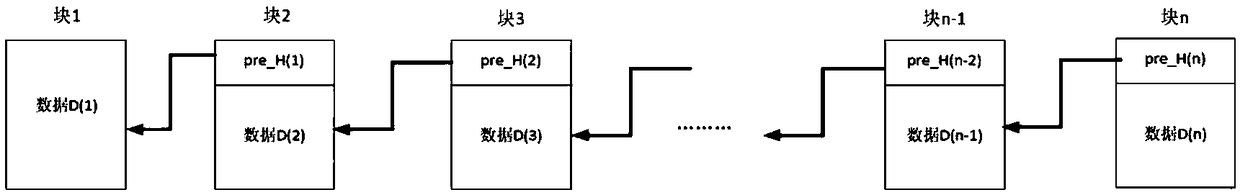
[0036] Suppose node A maintains a image 3 In the block chain shown, each block is interconnected by the hash value of the previous block according to the timestamp T. There are currently n blocks, and the content of each block includes: block data D and the previous block The hash pointer pre_H of the block.
[0037] The hash pointer on the blockchain can be simplified to:
[0038] pre_H(1)=hash(D(1))
[0039] pre_H(2)=hash(pre_H(1)||D(1))
[0040] ...
[0041] pre_H(n-2)=hash(pre_H(n-3)||D(n-2))
[0042] pre_H(n-1)=hash(pre_H(n-2)||D(n-1))
[0043] pre_H(n)=hash(pre_H(n-1)||D(n))
[0044] The anti-tamper detection mechanism is as follows:
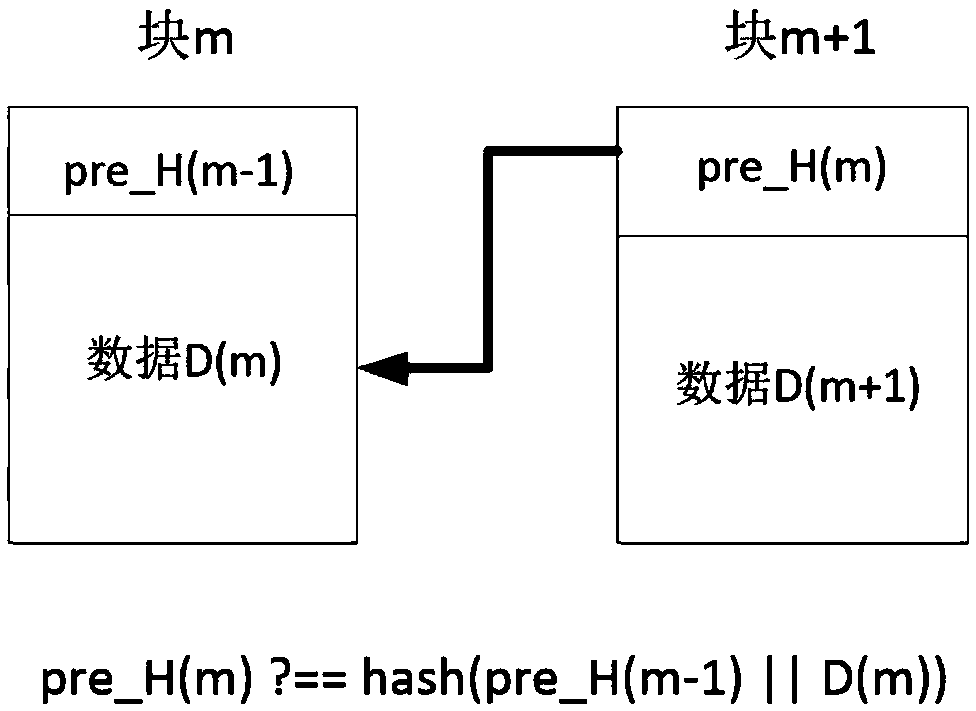
[0045] 1. Start the first test, which mainly performs inter-block pre_H comparison test on the entire blockchain, such as figure 1 As shown, if pre_H(m)=hash(pre_H(m-1)||D(m)), the test passes; otherwise, the t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com