Method, device, equipment and system for executing third-party authentication
A technology of an authentication device and an execution device, which is applied in the computer field, can solve the problems of user-side performance degradation, multiple authentication protocols, and integrated authentication protocols, etc., and achieve the effects of improving user experience, reducing conversion process, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in further detail below in conjunction with the accompanying drawings.
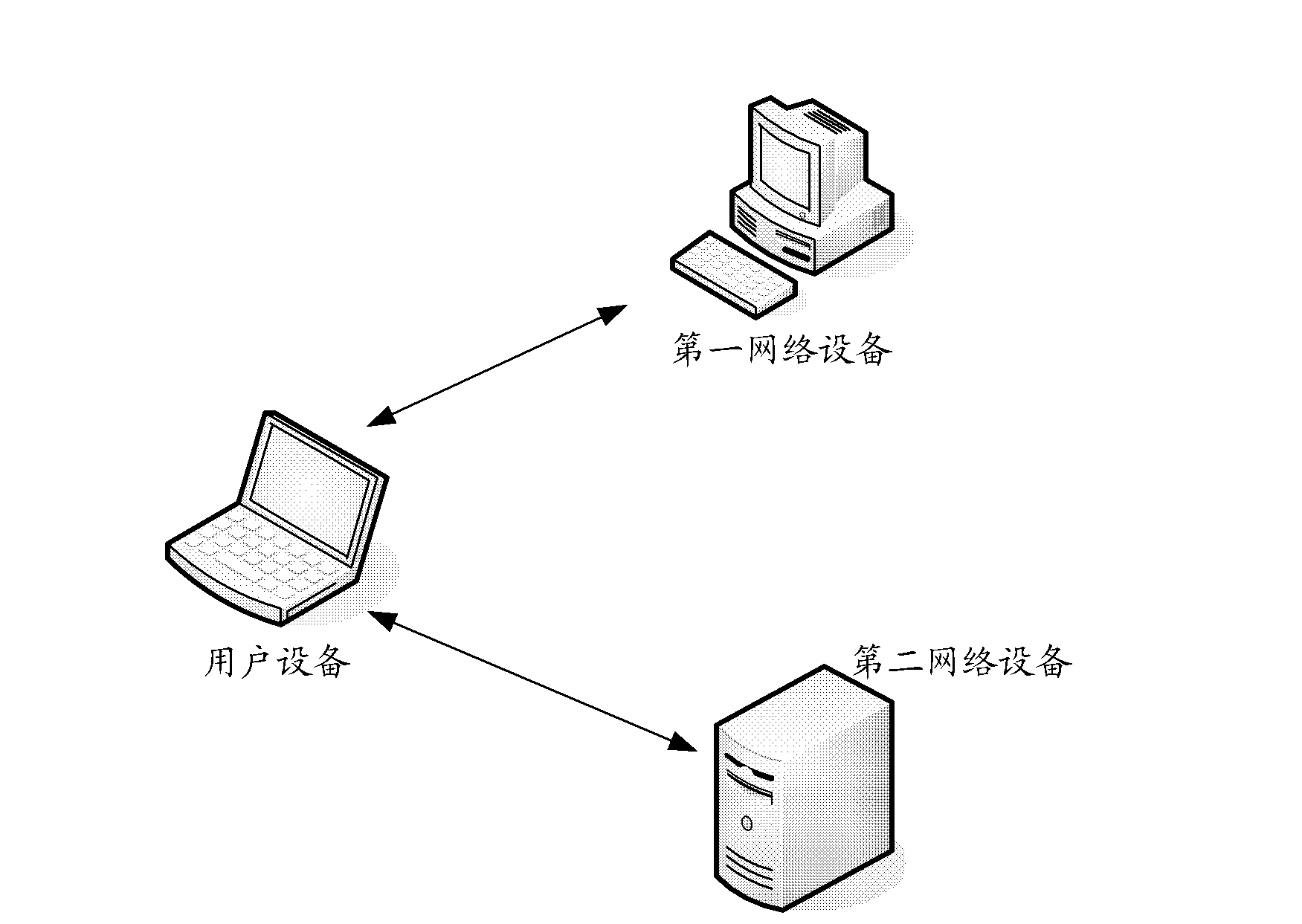
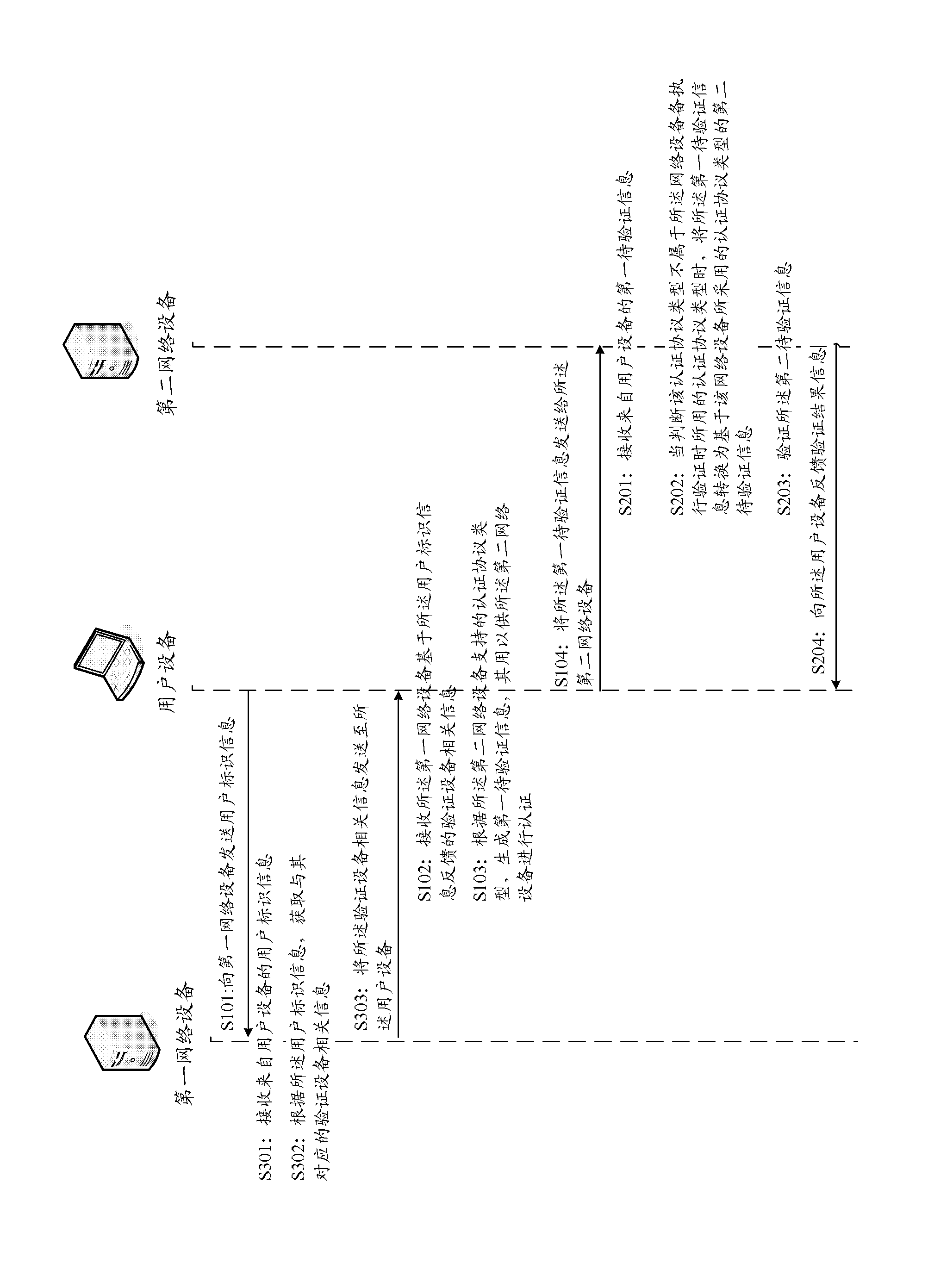
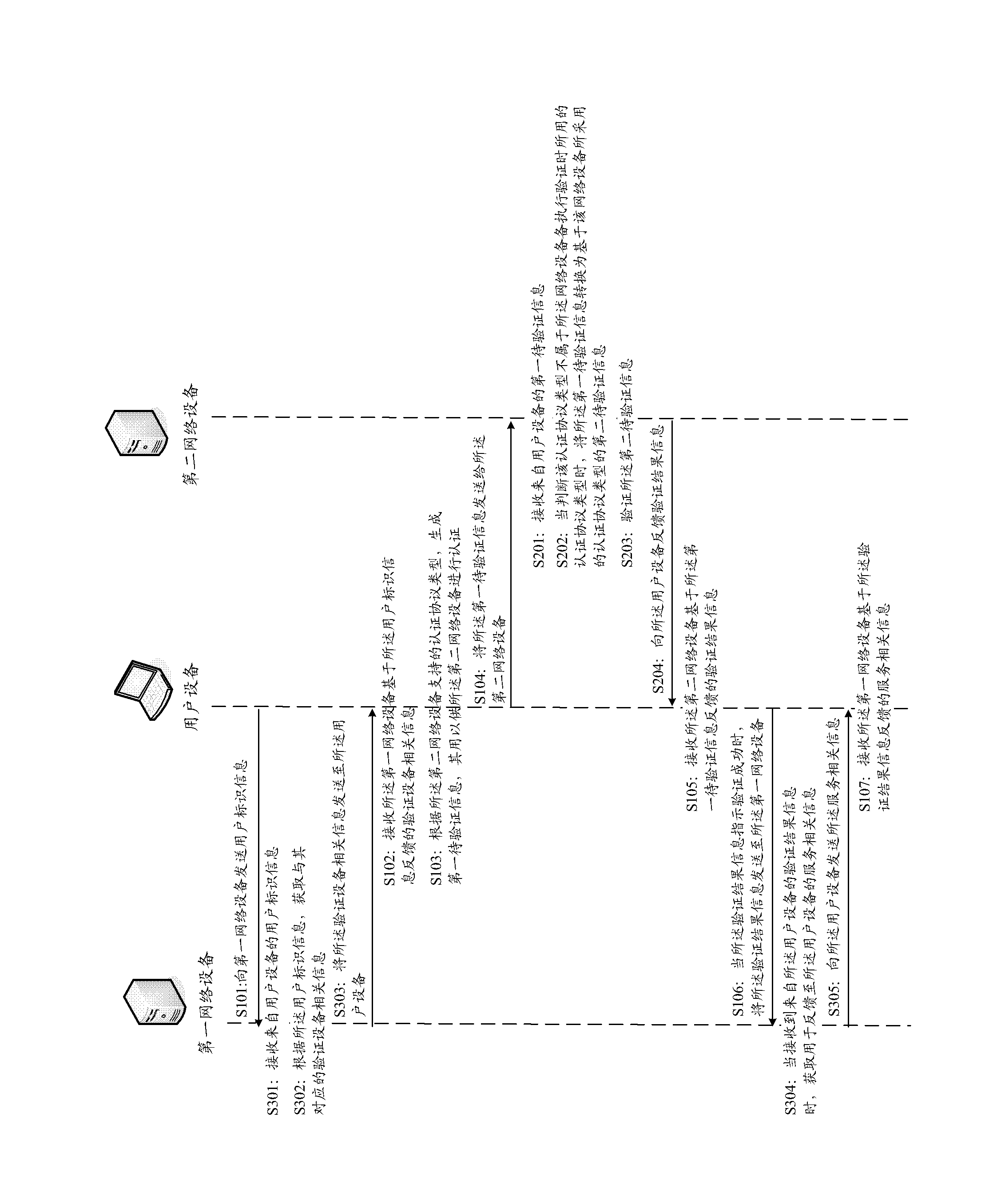
[0045] figure 1 A system topology diagram of an authentication system for third-party authentication according to one aspect of the present invention is illustrated. The authentication system includes a user device for requesting third-party authentication, a first network device for assisting in performing third-party authentication, and a second network device for performing the authentication process.
[0046] Wherein, the user equipment, the first network equipment, and the second network equipment are all electronic equipment capable of automatically performing numerical calculation and / or various information processing according to pre-stored programs, and its hardware includes but not limited to Microprocessors, FPGAs, DSPs, embedded devices, etc. Wherein, the user equipment includes but is not limited to a computer, a smart phone, a PDA, and the lik...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com