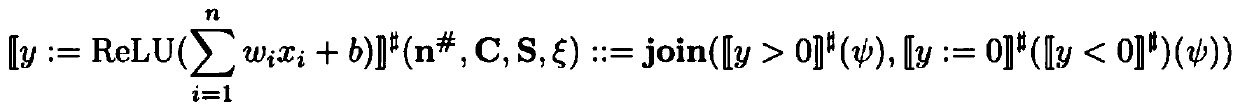Patents
Literature
68results about How to "Fast verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for verifying computer software test results
ActiveCN102122265AImprove test efficiencyImprove test qualitySoftware testing/debuggingTest executionComputer software
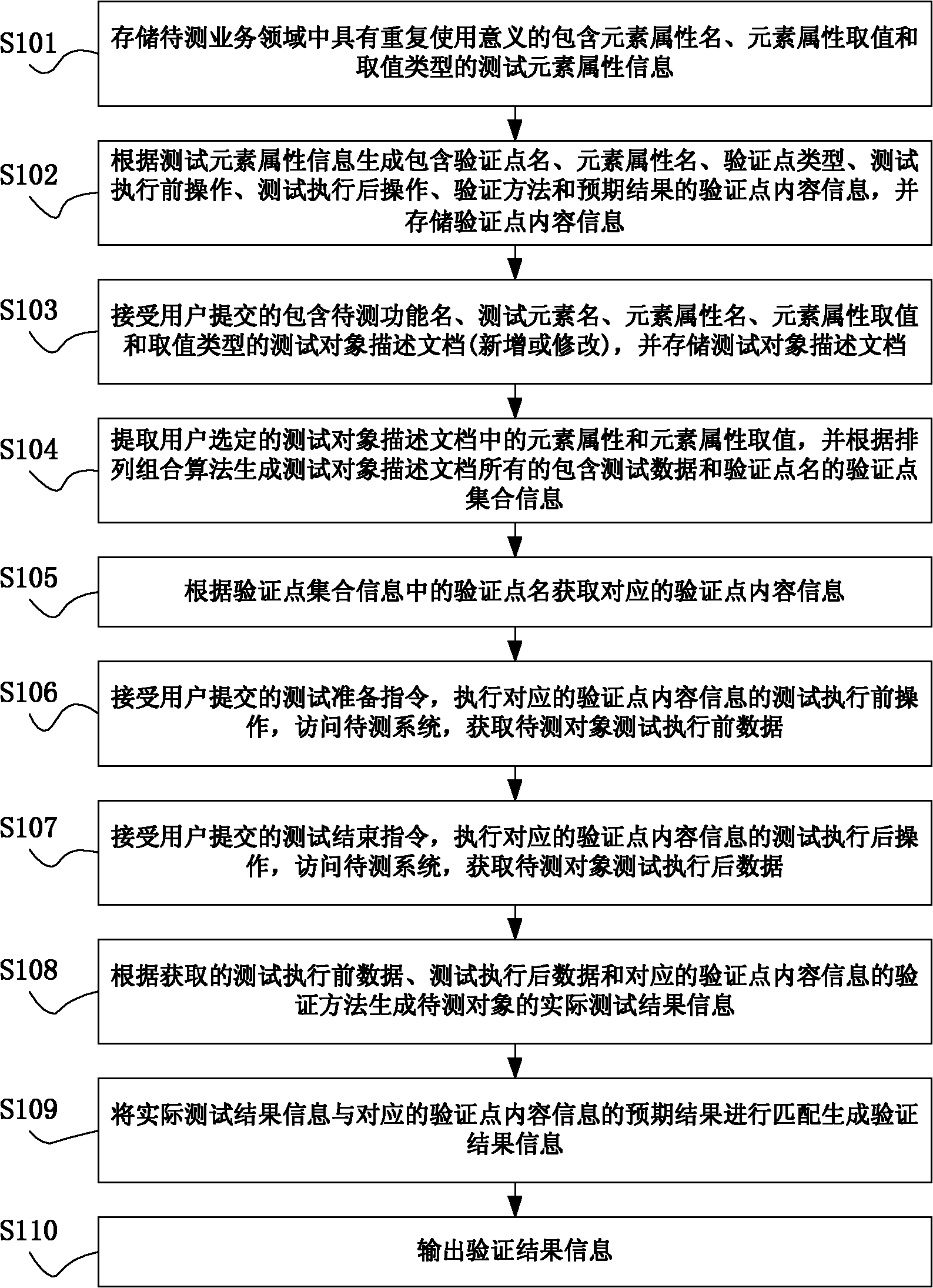
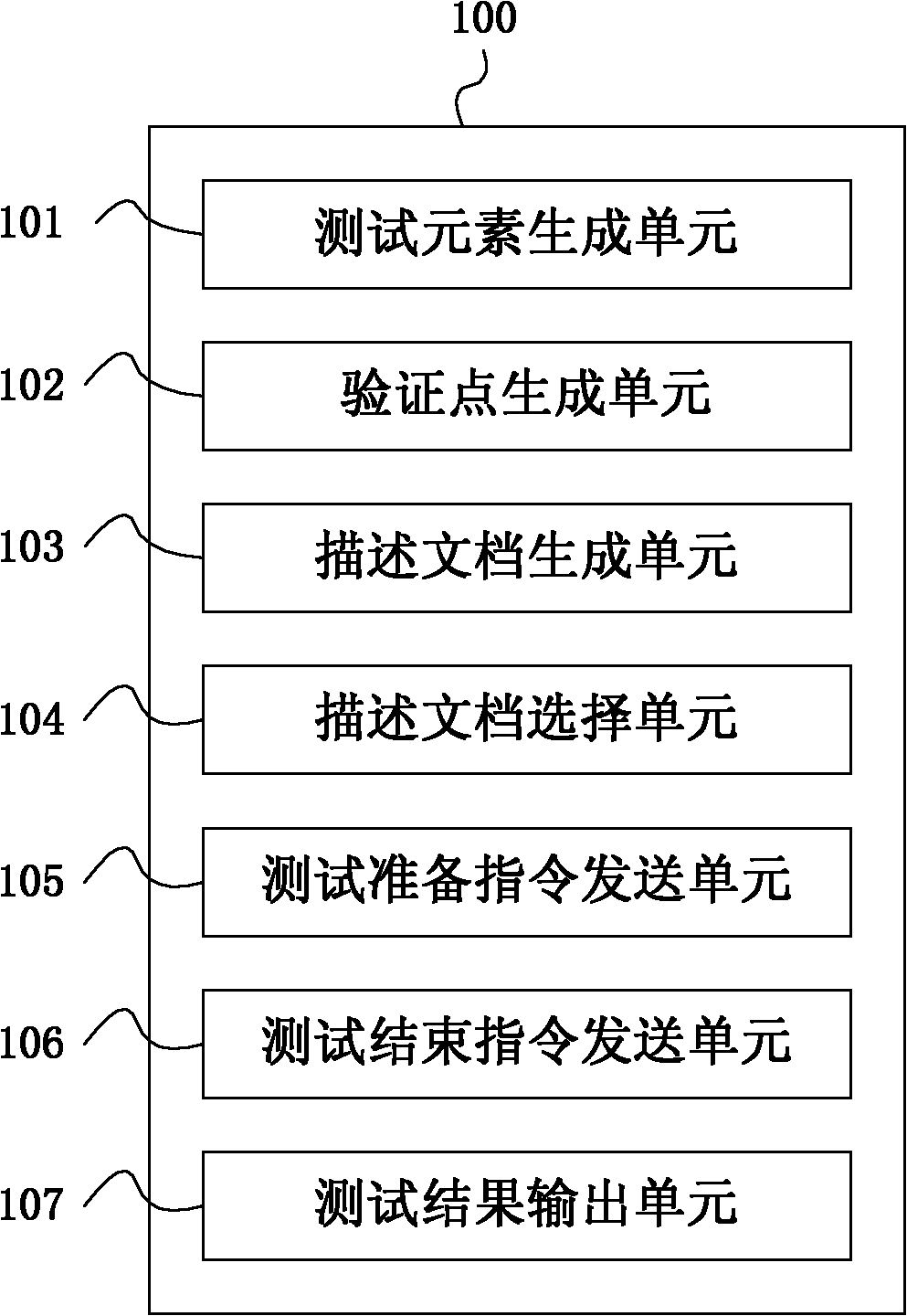
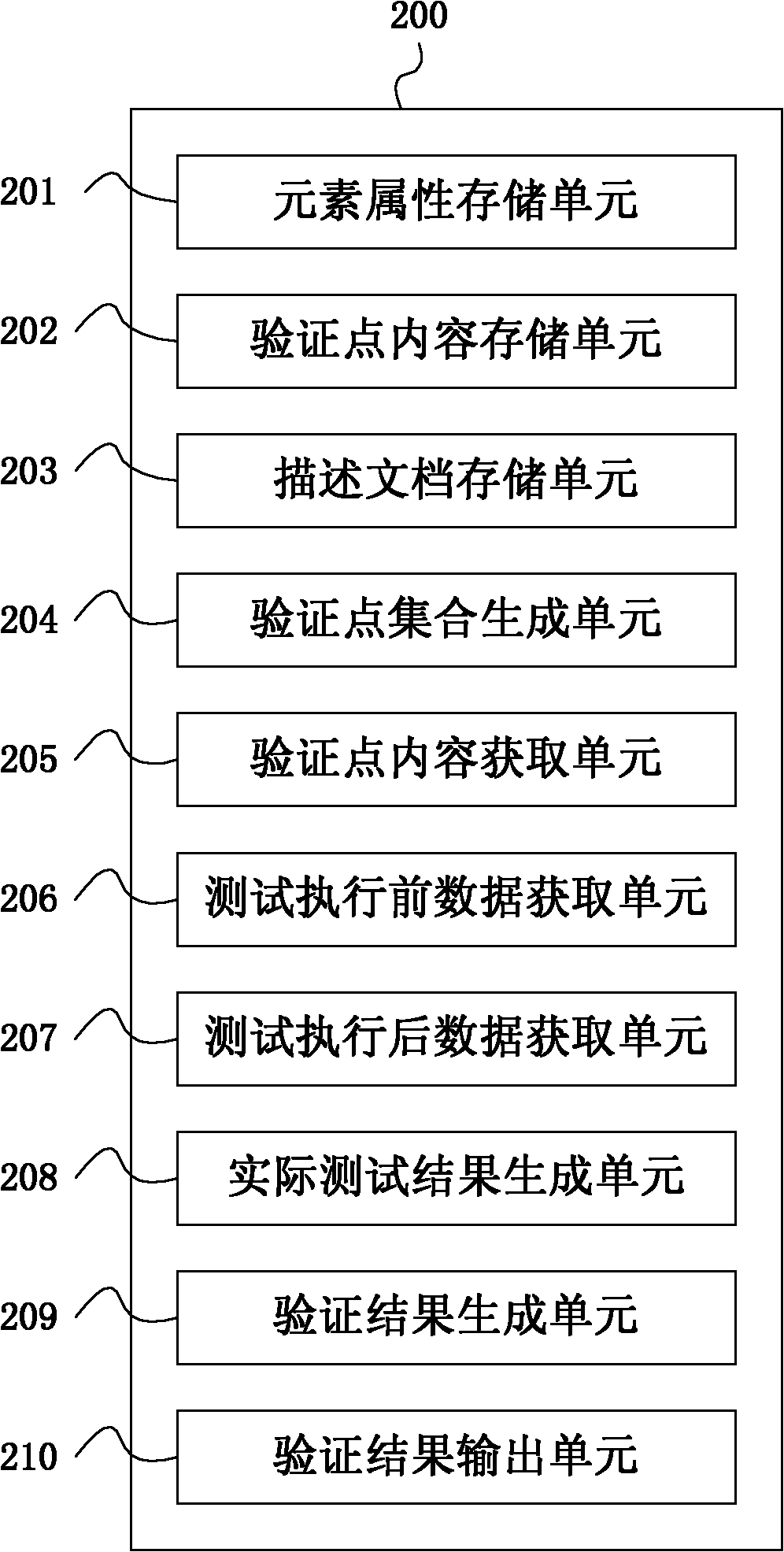
The invention provides a system and method for verifying computer software test results. The computer software test result verifying method comprises the steps of: storing test element attribute information; generating and storing verification point information; generating and storing a tested object description file; extracting the element attribute and the element attribute value in the tested object description file, and generating verification point set information; obtaining the content information of corresponding verification points; accessing a system to be tested, and obtaining the data before the test of the object to be tested is carried out and the data after the test of the object; generating actual test result information of the object to be tested according to the data before the test, data after the test and a method for verifying the content information of corresponding verification points; matching the actual test result information with an expected result and generating verification result information; and outputting the verification result information. The system and method for testing computer software test results aim at solving the problem that a computer software test result verification point can be used repeatedly in a plurality of test cases, and realize a fully covered combination of computer software test result verification points.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
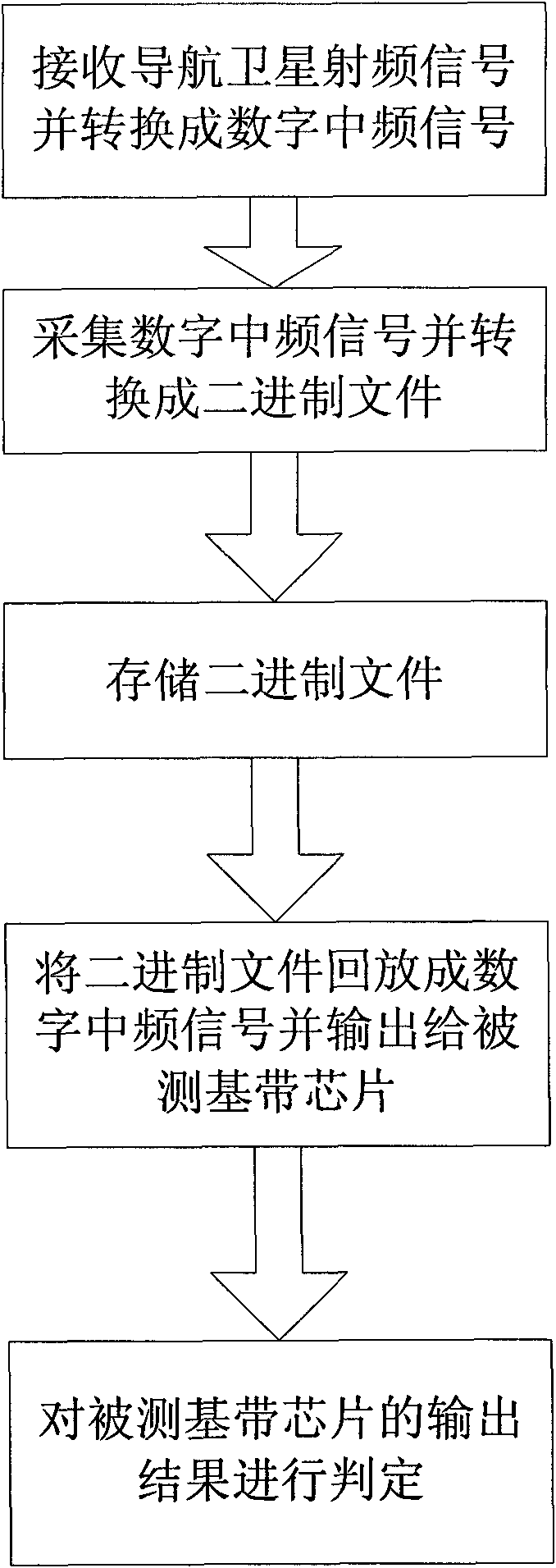
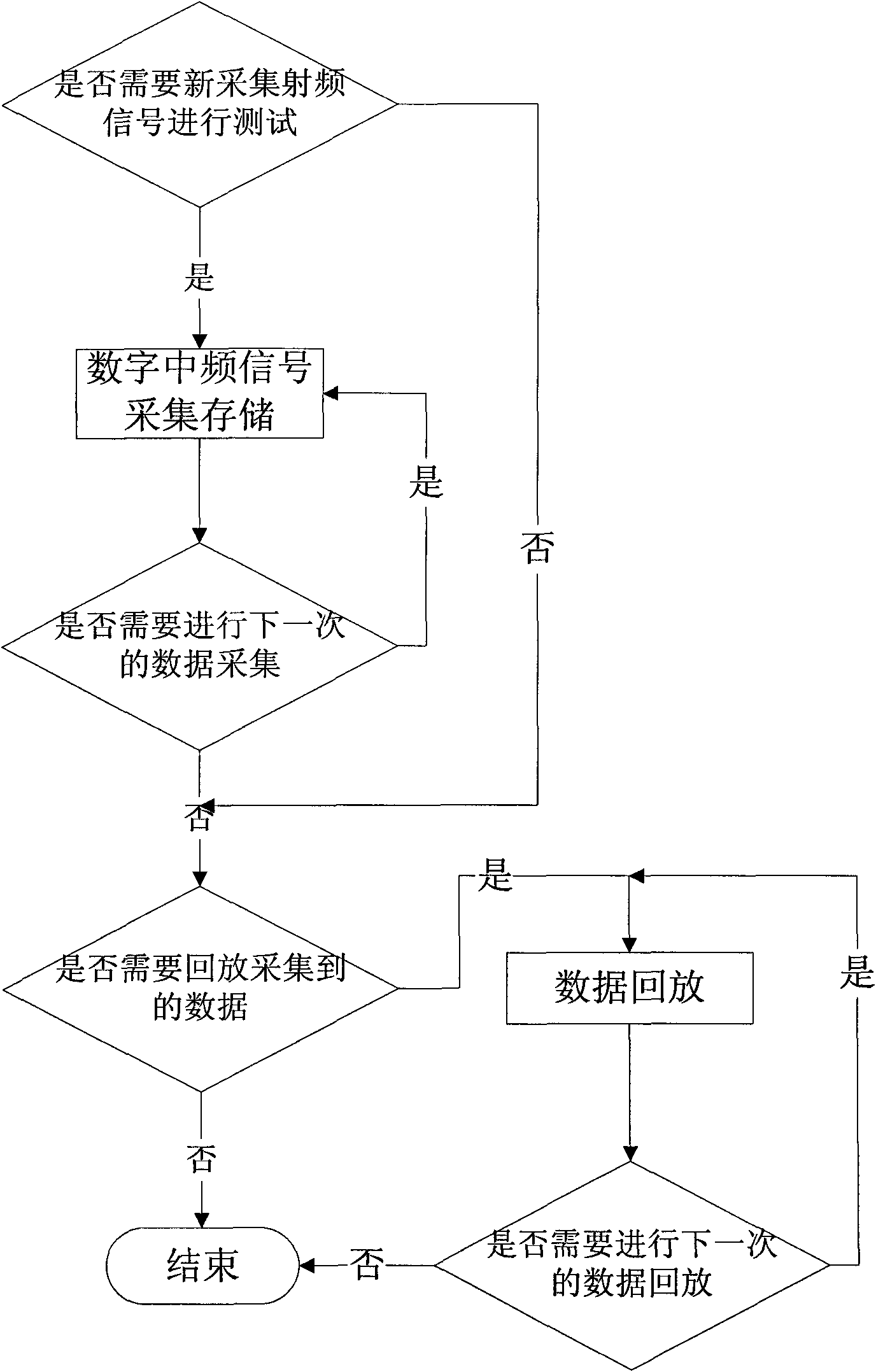
Method for testing base band chip of satellite navigation receiver
ActiveCN101813783AAdd collection stepsAdd data storage stepSatellite radio beaconingSatellite radioImage resolution
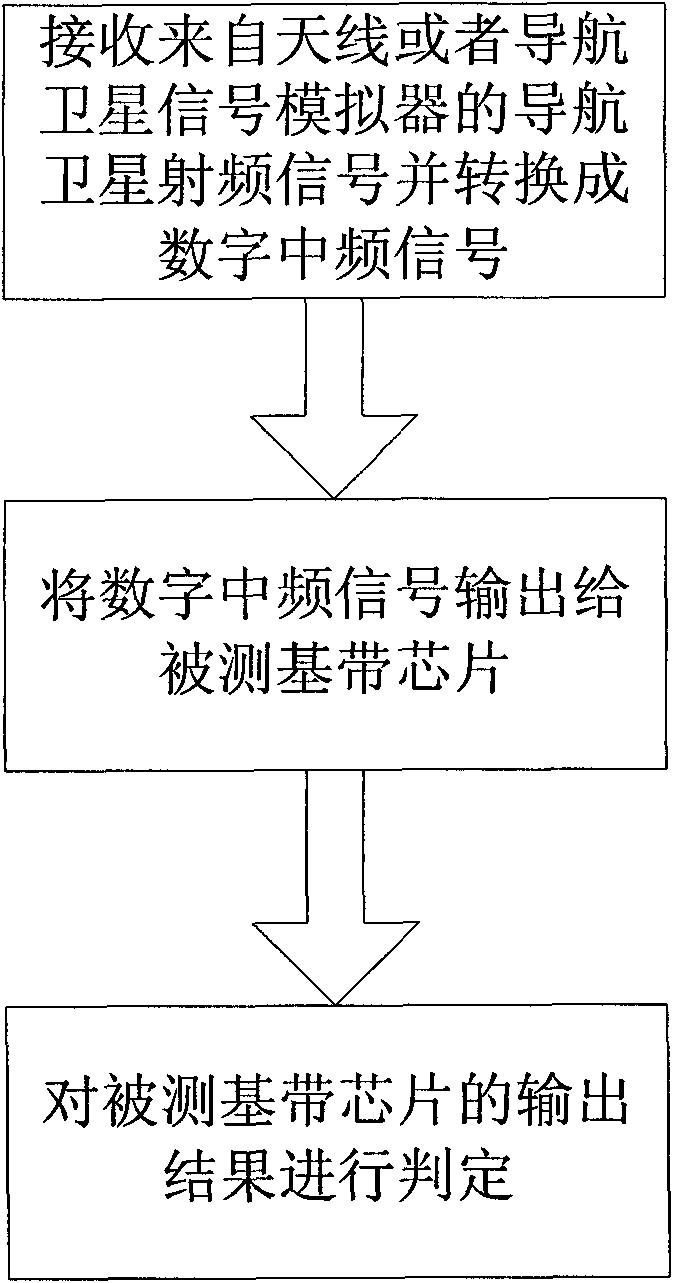
The invention relates to a method for testing a base band chip of a satellite navigation receiver. The method comprises the following steps in turn: receiving a navigation satellite radio-frequency signal and converting the radio-frequency signal into a digital intermediate-frequency signal; acquiring the obtained digital intermediate-frequency signal and converting the digital intermediate-frequency signal into a binary file; storing the obtained binary file; playing back the stored binary file to form the digital intermediate-frequency signal and transmitting the digital intermediate-frequency signal to the tested base band chip; and performing result accuracy judgment on the output of the tested base band chip. The method reduces the expense required for constructing a plurality of test platforms, and facilitates the judgment of the accuracy of the output of the to-be-tested base band chip on finer resolution.
Owner:TECHTOTOP MICROELECTRONICS
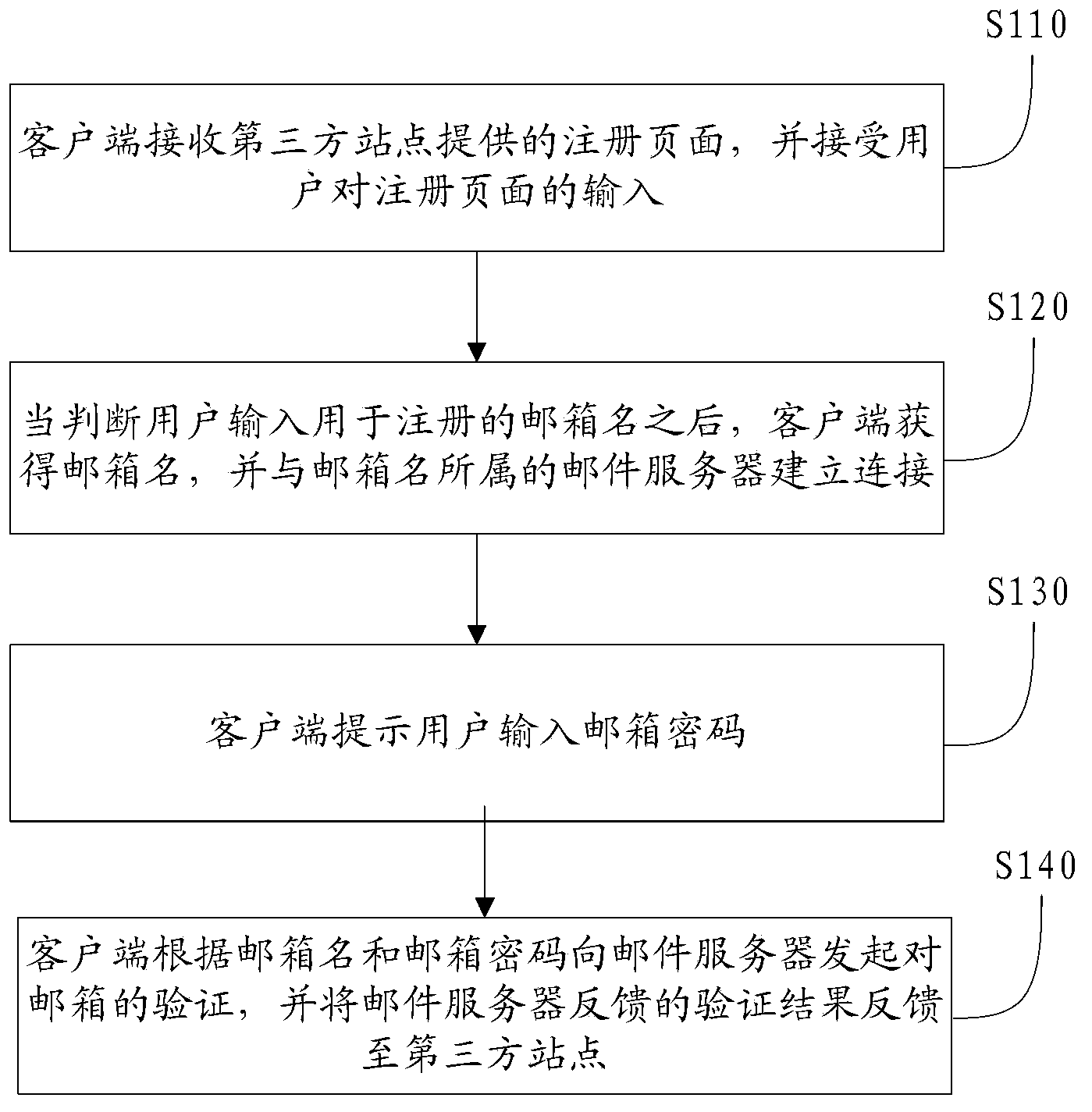
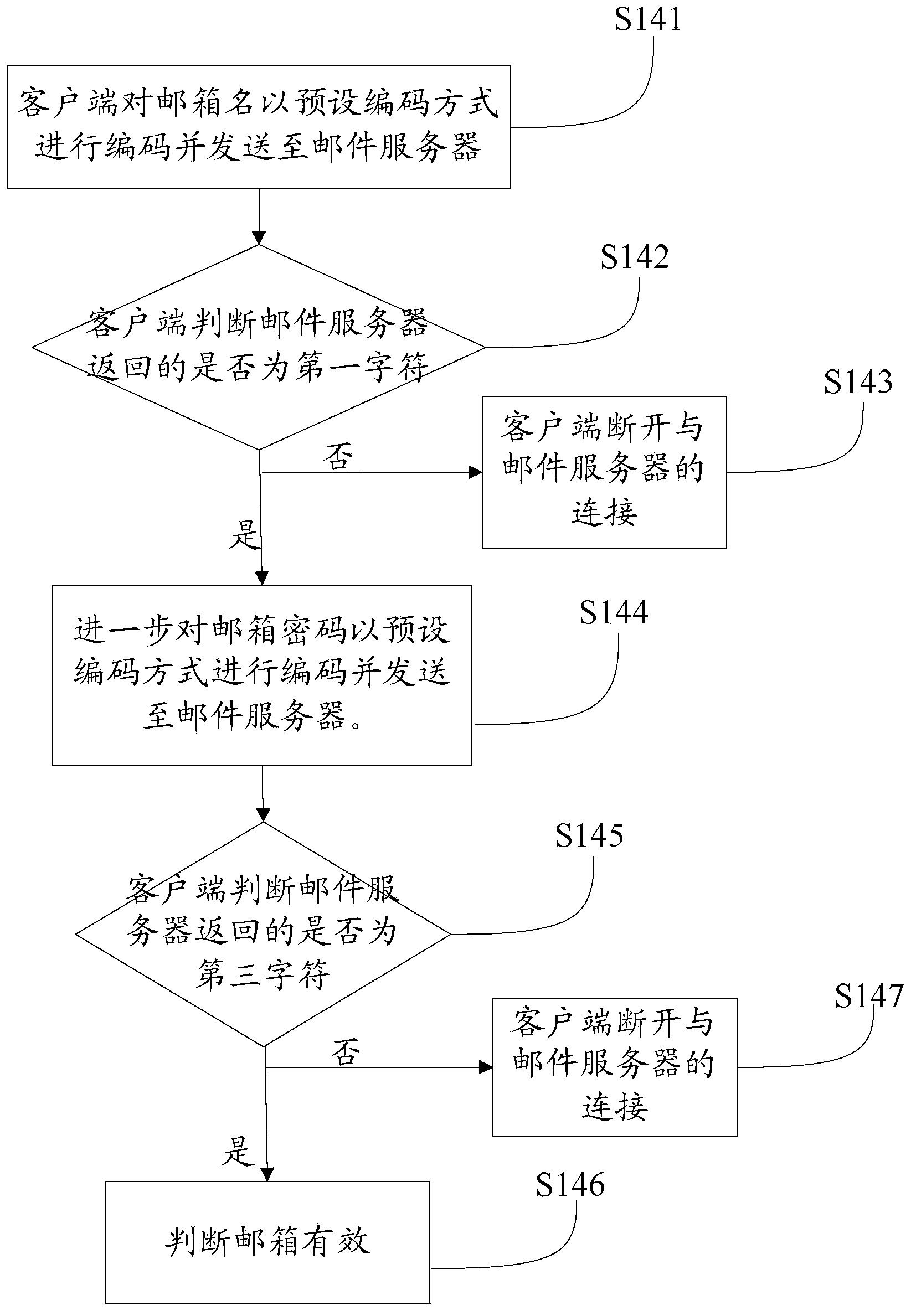
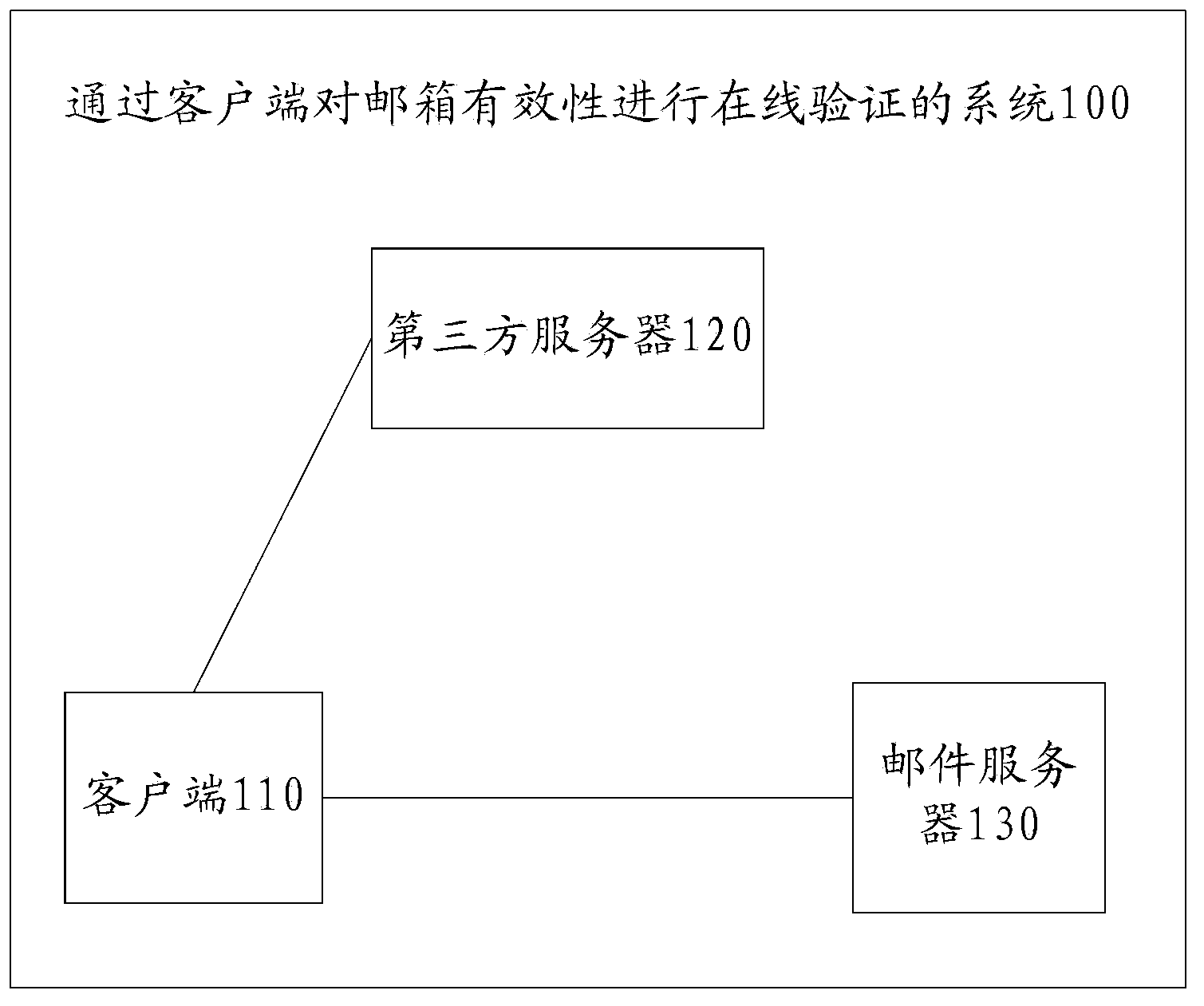
Method, system and client side for testing mailbox validity on line
InactiveCN103581151ASteps to reduce engagementImprove experienceKey distribution for secure communicationData switching networksThird partyPassword
The invention provides a method for testing mailbox validity on line through a client side. The method comprises the steps that the client side receives a registering page provided by a third-party station, input of a user to the registering page is received; after a mailbox name for registering of the user is judged, the client side receives the mailbox name, connecting with a mail server which the mailbox name belongs to is established; the client side reminds the user to input a mailbox password; the client side starts testing on a mailbox to the mail server according to the mailbox name and the mailbox password, and testing results fed back by the mail server are fed back to the third-party station. According to the method, the registering procedure is simplified, user operation is easy, response time is short, and testing efficiency is high. The invention further discloses a system for testing mailbox validity on line through the client side and the client side.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
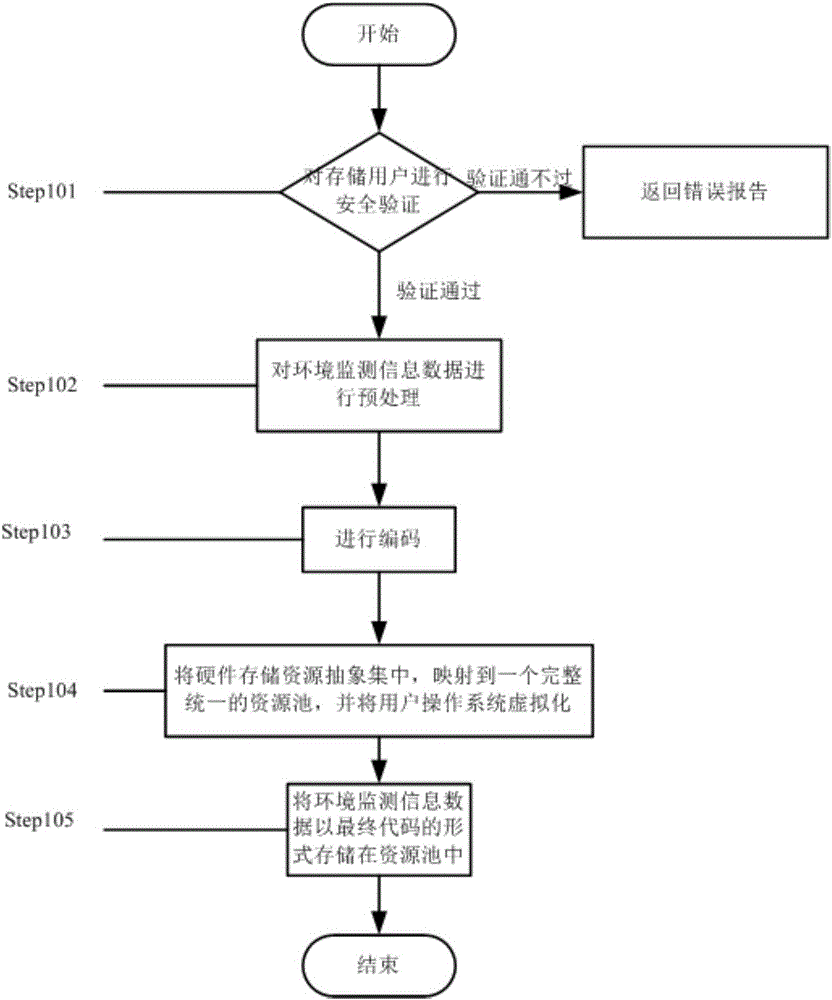
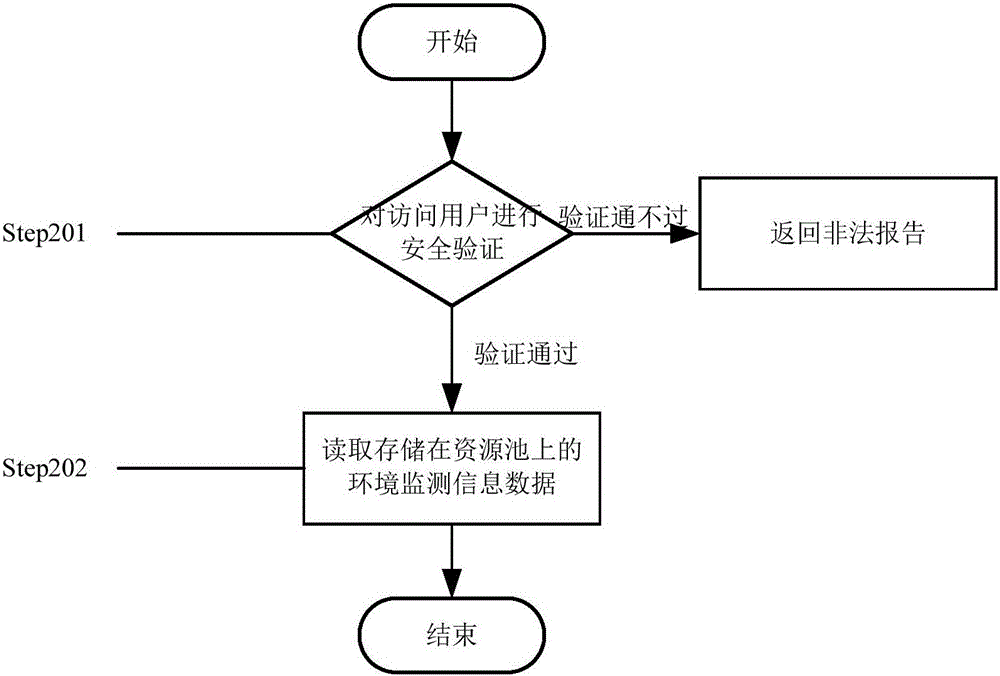
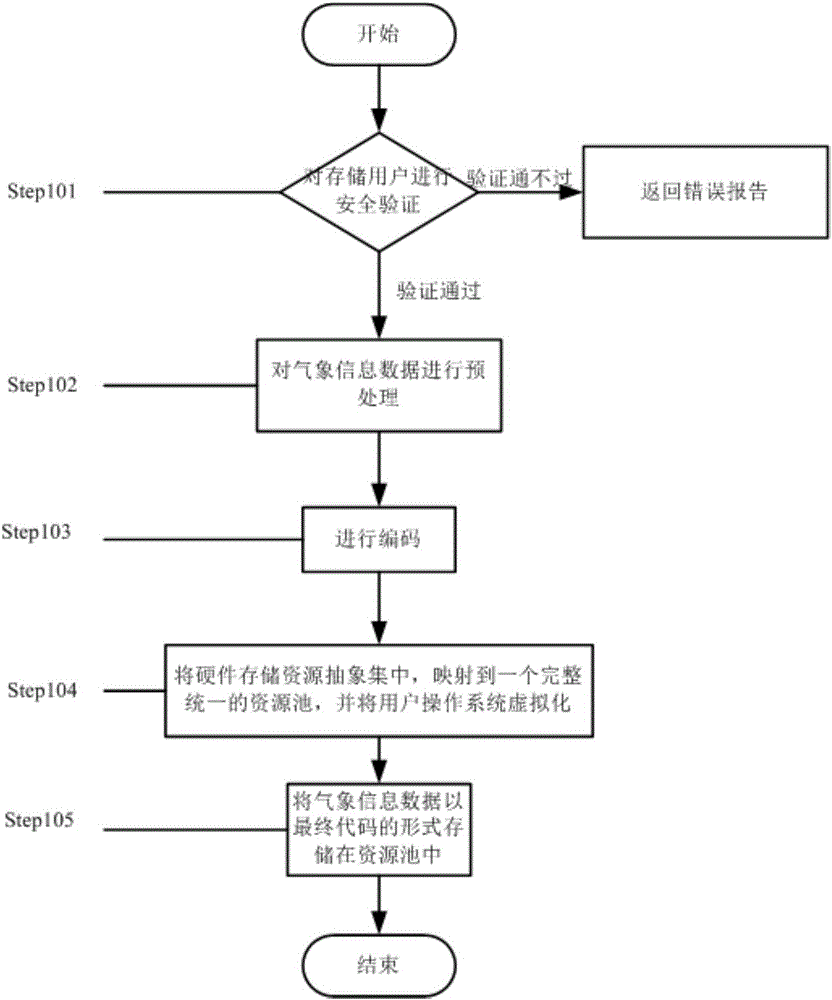
Method for sharing environment monitoring information data
InactiveCN106096061AEasy and barrier-free sharingImprove calling speedDigital data protectionDigital data authenticationVirtualizationResource pool
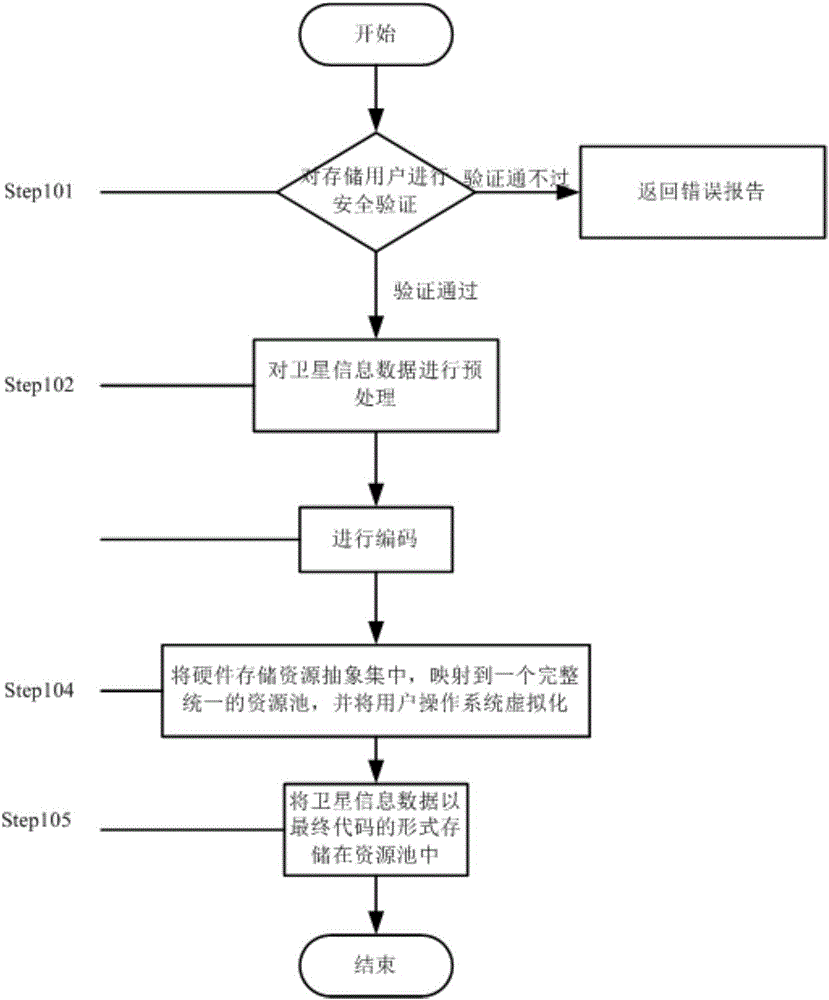
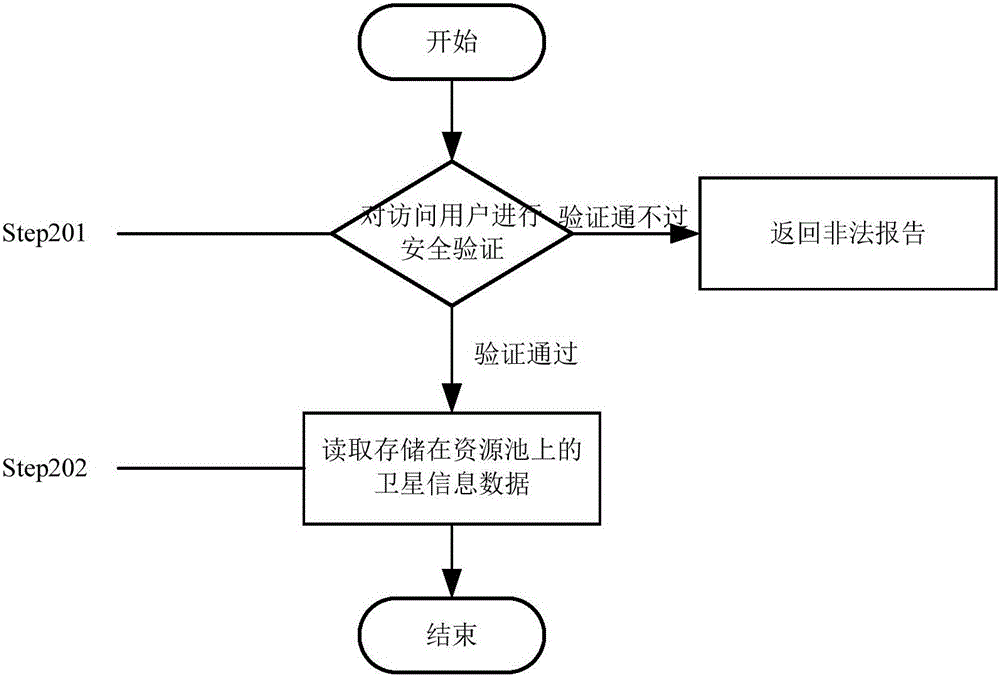
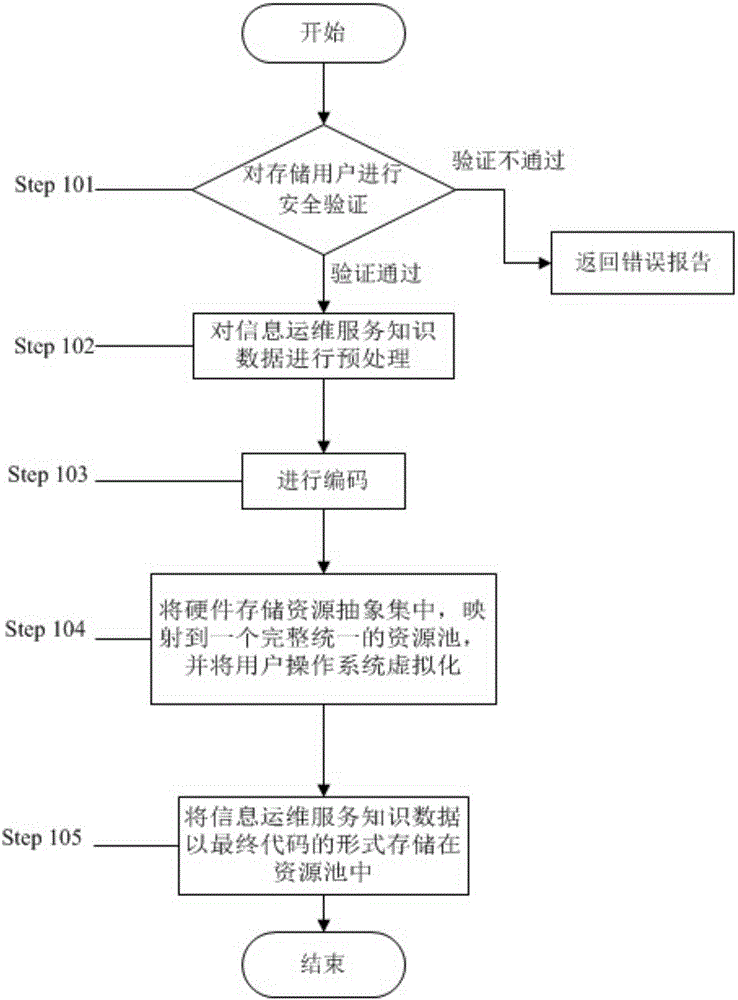
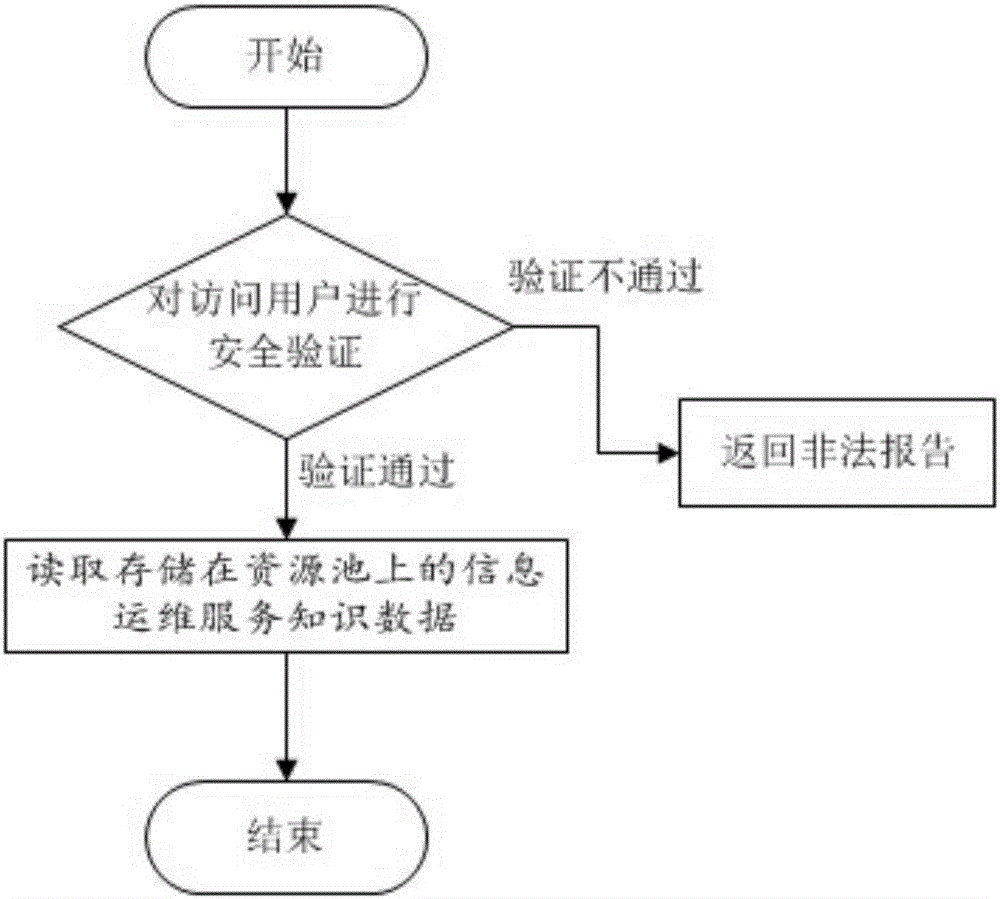
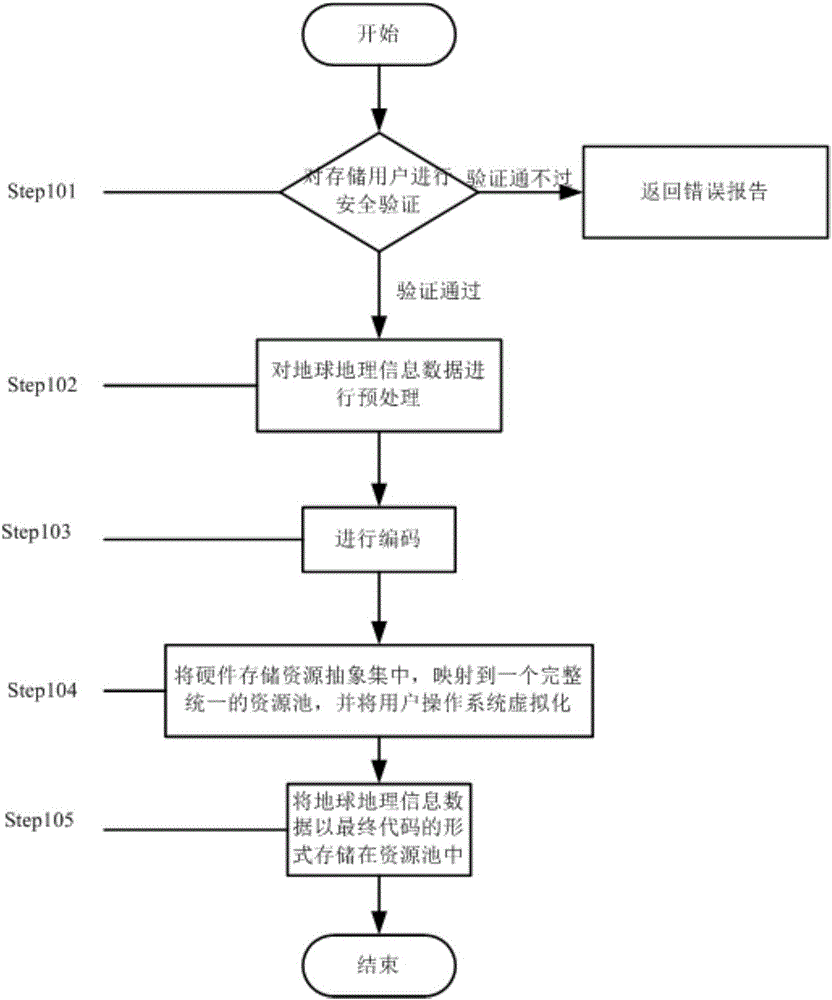
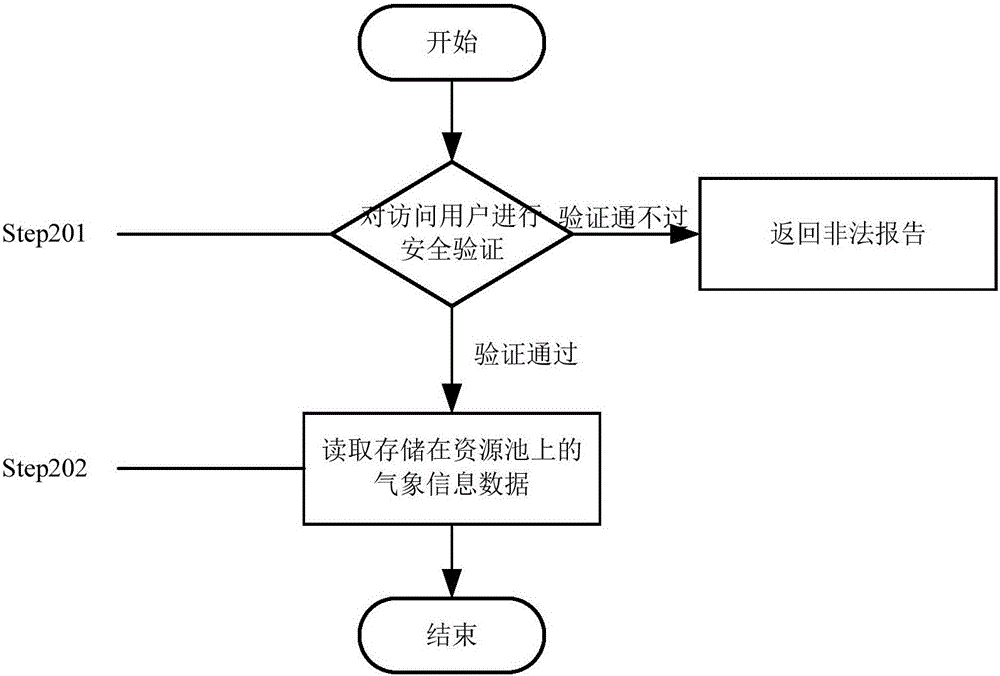
The invention provides a method for sharing environment monitoring information data. The method comprises secure storage of the environment monitoring information data and secure access of the environment monitoring information data. The secure storage of the environment monitoring information data comprises the following steps: (1) carrying out security verification on identity of a storage user; (2) preprocessing the environment monitoring information data; (3) encoding; (4) abstractly centralizing hardware storage resources, mapping to a complete and unified resource pool and carrying out virtualization on a user operation system; and (5) storing the environment monitoring information data in the resource pool in a final code form. The secure access of the environment monitoring information data comprises the following steps: (1) carrying out security verification on identity of the storage user; and (2) reading the environment monitoring information data stored in the resource pool. Through the method, the accessible sharing can be achieved; the memory occupation is reduced; the data calling speed is improved; the security of the environment monitoring information data is improved under the precondition that the convenience is ensured.
Owner:吴本刚
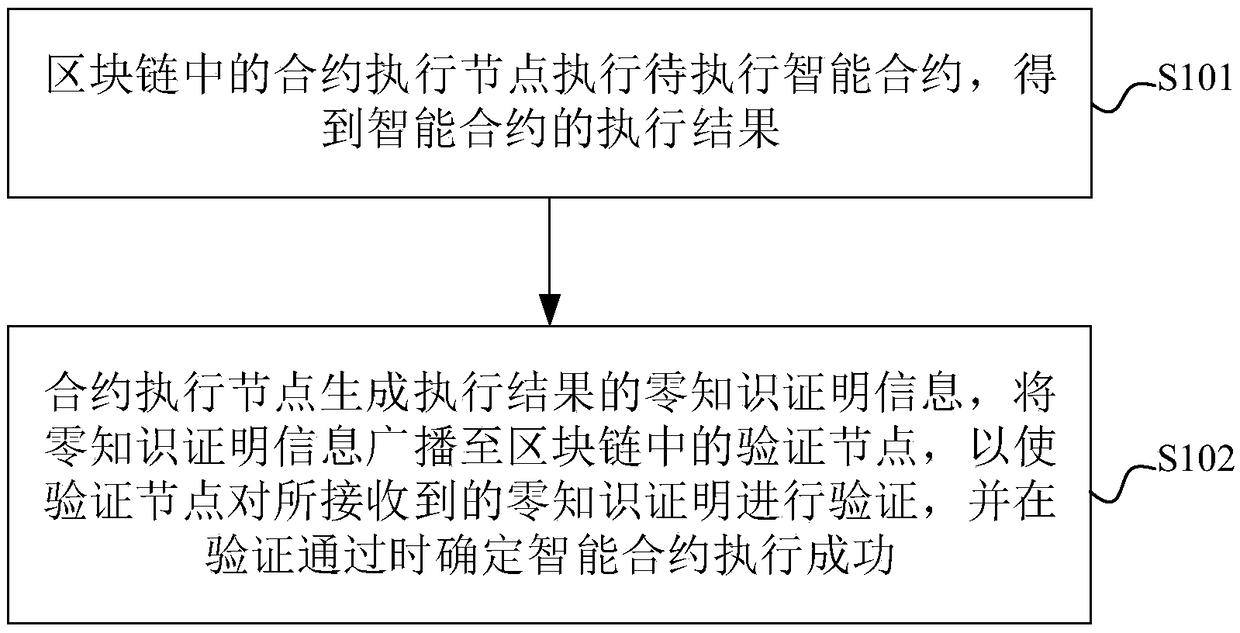
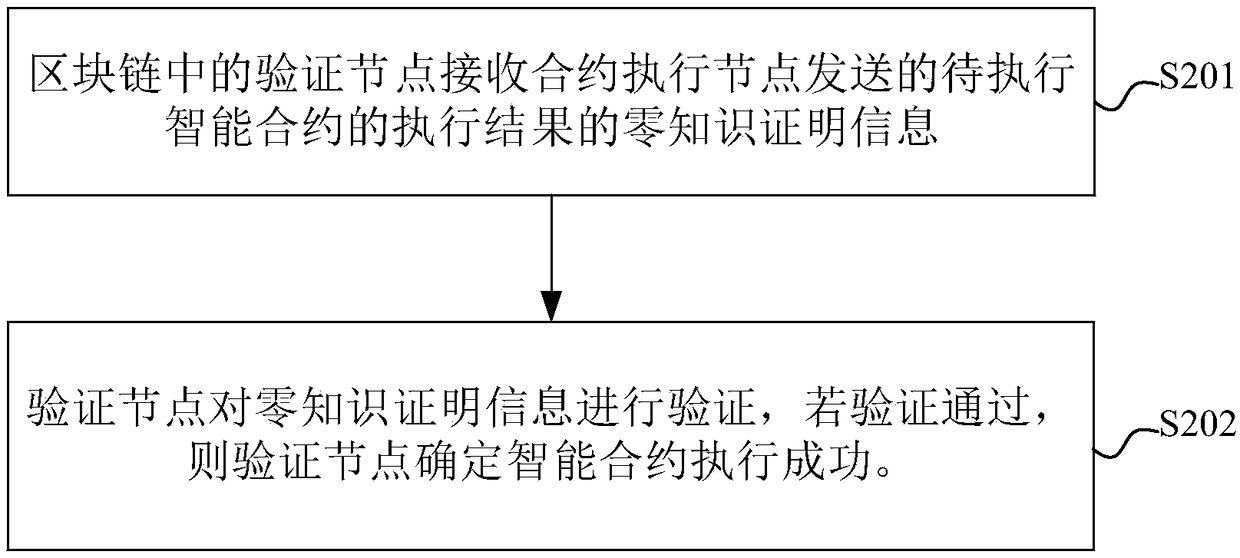
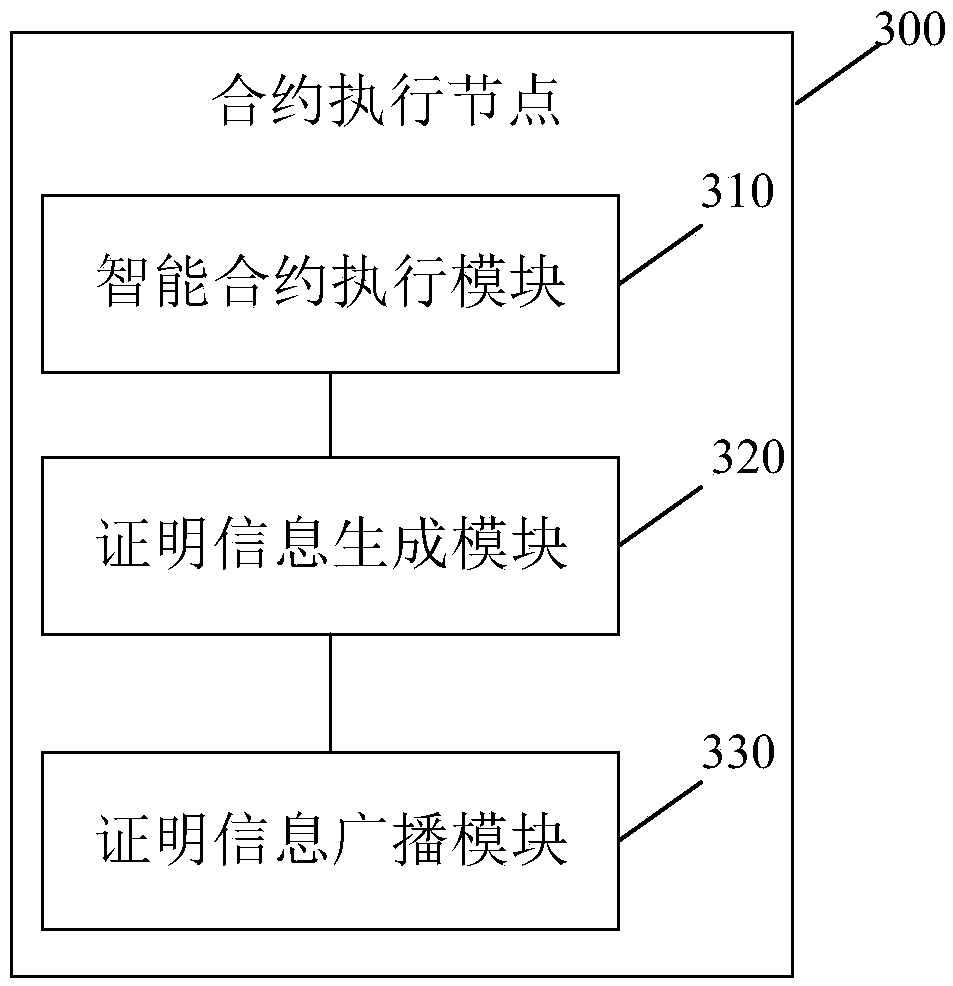
Method, node and system for executing intelligent contract, electronic device and storage medium
InactiveCN108898490AImprove execution efficiencySave computing resourcesFinanceSmart contractOperating system
Embodiments of the present application provide a method, node and system for executing an intelligent contract, an electronic device, and a storage medium. The method comprises the following steps: acontract execution node in a block chain executes an intelligent contract to be executed to obtain an execution result of the intelligent contract; the contract execution node generates zero-knowledgeproof information of the execution result, and the zero-knowledge proof information is broadcast to a verification node in the block chain, so that the verification node verifies the received zero-knowledge proof information, and it is determined that the intelligent contract is executed successfully when the verification is passed, wherein the verification node is a node other than the contractexecution node in the block chain. According to the scheme of the embodiment of the present application, the execution efficiency of the intelligent contract can be effectively improved.
Owner:BEIJING QIHOO TECH CO LTD
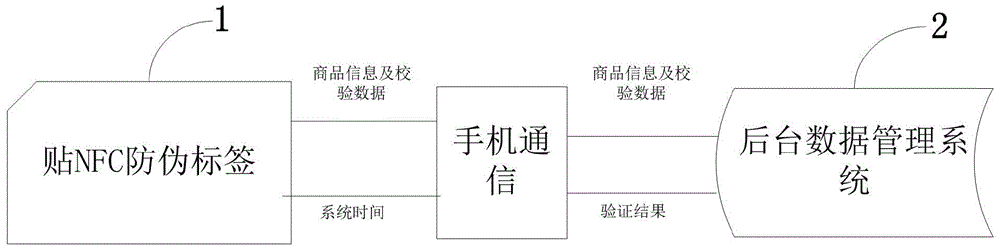
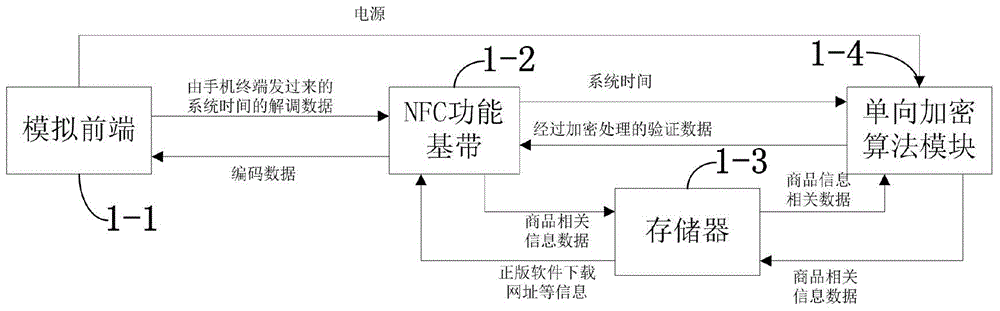
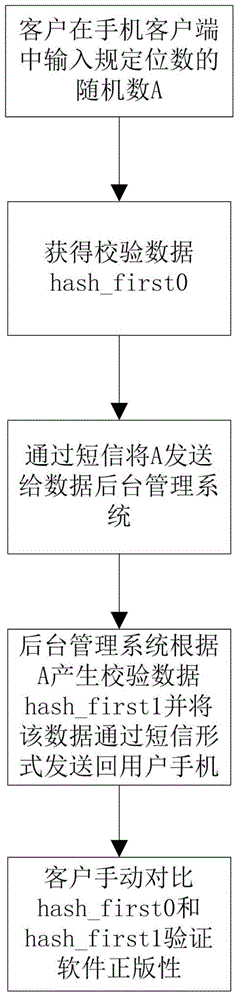
NFC mobile phone terminal anti-fake system and method based on time encryption
The invention discloses an NFC mobile phone terminal anti-fake system and method based on time encryption. The NFC mobile phone terminal anti-fake method comprises the following steps: firstly, transmitting system time to an NFC anti-fake label, after the NFC anti-fake label receives the system time, performing one-way data encryption so as to obtain verification data hash, and subsequently transmitting the ID of a product, other information of the product and the verification data hash to a mobile phone client from the NFC anti-fake label through wireless signals; transmitting the ID of the product and the verification data hash to a background data management system; after the background data management system receives the ID of the product and the verification data hash, acquiring verification data hash 0 according to an identical encryption algorithm, and comparing the obtained result hash 0 with a hash value; verifying, and transmitting the data verification result to the mobile phone client. The NFC mobile phone terminal anti-fake system comprises the NFC anti-fake label and the background data management system. The NFC mobile phone terminal anti-fake system is high in faking cost, large in faking difficulty, small in size, low in cost, high in verification efficiency, applicable to multiple products, and convenient to use.
Owner:HANGZHOU WOPUWULIAN SCI & TECH
Message sending method, message verification method, device and communication system
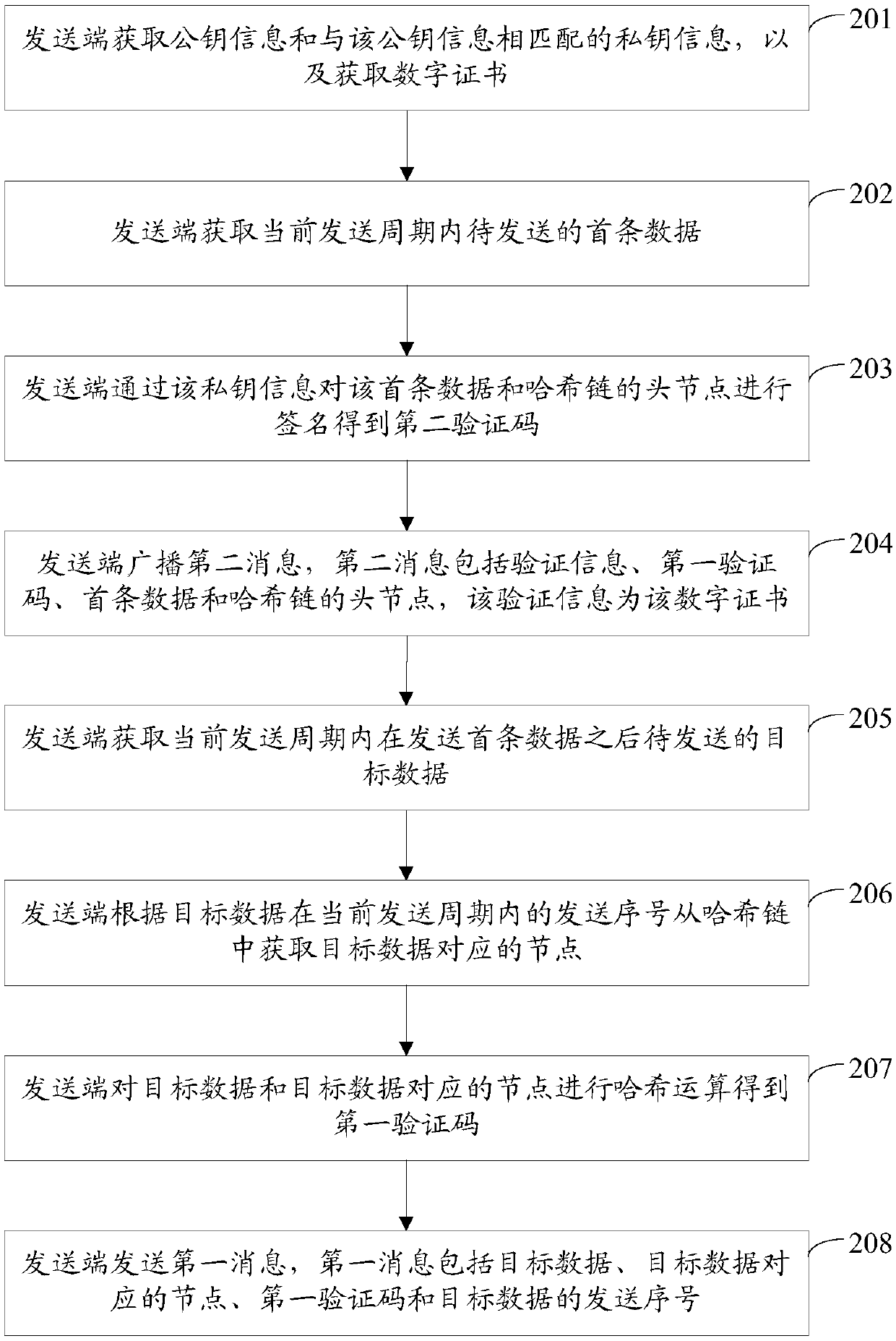
ActiveCN110896390ASimplify verification operationsSave computing resourcesParticular environment based servicesVehicle wireless communication serviceCommunications systemEngineering
The invention discloses a message sending method, a message verification method, a message sending device, a message verification device and a communication system, and belongs to the field of communication. The method comprises the steps that a sending end obtains to-be-sent target data, wherein the target data is to-be-sent data after a first piece of data is sent in a current sending period; the sending end obtains nodes corresponding to the target data from a hash chain according to the sending serial number of the target data in the current sending period, wherein the number of the nodesincluded in the hash chain is equal to the number of data allowed to be sent in the current sending period; the sending end performs hash operation on the target data and a node corresponding to the target data to obtain a first verification code, wherein the first verification code is used for verifying the target data by a receiving end; and the sending end sends a first message, wherein the first message comprises the target data, a node corresponding to the target data, the first verification code and a sending serial number of the target data. The message transmission efficiency can be improved.
Owner:HUAWEI TECH CO LTD
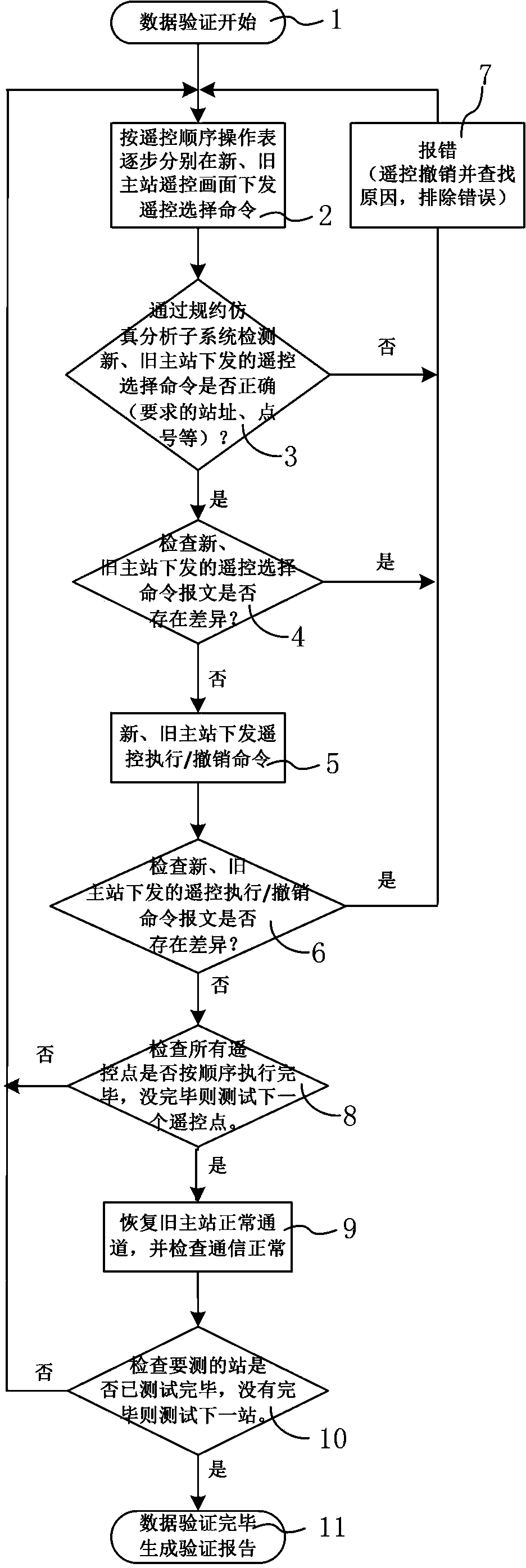
Migration data verification method for power dispatching automation system
The invention discloses a migration data verification method for a power dispatching automation system. The migration data verification method comprises the steps of selecting a new master station and an old master station corresponding to service migration of the power dispatching automation system, selecting some to-be-verified substation in the old master station, disconnecting a normal communication channel of the to-be-verified substation and the old master station and establishing a corresponding analog substation, enabling remote control points to be selected in the new master station and the old master station for the analog substation and serve as current remote control points, sequentially issuing a remote control selection command, a remote control execution command or a remote control revocation command according to the current remote control points, collecting original data of issued commands of the current new master station and the current old master station through the analog substation, checking and comparing the original data to finish data verification of every remote control point, and finally restoring the normal communication channel of the to-be-verified substation and the old master station. The migration data verification method can guarantee migration of the power dispatching automation system between the new master station and the old master station, and has the advantages of being quick in verification speed, high in verification efficiency, good in verification accuracy, and simple and practical.
Owner:STATE GRID CORP OF CHINA +1
Authorisation and verification method for password position grouping and special chip thereof
InactiveCN101382963AImplement password authorizationReduce volumeSpecial data processing applicationsArithmetic logic unitPassword
The invention provides an authentication method of code position combination authorization and a special chip thereof. The method conducts encoding to a code according to encoding rules of the CMG mechanism and then realizes the encoding of a group via a logical circuit so as to realize code authorization; position authorization is carried out by building an authorization central coordinate and authority radius; position authentication is carried out via the sum operation of extraction of square root and subtraction operation of an arithmetic logic unit; and after the position authentication is passed, a tri state gate is broken over, so that a state unit excites the pass of a signal, and operation of the state unit is started to carry out code authentication. The code authentication is passed by that a pin of the special chip generates a trigger signal, and authentication of an identifier combination is passed. The method is applicable to the technical field of electronic authorization.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
Method for sharing satellite information data
InactiveCN106056005AEasy and barrier-free sharingImprove calling speedDigital data protectionInternal/peripheral component protectionResource poolOperational system
The invention provides a method for sharing satellite information data. The method comprises a method for safe storage of the satellite information data and a method for safe access of the satellite information data, wherein the method for safe storage of the satellite information data includes the following steps of: (1) carrying out safety verification on an identity of a storage user; (2) preprocessing the satellite information data; (3) encoding the preprocessed satellite information data; (4) abstracting and centralizing hardware storage resources, mapping the abstracted and centralized hardware storage resources to a completely uniformed resource pool, and virtualizing an operation system of a user; and (5) storing the satellite information data in the resource pool in a form of a final code; and the method for safe access of the satellite information data includes the following steps of: (1) carrying out the safety verification on an identity of an accessing user; and (2) reading the satellite information data stored in the resource pool. According to the method, the obstacle free sharing can be realized, the memory usage is reduced, the data calling speed is boosted and the safety of sharing the satellite information data is improved on the premise of guaranteeing the convenience.
Owner:吴本刚
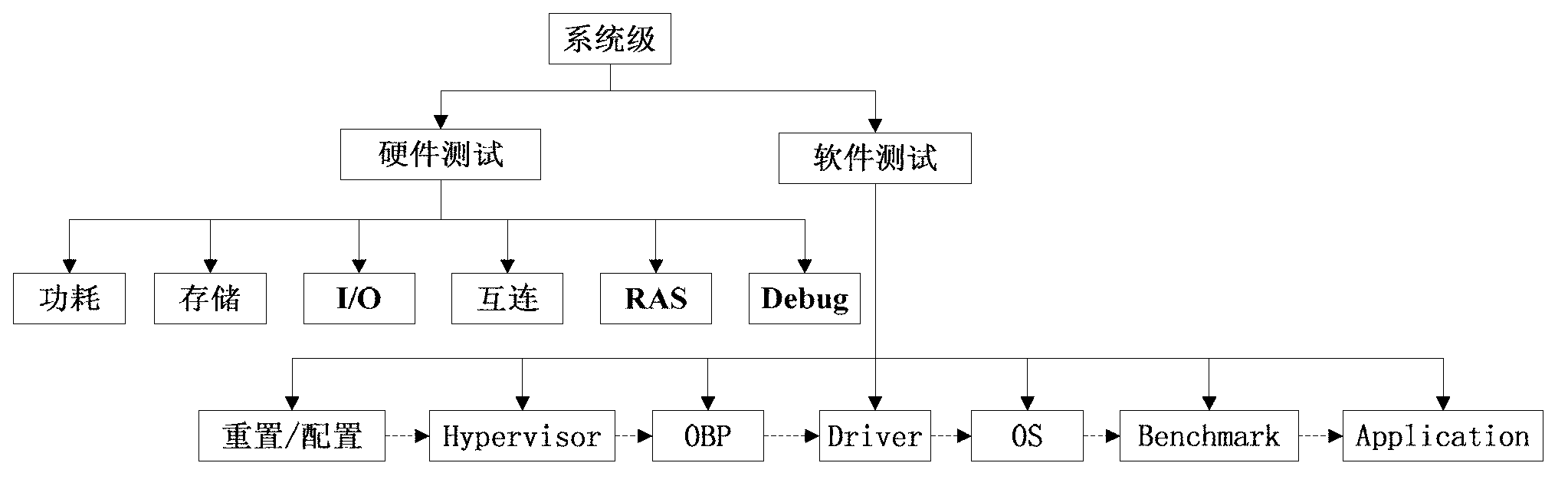
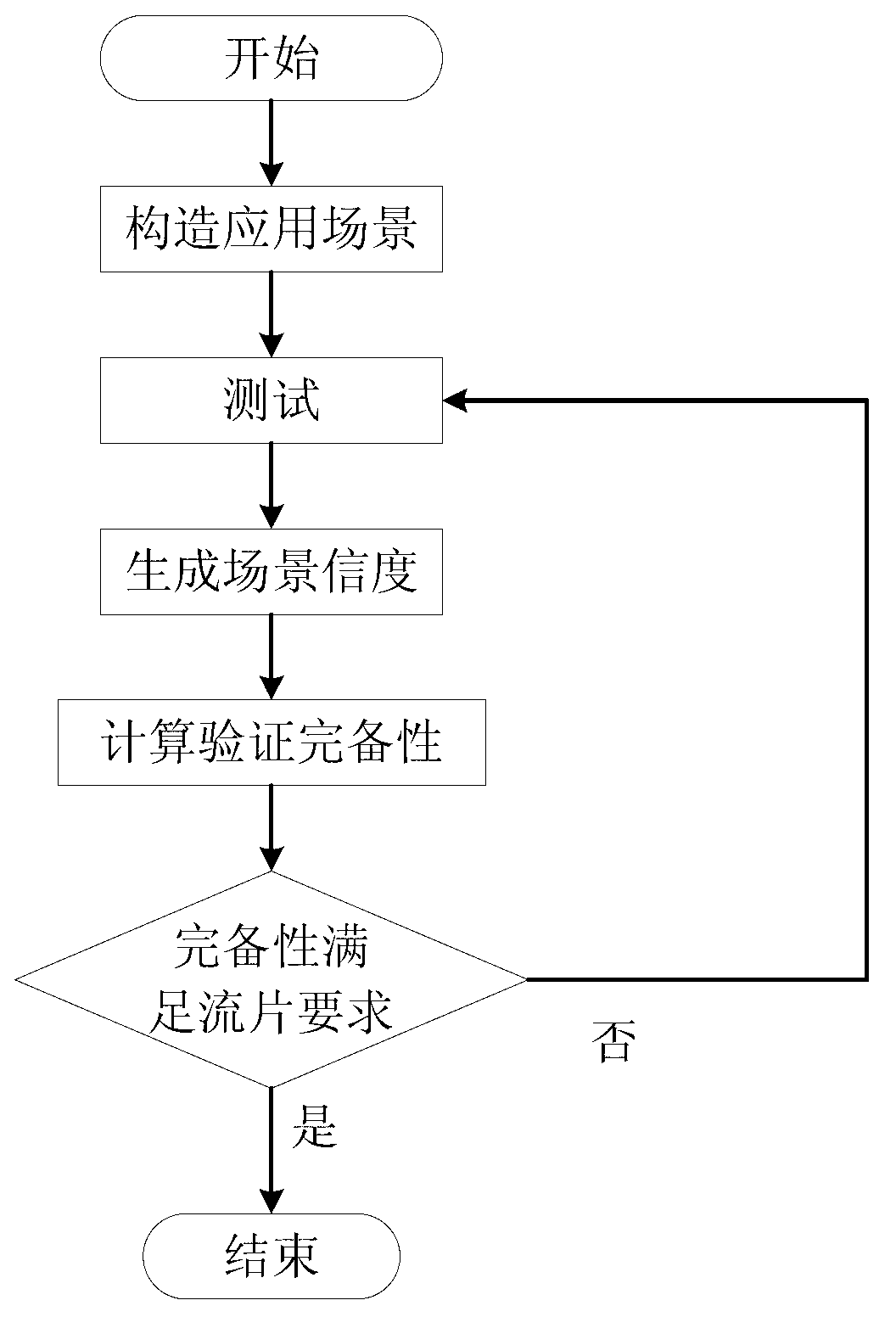
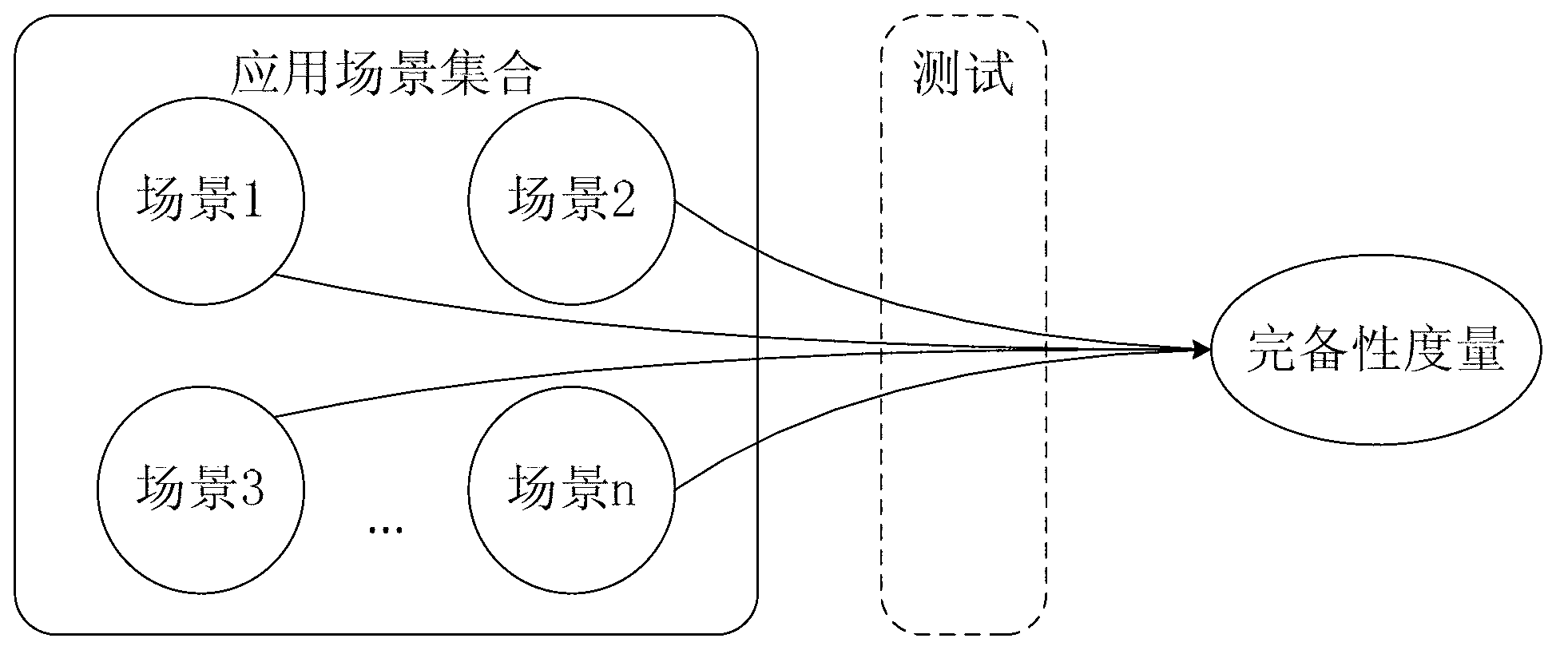
Scenario-based processor system-level verification completeness measurement method
ActiveCN103268272AFast verificationImprove verification efficiencyFunctional testingApplication areasComputer science
The invention discloses a scenario-based processor system-level verification completeness measurement method. The method includes 1), constructing typical application scenarios according to the application field of a processor; 2), constructing scenario testing environment for each application scenario to allow a scenario testing case to test the processor, generating scenario reliability according to test completion state, and taking a weighted average of scenario reliability of all the application scenarios as a system-level verification completeness measurement value; determining whether the completeness of the processor meets the processing requirements of the processor or not according to the system-level verification completeness measurement value; if not, returning to step 2) to test low-reliability application scenarios continuously; and if so, completing test and exiting. According to the scenario-based processor system-level verification completeness measurement method, basis is provided for processing through quantitative description of related verification reliability of the processor, and the scenario-based processor system-level verification completeness measurement method has the advantages of high verification speed, high verification efficiency, high testing environment utilization rate, and short verification time.
Owner:NAT UNIV OF DEFENSE TECH
Electronic lock and unlocking method thereof
ActiveCN105608770AImprove securityFast verificationIndividual entry/exit registersSubcutaneous biometric featuresFingerprintImage pre processing
The invention discloses an electronic lock and an unlocking method thereof. The unlocking method comprises steps as follows: S1, original image acquisition; S2, original image preprocessing; S3, fingerprint image verification; S4, vein image verification; S5, unlocking. The electronic lock is unlocked through sequential multiple verification including fingerprint image verification, vein image verification and the like, vein image verification can be performed only after a user passes fingerprint image verification, and unlocking can be realized through three-dimensional characteristic data-based living fingerprint verification conducted after the user passes vein image verification, so that the safety performance of the electronic lock is improved; vein image verification overcomes the defect that fingerprint verification is easy to copy, and the safety performance of the electronic lock is further improved.
Owner:CHENGDU BILSUM SCI & TECH DEVCO
Android third party push enhancement method and system, and related device
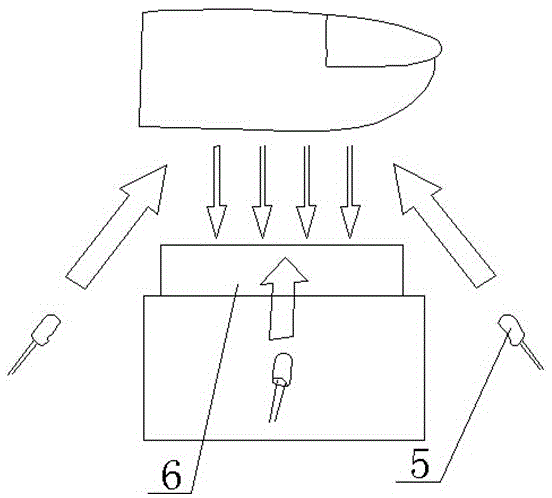
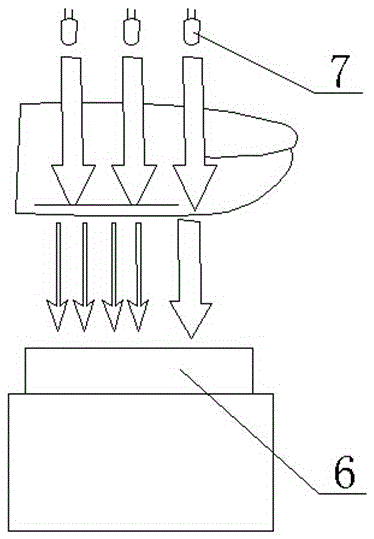
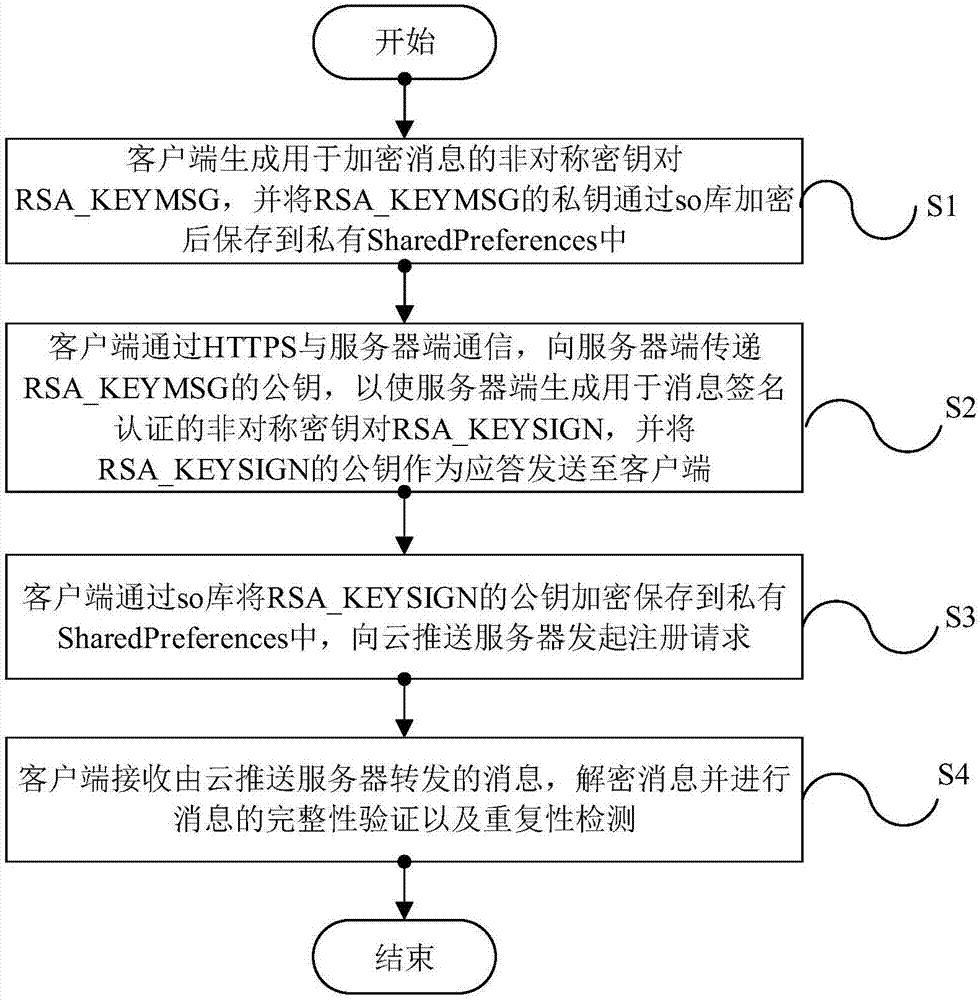
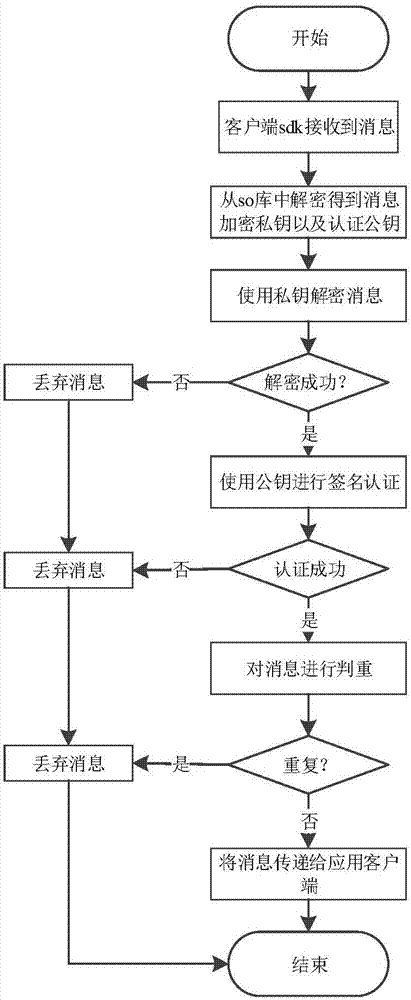
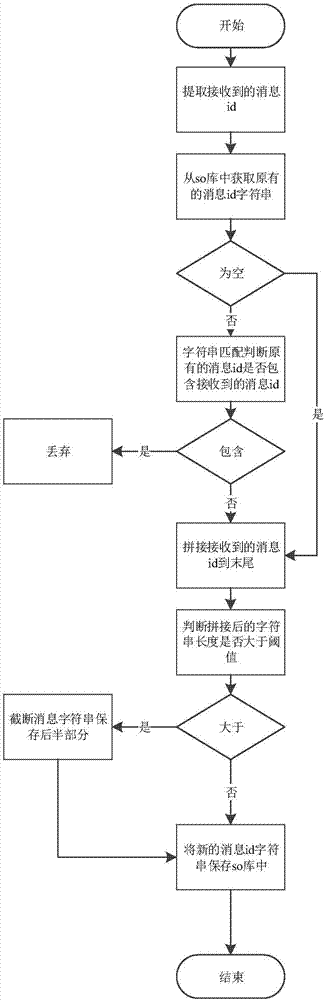
ActiveCN107148014AImprove securitySave storage spaceTransmissionSecurity arrangementThird partyHypertext Transfer Protocol over Secure Socket Layer
The invention discloses an Android third party push enhancement method and system, and a related device. The method comprises the following steps: realizing message encryption and signature authentication by using asymmetric encryption; signing and encrypting a message during message transmission, and transmitting the message through HTTPS; receiving the message by a client, decrypting and verifying the message, and meanwhile detecting the repeatability of the message in a character string matching mode, therefore the performance overhead is smaller; and on the respect of client key management, an asymmetric encryption key is stored in a private memory SharedPreferences through symmetric encryption by realizing encryption and decryption logic via a so library. The method provided by the invention has relatively high security, can resist against general message forgery, message leakage, message replay attack and untrusted third party push problems.
Owner:HUAZHONG UNIV OF SCI & TECH
Power grid data sharing method
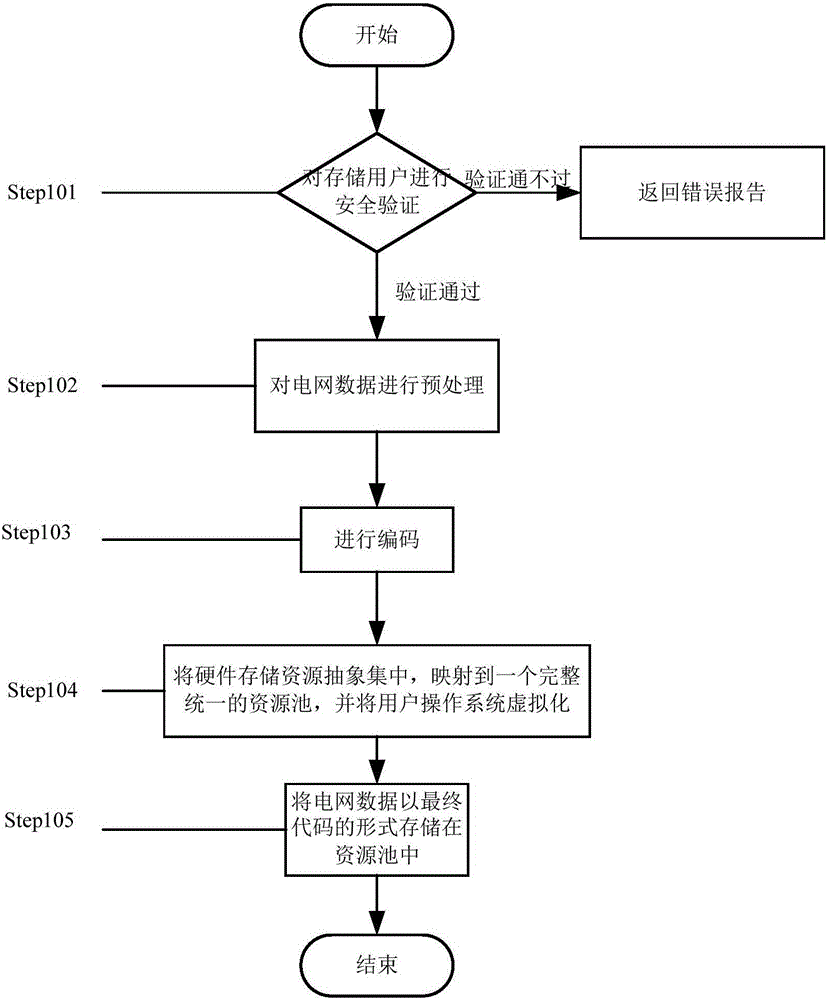
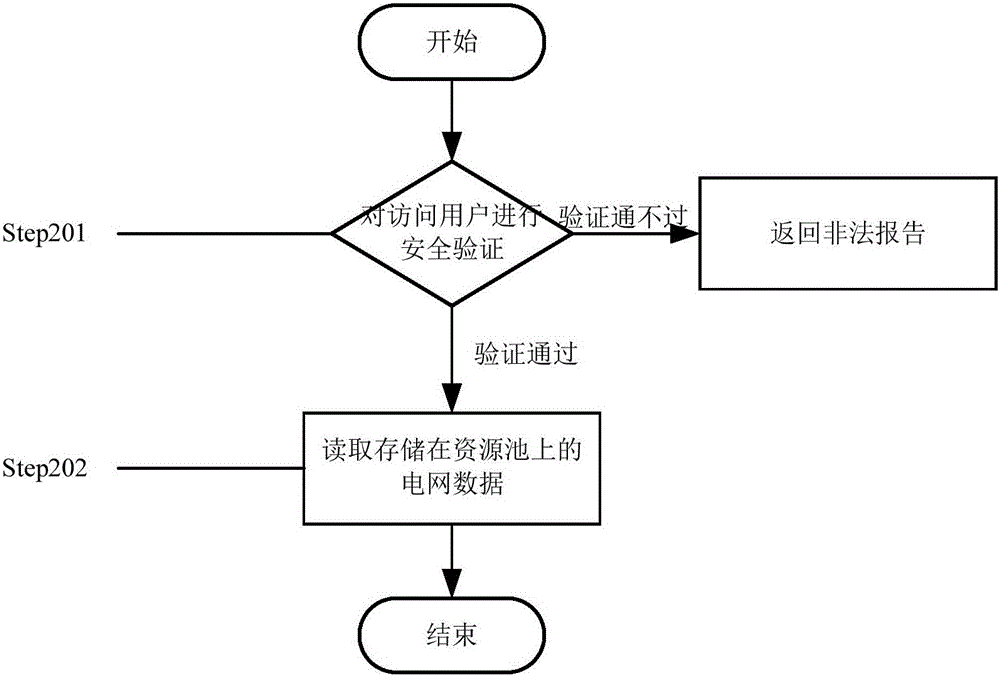
InactiveCN106131010AEasy and barrier-free sharingImprove calling speedData processing applicationsTransmissionResource poolVirtualization
The invention provides a power grid data sharing method comprising first treatment, power grid data safety storage and power grid data safety access. The power grid data safety storage comprises the following steps of 1, authenticating safety of a storage user; 2, preprocessing power grid data; 3, encoding; 4, abstractly concentrating hardware storage resources, and mapping the resources into a complete unified resource pool, and virtualizing a user operating system; and 5, storing the power grid data into the resource pool in a final code manner. The power grid data safety access comprises the following steps of 1, authenticating safety of an access user identity; 2, reading power grid data stored in the resource pool. According to the method of the invention, the barrier-free sharing can be achieved, the memory usage is reduced, the data calling speed is improved, and the sharing safety of the power grid data is improved on the premise of ensuring convenience.
Owner:吴本刚
Information operation and maintenance service knowledge sharing method based on trusted computing of big data
ActiveCN106156640AEasy and barrier-free sharingImprove calling speedInput/output to record carriersDigital data protectionResource poolOperational system
The invention provides an information operation and maintenance service knowledge sharing method based on trusted computation of big data. According to the method, a trusted degree assessment mechanism and a trusted relationship transfer mechanism are built on the basis of characteristics such as protective function, authentication, integrity measurement and the like; the method comprises steps as follows: secure storage of information operation and maintenance knowledge, secure access of information operation and maintenance knowledge as well as trusted evaluation, wherein the secure storage of the information operation and maintenance knowledge comprises following steps: (1), performing security verification on an identity of a stored user; (2), preprocessing information operation and maintenance service knowledge data; (3), performing encoding; (4), performing abstract concentration on hardware storage resources, mapping the resources to an integrated and unified resource pool, and virtualizing a user operating system; (5), storing the information operation and maintenance service knowledge data into the resource pool in a final code form; the secure access of the information operation and maintenance knowledge comprises following steps: (1), performing security verification on an identity of an access user; (2), reading the information operation and maintenance service knowledge data stored on the resource pool. With the adoption of the method, barrier-free sharing can be realized, memory footprint is reduced, the data calling speed is increased, and the security of information operation and maintenance service knowledge sharing is improved on the premise that the convenience is guaranteed.
Owner:广州同构信息科技有限公司
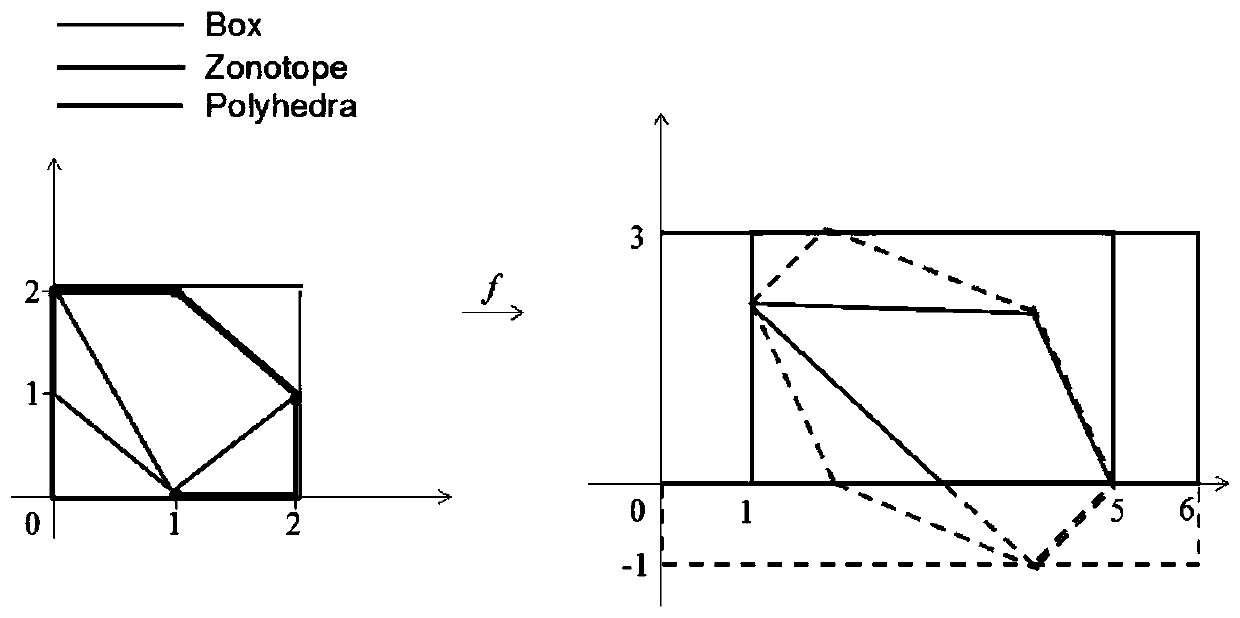
Local robustness verification method of neural network
PendingCN110991603AFix security issuesScale upNeural architecturesNeural learning methodsEngineeringArtificial intelligence
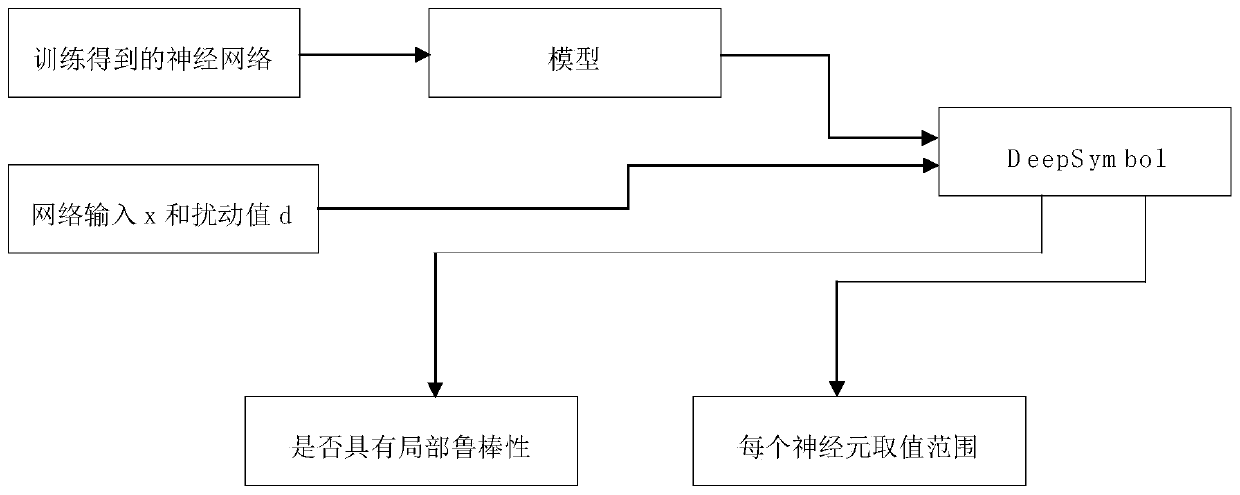
The invention relates to a local robustness verification method of a neural network, and the method comprises the steps: inputting the neural network obtained through training, and processing the semantics of the neural network to obtain a model; abstracting semantics of the neural network into operation on an abstract domain (or transformation on the abstract domain) of a mathematical structure based on the abstract interpretation; giving input and tiny disturbance; abstracting input and tiny disturbance into elements in an abstract domain, introducing a symbol propagation method, and converting a neural network local robustness verification problem into an abstract domain operation and judgment problem; and outputting an operation result so as to confirm whether the local robustness of the neural network is verified.
Owner:广州市智能软件产业研究院
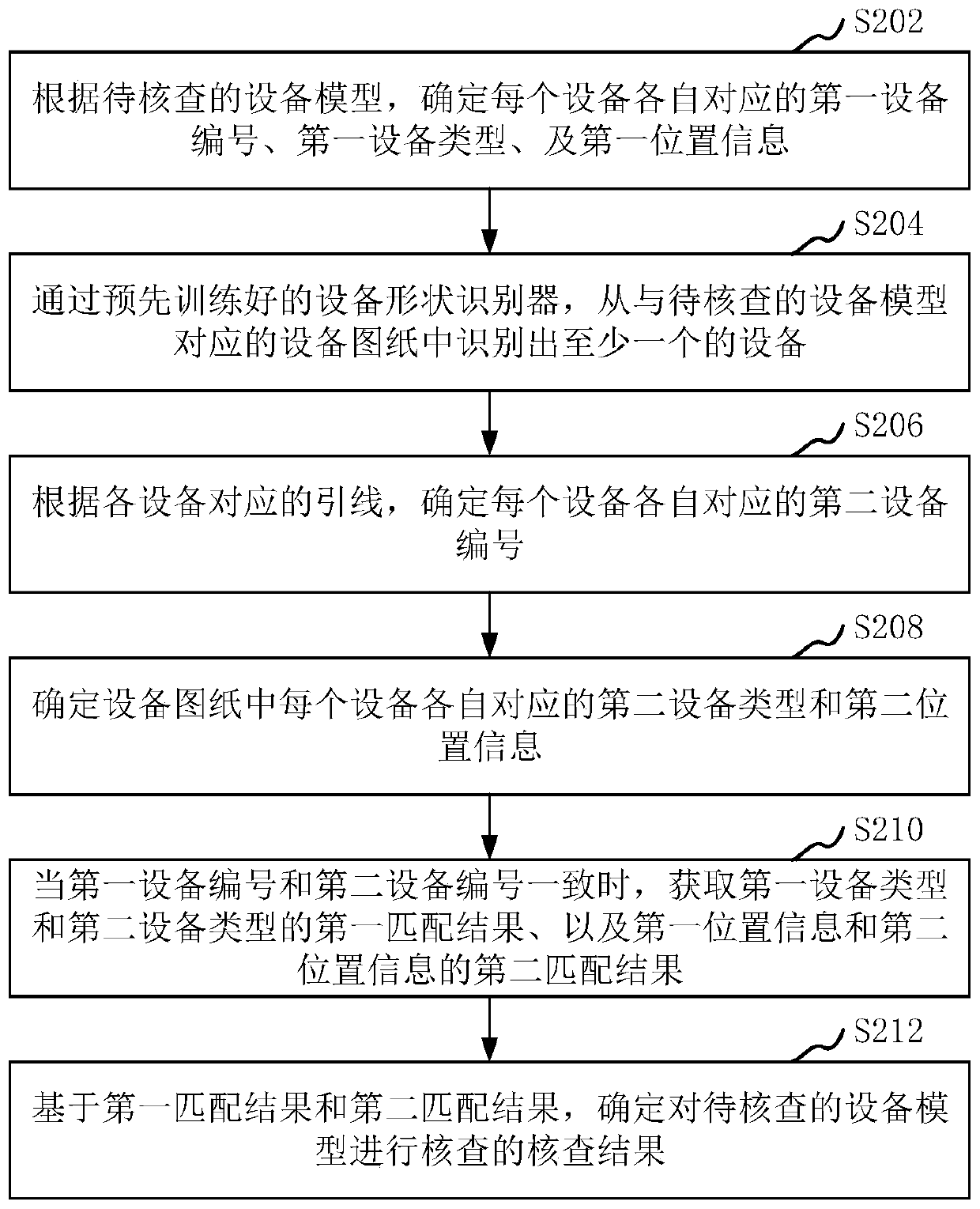
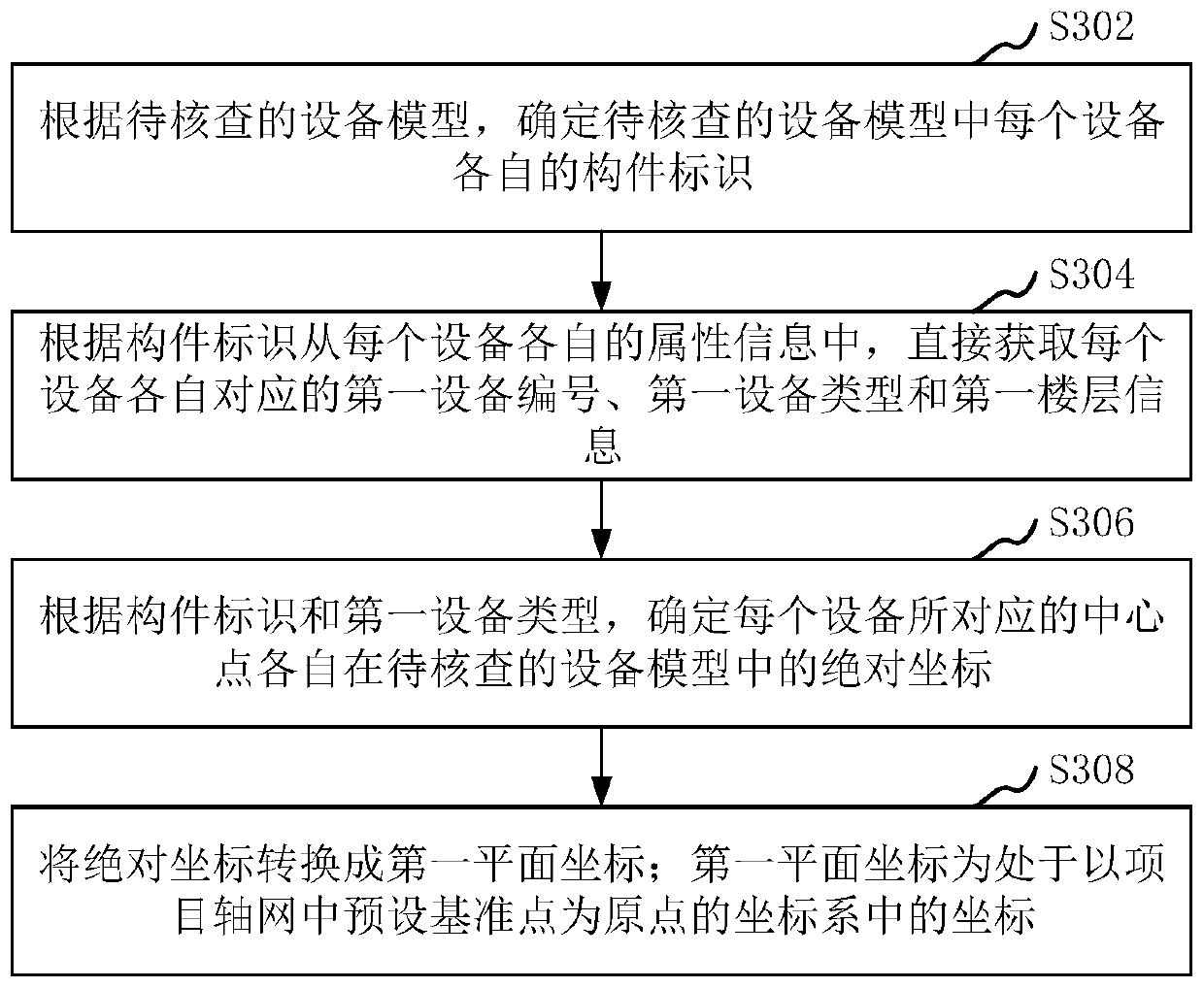
Method and device for equipment model checking, computer equipment and storage medium
ActiveCN111191800AImprove verification efficiencyFast verificationGeometric CADCharacter and pattern recognitionDevice typeSimulation
The invention relates to a method and a device for equipment model checking, computer equipment and a storage medium. The method comprises the following steps: determining a first device number, a first device type and first position information corresponding to each piece of equipment according to an equipment model; identifying at least one piece of equipment from an equipment drawing corresponding to the equipment model through a pre-trained equipment shape identifier; determining a second equipment number corresponding to each piece of equipment according to the lead corresponding to eachpiece of equipment; determining a second equipment type and second position information corresponding to each piece of equipment in the equipment drawing; when the first equipment number is consistentwith the second equipment number, obtaining a first matching result of the first equipment type and the second equipment type, and a second matching result of the first position information and the second position information; and based on the first matching result and the second matching result, determining a checking result for checking the equipment model. By adopting the method, the equipmentchecking efficiency of the equipment model can be improved.
Owner:深圳市万翼数字技术有限公司
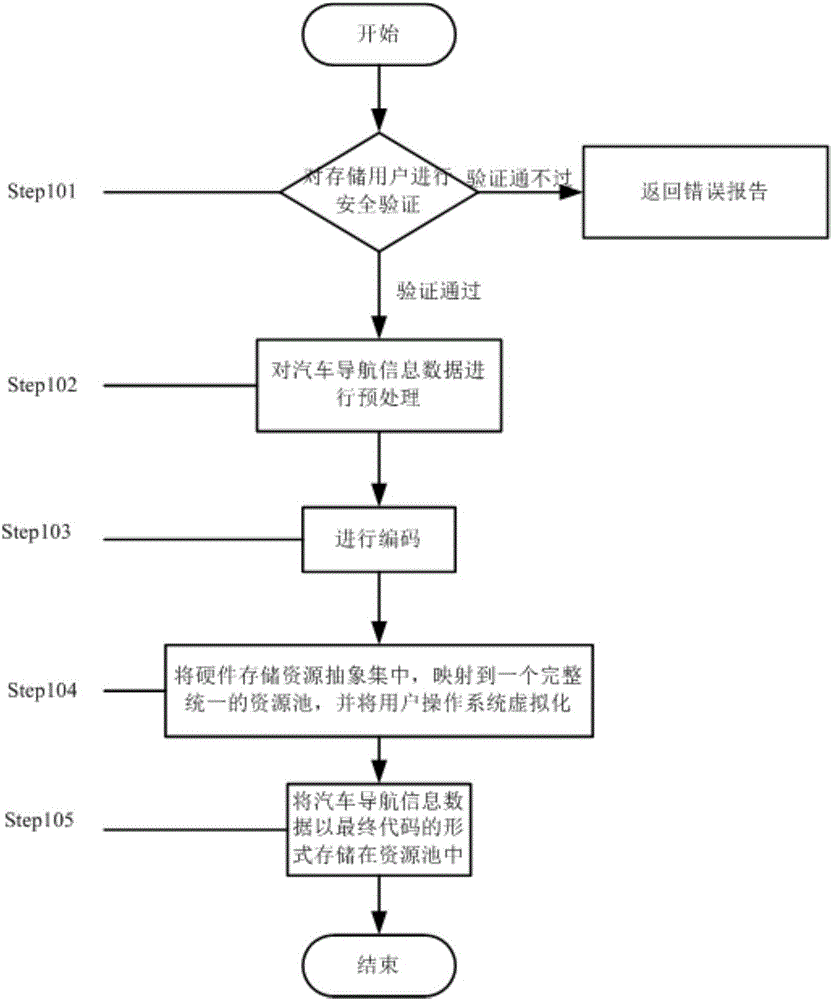
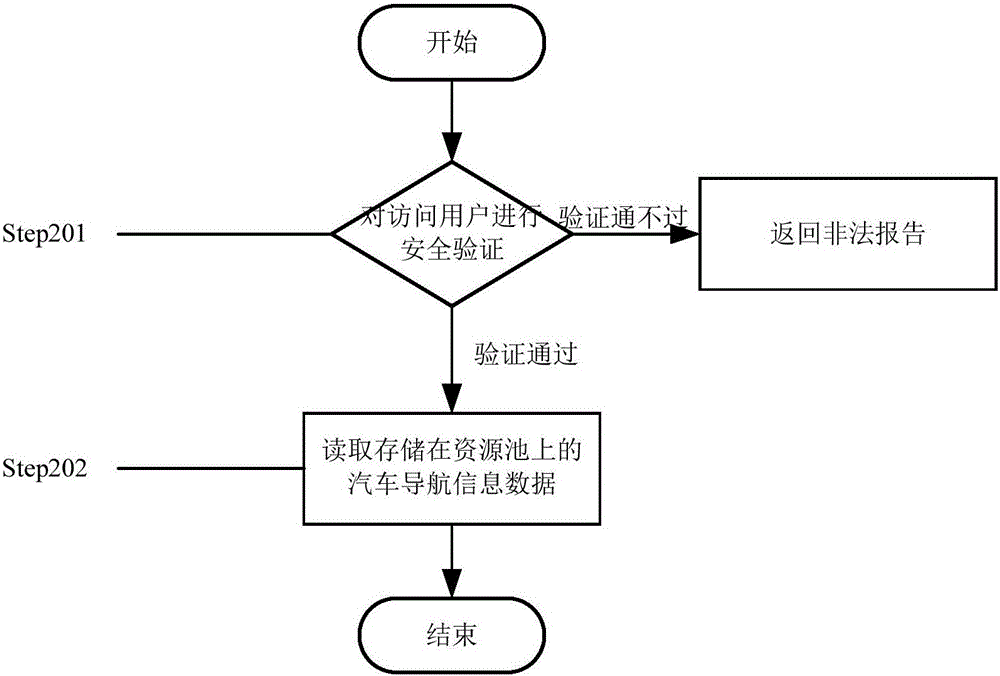
Automobile navigation information data sharing method
InactiveCN106203166AEasy and barrier-free sharingImprove calling speedDigital data protectionTransmissionVirtualizationResource pool
The invention provides an automobile navigation information data sharing method. The method comprises a step of secure storage of automobile navigation information data and a step of secure access of the automobile navigation information data, wherein the step of secure storage of the automobile navigation information data comprises the following sub-steps of: (1) carrying out security verification on the identity of a storage user, (2) pre-processing the secure storage of automobile navigation information data, (3) carrying out coding, (4) abstractly and intensively mapping hardware storage resources into a complete and uniform resource pool and virtualizing a user operation system, and (5) storing the navigation information data in the resource pool in a final code form; and the step of secure access of the automobile navigation information data comprises the following sub-steps of: (1) carrying out security verification on the identity of an access user, and (2) reading the automobile navigation information data stored in the resource pool. According to the automobile navigation information data sharing method, the barrier-free share can be realized, the memory usage is decreased, the data calling speed is improved, and the security of sharing the automobile navigation information data is improved under the premise of ensuring the convenience.
Owner:吴本刚
Ticket booking and checking system and ticket booking and checking method thereof
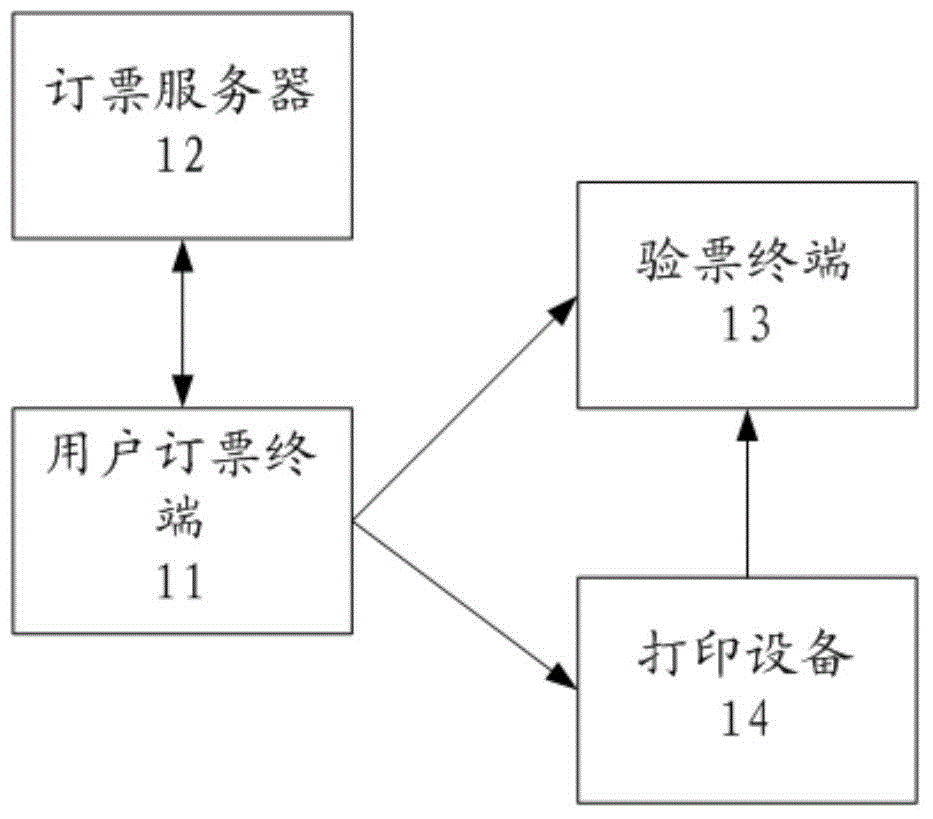
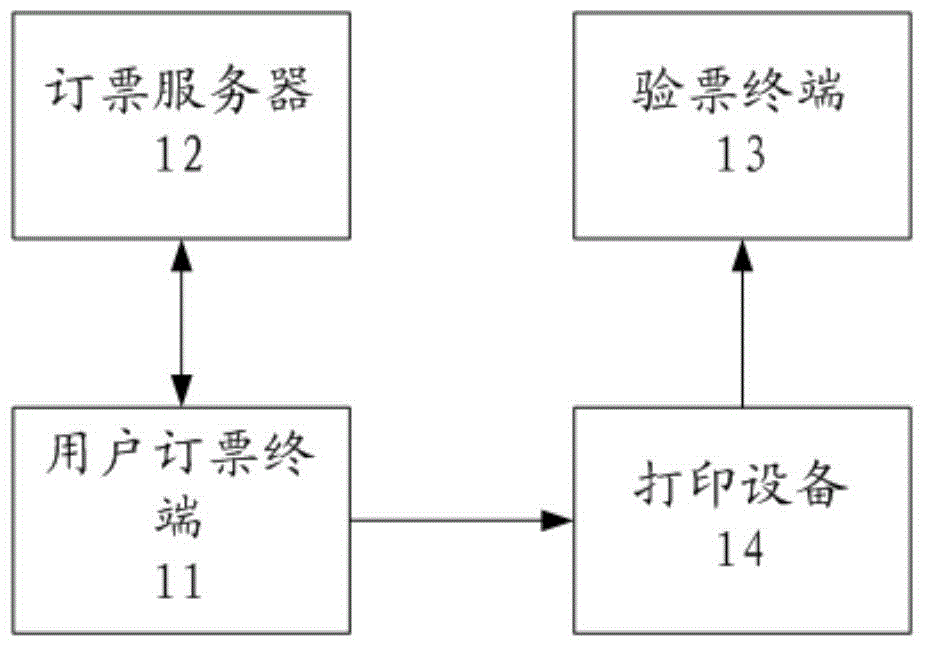
InactiveCN105321209AImprove securityFast verificationReservationsMachines for printing and issuing ticketsPasswordUser input
A ticket booking and checking system comprises a user ticket booking terminal, a ticket booking server, and a ticket checking terminal. The user ticket booking terminal is used for issuing a ticket booking request to the ticket booking server, prompting a user to input ticket booking data and a checking password according to the response of the ticket booking server and sending the ticket booking data and the checking password to the ticket booking server. The ticket booking server is used for responding to the ticket booking request from the user ticket booking terminal, generating an electronic ticket according to the ticket booking data and the checking password from the user ticket booking terminal and sending the electronic ticket to the user ticket booking terminal, wherein the electronic ticket is provided with plaintext information corresponding to the ticket booking data and a checking code generated by the checking password. The ticket checking terminal is used for prompting the user to input the checking password, scanning and identifying the checking code on the electronic ticket or a paper ticket printed based on the electronic ticket and matching the checking code with the checking password currently input by the user. The ticket booking and checking system is not affected by the condition of network, is quick in checking, safe and efficient.
Owner:SHANGHAI MINXING SECOND MIDDLE SCHOOL
Safe electronic lock and unlocking method
ActiveCN105427440AImprove securityPrevent forgeryIndividual entry/exit registersPasswordFeature data
The invention discloses a safe electronic lock and an unlocking method. The unlocking method comprises the following steps: S1, an original image capture step; S2, an original image preprocessing step; S3, an original image verification step; S4, a finger living body verification step; S5, an unlocking step. According to the unlocking method, in order to realize unlocking of the electronic lock, multiple verifications such as original image verification, finger living body verification and password verification need to be performed successively, and unlocking can only be realized when all the verifications are passed, so the safety performance of the electronic lock is greatly improved; during finger living body verification, pieces of feature data obtained by collection are coupled into three-dimensional data, a fingerprint center point is obtained in the three-dimensional data according to a fingerprint center point location algorithm, and whether a finger is a living body or not is judged by the relative position of the fingerprint center point and a finger vein, thus preventing another person from fabricating a finger and passing verification, and improving the safety performance of the electronic lock.
Owner:CHENGDU BILSUM SCI & TECH DEVCO
Dedicated vehicle identifying method and system thereof
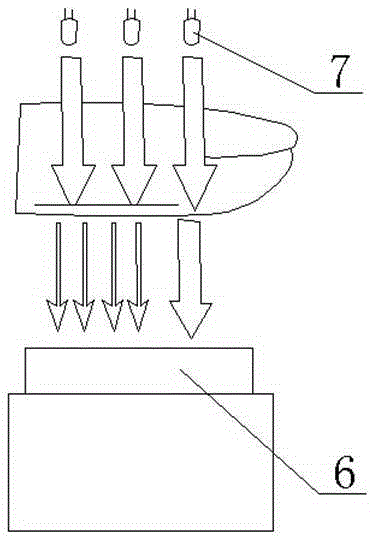
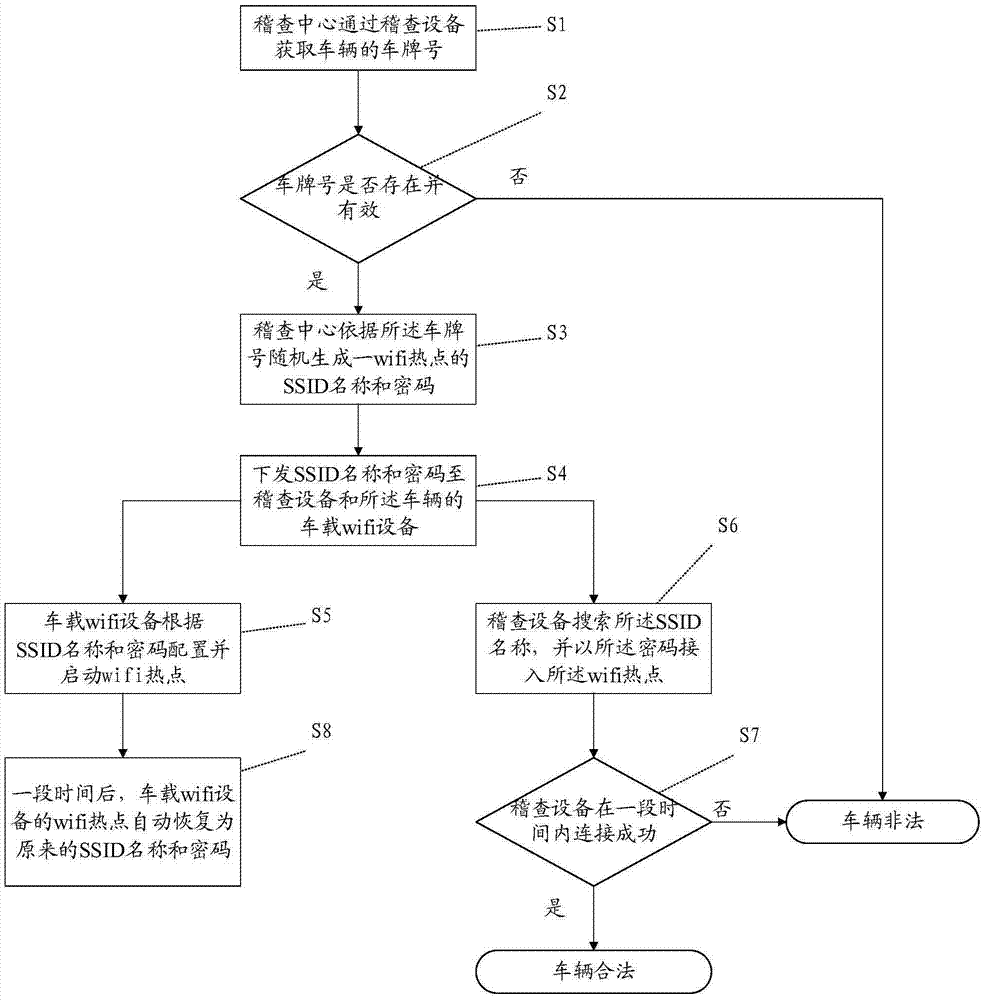
ActiveCN106981199APrevent cheating audit issuesLow costRoad vehicles traffic controlComputer science
The invention discloses a dedicated vehicle identifying method and a system thereof. The method includes the following steps: acquiring the plate number of a vehicle; on the basis of the plate number, randomly generating the SSID name and code of a wifi hotspot; issuing the SSID name and code of the wifi hotspot to an inspection device and an onboard wifi device of the vehicle; the onboard wifi device changing the SSID name and code of the self wifi hotspot to the SSID name and code, at the same time restarting the wifi hotspot; if the inspection device can successively access t the wifi hotspot on the basis of the SSID name and code, determining that the vehicle is legal. According to the invention, the method conducts dynamic matching and verification by issuing the SSID name and code of the wifi hotspot, prevents inspection from being tarnished by frauds led by complete cloning of electronic labels, obviates the need for installing intelligent overhead lights, and has low cost; also, the method can realize automatic operation in the entire process, has fast verification speed and high efficiency.
Owner:XIAMEN YAXON NETWORKS CO LTD
Earth geographic information data sharing method
InactiveCN106202415AEasy and barrier-free sharingImprove calling speedGeographical information databasesSpecial data processing applicationsVirtualizationSafe storage
The invention provides an earth geographic information data sharing method. The method comprises the steps of safe storage of earth geographic information data and safe access of earth geographic information data. Safe storage of earth geographic information data comprises the steps of 1, conducting safety verification on the identity of a storage user; 2, pretreating earth geographic information data; 3, conducting coding; 4, conducting abstract concentration on a hardware storage resource, mapping the resource into a complete and uniform resource pool, and virtualizing a user operation system; 5, storing the earth geographic information data in the resource pool in the form of final code. Safe access of earth geographic information data comprises the steps of 1, conducting safety verification on the identity of an access user; 2, reading earth geographic information data stored in the resource pool. By the adoption of the method, accessible sharing can be achieved, memory usage is reduced, data calling speed is increased, and earth geographic information data sharing safety is improved on the premise that convenience is guaranteed.
Owner:吴本刚
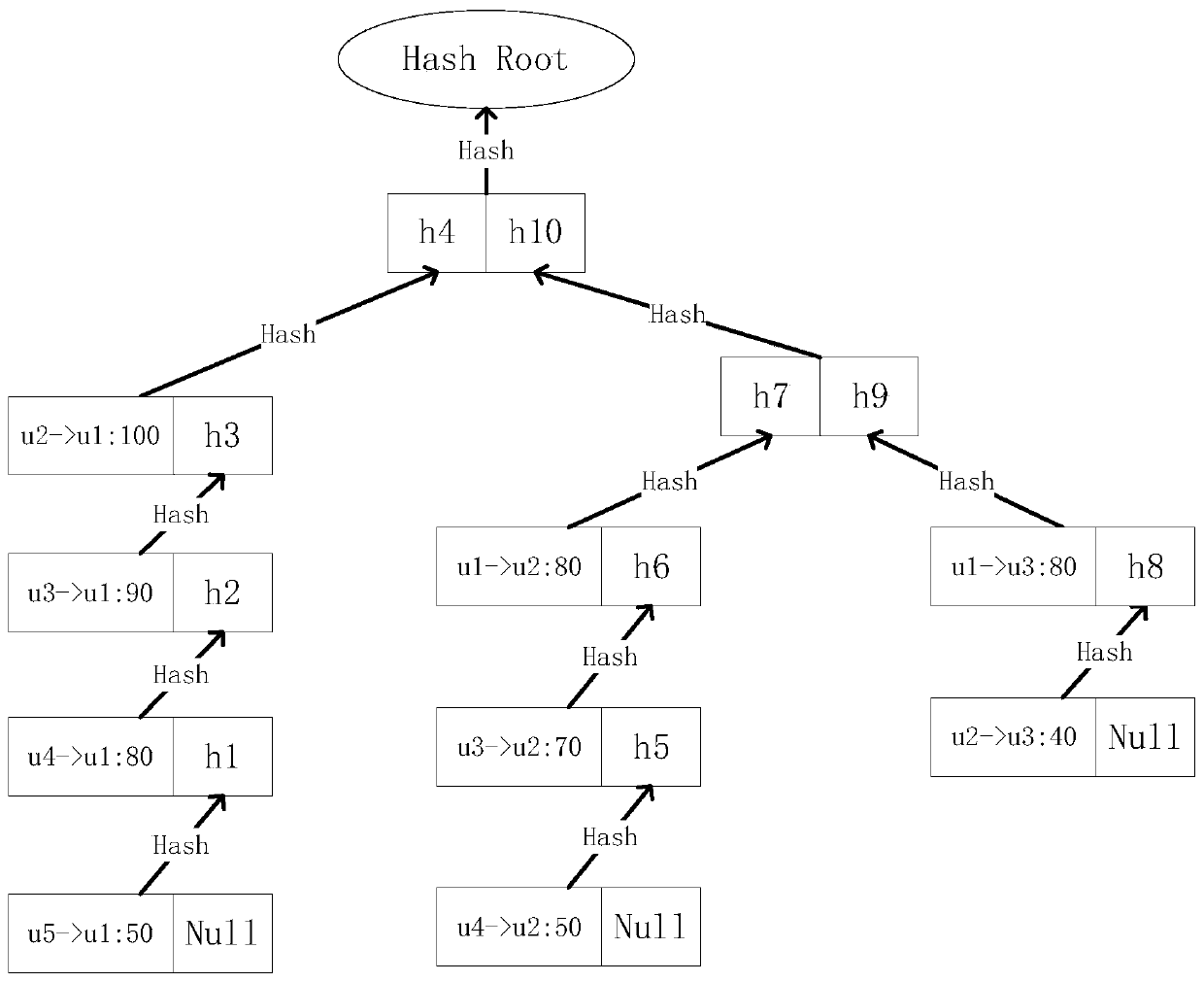
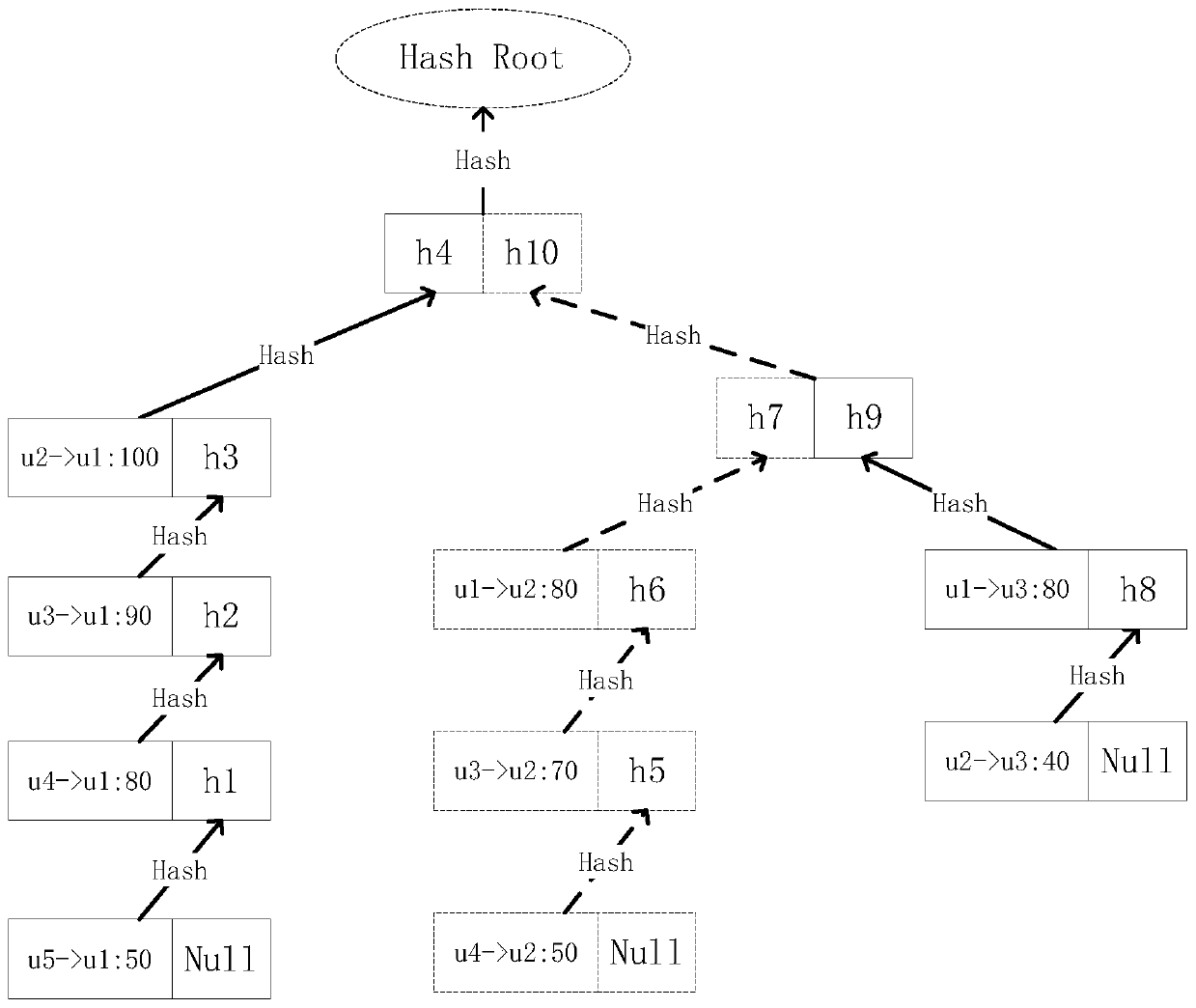
Block generation and transaction verification method suitable for energy blockchain
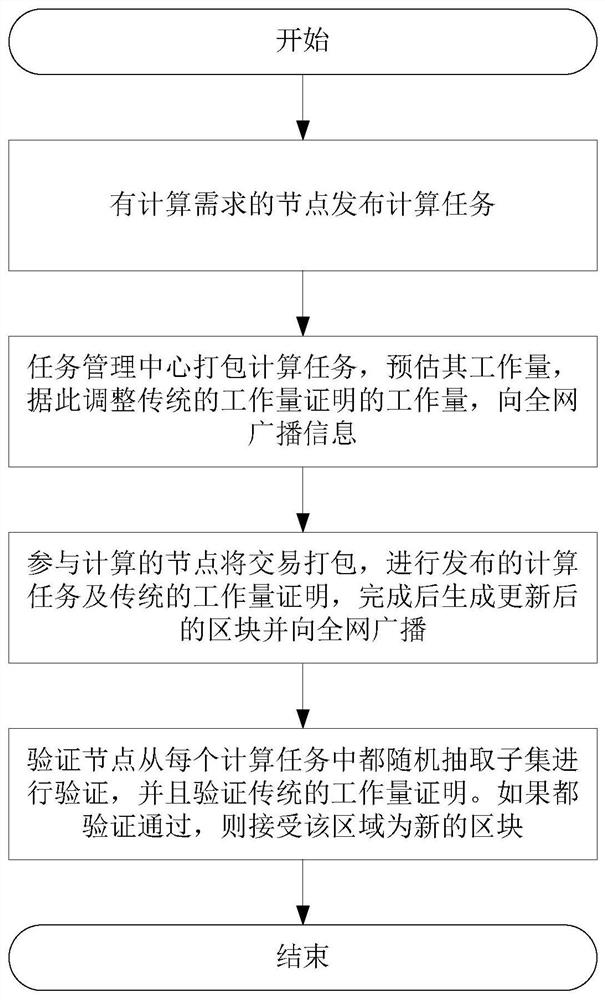
PendingCN111080298AFast verificationReduce verification timesFinanceDatabase distribution/replicationEngineeringFinancial transaction
The invention relates to the field of energy block chains, in particular to a block generation and transaction verification method suitable for an energy blockchain. An obvious hotspot account is provided for electric energy transaction; an original block generation mode enables a blockchain to verify whether a transaction is legal, and needs the same calculation and storage cost for each account.According to the invention, targeted optimization is carried out on an electric energy transaction scene; according to the method, by modifying the merkle tree organization form, the account with thehigh priority is closest to the root node of the query when forming the block and can be found more quickly, and compared with the prior art, the method can achieve the purpose of reducing the calculation cost and has the characteristics of flexibility, simplicity and high practicability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
Intelligent access control system with short message validation and validation method of intelligent access control system
InactiveCN104599378AFast verificationReduce the amount of informationIndividual entry/exit registersValidation methodsControl unit
The invention discloses an intelligent access control system with short message validation. The intelligent access control system comprises a processor, a memory, a bluetooth communication unit, a mobile phone terminal, an alarm unit, a signal search unit, a validation unit, a random number generation unit, a digital keyboard, a door control unit and a power supply unit; a validation method of the intelligent access control system comprises the following steps: setting a matched password, matching the mobile phone terminal of personnel allowed to enter with the intelligent access control system through the bluetooth communication unit and the set password; transmitting a search signal by the signal search unit of the intelligent access control system; searching the matched mobile phone terminal, generating a random number validation code by the random number generation unit and transmitting to the mobile phone terminal; inputting the received validation code by the personnel requesting to enter through the digital keyboard; and validating whether the input number is correct or not by the validation unit. The access control system is controlled through the validation code in a bluetooth communication manner; the validation speed is high; the jammed condition does not easily appear; and the validation code is generated through the random number generation unit, so that the intelligent access control system is high in safety performance and small in error.
Owner:天津瑞为拓新科技发展有限公司
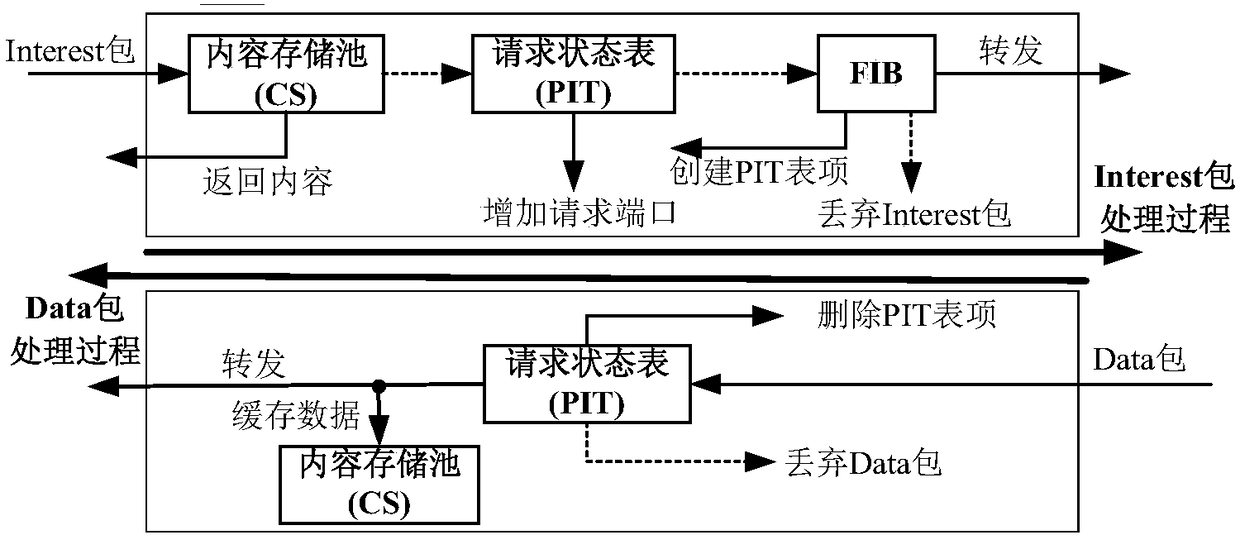
Content verification method and device
ActiveCN108632197AEnsure safetyFast verificationUser identity/authority verificationNetwork packetEncryption
Disclosed is a content verification method and device used for accelerating the speed of content verification. The method includes the following steps: a first network device receives a first data packet sent by a second network device, wherein the first data packet carries a first content; if the first data packet carries first symmetrical encryption information and the first symmetrical encryption information is used for verifying the first content in a trusted domain in which the first network device is located, the first network device verifies the validity of the first content carried bythe first data packet according to the first symmetric encryption information; and if the first content is valid, the first network device processes the first data packet according to a transmission path of the first data packet.
Owner:HUAWEI TECH CO LTD
Meteorological data sharing method
InactiveCN106209846AEasy and barrier-free sharingImprove calling speedError preventionVirtualizationSafe storage
The invention provides a meteorological data sharing method which comprises safe storage and safe access of meteorological data. Safe storage of the meteorological data comprises the following steps that (1) safety verification is carried out on identity of a storage user; (2) the meteorological data is pre-processed; (3) coding is carried out; (4) hardware storage resources are abstracted and concentrated, and mapped into a complete unified resource pool, and a user operating system is virtualized; and (5) the meteorological data is stored in the resource pool in the form of a final code. Safe access of the meteorological data comprises the following steps that (1) safety verification is carried out on the identity of an access user; and (2) the meteorological data stored in the resource pool is read. According to the invention, sharing without obstacles can be realized, memory occupation is reduced, the data calling speed is improved, and the safety of meteorological data sharing is improved on the premise that the convenience is ensured.
Owner:吴本刚
Computing task processing method and device, storage medium and processor
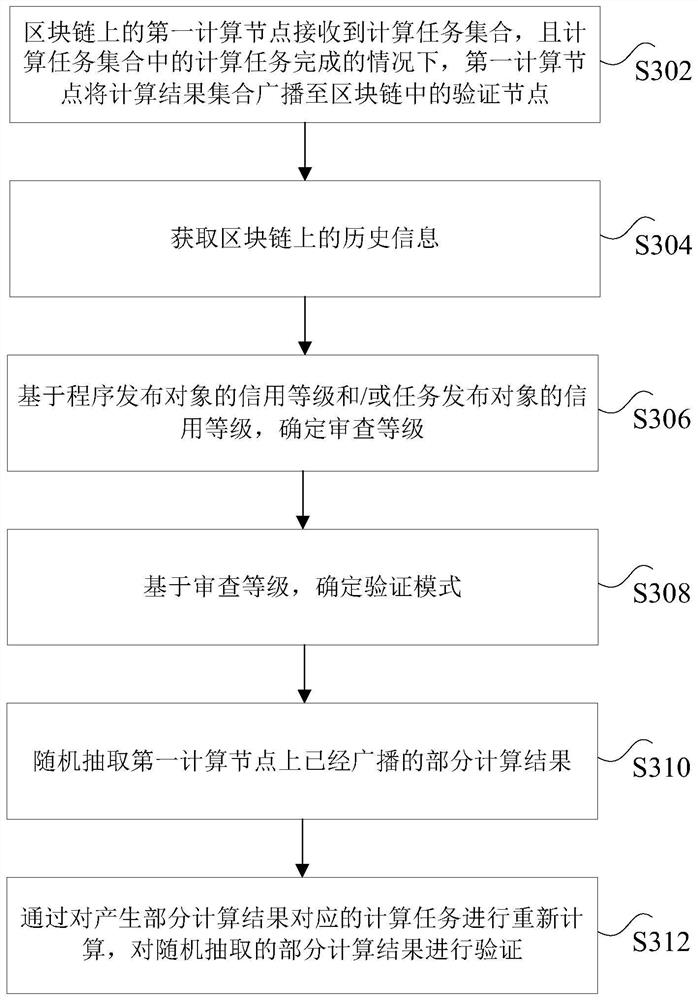
ActiveCN111881147AIncrease the difficultyFast verificationDatabase updatingFinanceParallel computingEngineering
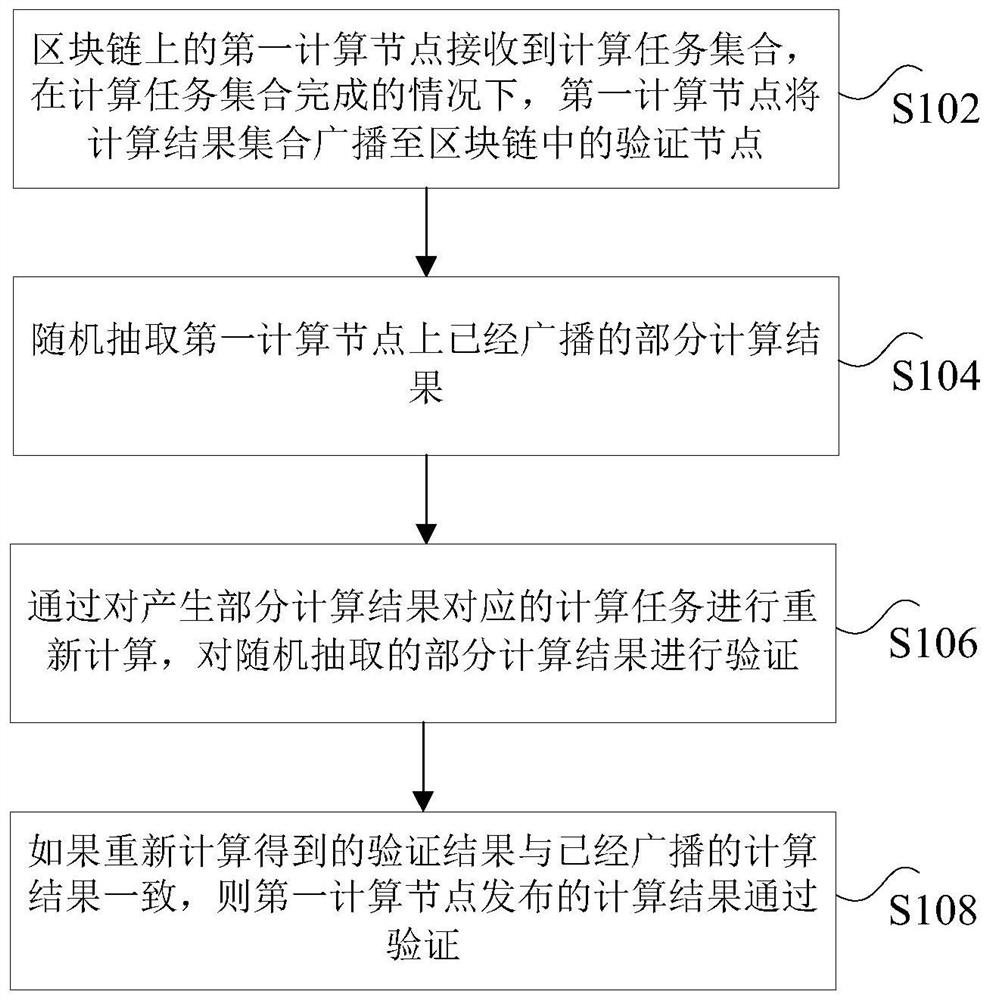
The invention discloses a computing task processing method and device, a storage medium and a processor. The method comprises the steps: enabling a first computing node on a blockchain to receive a computing task set; under the condition that the computing task set is completed, enabling the first computing node to broadcast a computing result set to a verification node in the blockchain, whereinthe verification node is any one computing node on the blockchain; randomly extracting a part of calculation results broadcasted on the first calculation node; recalculating the calculation tasks corresponding to the generated partial calculation results, and verifying the randomly extracted partial calculation results; if the recalculated verification result is consistent with the broadcasted calculation result, determining that the calculation result issued by the first calculation node passes the verification. According to the method and the device, the technical problems that a large number of calculation tasks exist in the block chain and calculation results cannot be quickly verified in the processing process of the calculation tasks in the prior art are solved.
Owner:SHENZHEN DIGITAL LIFE INST +1
Generation and verification method for visual digital identity of article
InactiveCN104009849ALow costConvenient verificationUser identity/authority verificationDigital identityDigital signature
The invention relates to a generation and verification method for the visual digital identity of an article, and belongs to the field of digital signature technologies and computer technologies. The method comprises key configuration, visual digital identity generation and identity verification. An article production or distribution unit has two keys, namely, one is the private key, and the other is the public key. The private key can be only owned by the unit and used for generating the visual digital identity of the article; the private key is composed of 16 characters. The public key can be disclosed and is stored on a unified verification platform and used for allowing a consumer to verify the visual digital identity of the article. According to the generation and verification method for the visual digital identity, neither an electronic chip nor a special card reader is required; the method has the advantages that cost is low, counterfeiting cannot be achieved, verification is convenient, the calculating speed is high, and error codes will not occur; besides, the method can be used for counterfeiting prevention and tracing of foods, medicines, agricultural products, cosmetics, crafts, bills, certificates, documents and the like and can also be used for establishing lightweight Internet of things in a cloud computing mode.
Owner:苏盛辉 +2
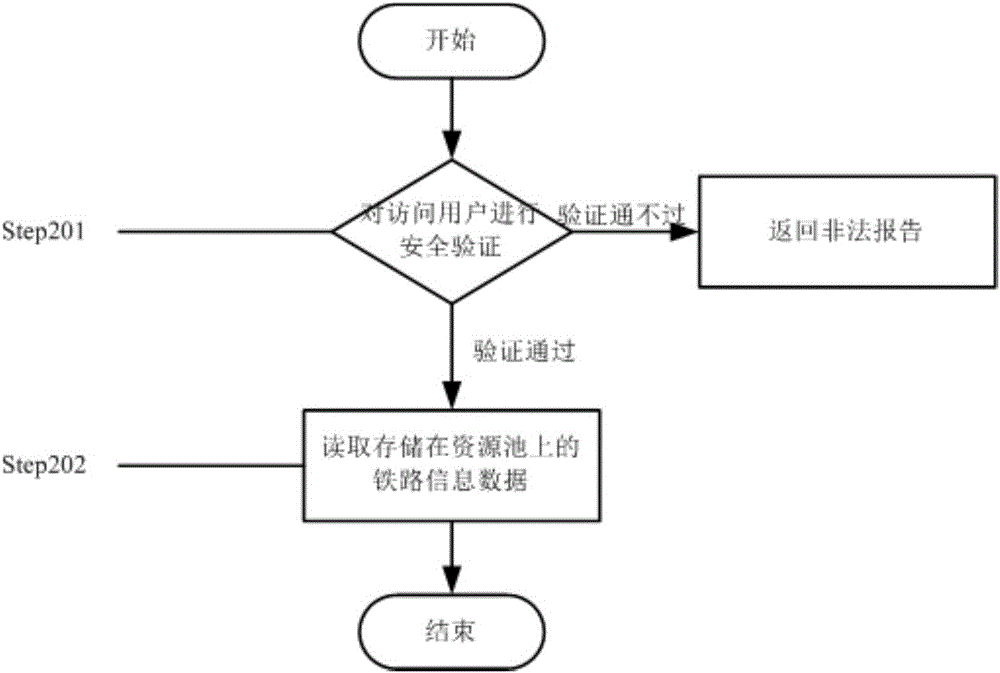
Railway information data sharing method
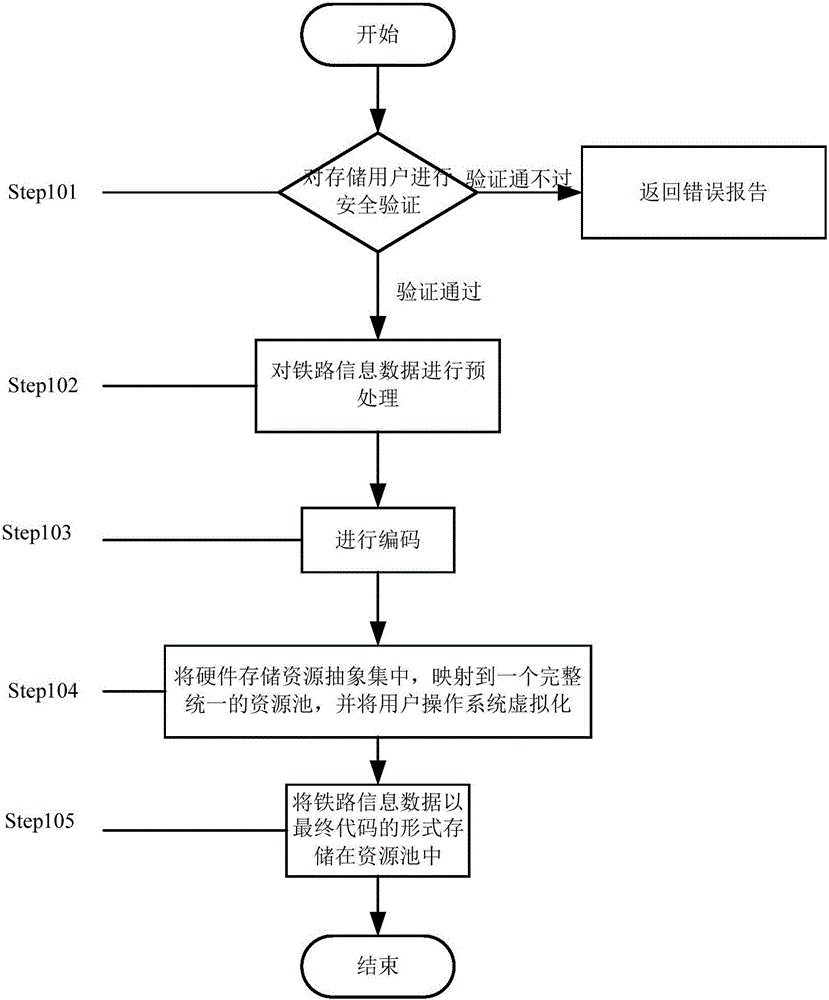
InactiveCN106203169AEasy and barrier-free sharingImprove calling speedUser identity/authority verificationDigital data protectionResource poolVirtualization
The invention provides a railway information data sharing method. The method includes secure storage of railway information data and secure access of railway information data; secure storage of the railway information data comprises steps as follows: (1) security verification is performed on a storage user identity; (2) the railway information data are pre-processed; (3) encoding is performed; (4) hardware storage resources are centralized abstractly and mapped to a complete and unified resource pool, and a user operating system is virtualized; (5) the railway information data are stored in the resource pool in the form of final codes; secure access of the railway information data comprises steps as follows: (1) security verification is performed on an access user identity; (2) the railway information data stored in the resource pool are read. With the method, barrier-free sharing can be realized, memory usage is reduced, the data call speed is increased, and the sharing security of the railway information data is improved on the premise that the convenience is guaranteed.
Owner:吴本刚
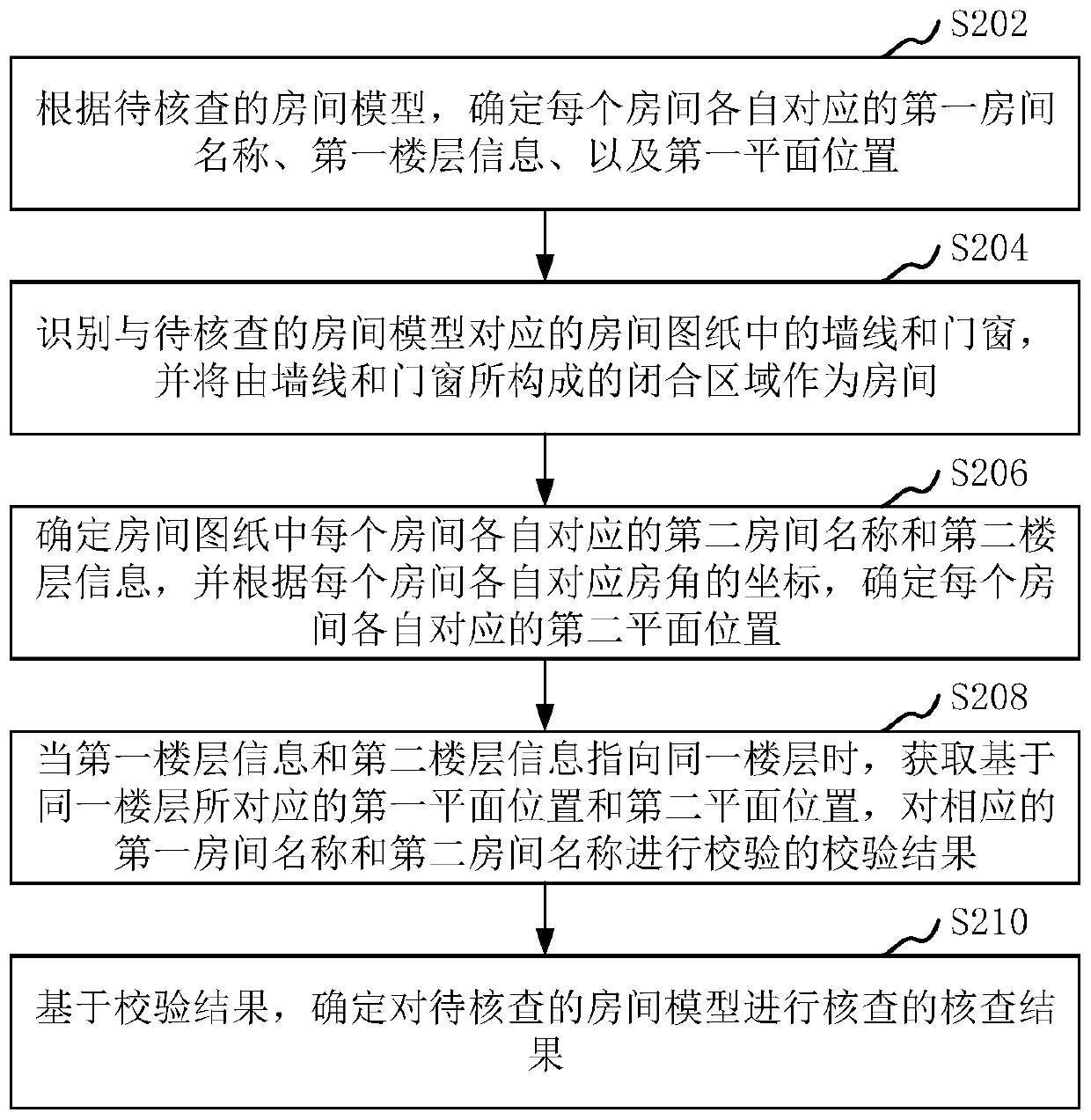
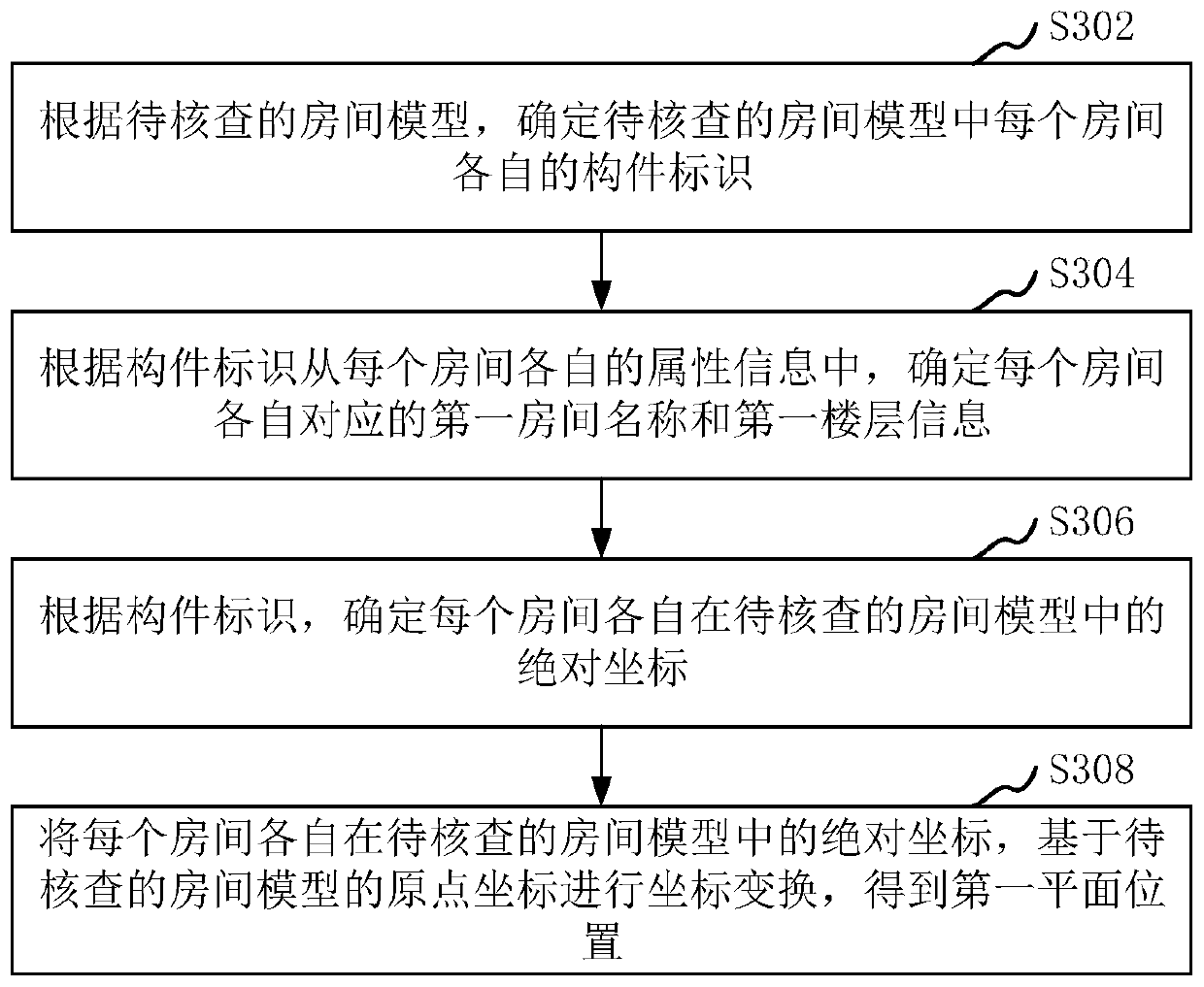
Room model checking method and device, computer equipment and storage medium
ActiveCN111210028AFast verificationImprove room inspection efficiencyGeometric CADCharacter and pattern recognitionSimulationRoomba
The invention relates to a room model checking method and device, computer equipment and a storage medium. The method comprises the following steps: determining a first room name, first floor information and a first plane position corresponding to each room according to a room model; identifying wall lines and doors and windows in a room drawing corresponding to the room model, and taking a closedarea formed by the wall lines and the doors and windows as a room; determining a second room name and second floor information corresponding to each room in the room drawing, and determining a secondplane position corresponding to each room according to the coordinates of the room angle corresponding to each room; when the first floor information and the second floor information point to the same floor, obtaining a verification result of verifying the corresponding first room name and the second room name based on the first plane position and the second plane position corresponding to the same floor; and determining a check result for checking the room model based on the check result. By adopting the method, the room checking efficiency can be improved.
Owner:深圳市万翼数字技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com